
 |
|
|||||||
| Peer to Peer The 3rd millenium technology! |
 |
|
|
Thread Tools | Search this Thread | Display Modes |
|
|
|
|
#1 | |
|
Join Date: May 2001
Location: New England
Posts: 10,016
|
Since 2002
  "This is a declaration of war on an entire generation of young voters." – Pirate Party leader Rickard Falkvinge "She had to use the bathroom on the floor. She said she was so thirsty she had to drink her own urine." – Adriana Torres-Diaz "It's affecting virtually every circus in America. We're still on hold. We've applied and haven’t gotten anything. We're trying desperately to recruit, but the artists will probably have to help out." – Jim Royal "It's true I have a hard time with the notion of creating a character and I feel it's a limit. I'm always really impressed by actors who are able to construct a character, like Johnny Depp. Then again, an actor who gives a big performance, it's always a little embarrassing, because he's there saying, 'Look at my performance.' And that bothers me a lot." – Louis Garrel "You have the world open to you now. You can get almost any song in the world as an mp3. Then you can try and find a version of it that you can actually listen to if you like good sound. The technology is taking us backwards. It's making it easier to make things worse." – Lou Reed "We can record something at night, put it on the site for breakfast and have the money in the PayPal account by 5. With all due respect for my very great friends who have come up in the record-company environment, it’s nice to see that technology has opened the doors to everybody." – Daniel Lanois "We hope this shows that using P2P in an intelligent way can benefit everyone. It allows us to use fewer resources on our network and get better performance for our customers." – Douglas Pasko, Verizon senior technologist and co-chair of the P4P Working Group "The BBC accidentally opened the floodgates and gave the world DRM-free downloads. If only it were down to something other than poor design, decisions and ineptitude." – Hacker "Last year YouTube consumed as much bandwidth as the entire Internet did in 2000." – Steve Lohr "Ex-girlfriend, Rachel Marsden, leaked instant messaging transcripts that purported to show [Wikipedia co-founder Jimmy] Wales using his influence to improperly make changes to Marsden's Wikipedia entry so he could continue 'f---ing [her] brains out'." – Asher Moses "Good beat. Love the scandal behind it." – Poster on Ashley Alexandra Dupre’s MySpace page March 15th, 2008  House Subcommittee Passes IP Bill Susan Butler A House Judiciary Subcommittee late last week passed a bill intended to strengthen the government's intellectual property (IP) enforcement efforts. Reps. John Conyers, D-Mich., Howard Berman, D-Calif., Lamar Smith, R-Texas, and others had introduced the Prioritizing Resources and Organization for Intellectual Property Act of 2007 (PRO IP Act, HR 4279). The Subcommittee on Courts, the Internet and Intellectual Property on March 6 passed the bill. The bill has the support of more than 500 diverse companies, trade associations and unions, including the Copyright Alliance, the National Music Publishers' Assn., the RIAA, 3M, Cargill, Honeywell, Nike, Verizon, the Teamsters and the American Federation of Musicians. "Having spent time at the Justice Department tackling IP enforcement and coordination issues, I understand the challenge of managing resources effectively and applaud the Subcommittee's efforts to provide leadership in this area," says NMPA president/CEO David Israelite. "This bill will go a long way towards making sure law enforcement agencies have what they need to get the job done on both domestic and international fronts." The bill creates stiffer penalties for piracy and counterfeiting activities, such as making criminal copyright violations interchangeable in order to apply enhanced penalties for repeat offenders and increasing maximum fines from $1 million to $2 million for willful use of a counterfeit mark. It harmonizes forfeiture procedures for IP offenses, making it illegal to export counterfeit goods, and eliminates loopholes that might prevent enforcement of otherwise validly registered copyrights. The bill also strengthens the administration's ability to address IP violations. It reorganizes and provides additional resources to the Justice Department to help prioritize IP related prosecutions. Additionally, it creates IP enforcement coordinators to facilitate greater enforcement efforts in foreign countries. It also provides $25 million in grant money to help state and local law enforcement combat IP crimes. The bill establishes an Intellectual Property Enforcement Representative (IPER) responsible for coordinating all federal government IP enforcement efforts, which include the work of at least eight government agencies and additional offices tasked with different roles in IP enforcement. To address the shortcomings in current IP enforcement efforts, the IPER will be established in the executive office of the president and, with the cooperation of all the relevant government agencies, will be responsible for developing a joint strategic plan for national IP enforcement. "With this vote, Congress has taken the first legislative step toward enacting a common sense bill that closes needless loopholes in the copyright laws and provides more resources to the federal government and law enforcement to fully address intellectual property theft," says Mitch Glazier, RIAA executive VP, government and industry relations. "This is great news for the music community and all businesses that rely upon intellectual property laws." http://www.billboard.biz/bbbiz/conte...cca1831b12481e  'A Declaration of War on Sweden's Youth' Plans for a new Swedish government proposal to counteract illegal file sharing met with mixed reactions on Friday. The proposal will enable courts to force internet service providers (ISPs) to give out IP addresses used in illegal file sharing to whoever owns the rights to the material. Internet service providers were quick to welcome the move, while the Pirate Party and The Pirate Bay were scathing in their criticism. "This is a declaration of war on an entire generation of young voters," said Pirate Party leader Rickard Falkvinge in a statement. Falkvinge characterized as "shameful" the government's decision to renege on its promise not to start hunting young people "on behalf of the American movie and music industries." Rather than "dismantling the rule of law", the government should recognize file sharing as "a techno-historical fact", he said. Writing in the opinion pages of newspaper Svenska Dagbladet, Minister of Justice Beatrice Ask and Minister of Culture Lena Adelsohn Liljeroth said the government was now united in how to approach the issue. Those who own the rights to illegally shared content must be able to prove that an internet service subscription has been used for infringement, the ministers pointed out. The Centre Party, one of four parties in the centre-right coalition government, reluctantly agreed to compromise on the issue despite having certain reservations. "It's not possible to get things 100 percent your own way in negotiations. It was with a degree of regret that we agreed to go along with this," spokeswoman Annie Johansson told Svenska Dagbladet. The party had previously said it would not support any policy that entailed releasing IP addresses to the courts. Speaking to Svenska Dagbladet, The Pirate Bay's Peter Sunde described the move as "completely the wrong way to go and an affront to personal integrity". With the new proposal, the government is effectively rejecting an alternative proposal put forward in a report by appeals court judge Cecilia Renfors. which called for ISPs to shut down subscribers who repeatedly downloaded films and music without permission. "It is good that the government has reached a decision on this issue and it is good that they have clearly distanced themselves from the Renfors inquiry, which would have put us providers in a position of having to police our own customers," said Bredbandsbolaget's CEO Marcus Nylén in a statement. These sentiments were echoed by Martin Tivéus, head of internet service provider Glocalnet. "It is important that the new copyright laws will take into account users' rightful interest in their own personal integrity," he said. " Neither we as a provider nor the Anti-Piracy Agency can or should make a decision as to when copyright is more important than personal integrity. For this reason it feels good that the government will hand this task to the courts." http://www.thelocal.se/10492/20080314/  Japan to Strip Internet for Illegal Downloaders: Report AFP Japanese companies plan to cut off the Internet connection of anyone who illegally downloads files in one of the world's toughest measures against online piracy, a report said Saturday. Faced with mounting complaints from the music, movie and video-game industries, four associations representing Japan's Internet service providers have agreed to take drastic action, the Yomiuri Shimbun said. The newspaper, quoting unnamed sources, said service providers would send e-mails to people who repeatedly made illegal copies and terminate their connections if they did not stop. The Internet companies will set up a panel next month involving groups representing copyright holders to draft the new guidelines, the report said. Company and government officials could not immediately be reached for comment on the report Saturday. The actions would be among the strictest in fighting online piracy. French President Nicolas Sarkozy late last year outlined similar measures to disconnect Internet users who flagrantly violated copyright laws. But for the most part, illegal downloading is being addressed through litigation against individuals. The music industry won a first-of-a-kind victory in a US court in October when a single mother in Minnesota was ordered to pay more than 220,000 dollars for sharing 24 songs online. The Yomiuri Shimbun estimated that 1.75 million people in Japan use file-sharing software, mostly to swap illegal copies. One Internet service provider considered two years ago a plan to disconnect people who swap illegal files but dropped the plan after the government said it may violate the right to privacy, the Yomiuri said. The best-known Japanese file-sharing software is called Winny, which allows users to swap games, movies and music online. It was developed by Isamu Kaneko, a young research assistant at the prestigious University of Tokyo who has become an Internet icon. But in 2006 he was fined 1.5 million yen (15,000 dollars), although he was spared jail. http://news.yahoo.com/s/afp/20080315...copyrightmusic  Authorities Seize Gadgets During Patent Raid at German Tech Fair AP Police and customs officials investigating suspected patent violations seized mobile phones, navigation devices and other gadgets in raids at a technology fair in Germany, with many Chinese exhibitors among those searched, authorities said Thursday. Police in Hanover said that more than 180 officials were involved in the searches Wednesday at the annual CeBIT trade and technology fair in the central German city. They said they filled 68 boxes with gadgets, documents and advertising material. The material included cell phones, navigation devices, electronic picture frames and flat-screen devices, a police statement said. Police said they took the identities of nine people. They added that nearly all the exhibitors searched were cooperative — except for one who resisted and was briefly taken to a police station. They said that of the 51 exhibitors affected, 24 were from mainland China, three from Hong Kong and 12 from Taiwan. Another nine were German, with one each from Poland, the Netherlands and Korea. Police did not identify the people or companies concerned. They said that "the background is the number that has been rising for years of criminal complaints by the holders of patent rights in the run-up to CeBIT." The alleged patent violations largely concerned devices with MP3, MP4 or digital video broadcast functions, as well as DVD players and blank CDs and DVDs, police said. They said the patent holders "had pointed out to the affected exhibiting firms in good time the lack of licensing contracts" and asked them to get in contact. http://www.iht.com/articles/ap/2008/...-Fair-Raid.php  Dungeon for a pirate Illegal Immigrant Left in Cell 4 Days Jon Gambrell A bailiff is under an internal investigation after a woman spent four days forgotten in a holding cell without food, water or a toilet. Bailiff Jarrod Hankins put Adriana Torres-Flores in the cell to await transport to jail Thursday and didn't let her out until Monday morning. No one on the fourth floor of the courthouse had heard her cries or her banging on the 2-inch-thick steel door of the 9 1/2-by-10 1/2-foot cell. "There's nothing at all that indicates this was done intentionally," said Washington County Chief Deputy Jay Cantrell. "This was a very, very horrible accident." Torres-Flores, 38, arrested on charges of selling pirated CDs, had been ordered held by a judge because the Mexican immigrant is in the country illegally. On Monday she was taken to a hospital, where she was treated and released and allowed to go home, though she still faces deportation. Torres-Flores told the Arkansas Democrat-Gazette through an interpreter -- her 14-year-old daughter -- that she used a shoe as a pillow to sleep in the holding cell, which had two benches, a metal table and a light she could not turn off. "She was feeling like she was going to die," said the daughter, Adriana Torres-Diaz. "She had to use the bathroom on the floor," Torres-Diaz said. "She said she was so thirsty she had to drink her own urine." The bailiff meant to call the county jail for deputies to pick her up, but got pulled away back into court and forgot Torres-Flores was waiting inside the cell, Cantrell said. The next day, snow blanketed Arkansas and the courthouse saw few employees come in for work, though both Hankins and the judge he works for, Circuit Judge William Storey, were there. No one checked the cell, as Storey did not hear cases all day, Cantrell said. "They were just a few feet away from the cell, but they never heard anything. Nothing got their attention," Cantrell said. As of Tuesday, Hankins, of Elkins, remained on administrative leave pending an internal investigation, Cantrell said. He described the bailiff as horrified over what happened. "He's extremely distraught over it," Cantrell said. "He's not distraught over his job or anything like that, he's distraught about this woman that he caused her to be left in there for four days." A bailiff for about two months, Hankins started part-time work for the sheriff's department in 2005 and in 2006 began working as an adult detention officer. Mexican consul Andres Chao said he visited Torres-Flores as she rested at home Tuesday. Chao said she still suffered from periodic headaches and stomach aches. "At this moment, Adriana is alive," Chao said. "But after four days without water, without food, in a small room -- it's unbelievable." Chao met Tuesday with Washington County Sheriff Tim Helder and county Judge Jerry Hunton to offer "the highest protest of the Mexican government." Torres-Flores will receive legal assistance from the consulate as her case moves on, Chao said. She pleaded not guilty in the criminal case against her and her trial is set for April 1. Sheriff's office deputies guarding the courthouse now check the small room at the end of their shifts to make sure no one still sits inside, Cantrell said. Deputies also plan to install a video system for the cell, as well as a light alerting passers-by that the cell is occupied. http://www.chicagotribune.com/news/n...,4294926.story  Everybody is Jumping on the Levy Bandwagon Michael Geist From levies on blank CDs to tariffs on background music played in dental offices, Canada has long held the reputation of being a haven for policies that support cultural and creator groups through levies, tariffs and other fees. In recent months, this love of levies has grown dramatically as a number of new proposals have emerged that could significantly increase the costs to consumers for Internet, television and new media services. While cultural and creator groups are the main proponents of these new funding schemes, they are by no means alone, as broadcasters, cable companies and Internet service providers have jumped into the levy and tariff game. The cultural group proposals have focused primarily on Internet services. The best known is the Songwriters Association of Canada plan to fully legalize peer-to-peer file sharing of music by adding a $5 monthly charge to the cost of Internet access. That proposal has generated considerable debate, with many consumers expressing concern about a plan that would hit all Internet users, without regard for whether they engage in peer-to-peer file sharing. Joining the SAC plan is a recent proposal that has garnered support from a handful of creator groups that includes the Canadian Film and Television Production Association, the Alliance of Canadian Cinema, Television and Radio Artists (ACTRA), the Directors Guild of Canada and Writers Guild of Canada. The proposal envisions the CRTC establishing a new mandatory ISP contribution of 2.5 per cent of broadband revenue to help fund Canadian new media content. Late last month, the groups released the results of a public opinion survey which they said found that "69 per cent of Canadians believe that ISPs should be required to help fund the production of Canadian digital media content in the same way that cable and satellite TV providers are required to contribute a small percentage of their revenues to the production of Canadian television programs." The proposals do not end there. Last week, ACTRA also called on the CRTC to require broadcasters to spend 7 per cent of their revenues on Canadian English-language drama programs. Moreover, the Creators Copyright Coalition, comprised of 16 associations and collectives, recently recommended that government extend the private copying levy to all technologies that permit private copying. Yet cultural groups are not the only ones clamouring for new levies and tariffs. Canada's broadcasters have been busy lobbying the CRTC to require cable and satellite companies to add a fee to their subscribers' bills for carriage of over-the-air broadcast signals. That would mean that advertiser supported networks such as CTV and Global would receive additional revenues from millions of Canadian television subscribers. The cable companies unsurprisingly oppose the broadcaster proposal; however, they are also looking at new tariffs of their own. In late 2006, Videotron proposed a new Internet transmission tariff that would allow ISPs to charge content creators for transmitting their work over the Internet. This proposal is viewed as part of the larger ISP push for a two-tiered Internet in which creators and websites would pay for the privilege of having their content transmitted on the "fast track," while consigning everyone else to a slow lane. Although it is unlikely that all of these proposals will be implemented in the short term, it would be a mistake to dismiss them out-of-hand. Indeed, the CRTC has already received submissions on the fee-for-carriage proposal and it is expected to conduct hearings that could address the 2.5 per cent broadband fee and the Internet transmission tariff later this year. As these plans make their way through the legislative and regulatory process, one thing seems certain. While cultural groups, broadcasters and ISPs battle it out, Canadian consumers will ultimately be left footing the bill. http://www.thestar.com/sciencetech/article/326749  Publishers Phase Out Piracy Protection on Audio Books Brad Stone Some of the largest book publishers in the world are stripping away the anticopying software on digital downloads of audio books. The trend will allow consumers who download audio books to freely transfer these digital files between devices like their computers, iPods and cellphones — and conceivably share them with others. Dropping copying restrictions could also allow a variety of online retailers to start to sell audio book downloads. The publishers hope this openness could spark renewed growth in the audio book business, which generated $923 million in sales last year, according to the Audio Publishers Association. Random House was the first to announce it was backing away from D.R.M., or digital rights management software, the protective wrapping placed around digital files to make them difficult to copy. In a letter sent to its industry partners last month, Random House, the world’s largest publisher, announced it would offer all of its audio books as unprotected MP3 files beginning this month, unless retail partners or authors specified otherwise. Penguin Group, the second-largest publisher in the United States behind Random House, now appears set to follow suit. Dick Heffernan, publisher of Penguin Audio, said the company would make all of its audio book titles available for download in the MP3 format on eMusic, the Web’s second-largest digital music service after iTunes. Penguin was initially going to join the eMusic service last fall, when it introduced its audio books download store. But it backed off when executives at Pearson, the London-based media company that owns Penguin, became concerned that such a move could fuel piracy. Mr. Heffernan said the company changed its mind partly after watching the major music labels, like Warner Brothers and Sony BMG, abandon D.R.M. on the digital music they sell on Amazon.com. “I’m looking at this as a test,” he said. “But I do believe the audio book market without D.R.M. is going to be the future.” Other major book publishers seem to agree. Chris Lynch, executive vice president and publisher of Simon & Schuster Audio, said the company would make 150 titles available for download in an unprotected digital format in “the next couple of months.” An executive at HarperCollins said the publisher was watching these developments closely but was not yet ready to end D.R.M. If the major book publishers follow music labels in abandoning copyright protections, it could alter the balance of power in the rapidly growing world of digital media downloads. Currently there is only one significant provider of digital audio books: Audible, a company in Seattle that was bought by Amazon for $300 million in January. Audible provides Apple with the audio books on the iTunes store. Apple’s popular iPod plays only audio books that are in Audible’s format or unprotected formats like MP3. Book publishers do not want to make the same error originally made by the music labels and limit consumers to a single online store to buy digital files that will play on the iPod. Doing so would give that single store owner — Apple — too much influence. Turning to the unprotected MP3 format, says Madeline McIntosh, a senior vice president at the Random House Audio Group, will enable a number of online retailers to begin selling audio books that will work on all digital devices. Some bookstores are already showing interest. The Borders Group, based in Ann Arbor, Mich., introduced an online audio book store in November using D.R.M. provided by Microsoft. Its books cannot be played on the iPod, a distinction that turns off many customers. But Pam Promer, audio book buyer for Borders, said the company welcomed moves by the publishers and planned to begin selling MP3 downloads by early spring. A spokesman for Barnes & Noble said the retailer had “no plans to enter the digital audio book market at this time.” Publishers, like the music labels and movie studios, stuck to D.R.M. out of fear that pirated copies would diminish revenue. Random House tested the justification for this fear when it introduced the D.R.M.-less concept with eMusic last fall. It encoded those audio books with a digital watermark and monitored online file sharing networks, only to find that pirated copies of its audio books had been made from physical CDs or D.R.M.-encoded digital downloads whose anticopying protections were overridden. “Our feeling is that D.R.M. is not actually doing anything to prevent piracy,” said Ms. McIntosh of Random House Audio. Amazon and Audible would not comment on whether they would preserve D.R.M. protections on their own audio books, citing Securities and Exchange Commission restrictions surrounding the recent acquisition. http://www.nytimes.com/2008/03/03/bu...audiobook.html  Amazon: What Are You Hiding? Mike Elgan Amazon shipped its Kindle e-Book reader way back in November of last year -- since then, the company has tried to paint a picture of runaway success by suggesting that the incredible popularity of the device prevents the company from keeping up with orders. Is the Amazon the Kindle really a secret failure? I wrote a blog entry back in December called "Kindle: gadget of mystery." In that piece, I listed unknowable details about the Kindle -- information that Amazon is concealing from everybody. Now, it's March, 2008, and Amazon is still stubbornly hiding the most basic facts about the Kindle -- while trying at the same time to paint a picture of success based entirely on the very facts it conceals -- such as: How many Kindles has Amazon sold? Since the day it shipped, people who wanted to buy a Kindle have been put on a waiting list -- often for more than a month and a half. In a recent earnings call, Amazon CEO Jeff Bezos said: "Kindle is, in terms of demand, is outpacing our expectations, which is certainly something that we are very grateful for. It's also on the manufacturing side causing us to scramble. We're working very hard to increase the number of units that we can build and supply per week, so that we can get back-our goal is to get into a situation as quickly as we can where when you order a Kindle, we ship it immediately." Why should we believe him? Why is Bezos so aggressively hiding the actual numbers. Have they shipped millions? Thousands? Dozens? Has Amazon sold ten times as many Kindles as Sony has the PRS-500 Reader? Or one-tenth as many? We have no idea. None! Is Amazon really working hard to ramp up production? Or is the company artificially creating a perception of high demand by playing games with production? If not, why hasn't it been able to fix the problem in four months? And since Amazon can't keep up with demand, why does it devote the very top center of the Amazon.com home page -- the most valuable real estate on the entire site -- to the creation of MORE demand? Normally, I would be willing to trust a company like Amazon when its CEO and others in the company say popularity is to blame for their inability to keep up with demand. But Amazon's conspicuous, needless secrecy about unit shipments -- an act of secrecy that has become the "elephant in the living room" for e-book reader watchers -- makes me wonder. Amazon: What are you hiding? http://blogs.computerworld.com/amazo...are_you_hiding  Pulp Fact: New Study Says Book Production is Greener Hillel Italie The latest report about the publishing industry doesn't compile sales figures, track the market for fiction or lament the future of reading. It does tell a great deal about books -- not what they say, but what they're made of. "Environmental Trends and Climate Impacts" is an 86-page summary, printed on 50 percent post-consumer recycled paper and full of charts about fiber, endangered forests and carbon footprints. The news: The book world, which uses up more than 1.5 million metric tons of paper each year, is steadily, if not entirely, finding ways to make production greener. "I was very pleasantly surprised," said Tyson Miller, founder and director of the Green Press Initiative, a nonprofit program which has worked extensively with publishers on environmental issues. "We're seeing a groundswell of momentum and real measurable progress." Commercially, publishers have certainly discovered the benefits of green, with best-sellers including Deirdre Imus' "Green This!" and Al Gore's companion guide to the Academy Award-winning movie "An Inconvenient Truth." Environmental themes can be found in novels, children's stories and business books. But reading books is healthier than making them. The climate impact survey, released Monday and co-commissioned by Green Press and the nonprofit Book Industry Study Group, offers a mixed picture about industry practices. There is great support in theory for going greener, but results are uneven. Just over half of publishers, for instance, have set specific goals for increasing use of recycled paper. About 60 percent have a formal environmental policy or are in the process of completing one. Declining to name any specific companies, Miller said "the other 40 percent just aren't taking the issue seriously or they aren't willing to pay a penny more to move in the right direction. "But," he added, "critical mass has no doubt been reached and my sense is that the majority of those publishers that aren't acting will step up and join their peers in this effort." Seventy-six publishers, representing just under half of the market, participated in the study, along with 13 printers (about 25 percent) and six paper mills (about 17 percent). One publisher that hasn't set targets is Houghton Mifflin Harcourt. A spokesman says Houghton "has been actively working to increase usage of recycled papers in its print products and has in fact substantially increased its use of recycled papers in recent years. "While we haven't formally adopted corporate-wide percentage goals for use of recycled papers, we are currently reviewing procurement policies from the standpoint of environmental impact," spokesman Rick Blake told The Associated Press. Regnery Publishing, a conservative press based in Washington, D.C., also has not set any targets and has no plans to do so. Jim Zerr, Regnery's director of production and distribution, said the reason isn't ideology, but economics; recycled paper is more expensive than regular paper. "We basically follow what our competitors and the leaders of the industry are doing," he said, adding that he didn't expect any changes until "the Random Houses of the world, and the HarperCollins and Simon & Schusters start ordering enough tonnage of that product" to make using it more practical. Compared to late 2001, when Miller began working with publishers, cooperation is easy. "University presses and a few smaller presses were making progress," he says, but no major company had announced any public environmental goals. Now, around 150 publishers, along with 10 printers and four paper manufacturers, have backed a treatise supporting recycled paper and fiber from forests certified by the Forest Stewardship Council, an international environmental organization. A turning point came in 2006 when Random House, Inc., said that it would dramatically increase its use of recycled paper, saving more than 500,000 trees a year. "We were already working on our own environmental initiatives, but to have Random House step up like that encourages everyone in the industry to come forward," said publisher Liz Perl of Rodale, which published Gore's "An Inconvenient Truth" and has another environmental book by the former vice president scheduled for 2009. Virtually all of the major publishers have taken some steps, from Hyperion switching to soy-based ink, to Penguin Group (USA) using wind power, to Scholastic, Inc. printing the deluxe edition of "Harry Potter and the Deathly Hallows" on 100 percent post-consumer waste fiber. Simon & Schuster and the Hachette Book Group USA are among those using e-book readers instead of paper manuscripts. The Random House Publishing Group is experimenting with sending books online to media outlets. http://www.newstimes.com/ci_8529962  Nine Inch Nails Slams Radiohead's 'Bait and Switch' Industrial Quality Andrew Orlowski Trent Reznor has taken a swipe at English whingers Radiohead for using the internet as a cynical marketing stunt. Like Radiohead, Reznor has released a digital version of his new album first, following it up with a physical release. Like Radiohead too, you can legally download the music for free. And it's brought Reznor immediate payback - the limited edition "deluxe" CD of Nine Inch Nails' Ghost sold out almost instantly, grossing $750,000 - although he hasn't revealed digital sales yet. So what's his beef? Reznor's proposition offers the paying fan considerably better value for money: lossless versions in FLAC, and artwork, for $5. And he contrasts this with the In Rainbows digital release. "What they did was a cool thing; I think the way they parlayed it into a marketing gimmick has certainly been shrewd," he told ABC's Michael Atkin. "But if you look at what they did, though, it was very much a bait and switch to get you to pay for a MySpace-quality stream as a way to promote a very traditional record sale." "There's nothing wrong with that - I but don't see that as a big revolution [that] they're kinda getting credit for." "What they did right: they surprised the world with a new record, and it was available digitally first. What they did wrong: by making it such a low quality thing, not even including artwork ... to me that feels insincere." Reznor agreed with the view that the model only really favors established artists, calling it a "fair critique". He also blasted the "stunning" ineptitude of major labels and said they're current licensing strategy is "five years too late". As we reported, technical problems last week drove fans to the P2P Torrent sites. Reznor took responsibility for the snafu - which he said was caused by his insistence on providing high quality streams - and apologized. "We were caught with our pants down," he said. http://www.theregister.co.uk/2008/03...ne_inch_nails/  Corned beef and a lot of cabbage Reznor's One-Week Take for 'Ghosts': $1.6 Million A week after releasing his four-volume instrumental work “Ghosts I-IV” through his Web site, Nine Inch Nails’ Trent Reznor is reporting that he amassed more than $1.6 million in orders and downloads. Reznor made the albums available at five different prices, including a free download, without any advance publicity. His marketing campaign, such as it is, consisted of a terse announcement on his nin.com Web site. On Wednesday, he reported 781,917 transactions, including free and paid downloads and orders of physical product. A $300 box set sold out of 2,500 copies within a day. Nine of the 36 songs were made available as a free download. The complete set also was available as a $5 download, a $10 double-CD and a $75 set with bonus visual content. A few months ago, Radiohead adopted a similar strategy in releasing its latest album, “In Rainbows.” Fans were allowed to name their price for the album, but the U.K. band did not release sales statistics. http://leisureblogs.chicagotribune.c...s-one-wee.html  'Guitar Hero' Subject of Patent Dispute Alex Veiga Video game publisher Activision Inc. has asked a federal court to declare that its popular "Guitar Hero" game does not violate a patent held by real-guitar maker Gibson Guitar Corp. Gibson's 1999 patent covers a virtual-reality device that included a headset with speakers and that simulated participating in a concert, according to a complaint filed on Tuesday by Santa Monica, Calif.-based Activision in U.S. District Court in Los Angeles. Gibson is trying to get Activision to stop selling "Guitar Hero" until it gets a license under the patent, according to the complaint. But Activision says it doesn't want or need a license under the patent. "We disagree with the applicability of their patent and would like a legal determination on this," George Rose, Activision's general counsel, said in a statement Wednesday. No one answered an after-hours call to Nashville, Tenn.-based Gibson. The dispute arose in January, when Gibson attorneys sent Activision a letter accusing it of violating a patent titled "System and Method for Generating and Controlling a Simulated Musical Concert Experience," according to the complaint. A copy of the patent included in the lawsuit and dated Nov. 23, 1999, describes a device that lets a user "simulate participation in a concert by playing musical instrument and wearing a head-mounted 3-D display that includes stereo speakers." The device described in the patent also includes playback of audio and video of a prerecorded concert and a separate track of audio from the user's instrument, according to the patent form. "Guitar Hero" users play songs using a stringless, plastic guitar by following graphics displayed on a TV connected to a game console. The TV also displays animated musicians playing along. All the versions of "Guitar Hero" have been a boon to Activision. The company reported last month a 90 percent increase in profit for the third quarter ended Dec. 31, in part due to strong sales of "Guitar Hero III: Legends of Rock." Shares of Activision fell 31 cents, or about 1 percent, to $26.82. http://ap.google.com/article/ALeqM5i...NlASQD8VC7K801  Games That Launched the Band GameCareerGuide.com staff Steve Schnur is worldwide executive of music and marketing for Electronic Arts. It's a high-level job that puts him in charge of the company's overall musical standing -- he is responsible for the pursuit, creation, and continuous development of the global vision for music in EA games. He believes that musical artists in the past few years have begun to see video games not as a product in which to license their music, but as an integral role in their careers. GameCareerGuide.com spoke to him about his work in the game industry and his views on music in games. GameCareerGuide.com: Tell us about your first job in either music or video games. Steve Schnur: I became part of the original programming team at MTV as a college intern, and the experience taught me more than I ever learned at NYU. In fact, much of what I absorbed at MTV remains with me to this day. I distinctly remember attending a focus group there in which a 15-year old was asked about videos compared to songs on the radio. His comment back was, "A song only becomes real to me when I see it." I still think about the implications of that kid's statement. You should, too. Since MTV first appeared in 1981, an entire generation has been raised with an expectation of visuals attached to audio. We are continuing a trend already in motion for more than 25 years, a trend already indelibly ingrained in future generations, generations raised on video games as a major entertainment source in their lives, generations raised on discovering music through these games. For this generation, the song now becomes real when they "play it." After MTV, I went on to more than two decades in radio promotion, A&R, marketing, and as a music supervisor for movies. ... But over the years, I began to sense a growing cultural shift that would lead me away from the traditional record business to where I am today. The most important lesson I've learned in 20 years is that the record business and the music industry are two distinctly different entities. And the most essential fact I know is that these last seven years at EA have been the most creatively rewarding of my entire career. GCG: What is the difference between the record business and the music industry? SS: Beginning in the mid to late 1990s, the record business fatefully chose short-term payoffs instead of long-term vision. They chased and milked trends rather than investing in creating them. They continued to believe that retail album sales were the only income that mattered. They allowed cookie-cutter radio play lists to fragment and sanitize the market. They ignored -- and often fought -- new media and digital technologies. When P2P file sharing appeared, total control suddenly belonged not to the record industry, but to the true music fans. And by using this digital technology, true music fans -- otherwise known as the consumers -- took it upon themselves to transform the industry like never before. Mergers and ownership by non-entertainment multinationals took care of the rest. When the smoke cleared, the traditional record business as we had known it was officially dead. Smart artists and their management have now finally begun to take their business to the next level. Within the past six months alone, three of the biggest acts in the world -- The Eagles, Madonna, and Radiohead -- have very publicly and profitably eschewed traditional record labels and retail distribution. Many more will follow. Deals like this are an essential part of the new music industry, growing hand-in-hand with widespread broadband access, the next generation of home entertainment systems, multi-function PDAs, and beyond. And while the traditional record business is all but buried, the music industry is about to enter one of the most extraordinary and exciting growth periods in our history. GCG: What kinds of trends do you see happening right now in video game audio? SS: I'm proud of the unprecedented relationships we've created between games and the music industry. What used to be a purely buy-sell licensing arrangement is now an ongoing series of groundbreaking co-marketing partnerships. Today, labels around the world are launching artists' entire careers around their inclusion in a top-selling title like Madden, FIFA, or Need for Speed. Radio is adding songs based on a band's inclusion in these games. Video channels are creating playlists based not on radio airplay, but on video game soundtracks. Even sports leagues are using our music selections to guide their future marketing. In less than seven years, video games have become the most effective -- and essential -- way of breaking new music in our world today. GCG: Who, for example? SS: Epic Records credits Madden 2003 as being instrumental in the breaking of Good Charlotte. Avril Lavigne was first introduced to European audiences through FIFA 2003. Fabolous was first introduced in America via NBA Live, and went on to sell over 2 million albums here. JET got their American iPod commercial based on exposure in Madden 2004. Avenged Sevenfold were an unsigned act when we featured them in Madden 2004. In the weeks following the game's release, their independent album sold tens of thousands of copies without radio airplay, and they were signed to a major label soon after. Our FIFA 2005 soundtrack featured the earliest appearances of Franz Ferdinand, Marcelo D2, and Scissor Sisters. Sony Records credits Madden 2005 as being instrumental in the breaking of Franz Ferdinand in North America. Ozomatli, a band that has existed for years with minimal sales and exposure, got an iPod commercial, a career-changing sales jump, and a Grammy nomination based on their exposure in Madden 2005. Def Jam Vendetta single-handedly created a new global market for hip-hop. Within the past two years, we've seen major international breakthroughs from acts that include Robyn, Mando Diao, Arctic Monkeys, Klaxons, Bloc Party, LCD Soundsystem, Dúné, Tribalista, Go Team, Bullet for My Valentine, The Caesars, Kasabian, Lupe Fiasco, MIA, Wolfmother, Hawthorne Heights, and others. That's just a small sampling of what we've helped make happen. It's all real and exciting proof that video games are a critical component of the new industry paradigm. I'm also excited about the monster success of Rock Band, which has instantly created an extraordinary new relationship between fans and music. Everything about it -- the remarkable software, the widespread demographic appeal, the unrivaled song library, the tremendous online capabilities, the downloadable content -- represents an entertainment breakthrough that cannot be underestimated. But most of all, I'm thrilled about Artwerk, our new joint venture with our friends at Nettwerk. For the past seven years, EA has been instrumental around the world in breaking new artists for other labels. With Artwerk we can now directly sign, launch and grow our own unique roster via our own full-service music company. Our roster, which includes Junkie XL, Airbourne, Jupiter One, and Datarock, already represents everything a label should be: diversified, unafraid, insanely talented and growing. We think of Artwerk as "music 2.0," where music, games, and digital entertainment come together like never before. GCG: Licensing music for video games has become a huge business. But there seem to be different viewpoints on whether it's any good for the art of video games. Some players enjoy the licensed music or games that allow the player to import his or her own music, or customize play lists. Other players would rather hear original scores and theme songs, arguing that games are a unique medium that requires unique music. What do you make of the debate? As an executive, what are the challenges and benefits of using licensed music or original music? SS: When we formalized in-game music under the name EA Trax, we established the new industry standards for fair licensing, label cross-promotion and artist involvement. This paradigm encompasses both original scores and licensed tracks, both of which are equally essential to the business -- and the art -- of the video game experience. The key aspect of every soundtrack must always be for the music to fit with a game's theme, lifestyle, and emotional heart. A soundtrack of licensed songs is carefully designed to maximize the emotional lift needed to enhance even greater gameplay. Each song must make you want to drive faster, score higher, hit harder. At the same time, the soundtrack has to give each artist, whether established acts or new bands, unprecedented exposure within the game itself so that a gamer can discover their favorite new song ... For titles like Medal of Honor or Command and Conquer, as well as our The Lord of the Rings, Harry Potter, James Bond, and Sims titles, we approach them as if they were major Hollywood films by contracting major Hollywood film composers. The challenge of creating any soundtrack will always be to discover, design, and define a game's ultimate audio personality. It is a creative challenge -- and opportunity -- that must be met with every title we release. Clearly, some gamers want to explore the control of full customization. We are currently developing a new technology capable of fully integrating music into existing audio -- sound effects, commentary -- while offering a continuous flow of customized tracks for every gaming platform. ... GCG: Can you explain how musical artists are contracted to work on games? And how is the process different when you're working with a contract audio engineer or audio designer rather than a musical artist? SS: My staff and I all come from similar A&R or music marketing backgrounds. We listen to a lot of music. We study all the international charts. We track college radio, mix tapes, underground clubs, and local scenes all over the world. We consult with our EA offices in every corner of the globe. We work with artists, composers, publishers and labels, both major and independent, often more than a year in advance to ensure that, in an EA game, the music will matter. EA also has a talented team of both in-house and outside engineers who handle the majority of audio design. And while the vast range of sounds you hear within our games are easily taken for granted, it is truly one of the most intricately creative elements of the software development process. ... GCG: What's the most rewarding part of your job? SS: The most rewarding part of this job has been, and always will be, the music. ... I got into the music business because I love music. Twenty-seven years later, it's what still motivates and rewards me every day. GCG: What advice do you have for people who are interested in working on the audio side of the video game business? SS: Learn everything you can and build on everything you learn. Explore all the digital capabilities of the new game systems and PDAs, but proactively prepare for the iPodTouch 2, Wii 3, PlayStation4, and the Xbox 5000. Game like no one's watching. Understand that we are on the cusp of one true global culture. Challenge your equipment, your teachers, your eyes and ears, and most of all, yourselves. Challenge everything! GCG: What games have you played recently? SS: You mean besides introducing my kids to Deep Purple, Molly Hatchet, and The Ramones on Rockband? Mostly I've been playing beta versions of upcoming EA titles. Not only do I want to ensure that each soundtrack and song choice works within the context of the gameplay itself, but I genuinely believe that EA creates and distributes the very best games in the industry. http://www.gamecareerguide.com/featu...nched_the_.php  Search Mission Russ Mitchell Google's business model of internet-search-driven advertising has become so dominant that competitors Microsoft and Yahoo can hardly compete. But will C.E.O. Eric Schmidt be able to keep Google true to its roots? When Google founders Sergey Brin and Larry Page wanted a C.E.O. for their rapidly growing company in 2001, they turned to a technology executive, Eric Schmidt, who had previously worked at Sun Microsystems and Novell. Coincidentally, Yahoo co-founders Jerry Yang and David Filo were also looking for a C.E.O. that year, and they picked a Hollywood insider: Terry Semel, who had run Warner Bros. Hollywood failed; technology prevailed. Since signing on with Google, Schmidt, 52, has channeled the founders' strategic vision and the company's technological assets to create a Web-search and online-advertising Goliath, with $5.7 billion in profits in 2007. Yahoo, meanwhile, has fallen behind Google technologically and is now fighting a hostile takeover by Microsoft. For his part, Semel quit last year. Along the way, Schmidt has become a billionaire several times over, rich enough to buy a Gulfstream G-550 and to fund philanthropic projects like the New America Foundation, a nonpartisan think tank that recently named him chairman of its board. In 2006, he was appointed to Apple's board of directors. But at Google, he faces challenges that didn't exist when he started. Already, growth in search-driven advertising is slowing, and Google's recently announced plan to run ads on mobile phones might not be a hit with consumers. The company's buyout of online-ad firm DoubleClick was approved in March. And a combined Microsoft-Yahoo would pose a more formidable threat than either company alone—which is why Google has offered to help Yahoo fend off the takeover bid. Schmidt sat down with Condé Nast Portfolio senior writer Russ Mitchell to talk about his plans for Google. Why does a merged Microsoft-Yahoo pose such a threat to Google? It's an unstable situation. But the theoretical issue is the concentration of Microsoft's resources and its history, combined with the very large share that it would have in certain applications—like instant messaging and email—that could be used essentially to break the internet and diminish choice. Break the internet? All internet-based systems today are highly interoperable, open systems. The whole antitrust trial that Microsoft went through was really about it breaking that. In favor of establishing its own proprietary standards. But what are you going to do about the deal? We've indicated that we don't think it's a good idea. All options are open. I don't want to rule out or rule in anything. Google's become so big and so successful that many would see your concerns about Microsoft's size as ironic. We had a debate about this a while ago, and it had nothing to do with Yahoo. The question was how to prevent what happened at Microsoft from happening at Google. Consumers have had more choice on the internet. And we have a set of policies that we follow—entrenched inside the culture—the most important of which is that we won't trap user data in proprietary systems. So we have a rule: You have to make it possible for people who don't like your service to get out. If I don't like Google, I can switch to Yahoo, Microsoft, or whatever. This has another impact that's not as obvious. It serves as a check and balance on poor-quality teams. They can't prevent users from fleeing bad products. It also helps us with this question of becoming too big and powerful. But you already dominate the market for Web search and online advertising, and now you're trying to buy DoubleClick, which is huge in display advertising. I don't think that DoubleClick has much to do with that argument. We decided that we wanted to work in this new space called display advertising, where we are not the leader—the leader is Yahoo. That's not the same thing as text ads, which is our primary business. The other issue that the DoubleClick deal has raised is privacy. And what we've done there—in response to U.S. and European governmental concerns—is make a series of commitments about privacy, which is very reasonable and which we should have done anyway. So you're saying that the concern about the DoubleClick deal was a good thing. To some degree. When you're inside a company, you have your own belief system. It's always good to get a look at how your company is perceived versus what your self-perception is. Google recently registered slower earnings growth. If the economy continues to worsen, how might that affect your business? Well, we don't know. There's evidence that more-measurable advertising does better than unmeasurable advertising during a slowdown. People only want to spend money on stuff that they can prove is effective. Ours is the most measurable of all the advertising systems in the world. We did well in 2001, 2002, in that recession, because people wanted measurability. You've gone through tremendous expansion, and the company is still growing. Does a slowing economy put any of your employees at risk? I think that's unlikely. The company had been hiring on the order of 100 people a week. That's a ballpark number. We hire people right out of college, so there’s a bubble in the spring, which is amortized over the year. We expanded so fast internationally that we have a lot of countries in which the oldest person by tenure has been there a year. The New York Times is under pressure to sell. Blogs are abuzz with the idea that Google ought to buy it, because it’s in your interest to keep the quality of journalism high. I'm not aware of a proposal for us to buy the New York Times, but I'd never rule anything out. So far, we've stayed away from buying content. One of the general rules we've had is "Don't own the content; partner with your content company." First, it's not our area of expertise. But the more strategic answer is that we'd be picking winners. We'd be disenfranchising a potential new entrant. Our principle is providing all the world's information. Is there anything about Sergey and Larry that drives you nuts, together or as individuals? They're clever in a way that's disruptive. Here I am, I've got it all figured out, and all of a sudden they have some idea. It disrupts this brilliant notion I just had, but they come in with a better idea. It's maddening, but that's an important part of innovation. You were brought onboard in 2001 almost as a grownup to guide the kids. Larry and Sergey are now perfectly capable of doing the things I brought to the company then. I don't come to the party today with unique knowledge that they don't have. I had a lot of management experience, but they've developed it. So what do they need you for now? We each have our own specialties. They spend time on products strategy and technology. They're heavily involved in new wireless technologies, climate-change stuff, making things faster, the expansion of search, how to make the advertising system even better from a technology perspective. My job is to run the management team on a daily basis. There are many problems that all three of us are dealing with, like the scaling of the company. I'm extremely interested in the international nature of the company because I think the future is outside the U.S., so obviously that requires a lot of travel. It was recently reported that the three of you signed a long-term agreement to stick together. Is that true? We made an informal agreement to work together for 20 years after Google went public, so I hope to be here for a long time. You're introducing Android, a mobile operating system for cell phones, later this year. Why does the world need another one? Most of the older mobile operating systems were not really designed for modern Web use. They don't run the internet applications right. Many companies are looking for an inexpensive, Web-based operating system for their upcoming mobile devices that's based on open systems—Linux, in this case. What might it do differently from what you can do on current wireless phones? Well, it has a full browser, it has Java support, and it's being marketed to the software developers to build new applications. We don't know what a lot of those are going to be, but the most interesting ones will probably combine social activity and location. I saw a freaky demo of an application in which you and I have phones with maps, and our phones find each other and tell us where to meet. When you bid on the new cell-phone spectrum back in January, you insisted that the winner open its network to new products—hardware and software—from competitors. Verizon, another bidder, said that it would open up not just the new spectrum but its existing network as well. Are you skeptical? I was initially, but actions speak louder than words. And I think Verizon has shown a commitment to open access. It concluded that it was good for Verizon's customers. The senior leadership of Verizon actually visited Google to talk to us about this and make sure they got it right. And I think it's great. I wish everybody else would open up their networks. You own a Gulfstream G-550 for your personal use. Is that what you take when you travel overseas? Well, it's very important to say that I fly with a professional crew, with a professional pilot, and I'm licensed as a crew member. Sounds like fun. How often do you take the controls? A lot. It's my hobby. http://www.portfolio.com/executives/...midt-Interview  Microsoft Challenges 'Vista Capable' Class Action Gregg Keizer Microsoft Corp. on Friday asked that a lawsuit claiming it duped consumers in a Windows Vista marketing program be suspended while the company appeals a judge's decision to grant the case class-action status. If granted, the motion would also postpone any new disclosures of potentially embarrassing company e-mails. Last month, the release of similar documents showed that top-level company executives struggled with the new operating system on machines labeled "Vista Capable," and that partners such as Dell Inc. warned Microsoft that the campaign would confuse consumers. Friday, Microsoft petitioned the Ninth Circuit Court of Appeals to hear its challenge of the case's class-action status, which was granted two weeks ago by U.S. District Court Judge Marsha Pechman. The company also filed a separate motion with Pechman on Thursday, asking her to stay the lawsuit's proceedings pending the appeal. "Continued proceedings here would cost Microsoft a substantial sum of money for discovery and divert key personnel from full-time tasks," said Charles Wright, an attorney for Microsoft, in the motion to suspend the case. "[It] would intrude on sensitive pricing decisions and strategies by OEMs, wholesalers, and retailers; and would jeopardize Microsoft's goodwill with class members -- all with respect to claims that might not proceed on a class basis at all." The papers filed with Pechman claimed that Microsoft had already produced nearly 50,000 pages of internal documents as part of the lawsuit's discovery process. Continuing the case pending appeal would likely mean disclosing even more documents. If the class-action status is denied on appeal, Microsoft argued, the money spent digging up messages and memos would have been wasted, and any negative publicity generated needlessly. Microsoft painted a picture of business secrets made public and damage done to its reputation. "Plaintiffs' discovery almost surely will involve intrusion into the most sensitive pricing decisions of the OEMs, wholesalers, and retailers who sell the PCs at issue and set their prices," said the motion. "Continued discovery thus will disrupt Microsoft's relationships with its business partners, a disruption that will be unnecessary if the Ninth Circuit reverses." Wright also contended that because the plaintiffs will have to do a national search for consumers who can join the class action, Microsoft might get a black eye for no reason. "The result will be nationwide publicity that impugns the [Windows Vista Capable] program," read the filing. "Although Microsoft fully expects to vindicate the program in the course of this litigation, allowing notice to proceed in the face of the pending appeal will jeopardize Microsoft's goodwill based on an Order that, Microsoft respectfully contends, might be held erroneous from its inception." The company's petition to the Ninth Circuit spelled out two questions it thinks the appellate court should consider. The first was Pechman's decision to base the call for class-action status on Washington state law because Microsoft is headquartered there. The second questions Pechman's approval of a "price inflation" theory, which argues that PC buyers paid more than they would have without the Vista Capable program, since Microsoft's marketing boosted demand and increased the prices of systems that could run the lowest-priced and lowest-powered version of Vista, Home Basic. Microsoft said it hoped to have a ruling on its appeal within 90 days, which would push back several tentative deadlines in the lawsuit, including a trial start in October, if the stay request is granted. All of this new legal maneuvering revolves around a lawsuit filed nearly a year ago that claims Microsoft misled PC buyers during the months leading up to Vista's release. Many of the machines that boasted the Vista Capable sticker, the lawsuit charged, were able to run only Home Basic, a version the plaintiffs said was not the "real" Vista because it omitted some of the most heavily promoted elements of the new OS, including the Aero interface. Microsoft has consistently disputed the charges, saying that Vista Home Basic was a "major advancement" over Windows XP, and part of its efforts to offer multiple versions of the new operating system. While it didn't repeat those claims in its filings last week with Pechman and the Ninth Circuit Court, it did argue that the "balance of hardship" was on it, not the plaintiffs, and so the stay should be granted. "Microsoft's interest in avoiding unnecessary litigation costs, preserving the time of its employees, insulating OEMs, wholesalers, and retailers from discovery into confidential pricing policies, and maintaining its goodwill far outweighs the interest of class members in relief they never expected before filing this action," Microsoft said. http://www.computerworld.com/action/...icleId=9067400  The BitTorrent Legend Returns: I Am aXXo Ernesto During November last year we reported that the popular DVD ripper aXXo had decided to take a break and stop releasing new material for a while. It now seems that he is back in business. A few hours ago aXXo uploaded his first movie in months. He chose “I Am Legend”. Since November 11 2007, when the last official aXXo torrent was uploaded, it has been awfully quiet. Some people assumed that aXXo had got himself caught while others claimed he had an accident. After a while it became clear that he simply decided to take some time off. An administrator on Darkside RG, the official home of aXXo explained at the time: “aXXo told us that he has decided to take a break, so you will not see new aXXo torrents anywhere for a while. Please show your support by keeping his torrents alive until he comes back, as always, he will post here first when he does.” Now, after nearly four months of absence aXXo has returned, and uploaded his first .torrent on Darkside RG and other torrent sites. It’s the news that many BitTorrent users have been waiting for. Marking his comeback with the movie “I Am Legend” could be seen as symbolic. Before aXXo decided to take a break, an estimated one million people downloaded his DVDrips every month. The search term aXXo was undoubtedly the most popular at many torrent sites. Although there are conflicting opinions in respect of the quality of his work, there can be no dispute that he was, and still is, very popular indeed. While some see him in an almost religious light, others have been quick to take advantage of his popularity for nefarious purposes, or have used the aXXo brand to draw attention to their own releases, like KLAXXON did. Even though some see him as a legend, aXXo certainly isn’t without his critics but whatever the position, his popularity is indisputable…..along with his modesty http://torrentfreak.com/axxo-returns-legend-080309/  Anonymize BitTorrent Transfers with BTGuard Ernesto BTGuard is an easy to use proxy service that adds an extra layer of privacy to your BitTorrent transfers. The service is designed for BitTorrent users who don’t want their ISPs or any third party to log or throttle their IPs or traffic. BTGuard reroutes all your BitTorrent traffic through their servers in Canada. This means that anyone who connects to you via BitTorrent, even the MPAA or RIAA, will see BTGuard’s IP, and not yours. BTGuard does not have any bandwidth or volume restrictions, and while we briefly tested the service (from Europe), the speeds were almost equal to an unsecured connection. Setting it up is fairly easy, the only thing you need to do is enter the username and password provided by BTGuard, and you’re ready to go. Please note that this is only a proxy service, so the traffic between the user and the server is not encrypted, which means that ISPs can (potentially) still monitor it. TorrentFreak asked one of the founders of the project why they launched the service, he told us: “More and more, people find their privacy being invaded on the Internet and we find it to be a very disturbing, unethical trend. There are some countries that still actively protect privacy, one of which is Canada.” The BTGuard team decided to setup in Canada not only for privacy protection, but also its close network proximity to the US. “The US is experiencing a privacy invasion epidemic more so than most. ISPs are issuing disconnection notices with little regard for privacy or the accuracy of those who notified them.” “Companies like MediaSentry collect IP addresses on P2P protocols like BitTorrent; right holders then send the IPs to your ISP. However, MediaSentry systems and techniques have no governments’ authority and are certified by no one and many institutions have received false claims. Companies like this should not be allowed to go around and make or break your Internet connection. These days, some people’s lives depend on it. This is where BTGuard comes in. The only IP companies such as MediaSentry will see is ours.” BTGuard works differently then some other similar services like VPNOut or Smarthide. Most notably it does not VPN your entire Internet connection. You simply configure your BitTorrent client to route through their servers, so it will only effect your BitTorrent downloads. BTGuard says it has received reports that it effectively bypasses throttling but at this point they cannot confirm that it works in all cases (please let us know in the comments if it does). BtGuard offers a free trial, and they welcome people to try it, so you can see if it’s works for you. After the trial it costs 4.75 Euro per month which is cheaper than most other services, and a small price to pay for privacy. http://torrentfreak.com/btguard-anon...orrent-080309/  Pirate Bay to Hollywood: Open your Own Torrent Site Ernesto Peter Sunde and Fredrik Neij from The Pirate Bay recently did a video interview which resulted in some great quotes. One such quote comes from Fredrik, he suggests that the movie and music industry should set up their own torrent site, and monetize it through advertisements. “We would be out of business.” he added. More  MTV Uses P2P Data for Playlist Selection Ernesto TMF, a popular Dutch music channel which is part of MTV said it will use data from BitTorrent and other file-sharing networks as a resource for their playlist selection. The data from these sources gives a more accurate picture of what people actually listen to, rather than counting single sales alone. TMF recently subscribed to a service from the P2P tracking company GfK. Based on a list of music titles, GfK will gather data from BitTorrent and other filesharing networks and report this back to the music channel. TMF said it will use the information to signal trends and target their audience. Initially, TMF announced that it would count downloads from file-sharing networks for their new Superchart, as more people download music than buy it. However, they canceled this plan last week after protests from the music industry, who said it would send out the wrong message. TMF, however, now say that they will use data from filesharing services as one of the sources for their playlist selection. Wouter Rutten, the spokesman for the Dutch IFPI said he doesn’t see the use of P2P data as problematic as long as they don’t explicitly use it for their music charts or advertise it in any other way. The negative reaction from the music industry on the pirate chart was to be expected, but also a little hypocrital. Last year we reported that Interscope Records, and probably other record companies, use P2P data as a marketing tool. They determine which tracks they will release as their next single, based on what people are downloading. http://torrentfreak.com/mtv-uses-p2p-data-080314/  China Seen Overtaking U.S. as Top Web Market China has surpassed the United States to become the world's largest Internet market by number of users, a research firm said on Thursday. The estimate by Beijing-based BDA was based on data from China Internet Network Information Centre which indicated that the country's Internet users totalled 210 million at end-2007. Nielsen/NetRatings put the United States Web population at 216 million for the same period, BDA said. "Based on these sources and the assumption that these markets have continued to grow in 2008 to date at the same rates that they grew in 2007, we can conclude that China has by now comfortably surpassed the United States as the world's largest Internet population," analyst Bin Liu said in a statement. BDA added that it expected e-commerce to become the next boom sector in China, as businesses take advantage of the mass market of consumers already online. (Reporting by Sophie Taylor; Editing by Edmund Klamann) http://www.reuters.com/article/media...29750720080313  Harvard Server Hacked, Database of Student Data on BitTorrent Tim Conneally Harvard, the Ivy-league bastion of higher learning released a statement on Monday that its database of applicants to the Graduate School of Arts and Sciences from last year was compromised. As many as 10,000 applicants could have had their information exposed, with at least 6,600 comprehensive profiles that include names, Social Security numbers, dates of birth, mailing and e-mail addresses, phone numbers, test scores, and school records. A small number of student records even included details as specific as personal health issues and food allergies. The statement said the extent of the hack was not fully revealed in the initial examination. However, the hackers made the degree of their compromise visible, by availing all the information on BitTorrent as a 125MB file containing a backup of the GSAS site, including the full directory structure and its three databases. According to the host of the file, the hack was executed to show that the server's admin does not know how to secure a Web site. That seems to be an echo of the 2004 case of two first-year students hacking into Oxford's computer system and publishing a front page story about it in the Oxford Student. While those students claimed to only have the security of the school in mind, the result was more a mockery of the school's inferior IT department. The GSAS' administrative dean said the school is "truly sorry" for the incident and is notifying and apologizing to everyone in the database. The school will be paying for identity theft recovery services for all parties involved. http://www.betanews.com/article/Harv...ent/1205436999  Easy to Crack Access to protected data areas without the right fingerprint Daniel Bachfeld Manufacturers of USB sticks and cards with fingerprint readers promise us that their data safes can only be opened with the right fingerprint. It turns out that an easy-to-find tool allows nosy parties to get around the protection in some products. Many secure USB sticks consist of three components: flash memory for data, a fingerprint sensor and a microcontroller that processes USB traffic, communicates with the flash memory, and controls the sensor. The flash memory itself is divided up into several logical partitions. The controller provides access to a public partition when connected to a PC. The pre-installed software on this partition then runs to perform fingerprint detection and authentication. If the fingerprint is valid, the microcontroller then provides access to the protected partition as a mapped drive on the PC. That's the theory. In practice, USB sticks with the USBest UT176 and UT169 controllers from Taiwan's Afa Technology provide access to the protected partition without any authentication. All you need to do is use the PLscsi tool to send a single USB command – Command Descriptor Block – to the stick for access to the public partition to be replaced by access to the protected one. At first, this flaw seemed to be an undocumented back door, but some sniffing with a USB monitor tool revealed it to be a major design flaw: the controller on the stick does not decide whether to provide access to the partition; the software running on Windows does. The software on the PC uses another command to decide whether read-only write access is possible. Based on the manufacturer's descriptions, you'd expect the biometrics and access control to take place entirely within the stick's microcontroller, an 8032 derivative. Various sticks affected In our tests, we found the vulnerability in the MyFlash FP1 from A-Data (USB-ID 1307:1169) and the 1GB Secure Card (USB-ID 7009:1765) sold by 9pay. The JetFlash 210 and 220 fingerprint sticks from Transcend use the chips in question and also provide access to the protected partition after transmission of a single USB command. The UT176 made by CySecure could also suffer from the same flaw, though we have not tested it yet. 9pay confirmed that it was aware of the problem, but said that only "very professional users" would be able to access the protected partition without authentication. The manufacturer says that it will be pointing out this vulnerability in the manual to prevent people from thinking that the fingerprint sensor provides a greater level of security. As a workaround, the firm recommends that users encrypt sensitive data before they save it on the card, which costs around €90 euros. The manufacturer is also thinking about switching to a different chip that would be safer. We also asked Transcend Afa, the manufacturer of the chip, to comment. Transcend said it would not be able to respond in detail because of the Chinese New Year's festival but did say that if the manufacturer of the controller confirms the bug, Transcend plans to provide a patch for partition security as a firmware update. Afa Technologies did not wish to comment at all, saying instead that we should contact the manufacturer of the sensor chip, LighTuning, which is allegedly responsible for the controller's communication with application programs. We have yet to receive a response. DIY test You can find out whether your USB stick can also be "opened" without authentication by using the open source tool PLscsi[1]. A precompiled command line version for in Windows is available; Linux users will have to compile the tool themselves. The command plscsi -w specifies USB drive as a variable. Keep in mind that the fingerprint sticks register two drives on the system when connected to the PC: a virtual CD-ROM and the normal drive. Select the latter and send the command for access (see image below). The procedure is similar for Linux, but before the command is sent you need to unmount both drives just in case the automounter automatically connected to them when the stick was plugged in. You can find the right drive by using the dmesg command and setting export PLSCSI=/dev/sdb as the variable. You will need administrator rights to perform all of these actions both on Windows and Linux. In addition to the protected partition, there is another small hidden partition where private PGP keys, passwords, and, apparently, fingerprint data are stored. We did not manage to get access to it, and in our analysis of USB traffic we could not establish whether the fingerprint stored on the hidden partition ever leaves the stick or the card. It would seem that the fingerprint stored is compared within the stick to the fingerprint read from the sensor. It;s all the more unfortunate, then, that the access command comes from outside. Conclusion The fingerprint sensors in the products mentioned above apparently only serve one purpose: they mislead interested buyers. They do not provide any significant level of protection. We can only recommend that these products not be purchased. If you want to protect your data effectively on a USB stick with a fingerprint, you would be better off with products such as MXI Security's Stealth MXP, which has integrated hardware encryption. The 1GB version also costs twice as much as 9pay's solution and more than 10 times as much as the A-Data stick. A quite affordable solution that is nonetheless secure is also available: a normal stick, the free TrueCrypt encryption software, and a good password. (dab[2]) This article was originally published in German in c't magazine 05/08, page 70 http://www.heise-online.co.uk/security/features/110280  Security Guide to Customs-Proofing Your Laptop Declan McCullagh If you travel across national borders, it's time to customs-proof your laptop. Customs officials have been stepping up electronic searches of laptops at the border, where travelers enjoy little privacy and have no legal grounds to object. Laptops and other electronic devices can be seized without reason, their contents copied, and the hardware returned hours or even weeks later. Executives have been told that they must hand over their laptop to be analyzed by border police--or be barred from boarding their flight. A report from a U.S.-based marijuana activist says U.S. border guards browsed through her laptop's contents; British customs agents scan laptops for sexual material; so do their U.S. counterparts. These procedures are entirely legal, according to court precedents so far. A U.S. federal appeals court has ruled that an in-depth analysis of a laptop's hard drive using the EnCase forensics software "was permissible without probable cause or a warrant under the border search doctrine." One lawsuit is seeking to force the government to disclose what policies it follows. The information security implications are worrisome. Sensitive business documents can be stored in computers; lawyers may have notes protected by the attorney-client privilege; and journalists may save notes about confidential sources. Regulations like Sarbanes-Oxley, the Health Insurance Portability and Accountability Act, and Gramm-Leach-Bliley may apply. A 2006 survey of business travelers showed that almost 90 percent of them didn't know that customs officials can peruse the contents of laptops and confiscate them without giving a reason. Fortunately, you have some technological defenses against overly snoopy border agents. Keep reading for our easy-to-understand, Homeland-Security-inspired, color-coded News.com Guide to Customs-Proofing Your Laptop. (And no, we're not responsible if you end up cooling your heels in some Burmese prison for using PGP; check local laws and use good judgment.) Let's assume you've already backed up your files before traveling in case your laptop gets seized for an indefinite period of time. The next thing to know is that merely setting an account password is insufficient. Unless you use encryption, a customs agent can simply remove your laptop's hard drive, plug it into another computer, and peruse its contents. There are plenty of programs, including Guidance Software's EnCase Forensic, that let police extract every bit of data possible from that hard drive. To guard against that, you can set aside a section of your computer's hard drive to be encrypted. This is the simplest approach because not all the files will be encrypted; the operating system itself and, in most cases, applications you use will remain unencrypted. For Apple OS X users, FileVault does this by seamlessly scrambling the contents of your home directory (to enable, select the Security panel in Preferences and click the "Use secure virtual memory" option). PGP sells volume encryption software for OS X and Windows. There's also the free TrueCrypt application, which runs on Windows Vista, Windows XP, OS X, and Linux. Most people use encrypted volumes to do things like save sensitive files--think tax returns, bank and credit card statements, medical records, and so on. But encryption isn't enough. Research published last month ("Lest We Remember: Cold Boot Attacks on Encryption Keys") demonstrates how encryption keys can be extracted from a laptop that's placed in sleep mode when the contents are retained in RAM. They haven't released the software to extract the contents yet, but it's not terribly difficult to write and you may not want to bet your privacy on government agencies being ignorant of this attack. The solution is to let the contents of RAM decay by turning off your computer and letting it sit for a few minutes. A test they did showed that, after five minutes, the memory contents had completely disappeared and could not be retrieved. Turning off your computer is especially important for OS X users, at least until Apple patches a security glitch that keeps account passwords in RAM. In the default configuration, the account password is the keychain password and yields passwords to wireless networks, Web sites, accounts accessed via SSH, network-mounted volumes, etc. There's more. You'll want to delete cookies and browser-stored passwords for Web sites. Erase the cache and Web browsing history. Securely delete files not protected by the encrypted volume so they can't be undeleted at the border. Here are still more tips. Another problem is that if customs agents have physical possession of your laptop and you can't see what they're doing, they can install spyware. (They have the technical ability to do so; let's put aside for the moment in which circumstances they would have the legal authority to do so. Besides, in some non-democratic regimes, questions about due process are irrelevant.) There are at least three cases in which the Feds have, with a court order, installed spyware on a suspect's computer. As encryption becomes more popular, so will the use of fedware. There may be no easy way to detect it--security software vendors generally say they will--short of booting off of a DVD or another trusted device and checking the operating system for tampering. Linux users can use a Knoppix CD or DVD for this. All these extra steps are irksome, and stem from the fact that Threat Level Yellow with an encrypted volume doesn't completely protect you. Why not? Unix-derived systems including Apple's OS X store details about VPN usage and user login times in unencrypted form. Some applications including Thunderbird save working copies of documents in an unencrypted area (/tmp or /private/tmp) outside the home directory. And the contents of the computer's virtual memory file may be readable as well. That brings us to Threat Level Orange, at which point you should encrypt everything. That means you won't have to worry about whether applications leak data outside the virtual safe of an encrypted volume. Microsoft has included the BitLocker Drive Encryption feature in the Enterprise and Ultimate versions of Windows Vista. A perpetual license for PGP Whole Disk Encryption 9.8--often viewed as the gold standard of encryption products--for Windows costs $149. Macintosh users are out of luck for now, though PGP did tell us last month that whole disk encryption for OS X is "in active development." Linux users have loop-aes and dm-crypt to choose from. The same advice as Threat Level Yellow holds for laptopping-across-the-border: shut down your computer for a few minutes to make sure the memory decays. While you're at Threat Level Orange, you might as well take some additional steps to harden your machine against other attacks. One of those is guard against having the entire contents of your computer's memory siphoned off through FireWire. This isn't new. In 2004, Maximillian Dornseif showed how to extract the contents of a computer's memory merely by plugging in an iPod to the FireWire port. A subsequent presentation by Adam Boileau in 2006 expanded the FireWire attack to Windows-based systems; he released exploit code this month. Under OS X, according to a security guide by Paul Day, setting an Open Firmware password disables physical memory access for FireWire devices. Here's how to set an Open Firmware password. If they're out to get you, or if you're sufficiently paranoid to think they are, you're at Threat Level Red. One downside with encrypted drives is that they can be a huge blinking neon side to customs officers saying: "Contraband! Likely! Here!" Even if you're law-abiding, an encrypted drive could mean unwanted hassles and delays, and the unpleasant prospect of customs officials preventing you from entering the country unless you type in your password. In the U.S., whether you can be compelled to divulge it by court order remains an unanswered question--and other nations may not observe such legal niceties. One answer is steganography, which means concealing data in a way that nobody even knows it's there. It's an electronic form of invisible ink. Data can be stored in MP3s, in videos, and even in apparently-empty space on the hard drive. Unfortunately, steganographic file systems are about as well developed as cryptographic ones were a decade ago--they're still more of a laboratory curiosity than something that's been thoroughly tested and built into commercial products. One exception is TrueCrypt, which offers two levels of plausible deniability, including a standard TrueCrypt volume that appears when you're forced to give your "password," and a hidden one that remains concealed. Some technologists remain skeptical. Jon Callas, PGP's chief technology officer, says: Quote:
Finally, there's always the option of bringing your data across the border electronically--by securely downloading it once you and your laptop have made it safely past customs. It may not work for everyone, and extremely large files may make it unwieldy as an option, but it may be the safest and easiest way to travel internationally nowadays. http://www.news.com/8301-13578_3-989...?tag=nefd.lede  2 for 1 Some Viruses Come Pre-Installed Jordan Robertson From iPods to navigation systems, some of today's hottest gadgets are landing on store shelves with some unwanted extras from the factory - pre-installed viruses that steal passwords, open doors for hackers and make computers spew spam. Computer users have been warned for years about virus threats from downloading Internet porn and opening suspicious e-mail attachments. Now they run the risk of picking up a digital infection just by plugging a new gizmo into their PCs. Recent cases reviewed by The Associated Press include some of the most widely used tech devices: Apple iPods, digital picture frames sold by Target and Best Buy stores and TomTom navigation gear. In most cases, Chinese factories - where many companies have turned to keep prices low - are the source. So far, the virus problem appears to come from lax quality control - perhaps a careless worker plugging an infected music player into a factory computer used for testing - rather than organized sabotage by hackers or the Chinese factories. It's the digital equivalent of the recent series of tainted products traced to China, including toxic toothpaste, poisonous pet food and toy trains coated in lead paint. But sloppiness is the simplest explanation, not the only one. If a virus is introduced at an earlier stage of production, by a corrupt employee or a hacker when software is uploaded to the gadget, then the problems could be far more serious and widespread. Knowing how many devices have been sold, or tracking the viruses with any precision, is impossible because of the secrecy kept by electronics makers and the companies they hire to build their products. But given the nature of mass manufacturing, the numbers could be huge. "It's like the old cockroach thing - you flip the lights on in the kitchen and they run away," said Marcus Sachs, a former White House cybersecurity official who now runs the security research group SANS Internet Storm Center. "You think you've got just one cockroach? There's probably thousands more of those little boogers that you can't see." Jerry Askew, a Los Angeles computer consultant, bought a new Uniek digital picture frame to surprise his 81-year-old mother for her birthday. But when he added family photos, it tried to unload a few surprises of its own. When he plugged the frame into his Windows PC, his antivirus program alerted him to a threat. The $50 frame, built in China and bought at Target, was infested with four viruses, including one that steals passwords. "You expect quality control coming out of the manufacturers," said Askew, 42. "You don't expect that sort of thing to be on there." Security experts say the malicious software is apparently being loaded at the final stage of production, when gadgets are pulled from the assembly line and plugged in to a computer to make sure everything works. If the testing computer is infected - say, by a worker who used it to charge his own infected iPod - the digital germ can spread to anything else that gets plugged in. The recent infections may be accidental, but security experts say they point out an avenue of attack that could be exploited by hackers. "We'll probably see a steady increase over time," said Zulfikar Ramzan, a computer security researcher at Symantec Corp. (SYMC) "The hackers are still in a bit of a testing period - they're trying to figure out if it's really worth it." Thousands of people whose antivirus software isn't up to date may have been infected by new products without even knowing it, experts warn. And even protective software may not be enough. In one case, digital frames sold at Sam's Club contained a previously unknown bug that not only steals online gaming passwords but disables antivirus software, according to security researchers at Computer Associates. "It's like if you pick up a gun you've never seen before - before you pull the trigger you'd probably check the chamber," said Joe Telafici, vice president of operations of McAfee Avert Labs, the security software maker's threat-research arm. "It's an extreme analogy, but it's the right idea. It's best to spend the extra 30 seconds to be sure than be wrong," he added. Consumers can protect themselves from most factory-loaded infections by running an antivirus program and keeping it up to date. The software checks for known viruses and suspicious behaviors that indicate an attack by malicious code - whether from a download or a gadget attached to the PC via USB cable. One information-technology worker wrote to the SANS security group that his new digital picture frame delivered "the nastiest virus that I've ever encountered in my 20-plus-year IT career." Another complained his new external hard drive had malfunctioned because it came loaded with a password-stealing virus. Monitoring suppliers in China and elsewhere is expensive, and cuts into the savings of outsourcing. But it's what U.S. companies must do to prevent poisoning on the assembly line, said Yossi Sheffi, a professor at the Massachusetts Institute of Technology specializing in supply chain management. "It's exactly the same thing, whether it happened in cyberspace or software or lead paint or toothpaste or dog food - they're all quality control issues," Sheffi said. While manufacturing breakdowns don't happen often, they have become frequent enough - especially amid intense competition among Chinese suppliers - to warrant more scrutiny by companies that rely on them, Sheffi said. "Most of the time it works," he said. "The Chinese suppliers have every reason to be good suppliers because they're in it for the long run. But it's a higher risk, and we've now seen the results of that higher risk." The AP contacted some of the world's largest electronics manufacturers for details on how they guard against infections - among them Hon Hai Precision Industry Co., which is based in Taiwan and has an iPod factory in China; Singapore-based Flextronics International Ltd. (FLEX); and Taiwan-based Quanta Computer Inc. and Asustek Computer Inc. All declined comment or did not respond. The companies whose products were infected in cases reviewed by AP refused to reveal details about the incidents. Of those that confirmed factory infections, all said they had corrected the problems and taken steps to prevent recurrences. Apple disclosed the most information, saying the virus that infected a small number of video iPods in 2006 came from a PC used to test compatibility with the gadget's software. Best Buy, the biggest consumer electronics outlet in the U.S., said it pulled its affected China-made frames from the shelves and took "corrective action" against its vendor. But the company declined repeated requests to provide details. Sam's Club and Target say they are investigating complaints but have not been able to verify their frames were contaminated. Legal experts say manufacturing infections could become a big headache for retailers that sell infected devices and the companies that make them, if customers can demonstrate they were harmed by the viruses. "The photo situation is really a cautionary tale - they were just lucky that the virus that got installed happened to be one that didn't do a lot of damage," said Cindy Cohn, legal director for the Electronic Frontier Foundation. "But there's nothing about that situation that means next time the virus won't be a more serious one." http://apnews.myway.com//article/200...D8VCSJKO0.html  To Aim Ads, Web Is Keeping Closer Eye on What You Click Louise Story A famous New Yorker cartoon from 1993 showed two dogs at a computer, with one saying to the other, “On the Internet, nobody knows you’re a dog.” That may no longer be true. A new analysis of online consumer data shows that large Web companies are learning more about people than ever from what they search for and do on the Internet, gathering clues about the tastes and preferences of a typical user several hundred times a month. These companies use that information to predict what content and advertisements people most likely want to see. They can charge steep prices for carefully tailored ads because of their high response rates. The analysis, conducted for The New York Times by the research firm comScore, provides what advertising executives say is the first broad estimate of the amount of consumer data that is transmitted to Internet companies. Privacy advocates have previously sounded alarms about the practices of Internet companies and provided vague estimates about the volume of data they collect, but they did not give comprehensive figures. The Web companies are, in effect, taking the trail of crumbs people leave behind as they move around the Internet, and then analyzing them to anticipate people’s next steps. So anybody who searches for information on such disparate topics as iron supplements, airlines, hotels and soft drinks may see ads for those products and services later on. Consumers have not complained to any great extent about data collection online. But privacy experts say that is because the collection is invisible to them. Unlike Facebook’s Beacon program, which stirred controversy last year when it broadcast its members’ purchases to their online friends, most companies do not flash a notice on the screen when they collect data about visitors to their sites. “When you start to get into the details, it’s scarier than you might suspect,” said Marc Rotenberg, executive director of the Electronic Privacy Information Center, a privacy rights group. “We’re recording preferences, hopes, worries and fears.” But executives from the largest Web companies say that privacy fears are misplaced, and that they have policies in place to protect consumers’ names and other personal information from advertisers. Moreover, they say, the data is a boon to consumers, because it makes the ads they see more relevant. These companies often connect consumer data to unique codes identifying their computers, rather than their names. “What is targeting in the long term?” said Michael Galgon, Microsoft’s chief advertising strategist. “You’re getting content about things and messaging about things that are spot-on to who you are.” The rich troves of data at the fingertips of the biggest Internet companies are also creating a new kind of digital divide within the industry. Traditional media companies, which collect far less data about visitors to their sites, are increasingly at a disadvantage when they compete for ad dollars. The major television networks and magazine and newspaper companies “aren’t even in the same league,” said Linda Abraham, an executive vice president at comScore. “They can’t really play in this sandbox.” During the Internet’s short life, most people have used a yardstick from traditional media to measure success: audience size. Like magazines and newspapers, Web sites are most often ranked based on how many people visit them and how long they are there. But on the Internet, advertisers are increasingly choosing where to place their ads based on how much sites know about Web surfers. ComScore’s analysis is a novel attempt to estimate how many times major Web companies can collect data about their users in a given month. Web companies once could monitor the actions of consumers only on their own sites. But over the last couple of years, the Internet giants have spread their reach by acting as intermediaries that place ads on thousands of Web sites, and now can follow people’s activities on far more sites. Large Web companies like Microsoft and Yahoo have also acquired a number of companies in the last year that have rich consumer data. “So many of the deals are really about data,” said David Verklin, chief executive of Carat Americas, an ad agency in the Aegis Group that decides where to place ads for clients. “Everyone feels that if we can get more data, we could put ads in front of people who are interested in them,” he said. “That’s the whole idea here: put dog food ads in front of people who have dogs.” Web companies also can collect more data as people spend more time online. The number of searches that American Web users enter each month has nearly doubled since summer of 2006, to 14.6 billion searches in January, according to comScore. ComScore analyzed 15 major media companies’ potential to collect online data in December. The analysis captured how many searches, display ads, videos and page views occurred on those sites and estimated the number of ads shown in their ad networks. These actions represented “data transmission events” — times when consumer data was zapped back to the Web companies’ servers. Five large Web operations — Yahoo, Google, Microsoft, AOL and MySpace — record at least 336 billion transmission events in a month, not counting their ad networks. The methodology was worked out with comScore and based on the advice of senior online advertising executives at two of the largest Internet companies. “I think it’s a reasonable way to look at how many touch-points companies have with their consumers,” Jules Polonetsky, the chief privacy officer for AOL, said of the comScore findings on Friday. But Mr. Polonetsky cautions that not all of the data at every company is used together. Much of it is stored separately. The information transmitted might include the person’s ZIP code, a search for anything from vacation information to celebrity gossip, or a purchase of prescription drugs or other intimate items. Some types of data, like search queries, tends to be more valuable than others. Yahoo came out with the most data collection points in a month on its own sites — about 110 billion collections, or 811 for the average user. In addition, Yahoo has about 1,700 other opportunities to collect data about the average person on partner sites like eBay, where Yahoo sells the ads. MySpace, which is owned by the News Corporation, and AOL, a unit of Time Warner, were not far behind. ComScore said it recorded the ad networks using different methods and that the exact ordering of these top companies might vary with a different methodology, but the overall picture would be similar. Google also has scores of data collection events, but the company says it is unique in that it mostly uses only current information rather than past actions to select ads. The depth of Yahoo’s database goes far in explaining why AOL is talking with Yahoo about a merger and Microsoft is willing to pay more than $41.2 billion to acquire the company. Traditional media companies come in far behind. Condé Nast magazine sites, for example, have only 34 data collection events for the average site visitor each month. The numbers for other traditional media companies, as generated by comScore, were 45 for The New York Times Company; 49 for another newspaper company, the McClatchy Corporation; and 64 for the Walt Disney Company. Some companies are trying to close the gap. Walt Disney, for example, is studying how to combine data from its divisions like ESPN, Disney and ABC. The News Corporation is exploring ways to use information that MySpace members post on that site to select ads for those members when they visit other News Corporation sites. IAC is using data from its LendingTree site to deliver ads on its other sites to people it knows are looking for mortgages. Some advertising executives say media companies will have little choice but to outsource their ad sales to companies like Microsoft and Yahoo to benefit from their data. The Web companies may prove they can use their algorithms and consumer information to better select which ads for visitors better than media companies can. “I think a lot of publishers are going to find they don’t have enough data,” said David W. Kenny, chief executive of Digitas, a digital advertising agency in the Publicis Groupe. “There’s only going to be a handful of big players who can manage the data.” People who spend more time on the Internet, of course, will have more information transmitted about them. The comScore per-person figures are averages; occasional Web users have far less transmitted about them. The comScore figures do not include the data that consumers offer voluntarily when registering for sites or e-mail services. When consumers do so, they often give sites permission to link some of their interests or searches to their user name. The figures also do not account for information people enter on social network pages. MySpace, for example, collects billions of user actions each day in the form of blogs, comments and profile updates, said Peter Levinsohn, president of Fox Interactive Media, which owns MySpace. Even with all the data Web companies have, they are finding ways to obtain more. The giant Internet portals have been buying ad-delivery companies like DoubleClick and Atlas, which have stockpiles of information. Atlas, for example, delivers 6 billion ads every day. The comScore figures do not capture such data. Executives from Web companies said they had been working to inform consumers on their data practices. These companies noted their consumer-protection policies. AOL, for example, lets users opt out of some ad targeting, Google lets users edit the search histories that are linked to their user names, Yahoo is working on a policy to obscure people’s computer identification addresses that are connected to search results, and Microsoft says it does not link any of its visitors’ behavior to their user names, even if those people are registered. A study of California adults last year found that 85 percent thought sites should not be allowed to track their behavior around the Web to show them ads, according to the Samuelson Law, Technology & Public Policy Clinic at the University of California at Berkeley, which conducted the study. http://www.nytimes.com/2008/03/10/te...10privacy.html  How Do They Track You? Let Us Count the Ways Louise Story In my article in Monday’s Times, “To Aim Ads, Web Is Keeping Closer Eye on What You Click,” I worked with comScore to develop a new measure for Web companies: how much data they can collect from users. On the Internet, companies are typically ranked by how many different people visit their sites in a given month. And when Microsoft announced its $41 billion bid for Yahoo, comScore and Nielsen Online promptly put out estimates counting how many people would be in the merged company’s total audience. But audience size is not everything in the online world. Advertisers increasingly want media companies to find their most likely customers and show their ads only to those people, rather than to the site’s entire audience. Such targeted advertising requires data, so there’s a good argument to be made that we can spot the companies that will lead the pack in online advertising by looking at the depth of data that large media companies can collect about each of their Web visitor. Here is some more detail about the methodology comScore and I came up with: The comScore study tallied five types of “data collection events” on the Internet for 15 large media companies. Four of these events are actions that occur on the sites the media companies run: Pages displayed, search queries entered, videos played, and advertising displayed. Each time one of those four things occurs, there is a conversation between the user’s computer and the server of the company that owns the site or serves the ad. The fifth area that comScore looked at was ads served on pages anywhere on the Web by advertising networks owned by the media companies. These include text ads provided by Google’s AdSense network, for example, and display ads from AOL’s Advertising.com unit. Ad networks add the ability for these companies to note where you are on other Web sites when they serve you an ad. Google, for example, can note that your Internet Protocol address is on Kelly Blue Book, if it serves you an AdSense ad there. So each time one of these five things occur, it is an “data collection event.” The data that is transferred varies for each. Typically, Web company receives information about the type of page the user is looking at, the user’s I.P. address (which sometimes has clues to the user’s location), and for advertising, the content of the ad. Most Web sites and advertising networks place cookies on users’ browsers, allowing them to recognize each time they interact with that user in the future. Cookies themselves don’t identify the name of users, but if users register with a Web site, their identities can be linked to their cookies. When all these data collection events are combined for users in the United States in December 2007, Yahoo had the potential to gather data, through 400 billion events in the month. Time Warner, which includes AOL, was second, with about 100 billion events. Google was not too far behind with 91 billion. Interestingly, Microsoft, with 51 billion events in December is far behind not only the other big Internet companies, but also the News Corporation’s Fox Interactive Media, which owns MySpace. Below is a view of this data. Here is an image that shows the data behind the graphic, as well as a version of the data that shows the average number of data collection events for each of the company’s users. See the Complete Data What is important here is not the precise numbers, but the overall picture that the biggest Internet companies are accumulating many different ways to collect data about users. Many caveats are needed: Not all of this data is useful; not all of it is retained by the companies with access to it; much of it cannot be traced back to individuals. Moreover, this method often identifies several data collection events on a single Web page. That is because one page can contain search results, video players, and ads from several sources, each of which can send different data in a different direction. Another caveat: ComScore’s method of measuring advertising networks has limitations that make it difficult to compare one network to another. For the networks run by Yahoo, Microsoft and AOL, comScore doesn’t count how many ads they actually display, but how many pages their ads could appear on. This substantially overcounts the networks’ data collection because some Web sites have several networks that compete to place ads on their pages. ComScore counts the page views on those pages - without knowing if that network did in fact serve an ad on that page view. So the ad network tallies for these companies represent potential data collection events, rather than definite ones. For Google, comScore can actually identify when ads from its AdSense network are loaded on a Web page. but this measure could overstate Google’s potential to collect data. That’s because Google may display several short text ads on one page, and comScore counts each of those text ads separately. To compensate in this study, comScore tried to figure out how many pages Google ads are loaded on pages. It took its count of ads displayed and divided that by 4.17, its estimate of the average number of AdSense ads that appear together on a page. ComScore’s December 2007 figures for AOL, moreover, do not include the reach of Tacoda, the behavioral targeting firm AOL just bought. I do not suggest using the ad network figures to make comparisons between the Internet giants. Instead, you should look at them as potential expansions of these companies’ reach. They do collect significant data from their ad networks - but possibly not as much as suggested by these figures. These comScore figures - though eye-popping - provide only a minimum level of data collection events. There are other ways these companies obtain data that comScore was unable to capture. The two largest ways left out here are ad-serving data (from the likes of Microsoft’s Atlas and Google’s desired partner DoubleClick) and user-volunteered data. By the latter, I mean the information that users enter when they register for sites or e-mail accounts as well as all the juicy details they post on social networking pages. Arnie Gullov-Singh, vice president of advertising technology at Fox Interactive Media, the owner of MySpace, likes to call this sort of information “hand-raiser data,” since people choose to type it in. I hope what I’ve done here will start a conversation. It would be fascinating to see someone try to quantify the aspects of data collection left out of this analysis. Atlas serves 6 billion ads per day, for example, which could be added in. It is also well worth watching whether most of the data proves lucrative. Perhaps there will be diminishing returns at some point, though Mike Galgon, chief advertising strategist at Microsoft (and co-founder of aQuantive), told me he didn’t think there would be. Consumers get all kinds of free services and content on the Web because they are shown ads, and media companies are increasingly showing them ads based on data they have collected about them. So, in a sense, consumers “pay” for free content and features like e-mail by letting companies collect this data about them. When regulators evaluate mergers from a consumer protection standpoint, they consider whether mergers would end up raising the prices that consumers pay for those companies’ products. Since people “pay” with information about themselves on the Internet, rather than with dollars, regulators should consider consumer data when they consider mergers. If Yahoo is to merge with Microsoft or any company, the merged company will be an entity that has significantly more data about consumers. Will consumers get more - or better - free services in exchange? http://bits.blogs.nytimes.com/2008/0...ount-the-ways/  Why We're Powerless To Resist Grazing On Endless Web Data Lee Gomes While there is a certain grand mystery to some aspects of human behavior, others can be easily explained. Just find yourself a garden-variety house cat, along with a $10 laser pointer. Many cat owners know that the lasers are the easiest way to keep the pet amused. The cats will ceaselessly, maniacally chase it as it's beamed about the room, literally climbing the walls to capture what they surely regard as some form of ultimate prey. Obviously, cats are hard-wired to hunt down small, bright objects, like birds. But since nothing in nature is as bright as a laser, they are powerless to resist its charms. Cats and lasers are useful in explaining some of the more addictive aspects of Web use, including a recent occurrence on the site for Andrew Sullivan, a popular political blogger. Mr. Sullivan's blog doesn't follow the standard practice of making room for readers to add their own comments after each blog item. Curious if he should change his policy, he put the question to a vote. Readers responded 60-40 against allowing comments. Even more striking than the fact that these readers were denying themselves a voice was the reason some of them gave for declining the offer: Like cats chasing a laser, they wouldn't be able to stop themselves. "In truth we would rarely opt not to read them," said one reader. "Blog comments have the power to hammerlock one's attention. ... We'd be impotent to resist looking over the rantings and counter-rantings. ... Not only would comments be an incredible drain on one's time (especially if we check your blog several times a day from work), but it also exposes readers to the nasty underbelly of blogging." What is it about a Web site that might make it literally irresistible? Clues are offered by research conducted by Irving Biederman, a neuroscientist at the University of Southern California, who is interested in the evolutionary and biological basis of the human need for information. Dr. Biederman first showed a collection of photographs to volunteer test subjects, and found they said they preferred certain kinds of pictures (monkeys in a tree or a group of houses along a river) over others (an empty parking lot or a pile of old paint cans). The preferred pictures had certain common features, including a good vantage on a landscape and an element of mystery. In one way or another, said Dr. Biederman, they all presented new information that somehow needed to be interpreted. When he hooked up volunteers to a brain-scanning machine, the preferred pictures were shown to generate much more brain activity than the unpreferred shots. While researchers don't yet know what exactly these brain scans signify, a likely possibility involves increased production of the brain's pleasure-enhancing neurotransmitters called opioids. In other words, coming across what Dr. Biederman calls new and richly interpretable information triggers a chemical reaction that makes us feel good, which in turn causes us to seek out even more of it. The reverse is true as well: We want to avoid not getting those hits because, for one, we are so averse to boredom. It is something we seem hard-wired to do, says Dr. Biederman. When you find new information, you get an opioid hit, and we are junkies for those. You might call us 'infovores.' " For most of human history, there was little chance of overdosing on information, because any one day in the Olduvai Gorge was a lot like any other. Today, though, we can find in the course of a few hours online more information than our ancient ancestors could in their whole lives. Just like the laser and the cat, technology is playing a trick on us. We are programmed for scarcity and can't dial back when something is abundant. The same happens with food: Because at one time we never knew when the next saber-toothed tiger might come along for food, it made sense to pack on the calories whenever we chanced upon them. That's not much help in today's world of snack aisles and super sizes. Using computers traditionally has been associated with Mr. Spock-style cerebration, the ultimate kind of left-brain activity. But Dr. Biederman is just one of many researchers now linking it with some of the oldest parts of the human brain. A group of Stanford University researchers, for example, recently found gender differences in the brains of computer gamers. Males showed more neural firings, suggesting that they were physically experiencing the game in a manner different from women. Watching a cat play with a laser, you realize the cat never learns there is no real "prey" there. You can show the cat the pointer, clicking it off and on, and it will remain transfixed. Indeed, while cats find a causal link between the pointer and the shimmering light, they come to a wrong conclusion. They believe the pointer is the container that holds the prey, and that the critter is released once the cat's owner gets the pen down from the shelf and starts to wave it around. People presumably are smarter than cats, and as we become more familiar with the Web and its torrent of information, maybe we'll do a better job learning what is useful and what isn't. http://online.wsj.com/public/article...=rss_free?=4ED  Lawsuit Could Force RIAA to Reveal Secrets Eliot Van Buskirk Things will get very ugly over the next few months for the RIAA, if one disgruntled file sharing lawsuit victim gets her way. Tanya Andersen, the single mother who filed a countersuit against the RIAA after the organization mistakenly sued her for sharing music online, attempted to hold it responsible for all sorts of heavy infractions ("RICO violations, fraud, invasion of privacy, abuse of process, electronic trespass, violation of the Computer Fraud and Abuse Act, negligent misrepresentation, the tort of 'outrage,' and deceptive business practices"). According to Mike Ratoza, a copyright lawyer with Bullivant, Houser and Bailey who teaches at the University of Oregon, Andersen is close to forcing the RIAA into the discovery phase of her countersuit, after having her original complaint dismissed on Feb. 19. Andersen's amended complaint, due March 14, will not be a layup, and there are no guarantees in litigation. But assuming her lawyer is able to craft the pleading to the judge's specifications, Andersen will have another chance to tilt at the RIAA windmill, with the case proceeding into the discovery phase. If that happens, the RIAA could be forced to release potentially incriminating details about its techniques for investigating alleged file sharers. This information would likely be held under a confidential seal, but if lawsuits over mold, tobacco, and asbestos are any indication, the RIAA's secrets will likely leak out into the legal community at large, potentially culminating in a class-action lawsuit. Once Tanya Andersen files her amended Complaint, which the RIAA is barred from contesting this time around, the organization could have to explain the following details by producing documents and allowing major-label anti-piracy executives to be deposed: - How much the RIAA's lawyers make - Why the average file sharing settlement fee is $4-5K - How it decides which file sharers to sue, and which ones not to sue - Where the settlement money goes (i.e. whether any of it makes it to the artists) If it turns out that the RIAA is paying its investigators (such as MediaSentry) a percentage of the settlements that result from their investigations, it is in even more trouble. That's illegal in many states, according to Ratoza, including New York. Things could get even worse for the RIAA. Andersen isn't likely to be granted class action certification for her suit, because federal courts (where copyright-related proceedings take place) are not friendly to class-action suits. But another RIAA lawsuit victim could use the information divulged in Andersen's case to countersue the RIAA for specific allegations (fraud and RICO violations) in a state court, where class action certification is more likely. Even without a class action lawsuit, the RIAA nutshell is likely to split wide open after Andersen's case hits the discovery phase, causing problems in subsequent cases. Ratoza expects the discovery phase in Andersen's case to start in about 90 days, and said it will last 4-6 months. The judge isn't likely to rule until early next year, but the RIAA's secrets could leak out a lot sooner. http://blog.wired.com/music/2008/03/andersen-might.html  Going to the Company Elders for Help Matt Richtel On a recent Saturday afternoon, John Toppel, a retired Hewlett-Packard sales manager, did not spend his leisure time golfing or mowing the lawn. He spent it at a local electronics store extolling the virtues of H.P. laptop computers to customers. He was not paid by the store or by Hewlett-Packard, for that matter. Mr. Toppel, 62, left the technology company four years ago, but he remains a volunteer cheerleader for H.P., one of thousands of its retirees whom the company is trying to galvanize into an auxiliary army of senior marketers, good-will ambassadors and volunteer sales people. None of them get paid; they do it, they say, because of their affection for the company. “I feel like I have two marriages: a wonderful marriage at home for 36 years and a wonderful marriage at H.P.,” Mr. Toppel said. “I guess that’s now a former marriage, but I still have strong feelings for it.” Across the country, companies are making use of retirees as part-time or temporary workers. They are taking advantage of not only their expertise, but also their desire to stay involved and engaged with the world through work. Hewlett-Packard’s twist is particularly unusual in Silicon Valley, where long-term company loyalty is as rare as a pinstripe suit. Here, people switch jobs and companies on Internet time, chasing the latest technology developments and the chance to cash in stock options or catch an initial public offering. But Hewlett-Packard, founded in 1939 before there even was a Silicon Valley, has tens of thousands of alumni, many who spent decades at the company, based in Palo Alto, Calif. Old-timers express a familial loyalty, telling stories of eating meals and drinking coffee with the founders, David Packard and William Hewlett, or receiving a baby blanket from Mr. Packard’s wife, Lucile, on the birth of a child. In a move it says reflects a renewed emphasis on grass-roots marketing in the Internet era, Hewlett-Packard is seeking to turn its retirees into a valuable asset that other, younger tech companies lack. “We’re moving forward with an effort to capitalize on the fact we have these great brand stewards,” said Michael Mendenhall, chief marketing office of Hewlett-Packard. “When you look at the importance of great word of mouth and great third-party endorsement — who better to do that than your own employees?” Mr. Mendenhall appeared last Monday at the retirees’ annual gathering with Hewlett-Packard’s chief executive, Mark Hurd. They urged more than 500 retirees who had gathered at the Computer History Museum in Mountain View, Calif. — hundreds more watched over the Internet — to do volunteer sales, join local alumni clubs, get involved in legislative issues the company cares about and represent Hewlett-Packard in philanthropic and community events. The company’s goal is to inspire involvement from as many as 40,000 retirees. Mr. Toppel, who did a recent stint as a volunteer salesman at Circuit City, said he gladly is participating because he feels great loyalty to the company. He and others also say they still own shares in the company, giving them a financial incentive to contribute. And, Mr. Toppel said, the company is giving a renewed sense of purpose to retirees. “It makes them feel good, makes them part of it, makes them feel wanted,” said Mr. Toppel, who spent 31 years at Hewlett-Packard and now is a professor of management at the business school at Santa Clara University. The idea of encouraging retirees to work for free has inspired some criticism. Susan Ayers Walker, founder of SmartSilvers Alliance, which offers consulting services to business looking to connect with older consumers, says she is offended that Hewlett-Packard can’t find some way to compensate volunteer workers, particularly salespeople. The company said participation is the reward. “It’s about being part of the H.P. community and its rich heritage,” said Mr. Mendenhall. “That’s what they get.” Their involvement can be bittersweet, say some of Hewlett-Packard retirees. The oldest among them — now into their 90s — are the last of the generation that helped build Silicon Valley, watching it evolve from endless fields of almond, plum and cherry orchards into laboratories, semiconductor companies and software makers. They also are workers from a bygone era of paternalistic employers that promised lifelong employment. That era is largely gone across the country, including at H.P., which broke a tradition of avoiding layoffs and has terminated more than 30,000 workers over the last five years. The contrast between the Hewlett-Packard of yesterday and the typical Silicon Valley company of today is especially pronounced, said Joe Schoendorf, 62, who spent 18 years at H.P. and is now a venture capitalist. “If I look at a résumé today, it says two years at Netscape, two years at Google, two years at Amazon, and then Facebook. That used to be a bad résumé that meant the person couldn’t keep a job,” said Mr. Schoendorf. “There is no institutional loyalty.” Leslie Berlin, a project historian for the Silicon Valley Archives at Stanford, said the ethos has probably changed today at Hewlett-Packard, which now has 172,000 employees. But in Silicon Valley’s history, the loyalty engendered by Hewlett-Packard stands alone, she said. “This is quite a unique phenomenon,” she said. “They represent the collective past of this place,” she said of the older retirees. To be sure, companies like I.B.M. and Lockheed Martin have loyal retiree groups. So do relatively newer entrants into the Valley’s economy and culture, like Intel. A tight-knit network of retirees in the area, alumni from places like SRI International and Xerox Palo Alto Research Center who helped build the Valley, have an enormous sense of tradition. But they often are tied not to a company but to their work on specific projects or technical standards. In the case of Hewlett-Packard, retirees talk about how the company treated them with respect. The company was, historians say, the first to adopt flexible work hours, and it put an early emphasis on ideas rather than titles. Last Monday, Chuck Ernst, 91, a former customer service manager, attended the retiree meeting with Frank Musso, 75, who spent 25 years at H.P. They said they might not have too much time or energy to get involved in volunteer projects, but they liked the way the company was reaching out. They said the company’s embrace of its retirees started in earnest several years ago and has been intensifying. “H.P. wants us to feel connected, and they’re doing all this work to keep us connected,” said Mr. Ernst. He said he thought the company probably ought to pay retirees to get involved in sales, but it’s not something he feels strongly about. “We’re proud of the company, and we don’t hesitate to let people know it.” Some former employees also do not hesitate to let the company know how it might do better. One of them is Art Fong, 88, who joined Hewlett-Packard in 1946 after being recruited by Mr. Hewlett over a spaghetti dinner. Every few years, Mr. Fong sends the company a technical suggestion, as he did on the day of the retiree meeting. “I suggested some improvements to their new TVs,” said Mr. Fong, who spent 50 years at the company, 40 of them full time, and, thanks to stock ownership, retired a wealthy man. He said he has another suggestion for the new Hewlett-Packard: “Be nice to your employees. Treat them like family.” http://www.nytimes.com/2008/03/10/te...gy/10hp-1.html  Tech’s Late Adopters Prefer the Tried and True Miguel Helft Every time he fired up his Netscape Web browser since mid-February, John Uribe was greeted with a message urging him to switch to one of Netscape’s two successors, Firefox or Flock. The missives came from AOL, Netscape’s parent company, and warned him that Netscape, which introduced millions of people to the Internet, was about to become a digital orphan. On March 1, he was told, AOL would stop providing support for Netscape, leaving a band of users loyal to the pioneering Web browser to fend for themselves if they ran into technical problems. Mr. Uribe, a 56-year-old real estate agent in Waldorf, Md., ignored every message. “It’s kind of irrational,” Mr. Uribe said as that deadline approached. “It worked for me, so I stuck with it. Until there is really some reason to totally abandon it, I won’t.” The technology industry thrives on its ability to sell new products to consumers at an ever-increasing pace, and it has turned many upgrades into painless, one-click operations. But millions of users of nearly every type of Internet service and technology, from Netscape and AOL dial-up to old e-mail systems, still prefer to ignore the pitches and sit still — or at least move ahead at their own pace. Mr. Uribe, a professed late adopter, is one of them. He still has dial-up Internet access at home and he does not lust after the latest tech gadgets. He is content with his aging Dell computer, which he said has an absurdly small amount of memory. He is hardly alone. Netscape users accounted for 0.14 percent of the Internet population in February, according to OneStat.com, which offers Web monitoring services. That is a tiny fraction of the market, but still represents more than a million users, many who use aging versions of Netscape. Meanwhile, more than nine million people still pay $10 to $25 for AOL’s dial-up service when faster broadband service is available in most parts of the country, often at comparable prices. Dial-up is a rapidly declining business, but it is not an insignificant one. After all, it accounted for most of AOL’s $5.2 billion in revenue last year. Yahoo updated its popular Web e-mail service last year, but tens of millions of its customers stuck with the company’s “classic” e-mail. And on the Well, a pioneering online community founded in 1985, hundreds of people communicate using an archaic text-only system, even though a Web-based graphical interface has been available for years. “Every other online conversational space has a toolbar where you can plug in your favorite winking face,” said David Gans, a musician and radio host, who has been a member of the Well for 22 years. Mr. Gans says he uses the Well’s text interface, in part, because it helps to keep the quality of conversations high. “Just because you can have a nuclear-powered thing that can dry your clothes in five minutes doesn’t mean there isn’t value to hanging your clothes in the backyard and talking to your neighbor while doing it,” Mr. Gans said. New, of course, is not always better, and people hang on to existing technologies for a variety of reasons, including loyalty, satisfaction with what they have, fear of time-consuming upgrades and even inertia. In the age of Facebook, blogs and micro-blogging services like Twitter, these are forces that technology companies need to understand and address as they bet their fortunes on their ability to market a nearly continuous stream of new products and upgrades. Experts say that late adopters, or technology laggards, are not necessarily Luddites and can play a pivotal role in keeping the beat of innovation. “Laggards have a bad rap, but they are crucial in pacing the nature of change,” said Paul Saffo, a technology forecaster in Silicon Valley. “Innovation requires the push of early adopters and the pull of laypeople asking whether something really works. If this was a world in which only early adopters got to choose, we’d all be using CB radios and quadraphonic stereo.” Mr. Saffo said that aspects of the laggard and early adopter co-exist in most people. They may buy the latest digital camera, but end up using only a fraction of its features, or they may proudly tote an iPhone but still pay their bills by check, rather than online. At 81, Jerry Gropp, an architect in the Seattle area, is a bit of both. He has a high-speed Internet connection through Comcast and Web e-mail accounts with Yahoo and Hotmail. But he still pays AOL for its dial-up service, largely because the desktop e-mail software packaged with it makes it easier to include maps, photographs and notes in the body of messages, rather than as attachments. “I’ve been on this for about 20 years,” he said about AOL’s service. “In some ways, the old may be the best, combined with the new.” Technology laggards are neither new nor unique to the Internet. Consider, for instance, that an estimated 13 million households are ill-prepared for the switch in February 2009 to all-digital TV broadcasts. And individuals and businesses alike have long complained about the upgrade “treadmills” that benefit software sellers, but not necessarily buyers. But the Web has changed things. In the past, many late adopters upgraded their software only when they bought new hardware or when they were forced to because they could no longer read the files they received from others. Now, Internet companies can, and do, deliver upgrades with a flip of a virtual switch — not always to the delight of their customers. In mid-2006, AOL turned its Netscape.com site, a once-popular portal that had faded into near obscurity, into a “social news” site where users’ votes would determine which items received top billing. The experience proved disastrous, as many of the mostly late adopters who still relied on Netscape.com, the default home page for the browser, disliked the change. AOL reversed course a little more than a year later, but not before losing about half of Netscape.com’s users in the United States. AOL declined to comment on the experience, but a spokeswoman pointed to a message in a company blog explaining the September 2007 course reversal: “We received some feedback that people really do associate the Netscape brand with providing mainstream news that is editorially controlled.” Dan Clifford, managing partner and founder of AnswerLab, a research company that conducts usability tests for clients like Yahoo, Intuit and eBay, offers a rule of thumb for Internet companies that want to succeed with upgrades. “People need to think about order of magnitude improvements in terms of benefits, efficiencies or costs,” Mr. Clifford said. Yahoo thought it was delivering such a vast technological improvement when it began unveiling a new e-mail system in September 2006. Eighteen months later, tens of millions of the company’s estimated 250 million e-mail users are still using the old service. Yahoo is now supporting both, saying it is happy to give customers a choice. “We have effectively segmented the market between people who have embraced the new interface and functionality that is in it, and others who are very content and have built their lives around the classic Yahoo mail interface,” said John Kremer, vice president for Yahoo Mail. There are times when people hold on to older technologies simply out of nostalgia. “I am not rational about these things,” said Stephen Lee, a doctor in Hanover, N.H., who still has dial-up access and e-mail from CompuServe, an online service founded in 1969 that AOL bought in 1998. “I have a soft spot for it,” he said, adding that he did not like to see early Internet icons fade into oblivion. It’s a similar sentiment that made Mr. Uribe hold on to the Netscape browser, even though in recent years the software had become nearly indistinguishable from Firefox, the much more popular open-source browser. But last week, Mr. Uribe reluctantly decided to upgrade, after reading an article warning that Netscape, without support, could become a target of hackers and virus writers. “I won’t continue using Netscape for old times’ sake,” he wrote in an e-mail message. “I’ve imported my bookmarks into Firefox and will remove Netscape from my computers. To avoid temptation.” http://www.nytimes.com/2008/03/12/te...12inertia.html  Centenarian Director’s Very Long View Dennis Lim WHEN referring to the Portuguese director Manoel de Oliveira, it is now — and has been for some time — customary to affix the phrase “world’s oldest active filmmaker.” The operative word is “active.” Mr. Oliveira, who turns 100 in December, has made at least one movie a year since 1990 (when he was 82). His late-career surge, a gratifyingly long goodbye, defies preconceptions of what an artist’s twilight period should be. Mr. Oliveira’s undaunted productivity is remarkable, as is the undimmed creative vigor of his films. The cultural critic Edward Said, in his writings on “late style,” identified two versions of “artistic lateness.” One produces crowning glories, models of “harmony and resolution” in which a lifetime of knowledge and mastery are serenely evident. The other is an altogether more restless sensibility, the province of artists who go anything but gently into that good night, turning out works of “intransigence, difficulty and unresolved contradiction.” Mr. Oliveira, force of nature that he is, represents both kinds of lateness, often in a single film. In this, as in so many other respects, he is his own special case. What are we to make of an artist who hit his stride in his 70s, and for whom “late style” is in effect the primary style? Many of Mr. Oliveira’s films have the pensive, melancholic quality of memento mori. But whether grappling with mortality (in “Voyage to the Beginning of the World” and “I’m Going Home,” both of which feature elderly protagonists) or with the birth pangs and death throes of empires and civilizations (“ ‘Non,’ or The Vain Glory of Command,” “A Talking Picture”), he poses many more questions than he answers. His movies, full of backward glances, are too eccentric or perverse to be considered nostalgic. While it’s tempting to liken his inquiring spirit to that of a man a quarter of his age, his longevity is hardly incidental to the work. In his richest films Mr. Oliveira creates the impression of a one-man century of cinema, a living link between old and new: the ideals of the Enlightenment, modernism and European high culture on the one hand, the uncertainty and multiplicity of the present age on the other. Regarded as a modern master in Europe, on a par with Buñuel, Dreyer and Bresson (filmmakers to whom he is sometimes compared), Mr. Oliveira is a more marginal figure in the United States. Despite regular appearances at the New York Film Festival, only a few of his films have received domestic distribution. BAMcinématek’s centennial retrospective, which opens on Friday and continues through March 30, is an opportunity to take stock of a singular career and to catch some rarely screened films: 18 of his 28 features will be shown, along with four shorts, including his first, “Working on the River Douro,” from 1931. (Mr. Oliviera is scheduled to make an appearance on Friday after a screening of his most recent film, “Christopher Columbus — The Enigma,” completed last year and shot partly in New York. The series will tour the United States in the coming months, stopping off at the Harvard Film Archive, the Film and Television Archive at the University of California, Los Angeles, and other locations.) The peculiar shape of Mr. Oliveira’s filmography — he made only three features and a smattering of shorts in the first 40 years of his career — is partly a function of Portuguese history. Born in Oporto to a well-off family, he competed in the pole vault, raced cars professionally and even performed as a trapeze artist in his youth. He had just turned to filmmaking when the dictator Antonio Salazar came to power in 1932. It took Mr. Oliveira years to make his first feature, the neo-realist street-kid parable “Aniki-Bóbó” (1942). The decades that followed were no more hospitable, especially since he did not conceal his opposition to the authoritarian regime. “I was never a political man,” Mr. Oliveira said in a recent e-mail message from Portugal. “But my obsession is with humanism, and I reject all action which is damaging to man.” During the period of enforced inactivity, Mr. Oliveira tended a farm and vineyard that his wife had inherited. “It was an enormous lesson, in terms of agriculture and human dealings with the farmers, even in regards to the laws of the land ruled by the immutable laws of nature,” he wrote. For years he acquired almost no experience as a filmmaker but was accumulating insight: “I had time for a long and profound reflection about the artistic nature of cinema, which transformed my previous certainties into new concepts between hesitations and doubt.” The ruminations led him to a guiding principle of sorts: “the simplicity of old Greek tragedies and the realism of Renaissance.” In 1931, when Mr. Oliveira made “Working on the River Douro,” a poetically edited documentary of riverside activity, the Soviet theories of montage were a big influence. Over the years, as his cinema became more cerebral, his style grew starker and more subdued, moving away from what he called “a distracting expression wherein shots succeed each other ceaselessly.” His second feature, “Rite of Spring” (1963), was pivotal. Ostensibly a piece of filmed theater, showing an enactment of the Passion of Christ in a peasant village, it is also a self-conscious making-of documentary with elements of political allegory. The tension between fiction and documentary — between different levels of reality and forms of representation — would prove central as Mr. Oliveira jump-started his career, quickly making up for lost time after the Salazar regime was overthrown in the Carnation Revolution of 1974. Many of his films are based on theatrical or literary texts and often deal with the disjunctions between film and theater, or between film and literature, even as they attempt to merge the respective mediums. Randal Johnson, the author of a new monograph on Mr. Oliveira (the first book in English about him), refers to this process as “palimpsestic writing,” resulting in films that are “consistently in dialogue” with existing texts. Some are relatively freewheeling riffs. “Abraham’s Valley” (1993) is a contemporary update of “Madame Bovary.” “Belle Toujours” (2006) is a speculative sequel to Buñuel’s “Belle du Jour.” Others, like 1978’s four-and-a-half-hour “Doomed Love” (based on a classic of Portuguese literature by Camilo Castelo Branco, and a title that sums up one of Mr. Oliveira’s favorite themes) or 1985’s seven-hour “Satin Slipper” (based on an epic Paul Claudel play, and one of the few major films not in the BAMcinématek series), are adapted with a fidelity that seems almost ascetic. “I think of film as a synthesis of all art forms,” Mr. Oliveira wrote. “And I try to balance the four fundamental pillars of film: image, word, sound and music.” He may have started in silent movies, but he is obsessed with language, as is apparent from some of his titles (“Word and Utopia,” “The Letter,” “A Talking Picture”). He layers his movies with intertitles and voice-overs, asserting that the text is as important as the image. Mr. Oliveira’s movies are often described as painterly or theatrical. His camera frame functions as a proscenium, and his actors tend to deliver their lines with a declamatory stiffness, sometimes facing the camera. This mode of direct address is in keeping with Mr. Oliveira’s notion of interactive cinema. “Each film must be finished by the spectators,” he said. (He also recognizes the comic potential of breaking the fourth wall. In “Abraham’s Valley” someone interrupts a monologue on the fall of Western civilization by tossing a cat at the camera.) His international profile went up in the ’90s when he started supplementing his stable of Portuguese actors (notably Luis Miguel Cintra and Leonor Silveira) with art-house stars like Marcello Mastrioanni, Catherine Deneuve, Michel Piccoli and John Malkovich. But his movies, steeped in history, philosophy and theology, have never made obvious concessions to the tastes of the art-film marketplace. It can seem that Mr. Oliveira, an artist liberated by age, is, as Cahiers du Cinéma once put it, beyond “the rules of cinematic decorum and commerce.” But the reality is trickier, even for an almost-100-year-old maverick. “Today the economic situation in our country and around the world has gotten much harder for resistance,” Mr. Oliveira wrote. “I don’t know if a career like his will ever be possible again,” said Mr. Malkovich, who has appeared in three of Mr. Oliveira’s films. “There’s a sense with Manoel that he feels profoundly he has a lot more to say. I think that still comes across in his movies, and that’s pretty amazing.” Already Mr. Oliviera is planning his next film, “The Strange Case of Angelica,” which, he said, “will deal with today’s situation in its terrible complexity,” much like the post-9/11 meditation on clashing civilizations, “A Talking Picture” (2003). As befits a man of his age Mr. Oliveira’s specialty is the long view, and the expanse of Portuguese history has given him plenty to work with. The new “Christopher Columbus” uses the quest of its hero — a researcher trying to prove Columbus was born in Portugal — to contemplate the once mighty empire’s central role in the age of discovery. “It expresses a certain melancholy before the greatness of a past faced with the mediocrity we have come down to today,” Mr. Oliveira wrote. Most artists are fortunate if they get to make a work with the culminating grace and authority of a final testament; Mr. Oliveira practically has half a career’s worth. (There is also one final film before the fact, made in 1982 and called “Visit, or Memories and Confessions,” about a house where he used to live, which he will only allow to be shown after his death — “for prudish reasons,” he said.) But he would be the first to caution against making too much of his longevity. “Nature is very capricious and gives to some what it takes from others,” he said. “I see myself being more admired for my age than for my films, which, being good or bad, will always be my responsibility. But I am not responsible for my age.” http://www.nytimes.com/2008/03/09/movies/09lim.html  Study: Profanity Affects PG Box Office Ryan Nakashima A new study by The Nielsen Co. found that the PG-rated movies with the least profanity made the most money at the U.S. box office. Sexuality or violence in those films had less to do with success than the language, the Nielsen PreView group said in a study being released Thursday. "The reality is that profanity, within PG, is the big demarcation between box office winner and box office loser," research and marketing director Dan O'Toole said at ShoWest, a conference where studios unveil upcoming movie lineups. "Parents are choosing PG films for their kids that have very, very low levels of profanity. We're talking one-third the level of the average PG film," he said. The research firm cross-referenced box office data on 400 films in wide release from the fall of 2005 to the fall of 2007 with their ratings for sex, violence and profanity given by Critics Inc.'s Kids-In-Mind.com Web site. Controlling for marketing and production budgets of films, as well as depictions of violence and sex, movies that scored an average 0.8 on a 10-point profanity scale collected an average of $69 million. Those that averaged 2.8 for profanity averaged $38 million. All PG movies averaged 2.3 on the profanity scale. The Nielsen unit, which launched a fee-based research Web site for studios Tuesday, also listed other early predictors of success. The company found that movies that received approval from more than 70 percent of critics, regardless of their stature, earned far more at the box office. In addition, Internet buzz about a horror film had little relation to its eventual box office draw. Other films, however, saw paydays increase in relation to Web chatter. http://ap.google.com/article/ALeqM5i...GXUKgD8VCE7PG0  Studios Announce a Deal to Help Cinemas Go 3-D David M. Halbfinger Eager to get American cinema complexes ready for a surge in 3-D movies next year, four major Hollywood studios announced on Tuesday a deal to subsidize the conversion of 10,000 theaters to digital projection systems. The announcement, at ShoWest, the annual trade show that gathers theater owners and movie distributors here, overlooked one point: the theaters that could be converted under the deal have yet to agree to it. The motion picture industry is racing to roll out digital projectors, not just because they avoid the costly printing and shipping of reels of film, but also because they’re needed to show the current generation of 3-D films, which have often been bonanzas at the box office. One, “Hannah Montana & Miley Cyrus: Best of Both Worlds Concert,” generated $31 million its opening weekend on only 683 screens, about one-fifth as many as the typical wide release. Under the deal announced on Tuesday, the Walt Disney Company, 20th Century Fox, Paramount and Universal all agreed to pay “virtual print fees” for each movie they distribute digitally to the participating theaters. Theater owners will use the fees to buy the projectors, servers and other equipment needed — about $75,000 for each auditorium. Also on Tuesday, Paramount executives confirmed that “Indiana Jones and the Kingdom of the Crystal Skull” would be released digitally, though its director, Steven Spielberg, has long insisted that his movies be released exclusively on film. Every movie that earned more than $100 million last year was released both digitally and on film. Access Integrated Technologies concluded a first round of 3,740 theater conversions last year. It now must go out and sell its systems to other cinema owners. It has three years to accomplish those installations; the studios will pay the virtual print fees for up to 10 years. The size of these virtual print fees was not disclosed, but one person involved said it would be around $800 per movie, per theater — down from about $1,000 in the first phase. Chuck Viane, president of distribution at Disney, said the studios were insistent that theater owners cover more of the cost of converting, including maintenance. “We’ve always felt that exhibition had to have some skin in the game,” he said. The announcement came as, in a separate deal, the nation’s three largest theater chains — Regal, Cinemark and AMC — were negotiating for what Variety reported would be a $1.1 billion line of credit to finance the conversion of their theaters to digital cinema. The three, bargaining as Digital Cinema Implementation Partners, own about 14,000 of the nation’s 37,000 screens. http://www.nytimes.com/2008/03/12/movies/12scre.html  Another DVD Format, but This One Says It’s Cheaper Eric A. Taub No sooner has the battle for the next-generation high definition DVD format ended, with Blu-ray triumphing over HD DVD, than a new contender has emerged. A new system that is incompatible with Blu-ray, called HD VMD, for versatile multilayer disc, is trying to find a niche. New Medium Enterprises, the London company behind HD VMD, says its system’s quality is equal to Blu-ray’s but it costs less. By undercutting the competition in production, replication and hardware costs, it thinks it can find a market among consumers with less disposable income, particularly outside the United States. An HD VMD player costs less than a Blu-ray because it uses the red-laser technologies found in today’s standard-definition DVD players. The Blu-ray and HD DVD machines use a more-expensive blue laser system. “We do not intend to take on Blu-ray,” said Shirly Levich, New Medium’s vice president and product development manager, in an e-mail message. “We see VMD as a natural extension of mass market DVD product enhanced to HD capabilities. We shall not rekindle the format war.” The industry and consumers may not see it that way, given that the company is promoting its price advantages. While Blu-ray players typically cost more than $300, an HD VMD unit is priced at $199. Sales through Amazon are scheduled to begin in five weeks, the company said. No talks have been held with the big-box retailers, like Wal-Mart Stores, to carry the product. New Medium thinks its secret weapon is Michael Jay Solomon, one of Hollywood’s best-known film distributors, who has been named its chairman. Although he has yet to approach the studios, Mr. Solomon, a former president of Warner Brothers International Television, said his long tenure in the industry would help him succeed in licensing movies for HD VMD. “It’s a combination of my good experiences and continual relationships,” Mr. Solomon said in a telephone interview from Shanghai, where he was visiting with company engineers. No matter how cheap a player is, it is useless unless major movies are released using its format. To date, New Medium has come up short. Just 17 movies are available to customers in the United States at the company’s online store, including little-known ones like “The Enigma With a Stigma” and “Kandukondain Kandukondain,” a Bollywood production. Its major suppliers to the American market are Anthem Pictures, Eros Entertainment and SFM Entertainment, all independent distributors. Some bigger movies, like “Apocalypto,” are available in other territories. Neither Walt Disney, Universal Studios nor Warner Brothers would comment on their interest in releasing movies on HD VMD. But even without major studio movies, Mr. Solomon thinks the company will be successful. The low cost of producing HD VMD master discs, from which the consumer products are made, and the inexpensive consumer players have attracted the owners of movie rights in China, India and Spain, Mr. Solomon said. He said Australia, China, India, Central Europe, Russia and Scandinavia would be major markets. “We can sell players for $90 and make a profit,” he said. In the United States, Mr. Solomon believes that producers of lesser-known movies, like religious organizations and independent filmmakers, will see HD VMD as a cost-effective way to create high-definition versions of their programming. The Blu-ray camp is unimpressed. New Medium’s price strategy will fail, said Andy Parsons, chairman of the Blu-ray Disc Association, a trade group, because it relies on a false assumption: Blu-ray technology will always be more expensive. “When you mass produce blue lasers in large quantities, hardware costs will absolutely come down,” Mr. Parsons said. “I’m sure we’ll eventually be able to charge $90 for a Blu-ray player.” The HD VMD camp “is pitching a solution at a market niche that does not exist,” said Carmi Levy, senior vice president for strategic consulting at AR Communications, a Toronto research firm. “And even if it is a niche, you will never sell enough to make it a business.” Mr. Solomon dissents. “Our idea is to create a player that people can afford. There is room for the two of us.” Unfortunately, those consumers who bought HD DVD players that are now orphaned may not agree. http://www.nytimes.com/2008/03/10/technology/10dvd.html  Serving Up Television Without the TV Set Brian Stelter The “stupid computer” is a repeated target of the dimwitted office manager Michael Scott on “The Office.” But the show itself may be motivating viewers to put down their remote controls and pick up their laptops. When the fourth season of “The Office,” an NBC comedy, had its premiere in September, one in five viewings was on a computer screen instead of a television. The episode attracted a broadcast audience of 9.7 million people, according to Nielsen Media Research. It was also streamed from the Web 2.7 million times in one week, the executive producer, Greg Daniels, said. “The Office” is on the leading edge of a sharp shift in entertainment viewing that was thought to be years away: watching television episodes on a computer screen is now a common activity for millions of consumers. “It has become a mainstream behavior in an extraordinarily quick time,” said Alan Wurtzel, the head of research for NBC, which is owned by General Electric and Vivendi. “It isn’t just the province of college students or generation Y-ers. It spans all ages.” A study in October by Nielsen Media Research found that one in four Internet users had streamed full-length television episodes online in the last three months, including 39 percent of people ages 18 to 34 and, more surprisingly, 23 percent of those 35 to 54. “I think what we’re seeing right now is a great cultural shift of how this country watches television,” said Seth MacFarlane, the creator of “Family Guy,” a Fox animated comedy that ranks among the most popular online shows. “Forty years ago, new technology changed what people watched on TV as it migrated to color. Now new technology is changing where people watch TV, literally omitting the actual television set.” Although people are watching their shows, the networks are loath to release data about how many people are watching TV shows online and how often. The reason? Possibly because Internet viewers are worth only a fraction of the advertising dollars of television viewers. “The four and a half billion we make on broadcast is never going to equate to four and a half billion online,” said Quincy Smith, the president of CBS Interactive. The most popular television shows tend to be the most-viewed online as well. While the doctors and nurses of the hit ABC drama “Grey’s Anatomy” look a little pixelated on a computer monitor, episodes of the show have been streamed more than 26 million times on ABC.com in the last six months, adding the equivalent of two full ratings points to each telecast. “Heroes,” “Ugly Betty,” “CSI,” “House” and “Gossip Girl” are among the other online hits, analysts say. Just how many shows are being streamed is unclear because there is no widely recognized version of the Nielsen TV ratings for the Internet yet. Regardless of the content, the shift is forcing the networks to rethink the long-held axioms of network schedulers and advertisers. In an address in January to television executives in Las Vegas, Jeff Zucker, the chief executive of NBC Universal, noted that NBC.com had measured more than half a billion video streams in just over a year. "Our challenge with all these ventures is to effectively monetize them so that we do not end up trading analog dollars for digital pennies,” Mr. Zucker said, calling it the No. 1 challenge for the industry. Some people pay for episodes via Apple’s iTunes Store and Amazon’s Unbox service, but many more appear to be watching streams of free, advertising-supported episodes on Web sites. In a closely watched effort, NBC Universal and the News Corporation are about to introduce their joint streaming site, called Hulu. One piece of good news for the networks and advertisers is that viewers are more likely to remember ads on the Internet versions of TV shows, partly because the commercials are less numerous and more demographically aimed online, according to many studies. For the moment, at least, conventional wisdom holds that the television and the Internet will essentially merge in the foreseeable future. Already, the hardiest of online viewers are letting PC screens replace their TVs altogether. Others are merely letting broadband connections supplement their digital video recorder. About six months ago, Peer Gopfrich, a screenwriter in Los Angeles, bought a high-resolution liquid-crystal display TV screen for his living room. Around the same time, he discovered that the television networks were offering some shows online in a high-definition format, so he hooked an old computer up to his TV monitor and started streaming. Mr. Gopfrich’s computer became a free and seemingly endless source of on-demand television. “All of a sudden, we could watch pretty much every popular show we wanted, when we wanted, in high definition in our living room,” he said. Mr. Wurtzel has found that most consumers — at least 75 percent in his studies — prefer to watch higher-quality versions of episodes via their trusty TV sets. They make distinctions between dialogue-driven comedies like “The Office,” which are better suited to laptops and iPods, and special-effects-laden dramas like “Heroes,” which look better on a big screen, he said. For a variety of shows, the Web proves valuable as a time machine, permitting users to catch up on missed episodes. The Web site for “Jericho,” a show that was canceled by CBS but revived last year because of Internet-savvy fans, had roughly 1.3 million video views in the first week after the show’s second-season debut on Feb. 12. Less than half of those views were of the premiere episode; the rest were from viewers catching up on the first season or sharing clips. In addition to tracking the episode views, CBS measures the amount of online conversation happening about shows. “We’re still midstream,” said Nina Tassler, the president of CBS Entertainment. “We’re still learning about people’s behaviors and we’re still learning about what shows really resonate with an online audience.” Other consumers use the Internet to discover new shows. Jason Kilar, the chief executive of Hulu, heard rave reviews of the NBC comedy “30 Rock” last year but never took the time to watch the show until he could stream it online. After one episode, he was hooked. “After I put my kids to sleep and I have a few minutes to spare, I’m able to catch up on the show,” he said. “It provides an opportunity to both sample and consume content without having to schedule the DVR, without having to think about the on-air schedule.” For the time being, broadcasters are harnessing the audience interest in different ways. Hulu content is widely distributed on MySpace, Yahoo, AOL and a variety of other sites. Similarly, CBS has chosen to syndicate its shows across a range of sites called the CBS Audience Network. ABC, a subsidiary of the Walt Disney Company, has been more guarded with its content, making episodes available for streaming on only its Web site. Mike Shaw, the president for sales and marketing for ABC, said ABC.com has served up more than 220 million ad impressions, or views, in the last six months, up 188 percent from the same time period a year earlier. And in the last month, all the broadcast networks have added classic series to their Web sites, making shows like “Star Trek,” “MacGyver,” “The A-Team” and “I Dream of Jeannie” available online. For companies that have sold all their available advertising space, tapping into their show libraries creates new opportunities. “We would love to have more inventory,” Patrick Keane, the chief marketing officer at CBS Interactive, told reporters last week. “The advertisers are raring to go.” http://www.nytimes.com/2008/03/10/te.../10online.html  The Battle for Wikipedia's Soul The internet: The popular online encyclopedia, written by volunteer contributors, has unlimited space. So does it matter if it includes trivia? IT IS the biggest encyclopedia in history and the most successful example of “user-generated content” on the internet, with over 9m articles in 250 languages contributed by volunteers collaborating online. But Wikipedia is facing an identity crisis as it is torn between two alternative futures. It can either strive to encompass every aspect of human knowledge, no matter how trivial; or it can adopt a more stringent editorial policy and ban articles on trivial subjects, in the hope that this will enhance its reputation as a trustworthy and credible reference source. These two conflicting visions are at the heart of a bitter struggle inside Wikipedia between “inclusionists”, who believe that applying strict editorial criteria will dampen contributors' enthusiasm for the project, and “deletionists” who argue that Wikipedia should be more cautious and selective about its entries. Consider the fictional characters of Pokémon, the Japanese game franchise with a huge global following, for example. Almost 500 of them have biographies on the English-language version of Wikipedia (the largest edition, with over 2m entries), with a level of detail that many real characters would envy. But search for biographies of the leaders of the Solidarity movement in Poland, and you would find no more than a dozen—and they are rather poorly edited. Inclusionists believe that the disparity between Pokémon and Solidarity biographies would disappear by itself, if only Wikipedia loosened its relatively tight editorial control and allowed anyone to add articles about almost anything. They argue that since Wikipedia exists online, it should not have the space constraints of a physical encyclopedia imposed upon it artificially. (“Wikipedia is not paper”, runs one slogan of the inclusionists.) Surely there is no harm, they argue, in including articles about characters from television programmes who only appear in a single episode, say? After all, since most people access Wikipedia pages via search, the inclusion of articles on niche topics will not inconvenience them. People will not be more inclined to create entries about Polish union leaders if the number of Pokémon entries is reduced from 500 to 200. The ideal Wikipedia of the inclusionists would feature as many articles on as many subjects as its contributors were able to produce, as long as they were of interest to more than just a few users. Deletionists believe that Wikipedia will be more successful if it maintains a certain relevance and quality threshold for its entries. So their ideal Wikipedia might contain biographies of the five most important leaders of Solidarity, say, and the five most important Pokémon characters, but any more than that would dilute Wikipedia's quality and compromise the brand. The presence of so many articles on trivial subjects, they argue, makes it less likely that Wikipedia will be taken seriously, so articles dealing with trivial subjects should be deleted. The rules of the game In practice, deciding what is trivial and what is important is not easy. How do you draw editorial distinctions between an article entitled “List of nicknames used by George W. Bush” (status: kept) and one about “Vice-presidents who have shot people” (status: deleted)? Or how about “Natasha Demkina: Russian girl who claims to have X-ray vision” (status: kept) and “The role of clowns in modern society” (status: deleted)? To measure a subject's worthiness for inclusion (or “notability”, in the jargon of Wikipedians), all kinds of rules have been devised. So an article in an international journal counts more than a mention in a local newspaper; ten matches on Google is better than one match; and so on. These rules are used to devise official policies on particular subjects, such as the notability of pornographic stars (a Playboy appearance earns you a Wikipedia mention; starring in a low-budget movie does not) or diplomats (permanent chiefs of station are notable, while chargés d'affaires ad interim are not). Jimmy Wales, the founder of Wikipedia, has himself fallen foul of these tricky notability criteria. Last summer he created a short entry about a restaurant in South Africa where he had dined. The entry was promptly nominated for deletion, since the restaurant had a poor Google profile and was therefore considered not notable enough. After a lot of controversy and media coverage (which, ahem, increased the restaurant's notability), the entry was kept, but the episode prompted many questions about the adequacy of the editorial process. As things stand, decisions whether to keep or delete articles are made after deliberations by Wikipedia's most ardent editors and administrators (the 1,000 or so most active Wikipedia contributors). Imagine you have just created a new entry, consisting of a few words. If a member of the Wikipedia elite believes that your submission fails to meet Wikipedia's notability criteria, it may be nominated for “speedy” deletion—in other words, removed right away—or “regular” deletion, which means the entry is removed after five days if nobody objects. (To avoid deletion or vandalism, many highly controversial articles, such as the entries on the Holocaust, Islam, terrorism or Mr Bush, can be “locked” to prevent editing or removal.) If your article is selected for deletion, you may choose to contest the decision, in which case you may be asked to provide further information. There is also a higher authority with the ultimate power to rule in controversial cases: the Arbitration Committee, which settles disputes that the administrators cannot resolve. Debates about the merits of articles often drag on for weeks, draining energy and taking up far more space than the entries themselves. Such deliberations involve volleys of arcane internal acronyms and references to obscure policies and guidelines, such as WP:APT (“Avoid Peacock Terms”—terms that merely promote the subject, without giving real information) and WP:MOSMAC (a set of guidelines for “Wikipedia articles discussing the Republic of Macedonia and the Province of Macedonia, Greece”). Covert alliances and intrigues are common. Sometimes editors resort to a practice called “sock puppetry”, in which one person creates lots of accounts and pretends to be several different people in a debate so as to create the illusion of support for a particular position. The result is that novices can quickly get lost in Wikipedia's Kafkaesque bureaucracy. According to one estimate from 2006, entries about governance and editorial policies are one of the fastest-growing areas of the site and represent around one-quarter of its content. In some ways this is a sign of Wikipedia's maturity and importance: a project of this scale needs rules to govern how it works. But the proliferation of rules, and the fact that select Wikipedians have learnt how to handle them to win arguments, now represents a danger, says Andrew Lih, a former deletionist who is now an inclusionist, and who is writing a book about Wikipedia. The behaviour of Wikipedia's self-appointed deletionist guardians, who excise anything that does not meet their standards, justifying their actions with a blizzard of acronyms, is now known as “wiki-lawyering”. Mr Lih and other inclusionists worry that this deters people from contributing to Wikipedia, and that the welcoming environment of Wikipedia's early days is giving way to hostility and infighting. There is already some evidence that the growth rate of Wikipedia's article-base is slowing. Unofficial data from October 2007 suggests that users' activity on the site is falling, when measured by the number of times an article is edited and the number of edits per month. The official figures have not been gathered and made public for almost a year, perhaps because they reveal some unpleasant truths about Wikipedia's health. It may be that Wikipedians have already taken care of the “low-hanging fruit”, having compiled articles on the most obvious topics (though this could, again, be taken as evidence of Wikipedia's maturity). But there is a limit to how much information a group of predominantly non-specialist volunteers, armed with a search engine, can create and edit. Producing articles about specialist subjects such as Solidarity activists, as opposed to Pokémon characters, requires expert knowledge from contributors and editors. If the information is not available elsewhere on the web, its notability cannot be assessed using Google. To create a new article on Wikipedia and be sure that it will survive, you need to be able to write a “deletionist-proof” entry and ensure that you have enough online backing (such as Google matches) to convince the increasingly picky Wikipedia people of its importance. This raises the threshold for writing articles so high that very few people actually do it. Many who are excited about contributing to the site end up on the “Missing Wikipedians” page: a constantly updated list of those who have decided to stop contributing. It serves as a reminder that frustration at having work removed prompts many people to abandon the project. Google has recently announced its own entry into the field, in the form of an encyclopedia-like project called “Knol” that will allow anybody to create entries on topics of their choice, with a voting system that means the best rise to the top. Tellingly, this approach is based on individualism rather than collaboration (Google will share ad revenues with the authors). No doubt it will produce its own arguments and unexpected consequences. But even if it does not turn out to be the Wikipedia-killer that some people imagine, it may push Wikipedia to rethink its editorial stance. http://www.economist.com/printeditio...ry_id=10789354  Wikipedia's Tin-Cup Approach Wears Thin The nonprofit website needs to raise funds, but it resists selling ads. Alana Semuels The new headquarters of one of the world's most popular websites is 3,000 square feet of rented space furnished with desks and chairs bought on the cheap from EBay and Craigslist. A sheet of printer paper taped to the door says the office belongs to the Wikimedia Foundation, the nonprofit that runs Wikipedia, the online almanac of anything and everything that users want to chronicle, from Thomas Aquinas to Zorba the Greek. With about 300 million page views a day, the site by some estimates could be worth many hundreds of millions of dollars if it sold advertising space. It doesn't. Wikipedia's business plan is, basically, to hold out a tin cup whenever it runs low on funds, which is very often. When it comes to money, "we are about as unsophisticated as we could possibly be," Executive Director Sue Gardner said as she swept up Styrofoam packing nuts in the office, the foundation's home since it relocated in January from St. Petersburg, Fla. "It's time for us to grow up a little bit." Growing up can be hard to do. Wikipedia, the "encyclopedia anyone can edit," is stuck in a weird Internet time warp, part grass-roots labor of love, part runaway success. A global democracy beloved by high school term paper writers and run largely by volunteers, the site is controlled for now by people who seem to view revenue with suspicion and worry that too much money -- maybe even just a little money -- would defile and possibly ruin the biggest encyclopedia in the history of the written word. "Imagine if the other top 10 websites in the world, like Yahoo or Google, tried to run their budgets by asking for donations from 14-year olds," said Chad Horohoe, a 19-year-old college student in Richmond, Va., who was until recently a Wikipedia site administrator, one of the 1,500 or so people authorized to delete pages or block users from making changes to articles. "It isn't sustainable." Looking at it one way, it's cheap to run Wikipedia and the Wikimedia Foundation's other endeavors, which include an online compendium of quotations and a multilingual dictionary and thesaurus. The annual budget is $4.6 million, more than half of it dedicated to 300 computer servers and other equipment. On the other hand, the foundation has a tough time raising a few million dollars. The last fundraising campaign featured a video of co-founder Jimmy Wales literally wringing his hands in desperation. The 45,000 or so individuals who contribute annually give an average of $33 each, so campaigns, which are conducted online, raise only about one-third of what's needed. For the rest, foundation directors have to hit up outside donors, such as Stephen J. Luczo of Seagate Technology and U2's Bono. Recent money-making proposals include a Wikipedia television game show, a Wikipedia board game and Wikipedia T-shirts. Gardner said that a board game might by OK but that a game show would be problematic, because game shows are competitive and Wikipedia is collaborative. How about selling advertising space like most big-time websites do? Don't go there unless you want to start a Wikipedian riot. Some members of the foundation's board of trustees and most of the site's editors and contributing writers zealously oppose advertising. After a staff member in 2002 raised the possibility in the Wikipedia community, a facet of the Spanish-language branch quit and created the forever ad-free Enciclopedia Libre Universal en Español. Its founders said that advertising "implied the existence of a commercialization of the selfless work of volunteers." Ads would be "threatening to Wikipedia's neutrality," said Michael Bimmler, a 16-year-old high school student who has been a contributor for more than four years and is president of the foundation's Swiss chapter. Readers would be suspicious about articles if ads were near them, he said, and would wonder why certain articles were longer than others. Besides, he added, ads are ugly. The debate over Wikipedia's future took a tabloid turn last week when gossip sites started buzzing over allegations by former Wikipedian Danny Wool, who recently launched Veripedia, which says it authenticates Wikipedia articles. Wool posted on his blog claims that co-founder Wales had, among other things, been imprudent with Wikipedia funds, asking the foundation to pay for visits to massage parlors and other non-Wikipedia-related activities. As those allegedly scandalous tidbits zoomed around the Internet, the website Antisocialmedia.net (which says it is in the business of "exposing user-generated discontent") got the attention of the blogosphere when it posted a rant about Wales supposedly having fiddled with one Wikipedia article on behalf of a girlfriend before he broke up with her and doctoring another in exchange for a $5,000 donation. Tech industry gossip site Valleywag got involved by posting what appeared to be instant message exchanges between Wales and the ex-girlfriend, political commentator Rachel Mardsen, who put some of his clothes up for sale on EBay. Wales and Wikimedia said he had never misused foundation funds, and Wales posted a statement online saying that he cared deeply about Wikipedia's integrity and would never abuse it. Gardner said in a statement that Wales "has consistently put the foundation's interests ahead of his own." In San Francisco, Gardner said that she wasn't planning wholesale changes as executive director, and that her first task was to "fix the basics and get the house in order." Gardner, a petite woman with black hair and a tattoo of a black widow spider on her wrist, joined Wikipedia nine months ago after leaving Canadian Broadcasting Co., where she oversaw the introduction of advertising on its website. She said she didn't foresee a time when Wikipedia would go that route, though she added that she should never say never. So far, Gardner has hired a staff lawyer, an accountant and a head of business development. She has created a travel policy, reimbursement policy and code of conduct for employees and instituted criminal background checks for potential hires (Wikimedia got unwanted publicity after a technology site revealed in December that the foundation's chief operating officer until July had been convicted of theft, drunk driving and fleeing a car accident before being hired.) Now comes the hard part: money. The foundation makes some -- less than 2% of its budget -- from ways other than flat out asking for it, Gardner said. For instance, it licenses the Wikipedia logo to companies such as Nokia, which used it to advertise a new phone, and it charges websites such as Answers.com for real-time feeds with page updates. "The most difficult issue for a nonprofit is always how to raise money in ways which are consistent with the mission," Gardner said, "and don't distract too much from the mission-related work." In the early days, funding wasn't a problem. Wales helped launched Wikipedia in 2001 with money he made through Bomis Inc., a Web portal known for directing users to pictures of women and celebrities, clothed and unclothed. By February 2004, the English-language Wikipedia had nearly 250,000 alphabetized articles. Today the English version has more than 2 million articles. Global interest in the volume of information -- and the fact that it's free -- helped the site grow from the 100th most visited in 2005 to the ninth most visited now, according to Web-traffic tracker Alexa. Decisions, financial and otherwise, are made by the Wikimedia Foundation board, whose seven directors include Wales, a French plant geneticist, a classical bassoonist studying law in Virginia and an Italian computer programmer. Most board members are nominated and elected, via e-mail debate and balloting, by Wikipedia editors and contributors. As Wikimedia adds features to its pages, such as videos, costs will rise. "Without financial stability and strong planning, the foundation runs the risk of needing to take drastic steps at some point in the next couple years," said Nathan Awrich, a 26-year-old Wikipedia editor from Vermont who supports advertising. Outsiders find it hard to see how the site can avoid selling ad space. "They either have to charge people or run ads, or both," said Greg Sterling, an analyst at Sterling Market Intelligence, which specializes in consumer behavior online. E-mail traffic among Wikipedia contributors shed light on the depth of financing anxiety and the details that cause angst. One worried about the tax implications of the site accepting more than $200 from any individual. Another complained about a proposal to give T-shirts to donors. Wrote one person: "All of this fundraising talk is very nice and dandy, but it sounds like plans for the local glee club, not an international foundation." Foundation Director Erik Moeller said the foundation had to be "very, very careful with the kinds of deals we want to make" to sustain itself. "We don't want to endanger the mission by entering into deals that would conflict with it," said Moeller, a German technology writer who was elected to the foundation board in 2006 and named director last year. Some people have abandoned Wikipedia for Wikipedia-like companies and organizations, including Citizendium and Veripedia, and speak of joining Google's yet-to-be-launched "knol" project. Co-founder Wales started a for-profit that operates a Google-like search engine and allows users to write Wikipedia-like articles. Wales' site, called Wikia, runs ads. Wales said that the free culture movement, as it's called, has to think creatively if it wants to keep spreading information to computers around the world. "There are some real problems with a nonprofit structure," he said. "One of the basic problems is funding: We can get enough money to survive but don't really have the funding to push forward or innovate." http://www.latimes.com/business/la-f...,7404443.story  More Woes for Wikipedia's Jimmy Wales Asher Moses The toughest two weeks of Wikipedia co-founder Jimmy Wales's career just became a whole lot worse, with a former chief scientist at one of the world's biggest technology companies claiming Wales traded Wiki edits for donations. Jeff Merkey, a former computer scientist at Novell, claims Wales told him in 2006 that in exchange for a substantial donation from Merkey, he would edit his uncomplimentary Wikipedia entry to make it more favourable. Merkey made a $US5000 ($5455) donation in 2006 and the edit history for his Wikipedia entry showed that, around the same time, Wales personally made changes to the entry after wiping it out completely and ordering editors to start over. Merkey's claims were published in a statement on a Wikipedia mailing list. On the same mailing list, Wales called the allegation "nonsense". The claim is the most damning yet against Wales, who was last week accused by a former Wikipedia executive of improperly using the non-profit organisation's funds for his own lavish recreation. Earlier, an ex-girlfriend, Rachel Marsden, leaked instant messaging transcripts that purported to show Wales using his influence to improperly make changes to Marsden's Wikipedia entry so he could continue "f---ing [her] brains out". On the Wikipedia mailing list, Wales said he would "never offer, nor accept any offer, whereby a donation would buy someone special editorial treatment in the encyclopedia". When he erased Merkey's Wikipedia entry in May 2006, Wales told Wikipedia users he did so "because of the unpleasantness of it" and asked them to "be extra careful here to be courteous and assume good faith". A Wikipedia user, "Aim Here", quickly questioned Wales's reasoning: "Have you been making secret dealings behind everyone's back? So much for Wikipedia's openness." Following his decision to erase Merkey's entry and start over, Wales placed it under his "special protection". Protected entries can only be edited by Wikipedia administrators. Wales's edits to the page related to various lawsuits Merkey had been embroiled in. Merkey was sued by Novell after his departure from the company for alleged misappropriation of trade secrets. In 2005, he filed a harassment lawsuit against various people and organisations including the geek news website Slashdot. Then in 2006 he filed suit against Natural Selection Foods and Delta Air Lines, claiming his son became ill from eating spinach contaminated with E. coli bacteria. http://www.smh.com.au/news/web/more-...125874243.html  Physics Journal May Reconsider Wikipedia Ban I don't believe in imaginary property The flagship physics journal Physical Review Letters doesn't allow authors to submit material to Wikipedia, or blogs, that is derived from their published work. Recently, the journal withdrew their acceptance of two articles by Jonathan Oppenheim and co-authors because the authors had asked for a rights agreement compatible with Wikipedia and the Quantum Wikipedia. Currently, many scientists "routinely do things which violate the transfer of copyright agreement of the journal." Thirty-eight physicists have written to the journal requesting changes in their copyright policies, saying "It is unreasonable and completely at odds with the practice in the field. Scientists want as broad an audience for their papers as possible." The protest may be having an effect. The editor-in-chief of the APS journals says the society plans to review its copyright policy at a meeting in May. "A group of excellent scientists has asked us to consider revising our copyright, and we take them seriously,” he says. http://science.slashdot.org/science/.../1425247.shtml  Bad Science Journalism and the Myth of the Oppressed Underdog Michael White There is a particular narrative about science that science journalists love to write about, and Americans love to hear. I call it the 'oppressed underdog' narrative, and it would be great except for the fact that it's usually wrong. The narrative goes like this: 1. The famous, brilliant scientist So-and-so hypothesized that X was true. 2. X, forever after, became dogma among scientists, simply by virtue of the brilliance and fame of Dr. So-and-so. 3. This dogmatic assent continues unchallenged until an intrepid, underdog scientist comes forward with a dramatic new theory, completely overturning X, in spite of sustained, hostile opposition by the dogmatic scientific establishment. We love stories like this; in our culture we love the underdog, who sticks to his or her guns, in spite of heavy opposition. In this narrative, we have heroes, villains, and a famous, brilliant scientist proven wrong. I'm sure you could pick out instances in science history where this story is true, but more often it is not. You wouldn't know this from the pages of our major news media though; in fact you'd probably get the impression that the underdog narrative is the way science works. And many journalists may think that too; after all, most of them read (or misread) Thomas Kuhn when they were in college, and Kuhn brought this kind of narrative to a new high. The impression this narrative leaves is that science only progresses by the efforts of brave individuals who are willing to wither the wrath of the scientific establishment. Why is this narrative about science wrong? Let me illustrate with the nearest example I have at hand right now: a piece out of the 2007 Best American Science and Nature Writing:"The Effeminate Sheep", by Jonah Lehrer, a piece that was originally published in Seed magazine. The piece is about Joan Roughgarden, a writer here at Scientific Blogging, an accomplished Stanford Biologist, and the transgendered author of the book, Evolution's Rainbow, about the sexual diversity that we find in nature. As we learn in her book, gay sex is quite popular in the animal world - bonobos, fish, giraffes, whales, and big-horn sheep make humans look incredibly prude. This raises a question: being gay has obvious evolutionary fitness consequences - without modern medicine, you have to have heterosexual sex to have offspring. So is homosexuality in nature just a freak occurrence, a case of bad genes; or is it something that is in some way adaptive and therefore under selective pressure? Does this mean that there are problems with our current understanding of sexual selection in evolutionary theory? (Important aside: let's make it clear right now that my intention is not to knock Dr. Roughgarden or her research, or her book - I'm talking here about how science is presented to the public. In fact I feel a little school pride in Roughgarden's accomplishments - she and I both spent some of our educational careers at the University of Rochester, though obviously not at the same time.) Getting back to our underdog narrative, take a look at how Lehrer sets up the story. After giving a very brief introduction to Darwin's ideas about sexual selection, using the classic example of peacock tails, he writes: "Darwin's theory of sex has been biological dogma ever since he postulated why peacocks flirt. His gendered view of life has become a centerpiece of evolution, one of his great scientific legacies." There you have the classic start of the narrative: Darwin, our brilliant scientist, came up with a theory about evolutionary sexual selection, which has been dogma among biologists ever since. But this story isn't true: Darwin's theories about selection took some time before they were widely accepted (in fact, Darwin's claim that all living species share a common ancestry was accepted before his ideas about selection). And even then, they weren't taken as dogma; researchers have been actively studying the subject for a long time. The theory of sexual selection has undergone heavy scrutiny and extensive modification, including an effort to put it within the mathematical framework of game theory - a development which didn't take place until 100 years after Darwin proposed sexual selection. Biological dogma ever since Darwin? Hardly! (Take a look at this book on the development and status of theories of sexual selection.) But Lehrer doesn't bother to tell his readers any of this; it would spoil the underdog narrative. It's time to introduce the underdog scientist ready to overturn it all: "Despite this new evidence [of gay sex among animals], sexual selection theory is still stuck in the nineteenth century. The Victorian peacock remains the standard-bearer. But as far as Roughgarden is concerned, that's bad science: 'The time has come to declare that sexual theory is indeed false and stop shoehorning one exception after another into a sexual selection framework ... To do otherwise suggests that sexual selection theory is unfalsifiable, not subject to refutation.'" Roughgarden is the underdog against the scientific establishment - an establishment stuck in the nineteenth century, so willing to protect its pet theory that it will go so far as to make it unfalsifiable. What is this revolutionary idea that the establishment is hostile towards? Roughgarden believes that homosexual behavior is an adaptive trait, one preserved by natural selection to play an important role in group cohesion, or as Lehrer puts it, "gayness is a necessary side effect of getting along." To support this, Roughgarden marshals examples of unorthodox sexual arrangements in many different species, and explains that these arrangements actually promote evolutionary fitness in complex animal societies. She has presented this evidence in a popular book, Evolution's Rainbow, and in a review article in the journal Science (subscription required). Her ideas are unquestionably bold. She and her co-authors set themselves an ambitious task to replace the current theory of sexual selection: "We think that the notion of females choosing the genetically best males is mistaken. Studies repeatedly show that females exert choice to increase number, not genetic quality, of offspring and not to express an arbitrary feminine aesthetic. Instead, we suggest that animals cooperate to rear the largest number of offspring possible, because offspring are investments held in common. We therefore propose replacing sexual selection theory with an approach to explaining reproductive social behavior that has its basis in cooperative game theory." They go on to present their new mathematical formalism for their ideas. This is how science is supposed to work, incidentally. Roughgarden wrote a popular book, but didn't expect that to be a substitute for genuine scientific papers. She knows she has to convince her scientific peers, and to do that, she wrote a technical paper, spelling out the mathematical basis for her novel ideas. The next step is for the people who understand those mathematical details to check them out, work them over, and see how persuasive they are. But that's not how the underdog narrative goes. According to Lehrer, by this point it should have been an open-and-shut case, if it weren't for the hostile scientific establishment: "Despite Roughgarden's long list of peer-reviewed articles in prestigious journals, most evolutionary biologists remain skeptical of her conclusions... In the absence of something conclusive, most scientists stick with Darwin and Dawkins." In the underdog narrative, it is wrong for the establishment to remain skeptical, which in reality is exactly the opposite of how science is supposed to work. It is not like a courtroom where innocence is the presumption; in science, a novel idea is unfounded until proven otherwise. And Roughgarden's publication record, impressive as it is, is not evidence that her hypothesis is correct. Nor is the fact that her review article was published in Science evidence that her idea is true. It does mean though that she's put something together serious enough to deserve a hearing. (One more nitpicking point - "scientists are sticking with Dawkins"? Dawkins may be the authority on the subject to someone like Lehrer who has probably read only popular books on evolution. Dawkins has done some professional work in this field, but he's not the reigning authority.) Our underdog narrative is almost complete: we have a reigning scientific authority, Darwin, whose ideas are entrenched dogma among an establishment that is skeptical of our underdog scientist, whose ideas are so obviously true that they would have been accepted if it weren't for the closed-mindedness of the defenders of orthodoxy. And closed-minded they are: Lehrer, instead of summarizing the real critiques that Roughgarden's paper generated (those with access to Science can read them here and here), suggests that biologists are unwilling to abandon their dogma of sexual selection and view homosexuality as anything but "sexual deviants" and "statistical outliers." That's not exactly what Roughgarden's critics are saying. The responses to her Science review included two major criticisms: that Roughgarden did not correctly characterize sexual selection as it is currently understood, and that some of her assumptions in her game theory model were wrong. Most writers did think that she had offered something interesting, although not something which completely negates the theory of sexual selection; several writers suggested that current theories could be modified to incorporate Roughgarden's ideas. Lehrer does quote one scientist who basically says just that. He quotes PZ Myers, a University of Minnesota biologist: "I think much of what Roughgarden says is very interesting. But I think she discounts many of the modifications that have been made to sexual selection since Darwin originally proposed it. So in that sense, her Darwin is a straw man. You don't have to dismiss the modern version of sexual selection in order to explain sexual selection of homosexuality." Our narrative would not be complete without a final look at our persevering underdog: "Roughgarden remains defiant," Lehrer writes. And we learn the real source of the establishment's skepticism. "I think many scientists discount me because of who I am," the transgendered Roughgarden says. "The theory is becoming Ptolemaic. It clearly has the trajectory of a hypothesis in trouble." We are left with the impression of scientists hanging on to a sinking theoretical ship, unable to move forward in their understanding because they have something personally against the underdog of the narrative. It's amazing science makes any advances at all, with such closed-minded people in control of the field! But that's not really how things work. The real story is an example of science operating the way it is supposed operate: a researcher comes up with new and very interesting observations that seem to challenge our current understanding of an important problem. She works to put those observations under some sort of theoretical framework, and presents the results in a paper to her scientific peers. Her fellow scientists think the work is interesting, but remain unconvinced because the evidence or theoretical development is not yet sufficient to support the hypothesis. What should happen next is that our researcher should go out and collect more evidence, correct any mistakes in the analysis or make a persuasive reply to her critics, and try again. A major new idea, one which overturns an existing, well-supported theory, does not get established in one paper. There has to be follow up and debate, and if the idea holds up to scrutiny it will be accepted. Beware the underdog narrative in science journalism. This narrative severely misrepresents how science really works. It's designed to elicit our sympathy for a not-yet-established theory, maybe one that is socially attractive, and to arouse our indignation against the staid community of eggheaded scientists. This underdog narrative plays on our emotions, it makes for a good read, and helps us feel good about ourselves when we stand up for our convictions. What gets lost is the scientific method, the idea that novel proposals need to be thoroughly vetted and tested, no matter how intuitively attractive they are. That vetting process is done by a dynamic community of smart, educated, competitive people, who care passionately about science. It's a community where everyone wants to come up with the next big theory that overturns long-held beliefs. But that's hard to do, especially in fields where all the low-hanging fruit has been picked over by really talented people for decades or centuries. If a new theory is being presented in the media as the centerpiece of an underdog narrative, you can bet the farm that this theory is not yet sufficiently substantiated by the evidence. That doesn't mean it's wrong necessarily, but it does mean that the hypothesis has not yet met the rigorous standards of evidence that have served science well for centuries. I said I wasn't writing this to knock Dr. Roughgarden, but I'm going to renege on that promise just a little: based on how she's quoted in the piece, she does seem to be feeding the narrative. She's not giving her colleagues enough credit for giving her ideas a hearing. What non-heterosexual behavior among vertebrates implies about evolution is a fascinating question, one many of biologists would be happy to know more about. I think the idea that homosexual behavior could be adaptive is intriguing, and its widespread occurrence in nature is a worthwhile scientific subject. But it's an issue that's only going to be settled by more evidence. http://www.scientificblogging.com/ad...sed_underdo g  Dropping 22TB of Patches on 6,500 PCs in 4 Hours: BitTorrent Iljitsch van Beijnum Get out your list, because you can add another application to the tally of legitimate uses of BitTorrent. Apparently, software updates are getting so big these days that simply downloading them from a server is becoming prohibitively time consuming, especially when the same updates need to be applied to many different machines. A Dutch university has some 6,500 desktop PCs in ten locations, which on occasion need to download 3.5GB worth of different types of updates. That's a handsome 22.2TB in total. In a traditional client-server world, that's some modest lifting. In fact, INHOLLAND University's IT department used to have almost two dozen servers distributed over the university's locations to serve up these downloads. The school was able to retire 20 of them after adopting a new way to distribute updates: BitTorrent. The peer-to-peer protocol allows PCs to download most of the updates from each other—the remaining servers are mostly needed to send out the first few copies and then coordinate the up- and downloading. One of the advantages of the BitTorrent protocol is that it uses bandwidth where it can find it: faster links are automatically used more. Using this technology, updating all 6,500 PCs can be done in less than four hours. Previously, this took four days. Four days down to four hours for the same needs! Leo Blom of ITeleo, who came up with the idea of using BitTorrent, told Ars, "Let me put it this way: if INHOLLAND wants to migrate to Windows Vista, they only have to send out an image through BT. All 6,500 desktops can be migrated overnight in two hours' time—with one push of a button. It's a real migration killer. Migration used to mean a lengthy and trying process. At INHOLLAND, we took a different approach." According to TorrentFreak, the university's management team was reluctant to adopt the peer-to-peer technology, but they quickly changed their minds after seeing a demonstration. Students and staff who think they can use the modified BitTorrent client for other purposes will be disappointed to learn that the system is completely locked down. http://arstechnica.com/news.ars/post...ittorrent.html  The Shareaza Conspiracy In a Nutshell enigmax The hijacking of Shareaza.com is a complex story with many twists and turns. Here is the story of Shareaza from its open source GPL roots, to the hostile takeover and where the project is today, directly from those at the heart of the news - the real Shareaza community. The fight for Shareaza has only just begun. Beginnings Are a Good Place To Start In mid 2002, a lone programmer by the name of Micheal Stokes released the first version of a Gnutella client he had written, dubbed “Shareaza”. Over the next two years Micheal added to his client and coded in support for the eDonkey 2000 network, BitTorrent and a rewritten Gnutella-based protocol which he named Gnutella2. Shareaza gradually became more and more popular and Mike started to receive several job offers based on the strength of his work on Shareaza. He eventually decided that continuing to work on a p2p application in an increasingly hostile legal climate was too risky, but he did the honorable thing and released the Shareaza source code under the GNU GPLv2 on June 1, 2004 (which coincided with the release of Shareaza V 2.0). Mike stopped working on Shareaza and went on to develop a new p2p-based streaming radio project named Mercora. As part of distancing himself from Shareaza, he transfered the shareaza.com domain to one of his old alpha testers named Jon Nilson, who continued to administer the domain until late 2007. The French (RIAA) Connection In late 2007 the Shareaza website went down for several weeks, but eventually came back online. Not long after that, the Shareaza.com domain began pointing to a different website which several sharp-eyed community members recognized as identical to shareazaweb.com, a known scam site purporting to offer users “legal p2p downloads”. It emerged that Jon Nilson had been forced to relinquish control of the domain as part of a settlement with La Societe Des Producteurs De Phonogrammes En France (the French version of the RIAA). Jon’s name was the only one connected with Shareaza that the SPPF could find and due to Shareaza’s popularity in France he had been named in a lawsuit along with Azureus and Morpheus. See here for more. A Dump for Ill-Gotten Gains Members of the Shareaza community managed to track the new “owners” of the Shareaza.com domain to MusicLab LLC, based in New York. MusicLab now distribute the “new and legal” iMesh p2p client after the original Gnutella-based iMesh developers were sued by the RIAA, and forced to settle for $4.1 million with a promise to turn their app into a paid download service. A similar legal fate befell another popular Gnutella application called Bearshare which was then rolled into the RIAA-approved iMesh. Nobody has managed to ascertain whether the original iMesh developers are still involved, but the merging of Bearshare seems to indicate that MusicLab is a vehicle used by the recording industry to dump assets acquired through lawsuits into. It would seem that since Shareaza is developed by anonymous group of individuals and organized via “ad-hocracy”, there was no company to sue, so stealth tactics were employed against the weakest link in the chain: Jon Nilson. iMesh, Bearshare and the fake Shareaza being distributed from Shareaza.com are all the same application with appropriate re-branding. Threats of C&D As you can imagine, the members of the Shareaza community were rather upset about all of this and set up a new website with user forums. After two users made some offhand remarks about a distributed denial of service attack against the servers in Israel where the hijacked Shareaza.com site is located, our forum administrator received an email from one Jeffrey A. Kimmel of Meister Seelig & Fein, in his capacity as a representative of Discordia Ltd, the new new “owners” of Shareaza. Mr Kimmel stated that DDoS attacks are illegal and any further talk by “users [who] begin to promote the destruction of a legitimate business” would result in Discordia Ltd “tak[ing] all necessary action to vigorously and relentlessly protect its rights.” He went on to state that “if this action is not immediately taken and, as result, our client’s business is harmed, we will not only pursue, locate and hold fully responsible each and every one of those who have implemented this, or any similar DoS, but also those responsible for maintaining your site and the forums.” The posts in question had actually been taken down by forum moderators already (as per forum rules on objectionable content), however this email was cause for great concern: not only were the domain hijackers starting to create a series of shell companies to avoid being identified, but they had engaged lawyers to monitor our forums and threaten anyone making disparaging statements about them. A Tangled Web More research by community members revealed that Discordia Ltd is registered in Cyprus, possibly owned by MusicLab but at arm’s length to avoid as much fallout as possible. Meister Seelig & Fein’s Kimmel also appears to have a long history of dealings with the recording industry, notably in the participation of the iMesh and Bearshare lawsuits and an interesting Amicus Curiae brief in the MGM vs Grokster which details how the new iMesh software has all the answers to stopping piracy and creating a wonderful legal download service. Making The Takeover Official In what is possibly the most audacious step so far, Discordia Ltd filed for a trademark on “Shareaza” with the USPTO on January 10, 2008. If granted, our use of the Shareaza name will immediately infringe upon Discordia Ltd’s official trademark and we will doubtless be subject to legal action until we stop any infringing action i.e. we rename the project, remove all references to “Shareaza” and forget about the whole thing. The Danger Posed To Open Source Software Unless we are able to prevent the trademark being granted and regain control of the domain, our project will die. It really is as simple as that. Seven-odd years worth of brand recognition as “Open Source, Spyware, Malware and Advertising Free” will disappear and although we can (and have) dealt with “clones” who take our OS code base, add some spyware and release a “new” client as their own (breaking the GPLv2 in the process by not releasing the source) there is no possible way that we can survive having our identity stolen like this. Unlike a run-of-the-mill copyright violation, we are going to be permanently deprived of something. Our code is open to whoever wants to see it, we charge no money for the use of the program; the only thing of value that we have is the name and recognition that goes with it. The worst of it all is that this “software identity theft” could signal the beginning of hostile corporate takeovers of common property - the fact that we are in this predicament proves it to some extent. What we need to know is if the people who stood up for an open culture by hacking copyright law will help protect that culture where it comes to trademarks and halting the advancement of encroaching corporate interests. If “common law” trademarks can’t be protected there is a very real danger that what happened to us will happen again and again and again. Many of us who work on the Shareaza project can foresee things becoming so that people will stop bothering to work on OS projects: open source software is, by it’s nature, more useful that closed source software and the more useful something is, the more popular it becomes…and then someone with expensive lawyers will come along and take it all away from the people who actually created it. We recently asked for donations from our users for a legal defense fund and (very) quickly raised $2000. In our public thank you letter we wrote the following: “There is one fundamental right that should never be in dispute: the right to be recognized as a creator. This moral right transcends arguments on whether copyright should last for 50 years or a hundred, whether software should be patentable or not, or even what a fair price price for an MP3 file is. Being able to say to the world “I made this” and be acknowledged for it is, for many people, the only reward they receive for their work. To deny that right is an insult to the creative forces flowing through every writer, performer, musician, actor and programmer who brings their work to the world.” We have a section dedicated to this whole situation on our new forums which includes full details of all the events that have taken place so far. Any help you are able to provide would be very, very gratefully accepted. Any advice, introductions or referrals to others who may be able to help us will be a great help. Kind regards, Shareaza Community http://torrentfreak.com/the-shareaza...tshell-080313/  Lisa Marie Presley Sues Over 'Fat' Story Tariq Panja Lisa Marie Presley has sued a British newspaper for alleging that she was piling on the pounds because of her unhealthy appetite, her lawyer said Monday. Presley, who is pregnant, alleges in a suit filed at London's High Court on Friday that the story in Britain's Daily Mail was slanderous and degrading. The newspaper has since reported on the 40-year-old singer's pregnancy. "Once they got a glimpse of my expanding physique a few days ago, they have been like a pack of coyotes circling their prey whilst eerily howling with delight," she said on her blog. The daughter of the late singer Elvis Presley claims the pictures taken at a Hollywood restaurant last week forced her to go public about the baby she is having with her fourth husband, music producer Michael Lockwood. "It really upset her," Presley's attorney Jo Paton told The Associated Press. "She was about to announce her pregnancy and was shocked and hurt by the unkind article about her appearance." Paton said Presley was seeking an apology and damages. The Daily Mail said the first indication they had of Presley's complaint was when they were served with court documents. "We are investigating the matter," the newspaper said in a statement. The child will be Presley's third. She has an 18-year-old daughter and 15-year-old son from her first marriage to musician Danny Keough, which ended in 1994. She was briefly married to Michael Jackson and to actor Nicholas Cage. She married Lockwood in January 2006. http://ap.google.com/article/ALeqM5i...RVZvAD8VAMSTG0  A Glossy Rehab for Tattered Careers Ruth La Ferla  LINDSAY LOHAN wants you to know that she’s all right. Reminiscing about the series of scandals that have sullied her name and nearly deep-sixed her career, she is all contrition. “When I look back on this last year, it’s like what was I thinking?” she confided in the March issue of Harper’s Bazaar. “I’ve learned so much, though, like learning to live my life a different way.” No need to take her word for it. Images speak persuasively, and in the case of Ms. Lohan, who appears this month inside Bazaar and on its cover, they do what they can to counter the perception that she is a train wreck, yesterday’s news. The cover, shot by Peter Lindbergh soon after Ms. Lohan’s third round in rehab for alcohol abuse, makes her look as if she had spent the last 12 months thriving on yoga and a diet of sprouts. It is the most sophisticated of a trifecta of March magazine covers to feature the troubled star — including a near-nude shot by Bert Stern for New York magazine’s spring fashion issue and a provocative pose for Paper, the alternative style monthly. Together the covers represent a full-court press by Ms. Lohan and her handlers to reposition her as fresh-faced and comeback-ready. She is the latest Hollywood celebrity to seek to overcome scandal through the redemptive power of glossy fashion imagery. Last June, six months after her arrest for drunken driving, Nicole Richie modeled on the cover of Bazaar with Paris Hilton. In September, not long after Britney Spears’s first go at rehab and her divorce from Kevin Federline, she vamped for Allure, the beauty magazine. Drew Barrymore, Vogue’s current cover girl, first graced the magazine’s front in 2005 when many readers still recalled her years of drug abuse. “A cover on Vogue or Bazaar, I think of it as the new celebrity rehab,” said Liz Rosenberg, the publicist for Madonna. “Some people go to Utah,” she said, a reference to the Cirque Lodge detox program, where Ms. Lohan was treated. “Others go to Smashbox and do a photo shoot.” The audience for such makeovers is not just the ticket-buying public. The glamorous covers are also aimed at movie directors and executives — a very high-end head shot. “A person in a position to greenlight a movie project might say, ‘Oh, I guess she’s turning her life around,’ ” Ms. Rosenberg said. That is Ms. Lohan’s hope, her publicist, Leslie Sloane Zelnik, acknowledged last week. “Her appearance on Bazaar is part of a strategic repositioning,” she said. It is an attempt to recast the actress as the pulled-together antithesis of the bad girl who was scolded in 2006 by a producer for failing to show up on the set of “Georgia Rule.” “Right now I just want to find a great script, a great role,” Ms. Lohan said in the March issue of Paper. She is shooting “Dare to Love Me,” a movie about a tango star, but has not completed a movie since starring last summer in the horror film “I Know Who Killed Me,” which flopped. “Fashion can put a calm, fresh and vital face on a recovering soul,” said Sally Singer, the fashion features director for Vogue. “Some people can appear on a cover and suddenly seem relevant again.” Ms. Lohan, 21, looks mature and confident on the cover of Bazaar. Such a laboriously constructed image, thanks to makeup artists and digital retouchers, is meant to serve as a corrective to the awkward, sometimes ugly celebrity candids in tabloid weeklies. “As a publicist, I would be high-fiving myself for getting Lindsay Lohan on the cover of Harper’s Bazaar,” said Chris Miller, Ms. Barrymore’s manager and publicist. “It tends to smooth out that edge and negate when she’s on the cover of Life & Style.” He added that it can eventually translate not just to film roles but to advertising contracts. Ms. Barrymore, who wrote directly to Anna Wintour, the Vogue editor, to campaign for a cover in 2005, according to Mr. Miller, is the current face of Gucci fine jewelry and the latest face of CoverGirl cosmetics. “That first cover was a power tool in putting her out there,” Mr. Miller said. More than a talk show appearance or a stroll along the red carpet, a magazine photo shoot, with its army of enablers to select the right clothing and makeup, casts a performer in the best light. “It’s a safe atmosphere where the star has some control of her image, her words and the fashion that she is putting out there,” Ms. Sloane Zelnik said. Winona Ryder must have thought so. Last August, five years after a humiliating trial and conviction for shoplifting, she was persuaded by Vogue’s editors to pose for the cover. It was Ms. Singer’s job to reassure her. “Before the shoot I told her, You can show your face to the world in the context of clothes in which you look beautiful,” she recalled. If an actress is hoping to dust herself off after a fall, she added, “this is a good way to do it.” Of course it also pays returns for the magazines, as scandal-craving readers snap up the issues, which often promise a star’s first on-the-record account of her troubles. And if the interview is anodyne — or even nonexistent — there are always the pictures. Ms. Lohan’s Marilyn Monroe-inspired striptease for New York was the magazine’s biggest selling issue of the past four years, a company spokeswoman said. The kid-glove treatment from fashion magazines has long made them popular with public figures who have suffered a reversal, especially when they are seen as women scorned. For them, “the best revenge is looking good,” Ms. Singer said. In 1990, Vogue put Ivana Trump on its cover weeks after her highly publicized split with Donald Trump, who had left her for a model. The magazine photographed Hillary Clinton in 1998, in the aftermath of her husband’s dalliance with Monica Lewinsky. Jennifer Aniston scored her Vogue cover in April 2006, just after separating from Brad Pitt. Alas, readers’ approval is not an assurance of a career comeback. Ms. Ryder has not been in a hit movie since her conviction, despite the Vogue cover. In Hollywood there is a feeling that a fallen star needs more than a magazine cover to redeem herself. Fashion, and the reader, can be forgiving. Movie executives? Not necessarily. A star like Ms. Lohan, certainly, can hope to rehabilitate her image through fashion, said Robert Green, an executive producer of “Mad Money.” “But until she gets in a movie and it makes a lot of money, no one in the industry is going to care.” Mr. Green had considered casting Ms. Lohan in “Mad Money.” But the idea, he recalled last week, “was made moot by the fact that at the time she was not insurable.” Her off-camera behavior was seen to be so irresponsible that the underwriters of film production budgets would not issue a policy. “I told myself, O.K., let’s call Katie Holmes,” Mr. Green said. “She may have a weird personal life, but nobody thinks she’s not going to show up on time.” Mr. Green is skeptical that a fashion makeover, however slick, holds much sway with industry power brokers. “I don’t think a Lindsay Lohan can overcome the things she’s done in her personal life by being on the cover of a fashion magazine,” he said. Some of his peers are more generous, however. “An image on the cover of a fashion magazine could make you rethink somebody,” said Janet Hirshenson, a casting agent whose film credits include the coming “Angels and Demons.” “People are not morons,” said Alison Owen, the producer of the current release “The Other Boleyn Girl.” “They know that with fashion, a lot of retouching goes on. Still, if you see someone in a magazine looking perkier, healthier and less skinny than they have for some time, consciously or subconsciously it makes you think, ‘Oh, this person is back in the ring; they want to be considered.’ “That undoubtedly is going to have an effect on you.” http://www.nytimes.com/2008/03/09/fa...magazines.html  Magazines to Spitzer Call Girl: Call Us Clare Trapasso The woman at the center of the Eliot Spitzer call girl scandal will have no problem cashing in on her notoriety: Penthouse and Hustler are already knocking on her door. ''We've been looking at that very closely. She's young. She's pretty. She's a model,'' said Hustler magazine publisher Larry Flynt. ''We would love to do business with her, and we will approach her.'' Penthouse has been trying to reach out to 22-year-old Ashley Alexandra Dupre, too, but had yet to make contact Thursday afternoon. Penthouse Magazine Group president and publisher Diane Silberstein said she would ''love to have her in the magazine'' and would consider offering her a cover shot. ''She sounds like a very interesting and talented young woman, and I'm sure she has a great story to tell,'' Silberstein said. ''We promise to make it worth her while.'' The New Jersey-born Dupre was thrust into the limelight Wednesday when The New York Times identified her as the high-priced call girl whose arrangements for a rendezvous with New York's governor at a Washington, D.C., hotel were secretly monitored by the FBI. So far, authorities haven't filed charges against Spitzer or Dupre, who was identified in court papers only by her escort agency pseudonym, Kristen. But she has a lawyer and hasn't been speaking about her encounter with the governor while the case is under investigation. Flynt, who last June took out a full-page advertisement in The Washington Post offering $1 million for anyone who could prove he or she had illicit sexual relations with a prominent politician, suggested that by the time Dupre starts talking she may be too big a media phenomenon for a simple magazine spread. ''She is no doubt going to do a book. There will probably be a movie,'' he said. ''I think she is going to have so many offers coming in that it will probably be wishful thinking just to get in the door.'' http://ap.google.com/article/ALeqM5h...QsqLQD8VCRQV80  Music Reps Seeing Green Over Spitzer Call Girl's Songs David Segal Hooking for the Emperors Club and emerging as the Earth's best-known call girl is surely not the career plan Ashley Alexandra Dupre had in mind when she moved to New York to make it as a singer. But now that she's achieved fame at the media stakeout level, as "Kristen," a bunch of music biz talent scouts and managers are giving her a listen. Hello, silver lining! No, a record deal isn't a sure thing. But look at it this way: She had no chance on Tuesday, before anyone knew her name, and she has a slender chance now that more than 2.3 million people have visited www.myspace.com/ninavenetta and heard her songs. "People want to see if there's an opportunity there," says Ted Cohen, a former talent scout for Warner Bros. and now managing partner at TAG Strategic, which advises startup music companies on all aspects of digital media. "Is what she's posted a hit? No. But if someone like Jay-Z or Danger Mouse or Jimmy Iovine wanted to give her a shot, she'll have a shot." As any aspiring singer will tell you, the hard part of breaking out is getting noticed, and let's just say Ms. Dupre has that covered. Thursday, a scrum of reporters hunkered down at the apartment building in the Flatiron District where she lives, waiting for just a glimpse of the woman who brought down Gov. Eliot Spitzer. And as news of her life's ambitions spread over the Internet ("I am all about my music," she proclaims on her page, "and my music is all about me") the songs she'd posted online were suddenly getting what they apparently never had before: an audition with some of the more powerful figures in the music biz. "I read that she's a singer, and so I checked out her stuff on Wednesday evening," says Chad Jensen, an artist manager. Jensen has found platinum online before. He first heard his greatest find — Colbie Caillat, whose debut album, "Coco," has sold more than 1 million copies since July — on a Myspace page. What he heard from Dupre, however, didn't have nearly the same impact. "It didn't blow me away," he says. "Part of it is that I could barely hear her voice. But here's the thing — if she has even an ounce of talent, someone is going to take a chance. I mean, they gave ("American Idol" reject) William Hung a shot. And I know for a fact that Tila Tequila" — the much page-viewed Myspace phenom turned reality TV star — "has been in the offices of every major label." It was the same refrain, time and again, Thursday from the music industry pros. None swooned for Dupre's music, all of it club R&B in the dance-vixen vein of JLo and Beyonce. (Sample lyric, "I know what you want / You got what I want / I know what you need / Can you handle me?") A couple said the tunes are pretty uninspired, a tad derivative. But with the right song and the right producer, these people say, you never know. "If Paris Hilton can make a hit song, anyone can," says Erik Parker, director of content at the hip-hop Web site SOHH.com. "Paris Hilton, she swung the doors wide open." Actually the doors were open before Hilton. "Look, Traci Lords had a music career after she'd acted in pornographic movies as a minor," says Cohen. "People are very forgiving, and she's going to emerge as the victim in all this." Whether any producers or managers have made any offers, we don't know. So far, the only opportunity offered publicly to Dupre has come from Penthouse, whose publisher, Diane Silberstein, said she'd "love to have her in the magazine," perhaps even on the cover. To which we say: Perhaps? If the past is any guide, Dupre is about to hear about plenty of business ventures that she'll want no part of. That's the guess of another woman who was caught in the middle of another national sex scandal — one who had a modest singing career before achieving infamy. "It's very scary," says Gennifer Flowers, who spoke from Las Vegas, where she'd recently ended a run in a musical comedy. Flowers recounted the fallout from revelations of her affair with then-governor Bill Clinton. She'd been a local-to-Arkansas nightclub singer until her name went household during the 1992 presidential campaign. After that, the professional offers she got were "a lot of stuff like, have sex with a Bill Clinton lookalike. Or pose naked with a Bill Clinton lookalike." The publicity put a serious kibosh on Flowers' career prospects for years, she says, because no club owner wanted to hire a singer who'd be accompanied by a pack of reporters. "What is fame without dignity?" she says. We'll see! Music publicist Diana Baron suggested that Dupre's best shot is to end up in some glossy lad magazines, then segue from that platform to a music contract. Switching into "American Idol" voice critique mode, Baron adds that Dupre needs to convey more confidence when she sings. Some "clear intent and feeling of who she is" would be a good idea, too. Eh, details. To judge from the feedback she's getting online, Dupre already has some ardent fans. "I wouldn't have known about this artist without her recent play in the political press," wrote one. "Oddly, I think she's going to take off in clubs!" Another gave a very strong, perhaps totally sarcastic, thumbs up. "Best song of the century BAR NONE!" "Good beat," quipped another poster, "love the scandal behind it." http://www.chron.com/disp/story.mpl/nation/5618119.html |
|
|
|

|
|
|
#2 | ||
|
Join Date: May 2001
Location: New England
Posts: 10,016
|
Governor Signs Textthreat Measure
Joe Kafka A state law to be enacted July 1 will make ominous or annoying text messages illegal in South Dakota. The statute will revise an existing law on threats and harassment to include not only traditional telephones but also cell and satellite phones, and computers hooked to the Internet by cable TV. The law will make it a crime to use electronic devices to: Terrorize, intimidate, threaten, harass or annoy with lewd language. Threaten physical injury or property damage. Attempt to extort money or valuables. Disturb repeatedly by anonymously contacting people. Violations could bring up to one year in jail and $2,000 fines. http://www.kxmb.com/News/218636.asp  Another Lawmaker Wants to Make Anonymous Internet Posting Illegal Kentucky Representative Tim Couch filed a bill this week to make anonymous posting online illegal. The bill would require anyone who contributes to a website to register their real name, address and e-mail address with that site. Their full name would be used anytime a comment is posted. If the bill becomes law, the website operator would have to pay if someone was allowed to post anonymously on their site. The fine would be five-hundred dollars for a first offense and one-thousand dollars for each offense after that. Representative Couch says he filed the bill in hopes of cutting down on online bullying. He says that has especially been a problem in his Eastern Kentucky district. Action News 36 asked people what they thought about the bill. Some said they felt it was a violation of First Amendment rights. Others say it is a good tool toward eliminating online harassment. Represntative Couch says enforcing this bill if it became law would be a challenge. http://www.wtvq.com/content/midatlan...3-05-0011.html  Syria Expands "Iron Censorship" Over Internet Khaled Yacoub Oweis Syrian authorities have ordered Internet cafe users to reveal their identity, the latest measure in their "iron censorship" of cyberspace, a Syrian monitoring group said on Thursday. Security officials ordered Internet cafe owners this week to take down the names and identification cards of their clients as well as the times they come and leave, Mazen Darwich, head of the Syrian Media Centre, told Reuters. The records are to be presented regularly to the authorities, who targeted bloggers and Internet writers in recent months as part of a renewed campaign against dissent. "These steps are designed to terrorise Internet users and spread fear and self censorship in violation of the right to privacy and free expression," Darwich said. "The government has been methodical in extending the scope of its iron censorship," he said. There was no comment from the government. Officials had said Internet controls were needed to guard against what they described as attempts to spread sectarian divisions and "penetration by Israel". Several Internet cafes confirmed the new regulations. Restrictions have also increased on surfing the World Wide Web and online publishing. An increasing number of Syrians who have voiced opinions on the Internet were being jailed, Darwich said. The Syrian Media Centre, an independent body that tracks curbs on media, said at least 153 Internet sites are blocked in Syria with bans expanding over the past few weeks to Googleblog and the Arab Maktoobblog. "Open forums have been used by thousands of Syrians to launch a counteroffensive against the government's curbs on public expression," Darwich said. The forums also provide a way for users to share information on how to bypass government blocking of sites through what is known as Internet proxies, he said. Facebook and YouTube are already banned as well as sites for Syrian opposition parties, Lebanese newspapers and Lebanese groups opposed to what they call Syrian interference in Lebanon. The site of the Saudi Asharq al-Awsat newspaper is blocked although the daily has a correspondent in Damascus. The government last year ordered Internet sites based in Syria to provide the "clear identity and name" of those behind any article or comment they publish. A poet is facing trial at a state security course for publishing articles on a civic society forum. Another writer spent a week in prison for an Internet piece about fuel and electricity shortages, Syrian human rights organisations said. A teacher from the farming province of Reka is facing trial for criticising online what he described as patronage and nepotism in the state-run education system. The Internet spread in Syria after President Bashar al-Assad succeeded his late farther, Hafez al-Assad in 2000. The country is ruled by the Baath Party, which took power in a coup in 1963, imposed emergency law and banned all opposition. (Editing by Dominic Evans) http://www.reuters.com/article/inter...38353620080313  Malaysia Opposition Win Shows Power of Cyberspace Bill Tarrant Malaysia's weak opposition was up against a hostile mainstream media and restrictive campaign rules, but it can chalk up much of its stunning success in Saturday's election to the power of cyberspace. Voters exasperated with the unvarnished support of the mainstream media for the ruling National Front furiously clicked on YouTube and posted comments with popular bloggers about tales of sex, lies and videotapes in the run-up to Saturday's election. Jeff Ooi, a 52-year-old former advertising copywriter who made his name writing a political blog, "Screenshots" (www.jeffooi.com) won a seat in northern Penang state for the opposition Democratic Action Party (DAP). Elizabeth Wong, a human rights activist and political consultant who runs a blog (http://elizabethwong.wordpress.com), won a state assembly seat in the central state of Selangor. YouTube, the phenomenally popular video Web site, did as much damage as any opposition figure could hope to inflict, after netizens uploaded embarrassing videos of their politicians in action on hot-button issues. One YouTube video in January showed ruling party MP Badruddin bin Amiruldin causing a ruckus in parliament over whether Malaysia was an Islamic state. "Malaysia is an Islamic state", he declared. "You don't like it, you get out of Malaysia!" Muslim Malays form the majority in multi-racial Malaysia, but ethnic Chinese and Indians account for a third of the population and they deserted the ruling National Front in droves, partly in outrage over the religious debate. Sex, Sleaze, Corruption Another YouTube video that got wide distribution shows a rambling and incoherent Information Minister Zainuddin Maidin, in a live interview with al-Jazeera, excitedly defending a police crackdown against peaceful protesters calling for changes to the electoral process in November. Zainuddin was one of several "big guns" in the National Front that fell to the opposition's onslaught. Sex, sleaze and corruption were election issues and they all had video soap operas on Web sites. Malaysia's health minister resigned in January after admitting he and a female friend were the couple in a secretly filmed sex video uploaded on YouTube. That cost some votes. "We were concerned about the morality of our leaders," said Maisarah Zainal, a 26-year-old teacher in Kuala Lumpur. "It didn't help that Chua Soi Lek was involved in a sex video." Loh Gwo Burne, who secretly videotaped a phone conversation, allegedly showing a high-profile lawyer trying to fix judicial appointments with Malaysia's former chief judge, was elected to a seat in parliament from a seat in suburban Kuala Lumpur. The grainy video hit a nerve in Malaysia, whose judiciary has been under question since the late 1980s. Malaysia's blogging community offer alternative views in a country where the government keeps a tight control on mainstream media. The government said last year it might compel bloggers to register with the authorities to curb the spread of malicious content on the Internet. Government backers doubt whether bloggers turned opposition politicians could make their presence felt. "Beyond the major cities like Kuala Lumpur and Penang, there's not much the bloggers can really hope to accomplish," says Mohamad Norza Zakaria, a leader in Prime Minister Abdullah Ahmad Badawi's UMNO party ( www.umno-online.com ) The Chinese-backed DAP, by contrast, appointed blogger Ooi to head the party's "e-campaign". Even a barely literate 89-year-old grandmother running for parliament with little money and only a bicycle to get around on, hopped the cyberspace bandwagon with a Facebook profile and her own blog, courtesy of some Internet savvy supporters. Mamin Yusuf, however, lost. It wasn't clear how many of her potential voters were hooked up to the Internet in northeastern Terengganu. (Editing by Sanjeev Miglani) http://uk.news.yahoo.com/rtrs/200803...e-566e283.html  A Fading Sound Spreads Echo Far From Indonesia Peter Gelling BOGOR, Indonesia — Every day, a dozen grizzled men — shirtless, shoeless and with clove cigarettes dangling from their lips — hover over a pit of fire here in a tin-roofed shack, taking turns pounding glowing metal into the shape of a gong with the crudest of hammers. The men are artisans, turning out the xylophones, gongs, drums and strings that make up this country’s traditional gamelan orchestras. All the workers are descendants of the laborers hired when this family-run business began making instruments in 1811. Theirs is a dying art form. The business, the Gong Factory, is one of Indonesia’s few remaining gamelan workshops. Fifty years ago there were dozens of such tiny workshops in Bogor here on the island of Java alone. The workshop in this small city 30 miles south of Jakarta has been one of the main suppliers of gamelan instruments in Java since the 1970s, when three of its competitors shut their doors because of a lack of demand. For a time, the lack of competition increased the workshop’s orders. But over the past decade, orders have been steadily declining here, too, adding to worries over the rising cost of tin and copper and the decreasing supply of quality woods like teak and jackfruit, which are used to build the ornate stands that cradle the gongs, xylophones and drums. “I try to make sure there is always work for them so they can earn money,” Sukarna, the factory’s sixth-generation owner, said of his workers, who earn about $2 a day. “But sometimes it is difficult.” Gamelan, which is indigenous to Indonesia, has evolved over the centuries into a complex system of layered melodies and tuning, a system unfamiliar to the Western ear. (Fans of the television show “Battlestar Galactica” will recognize strains of gamelan from the show’s music.) Each orchestra is uniquely tuned and cannot use another’s instruments. With no conductor, gamelan is a communal, and often delicate, negotiation among a dozen or more musicians where age and social status factor into the music’s evolution through a single performance. Though gamelan music is still played throughout Indonesia — it can be heard at most traditional ceremonies and wafting out of Bali’s open-air meeting houses, where neighbors gather to discuss local issues or simply gossip — its popularity is dwindling among the younger generation of Indonesians, who are more easily lured by Western rock. Sukarna, who like many Indonesians uses just one name, is 82 years old and worried for years that his two sons, who do not share his passion for gamelan, might abandon the family business. He was relieved when his younger son, Krisna Hidayat, who is 28 and has a business degree, reluctantly agreed to take over as manager. Still, Mr. Hidayat said his favorite band was the American hard-rock spectacle Guns N’ Roses. “My father still listens to gamelan at home,” he said. “I prefer rock ’n’ roll.” Joan Suyenaga, an American who came to Java to indulge her fascination with its traditional performing arts and married a gamelan musician and instrument maker, said it had been dispiriting to witness decreasing local interest in an art form that had such a storied history. According to Javanese mythology, an ancient king invented the gong as a way to communicate with the gods. “Our children play in rock bands and are immersed in emo, ska, pop and Western classical music,” she said. “There definitely are a few desperate attempts to preserve the gamelan tradition here in Java, but not nearly as much as there could be.” But in a twist, as interest in gamelan has waned in its birthplace, foreign musicians have become enamored with its sound. Bjork, the Icelandic pop star, has used gamelan instruments in a number of her songs, most famously in her 1993 recording “One Day,” and has performed with Balinese gamelan orchestras. Several contemporary composers have incorporated gamelan into their works, including Philip Glass and Lou Harrison, as did art-rock bands of the 70s like King Crimson, which adopted gamelan for Western instruments. Perhaps more significantly, some schools in the United States and Europe now offer gamelan courses. Britain even includes it in its national music curriculum for primary and secondary schools, where children study and play gamelan. “It is interesting and very sad that gamelan is used to teach basic musical concepts in Great Britain, whereas in Indonesian schools our children are exposed only to Western music and scales,” Ms. Suyenaga said. Ms. Suyenaga’s disappointment aside, the uptick in Western interest in gamelan has had one very practical impact in Indonesia. These days, it is orders from abroad that keep the Gong Factory, and other workshops like it, in business. “Most orders come from America, but we also get many from Australia, France, Germany and England,” said Mr. Hidayat, the manager. To fill those orders, he and his father wake up every weekday morning at 5 to begin the process of mixing the metals that is crucial to producing high-quality gongs. Only the two men know the exact mix of tin and copper the workshop uses. “It’s like making dough: it can’t be too soft or too hard, it has to be perfect,” Mr. Hidayat said. “A lot of this process is instinctual.” Once he and his father have found the right blend, workers take it to the shack, where the smoke from the fire mixes with the men’s cigarette smoke. The men begin their banging, sending sparks flying. Once they are satisfied with the shape, another laborer cradles the gong between his bare feet and carefully shaves it down, testing it often until he thinks the tone is right. It often takes days to make a single gong. Mr. Hidayat holds out at least some hope that Western interest in the music will jump start a resurgence of interest in gamelan music in Indonesia. But he acknowledges that he will not be uploading traditional songs to his iPod anytime soon. Ms. Suyenaga is less optimistic. “I cannot say the situation is improving or even healthy,” she said. “Probably the peak for us was 5 to 15 years ago.” Retno Pratiwi contributed reporting. http://www.nytimes.com/2008/03/10/wo...10indo.html?hp  A D.I.Y. Approach to Making a Web Commercial Bob Tedeschi THE masses have flooded the Web with schlocky home movies. Big companies have added streams of more polished videos. But millions of businesses have sat out the revolution because they would rather not make fools of themselves trying to make their own commercials. What they need is a crutch, and somebody is about to hand them one. Online start-ups are percolating new methods to help companies create passable videos and commercials on the cheap, and distribute them across the Internet. For consumers, the trend promises a shopping experience more akin to QVC than eBay or Amazon. “This won’t transform the online experience, but it can really add value for customers, so companies will be interested in this,” said Patti Freeman Evans, an online retail analyst with JupiterResearch. “And if they can get help from someone who’s learning how video works online, that can be a great advantage.” That, Ms. Evans said, describes Matt Singer, a founder of The Talk Market (www.talkmarket.com) in New York, which bills itself as a sort of QVC for the masses. Mr. Singer helped clients sell “hundreds of thousands” of CDs on QVC from 2000 through 2007, he said, before deciding last year to take that expertise to smaller companies. Merchants can sell huge quantities on QVC, Mr. Singer said, thanks largely to a highly personal sales approach where product designers or the channel’s sales staff create a story around an item. Only those willing to bet big on their products can play on television, however. “I basically lived in fear that some big current event would cause people to turn to another channel at that moment,” he said, “and all those CDs would come back to me.” Mr. Singer joined last year with Amanda Eilian, a former Baker scholar at Harvard Business School, to build The Talk Market, which helps businesspeople shoot, edit and post videos to the Web. The service costs nothing, although users share with The Talk Market a 5 percent commission whenever someone clicks on the “buy” button in the video window. The Talk Market begins with an online tutorial on how to shoot product demonstration videos: light well, change camera angles, speak as if you are talking to a friend and look directly into the lens “as if you’re locking eyes with your audience.” On their home computers, users splice together a clip, typically two minutes or less, relying on background music and animated graphics from The Talk Market to lead into key moments in the presentation (“here’s how I make it,” for instance). Users then upload the completed file to The Talk Market, where it is posted according to the product category. They may also post the video on their own Web sites. In the future, fans of a particular designer will be able to post the videos on their own sites and collect a bounty for whatever sales they help generate. According to Nina Valenti, owner of naturevsfuture, an apparel company based in Brooklyn, The Talk Market approach “helps me explain a garment like I would if someone was one-on-one with me.” “I may not necessarily have TV charm, but I’m thorough,” Ms. Valenti added. “And I think I can get people excited about the product by telling them about the concept, and about my background, or why I chose this fabric.” Mr. Singer and Ms. Eilian, who is also vice president of the Capitol Acquisition Corporation, a mergers and acquisitions company that raised roughly $262 million in a public offering late last year, said they were in the midst of seeking financing to market the service more aggressively this spring. • In the meantime, other companies are also taking aim at this category, with slightly different approaches. TurnHere, a company based in Emeryville, Calif., has an online network of about 3,500 freelance video producers who can shoot, produce and post videos of small businesses, typically for under $1,000, according to Bradley J. Inman, TurnHere’s chief executive. Mr. Inman, who is the founder of Inman News, a real estate publisher, said the service, which had its debut in mid-2006, has produced roughly 3,500 of these minute-long “minidocumentaries” for clients. An increasing number of those clients are smaller companies. “This can really capture the fabric of a small business, which has never been able to afford television advertising,” he said. In some cases, companies like IAC/InterActiveCorp’s Citysearch unit will sell TurnHere’s service to its advertising clients and post the videos on Citysearch. TurnHere pays freelance producers market rates, Mr. Inman said, and earns a premium on fees it collects from clients. That model helped the company attract $7.5 million in venture financing recently, from Hearst Interactive Media and Venrock, among others. • Online merchants, who have experimented with video for years, are also beginning to see the value of letting manufacturers and designers pitch products themselves, rather than posting runway shows or conventional commercials. At eBags, the online bag and apparel site, Scott Roon, a young employee in the marketing department, suggested to management last year that they shoot short profiles of designers and post those online. They suggested he try it himself. Mr. Roon now has about 60 videos completed, and a new job, flying around the country shooting and producing video profiles. Peter Cobb, an eBags founder, said he had been unable to determine how many additional sales the company has made from the videos. “But there are absolutely huge benefits,” he said. “We’ve gotten great feedback from customers, and the brands love it.” http://www.nytimes.com/2008/03/10/te...gy/10ecom.html  Facebook Founder Heckled at Web Conference A keynote talk with Facebook founder Mark Zuckerberg descended into chaos as the audience heckled the interviewer for failing to get to the point. Zuckerberg, the 23-year-old billionaire, was the keynote speaker at the SXSW Interactive Festival in Austin, Texas. Business Week journalist Sarah Lacy took the stage to question Zuckerberg, but the audience quickly grew tired of the topics she focused on, claiming that the real issues were being ignored. "Never, ever have I seen such a train wreck of an interview," claimed audience member, Jason Pontin, via Twitter. Lacy finally allowed the crowd to take over, and Zuckerberg was subjected to an enthusiastic barrage of questions about the real issues facing the social networking site, such as privacy and data portability. "The audience is asking Zuckerburg better questions than Lacy did," said former Microsoft blogger, Robert Scoble, via his Twitter feed. When asked about Facebook's Beacon advertising system, which he said last year was the beginning of a new era of advertising, Zuckerberg admitted that his claims may have been premature. "We probably got a little bit ahead of ourselves. We came across as knowing more than we really knew... We have a lot of things we need to build before we get there," admitted Zuckerberg. Questions about the possible emergence of a rumoured Facebook music download service, following talks with record labels, were met with denial. "What's going on there is we talk to a lot of companies all the time... there are [already] music applications on Facebook," Zuckerberg said. "As a company we are out building relationships, but at this point I can say we have nothing to talk about right now." Another popular topic from the audience was data portability and privacy. In recent months several scandals have emerged over security vulnerabilities in the site and the company's practices when dealing with users' personal information. "Almost all of the mistakes we made, we didn't give people enough control. We need to give people complete control over their information," said Zuckerberg. "The more control and the more granular the control, the more info people will share and the more we will be able to achieve our goals." Another revelation was that recent management changes at Facebook may have been due to a disagreement over a potential takeover bid from Yahoo. The company offered $1 billion for Facebook last year, but the deal was turned down, with most staff opposing the offer. "We made some management changes," said Zuckerberg, when asked what happened to those that didn't. http://www.pcpro.co.uk/news/176130/f...onference.html  Oops Cop's 8742 Child Porn Mistakes Christine Kellett A Queensland police officer caught with more than 8000 child porn images on his home computer has avoided spending any time in jail. Thomas James Anthony Wilson, 25, pleaded guilty in Brisbane's District Court today to possessing the lewd material, including pictures of boys as young as 10 engaging in sex acts. He was sentenced to 18 months' jail, but the term was wholly suspended after his lawyer successfully argued Wilson had downloaded the images by mistake. The former policeman, who has since lost his job, was one of 1717 suspects identified as part of a 2003 child porn investigation by US Customs and FBI agents. Police traced his credit card to a child porn website titled “Sunshine Boys”, where Wilson had paid a $35 access fee. A March 28, 2006 raid on his Shorncliffe home on Brisbane’s northside uncovered a computer loaded with pornography. In all, 8742 images were identified as depicting children aged between 10 and 18 posing nude, masturbating and engaging in sex acts. Wilson's defence barrister Craig Eberhardt told the court his client had not purposefully sought out child abuse images when he downloaded pornography files from the internet. He suggested Wilson may have viewed some of it as a way to deal with his own sexuality as a young man. "(He is) not a pedophile, he does not have pedophilic tendencies," Mr Eberhardt said, citing medical evidence. "His culpability comes from his failure to get rid of it once he knew it was there." Judge Tony Rafter SC said a wholly suspended sentence was appropriate because Wilson posed no risk to children and was unlikely to reoffend. But he said the actions of the disgraced policeman had nonetheless helped to feed an "evil and exploitative industry". "You should have been accutely aware of the seriousness of the offence because you were a serving police officer at the time," Judge Rafter chastised. "I accept that you did not actively seek child pornography and these images were accessed somewhat accidentally. "I am also mindful that as a former police officer, a period of imprisonment would be harsher upon you." Wilson left court supported by family. http://www.brisbanetimes.com.au/news...126085158.html  Rate-My-Cop: New Website Has Police Furious Police agencies from coast to coast are furious with a new website on the internet. RateMyCop.com has the names of thousands of officers, and many believe it is putting them in danger. Officer Hector Basurto, the vice president of the Latino Police Officers Association, recently learned about the site. "I'd like to see it gone," he said. "Having a website like this out there puts a lot of law enforcement in danger," he said. "It exposes us out there." Kevin Martin, the vice president of the San Francisco Police Officers Association, agrees. "Will they be able to access our home addresses, home phone numbers, marital status, whether or not we have children? That's always a big concern for us," he said. Creators of the site say no personal information will be on the site. They gathered officers' names, which are public information, from more than 450 police agencies nationwide. Some listings also have badge numbers along with the officer's names. Rebecca Costell says, in a statement, that the site helps people rate more than 130,000 officers by rating them on authority, fairness and satisfaction. She adds, "Our website's purpose is to break the stereotype that people have that cops are all bad by having officers become responsible for their actions." The site is so new that many Bay Area police agencies are not aware of it. San Francisco police say they have no connection with the site and would not take any of its comments seriously. Police associations that represent more than 100,000 police and sheriffs in California are now seeking legislation to see if they can eliminate the site altogether. They say that officers who are rated face unfair maligning without any opportunity to defend themselves. The CPCA will work with other law enforcement associations to pursue legislation to stop the website. Constitutional attorney and former San Francisco Police Commissioner Peter Keane said eliminating the site is difficult. "Any kind of publication is protected as long as it's not publishing privileged information," he said. The First Amendment would be the site's protection. http://cbs13.com/local/rate.a.cop.2.673410.html  GoDaddy Silences Police-Watchdog Site RateMyCop.com Kevin Poulsen A new web service that lets users rate and comment on the uniformed police officers in their community is scrambling to restore service Tuesday, after hosting company GoDaddy unceremonious pulled-the-plug on the site in the wake of outrage from criticism-leery cops. Visitors to RateMyCop.com on Tuesday were redirected to a GoDaddy page reading, "Oops!!!", which urged the site owner to contact GoDaddy to find out why the company pulled the plug. RateMyCop founder Gino Sesto says he was given no notice of the suspension. When he called GoDaddy, the company told him that he'd been shut down for "suspicious activity." When Sesto got a supervisor on the phone, the company changed its story and claimed the site had surpassed its 3 terabyte bandwidth limit, a claim that Sesto says is nonsense. "How can it be overloaded when it only had 80,00 page views today, and 400,000 yesterday?" Police departments became uneasy about RateMyCop's plans to watch the watchers in January, when the Culver City, California, startup began issuing public information requests for lists of uniformed officers. Then the site went live on February 28th. It stores the names and, in some cases, badge numbers of over 140,000 cops in as many as 500 police departments, and allows users to post comments about police they've interacted with, and rate them. The site garnered media interest this week as cops around the country complained that they'd be put at risk if their names were on the internet. "Having a website like that puts a lot of law enforcement, in my eyes, in danger because it exposes us out there," Officer Hector Basurto, vice president of the Latino Police Officers Association, told ABC television affiliate KGO. Since undercover officers aren't in the database, and the site has no personal information like home addresses, that fear seems unfounded. Chief Jerry Dyer, president of the California Police Chiefs Association, voices what sounds like a more honest concern: that officers will face "unfair maligning" by the citizens they serve. Sesto says police can post comments as well, and a future version of the site will allow them to authenticate themselves to post rebuttals more prominently. Chief Dyer wants to get legislation passed that would make RateMyCop.com illegal, which, of course, wouldn't pass constitutional muster in any court in America. Unfortunately for the startup, the company it chose for hosting is known to be quick to censor its customers. In January of last year, GoDaddy took down entire computer security website -- delisting it from DNS -- to get a single, archived mailing list post off the web. On that occasion, at least, it gave the site's owner 60 seconds notice. GoDaddy notified Seto by posting its "Oops!" message to his public website. "You put on my website for me to call you, when you have my phone number?," says Sesto. A GoDaddy spokeswoman says the company can't comment on the RateMyCop takedown due to its privacy policy. Sesto says he's already arranged hosting elsewhere, and hopes to have the site online Tuesday night. http://blog.wired.com/27bstroke6/200...y-silence.html  Stunning New Report on Domestic NSA Dragnet Spying Confirms ACLU Surveillance Warnings (3/12/2008) FOR IMMEDIATE RELEASE CONTACT: 675-2312 or media@dcaclu.org WASHINGTON – The American Civil Liberties Union responded today to a stunning new report that the NSA has effectively revived the Orwellian "Total Information Awareness" domestic-spying program that was banned by Congress in 2003. In response, the ACLU said that it was filing a Freedom of Information Act (FOIA) request for more information about the spying. And, the group announced that it was moving its "Surveillance Clock" one minute closer to midnight. "Congress shut down TIA because it represented a massive and unjustified governmental intrusion into the personal lives of Americans," said Caroline Fredrickson, Director of the Washington Legislative Office of the ACLU. "Now we find out that the security agencies are pushing ahead with the program anyway, despite that clear congressional prohibition. The program described by current and former intelligence officials in Monday's Wall Street Journal could be modeled on Orwell’s Big Brother." The ACLU said the new report confirmed its past warnings that the NSA was engaging in extremely broad-based data mining that was violating the privacy of vast numbers of Americans. The Total Information Awareness (TIA) program was a mammoth data mining program that envisioned programming computers to trawl through an extensive list of databases containing personal information about Americans – including communications, medical, travel, education and financial data – in an attempt to detect supposedly "suspicious" patterns. Congress shut down the program amid bipartisan objections that it was the most far-reaching domestic surveillance proposal that had ever been offered. "Year after year, we have warned that our great nation is turning into a surveillance society where our every move is tracked and monitored," said Barry Steinhardt, Director of the ACLU’s Technology and Liberty Project. "Now we have before us a program that appears to do that very thing. It brings together numerous programs that we and many others have fought for years, and it confirms what the ACLU has been saying the NSA is up to: mass surveillance of Americans." Last year, the ACLU created its Surveillance Clock (www.aclu.org/clock) as a way to symbolize the nation’s rapid descent toward a surveillance society. Initially set to six minutes before midnight, the ACLU today moved it up to five minutes before midnight to highlight the greater threat to privacy Americans face in light of the NSA’s activities. According to the new Journal report, the NSA was engaging in broad domestic spying operations that involve collecting and analyzing the personal information of Americans in ways that are "essentially the same" as TIA. The elements that reportedly make up the new spying encompass a variety of mass surveillance and data mining programs about which the ACLU has previously warned, including: TIA and other data mining programs. • The NSA’s illegal wiretapping program, the so-called Terrorist Surveillance Program (TSP). • The Patriot Act’s broadening of FBI power to collect third-party personal information without a subpoena through Section 215 searches and National Security Letters. • The Treasury Department’s expanded surveillance of financial transactions through Cash Transaction Reporting and Suspicious Activity Reporting. • The CIA’s illegitimate access to the SWIFT database to monitor international financial transactions. • DHS’s efforts to increase collection and monitoring of airline passenger data. • Partnerships between these government agencies and private sector entities to collect and monitor customers’ data and transactions. The erosion of privacy through the judicial creation of a distinction between content and "transactional data" (such as the recipients of e-mails or phone calls and the times and dates of each communication) through the Patriot Act and prior developments. "Congress needs to investigate immediately whether its will has been thwarted, and the media needs to give this program the attention it deserves as a radical departure from the privacy that Americans have always expected," said Fredrickson. "Just how many times is Congress going to sit back and watch this administration run roughshod over its prerogatives?" The FOIA request the ACLU filed today is intended to gain information about the "role that the NSA plays as a hub for the collection, analysis and distribution" of "transactional information of Americans." It seeks information from the NSA as well as the FBI, CIA, the Office of the Director of National Intelligence, and the Departments of Treasury, Justice, Defense, and Homeland Security. In 2006, the ACLU published a summary of what it believed the NSA was doing, based on the various media reports citing current and former intelligence officials. In the piece, entitled "Eavesdropping 101," the ACLU warned that the NSA was not just carrying out warrantless wiretaps on selected individuals, but probably carrying out broader data dragnets that violated the privacy of millions of Americans. This prospect has not always remained in focus during the debates over the agency’s illegal spying. "We now know that TIA lives," said Steinhardt. "The question is, does American privacy live? And does Congress’ will to defend it? This program will be a test case; may we prove worthy of the freedom we have inherited." The ACLU white paper "Eavesdropping 101" is online at http://www.aclu.org/safefree/nsaspyi...s20060131.html Other information about NSA spying can be found at www.aclu.org/nsa Information about TIA can be found at http://www.aclu.org/privacy/spying/1...s20040116.html To read the ACLU's FOIA request, go to: http://www.aclu.org/privacy/gen/34443leg20080312.html  FBI Tried to Cover Patriot Act Abuses With Flawed, Retroactive Subpoenas, Audit Finds Ryan Singel FBI headquarters officials sought to cover their informal and possibly illegal acquisition of phone records on thousands of Americans from 2003 to 2005 by issuing 11 improper, retroactive "blanket" administrative subpoenas in 2006 to three phone companies that are under contract to the FBI, according to an audit released Thursday. Top officials at the FBI's counter-terrorism division signed the blanket subpoenas "retroactively to justify the FBI's acquisition of data through the exigent letters or or other informal requests," the Justice Department's Inspector General Glenn Fine found. The revelations come in a follow-up report to Fine's 2007 finding that the FBI abused a key Patriot Act power, known as a National Security Letter. That first reports showed that FBI agents were routinely sloppy in using the self-issued subpoenas and issued hundreds that claimed fake emergencies. With the flawed follow-up letters, the Counterterrorism division attempted to provide retroactive legal justification for telephone data the division had gotten on 3,860 phone numbers, gotten either through verbal requests to the companies or false emergency requests. The letters are related to still-secret contracts the FBI's Communication Analysis Unit has with AT&T, Verizon and MCI. The contracts pay the companies to store subscribers' phone records for longer periods of time and to provide faster service for FBI subpoenas. Those contracts began in May 2003, but the FBI refuses to release them. At least one of the letters was signed by an assistant director and none were cleared with the FBI's general counsel. FBI agents issue tens of thousands of National Security Letters annually to get phone records, portions of credit histories, and track down IP addresses without getting a judge's approval in cases involving suspected terrorism, computer crimes or espionage. Additionally, some of those retroactive NSLs sought records that the FBI was not authorized to obtain, and failed to explain -- as required by policy -- what investigation the records pertained to. Fine found that all were "issued in violation of internal FBI policy." In his 2007 report on the FBI's use of that Patriot Act power during 2003 to 2005, Fine disclosed that officials at the counter-terrorism division had issued more than 700 emergency requests for data to telephone companies -- so-called exigent letters -- most with false promises that a court order was in the works and would be delivered after the fact. Those letters prompted a further investigation of those letters, including a reported criminal probe of counter-terrorism officials, and Thursday's report says an in depth report on that office is forthcoming. The report shows the need for Congress to narrow the FBI's powers and strengthen privacy laws, according to Mike German, a longtime FBI agent who now works for the ACLU, who says it's clear the FBI has been breaking the law. "The FBI has flagrantly put aside the rule of law and its internal guidelines time and again," German said "This is the kind of abuse that is inevitable when we broaden the government's surveillance power and do not attempt to modernize privacy standards. Both the House and Senate have bills waiting to be marked up that will greatly limit this authority. Congress needs to act on this now.” The 187-page report (.pdf) focused on NSL usage in 2006 and how the FBI attempted to correct the abuses brought to light by last year's report. Fine said the FBI had made "significant progress in implementing our recommendations," but tempered that statement by concluding "it is too soon to definitively state whether the news systems and cohntrols developed by the FBI and the Department will eleiminate fully the problems with the use of NSLs." The Justice Department issued a statement Thursday saying it was pleased with Fine's assessment of their efforts after his 2007 report and downplayed the report's revelations of abuses in 2006, saying it is "no surprise that this year’s report found problems similar to those identified in the first OIG report, which covered the period 2003 through 2005." The Inspector General took issue with the FBI's inability to track where data is shared or if the data is used in criminal prosecutions by state and local law enforcement. The report also criticized the FBI's insistence that all data collected by the letters -- even phone records that cleared a suspect -- should be stored for decades in the FBI's massive Investigative Data Warehouse. That storehouse allows investigators to search for and comb through data from other investigations. The FBI issued 49,425 NSLs in 2006, up slightly from 2005's 47,221 requests. Since NSLs can name more than one person, phone number or email address, it is not known how many persons were investigated through these requests. In a footnote, Fine reveals that in a 2004 investigation the FBI issued 9 NSLs that sought subscriber information on 11,100 phone numbers. The report also shows that the FBI is increasingly targeting citizens and green card holders, with more than 11,517 requests in 2006 targeting U.S. persons, while Non U.S. persons were targeted with 8,605 requests. http://blog.wired.com/27bstroke6/200...ied-to-co.html  Wikileaks Publishes FBI VoIP Surveillance Docs Anonymous The folks on wikileaks have published a new interesting and shocking report: FBI Electronic Surveillance Needs for Carrier-Grade Voice over Packet (CGVoP) Service. The 88 paged document, which is part of the CALEA Implementation Plan was published in January 2003 and describes in detail all needs for surveillance of phone calls made via data services like the internet. Wikileaks has not published any analysis yet, so maybe some of the techies hanging around this end of the internet are interested in taking that one on. http://yro.slashdot.org/yro/08/03/15/2021257.shtml  NSA Quietly Expands Domestic Spying Program, Even as Congress Balks "The central role the NSA has come to occupy in domestic intelligence gathering has never been publicly disclosed," The Wall Street Journal's Siobhan Gorman reports on Monday page ones. "But an inquiry reveals that its efforts have evolved to reach more broadly into data about people's communications, travel and finances in the U.S. than the domestic surveillance programs brought to light since the 2001 terrorist attacks." "According to current and former intelligence officials, the spy agency now monitors huge volumes of records of domestic emails and Internet searches as well as bank transfers, credit-card transactions, travel and telephone records," Gorman adds. "The NSA receives this so-called 'transactional' data from other agencies or private companies, and its sophisticated software programs analyze the various transactions for suspicious patterns. Then they spit out leads to be explored by counterterrorism programs across the U.S. government, such as the NSA's own Terrorist Surveillance Program, formed to intercept phone calls and emails between the U.S. and overseas without a judge's approval when a link to al Qaeda is suspected." "The NSA's enterprise involves a cluster of powerful intelligence-gathering programs, all of which sparked civil-liberties complaints when they came to light," he continues. "They include a Federal Bureau of Investigation program to track telecommunications data once known as Carnivore, now called the Digital Collection System, and a U.S. arrangement with the world's main international banking clearinghouse to track money movements." Excerpts follow: The effort also ties into data from an ad-hoc collection of so-called "black programs" whose existence is undisclosed, the current and former officials say. Many of the programs in various agencies began years before the 9/11 attacks but have since been given greater reach. Among them, current and former intelligence officials say, is a longstanding Treasury Department program to collect individual financial data including wire transfers and credit-card transactions. ... Two former officials familiar with the data-sifting efforts said they work by starting with some sort of lead, like a phone number or Internet address. In partnership with the FBI, the systems then can track all domestic and foreign transactions of people associated with that item -- and then the people who associated with them, and so on, casting a gradually wider net. An intelligence official described more of a rapid-response effect: If a person suspected of terrorist connections is believed to be in a U.S. city -- for instance, Detroit, a community with a high concentration of Muslim Americans -- the government's spy systems may be directed to collect and analyze all electronic communications into and out of the city. The information doesn't generally include the contents of conversations or emails. But it can give such transactional information as a cellphone's location, whom a person is calling, and what Web sites he or she is visiting. For an email, the data haul can include the identities of the sender and recipient and the subject line, but not the content of the message. ... Two current officials also said the NSA's current combination of programs now largely mirrors the former TIA project. But the NSA offers less privacy protection. TIA developers researched ways to limit the use of the system for broad searches of individuals' data, such as requiring intelligence officers to get leads from other sources first. The NSA effort lacks those controls, as well as controls that it developed in the 1990s for an earlier data-sweeping attempt. ... NSA gets access to the flow of data from telecommunications switches through the FBI, according to current and former officials. It also has a partnership with FBI's Digital Collection system, providing access to Internet providers and other companies. The existence of a shadow hub to copy information about AT&T Corp. telecommunications in San Francisco is alleged in a lawsuit against AT&T filed by the civil-liberties group Electronic Frontier Foundation, based on documents provided by a former AT&T official. In that lawsuit, a former technology adviser to the Federal Communications Commission says in a sworn declaration that there could be 15 to 20 such operations around the country. Current and former intelligence officials confirmed a domestic network of hubs, but didn't know the number. "As a matter of policy and law, we can not discuss matters that are classified," said FBI spokesman John Miller. The budget for the NSA's data-sifting effort is classified, but one official estimated it surpasses $1 billion. The FBI is requesting to nearly double the budget for the Digital Collection System in 2009, compared with last year, requesting $42 million. "Not only do demands for information continue to increase, but also the requirement to facilitate information sharing does," says a budget justification document, noting an "expansion of electronic surveillance activity in frequency, sophistication, and linguistic needs." http://rawstory.com/news/2008/NSA_qu...gram_0310.html  New Camera Vastly Improves Surveillance Revolutionary camera design could have far-reaching implications for the military, crime prevention, and enforcement as well as traffic analysis and emergency response support; design is based on an array of light sensitive chips placed at the focal plane of a large multiple-lens system Researchers at The University of Alabama in Huntsville have developed a wide-angle camera which will be able to provide security forces with the ability to monitor large areas through high-resolution images taken from a satellite or an airborne craft, says researcher David Pollock. Pollock first discovered that if you point a large number of lenses toward a common point, and then make a small correction on each of the lenses, you provide a camera with capabilities that far surpass existing technologies. "If you look at high-resolution images taken by satellite or aircraft, the field-of-view in those photographs is tiny," he said. "This camera provides anyone with the ability to view the entire scene and, simultaneously, zoom in closely on a certain area with very high resolution at real time." Flying at an altitude of 15,000 feet, a developmental version of the camera can see a 21-kilometer diameter area with a resolution of 0.3 meters. As a comparison, most Google Earth imagery is one meter. The optics systems patent is shared by UA Huntsville and Sony. Images from existing cameras have to be tiled like the pieces of a jigsaw puzzle before a full picture can be seen. This can create problems for security forces, such as Department of Defense, border or harbor patrol, or homeland security. For example, vehicles can end up appearing more than once if they move from one image to the next between exposures. These types of errors frequently exist in online mapping tools, such as Google Earth or Microsoft’s Virtual Earth, according to Pollock. This is where researchers at UA Huntsville stepped in to configure an array of light sensitive chips -- each one recording small parts of a larger image -- and place them at the focal plane of a large multiple-lens system. The Week in Review is edited and published by Jack Spratts. The system has the structure of a common kitchen utensil, a colander. The camera would have one giga-pixel resolution, and be able to record images at five frames per second. Springfiled, Virginia-based ArguSight has signed a licensing agreement with the university and seeking venture capital to bring the product to the commercial marketplace. CEO Stuart Claggett compares the product to a popular TV product. "The complete camera system is like a ‘TIVO’ in the sky," he said. "It captures high-quality imagery and records all the data. A user can request numerous high-definition video windows of live data in real-time or you can review all of the video on demand on the ground when the aircraft lands." Ultimately the camera can cover nearly a hemispherical field-of-view with uniform image quality and sensitivity. The initial camera design constraint was to obtain greater than 109 samples within a 10 x 10 km ground footprint. It was quickly realized that with 4 mega-samples (mega-pixel) per camera this would require 271 cameras. The constraint leads to significant, greater than 90 percent sample redundancy. Reducing the redundancy to less than 1 percent significantly expands the field-of-view, Pollock said. Further, because of the modular nature, the field-of-view can be configured to suit specific applications. For example, what one might call a Mohawk, an arc of cameras would sample a long, narrow strip. Also, a camera that can operate in other spectral regions, with a field-of-view configuration and a sample size to suit the application is feasible, according to Pollock. He states that software development to fully exploit the camera data capacity continues. Pollock said the camera could have far-reaching implications for the military, crime prevention, and enforcement as well as traffic analysis and emergency response support. The giga-pixel camera will fit in a one-meter cube, could be flown on any type of vehicle – airplanes, helicopters, blimps or unmanned aerial vehicles. UA Huntsville filed the patent for the large-format giga-pixel camera and shares that patent on a 50-50 basis with Sony Corp. http://hsdailywire.com/single.php?id=5745  But can it find my keys? Researchers Show Principles of Mind-Reading Machine Researchers have developed a more sophisticated way to extract visual stimuli from brain signals; they developed a computational model that uses functional MRI (fMRI) data to decode information from an individual's visual cortex; system may help in decoding dreams, and may offer a more humane interrogation technique A device which reveals what a person sees by decoding their brain activity could soon be a reality, say researchers who have developed a more sophisticated way to extract visual stimuli from brain signals. Scientists at the University of California, Berkeley, developed a computational model that uses functional MRI (fMRI) data to decode information from an individual's visual cortex -- the part of the brain responsible for processing visual stimuli. "Our research makes substantial advances towards being able to decode mental content from brain activity as measured using fMRI," Kendrick Kay, a coauthor of the study, told the New Scientist's James Urquhart. "In fact, our results suggest it may soon be possible to reconstruct our visual experiences from brain activity." Previous research has shown that fMRI can pick out brain activity associated with viewing different images, but so far it has only been possible to identify very basic images, from fixed categories, such as a face or a house. The process also depends on prior knowledge of the associated brain activity. Now the Berkeley team has shown that brain imaging can reveal much more complex and arbitrary images, without prior knowledge of brain activity. The team first used fMRI to measure visual cortex activity in people looking at more than a thousand photographs. This allowed them to develop a computational model and "train" their decoder to understand how each person's visual cortex processes information. Next, participants were shown a random set of just over 100 previously unseen photographs. Based on patterns identified in the first set of fMRIs, the team was able to accurately predict which image was being observed. "It is going to be particularly powerful in the field of visual perception and possibly the field of decoding motor responses," says John-Dylan Haynes of the Max Planck Institute for Human Cognitive and Brain Sciences in Leipzig, Germany. The research also hints that scientists might one day be able to access dreams, memories, and imagery, says Haynes, providing the brain processes dreams in a way that is analogous to visual stimuli. "The difficulty is that that it's very hard to set up models for other types of complex thoughts, such as memories and intentions," Haynes says. http://hsdailywire.com/single.php?id=5713  House Democrats Refuse to Give Telecoms Immunity, Seek Warrantless Wiretapping Investigation AP Locked in a standoff with the White House, House Democrats on Tuesday maintained their refusal to shield from civil lawsuits telecommunications companies that helped the government eavesdrop on their customers without a secret court's permission. But they offered the companies an olive branch: the chance to use classified government documents to defend themselves in court. House Democratic leaders unveiled a bill that they hoped would bridge the gap between the electronic surveillance bill passed by the Senate last month and a rival version the House approved last fall. The House bill also would create a bipartisan commission, modeled after the 9/11 Commission, to investigate the Bush administration's secret wiretapping program. The legislation drew swift criticism from congressional Republicans and from Attorney General Michael Mukasey and National Intelligence Director Mike McConnell, who said it fails to fix problems with the 30-year-old Foreign Intelligence Surveillance Act that Congress is trying to update. They also said any bill that does not provide telecom immunity is unacceptable to the Bush administration. White House Press Secretary Dana Perino said the bill would impose "cumbersome" requirements on the intelligence agencies to conduct wiretaps. She also said the proposed investigative commission shows "House leaders are more interested in playing politics" than they are in preventing terrorist attacks. House Democrats point out that Congress still does not know what the telecommunications companies did that requires legal immunity because the White House has only allowed Judiciary and Intelligence committee members to read the secret documents that underpin the program. The 1978 FISA law dictates when the government needs court permission to conduct electronic eavesdropping inside the United States. The law has taken on particular importance in the global effort to thwart terrorists since the 2001 attacks on the United States. The most contentious difference between the two bills is whether they grant legal immunity to telecommunications companies that helped the government wiretap phone and computer lines after the Sept. 11 terrorist attacks without first getting approval from the FISA court. Congress created that court 30 years ago to prevent government abuse of its surveillance powers. The Senate bill would provide full immunity to the telecommunications companies. The House bill includes no such provision. The compromise proposed Tuesday by House Democratic leaders is expected to be brought to the floor for a vote Thursday. It would allow the roughly 40 lawsuits that are pending against the companies for their participation in the secret wiretapping program to go forward. "We are not going to cave in" on immunity, said House Judiciary Committee Chairman John Conyers, D-Mich. The companies are hamstrung from defending themselves in court, however. The Bush administration is invoking the "state secrets" privilege to block the companies from revealing secret documents that might bolster their argument that the eavesdropping program was legal. The House compromise bill would encourage the federal district judge hearing the telecommunications lawsuits to review those classified documents in secret to determine whether the companies acted legally. Judges in criminal cases often hear classified evidence in secret, but judges in civil cases do not, said House Majority Leader Steny Hoyer, D-Md. President Bush has vowed to veto any bill that does not grant the companies full retroactive immunity from lawsuits. Democratic leaders say they are trying to strike a balance between protecting the country against terrorist attacks and protecting civil liberties. http://www.siliconvalley.com/news/ci_8535518  House Dems Proposing Commission to Investigate Warrantless Spying, Still Reject Amnesty Ryan Singel Not only shouldn't companies that helped the government's warrantless spying on American citizens be given retroactive amnesty, the government should establish a national commission --- similar to the 9/11 Commission --to subpoena documents and testimony in order to find out -- and publish -- what exactly the nation's spies were up to during their five year warrantless, domestic surveillance program. In other words, House Democrats aren't planning a compromise on telecom amnesty and are actually going on offense to find a way to learn more about President Bush's five-year secret "Total Information Awareness" program. At least that's what's suggested by a 119-page draft bill being circulated by the leaders of the House Intelligence and Judiciary committees as answer to the Administration-backed Senate spying bill. The bill proposes a way for the government to issue blanket surveillance orders in order to force American telecom and internet providers to give the government a copy of every phone call, email or instant message that is believed to involve a foreigner. That mimics the Senate version and largely legalizes the president's warrantless wiretapping program. However, the bill restates -- as the 30-year old spying law stated -- that the law is the only route for the government to conduct electronic surveillance inside the United States. Bush opposes that language and says he has the power as Commander in Chief to spy inside America without any Congressional or court oversight. The bill also requires two audits of the warrantless wiretapping program -- a bipartisan National Commission and an Inspector General review of the warrantless wiretapping program. House Democrats are also seeking to block the administration from using the 'state secrets' privilege to block telecoms from showing federal judges -- even in chambers -- the letters given to them by the federal government about the legality of the program. Under the Foreign Intelligence Surveillance Act which the companies are being sued for violating, the companies could escape the lawsuits if they have a signed letter from the Attorney General, signed under oath, that the surveillance has "no substantial likelihood" of acquiring the content of a U.S. person's communication and the surveillance is targeted at communication means used exclusively by foreign powers (this is the foreign embassy exception). The companies claim that they have no defenses against the suits filed against them because the government says the letters are too-classified for even federal judges to see. The groups suing the companies doubt the letters comply with the requirements of the nation's spying laws and say they would be fine with the telecoms showing those letters in court. UPDATE - Electronic Frontier Foundation attorney Kevin Bankston -- who has been the San Francisco-based group's emissary to D.C. -- says he's very pleased with the proposal: Quote:
THREAT LEVEL hasn't had time to parse the entire bill yet and could use help seeing what is and is not in the fine print. The bill summary says: Quote:
http://blog.wired.com/27bstroke6/200...dems-prop.html  House to Close its Doors for Spying Bill Pamela Hess House Democratic leaders agreed Thursday to a rare closed-door session — the first in 25 years — to debate surveillance legislation. Republicans requested privacy for what they termed "an honest debate" on the new Democratic eavesdropping bill that is opposed by the White House and most Republicans in Congress. The closed-door debate was scheduled for late Thursday night, after the House chamber could be cleared and swept by security personnel to make sure there are no listening devices. The last private session in the House was in 1983 on U.S. support for paramilitary operations in Nicaragua. Only five closed sessions have taken place in the House since 1825. President Bush vowed to veto the House Democrats' version of the terrorist surveillance bill, saying it would undermine the nation's security. House leaders said they would vote on the bill Friday, just before taking a two-week recess. The bill would then have to be approved by the Senate. Bush opposes it in part because it doesn't provide full, retroactive legal protection to telecommunications companies that helped the government eavesdrop on their customers without court permission after the Sept. 11 terrorist attacks. About 40 lawsuits have been filed against telecommunications companies by people and organizations alleging they violated wiretapping and privacy laws. The lawsuits have been combined and are pending before a single federal judge in California. The Democrats' measure would encourage the judge to review in private the secret government documents underpinning the program in order to decide whether the companies acted lawfully. If they did, the lawsuits would be dismissed. The administration has prevented those documents from being revealed, even to a judge, by invoking the state secrets privilege. That puts the companies in a bind because it puts off limits evidence they might use to defend themselves. It wasn't clear what information would be presented in the closed session. Just a fraction of Congress has been allowed to read secret documents underpinning the surveillance program, and those who have arrived at varying conclusions. The Senate Intelligence Committee, after seeing classified material, said the companies acted on the good-faith belief that the wiretaps they allowed were lawful. Democrats on the House Judiciary and Intelligence Committees were unconvinced after being presented with the same material. Rhode Island Democrat Sen. Sheldon Whitehouse sits on both the Senate Intelligence and Judiciary committees. He said the documents lay out the Bush administration's rationale for why it was legal to sidestep a special secret court that normally authorizes wiretaps. Congress created the Foreign Intelligence Surveillance Court in 1978 to prevent government abuse of wiretapping. Whitehouse said the documents assert that the president has the power to determine what his constitutional powers are, particularly in a time of war. The surveillance law is intended to help in the pursuit of suspected terrorists by making it easier to eavesdrop on foreign phone calls and e-mails that pass through the United States. A temporary law expired Feb. 16 before Congress was able to produce a replacement bill. Bush opposed an extension of the temporary law as a tactic to pressure Congress into accepting the Senate version of the surveillance legislation. The Senate's bill provides retroactive legal immunity for the telecommunications companies. Bush said lawsuits against telecom companies would lead to the disclosure of state secrets. Further, he said lawsuits would undermine the willingness of the private sector to cooperate with the government in trying to track down terrorists. Michigan Rep. Peter Hoekstra, the top Republican on the House Intelligence Committee, said intelligence is already being lost. "Each and every day our capabilities are eroding," he said. Directing his message at the House, Bush said, "They should not leave for their Easter recess without getting the Senate bill to my desk." Bush predicted the Senate would not pass the House version of the bill, and said even if it did, he would veto it. At least one Senate Republican said the lawsuits should go forward to determine whether the wiretapping program was illegal. But Pennsylvania Sen. Arlen Specter wants to substitute the government for the phone companies as the defendant in the court cases. "The president can't have a blank check," Specter said in an interview. "If you close down the courts, there's no check and balance." He added: "Wiretaps are important for national security. There's no doubt about that. Al-Qaida and terrorism continue to be a major threat to this country. It is my hope that the president will not find it necessary to veto the bill, that we'll be able to work it out." House Majority Leader Steny Hoyer said Bush is misrepresenting the House bill, and suggested the fight is less about surveillance powers than it is that House Democrats are refusing to bend to Bush's wishes. "Congress owes the American people more than blind obeisance to the executive branch," said Hoyer, D-Md. http://news.yahoo.com/s/ap/20080313/...lHyjEBOwqs0NUE  House OKs Democratic Surveillance Bill AP The House has passed by a narrow margin a Democratic surveillance bill that President Bush has vowed to veto if it reaches his desk. The president objects to the bill because it does not protect from civil lawsuits the telecommunications companies that may have helped the government eavesdrop on American phone calls and e-mails without court permission after the Sept. 11 terrorist attacks. House Democrats say a federal judge should decide whether the wiretapping was legal. Bush favors a Senate version of the bill that does give the companies legal immunity, saying it is a matter of fairness to the companies. The White House had assured them no court order was needed for the wiretapping program. http://www.examiner.com/a-1278893~Ho...ance_Bill.html  Navy to Focus Only on Open Systems Peter Buxbaum The Navy will acquire only systems based on open technologies and standards. Vice Adm. Mark Edwards, deputy chief of naval operations for communications, broke the news March 5 to a Navy IT Day audience in Vienna, Va., sponsored by AFCEA International. “The days of proprietary technology must come to an end,” he said. “We will no longer accept systems that couple hardware, software and data.” The Navy’s decision was informed by a combination of motivations, including the desire to provide the latest capabilities to warfighters and control the costs of its information technology operations, he added. “We can’t accept the increasing costs of maintaining our present-day capabilities,” Edwards said. “In the civilian marketplace, it’s just the opposite. Some private-sector concerns are cutting their costs by 90 percent while expanding their performance.” Edwards noted that the Navy has cut the number of databases and applications it maintains and has reduced its networks by 40 percent. “But it is not enough,” he added. “We would have to double our IT budget over the next several years just to run in place.” By using an open network architecture, the Navy could rapidly upgrade its capabilities and handle increases for demand, Edwards said. “Above all, we must break the stovepipes of data so that we can share information across domains,” he said. The failure to lead in technology could have dire consequences, Edwards said. “The situation is very similar to that of the Soviet Union at the end of the Cold War,” he said. “Because we put them in a position of always having to catch up, the mere threat of the Strategic Defense Initiative crippled the Soviet ability to continue the arms race and enabled our side to dictate terms. If we remain behind in technology, a future adversary will eventually bring terms to us.” http://www.fcw.com/online/news/151858-1.html  Businesses Face Cut in Immigrant Work Force Katie Zezima For years, William Zammer Jr. has relied on 100 seasonal foreign employees to turn down beds, boil lobsters and serve cocktails at the restaurants, golf course and inn he owns on Cape Cod and in nearby Plymouth. This summer, however, the foreign workers will not be returning, and Mr. Zammer, like other seasonal employers across the nation, is scrambling to find replacements. “It’s a major crisis,” he said. “We’re very short on work force. We’ll be looking at opening a little later, closing a little earlier, looking at how we do our menus.” Mr. Zammer is caught up in a Congressional standoff over immigration overhaul that is punishing employers who play by the rules and that, advocates of change say, could cost small companies billions in lost business. In an effort to win support for a comprehensive immigration overhaul, the Congressional Hispanic Caucus and its allies have blocked voting on legislation that would allow employers to rehire foreign seasonal nonagricultural workers independent of a 1991 quota. As a result, the government is limited to issuing the 66,000 seasonal work visas set when the visa program, known as H-2B, became law — 33,000 for winter workers and 33,000 for summer workers. Last year, more than 120,000 foreign workers entered the country on H-2B visas. For Cape Cod, the impact has been devastating. Employers will receive only 15 of the 5,000 visas they had requested, according to the Cape Cod Chamber of Commerce. “It’s just ruthless for the Hispanic caucus to do this, use it as a bargaining chip,” said Mr. Zammer, whose foreign workers — mostly from Jamaica and Eastern Europe — normally make up 25 percent of his staff. “We’re working at finding new people. We have to. But it’s extremely difficult, because you end up stealing from other people who are also trying to get help.” Returning workers became exempt from the cap in 2005, when Congress passed the Save our Small and Seasonal Businesses Act, and President Bush signed it into law. The act expired in 2007, and Congress passed a one-year extension that was attached to the National Defense Authorization Act. The extension expired on Sept. 30, 2007, the end of the 2007 fiscal year. Employers say that unless Congress acts soon, they will have to scale back operations, because the labor pool in many resort areas is not deep enough to provide new workers, and many people do not want seasonal jobs. Patti Ann Moskwa, owner of the Yankee Rebel Tavern on Mackinac Island, Mich., plans to cut back dinner hours because she will be understaffed this summer. She said the 15 foreign workers who cooked and cleared tables at her restaurant were more than employees. “They’re like our family,” Ms. Moskwa said. “You don’t want to be the person to call these people and tell them the government won’t let them back. It’s a sad situation for us and the workers.” Republicans in Congress have resisted immigration overhaul, insisting that the focus be first on enforcing current laws. The Hispanic Caucus contends that a broad overhaul is needed and that legislation exempting returning foreign workers from the cap on visas should be part of it. “I recognize that H-2B visa fixes are an important part of the immigration crisis,” said Representative Joe Baca, Democrat of California and chairman of the Hispanic Caucus. “But that should be just another check mark in the column as to why this Congress must take real action on immigration reform.” A bipartisan coalition of 182 members of Congress has co-sponsored measures sponsored by Representative Bart Stupak, Democrat of Michigan, and Senator Barbara A. Mikulski, Democrat of Maryland, that would allow returning workers back. “The H-2B visa program is being held hostage,” said Representative Bill Delahunt, a Democrat who represents Cape Cod. “We’re talking about a stimulus package, and yet we’re putting at risk regional economies from the East Coast to the West Coast and many sections of the country in between.” Representative Charles Boustany Jr., Republican of Louisiana, has introduced a measure that calls for immediate consideration of Mr. Stupak’s bill. Congressional aides involved in the negotiations over the measure said Democratic leaders were discussing a compromise measure with the Hispanic Caucus and others. Some advocates for business owners argue that employers who go to the trouble of hiring legal employees are being unfairly punished. “It’s kind of sad that those who have followed the law, paid an inordinate amount of money to follow the law by paying attorneys’ fees, prevailing wage and following the rules, are those who are getting hurt,” said Don Mooers, an immigration lawyer working with Save Small Businesses, a group of small business owners lobbying for the cap to be lifted. “I get that question every day, ‘Why are we following the law when the guy down the street isn’t, and I’m the one who may face going out of business,’ ” Mr. Mooers said Here on Cape Cod, the need for imported seasonal labor is especially acute, as 25 percent of residents are over 65 and high real estate prices have driven many blue-collar workers elsewhere. “We have a very old population, twice the national average of people on Medicare and we’re losing population to other parts of the country because of our affordable housing problem,” said Wendy Northcross, chief executive of the Cape Cod Chamber of Commerce. “We’re losing the population that could potentially take some of our seasonal jobs.” D. J. Vander Silk, owner of D. J.’s Lawn Service in Grand Rapids, Mich., said he had planned to hire 30 workers from Mexico on temporary seasonal visas, but will not get any. “I feel like we’re right on the edge,” he said. “There’s a robber outside the house and we’re about to get hit in the head.” Now Mr. Vander Silk and his 20 remaining employees are not accepting new clients and are trying to recruit workers from Florida and the local community. The homes he bought a few years ago to shelter the temporary workers will remain empty for the near future. “We’re in uncharted waters,” he said. Sandy Munley, executive director of the Ohio Landscape Association, said the industry employed about 3,000 H-2B workers in Ohio last year, and did not know how many would return. Many contractors are giving away jobs to businesses with adequate staffing, Ms. Munley said. “This industry tends to be very supportive of each other,” she said, “but I don’t think anything’s ever come to this degree, where people are giving away work. Typically, contractors tend to get it done, but they all definitely say this is historic in a sad way.” Jim Royal, who operates Kelly Miller Circuses, said he could not find employees to assemble big tops for his traveling circus. He usually relies on 25 H-2B workers from Mexico. “It’s affecting virtually every circus in America,” Mr. Royal said. “We’re still on hold. We’ve applied and haven’t gotten anything. We’re trying desperately to recruit, but the artists will probably have to help out.” http://www.nytimes.com/2008/03/14/us/14visa.html?hp  Stories From a World in Motion A. O. Scott IT seems fair to say that in the world today there are not many stories bigger or more complicated than the movement of large groups of people from one country to another. And yet, perhaps because it is so vast and complex, it is a story that can be comprehended only in its fine-grained, human particulars. A timeworn piece of Hollywood wisdom (occasionally attributed to Dostoevsky, John Gardner or some other writer) holds that every narrative arises from one of two situations: Someone goes on a journey, or a stranger comes to town. The immigrant’s story, in its basic form, fulfills both of these archetypes. An individual or a family leaves a familiar world, by either choice, necessity or some perceived combination of the two, and arrives in a place that is as strange to the newcomers as they are to it. In the United States, Western Europe and other relatively wealthy parts of the world, immigration is currently a subject of raw political contention. As such, it is a topic that tends to be discussed both heatedly and somewhat abstractly. The debate is heavy with numbers: the millions of new arrivals; the estimated costs and benefits of allowing them in or trying to keep them out; the changing demographic profiles of neighborhoods, cities and regions. Hovering above these calculations are cultural anxieties and ideological conundrums that are, if anything, even more abstract: questions of assimilation and diversity, of security and cultural identity, of human rights and social obligations, of economic globalization and national sovereignty. Organizing all this argument and emotion into stories has become an especially acute and fruitful challenge. Of course, variations on the two-fold tale of departure and arrival have been a literary staple, especially in the United States, for more than a century. The wave of immigration, mainly from Eastern and Southern Europe, that began at the end of the 19th century and ended in 1925 has been, for subsequent generations, a wellspring of nostalgia, a way of connecting modern American lives with a more exotic history in the old country or the old neighborhood. And since 1965, when new immigration laws began to bring in large numbers of new arrivals from Asia, South America and elsewhere, there has been a revival of this tradition. Every publishing season brings novels and memoirs that offer fresh variations on the apparently inexhaustible themes of displacement and relocation. But until recently these themes have never been quite as ubiquitous on movie screens. Though the American film industry was founded largely by enterprising immigrants and has been fed by successive streams of talented émigrés, Hollywood has generally preferred to depict an idealized, homogeneous America, where the nonwhite and the nonnative linger in the margins and the shadows. The exceptions have mainly been examples of the backward-looking, second-generation tradition, films like the “Godfather” cycle, an ambivalent epic of an Italian family’s incomplete Americanization, or “Fiddler on the Roof,” a sentimental journey back to the world of the Eastern European shtetl, from whence the grandparents and great-grandparents of so many American Jews had come. Knowing how the story ends — with Americans paging through their family albums, marveling at what their ancestors had been through — gives even the painful passages in stories like these a warm, soothing glow. Retrospect also helped make the experience look simpler than it may really have been and certainly simpler than what confronts the world now. Those films, and others like them, traced the passage from a premodern, peasant way of life into a modern world of cities, factories and social mobility. “Golden Door,” a recent film by Emanuele Crialese, an Italian director, re-enacts this transition in an especially stark and powerful way, bringing an extended family from a poor, rural corner of southern Italy up to the edge of New York City and leaving the viewer to imagine what the new arrivals find when they cross the threshold. The voyagers themselves, having been seduced by doctored postcards showing giant chickens and coins growing on bushes, cannot imagine what they will encounter, and Mr. Crialese succeeds in conveying the intense strangeness of their impending arrival. He tries, with some success, to overcome the comforting artifice of costume drama, to infuse history with the uncertainty of the present tense. Mr. Crialese also recalls an era when global communication relied on steamships and telegraphs and when differences of language and custom seemed more profound than they might today. “The Golden Door” uses the medium’s powers of empathy and estrangement — its capacity to bring about an intuitive recognition of an utterly alien human reality — to measure the enormous distance its characters travel. But in the present, the distances have shrunk. Movies that deal with migration in the modern world tend to emphasize the often disconcerting connections that seem to web the Earth and link people whether they are aware of the links or not. Their stories are, perhaps as a consequence, less linear, shuttling between places and times rather than moving irreversibly from one to the other. And the camera too crosses borders, traveling, perhaps with deceptive ease, from one country to another without necessarily coming to rest anywhere. In “La Misma Luna” (“Under the Same Moon”), a new film from the Mexican director Patricia Riggen, a young boy and his mother live on opposite sides of the United States-Mexico border, she in Los Angeles, he in the town she left when she moved North. In some ways, they live in different worlds, and Ms. Riggen takes note of the small, everyday details that distinguish one place from the other. But they are also connected by telecommunications and by the director’s narrative method, which cross-cuts between them as they move toward a possible reunion. Carlitos, the boy, sets out across the border, facing the hazards and hardships with disarming cheerfulness, while his mother, Rosario, contemplates a journey home, an escape from hard work and the constant fear of deportation as well as a chance to see Carlitos again. “La Misma Luna,” which is rated PG and was recently shown in the New York International Children’s Film Festival (it is set to open Wednesday ), is a gentle and accessible movie. Rosario’s life is hard, and her son encounters some serious danger, but the tone is adventurous and mildly melodramatic rather than harsh or upsetting. But Ms. Riggen’s narrative strategy is, in some ways, a simplified version of the multistranded storytelling found in movies like “Babel” or “Fast Food Nation.” Neither of those movies, both of which came out around the same time in 2006 (after having their premieres at that year’s Cannes Film Festival), is, strictly speaking, an immigrant tale, but both take the global flow of people and information as a theme and a plotline. And they, like “La Misma Luna,” take pains to point out that inequality and exploitation, along with isolation and estrangement, are features of the global economy. They offer an implicit critique of the optimistic, tolerant multiculturalism that has become a central feature of modern American ideology: a more fatalistic sense of contradiction and complication. Something similar — a feeling that migration is the symptom of a large-scale social crisis rather than the individual solution to an economic or political problem — arises in many of the European films that focus on the experiences of immigrants. In Europe, mass immigration is both a newer phenomenon than it is in the United States and also a source of more pronounced political tension. In some cases, the presence of large foreign-born populations tests traditions of liberalism and openness; in others, it brings up unresolved legacies of colonialism or extreme nationalism. And the stories told by French, Italian and German filmmakers — some of them immigrants or the children of immigrants from North Africa or the Middle East — reflect this unsettlement. But they also try to find within it a core of human reality, which may be the most complicating factor of all. A sense of stubborn individualism, which can’t be reduced to cultural identity or political abstraction, informs the films of the Tunisian-born French director Abdellatif Kechiche, whose three features so far (“La Faute à Voltaire,” “L’Esquive” and “La Graine et le Mulet”) are thick with idiosyncrasy and cultural complication. The same might be said of Fatih Akin, the German son of Turkish parents, whose films confound every imaginable cliché and assumption about Europe, Islam, community and desire. His new film, “The Edge of Heaven,” is a tale of crosshatched destinies in which the journey from Turkey to Germany is made and reversed several times. One of the characters is a professor of German literature who travels to Turkey, his father’s homeland but no longer really his own, and opens up a German bookstore. He is, perhaps, Mr. Akin’s surrogate in the film, but he is certainly its embodiment at once of cosmopolitanism and also of a pervasive cultural confusion — which may, in the end, be the same thing. “The Edge of Heaven” never comes to rest: there is no point of arrival, of assimilation to a new home or return to an old one. And “La Misma Luna,” a very different kind of movie in most ways, concludes on an image of irresolution, or continued perpetual motion. It tells an old story — one of the oldest — but one that never ends, except in the discovery, once again, of a new world. http://www.nytimes.com/2008/03/16/movies/16scot.html  For France, an All-Purpose Heartthrob Kristin Hohenadel PARIS DURING his brief but eye-catching career, the 24-year-old actor Louis Garrel has been cast as a love interest for young girls, older women and teenage boys, not to mention his own onscreen mother (“Ma Mère”) and sister (“The Dreamers”). “I’m a sexual object,” the tall, pale, dark-eyed Mr. Garrel said with a smile, taking a drag on his fifth Marlboro at a cafe in Saint-Germain-des-Prés. “It’s true that for me there’s something very sexual about the cinema. Not in the sense of the act, but of creating desire.” In his new film, “Love Songs,” directed by Christophe Honoré, Mr. Garrel plays Ismaël, caught in a ménage à trois with his girlfriend (Ludivine Sagnier) and colleague (Clotilde Hesme) as well as being the obsession of an ardent male student (Grégoire Leprince-Ringuet). His third film with Mr. Honoré, “Love Songs” is a modern musical about love and loss in which the characters break into song to express their emotions. Nominated for a Palme d’Or at last year’s Cannes Film Festival, it opens Friday in New York. Mr. Garrel is the youngest member of an esteemed French cinema clan that includes his grandfather, the actor Maurice Garrel, and his father, the director Philippe Garrel (who cast him as a 5-year-old in the 1989 film “Emergency Kisses”). His mother is the actress Brigitte Sy, and the actor Jean-Pierre Léaud is his godfather. Despite his brief foray into child acting, Mr. Garrel said he didn’t decide to become an actor until he was 15, inspired by François Truffaut’s landmark films about the adolescent Antoine Doinel, played by Mr. Léaud. “I wanted to have a life that resembled his,” he said of Doinel. “Léaud didn’t obey any laws of acting. He sends signs that are recognizable but that we’ve never seen. And that’s what I think it means to be an actor.” His first film role followed in Rodolphe Marconi’s “Ceci est mon corps” (“This Is My Body,” 2001) and he studied drama in Paris. But his recent work with Mr. Honoré has earned him a reputation as something of a 21st-century Doinel. “A lot of directors have a moment when they believe in an actor and that actor could be the character in all of their films,” said Mr. Honoré, who first cast him as the son of an incestuous mother (Isabelle Huppert) in his 2004 film “Ma Mère.” “It was a dark role,” Mr. Honoré said. “Off-camera he was lighter and more joyful, but with a certain melancholy, and I wanted to offer him something that would better correspond to his personality.” A gentler turn in “Dans Paris” followed in 2006, with “Love Songs” last year. “He has a very lyrical way of playing a role, like a character in a novel,” Mr. Honoré said, referring not just to his appealing singing style, demonstrated in “Love Songs.” “He seems to have escaped somehow from the 1960s but is totally of his time.” Mr. Honoré is now editing their fourth collaboration, “La Belle Personne.” “Even in the editing room, I’m surprised by what he does,” Mr. Honoré said. “I have the impression that my films resemble me more and more because of Louis.” Onscreen, Mr. Garrel bites his nails and smokes, charms and broods. On a gray afternoon in a Left Bank cafe, he seemed to have stepped straight off the screen. “It’s true I have a hard time with the notion of creating a character,” Mr. Garrel said. “And I feel it’s a limit. I’m always really impressed by actors who are able to construct a character, like Johnny Depp. Then again, an actor who gives a big performance, it’s always a little embarrassing, because he’s there saying, ‘Look at my performance.’ And that bothers me a lot.” Playing Ismaël, Mr. Garrel said, he had in mind Yves Montand, as a man who befriends his rival for the same woman’s heart, in Claude Sautet’s 1972 film, “César et Rosalie.” “I’m crazy about Yves Montand,” he said. “You want to live like he does in the film, to be his friend. He has a certain rhythm — he’s always trying to cheer people up, to carry them along — and I thought Ismaël should be like that.” While shooting “Love Songs,” Mr. Garrel said, he did his best to forge real relationships with fellow cast members. “That’s how mystery is created,” he said. “I want the camera to be a bit like a voyeur. I like to say to myself that the film is a residue of a larger life.” Ms. Sagnier, his “Love Songs” co-star, said: “Louis really likes to share his energy. That’s very rare for an actor. The only bad part is that he also shares his anguish.” Mr. Honoré agreed that Mr. Garrel is “very inventive and spontaneous on set.” “But he’s also very much an intellectual who wants to master everything.” he added. “It’s hard for him that he’s not the one choosing the takes. He often calls me up late at night full of anguish, but after the fact.” Said Mr. Garrel: “I hope each day to have done 10 seconds of good work that they can use in the film. And I’m always afraid I didn’t get those 10 seconds.” He finds it painful to wait while a film is finished without him. But he’s not one of those actors who refuses to see the final product. “ ‘Love Songs’ is a very tender film,” he said. “I wasn’t watching myself and my faults. And that’s my goal. I want to take pleasure in watching the film.” Mr. Garrel won the French César for most promising male newcomer in 2006 for his role in “Regular Lovers,” his father’s film set during the May 1968 student protests in Paris, and has a taste for the ever more rarefied French cinéma d’auteur. It was the second time he’d participated in a movie about May 1968, after Bernardo Bertolucci’s “Dreamers,” his best-known film. His striking looks are also the stuff of fashion shoots and fan sites, and he routinely turns down work in more commercial films. “I like to be able to understand the feeling of the director,” he said, “that a film corresponds to something in his life. Otherwise, it doesn’t interest me much.” Mr. Garrel has recently completed a second film with his father, “La Frontière de l’Aube,” and is working on his own short film about a young man who feels that time is passing too quickly. “I don’t know how long I’ll live,” he said when asked what his own future may hold. “But I’d like to make communist films with Ken Loach, libertine films with Almodóvar, esoteric films with Kaurismaki. That’s not bad for a start.” http://www.nytimes.com/2008/03/16/movies/16hohe.html  Is Ben Stein the New Face of Creationism? Roger Moore  How do you re-package that tried, untested and untestable faith-without-facts warhorse, "Creationism" after its nearly-annual beat-down by an increasingly exasperated scientific community? After you've tried renaming it "Intelligent Design," I mean. With comedy. Mock your "Darwinist" foes the way comics, thinkers, scientists and educated people everywhere have been mocking creationism since Scopes took that monkey off our back. Tuck into them the way Michael Moore would, with a documentary hosted by a funny Don Quixote willing to tilt at science the way MM has gone after the gun culture, corporate cold-heartedness, George W. Bush and Big Health Care. Get droll funnyman and ex-Nixon speech writer Ben Stein to host it, to be the on-camera jester-interviewer. And re-cast this argument about what people chose to believe vs. what others can prove as fact as a fight for "Freedom." That's the mnemonic device Stein came back to, time and again, last night in an Orlando screening of his new documentary, Expelled: No Intelligence Allowed. It's a rabble-rouser of a doc that uses all manner of loaded images, loaded rhetoric, few if any facts and mockery of hand-picked "weirdo" scientists to attack those who, Stein claims, are stifling the Religious Right's efforts to inject intelligent design into science courses, science curricula and the national debate. He was showing the movie to what he and the producers hoped would be a friendly, receptive audience of conservative Christian ministers at a conference at the Northland mega-church next to the dog track up in Longwood. They're marketing this movie, which they had said, earlier, they'd open in Feb. (now April) the same way other studios pitched The Passion of the Christ and The Chronicles of Narnia, said Paul Lauer of Motive Entertainment, who introduced Stein. In other words, a stealth campaign, out of the public eye, preaching to the choir to get the word out about the movie without anyone who isn't a true believer passing a discouraging judgment on it. Friendly words in the press only. They postered the Orlando Sentinel with email invitations, then tried to withdraw the one they sent to me. No dice. They also passed out non-disclosure "statement of confidentiality" agreements for people to sign. I didn't. What are they hiding from you? Straight propaganda, to be sure. But again, if Michael Moore or Robert Greenwald can do it, why not Ben Stein? It's a movie that uses animation, archival documentary footage, interviews with outraged "people of science" who want ID on the table, and "atheists" (scientists) who see all this as a step backward, all freighted to back up the argument that it stifled "freedom" when you refuse to consider the work of a supernatural being in America's science classes. It just isn't particularly funny. Or the least bit convincing. I lost track of the number of times Stalin's image hit the screen, and in the ways the movie equated science with Darwinism with atheism with Hitler or Stalin. Subtle, it's not. Stein (he co-wrote it) builds his movie on classic Big Tobacco Tactics. Create just a sliver of doubt about evolution by pitching this argument in terms of academic freedom. "Legitimate" learned scientists are being silenced by the Darwinian cabal of thought police. Says Stein. He uses anecdotes from a few Fox-over-publicized cases of people who claim to have lost tenure/their jobs/their position in the scientific world for daring to suggest the hand of a supernatural being in the creation of life. He hasn't a scintilla of proof of, well, anything. Then he has the audacity to whine, "Where's the data" when questioning cellular biologists and other real scientists who build their lives around doubt, and finding testable, legitimate answers to those doubts. Where's YOUR data, Ben? He uses "straw man" tactics to attack, mainly The Origin of the Species, as Darwin wrote it in 1859. That's like a music critic reviewing "the latest" by only referring to Edison's wax cylinders. He sets up false theses that "the other side" must hold (classic Limbaugh, putting lies in the other fellow's mouth, then calling him a liar) and knocks those straw men down. Citing scientific research as recent as 1953, he can't understand why no peer-reviewed scientist thinks his "fairytale" version of the emergence of life is worth his or her time. No, not having a definitive answer about the moment life began...YET...is damning enough for Ben. Most despicably, Stein, a Jew, invokes the Holocaust, making the Hitler-was-a-Darwinist argument, this AFTER he's used the Holocaust denier's favorite trick, probabilities, "math," to show how remote the chances are that life was created by natural, not supernatural processes. There were plenty of reasons eugenics caught on as an idea among certain nationalist-conservative and even scientific circles in the early 20th century, and most of them have nothing to do with Darwin. It reminded me of the phony slump Michael Moore showed walking away from ambushing crusty old Charlton Heston in Bowling for Columbine. Animation, similar to that used in Columbine, makes its mock points about how science comes to conclusions and how the culture is structured to accept them. Snippets of The Wizard of Oz, Inherit the Wind and other films (if this polished, credited, scored film is indeed "unfinished," it may be from unresolved rights-clearance issues) to make his points funny. Not really. The Stalin and Soviet and Nazi clips are used in a not-quite-subliminal seduction way to demonize the people who might hold a contrary view. But all the creative editing in the world only appears to let Stein hold his own with noted British scientist and atheist Richard Dawkins, whose words can be twisted to suggest that "aliens" seeded life on Earth, or at least that's more likely than anything in the Bible being literally true about creation. That's still a more rational explanation than any Stein, being a veteran Republican persuader/operator, offers. Does he really believe the blather he tosses out here? Introducing the movie at the church screening I attended, he had to trot out some nonsense about living in Malibu but not among "the stars. The REAL stars are fighting and dying for our freedom in Iraq and Afghanistan." Ok. Know your audience, if you're a speech-writer (He used to work in the Nixon White House). Pander, baby, pander. I remember stumbling across, at a bookstore, one of the more shrill and lunatic "Bill Clinton had people KILLED in Arkansas" books that came out during the 90s. I open it at the B. Dalton, and lo and behold, there's Ben Stein writing the foreward. I had no idea... Before that, he was just the guy giving away money on Comedy Central, the ever-droning teacher of TV shows and movies ("Bueller. Bueller."). The PBS NOVA series did a terrific piece on the court battle over intelligent design as fought in the courts in Pennsylvania, a lacerating film of finely honed facts and dagger-sharp arguments that should be shown in every school district with intel. design-dreamers running for the school board. ID is "creation science" is "creationism" is "God dun it." Teaching that as something provable beyond faith in a science curriculum is a big reason future Nobel winners will pour out of China and India, and not Kansas. Or Florida. That's the reason a consensus of the world's scientists fret so much over the time they have to waste on this non-debate. Stein found a Pole and the infamous Discovery Institute to back up his attacks, even though they offer no counter theories that they can back up. Expelled makes good points about academic freedom and the ways unpopular ideas are shouted down in academia, the press and the culture. But not offering evidence to back your side, where the burden of proof lies, makes the movie every bit as meaningless and silly as that transcendental metaphysical hooey of a couple of years back, What the Bleep Do We Know? In Stein's case, you really do wonder what he knows, or what he's willing to claim he believes just to make a buck off the Scopes deniers. Oh, and keeping your movie from the public because you're afraid of ridicule is just gutless. Put it out there, let people have time to chew on your arguments. Your fans will buy tickets. And plenty of folks will emerge to tear it apart. Even Michael Moore has the courage to do that. Maybe Stein will repackage himself as the new face of creationism. The new face of cynicism is more like it. But as Nixon must've reminded him, there's a sucker born every minute. And a lot of them vote. http://blogs.orlandosentinel.com/ent...-stein-th.html  Ten Years Old: the World's First MP3 Player Tony Smith Forgotten Tech The MP3 player is ten years old this month. The first commercially released personal music player capable of handling MP3 files was the MPMan F10, manufactured by Korea's Saehan Information Systems and launched in March 1998. The F10 contained 32MB of Flash storage, enough for a handful of songs encoded at 128Kb/s. It measured 91 x 70 x 165.5mm. It connected to an old-style parallel port on the host PC from which songs could be copied to the player. There was a tiny LCD on the front to give an indication as to what you were listening to. The device made its debut at the CeBIT show in Hannover, Germany. It was a prototype, but Saehan must have garnered enough interest to put the player into mass production, which it did in May 1998 before going on sale in the US and Europe through importers in the summer. In the US, local supplier Eiger Labs wanted $250 for the F10, though the price fell to $200 the following year prompted by the release of the Diamond Multimedia Rio PMP300, which was priced at $200. The PMP300 - widely but wrongly held to be the world's first commercial MP3 player - also had 32MB of storage fed through a parallel port. But it boasted a larger display than the F10 and also featured a Smart Media slot to allow users to increase the gadget's storage capacity. The Rio was released in September 1998, but by 8 October had become the subject of a lawsuit from the Recording Industry Ass. of America (RIAA), which claimed the player violated the 1992 US Home Recordings Act. By that point, Rio had already teamed up with MP3.com to offer songs from the website. The RIAA asked for a sales ban, and got one on a temporary basis on 16 October, only to have it withdrawn on 26 October. In December, Rio countersued the RIAA, claiming the organisations actions were an attempt to impede the growth of a market - digital music - which it didn't control. It was later ruled that Diamond had not infringed the Act because it was not responsible for the actions of its customers. The RIAA appealed against the verdict, but lost there too: the Court judged that the PMP300 was not a recording device and so did not fall within the boundaries of the Act. The RIAA and Diamond would eventually settle their differences in August 1999, but by then Rio was a household name, especially among internet users busily sharing MP3 music on the internet using newly created peer-to-peer (P2P) file-sharing software. Thanks to its lesser known name, the F10 avoided such legal entanglements, but at the cost of all the free publicity its rival gained through from the lawsuit. Saehan soon established MPMan as a sub-division, and as such it later appeared among the roster of members joining the Secure Digital Music Initiative (SDMI), an cross-industry attempt to develop a universal digital rights management (DRM) technology. SDMI ran out of steam in 2001, largely because of a highly publicised cracking of its encryption technology, leaving the way open for Microsoft's Windows Media DRM technology to fill the gap. And it might have done if Apple's release of the iPod in the October of that year hadn't proved ultimately so successful. In the interim, MPMan had continued developing and offering MP3 players, but Apple's move to allow Windows PC owners to use the iPod, from April 2003, resulted in explosive growth. MPMan, Rio and other pioneers couldn't keep up. http://www.reghardware.co.uk/2008/03...st_mp3_player/  Intel Confirms 160GB Solid-State Drives Will be Unveiled Soon Brian Fonseca Intel Corp. today confirmed that it is close to unveiling a new line of solid-state drives for laptop and notebook PCs that will feature a storage capacity up to 160GB. An Intel spokesman said that the chip maker will introduce 1.8-in. and 2.5-in. solid-state drives offering between 80GB and 160GB diskless storage during the second quarter of 2008. The spokesman declined to provide further details about the ship date or disclose the storage density of the drives. Intel had demonstrated the high-performance solid-state drive prototype at the Consumer Electronics Show in Las Vegas earlier this year. At the time, an Intel spokesman said the manufacturer had not decided whether to sell the drives directly to retailers or through laptop and PC makers. The spokesman said in January that the solid-state technology would be shown again in April at the Intel Developer Forum, where some observers said it may be officially released. Intel currently offers ultrasmall low-power solid-state storage offerings for mobile devices. These include the 2GB Z-P140 PATA and the 4GB Z-U130 USB offerings. The company has made no secret of its desire to significantly broaden its solid-state portfolio along with boosting flash performance for customers. Last month IM Flash Technologies, a joint venture of Intel and Micron Technology Inc., unveiled a new high-speed NAND flash memory technology that it said offers data transfer speeds that are five times faster than conventional NAND technology. An aggressive move into the laptop and PC notebook flash disk drive business would catapult Intel into direct competition with hard drive manufacturers such as Toshiba Corp. and Samsung Electronics Co. that are trying to spark demand before their SATA-based offerings are released in the coming months. Samsung said it will ship a 2.5-in. 128 solid-state drive in Q2 while Toshiba Corp. has announced plans to produce solid-state drives ranging in capacity from 32GB to 128GB for notebook PCs by May. Although analysts do expect that corporations will begin to seriously consider the benefits of solid-state drives during 2008, the high price tag for the technology may keep sales in check for a few years. http://www.computerworld.com/action/...tsrc =hm_list  Ericsson Predicts Swift End for Wi-Fi Hotspots Stuart Turton The rapid growth of mobile broadband is set to make Wi-Fi hotspots irrelevant, according to an Ericsson executive. "Hotspots at places like Starbucks are becoming the telephone boxes of the broadband era," claimed Ericsson's chief marketing officer Johan Bergendahl, speaking to delegates at the European Computer Audit, Control and Security Conference in Stockholm. "In Austria they are saying that mobile broadband will pass fixed broadband this year. It's already growing faster, and in Sweden, the most popular phone is a USB modem," Bergendahl claimed, according to ComputerWorld. Bergendahl pointed to a couple of significant factors in the future growth of mobile broadband, including the price, which is as low as 20 euros per month in Austria, Denmark and Sweden. He also highlighted the increasing tendency of manufacturers to build High Speed Packet Access (HSPA) into their laptops, pointing specifically to Lenovo, which uses Ericsson's HSPA technology. However, he admitted challenges remain for mobile broadband. "Industry will have to solve the international roaming issue," he said. "Carriers need to work together. It can be as simple as paying 10 euros per day when you are abroad." He also pointed to a lack of coverage as a potential hindrance to the growth of the technology. http://www.pcpro.co.uk/news/176220/e...-hotspots.html  Gates Urges U.S. to Free up More Spectrum for Wi-Fi Peter Kaplan Microsoft Corp co-founder Bill Gates urged U.S. communications regulators on Thursday to free up more vacant television airwaves to be used for wireless services such as broadband Internet access. During an appearance before a Northern Virginia technology group, Gates said the so-called "white space" spectrum between analog broadcast channels could be used to expand access of wireless broadband service using Wi-Fi technology. "We're hopeful that that will be made available so that Wi-Fi can explode in terms of its usage, even out into some of these less dense areas (of the United States) where distance has been a big problem for Wi-Fi," Gates said in response to a question from the audience. Microsoft is part of a coalition of technology companies that has been lobbying the U.S. Federal Communications Commission to allow unlicensed use of white space spectrum. The group also includes Google Inc, Dell, Intel Corp, Hewlett-Packard Co and the north American unit of Philips Electronics. However, the idea is opposed by U.S. broadcasters and makers of wireless microphones, who fear the devices would cause interference. "Broadband penetration could be drastically improved through a fixed, licensed service without interference to TV reception. Unfortunately, Microsoft continues to push for an unlicensed technology that simply does not work," said Dennis Wharton, a spokesman for the National Association of Broadcasters. "TV viewers should not be inundated by the inevitable interference caused by such faulty devices," Wharton said. A proposal being studied by the FCC would create two categories of users for the airwaves: one for low-power, personal, portable devices like Wi-Fi and a second group for fixed commercial operations. The proposal would require that the devices include technology to identify unused spectrum and avoid interference. The FCC currently is testing prototype devices to see if they can make use of the white space spectrum without interfering with TV broadcasts. Also appearing with Gates was Craig Mundie, Microsoft's chief research and strategy officer, who said a shortage of spectrum could hurt U.S. competitiveness. He said past decisions have not made enough spectrum available. "White space activity today is sort of our last hope to get some good spectrum," Mundie said. (Reporting by Peter Kaplan; Editing by Tim Dobbyn) http://www.reuters.com/article/techn...32446720080313  Wireless Networks That Build Themselves From traffic lights to mobile phones, small computers are all around us. Enabling these ‘embedded systems’ to create wireless communications networks automatically will have profound effects in areas from emergency management to healthcare and traffic control. Networks of mobile sensors and other small electronic devices have huge potential. Applications include emergency management, security, helping vulnerable people to live independently, traffic control, warehouse management, and environmental monitoring. One scenario investigated by European researchers was a road-tunnel fire. With fixed communications destroyed and the tunnel full of smoke, emergency crews would normally struggle to locate the seat of the blaze and people trapped in the tunnel. Wireless sensors could cut through the chaos by providing the incident control room with information on visibility, temperatures, and the locations of vehicles and people. Firefighters inside the tunnel could then receive maps and instructions through handheld terminals or helmet-mounted displays. For this vision to become reality, mobile devices have to be capable of forming self-organising wireless networks spanning a wide variety of communications technologies. Developing software tools to make this possible was the task of the RUNES project. Intelligent networking ‘Ad-hoc’ mobile networks are very different from the wireless computer networks in homes and offices, explains Dr Lesley Hanna, a consultant and dissemination manager for RUNES. Without a human administrator, an ad-hoc network must assemble itself from any devices that happen to be nearby, and adapt as devices move in and out of wireless range. And where office networks use powerful computers with separate routers, the building blocks of ad-hoc mobile networks are low-power devices that must do their own wireless routing, forwarding signals from other devices that would otherwise be out of radio range. A typical network could contain tens or even hundreds of these ‘embedded systems’, ranging from handheld computers down to ‘motes’: tiny units each equipped with a sensor, a microcontroller and a radio that can be scattered around an area to be monitored. Other devices could be mounted at fixed points, carried by robots, or worn as ‘smart clothing’ or ‘body area networks’. Wireless standards are not the issue: most mobile devices use common protocols, such as GSM, Wi-Fi, Bluetooth and ZigBee. The real challenge, suggests Hanna, is to build self-managing networks that work reliably on a large scale, with a variety of operating systems and low-power consumption. Middleware and more The EU-funded RUNES (Reconfigurable Ubiquitous Networked Embedded Systems) covered 21 partners in nine countries. Although RUNES was led by Ericsson, it had an academic bias, with twice as many universities as industrial partners, and most of the resulting software is publicly available. RUNES set out to create middleware: software that bridges the gap between the operating systems used by the mobile sensor nodes, and high-level applications that make use of data from the sensors. RUNES middleware is modular and flexible, allowing programmers to create applications without having to know much about the detailed working of the network devices supplying the data. This also makes it easy to incorporate new kinds of mobile device, and to re-use applications. Interoperability was a challenge, partly because embedded systems themselves are so varied. At one end of the spectrum are powerful environments, such as Java, while at the other are simple systems designed for wireless sensors. For devices with small memories, RUNES developed middleware modules that can be uploaded, used to carry out specific tasks, and then overwritten. Project partners also worked on an operating system and a simulator. Contiki is an open-source operating system designed for networked, embedded systems with small amounts of memory. Simics, a simulator allowing large networks to be tested in ways that are impractical with real hardware, is commercially available from project partner Virtutech. Taking the plunge The tunnel fire scenario was valuable in demonstrating what networks of this kind can achieve. Using real sensor nodes, routers, gateways and robots developed during the project, a demonstration setup showed how, for instance, a robot router can manoeuvre itself to cover a gap in the network’s wireless coverage. “A lot of people have been looking at embedded systems networking, but so far there has been a reluctance to take the plunge commercially,” says Hanna. “RUNES’ open-source model is an excellent way to stimulate progress, and it should generate plenty of consultancy work for the academic partners.” Adapted from materials provided by ICT Results. http://www.sciencedaily.com/releases...0311200326.htm  IFPI Takes ISP to Court to Impose Music Piracy Filter enigmax The ‘Big Four’ record labels - EMI, Sony, Universal and Warner have started legal proceedings to force an ISP to end piracy on its network. The action, brought against Irish ISP, Eircom, is the first of its kind. Eircom is the largest Irish ISP. Today, the Big Four record labels have started legal proceedings which they hope will force Eircom to effectively end music piracy on its network. According to the Ireland.com report, this action is the first against an ISP, rather than individual file-sharers. Mr Justice Peter Kelly today admitted the proceedings at the court under the Copyright and Related Rights Acts 2000. It appears the labels are trying to get an order to effectively force Eircom to take responsibility for their customer’s actions by saying that it’s the ISP that is doing the ‘making available’ to the public, by facilitating the infringement. Eircom’s lawyers see if differently. They say that Eircom was “not on notice of specific illegal activity that infringed the rights of the companies”, adding that it was under no legal obligation to monitor traffic on its network. Willie Kavanagh, Managing Director of EMI records in Ireland said of Eircom: “with the greatest of respect” it was “well aware” that its customers used its networks to infringe copyrights “on a grand scale”. Previously, Eircom has refused to use any filtering technology to interfere with file-sharers, something the labels wish to address in this case too. It looks like the IFPI has shifted its focus from the individual filesharer to the ISPs. Last month, the IFPI won a court case in Denmark, and the ISP “Tele2″ was ordered to block all access to The Pirate Bay. Tele2 announced later that it will fight the decision. Banning illegal filesharing from their network, voluntary or not, is in the best interest of ISPs according to the IFPI: “Illegal P2P file-sharing may have helped drive broadband subscriptions in the past, yet today these activities, particularly in respect of movies, are hogging bandwidth,” they state. http://torrentfreak.com/ifpi-isp-mus...piracy-080310/  ‘IFPI Advertising’ Boosts Visitors To Blocked File-Sharing Site enigmax Last week a court ruled that Israel’s largest ISPs should block access to HttpShare, a BitTorrent and http hyperlink site. Thanks to what the owners call “IFPI advertising”, the site is now so busy they’ve had to upgrade their hardware. TorrentFreak caught up with them as they cracked open the champagne. Haifa District Court Judge, Gideo Ginat: “I order the respondents, that is Israeli internet service providers, to systematically block access to the illicit site, HttpShare, so that surfers cannot enter this site and utilize it in in order to impede upon the claimants’ copyrights.” In response, the site owners state: “According to Dutch law, sites providing external links allowing surfers to download movie, music, games and program are perfectly legal. Sites cannot store these illicit files on their internet servers, and that is precisely what we do not do. The site merely provides links to file sharing sites that host BitTorrent files or http downloads.” This fact doesn’t seem to have influenced the judge when he ordered the blocking of the site. Unfortunately for the IFPI, this block has achieved nothing other than boosting the popularity of the site - dozens of news outlets wrote about the block and the result so far is that visitors are now up to 70,000 a day. HTTPShare even had to get new hardware to cope with the demand - “Big Thanks to IFPI Advertising” says a note on the site. TorrentFreak caught up with admin ‘Andre’ to hear more: TF: Please tell us a little about the history leading directly to the creation of HTTPShare. HTTP: Before HTTPSHARE there was a warez site back in 2003 called ELICOMP.CO.IL. The site’s owner was Eli Amar. Eli had to join the army and could not continue running the site, however he met me and I agreed to fund the site and keep it running. The site indexed HTTP links on all sorts of servers, then we grew in size and developed a crawler which job was to track fast speed .torrent files. The crawler was added to the the site which made it even more popular. We created the VIP zone in which users get fast and direct links (min. 500KB/s) to cover the servers and the programmers cost. TF: When did your legal problems with the IFPI begin? HTTP: About 9 months ago, Eli got a package with IFPI prosecution documents, including a court order to shut down the site. Eli didn’t know what to do so he mailed the files to me and I canceled the domain and opened a new one - HTTPSHARE.COM. Then 150K of emails were sent to previous members telling them about the new site and it wasn’t long before search engines like Google and Yahoo picked us up. TF: Obviously changing the domain name and owner didn’t persuade the IFPI to leave you alone, so what happened next? HTTP: The IFPI kept sending sending emails demanding us to shutdown the site. I never did so because the site is legal, we do not upload illegal stuff to our server [do not host any infringing media], and what we are doing is not against the law of the country in which we are hosted [Netherlands]. TF: How did the ISP block come about? HTTP: After the IFPI understood that they are dealing with a new owner they asked the Israeli court to order the ISPs to block the “www.httpshare.com” domain. We all know that the legal system in Israel is corrupted and driven by money and power of the share holders. How can you accept such a ruling from a judge whose son was suspended from his job as a lawyer because of counterfeiting documents and money blackmail? TF: Why do you think you became an IFPI target? HTTP: We were a target of the IFPI and similar organizations even at the time of Elicomp. I think we were targeted because of the huge amount of bandwidth my site used while providing Direct external links. At that time the ISPs blocked us, but were then forced to unblock as a result of complaints from their subscribers. TF: What actions have you taken to try to counter the block? HTTP: For now we changed the IP of the server and released a program (browser) for the members that uses a server with 10 IP ranges so that it will be a lot more difficult to block it. Since we introduced the browser, the number of visitors has doubled. Also, thanks to the huge amount of publicity we got from the IFPI and sites like yours, we have added an English language forum to the site and translated the names of the forums to make the site easy to use. TF: Thanks for taking the time to speak with us. Suing individual users doesn’t work, bullying site owners doesn’t appear to be effective and ISP bans simply create more traffic and popularity for the target site. All this on top of reduced funding for chasing copyright infringers. So where next for the IFPI? http://torrentfreak.com/ifpi-adverti...raffic-080312/  Verizon Touts Smart P2P Software Marguerite Reardon A real-world Internet test reveals that "intelligent" routing of peer-to-peer traffic can drastically reduce network utilization and speed up downloads for subscribers, according to a new study. Verizon Communications, which participated in the study headed by researchers at Yale University, plans to release the data on Friday at the Distributed Computing Industry Association's P2P Market Conference in New York City. Using network topology data from Verizon and Telefonica, Yale University tested a software enhancement to the peer-to-peer protocol that it developed with software developer Pando Networks. What the researchers discovered was that when using the so-called P4P software they were able to reduce the impact of peer-to-peer traffic on Verizon's network by more than 50 percent. This is significant because peer-to-peer traffic makes up roughly half of all traffic traveling over Verizon's network. The P2P protocol, which is used to distribute large data files, works by requesting pieces of a single file from different hosts all over the Internet. The technology has become popular for distributing high-definition video. But applications that use P2P eat up a lot of bandwidth, which some service providers say is a problem. Cable operator Comcast has slowed down certain kinds of peer-to-peer traffic in an effort to manage its network. And Time Warner Cable is experimenting with a tiered usage model to deter people from sharing P2P files. Traditionally, the P2P protocol has requested bits and pieces of content randomly, without considering the physical location of the data. This often results in some pieces of the content traveling over long distances across the network. For example, a user in New Jersey downloading a movie might get some bits of the file from New York and others from China or California. The P4P software enhancements add intelligence to this process so that the bits are served from local hosts. Douglas Pasko is Verizon senior technologist and co-chair of the P4P Working Group, which was formed by Verizon, Pando Networks, and the university to develop P4P. He said that when the P4P software was used on the Verizon network it found that 58 percent of its peer-to-peer network traffic stayed local. Using regular P2P technology, only 6 percent of the traffic stayed local. Reducing the number of hops is key Pasko said that keeping the traffic local is important because every link that a bit passes through costs the operator something. This means that if a Fios subscriber in New Jersey can get bits of content from Verizon customers in New York City instead of getting them from Singapore or Taiwan, Verizon can save money. The key is reducing the number of routers or hops the traffic has to go through to get to its destination. On average, Pasko said that regular P2P traffic makes 5.5 hops to get its destination. Using the P4P protocol, those same files took an average of 0.89 hops. Reducing hops means that Verizon can cut its network costs. Exactly how much the company saves depends on the individual links, but Pasko said the savings are significant. Verizon broadband subscribers also saw a benefit when the P4P protocol was used. Customers using Verizon's all-fiber network called Fios saw movies downloading on average twice as fast as when they used the traditional P2P software. Some customers saw as much as a 6x improvement in download speeds, Pasko said. For customers on regular DSL service, the improvement in download speeds wasn't as great because these customers don't have high bandwidth connections anyway. This real-world field trial validates the value of P2P content providers working closely with Internet service providers to provide the most efficient service for customers, Pasko said. There are already 50 members in the DCIA's P4P Working Group, including some cable operators, such as Comcast, Cablevision, and Time Warner, he said. "We hope this shows that using P2P in an intelligent way can benefit everyone," he said. "It allows us to use fewer resources on our network and get better performance for our customers." http://www.news.com/8301-10784_3-989...l?tag=nefd.top  Video Road Hogs Stir Fear of Internet Traffic Jam Steve Lohr Caution: Heavy Internet traffic ahead. Delays possible. For months there has been a rising chorus of alarm about the surging growth in the amount of data flying across the Internet. The threat, according to some industry groups, analysts and researchers, stems mainly from the increasing visual richness of online communications and entertainment — video clips and movies, social networks and multiplayer games. Moving images, far more than words or sounds, are hefty rivers of digital bits as they traverse the Internet’s pipes and gateways, requiring, in industry parlance, more bandwidth. Last year, by one estimate, the video site YouTube, owned by Google, consumed as much bandwidth as the entire Internet did in 2000. In a widely cited report published last November, a research firm projected that user demand for the Internet could outpace network capacity by 2011. The title of a debate scheduled next month at a technology conference in Boston sums up the angst: “The End of the Internet?” But the Internet traffic surge represents more a looming challenge than an impending catastrophe. Even those most concerned are not predicting a lights-out Internet crash. An individual user, they say, would experience Internet clogging in the form of sluggish download speeds and frustration with data-heavy services that become much less useful or enjoyable. “The Internet doesn’t collapse, but there would be a growing class of stuff you just can’t do online,” said Johna Till Johnson, president of Nemertes Research, which predicted the bandwidth squeeze by 2011, anticipating that demand will grow by 100 percent or more a year. 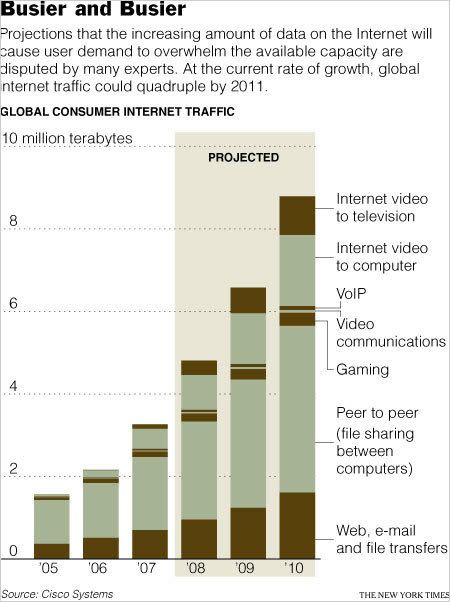 Others are less worried — at least in the short term. Andrew M. Odlyzko, a professor at the University of Minnesota, estimates that digital traffic on the global network is growing about 50 percent a year, in line with a recent analysis by Cisco Systems, the big network equipment maker. That sounds like a daunting rate of growth. Yet the technology for handling Internet traffic is advancing at an impressive pace as well. The router computers for relaying data get faster, fiber optic transmission gets better and software for juggling data packets gets smarter. “The 50 percent growth is high. It’s huge, but it basically corresponds to the improvements that technology is giving us,” said Professor Odlyzko, a former AT&T Labs researcher. Demand is not likely to overwhelm the Internet, he said. The question of the problem’s severity is more than a technical one, since it will affect the shape and cost of the nation’s policy on broadband infrastructure, a matter that is expected to attract political attention after a new administration takes over in Washington. While experts debate the immediacy of the challenge, they agree that it points to a larger issue. In the Internet era, they say, high-speed networks are increasingly the economic and scientific petri dishes of innovation, spawning new businesses, markets and jobs. If American investment lags behind, they warn, the nation risks losing competitiveness to countries that are making the move to higher-speed Internet access a priority. “The long-term issue is where innovation happens,” Professor Odlyzko said. “Where will the next Google, YouTube, eBay or Amazon come from?” The Internet, though a global network, is in many ways surprisingly local. It is a vast amalgam of smaller networks, all linked together. The worries about digital traffic congestion are not really about the Internet’s main trunk lines, the equivalent of network superhighways. Instead, the problem is close to home — the capacity of neighborhood switches, routers and pipes into a house. The cost of stringing high-speed optical fiber to a home, analysts estimate, can be $1,000 or more. That is why Internet access speeds vary so much country by country. They depend on local patterns of corporate investment and government subsidy. Frederick J. Baker, a research fellow at Cisco, was attending a professional conference last month in Taiwan where Internet access is more than twice as fast and costs far less than his premium “high speed” service in California. “When I mention my own service, people here shake their heads in disbelief,” said Mr. Baker, who is a board member of the Internet Society, a nonprofit organization that helps guide Internet standards and policy. In the United States, the investment required to cope with rising Internet traffic will need to be made at several levels, not just cable and telecommunications carriers. Tim Pozar, an engineer and a co-owner of the Internet services company UnitedLayer in San Francisco, said a number of forces were combining: the surge in bandwidth-hungry video applications on Web sites, the need to handle traffic from more Internet-enabled devices like cellphones, and shortages of electrical power for data centers in places like San Francisco. “We’re running out of horsepower to accommodate the demand,” said Mr. Pozar, whose company’s data centers support Web sites for customers ranging from museums to social networks. “And upgrades needed in data centers are going to be a lot more expensive than in the past, now that all the excess capacity left over after the dot-com bubble burst has been gobbled up.” The pace of future demand is the big uncertainty surrounding the Internet traffic challenge, and how fast people will adopt emerging technologies is notoriously difficult to foresee. In the aftermath of the bursting of the technology bubble in 2000, there was a glut of capacity — so-called dark fiber, strung around the world and then left dormant. Now demand is catching up with that supply. In its prediction of more than 100 percent annual growth, Nemertes, a telecommunications research firm, assumes brisk use of new innovations like high-end videoconferencing, known as telepresence, which corporations are beginning to embrace as an alternative to costly, time-consuming travel. If this technology becomes a consumer product in the next few years, as some analysts predict, Internet traffic could spike even more sharply. Slick video chats are something that William Bentley, a 13-year-old New Yorker, would like to see. He is fairly representative of the next generation of digital consumer: He has made and posted his own YouTube videos, subscribes to YouTube channels, enjoys multiplayer games like World of Warcraft and Unreal Tournament, and downloads music and videos. Asked what he would want next from the Internet, he replied, “It would be nice to have everybody always right there — just click and you could see them clearly and talk to them.” That sort of service is certainly going to require more bandwidth and more investment, with higher costs across the spectrum of the Internet ecosystem that includes cable and telecommunications carriers, Internet companies, media Web sites and even consumers. AT&T, for one, said last week that it would spend $1 billion this year — double its 2006 expenditures — to expand its overseas infrastructure. But even if investment lags behind, there will be no Internet blackout. Indeed, the Internet has survived predictions of collapse in the past, most notably by Robert M. Metcalfe, a networking pioneer and entrepreneur, who in a 1995 magazine column warned of a “catastrophic collapse” of the Internet in 1996. There were service problems, but nothing like Mr. Metcalfe predicted, and on stage at a conference in 1997 he ate his words. “The Internet has proven to be wonderfully resilient,” said Mr. Metcalfe, who is now a venture capitalist. “But the Internet is vulnerable today. It’s not that it will collapse, but that opportunities will be lost.” http://www.nytimes.com/2008/03/13/te.../13net.html?hp  YouTube Makes Video Sharing Easier Steve Johnson In a move likely to broaden its reach globally, YouTube today unveiled an easier way for people to share with the world the videos they create. The video-sharing subsidiary of Mountain View-based Google said it is providing free access to so-called Application Programmer Interfaces - or APIs as techies call them - that will let people greatly expand their use of YouTube on Web sites, cell phones and even video games. Previously, people could place the YouTube player on their personal Web sites and view videos from the YouTube library. But they had little control over how the videos were displayed on their sites and were unable to play videos they created themselves or send comments back to YouTube about what they had watched. Now, people will be able to customize the YouTube player, comment and send YouTube the videos they make - all from their own Web sites and cell phones. Users even can share animated monsters they create on their personal computers. Redwood City-based Electronic Arts has already incorporated the advanced YouTube feature into its upcoming video game Spore, in which players design their own horrific creatures. As a result, gamers will be able to share images of their ogres with YouTube users everywhere when it hits stores in September. That ought to please Spore aficionados, according to Will Wright, an Electronic Arts vice president and designer. "By allowing players to seamlessly broadcast their experiences on YouTube, we're giving the community even more tools to easily create and share their content," he said in prepared comments that YouTube has posted on its Web site. The new service was offered in large part because many people want to put a personal touch on their video sharing, said Jim Patterson, YouTube's product manager. "Ultimately, they want to make it their own," he said. "They want to use it in ways you couldn't imagine." So how does YouTube benefit from the deal? Aside from noting that the new service should make YouTube accessible to a vast new audience worldwide, Patterson demurred on that point. "Trying to make money with the APIs now isn't our focus," he said. "We'll work that stuff out." In fact, one feature of the new service allows people to customize the way the YouTube video player appears on their own Web sites so it fits more with their sites' designs. That allows people to remove some of the YouTube identifiers that normally appear on the player. Still, a small company emblem will remain so everyone can tell it's YouTube's technology, Patterson said. Moreover, by letting people use the video-sharing service in ways they couldn't before, YouTube is likely to become much more widely used, he noted. As a result, "it does get the YouTube brand out there," he said. http://www.siliconvalley.com/news/ci_8549624  TiVo Expands its Reach with YouTube Videos David Lieberman TiVo (TIVO) and YouTube removed another brick from the wall separating computers and television sets on Wednesday with an agreement that will let consumers watch user-generated videos from the Google-owned (GOOG) website on their TVs. The deal will provide TiVo with a vast reservoir of clips. YouTube accounts for about a third of all videos streamed on the Internet. TiVo hopes that will enhance its drive to market itself as a premium digital video recorder service vs. the fast-growing and less-expensive alternatives offered by cable and satellite providers. "TiVo's the only company that allows you to record (conventional) television and pull up broadband video with one menu and one search," says Tara Maitra, vice president of content services. YouTube says that the agreement is one example of how it plans to expand its reach. "This is part of a broader goal to bring YouTube everywhere," says Jim Patterson, YouTube product manager. Although the companies wouldn't disclose financial details, YouTube says that no ads initially will appear in or next to its clips when they run on TiVo. That makes it different from services such as Apple TV that send websites to televisions. TiVo's Maitra says that "we never pay" to license programming. Patterson says it's just a coincidence that the announcement of the plan to bring YouTube to televisions via TiVo came out the same day as the official launch of Hulu.com. That site, backed by NBC Universal and News Corp., brings TV shows to the Web. Although the TiVo-YouTube agreement illustrates where television is headed, it will take awhile before it affects many viewers. The DVR pioneer says it will offer YouTube "later this year." Maitra says it likely will be "closer to the middle than the end." The service will be available only to TiVo subscribers who have broadband Internet connections to its high-definition digital video recorders. TiVo says that it took awhile to develop a process to handle YouTube videos, and technological problems still prevent it from offering the clips to most of its 3.9 million DVRs, most of which aren't high-def. TiVo won't say how many customers initially will be able to use its YouTube service. "Search was a cumbersome process to solve," Maitra says. The user interface will be "a combination of the TiVo aesthetic with the YouTube functionality." Videos will be streamed, and users won't be able to record them on their DVRs. The companies are developing plans to integrate YouTube with TiVo's KidZone service, which lets parents prevent children from watching violent or risqué shows. http://www.usatoday.com/money/media/...e-videos_N.htm  BBC 'Opens Floodgates' to iPlayer Hackers Bobbie Johnson • Anti-piracy breach allows unrestricted downloads • Corporation says it is working to close loophole Hackers have managed to circumvent the BBC's anti-piracy systems to gain unrestricted access to the programmes on the corporation's iPlayer internet TV service. The loophole potentially allows millions of people to download television shows on to their computers without any copyright protection. The iPlayer system, which lets surfers watch BBC videos online in a similar way to websites such as YouTube, has proved massively popular since it launched late last year. Shows such as Top Gear and Doctor Who can be watched over the web or downloaded to a computer for viewing at a later point. When developing the iPlayer, however, the BBC agreed to include anti-piracy measures in all programmes in order to appease TV production companies and broadcasting unions. The addition of so-called digital rights management (DRM) software means new shows disappear from the website after one week, and files downloaded on to a computer have a 30-day expiry date. After the limit is reached, the videos are no longer viewable. However, the backdoor in the iPlayer allows users to completely bypass those protections and download unprotected versions of any show on the website. One of the hackers responsible said it took him only 12 minutes to find the loophole and make it work - but that such a simple hack potentially opened up every programme on iPlayer for unlimited downloading. "The BBC accidentally opened the floodgates and gave the world DRM-free downloads," said one hacker with knowledge of the breach. "If only it were down to something other than poor design, decisions and ineptitude." The BBC said the system was still in its trial phase, known as "beta", and that it was already working to come up with a solution. "This is not unusual or surprising," said a BBC spokeswoman. "We have made it clear the BBC iPlayer on iPhone and iTouch is currently in beta, which enables us to pick up on such issues and find a solution before we roll the service out in full in due course." The iPlayer was launched last year at a cost of several million pounds, and initial reaction to the download service was modest. But the ability to watch online - which was added last Christmas - has proved highly successful: the most recent figures indicate that programmes were viewed more than 17m times between December 25 and mid-February. However, the decision to incorporate anti-piracy protections has angered some campaigners, who believe that British citizens should have unprotected access to shows for which they have already paid with their TV licence fee. http://www.guardian.co.uk/technology...deo.television  Report: DVR Could Turn Apple TV Into Multi-Billion Dollar Business Katie Marsal By integrating digital video recording (DVR) features into Apple TV, Apple stands to transform it's niche media hub business into a serious growth driver worth over a billion dollars annually, according to one Wall Street analyst. Reacting to a patent filing uncovered by AppleInsider on Thursday, American Technology Research analyst Shaw Wu said he sees DVR features like those portrayed in the filing cropping up in a third or fourth revision to Apple TV, turning the device into a real business rather than just a "hobby." "We estimate AppleTV to be a very minor contributor today at ~0.3-0.4 percent of revenue or $100-125 million annually," he wrote in a note to clients. "We believe adding the ability to watch and record live TV could turn this into a billion dollar, if not multi-billion dollar business." Wu said the cost of hardware components needed to equip the media box with DVR features is almost negligible, or about $12-15 in incremental cost per unit. "We (as well as many others) have been clamoring for DVR and/or TV tuner capabilities since the introduction of Apple TV 1.0 in January 2007 and even Apple TV 2.0 with movie rentals in January 2008," he added. "We are pleased to see Apple listening to customers similar to what it has done with iPhone, with adding native access to Exchange server." The analyst, however, took pause in his report to note that there have been patent filings from Apple in the past that have not come to fruition "yet." One example, he said, is Bluetooth stereo headsets which have yet to ship but "will at some point as cost of components decline." Separately, he cited his own sources as saying that Apple and Sony appear to be in the final negotiation stages of bringing Blu-ray to Macs. "Thus while near-term trends look difficult with a looming recession and a slow-down in consumer spending, we continue to believe Apple is well-positioned to weather the storm better than most with its strong fundamentals," he wrote. "[We] reiterate [our] BUY rating and price target of $175." http://www.appleinsider.com/articles...us iness.html  Wal-Mart Ends Test Run for Linux Operating System Computers in Stores Computers that run the Linux operating system instead of Microsoft Corp.'s Windows didn't attract enough attention from Wal-Mart customers, and the chain has stopped selling them in stores, a spokeswoman said Monday. "This really wasn't what our customers were looking for," said Wal-Mart Stores Inc. spokeswoman Melissa O'Brien. To test demand for systems with the open-source operating system, Wal-Mart stocked the $199 "Green gPC," made by Everex of Taiwan, in about 600 stores starting late in October. Walmart.com, the chain's e-commerce site, had sold Linux-based computers before and will continue selling the gPC. This was the first time they appeared on retail shelves. Paul Kim, brand manager for Everex, said selling the gPC online was "significantly more effective" than selling it in stores. Wal-Mart sold out the in-store gPC inventory but decided not to restock, O'Brien said. The company does not reveal sales figures for individual items. Walmart.com now carries an updated version, the gPC2, also for $199, without a monitor. The site also sells a tiny Linux-driven laptop, the Everex CloudBook, for $399. Linux software is maintained and developed by individuals and companies around the world on an "open source" basis, meaning that everyone has access to the software's blueprints and can modify them. There is no licensing fee for Linux, which helps keeps the cost of the Everex PC low. Manufacturers have to pay Microsoft to sell computers with Windows preloaded. Linux is in widespread use in server computers, but it hasn't made a dent in the desktop market. Surveys usually put its share of that market around one per cent, far behind Windows and Apple Inc.'s OS X. Smaller laptops like the CloudBook could provide an entree for Linux, since it runs well on systems with modest memory and hard drive capacity. http://canadianpress.google.com/arti...C7J5MQLVJxp5HA  Testing Over, Hulu.com to Open Its TV and Film Offerings This Week Brad Stone Hulu.com, the long-gestating Internet joint venture between NBC Universal and Fox, emerges from limited testing on Wednesday to make its catalog of TV shows and video clips available to anyone on the Web. The streaming-video site displays free, ad-supported shows and feature films from NBC, Fox and more than 50 media companies, including Sony Pictures and Metro-Goldwyn-Mayer. On Wednesday, Hulu is also planning to announce that the Warner Brothers Television Group and Lionsgate will add content from their libraries. Hulu will also give sports fans highlights from N.B.A. and N.H.L. games, and full-length N.C.A.A. men’s basketball games from the last 25 years, the company said. Hulu’s videos also appear on AOL, MSN, Comcast, MySpace and Yahoo. Over 5,000 Web sites have embedded clips from Hulu, the company said. Hulu has so far failed to recruit two major television networks, ABC, a division of Walt Disney, and CBS. Jason Kilar, Hulu’s chief executive, said that he was still having regular conversations with executives at the two networks. But even without them, he said, the company has quadrupled the number of show titles in its library since testing began. “We won’t stop until we have everything in terms of premium content. That is our mission,” he said. “I just think back to the fact that 24 months ago, there wasn’t anything online legally in terms of full TV episodes or films. In just 17 weeks, we have gone from nothing to over 200 premium titles.” NBC Universal, a division of General Electric, and Fox, a division of the News Corporation, announced their joint venture to much fanfare nearly a year ago. The then-unnamed company was at first viewed skeptically by many in the industry as a desperate attempt to keep up with the Google’s YouTube, the dominant player in online video. Recently, Hulu has received high marks from media and Web executives for creating an easy to use site with high-quality video and professional content attractive to advertisers. Hulu has been in a password-protected testing period since October, but has slowly been inviting users to enter the site. Mr. Kilar said that more than five million viewers have watched Hulu videos in the last 30 days, and that 80 percent of the shows on the site are viewed at least once a week. Hulu is experimenting with giving viewers a choice in advertising. During certain shows, viewers will be able to choose which commercial they want to watch — for example, whether they want to see an ad for Nissan’s Rogue S.U.V., Maxima sedan or Z sports car. Some viewers will also be given the opportunity to watch a two-minute film preview before a TV show, and then skip all the other advertising breaks. One challenge Hulu faces is building a predictable and stable library of content. To protect DVD and Web download sales, media companies often make TV shows and films available free on the Web for certain periods of time and then remove them. For example, there are 11 episodes of the TV show “24” on Hulu — beginning with episode 18 of the first season. “If those episodes keep disappearing, they are going to have trouble getting people to go back and recommend TV shows on Hulu to their friends,” said Bobby Tulsiani, an analyst at JupiterResearch. http://www.nytimes.com/2008/03/11/bu...ia/11hulu.html  Sony Joins We7 to Make Music Free A new advertising-backed streaming service has signed its first major label Richard Wray and Owen Gibson We7, a free, advertising-supported online music service backed by Peter Gabriel, has become the first to claim the support of a major label, after Sony BMG, home to Mark Ronson, Bruce Springsteen and the Hoosiers, pledged to license its catalogue of more than 250,000 tracks to the company's new online music streaming service. The news comes as digital media group 24-7 Entertainment, which has built more than 40 online and mobile music services including Tesco's download site and a music portal for 3, prepares to launch an innovative unlimited music download service for a Nordic mobile and broadband provider, rumoured to be Denmark's TDC. It is also understood to be in talks with a number of UK internet service and mobile phone providers about a similar service. Meanwhile mobile phone operator O2, owned by Spain's Telefónica, will this week announce a deal with online music pioneer Napster. Vodafone is also understood to be in talks with the outfit. These moves making it easier for consumers to listen to and legally download music are the latest steps towards persuading consumers to stop illegally sharing and downloading tracks. They come as governments in Britain and France have warned that they will introduce legislation that demands internet service providers (ISPs) monitor what their users are doing if the tide of illegal file-sharing cannot be turned. The new service developed by 24-7, expected to launch next month, is a big step towards helping ISPs produce legal music services attractive enough for consumers that they will not resort to peer-to-peer sharing networks. The service, developed under the codename UMAP or unlimited music across all portals, will allow all mobile and broadband customers of the company unlimited access to music for no extra cost. They will not have to pay any subscription or fee above what they are already paying for their mobile or broadband service. Consumers will be able to download as many tracks as they want to their computers or mobile phones and keep them for as long as they remain a customer. The tracks are protected by digital rights management (DRM) technology, so they cannot be copied on to a CD or transferred to a standalone music device such as an iPod. The service will have well over a million tracks at launch, with 24-7 understood to have signed up EMI. Other major labels, including Universal and Warner, are also in talks with the company. "It will allow every customer of this company from day one to access music without any extra cost, whether they are a mobile or online customer," explained Frank Taubert, chief executive of 24-7 Entertainment. "It will be a major shift for the industry. "The music market is still looking at illegal downloads and peer-to-peer sharing and we all have to think about how we are going to shift these people over to legal services," he added. "Why would anyone want to download illegal tracks again if they can get everything for free legitimately?" For the company offering the service it provides another way of increasing customer loyalty and the amount it saves in consumer acquisition costs can be used to subsidise the "free" element of the service. The music companies get paid every time one of their tracks is downloaded. The industry will be watching, however, to see whether offering music at no extra cost to the consumer hits sales of digital downloads. The hope is that people who have up until now heard tracks they liked on the radio, downloaded them illegally, listened to them a few times and then moved on, will instead use the free service to download them legitimately. It remains to be seen, however, whether when these consumers decide that they like a track and want to keep it, they will return to using illegal sharing networks or pay for the track. Rather than rely upon an ISP or mobile company that already makes money from consumers to subsidise a free service, other digital music companies are looking to advertising to fund music. We7 already offers free music downloads. It attaches targeted adverts to a song for 30 days before they are removed by DRM software. The tracks provided to We7 by Sony BMG will be made available through a new streaming service that will allow users to build up playlists of songs they want to hear while they remain online. The label hopes people will sample new music before clicking through to a download store to buy it. Sony BMG UK chief executive Ged Doherty did not rule out also contributing tracks to We7's own download service but said the streaming service was a logical first step. The download service, which has deals with several independent labels, appends a short ad to the beginning of each song that remains in place when it is downloaded and transferred to a portable player. Acknowledging that the troubled music industry had previously been too slow to experiment with new revenue models, Doherty said the move was part of its "do and build" strategy. Sony BMG is in talks with a range of other ad-funded services, he added. We7, which launched last year, will initially offer the service to its existing members before rolling it out to new ones. It will pay royalties to Sony BMG for each song listened to. Gabriel, who has consistently been in the vanguard of the digital music business and previously had a hand in launching early download business OD2, said: "The digital revolution has produced exciting and extraordinary opportunities in the music business, even though it has been largely written off by many. We7 is a model that will supply free music to the consumer and still provide a stream of revenue to musicians and content owners." Chief executive Steve Purdham said the move was "a significant leap forward for We7 and the industry as a whole" and confirmed it was in talks with the other major labels. He dismissed concerns that an infinite jukebox of the kind envisaged by We7 would devalue music, saying it would become just one of several means of distributing music while ensuring artists and labels got paid. Doherty added: "What appealed to us about We7 is that they've quietly got on with business rather than making big promises. It's easy and user-friendly." A new model army: download and streaming devices Though Apple's iTunes hogs the headlines, the music industry is working with a host of online and mobile companies to try and persuade consumers to stop stealing music by offering a range of download and streaming services. All five of the UK's mobile phone networks have their own download stores and Vodafone has also signed up with UK-based MusicStation for an all-you-can-download subscription service, which costs £1.99 a week. Nokia has announced plans for a service called Comes With Music, to be launched this year, which will give users access to an unlimited number of music tracks that they get to keep forever, although only on their Nokia phones, according to reports. A host of retailers are selling track and album downloads - from online brands such as Play.com and Amazon to "bricks and mortar" players such as Tesco and HMV. Some of these stores recently started offering tracks in the open MP3 format, so they can be played on any device. Services such as Napster and Rhapsody, meanwhile, helped pioneer the subscription music model on the internet and Last.fm, which was snapped up last year by CBS, helped popularise streaming music services. Last.fm has agreed deals with the major labels to offer three free streams of any track before consumers have to buy it and US social-networking site Imeem also offers free streaming of any track. We7 is one of several attempts to launch advertising-funded download services, but many of its rivals are still battling through the rights-clearance process. SpiralFrog has launched in the US, with major label Universal on board, but Qtrax, which this year promised 25m tracks via a legal peer-to-peer service, has still to launch its download offering. http://www.guardian.co.uk/technology.../sony.netmusic  Apple Sued Over ITunes Technology AP Apple Inc. was sued Wednesday over allegations its iTunes online music store and iPod music players are illegally using a patented method for distributing digital media over the Internet. Atlanta-based ZapMedia Services Inc. sued Apple in U.S. District Court for the Eastern District of Texas, accusing the Cupertino-based company of violating two ZapMedia patents. ZapMedia wants royalties on Apple's sales of iPods and iTunes music, which reached nearly $11 billion last year. The success of iTunes has helped make Apple the No. 2 music retailer in the U.S. behind Wal-Mart Stores Inc., according to market researcher NPD Group. The patents in question cover a way of sending music and other digital content from servers to multiple media players, a broad description that could also apply to a wide swath of other companies selling digital media and the devices to play it. ZapMedia applied for the patents in 1999. One was granted in March 2006, the other on Tuesday. ZapMedia said it met with Apple to discuss licensing, but Apple rebuffed the offer. "When someone takes our vision and our intellectual property without a license after several attempts, we have no option but to protect it through every means available to us," Robert Frohwein, ZapMedia's general counsel, said in a statement. An Apple spokeswoman said the company doesn't comment on pending lawsuits. http://www.washingtonpost.com/wp-dyn...031203513.html  Advertising Sent To Cellphones Opens New Front In War on Spam Kim Hart The spam messages that have long plagued e-mail inboxes are now finding victims through a much more personal route: the cellphone. Text messages are the latest tool for advertisers and scammers to target consumers. But unlike junk e-mail that can be deleted with the click of a button, text-message spam costs money for the person who receives it and chips away at the mobile phone's aura of privacy. "It's so annoying because I get charged every time I get one," said Ryan Williams, 27, of Falls Church, who receives half a dozen spam messages on a daily basis. They ask him to download ring tones, visit questionable sites over his phone's Internet connection or urge him to subscribe to horoscopes or sports-score updates. Williams downloaded a program that was supposed to block texts from numbers not stored in his phone's contact list, but the junk messages still get through. Spammers even make the messages appear as if they're coming from his own number, so his wireless carrier cannot block them. "Spam e-mail usually goes right into my spam filter, but the texts are there, on my phone, and they just keep coming," he said. More than 1 billion text messages are sent every day in the United States. U.S. consumers are expected to receive about 1.5 billion spam text messages this year, up from 1.1 billion last year and 800 million in 2006, according to Ferris Research, a San Francisco market research firm. Those are conservative figures; some estimates are far higher. Verizon Wireless said it blocks more than 200 million spam text messages every month, and cellphone companies are ramping up efforts to shut them out by taking spammers to court and by using more sophisticated filters. Compared with spam e-mail, junk text messages are seen as more invasive because the cellphone is more intimate and is used for one-on-one communication -- a quality marketers are trying to utilize. Political campaigns and banks use text messages to mobilize voters or send account balance updates. Travel site Orbitz.com offers text-message updates on flight status. Television shows such as "American Idol" ask viewers to vote or take polls via text messages, and social networking sites like Facebook often use such notes to update members about friends' activities. Spam is often a nuisance, but more malicious messages can lead to a new form of fraud called smishing, a variation of a spam e-mail attack known as phishing. Smishing attacks, called such because text messages are also known as SMS messages, disguise themselves as legitimate messages from e-commerce or financial sites such as eBay, PayPal or banks, and seek to dupe consumers into giving up account numbers or passwords. Lori Small, a massage therapist in Ellicott City, fell for such a come-on. Her bank sends her a text message every time a transaction occurs on her checking account. In November, a message informed her that her account was overdrawn and asked her to provide the last four digits of her Social Security number to verify her ownership of the account. She sent the four digits to the sender. After getting suspicious, she called her bank, which told her it did not send the message and that it has a policy of not asking for account details via cellphone. She changed her cellphone number and now closely monitors her balance for any mysterious changes. "I couldn't believe how sneaky it was," she said. "I mean, e-mail spam is one thing, but this is my personal phone number . . . and now someone out there has one more clue about who I am." Spam messages and smishing attacks are more prevalent in Asia, where consumers often use phones to access the Internet and are more accustomed to receiving mobile advertisements, said Richi Jennings, an analyst who studies spam issues for Ferris Research. Spammers use similar techniques to target people through text messages as they do through e-mail. They harvest phone numbers from databases or hack into the records of legitimate companies that have permission to send text messages, such as travel sites or online retailers. The guesswork involved in targeting cellphone numbers is easier than randomly selecting e-mail addresses; while an e-mail address has a unique sequence of characters and a variable length, phone numbers are 10 digits. Therefore, it is easier to blitz thousands of potential customers at once. Most text messages are sent without any form of encryption, allowing tech-savvy spammers to intercept the messages and get access to personal information, said Larry Ponemon, founder of the Ponemon Institute, a privacy and security research firm. As of 2005, federal agencies banned companies from sending unsolicited commercial e-mail and text messages to mobile phones. To receive promotional material or updates, consumers typically must text a message to a short code to opt in to the service. But Simeon Coney, marketing director at anti-spam software maker AdaptiveMobile, said spammers are breaking the law, bombarding cellphone users with unwanted mail that could infect phones and BlackBerrys with viruses. Consumer complaints about text-message spam have been sporadic, according to the Federal Trade Commission, the FBI and Consumers Union. But Coney said his firm is starting to see "overall increases in mobile-spam traffic." Last year, Verizon Wireless sued telemarketers it said inundated its networks with more than 12 million unsolicited commercial text messages. In its lawsuit, the wireless carrier said it was able to block all but 4,618. Customers were hit with unwanted charges and the spam slowed legitimate traffic, according to Verizon Wireless. Individuals have also taken legal action against unwanted messages they perceive as spam. In October, Lindsey Abrams of Illinois filed a complaint against Facebook for sending "unauthorized text messages" to her wireless phone number, which had previously been assigned to another Facebook member. "These messages can come during all times of the day or night and, because the senders are often hard to identify, can be seen as intimidating or unsettling," Abrams said in the complaint. In 2006, Lei Shen, also of Illinois, sued District-based mobile marketing company Distributive Networks for sending her unauthorized ads in the form of text messages. Nearly a quarter of U.S. mobile subscribers say they've viewed a mobile advertisement in the last month, and more than half of them responded to it by sending a text message, clicking on it or calling a specific number, according to a report released last week by Nielsen Mobile. A separate survey conducted by M:Metrics, a Seattle firm that tracks mobile trends, found that 28 percent of the people who get text-message ads did not give permission to receive them, up from 19.5 percent eight months ago. The rise of spam could spoil trust in text messaging as a mode of communication, not to mention its potential for mobile advertising, according to Charles R. Taylor, a Villanova University marketing professor who has studied online and mobile ads. "Trust is crucial for an ad to be effective, and the minute you start clogging up cellphones and BlackBerrys, it's a real turn-off and an invasion of your personal space." The revenue generated by data services, such as text messages, has grown along with the consumer demand. About 20 percent of wireless carriers' total revenue now comes from the delivery of text messages, said Roger Entner, senior vice president for the communications sector for IAG Research. Each text message typically costs between 10 and 20 cents, although the four largest U.S. carriers -- AT&T, Verizon Wireless, Sprint Nextel and T-Mobile -- are rolling out flat-rate plans for text messaging. The carriers said they have rigorous filters to block spam, and they allow customers to block messages from certain numbers. They also try to remove charges for unsolicited spam. "We have every incentive to stop spam texts from getting through, since we end up footing the bill for a lot of it," said Verizon Wireless spokesman Jeffrey Nelson. "The longer a service like text is out there, the bigger the bulls'-eye gets." Staff researcher Richard Drezen contributed to this report. http://www.washingtonpost.com/wp-dyn...030902213.html  Paramount Making Movie Clips Available as Facebook Messages Ryan Nakashima Paramount Pictures will become the first major studio to make clips from thousands of its movies available for use on the Internet. The unit of Viacom Inc. is teaming with Los Angeles-based developer FanRocket to launch the VooZoo application Monday on Facebook. The service gives Facebook users access to footage from thousands of movies, ranging from "The Ten Commandments" to "Forrest Gump," to send to others on the popular social networking site. "The short clips for a movie that you've already seen before helps you relive the moment," Paramount senior vice president of entertainment Derek Broes said. The clips last from a few seconds to several minutes and cover the gamut from Eddie Murphy's guffaw in "Beverly Hills Cop" to Audrey Hepburn's pleas over her "no-name slob" cat in "Breakfast at Tiffany's." The studio will market DVDs of the movies through a button that appears after each clip is played. It eventually wants to use the application to virally market upcoming releases. For example, VooZoo is withholding clips from the "Indiana Jones" series until it works out a way to market the May 22 release of the latest installment, "Indiana Jones and the Kingdom of the Crystal Skull." FanRocket founder Danny Kastner said he is aiming to get a few hundred thousand users within two months and added that the company is in talks with other Hollywood studios to package their titles on VooZoo. That could take time, however, since Paramount staffers needed more than a year to select clips from the archive and tag them with search terms. Paramount said it has not set revenue goals for the new venture. "My benchmark for success is that people are joining and sending," Broes said. http://www.bostonherald.com/business...osition=recent  Latest Facebook Application Pays Users 10 Percent When Friends Buy on Their Recommendations AP Facebook Inc.'s popular online hangout so far has proven to be a better place for promoting fun and games than peddling products. But a new application aims to inject more commerce into the social playground by paying Facebook members who help merchants sell to their friends. The program, called Market Lodge, revolves around the notion that consumers are more likely to buy merchandise or services recommended by someone they know and trust. Market Lodge, made by a startup called bSocial Networks Inc., will pay Facebook members a 10 percent commission on all sales made on their recommendations. Facebook tried to capitalize on the bonds of friendship last year by introducing a marketing system that includes broadcasting product endorsements among people who know each other. The strategy hasn't paid off yet, largely because many of Facebook's users rebelled against a feature called "Beacon" that tracked and shared information about their purchases and other actions made on other Web sites. Spurred by the backlash, Palo Alto-based Facebook now allows its users to turn off Beacon. Conifer, Colo.-based bSocial is betting that Facebook's roughly 67 million users will be more receptive to an approach that dangles a financial incentive for participating. Facebook members who decide to use Market Lodge can customize their own stores, selecting from more than 1,200 products sold by about 50 different merchants. Once the personal store is set up, Facebook users can then invite others in their network to check out the stuff they're recommending. Market Lodge users can make purchases from their own stores and still qualify for the 10 percent sales commission. All the inventory, order processing and delivery arrangements are handled by the merchants -- just as they would be for any other sale. "We think this could be very lucrative for Facebook's members," said bSocial co-founder Sue Spielman. More than 100 people have signed up for Market Lodge since it quietly rolled out last week. For now, Facebook won't receive a cut of the sales made through Market Lodge, but bSocial Networks eventually may consider sharing revenue with the social network or other Web sites that might be interested in the application, Spielman said. Market Lodge is just one of more than 16,000 applications that have been designed for Facebook since the social network opened itself up to outside programs. Most of the applications, commonly called "widgets," provide Facebook users with new ways to play games or share photos or musical interests. Although they are attracting big crowds, online social networks so far have had trouble reaping huge profits from advertising. Even Google Inc., which runs the Internet's most lucrative advertising network, has acknowledged having trouble finding the right marketing mix in its business partnership with News Corp.'s MySpace.com, the only social network larger than Facebook. The owner of White Swan, a Boulder, Colo.-based seller of recorded music, thinks paying Facebook members to drum up sales could be more effective than advertising, which can cost up to $15 for every $100 in sales. "Right now when you do marketing, you are competing with so many voices that it's easy to get lost," said Parmita Pushman, White Swan's owner. If Market Lodge bears fruit, Pushman said she will face a new problem: figuring out how to persuade more Facebook members to recommend her products in their personal stores. http://www.latimes.com/business/la-f...,1571739.story  $40,000 for Man Tasered on YouTube Mike Nizza About two months went by after Jared Massey was tasered by a highway cop in Utah before he turned to YouTube. The video, footage filmed from within the police car, was an instant hit, rocketing up the charts and making him the latest internet celebrity. It’s been played more than 1.7 million times. Like other YouTube tasings, waves of outrage over excessive force followed — fire the cop, ban Tasers — and the police started an investigation a week and a half later. But the initial results were discouraging for the critics: The cop was cleared of wrongdoing; Mr. Massey paid the speeding ticket that he protested before being shocked twice. But a civil suit filed after has resulted in a settlement that will more than cover the ticket, and Mr. Massey’s lawyer suggested it covered everything else as well. ‘’They made what we consider to be a very fair offer of a significant amount of money,'’ Bob Sykes told The Associated Press. To be exact: he was awarded $40,000, including attorney’s fees. The deal was announced a week after a Utah prosecutor ruled the Mr. Massey did not commit any crimes in the traffic stop, according to The Salt Lake Tribune. His civil case focused on the fact proven in the video — that the officer did not seek to arrest him before drawing and firing the Taser. While the video evidence would have surely been used in any case, YouTube couldn’t have hurt Mr. Massey’s campaign. http://thelede.blogs.nytimes.com/200.../index.html?hp  Europe Approves Google’s Merger With DoubleClick Stephen Castle and David Jolly BRUSSELS — European regulators on Tuesday approved Google’s $3.1 billion takeover of the online advertising company DoubleClick, the final hurdle to a deal that would strengthen Google’s already powerful position on the Web. The European Commission, the executive arm of European Union, said that its investigation, opened in November had concluded “that the transaction would be unlikely to have harmful effects on consumers, either in ad serving or in intermediation in online advertising markets.” The merger had been opposed by rivals like Yahoo and Microsoft, which had voiced concern about Google’s advertising clout, as well as by consumer groups, which feared that the combined company would have access to a large amount of data on individual Web-surfing habits. Tuesday’s approval follows that of competition authorities in the United States. “We are thrilled that our acquisition of DoubleClick has closed,” Eric E. Schmidt, Google’s chief executive, said in a statement. The deal with DoubleClick, Mr. Schmidt said, “will dramatically improve the effectiveness, measurability and performance of digital media for publishers, advertisers and agencies, while improving the relevance of advertising for users.” Shares of Google rose $13.68, to $427.30 in New York mid-afternoon trading Tuesday. The commission said Google and DoubleClick “were not exerting major competitive constraints on each other’s activities and could, therefore, not be considered as competitors,” and even if DoubleClick could become an effective rival in online intermediation services, “it is likely that other competitors would continue to exert sufficient competitive pressure after the merger.” Microsoft and ATT had asked regulators to block the deal, arguing that a merged Google-DoubleClick would have too much power to set advertising rates. The commission uses different, and slightly broader, criteria to assess mergers than the Federal Trade Commission, which approved the DoubleClick deal in December. However, there was never much expectation that the top European regulator, Neelie Kroes, would block the deal. Ms. Kroes has shown a willingness to take on large companies — including, notably, Microsoft — but has been reluctant to intervene in mergers. Since she came into office in 2004, Ms. Kroes has blocked two mergers: a Portuguese power utility deal and the proposed takeover of the Aer Lingus by the budget carrier Ryanair. Her predecessor, Mario Monti, suffered several setbacks when the courts overturned his efforts to block mergers. As a consequence, Ms. Kroes has concentrated on cartel-busting and on seeking to prevent companies like Microsoft from abusing their dominant market position. Last month, the commission fined Microsoft 899 million euros, or $1.3 billion, for failing to comply with a 2004 judgment that the company had abused its market dominance. The fine was the largest ever imposed on an individual company. Microsoft’s battle with the commission has cost it 1.68 billion euros in fines. http://www.nytimes.com/2008/03/11/te...nd-google.html  File-Sharers Should Get Ready to Pay, Say Experts Greg Quill Some of North America's leading experts in peer-to-peer file sharing on the Internet are convinced that sooner rather than later – maybe within a couple of years – we won't be downloading music, movies and TV shows for free. In fact, the consensus at Thursday's key panel discussion – The Evolution of Peer-to-Peer Music: From Enemy to Business Partner – in a day-long round of seminars during Canadian Music Week was not dissimilar to a controversial idea advanced just last month by the Songwriters Association of Canada (SAC). SAC has proposed making it legal to share music on peer-to-peer networks in exchange for a monthly fee of $5 going to royalties for music's creators. But David Hughes, senior vice-president of the technology division of the Record Industry Association of America, suggests that business may find its own solution, with internet service providers charging some users an extra fee for their downloading habits. Downloading eats up precious bandwidth and slows down the network. "Eighty-five per cent of available bandwidth is used for piracy," Hughes told a tightly packed crowd at Toronto's Fairmont Royal York. "It's the ISPs who have to crack down, and they will, once they realize they can make money from the people who use the most bandwidth. The shift will be to subscription services costing (high bandwidth users) a fee, as much as $12 a month," Hughes predicts. Eric Garland, CEO of BigChampagne, the California-based media measurement company that monitors digital music activity on the Internet, added: "Maybe the ISPs will have to find the bandwidth hogs and charge them extra; making it more difficult and expensive for ordinary subscribers to acquire bandwidth isn't a good strategy. It doesn't serve the hunger. This is a beast and you have to feed it." Eric DeFontenay, founder of the New York-based MusicDish e-journal, about online music by new and emerging artists, agrees that things should and will change. "Radio was the first medium accused of ripping off music and musicians, till performing rights and (methods of) compensation were established. What's needed is compensation for artists that's transparent to consumers, something like the SAC proposal. "If you want all-you-can-eat music, $60 a year is cheap," he said. The analysts and experts at Thursday's discussion – including Washington-based Gary Greenstein, a specialist in the future financing of digital media space, and Chris Gillis, a business development manager at the California-based Mediadefender Internet piracy prevention company – offered different hypothetical solutions to the increasing use of the Internet by peer-to-peer file sharers, free music downloaders and the subsequent massive loss of revenue to music creators. They generally agreed that the commercial music industry in the U.S. had erred in pursuing and penalizing peer-to-peer networks and those who used them. "Suing customers is not a good way to do business," DeFontenay said. "Music industry efforts to stop file sharing by litigation was a huge failure." Hughes says there needs to be another way to raise obstacles for downloaders. "Raising awareness of the morality of free downloading doesn't work, nor does litigation," he says, adding, "If you make the hassle factor high enough, people will pay." Greenstein warns, however, that customers won't go for extra fees. "Only a fraction of music consumers in the U.S. use existing (legal) subscription services such as Napster and Rhapsody (or Puretracks in Canada). They aren't going to buy into an ISP-based subscription . . . they'll go around it, find other ways to get their music for nothing. "In the meantime, they're looking at an empty screen waiting for searches and downloads – that's a huge and untapped opportunity for advertisers. " Trying to stop free music-file exchanges – in Canada there's no legal impediment – is a waste of time and effort, most of the panelists agreed. "People don't care that they're using peer-to-peer," Garland said. "They use it without knowing or caring because it's easy, it's comfortable and it works. It's the very definition of the Internet. You can't stop people using the Internet for entertainment. The problem is getting them to pay for it." http://www.thestar.com/entertainment...article/326536  Congress Dons Rubber Glove, Prepares Probe of FCC Chairman Matthew Lasar Federal Communications Commission Chair Kevin Martin has two weeks to deliver a truckload of written records to Congress related to over a dozen hot-button FCC issues and policies. They're being demanded by House Energy and Commerce Committee Chair John Dingell (D-MI), who sent Martin the request letter today, cosigned by Rep. Joe Barton of Texas, the ranking Republican on the Committee. The missive warns Martin that Dingell's Committee is "investigating allegations from current and former FCC employees and other sources, which we have reason to believe are credible." The charges concern "management practices that may adversely affect the Commission's ability to both discharge effectively its statutory duties and to guard against waste, fraud, and abuse." It's no secret that Martin and his subordinates are suspected of putting pressure on career FCC staff to emphasize data or produce studies that come to conclusions that the Chair likes. The biggest blowup concerns a 2003 study on television that suggested that locally owned TV stations produce more local news than nonlocally owned broadcasters—distasteful data for supporters of relaxing the agency's media ownership rules. When the FCC did not publish this document, Senator Barbara Boxer in 2006 accused the agency of "deep-sixing" the report. Eventually the Commission exonerated itself with an internal audit that a whistle blower in the case called "skewed in its judgments." Now Dingell wants all e-mails, handwritten notes, phone conversation records, meeting schedules, and whatever else exists in paper or electronic form since January 2005 involving the audit's case file, plus all records related to: • The FCC's decision to drop the conclusions of a 2004 study that concluded that "a la carte" video programming—in which consumers can pick and choose which channels to buy—will hurt cable networks attempting "innovative or untested formats." The agency Commissioned the work from Booz Allen, but revised its position the next year with a "Further Report" that criticized the Booz Allen study, questioning its assumptions and mathematical calculations. Martin is an outspoken advocate of a la carte programming, at one point publishing an op-ed piece with Senator John McCain on behalf of the concept. • The Commission's conclusion in November of 2007 that the cable industry had reached the so-called "70/70" threshold. The Communications Act stipulates that when cable systems with 36 or more activated channels can be viewed by 70 percent of US households and when 70 percent of those households subscribe to them, the FCC can impose "additional rules necessary to promote diversity of information sources." Up until last year the agency had consistently concluded that while big cable had surpassed the first prong of the test, it had not reached the second. Dingell's letter specifically wants intel explaining why the FCC based its 2007 decision, which it eventually rescinded, entirely on Warren Communications company data and none other, including the information that the cable industry submits to the agency every year. • The FCC's ten recently commissioned media ownership studies, and documents related to the agency's decision not to change any of the Commission's media ownership rules save the newspaper/TV cross-ownership ban. And that's only for starters. Dingell and Barton want Martin to hand over any directives involving "limitations or restrictions imposed on FCC employees' ability to communicate with each other concerning official agency business"; records that illuminate the Commission's policies on "communications between FCC personnel and outside entities"; documents that explain how the agency decided who would go to the recent World Radiocommunication Conference in Switzerland; a list of all new FCC employee hires and reassignments from March 2005 to the present; and the individual meeting schedules of all Commissioners and all Bureau Chiefs and the FCC's Inspector General since January 2005. This request has got to be turning the FCC completely upside down. Significantly, it appears to reflect a bipartisan discontent with Martin's performance. Democrats and some Republicans are upset over his recent move to relax one of the agency' key media ownership rules, as well as the rushed manner in which he handled the matter late last year. Other Republicans dislike what they see as Martin's persecution of the cable industry, especially Comcast. The letter may even reflect some Republican dismay that Martin did not go further in relaxing the Commission's broadcast ownership guidelines. The question of Martin's perspective on cable will be explored in an upcoming Ars Technica feature—that is, if the FCC's chief survives this Congressional inquiry. http://arstechnica.com/news.ars/post...-chairman.html  House Judiciary Committee Logs On to Network-Neutrality Issue Debate Continues Over Network-Management Practices John Eggerton The House Judiciary Committee heard testimony Tuesday on the anticompetitive implications of the network-neutrality issue. A representative of the Christian Coalition argued that the group did not seek "burdensome regulations" and preferred less regulation but suggested that it might be necessary anyway because of actions taken by some broadband-network providers. Michele Combs, vice president of communications for the Christian Coalition, cited Verizon Communications’ blocking of text messages, AT&T’s blocking of political speech (some anti-administration lyrics in a Pearl Jam concert), and the AP test of Comcast peer-to-peer network management in which the downloading of a King James Bible was blocked. All those have been the subjects of complaints to the Federal Communications Commission, which is currently considering what, if anything, to do about network management, including coming up with a better definition of what is off-limits. Combs said faith-based groups are increasingly using the Internet, that networks must not be allowed to block political speech and that those networks appear to be using the same techniques as China has used to block the Christian Coalition. Seconding that concern about so-called network neutrality was Caroline Fredrickson, director of the American Civil Liberties Union's Washington legislative office. She blamed FCC inaction and the Supreme Court's decision to uphold the Brand X ruling for network "gatekeepers" increasingly controlling access to content. The Supreme Court in 2005 upheld the FCC's decision that phone networks’ provision of Internet was not subject to the same mandatory access provisions as telephone common-carrier service. In the interests of regulatory parity, it said, the commission has since extended that to cable, satellite and other network providers. Frederickson said those provisions, which had been applied to data services as far back as the late 1960s, allowed the Internet to flourish. She added that nondiscrimination principles do not violate network operators' free speech. In fact, she said, network operators aren't speakers, per se, but provide wires in much the same way telephone companies do. But the essential factor is free speech, she added, and that is the speech of users and content providers. Whether networks have to engage in network management is up to the technology people, she said. But if there must be such management, it must be equitable and not used as a "cover" for blocking certain types of content. She called for legislation: “Congress should act to protect the rights of all Internet users to send and receive lawful content free of censorship from government or business,” she said. “Restoring meaningful rules that protect Internet users from corporate censorship is vital to the future of free speech on the Internet.” Rick Carnes, president of the Songwriters Guild of America, put in a plug for network management, saying that the real bottleneck is not networks but the illegal P2P file sharing that is killing the songwriting business. He pointing out that his song publisher used to have one-dozen writers on staff and now has one. He is particularly concerned with legislation that would impede the ability of networks to manage traffic or that would prevent them from employing illegal file-detection technologies. Carnes said 5% of Internet users are responsible for 70% of the P2P traffic and 90% of that traffic is illegal. He added that studies showed that the majority of pirates would stop if their network warned them or made them stop. He called it odd that the problem of network congestion would be addressed by denying networks the ability to manage congestion, saying management was, instead, a case of the market dealing with the problem. University of Pennsylvania Law School Professor Christopher Yoo said networks and content providers are symbiotic. There is a small potential for anticompetitive behavior, but that should be looked at on a case-by-case basis rather than broad regulation, he added. In a bit of serendipity, the live video of the hearing first froze and then was inaccessible for several minutes due to problems with the streaming, according to a committee spokesperson. http://www.broadcastingcable.com/art...dustryid=47174  Key House Democrat Opposes Network Neutrality Law Dow Jones/AP A senior House Democrat said Tuesday there was no need for Congress to consider regulating content that travels over the Internet, setting up a possible dispute with rival Democrats over the need to preserve so-called network neutrality. Rep. John Conyers, D-Mich., chairman of the House Judiciary Committee, said the argument hadn't been made for Congress to consider passing laws governing the flow of traffic over the Web. He said the only reason lawmakers should consider getting involved in legislating network neutrality was if there were concerns that telecommunications companies that run Internet networks were engaging in anti-competitive behavior. Then, said Conyers, existing antitrust laws would suffice to ensure the market was working effectively. "Unless we've clearly documented a specific incident" of violation of network neutrality, "I don't believe Congress should regulate," said Conyers. Conyers made the comments at a hearing of the judiciary panel into the issue of network neutrality. His view was endorsed by the several Republican members of the committee present at the hearing. Rep. James Sensenbrenner, R-Wis., a former chair of the Judiciary Committee, said he was against the notion of the Federal Communications Commission introducing prescriptive regulation over the issue. Conyers' position puts him at odds with Rep. Edward Markey, D-Mass., chairman of the House Telecommunications Subcommittee, a strong proponent of legislation enshrining network neutrality. Last month, Markey introduced legislation which would instruct the FCC to conduct a wide-ranging investigation into the need for enhanced network neutrality regulations, and beef up fines for violators of these new rules. Markey's bill has little chance of becoming law in a presidential election year, but he is hoping to line up sufficient backing for the legislation, and then reintroduce it in 2009. The judiciary panel heard testimony from a number of witnesses, the majority of whom were in favor of legislation to bolster regulation of Internet network operators. These included Damian Kulash, lead singer of the band OK Go, which has established a loyal fan base primarily using the Internet rather than more traditional channels. Kulash urged the committee to take steps to preserve an open and free Internet. The issue of network neutrality was a dominant one on Capitol Hill in 2006, the last time that an attempt to pass a law on the issue came close to fruition. The FCC is currently investigating claims that Comcast Corp. violated network neutrality by degrading access of its broadband Internet network customers to a file-sharing software application. Last week, speaking at a function in California, Kevin Martin, the agency's Republican chairman, gave a clear sign that he planned to seek a ruling that the company did violate the commission's existing four principles on network neutrality. http://www.siliconvalley.com/news/ci_8535517  BT Calls for Action on Net Speeds Rory Cellan Jones The UK's largest broadband supplier has called for the industry to be clearer about how it advertises net speeds. BT Wholesale, which supplies eight million people, said many customers were disappointed by the mismatch between advertised and actual speeds. An independent survey found that 15% of people who bought eight megabit per second packages actually got the speed. The firm said regulators needed to agree rules about how broadband speeds could be sold to the public. "The reality is we are all trying to push the technology," Guy Bradshaw of BT Wholesale told BBC News. "The industry needs to join together with Ofcom to agree a set of principles as to how these messages should be communicated and advertised so that the understanding with the consumer is as accurate as it can be." Traffic problems BT said that, while its DSL Max product offers a range of speeds up to eight megabits per second (Mbps), it tells its customers - the Internet Service Providers (ISPs) - that actual speeds will vary from user to user. Cameron Rejali, Managing Director of Products at BT Wholesale, said it is up to the ISPs how they market broadband, "but if they are marketing it badly, the market will punish them." BT said users need to know that there is a difference between the line speed - what the line between their home and the exchange can support - and what it describes as "throughput", a measure of the data coming down the line during an activity such as the downloading of a video. Only 35% of BT's DSL Max customers are achieving an eight mbps line speed - the rest will see their speed cut by factors such as distance from the exchange, poor equipment, and interference from electrical appliances. But none of these five million users will achieve eight mbps "throughput" because of internet congestion and other network issues. "The reality is if you are very far from an exchange or there are environmental factors then your speed will come down and there is not much we can do in the short-term to address that problem," said Mr Bradshaw. Ofcom is currently reviewing the way broadband is marketed to consumers. A spokeswoman said: "Whilst there are technical reasons why a consumer may not get the full speed of the package to which they have signed up the key point is that consumers should be able to make an informed decision about what broadband package is best for them at the point of purchase." http://news.bbc.co.uk/go/pr/fr/-/2/h...gy/7292932.stm  Sprint Phone First to Use Fast Network AP Sprint Nextel Corp. is upgrading one of its cell phone models so that it can connect to a faster data network, doubling its download speeds and boosting upload speeds by about eight times. Both Sprint and Verizon Wireless operate so-called EV-DO Rev. A networks, but have used them only for laptop cards. Their fastest phones have used the older and slower EV-DO Rev. 0 network. Sprint said Monday it was releasing a software update for the Mogul phone, made by HTC Corp. of Taiwan, that will enable the phone to connect at Rev. A speeds. Downloads speeds should be 600 kilobits per second to 1,400 kbps, up from a range of 400 kbps to 700 kbps with Rev. 0. It will be capable of uploads of 350 to 500 kbps, up from 50 kbps to 70 kbps. Sprint said its broadband network now covers 234 million people, and the vast majority of it has been upgraded to EV-DO Rev. A, short for Evolution-Data Optimized Revision A. The Mogul is a smart phone that runs Windows Mobile software and can be used as a modem for a laptop. It costs $199.99 with a two-year contract and went on sale in June. The software update will be available immediately from HTC's site. Verizon Wireless has not announced a phone using Rev. A. Spokeswoman Brenda Raney said the main advantage of Rev. A is higher upload speeds, which is important to laptop users but less so for cell-phone users. AT&T Inc. already sells phones that use its fastest network technology, known as HSDPA, for High-Speed Downlink Packet Access. Its listed download speed is the same as EV-DO Rev. A, with a slightly higher upload speed. http://www.physorg.com/news124367657.html  P2P is for Piracy... and We're Going to Use it Rick Cotton, NBC Universal's top lawyer, is sitting across the table from me at a Midtown restaurant only blocks from Cotton's base at Rockefeller Center. Apparently, media moguls do not breakfast on a diet of puppies and children, as some consumers seem to think; bagels, toast, and oatmeal are the order of the day. George Kliavkoff, NBC's first "Chief Digital Officer," has also joined us to talk policy. "I'm curious if you necessarily equate peer-to-peer protocols like BitTorrent with piracy?" I ask after the orange juice arrives. Cotton's opinion on that question matters. As general counsel for NBC Universal, he has been one of the strongest US backers of the idea that ISPs have some duty to start filtering the undeniably massive volume of illicit P2P traffic that passes through their networks. AT&T has already publicly committed to take up the challenge, and Cotton hopes to see more action from other ISPs. "Well, I think the answer today is yes," he says. "It's obvious that peer-to-peer is capable, and in fact may in the future be a significant mode of efficient transport of legitimate content. But today, in terms of that consumption of bandwidth, it's overwhelmingly pirated content. There's probably a percentage of pornography mixed in, but one is not talking about legitimate content." Cotton and Kliavkoff are affable, intelligent, and interesting to chat with—but they also inhabit a conflicted world, and it shows as we talk. Take our discussion of peer-to-peer, for instance, with its lack of "legitimate content." I ask about the current FCC hearing on Comcast's BitTorrent "delaying," where a company called Vuze is in fact offering just such legitimate content using BitTorrent (to say nothing of BitTorrent, the company, which is doing the same thing). "You have to start with the first proposition," Cotton says, "which is: should we collectively be concerned about the fact that 50 to 75 percent of the total bandwidth of broadband ISPs is today taken up by P2P traffic which is in fact overwhelmingly pirated? I have to tell you, I think the answer to that is yes." He goes further; P2P protocols themselves disrupt the Internet by passing bandwidth costs from content owners onto ISPs. Cotton told the FCC in a recent filing, "P2P applications shift the costs of centralized storage and distribution to end users and their broadband network providers." In addition, installing P2P apps "can slow down the processing speed of [consumers'] computers, open up the contents of their hard drives to third parties and expose them to potential copyright liability," the NBC filing noted. Worse, P2P protocols "exacerbate the congestion" that Comcast's RST packet solution attempts to solve. Fair enough: P2P is a hotbed of piracy, it's bad for ISPs, it disrupts the Internet, it can bog down computers, and it harms corn farmers in Iowa. It seems safe to say that NBC won't be using BitTorrent any time soon. So it comes as a complete surprise when, at the end of our wide-ranging conversation, Kliavkoff drops a casual bombshell. "We're coming up on an announcement of using some peer-to-peer technology for distribution of some of our own content," he says. "We generally think that peer-to-peer technologies are very useful for distributing large files, they can significantly reduce bandwidth costs, and generally they are technologies today without a business model. We think the distribution of legitimate content using that technology saves us a lot of costs and we're happy to share some of that savings." I beg your pardon? NBC: Old media no longer It's not that NBC is hypocritical, stupid, or worse; it's that the transition currently engulfing media businesses is both terrifying and the source of bold new opportunities. NBC hopes to transform itself from old media giant into a new media pioneer that makes its content available through MySpace, AOL, and Comcast, allows embedding and clipping, and fully supports the emerging world of widgets and web apps. With NBC's Hulu officially launching today, Kliavkoff estimates that its video content will reach more than 95 percent of the US Internet audience through its major portal partners. It's a "groundbreaking thing for big, old, traditional media to do," he says, and he's right. Instead of ceding Internet video to distributors like YouTube, NBC and News Corp. have partnered on a bold plan to do the digital distribution themselves. The site wasn't coded up over the weekend by a team of hackers slaving away in the basement, either; Hulu cost "tens of millions of dollars." Both Cotton and Kliavkoff face "a lot of concern reaching up to the board level that the material that's on Hulu is not available next door on a pirated basis," and it's easy to see why with that kind of money at stake. This is the concern that drives Cotton's crusade against illicit file-swapping. He's convinced that the pirate problem is costing NBC Universal real revenue and that the scale of the problem is so vast as to discourage investment in the "carrots," positive solutions like Hulu. "With all that pirated material available, it creates tremendous disincentives to content owners who need to invest in new content," Cotton says, "and that just hurts consumers over time." After all, if two video stores sit next to each other at the local mall and one charges for DVDs while the other hands free, illegal copies out without penalty, what incentive does the legitimate video owner have to invest any money in buying new DVDs? It's a fair question, so I ask Cotton why NBC has, in fact, just invested millions in a service like Hulu. File-swapping, though rampant, is obviously not enough of a problem to stop this kind of investment yet, but Cotton suggests that if large projects like Hulu fail to show returns, there may not be many more attempts in the future. He fully recognizes the need to use both carrots and sticks, to "compete with free" while trying to shut down the illegal distribution channel, and he sees both efforts as complementary; "hand in glove," he calls them. Which brings us to the stick: ISP filtering. Bring on the filters Back in June 2007, Cotton filed comments with the FCC that laid out NBC Universal's position quite clearly: ISPs have a role to play in protected copyrighted work, and if they won't play that role, the government should make them. "The Commission should make unmistakably clear, as part of its regulations governing broadband industry practices, that broadband service providers have an obligation to use readily available means to prevent the use of their broadband capacity to transfer pirated content," he wrote at the time. Loving and loathing P2P These efforts would include notification of users (Cotton doesn't appear interested in some sort of "sue-'em-all!" strategy), possibly followed by curtailing Internet access. It's a plan that has been mooted in both the UK and France, but all of the solutions would be based on accurate identification of copyrighted work flowing through ISP pipes. That means one thing: ISP deep packet inspection of all P2P traffic, with attempted identification to follow. When we talk, Cotton makes clear that he's not "a technology guy" and that he doesn't much care how the filtering is accomplished. He fully grants the importance of privacy and fair use, and he's concerned about casting a net too widely. But something, anything, needs to be done. "In this conversation, we talked fairly cavalierly and easily about the notion of lots of people on the Internet accessing illegal content," he says at one point. "I mean, normally, if we translate that to the physical world and we were sitting here observing as a neutral social phenomenon that huge numbers of people were walking into stores and taking product off the shelf... I think the reason for that is that historically, the technology talks to people; certainly it talks to kids. And if it's totally easy, if the technology sends no message, I think the thought process of individuals and particularly kids is, 'If it's so easy, it can't be wrong.'" This is technology as road sign rather than electric fence; it won't put a stop to piracy, but it will give people a clear warning when limits have been reached. The same argument has been trotted out for years by DRM proponents when asked why they bothered to keep hassling paying customers when illegal copies were widely available online. DRM could be breached, was the usual response, but at least it let people know when they start doing something they shouldn't be doing. The problem with this answer was that the "signposts" erected by DRM conveyed information that went far beyond the limits imposed by law; it told people, for instance, "No, you can't put a copy of that DVD you own on your iPod." At least Cotton's solution has the virtue of not necessarily encumbering a user's digital property with locks and restrictions, since all the intelligence and filtering takes place in the middle of the network. He knows it won't stop piracy, but he points out that any real-world lock can be picked and "that hasn't led people to stop locking their doors." What's needed, in NBC's view, is for technologists to put more trust in their own technology. Cotton appears exasperated by the tech community's general hostility to his idea. "The technology community and the blogosphere, who are enormously enamored of and respectful of the capabilities of technology in every other respect... there's just this underlying assumption that technology is completely incapable of addressing the challenge of reducing the among of pirated content that's accessed online, and I just think that's naïve or intentionally blind," he says. Meet the obstructionists In Cotton's view, privacy concerns and other problems raised by ISP filtering are real, and they need to be resolved. He and Kliavkoff are both cognizant of the need to tread carefully in this area, to avoid giving NBC Universal the slightly sinister reputation that now clings to the RIAA's name in much of the blogosphere. "I do worry about it," he tells me when I ask about reputation, but he returns once more to the scope of the problem. "Everyone wants to ignore the scale of the pirated material online," he says; "most of the concerns [about filtering] are really efforts to do nothing about it." This approach to opponents pervades our discussion. I'm told that filtering has been attacked by people "with a vested interest in obstruction" who have put out a set of "bogeymen" that are, in reality, an attempt to avoid doing anything about the unfettered online trading of copyrighted work. Cotton sees his position as eminently reasonable; after all, he supports privacy rights, he's not wedded to any particular technology, and he's far more concerned with the transmission of complete, verbatim TV shows and movies than any amount of "fair use" copying, sampling, or remixing. Surely, if everyone could just admit the scope of the problem and agree that it needs to be addressed, a solution could be found. But so far it hasn't, due in part to the fact that the issue (like most interesting issues) is far more complicated than just filtering out complete copies of films. Safe harbors ISPs like Verizon and Comcast aren't generally "pro-pirate." As Cotton and Kliavkoff point out, ISPs have an interest in curtailing the huge bandwidth slurped up by P2P users, and if it were truly as simple as installing a few racks of gear and flipping a switch, piracy would have been blocked from the tubes years ago. There's a reason why ISPs don't want to get involved in this sort of filtering, and it's more complicated than "obstructionism." Network operators like Verizon and Comcast are protected by "safe harbor" rules found in the DMCA that exempt them from liability for what passes over their networks, but only if they do not control or alter that traffic. Filter that traffic, and it's possible that your safe harbor drains away. Only AT&T has publicly signed on to the filtering idea, and the move led Columbia's Tim Wu to ask in a recent Slate column (aptly titled "Has AT&T lost its mind?") what the company could possibly be thinking. "Once AT&T gets in the business of picking and choosing what content travels over its network," Wu said, "while the law is not entirely clear, it runs a serious risk of losing its all-important immunity. An Internet provider voluntarily giving up copyright immunity is like an astronaut on the moon taking off his space suit. As the world's largest gatekeeper, AT&T would immediately become the world's largest target for copyright infringement lawsuits." Cotton scoffs at the idea. "I frankly don't think it's an issue," he says, saying that there's "no incentive for us to sue them" if ISPs start filtering. But lawsuits against ISPs go much further than the legal department at NBC Universal, and ISPs certainly don't want to cut similar deals with every industry or activist group that doesn't like some subset of material passes through their networks. While AT&T has agreed to the plan in theory, it has yet to roll out any sort of filtering solution, making it too early to tell how the legal issues will develop. But by agreeing to be the first major ISP to filter, AT&T "deserves praise, not criticism," says Cotton. Will such filtering even work? That's another huge unknown. Video filtering technology certainly works; YouTube has rolled out its own solution, while companies like MotionDSP offer commercial products. But deploying filters on user-generated content sites, where the site has a full, unencrypted copy of the video; well, that's one thing. Rolling this technology out on the Internet backbone, where P2P files are broken into bits, come out-of-order from dozens of different machines, and can be easily encrypted is another. Doing all of that in real time is daunting task, but AT&T apparently has confidence in a firm called Vobile. NBC: the "pirate peacock"? Despite the desire for ISP filtering of P2P content, Cotton and Kliavkoff see in P2P technology a way to save money. Sure, it will exacerbate Comcast's current problem with limited upload bandwidth, a problem largely caused by P2P seeding, but NBC Universal is willing to spread its cost savings around in such a way that everyone in the ecosystem will benefit. Don't worry; he's just using NBC Direct When NBC says that it doesn't hate P2P as a technology, it's serious, and the proof was on display late last week when the official announcement surfaced. NBC will start using P2P technology from Pando Networks to distribute its shows through NBC Direct. Using P2P allows the company to save on the massive bandwidth bills it would otherwise incur from distributing HD-quality video. Given the timing of the announcement, NBC's recent FCC filing is curious, since it sides with Comcast's right to block BitTorrent uploads during periods of network congestion (Pando's P2P component is based on BitTorrent). The announcement raises all sorts of questions, among them: how would NBC avoid the very filters it's advocating? If the answer is that the shows are wrapped in DRM and encrypted, as they appear to be, then this only indicates how easily most packet inspection tools can be bypassed. If the answer is that NBC's content gets a pass from the filters, other P2P companies like Vuze will clamor for the same privilege, and groups like Free Press will complain that only large content owners get to avoid the communications dragnet while independent voices streaming Miro channels face a risk of being snagged, blocked, or delayed. We'll see how things shake out. In the meantime, while enjoying your unfiltered 'Net access and Trent Reznor's new album (a copyrighted work conveniently and legally distributed through P2P), take a moment to say thanks to Cotton and Kliavkoff. Yes, they want to filter your Internet, but they (and the media moguls like them) are also legitimizing a promising technology that only a few years ago could reasonably be described as a pirate protocol. Just this week, a House member of the subcommittee that deals with IP and Internet issues wrote an editorial in which he suggested that a total ban on P2P apps was a positive step for colleges to take. As major media companies become a part of the P2P ecosystem, though, suggestions like this will be harder to make and will soon become untenable. It's an odd thought, but P2P's one-time detractors, the content owners, have recognized the promise of the technology and could be the very group that fights to defend its legal uses. Because of NBC and Vuze and Blizzard and Linux and Skype, P2P has quietly become ingrained in the computing landscape. And as the technology expands even further, it may force the world's largest ISPs to change the assumptions that underlie their network: servers in the middle pushing content downstream to users have given way to a model where upstream bandwidth is under severe pressure and ISPs are scrambling to keep up. Not bad for a one-time rogue technology. Even Cotton, while convinced that illicit file-swapping is much like walking out of store with a DVD under your jacket, makes clear that he has no intention for pushing any sort of blanket ban on P2P protocols (though he'd still like you to stop swapping his TV shows). P2P is just too valuable for that, even to the Peacock Network. http://arstechnica.com/articles/cult...dia-moguls.ars  Music Industry Proposes a Piracy Surcharge on ISPs Frank Rose Having failed to stop piracy by suing internet users, the music industry is for the first time seriously considering a file sharing surcharge that internet service providers would collect from users. In recent months, some of the major labels have warmed to a pitch by Jim Griffin, one of the idea's chief proponents, to seek an extra fee on broadband connections and to use the money to compensate rights holders for music that's shared online. Griffin, who consults on digital strategy for three of the four majors, will argue his case at what promises to be a heated discussion Friday at South by Southwest. "It's monetizing the anarchy," says Peter Jenner, head of the International Music Manager's Forum, who plans to join Griffin on the panel. Griffin's idea is to collect a fee from internet service providers -- something like $5 per user per month -- and put it into a pool that would be used to compensate songwriters, performers, publishers and music labels. A collecting agency would divvy up the money according to artists' popularity on P2P sites, just as ASCAP and BMI pay songwriters for broadcasts and live performances of their work. The idea is controversial but -- as Griffin and Jenner point out -- hardly without precedent. The concept of collecting a fee for unauthorized use of music was developed in France in 1851 as a way of reimbursing composers whose work was being performed without their permission in cafes and the like. The practice spread to the United States in 1914 and currently applies to radio airplay and webcasts in addition to live performances. In a 2004 white paper, the Electronic Frontier Foundation called for it to be applied to file sharing, but the Recording Industry Association of America immediately dismissed the proposal. Things are different now. "The labels are beginning to like the idea of an access-to-music charge," says Jenner, who once managed Pink Floyd and the Clash, "because they're increasingly aware that their current model is broken." U.S. music sales, which peaked in 1999 at nearly $15 billion, dropped to $11.5 billion in 2006. Last year's figures are still being tallied, but with CD sales cratering and online sales overwhelmingly dominated by singles, the only question is how far they'll fall. Meanwhile, the industry's antipiracy efforts appear more and more futile. Digital rights management, long touted as a solution, has been all but abandoned. And though the RIAA is said to have threatened or taken action against some 20,000 suspected file sharers, the market-research firm NPD Group reports that nearly 20 percent of U.S. internet users downloaded music illegally last year. The score to date: 0.02 million alleged P2P users down, 40.98 million to go. At the music industry trade show MIDEM last year, John Kennedy, the head of IFPI -- the RIAA's international affiliate organization -- offered modest support for the kind of licensing fee Griffin and Jenner propose. "It's a model worth looking at," he said at a press conference. "If the ISPs want to come to us and look for a blanket license for an amount per month, let's engage in that discussion." The tone at the January 2008 MIDEM in Cannes, France, was more combative. Longtime U2 manager Paul McGuinness said in a widely reported speech that it was time to hold ISPs responsible for the file sharing deluge. McGuinness wants network operators to cut off those the industry deems offenders -- an approach France's Sarkozy government is already pushing in that country. "If ISPs do not cooperate voluntarily," McGuinness declared, "there will need to be legislation to force them to cooperate," McGuinness said. Behind closed doors, however, MIDEM attendees discussed the prospect of collecting money from ISPs instead. An invitation-only meeting on the subject drew about 50 people, including representatives of IFPI, Sony BMG, T-Mobile, the giant European ISP and mobile-carrier Orange, and performing-rights organizations like BMI. The response, according to Jenner, "ranged from 'What do we do now?' to 'It sounds good, but can it possibly work?' A lot of people are like rabbits in the headlights: They're terrified they're going to lose their jobs. No one dares to feel that this might be the solution." Even so, notes Shira Perlmutter, IFPI’s head of legal policy, “none of our members are ruling anything out. These companies are all very open to creative new ideas that would allow customers to do things they want -- including using file sharing technologies.” Not everyone sees the two approaches as an either-or situation. "I love Paul McGuinness' idea," says another scheduled SXSW panelist, Dina LaPolt, a Los Angeles attorney who represents Mötley Crüe and the estate of Tupac Shakur. "And I love the idea of trying to make ISPs pay artists and make up for all the free crap that's going on. I support both, so long as artists are getting paid for their work." Whether ISPs will be willing to ante up remains far from clear, especially since many users can be expected to protest the extra charge. One option would be to introduce different service tiers and impose the surcharge only on customers who buy enough bandwidth to make file sharing feasible. But for ISPs, other music-industry demands could be far more onerous. In the weeks since MIDEM, antipiracy zealots have been using McGuinness's speech as a rallying cry. Last month the British media reported that a government white paper was about to call for legislation to force ISPs to move against suspected file sharers. As it turned out, the white paper merely included a vague call for "voluntary, preferably commercial solutions" by April 2009. Just Monday, the four majors sued the largest ISP in Ireland in an attempt to force it to block illicit downloads. Attorneys for Eircom retorted that it was not legally obligated to monitor its network traffic. AT&T has been looking into content-sniffing technology that could turn it into a spy agency for music labels and film studios, but most ISPs seem distinctly unenthusiastic about the idea. They have good reason to be. Technology experts say it would be impossible to reliably inspect trillions of packets for pirated material, especially if file sharing networks resort to encryption mechanisms. Legal experts point out that any attempt by an ISP to monitor its traffic in this way would jeopardize its status as a common carrier. It could also leave the ISP open to lawsuits from subscribers who get cut off without good reason. And financial experts say it would cost a bundle to implement. But the bottom line is, it simply won’t work. “Ultimately there is no real hope of eradicating copyright-infringing technology,” says another SXSW panelist, Eric Garland, CEO of BigChampagne, which tracks the popularity of music online. “You can push piracy around, discourage people from doing it in this or that venue, but I don’t think in even the most Orwellian scenario you could reduce massive infringement in a comprehensive way.” So, which will it be: A last-gasp assault on piracy, or a truce that would bring in money and benefit everyone except the lawyers? At this point, the music industry seems too dazed to decide -- and several nights in Austin probably won't help. Though Jenner and McGuinness are on opposite sides of the debate, their good cop-bad cop routine could ultimately prove synergistic. Pay up, the music people are telling internet providers, or we'll sic Washington on you -- and London and Paris and anybody else we can find. http://www.wired.com/entertainment/m...urrentPage=all  Free Music? Only With a Fight Dan Mitchell LIKE most purveyors of media, music labels are flailing about for a new business model even as their old one is quickly becoming outmoded. One proposed solution — giving music away online, supported by advertising — was the subject of a panel discussion this week at the South by Southwest music conference in Austin, Tex. “Of course a panel on online music-business models was going to degenerate into a food fight,” wrote Joseph Weisenthal of paidContent.org. The stew boiled over when Ted Mico, the head of digital strategy at Interscope/Geffen/A&M records, declared, “I need more marketing and promotion on the Internet like I need a root canal without anesthetic.” He was responding to his fellow panelist, Peter Rojas, the founder of a new music blog, RCRD LBL (pronounced record label.) Mr. Rojas is one of many advocates of the idea that music shouldn’t really be “sold,” but rather used to promote other things, like advertised goods, with a portion of revenue going to artists. On RCRD LBL, artists offer their music free, without restrictive digital rights management software. In return, the artists get a portion of the site’s ad revenue. Such blogs, he said, are “a huge force in music right now and in some ways more important than the labels because that is where bands are being broken.” Mr. Mico disagreed. “Different people want different forms of access,” he allowed, but giving away music on blogs isn’t the answer. Several people in the audience sided, loudly, with Mr. Mico, with some going so far as to accuse Mr. Rojas of ripping off the artists on his site. They had to be reminded that the artists are there by choice. Mr. Mico said he believed that subscription services like Rhapsody may yet catch on. “It is clear that somebody at some point will crack the subscription nut,” he said. A subscription service, he said, “allows people to discover music without having to pay extra for it.” It also tends to keep labels in control of the music-distribution chain. But even Mr. Mico had to admit that when it comes to subscription services, “the trouble is, nobody that hasn’t experienced it wants to experience it.” Mr. Levy should know, because he lost his. After tearing his apartment apart and considering that the laptop might have been stolen, he remembered leaving it on the coffee table, where newspapers and magazines tend to pile up. “My wife,” he wrote, “whose clutter tolerance is well below my own, sometimes will swoop in and hastily gather the pulp in a huge stack, going directly to the trash-compactor room just down the hall.” As far as Mr. Levy can tell, that’s where his laptop ended up. LITANY OF ERROR Record labels were making terrible missteps long before the advent of the digital age. Blender.com offers a list of what it considers the 20 worst. They include MCA Records’ decision in 1989 to pass on a Seattle upstart band called Nirvana while also betting big on “Leather Boyz With Electric Toyz,” the debut album of a hair-metal band called Pretty Boy Floyd. The worst record-label mistake ever, according to Blender, was the labels decision to sue Napster out of existence. “Napster’s users didn’t just disappear,” the site reminds us. “They scattered to hundreds of alternative systems — and new technology has stayed three steps ahead of the music business ever since.” http://www.nytimes.com/2008/03/15/bu.../15online.html  D’oh! War Against Web Tops Music Biz "Screw-Ups" List Dean Goodman The talent scout who turned down the Beatles has long been credited with committing the music industry's biggest gaffe. But Dick Rowe's billion-dollar boo-boo has been beaten to the top spot on Blender magazine's list of the "20 biggest record company screw-ups of all time" by the failure of record companies to capitalize on the Internet. The major labels took top dishonors for driving file-sharing service Napster out of business in 2001, instead of figuring out a way to make money from its tens of millions of users. The downloaders merely scattered to hundreds of other sites, and the industry has been in a tailspin ever since. "The labels' campaign to stop their music from being acquired for free across the Internet has been like trying to cork a hurricane -- upward of a billion files are swapped every month on peer-to-peer networks," Blender said in the report, which appears in its newly published April issue. Rowe came in at No. 2 for politely passing on the Beatles after the unpolished combo performed a disastrous audition in 1962. Beatles manager Brian Epstein later claimed the Decca Records executive had told him that "groups with guitars are on their way out," a comment that Rowe denied making. He went on to sign the Rolling Stones. Motown Records founder Berry Gordy was No. 3, because he sold the money-losing home of the Supremes and Marvin Gaye for about $60 million in 1988. The sum was dwarfed the following year when A&M Records sold for about $500 million. And in 1990, David Geffen got about $700 million for Geffen Records. (Gordy did retain ownership of the lucrative Motown copyrights.) Geffen Records grabbed two spots on the list: No. 11 for suing Neil Young in the 1980s because it did not like his uncommercial musical direction; and No. 12, for pumping a reported $13 million into a Guns N' Roses album that still has not seen the light of day after more than a decade of work. Other hall of shamers included Columbia Records at No. 10, for dumping Alicia Keys and rapper 50 Cent before they became famous; and Warner Bros. Records at No. 13 for signing rock band R.E.M. to a money-losing $80 million contract in 1996. (Editing by Belinda Goldsmith) http://www.reuters.com/article/techn...24104520080312  A Fond Look at Lennon’s ‘Lost Weekend’ Allan Kozinn If there’s one thing that May Pang has been fighting for the last 28 years, it’s the idea that John Lennon was depressed, isolated and out of control during the 18 months she lived with him, from the summer of 1973 to early 1975, when he reconciled with his second wife, Yoko Ono. Lennon himself fostered that notion by referring to the time as his “Lost Weekend” in interviews he gave in 1980, when he released “Double Fantasy,” a joint album with Ms. Ono that was his return to music-making after five years’ silence. And lurid, oft-repeated tales of a drunken Lennon’s being evicted from the Troubadour, a nightclub in Los Angeles, seemed to support that image. But to Ms. Pang, now 57, the “Lost Weekend” was a remarkably productive time, during which Lennon completed three albums — “Mind Games,” “Walls and Bridges” and “Rock ’n’ Roll” — produced albums for Ringo Starr and Harry Nilsson, and recorded with David Bowie, Elton John and Mick Jagger. And having already detailed these experiences (along with the Troubadour expulsions and other dark moments) in “Loving John,” her 1983 memoir, Ms. Pang has returned with the photographic evidence. Her new book, “Instamatic Karma” (St. Martin’s Press), is a 140-page collection of casual photos that Ms. Pang took during her time with Lennon. Apart from a handful included in “Loving John” — cropped and in black and white, but mostly printed in full and rich color here — she has kept them in a shoe box in her closet, occasionally pulling them out to show friends. “I began to think about publishing them just in the last couple of years,” Ms. Pang said on Monday at her publisher’s office in the Flatiron Building. “A friend of mine kept saying, ‘You tell all these stories about John, and when you do, you say, “Wait a minute, I have a photo to go along with that!” How come we never see these photos in a book?’ So, I thought maybe it’s time to put them out. It would let people see John in that world, through my eyes. And it would get rid of that whole ‘Lost Weekend’ thing, where everyone says he was always down and looked terrible. I don’t think these photos appear that way.” They don’t: in the pages of “Instamatic Karma” — the title is a play on Lennon’s song “Instant Karma” — Lennon looks relaxed and happy, and is seen spending time with his first son, Julian, as well as with some famous friends, among them Paul McCartney, Ringo Starr, Nilsson and Keith Moon. He is shown working in the recording studio, swimming in Long Island Sound, clowning around in Central Park and visiting Disney World. “They are personal and unique and very touching,” said Cynthia Lennon, Lennon’s first wife, who flew to New York from her home in Mallorca, Spain, to be the host of Ms. Pang’s publication party at the Cutting Room on Tuesday. Ms. Lennon got to know Ms. Pang when she escorted her son, Julian, on two of his four trips to visit his father while he was living with Ms. Pang. “It’s lovely for me to look back, especially with Julian in these photographs,” she said. “But I’m here just because May is a good friend of mine and has been since we met.” Ms. Pang arranged her book by subject instead of chronologically, with four chapters labeled “At Home,” “At Play,” “At Work” and “Away.” To her regret, she did miss a few famous moments. The March 28, 1974, Los Angeles jam session that included Lennon, Nilsson, Mr. McCartney and Stevie Wonder, for example, was not documented. But Ms. Pang did capture one momentous event: Lennon’s signing the agreement that dissolved the Beatles’ partnership on Dec. 29, 1974. After four years’ negotiation, the Beatles had agreed — or appeared to have — on the terms governing their formal split, and a meeting had been arranged at the Plaza Hotel in Manhattan on Dec. 19. George Harrison was performing at Madison Square Garden that night; Mr. McCartney had flown in from London; and Mr. Starr, having signed the document earlier, was on the telephone. At the last minute, Lennon objected to a clause that he felt would create tax problems for him (as the only Beatle living in the United States), and decided not to attend. Harrison, furious, canceled plans for Lennon to join him onstage at Madison Square Garden, but Mr. McCartney turned up at the East 52nd Street apartment that Lennon and Ms. Pang shared to discuss the sticking point. Ten days later, when Lennon, Julian and Ms. Pang were at Disney World, a lawyer bearing the revised contract turned up, and Lennon asked Ms. Pang to take out her camera. As Ms. Pang describes the scene in “Instamatic Karma,” Lennon had a last-minute telephone conference with his own lawyer “When John hung up the phone,” she writes, “he looked wistfully out the window. I could almost see him replaying the entire Beatles experience.” Ms. Pang then photographed him signing just beneath the clearly legible signatures of Paul McCartney, George Harrison and Richard Starkey (Mr. Starr’s real name), the shutter clicking between the “h” and “n” of his first name. Given that Lennon had been particularly militant about leaving the Beatles in 1969, it might seem odd to learn that he did so wistfully. Not to Ms. Pang. “Everybody changes,” she said. “With John things changed on a daily basis. It’s a question of time. Five years earlier was not the same situation. In 1974 he had just seen everyone. The friendship was still there. They were brothers. There was no animosity. And even though they all felt they had to break up to get to the next level of their musical careers, John had started this band that changed the world. It changed pop culture. It changed how we live and how we dress. And he knew that. So when he sat down to sign, he knew that this was it. His was the last signature. As he had started the group, he was the one to end it.” http://www.nytimes.com/2008/03/12/ar...12pang.html?hp  Justin Frankel Rocks On Eliot Van Buskirk When Justin Frankel quit America Online nearly three years ago, Rolling Stone dubbed him "the world's most dangerous geek." The title seemed especially apt at the time. After selling his startup Nullsoft and the hit music application Winamp for $100 million to the world's then most powerful internet company, Frankel repaid his corporate handlers by developing unauthorized file-sharing applications, such as Gnutella and Waste, that set the music and media industries on their ear. These days the spotlight may have moved on, but Frankel has lost nothing of his inventiveness -- or his subversiveness. Through his follow-up company, Cockos, he has developed a string of intriguing music applications over the past two years, including a networked collaboration tool called Ninjam that lets musicians play together simultaneously over the internet. These projects all exemplify a radical, anti-business approach that Frankel dubs "sustainable software" -- a method he says is all about "carefully respecting relationships with users and always keeping product first over business interests the goal is to just build stuff and do it in such a way that it never gets compromised." Sound familiar? It should. These factors still account for much of the allure of Winamp and Gnutella; and in fact, they sum up an approach that still seems to work best for online businesses that want to last, rather than just hitting consumers up for a quick profit. AOL now considers Winamp to be its "first open platform," and, of course, Gnutella (the foundation of LimeWire and other P2P programs) has proven remarkably difficult to compromise. We caught up with Frankel to find out what he's up to now. Wired News: So, what have you been up to since leaving AOL in January 2004? Justin Frankel: I took a little time off, but found myself getting interested in making music, so a lot of work was done and sort of evolved around that. I didn't really decide, "Hey, this is what I want to do." It was more like just gradually getting into it. WN: And thats your new software company, Cockos? Is there an etymology behind that? Frankel: It sort of evolved out of mis-hearing a quote from the movie Office Space.... I dont want to get too much more into it other than that, but if people go watch that film.... We were playing around with making software for processing effects for guitars and other instruments (Jesusonic), and then my brother and I decided to do a project called Ninjam, which is something that lets people play music with other people in a very unusual fashion (see below), so we had a lot of fun with that. I realized that a lot of the work we were doing was similar to everything you do for making digital-audio work-station-type software. And at the same time, I had been recording a lot using other software, and was very dissatisfied with the functionality of it as well as the user experience. WN: So that led to the development of Reaper, your digital-audio workstation software? Frankel: Thats correct. WN: What features are you proudest of in the Reaper program, that other audio recording programs don't do well enough? Frankel: What I'm most proud of is the fact that it takes a lot of the best aspects of many other pieces of software and tries to do them all pretty well. If you need to edit audio, it's up there with Vegas (developed by Sonic Foundry, purchased by Sony), which is really good for that. If you need to do complex routing, it's as capable as any other software out there. It can pretty much compete with just about anything, and at the same time, it's very straightforward to use and there's not a ton of different ways of doing the same things. If they've used a similar kind of software, people can just drop in there and everything is pretty intuitive. WN:I have a feeling I know the answer to this, but are you involved in Gnutella anymore, or does that have a life of its own? Frankel: No, I havent been involved with it since the conception, basically. WN: I once met with Gene Kan, the (late) Gnutella developer who testified in front of Congress on P2P. Did you guys know each other at all? Frankel: Yeah, we actually had a mutual friend, and he was a pretty nice guy.... With Gnutella, I basically wrote it originally and released a version, and then he was one of a group of people who reverse-engineered it. Presumably, because I wasnt available as a figurehead, he became that. WN: Right, because of your AOL relationship. Frankel: Yeah, because at that point I was working for them and couldn't be talking to anyone about it.... WN: Speaking of your time at AOL, I was reading up on that Waste program, which is now an open-source thing for chat and file sharing. Frankel: We opened-sourced it and then AOL did something which may or may not be, I don't know.... We released it then they said it wasn't authorized, so therefore the open-source license isn't valid. And, whether or not I was authorized, that would be something that would be questionable. So technically, the Waste software's out there, and people who use it could be violating AOL's intellectual property rights, but it doesnt seem to be a big deal. WN: I noticed that Reaper, your multi-track recording program is un-crippled shareware just like Winamp was back in the day (and still pretty much is), with people sending you fees. How's that been working with Reaper so far? Frankel: It's different in terms of scale, because Reaper has a much smaller audience and also because it's more expensive than Winamp was. It's a similar idea and it's enjoying some success. WN: You're one of the originators of this whole digital music thing in my eyes. If you were magically in charge of digital music (like anybody could be) what do you think the answer is? Frankel: Well, there's no easy answer. I like to draw an analogy to software and copy protection. This is something that is particularly interesting to me, because a lot of the other competing digital audio workstations and plug-ins -- all of these software companies actually use dongles and things like that to protect their software. And the terrible thing about it, and this is what just pisses me off to no end, is that the people who pay for the software ultimately have to deal with all of this. They have to deal with dongles and activation schemes, and the people who pirate it and get cracked versions, they don't have to do anything, they get the best experience. I understand why these companies do it, but I just don't think they're considering what they're making their users go through. Or they just don't care, because it's really just all about money to them, and making their customers upgrade and whatnot. So to answer that question: DRM is similar. It's not a good solution for the consumer. I know plenty of people who don't want to buy encrypted, DRM-ed content because they want to be able to play it wherever they need to play it. I don't think DRM s the solution for anything. I think it's a step backward. So, how does that pertain to artists? I think that as labels become less important, it's going to be less of an issue because people will have a closer relationship to their artists and will like to support their artists. Most artists are not worried about people stealing their music; they're just worried about people hearing their music. The people who are really concerned are the labels, because they're the ones who are really profiting from record sales. At some point, hopefully, the label won't be relevant, and it'll get back to sort of a decent state. But there're a lot of problems with that because it's hard to find music when everybody's independent. WN: Yeah, that'll be the next killer app, right? Frankel: Well, yes and no. Yeah, maybe at some point. WN: On your site, it looks like you're like putting out a song every couple of days and as somebody who makes music myself and never gets around to it ... what's your secret? Frankel: Well, I do two different kinds of things: First, I have a group of friends and we all like to play together.... I'm also in a band with my brother and Kristoph who also works for Cockos, and we rehearse and occasionally play a show. On top of that, when I'm at home, I have a friend in Hoboken, who I'll send stuff, and he'll record some vocals over it and send it back (links on the first page of this story showcase some of these songs). And since I've been working on the digital-audio workstation software for the last year, a lot of what I do is just use it, and when I want to do something and it's not the way I want it to be, I'll go fix it. So it's a nice feedback loop between programming and making music as well. The secret for making quantity of music is just lowering your standards. That's it. Play a lot and experiment and don't be afraid to post something that's bad, because there'll be good things about it too. And also, I always encourage people to collaborate -- even if it's online. Post some music you made and see if someone wants to rap on it. It can be great; people can come back and add things you would have never thought of, and amaze you. WN: A collaboration, that's what Ninjam is about too, right? Frankel: Ninjam is more about jamming with other people live. It delays everything by a certain amount. Actually synchronizing people would be very difficult because even with a Skype conversation, where you have 100 milliseconds latency -- for a voice conversation this is not a big deal. But for music, that's an eternity. (Ninjam works by getting everyone) playing at 120 beats per minute with a click track, then delaying everybody else's track by two measures. WN: I have one question that I hope isn't obnoxious. What is the most extravagant thing you've bought since you sold Nullsoft? Is your house looking like Cribs (the TV show) by now, or are you keeping it pretty low key? Frankel: Nothing too crazy. I was into cars for a while, but I'm not so much anymore. But I didn't like go and get a Ferrari or anything, yet. WN: Or a Hum-Vee. Frankel: Yeah, or that. I bought a statue of a llama. It's made out of barbed wire and it weighs about 300 pounds and it's flexible, so whenever we move it, people get injured. WN: What is up with the llama? Where did that come from? (Nullsoft's mascot is a llama.) Frankel: I think it originally came from someone who e-mailed us saying "Winamp whips the llama's ass!" That was, I think, an homage to Wesley Willis. And then it just kind of went from there, but at some point along the way, I actually met some llamas, and llamas are awesome! They are so cool, and theyre very cute too. WN: Isn't there a danger llama's spitting? Frankel: I think it's only really when you piss them off.... Like, if you're nice to them, I don't think they really spit at you. From October 2006 http://www.wired.com/politics/online.../2006/10/71876  1,700 Bands, Rocking as the CD Industry Reels Jon Pareles “I don’t want to feel like I don’t have a future,” sang the Shout Out Louds, one of more than 1,700 bands that have been performing day and night at Austin’s clubs, halls, meeting rooms, parking lots and street corners since Wednesday. The Shout Out Louds, from Stockholm, were singing about a romance, but they could have been speaking for thousands of people attending the 22nd annual South by Southwest Music Festival. It is America’s most important music convention, particularly for rising bands, gathering a critical mass of musicians and their supporters and exploiters from the United States and across the world. While major labels have a low profile at this year’s gathering, other corporations are highly visible, using sponsorships to latch on to music as a draw and as a symbol of cool. Southwest is a talent showcase and a schmoozathon, a citywide barbecue party and a brainstorming session for a business that has been radically shaken and stirred by the Internet. For established recording companies, the instantaneous and often unpaid distribution of music online is business hell; CD album sales are on an accelerating slide, and sales of downloads aren’t making up for the losses. But for listeners, as well as for musicians who mostly want a chance to be heard, the digital era is fan heaven. As major labels have shrunk in the 21st century, South by Southwest has nearly doubled in size, up to 12,500 people registered for this year’s convention, from 7,000 registered attendees in 2001, not including the band members performing. In an era of plummeting CD sales and short shelf lives even for current hit makers, the festival is full of people seeking ways to route their careers around what’s left of the major recording companies. Sooner or later, public forums and private conversations at this year’s festival end up pondering how 21st-century musicians will be paid. For nearly all of them, it won’t be royalty checks rolling in from blockbuster albums. Musicians’ livelihoods will more likely be a crazy quilt of what their lawyers would call “alternative revenue streams”: touring, downloads, ringtones, T-shirts, sponsorships, Web site ads and song placements in soundtracks or commercials. Festival panels offer practical advice on all of them, for career-minded do-it-yourself-ers. The key is to gain enough recognition to find an audience. Over its four days, SXSW, as the festival is called, is like MySpace moved to the physical realm: more music than anyone could possibly hear, freely available and clamoring to be heard. Major labels used to help create stars through promotion and publicity, but their role has been shrinking. Multimillion-selling musicians who have fulfilled their major-label contracts — Radiohead, the Eagles, Nine Inch Nails — are deserting those companies, choosing to be free agents rather than assets for the system that made them famous. Even a moderately well-known musician can reach fans without a middleman. Daniel Lanois, who has produced U2 and Bob Dylan and is also a guitarist and songwriter, noted during his set that he now sells his music directly online in high fidelity at the Web site redfloorrecords.com. “We can record something at night, put it on the site for breakfast and have the money in the PayPal account by 5,” he said. “With all due respect for my very great friends who have come up in the record-company environment, it’s nice to see that technology has opened the doors to everybody.” South by Southwest has insisted, ever since it started in 1987 as a gathering for independent and regional musicians, that major-label contracts have never been a musician’s only chance. Musicians who have had contracts are lucky if they recoup their advances through royalties. Lou Reed, who gave an onstage interview as a convention keynote, was terse about getting a label contract. “You have the Internet — what do you need it for?” There’s never a shortage of eager musicians. Many bands drive cross-country by van or cross an ocean to perform an unpaid showcase at South By Southwest, and the most determined ones play not only their one festival slot but also half a dozen peripheral parties as well, hoping to be noticed. Sixth Street and Red River, two downtown streets lined with clubs, are mobbed with music-hopping pedestrians until last call. Musicians make the trek even though discovering a local band from another town or another country is just a few clicks away. That spread of information opens new career paths, from tours stoked by blog buzz to recognition for a song tucked into a commercial or a soundtrack. South by Southwest draws like Ingrid Michaelson and Sia got big breaks through songs that appeared in television shows, while Yael Naim found an international audience through a MacBook Air commercial. With music whizzing across the Internet, South by Southwest probably has fewer completely unknown so-called baby bands, but hundreds of more toddlers. They have unlikely allies now. If record labels can’t help them, corporations might. Few musicians worry about selling out to a sponsor; now it’s a career path. This year’s festival has brand-name sponsors everywhere, from Citigroup and Dell to wineries, social-networking Web sites and the chef Rachael Ray (who is the host of her own day party). Governments subsidize bands from countries including Australia, Norway, Spain and Britain, which see new markets and trade value in music. Radio stations are also active. Two well-established bands, R.E.M. and My Morning Jacket, played through their coming albums at packed South by Southwest shows that were broadcast live on National Public Radio and can be streamed at nprmusic.org/music — giving away new songs they know full well will soon be bootlegged. The logic is that fans who hear them will show up for concerts, pick up T-shirts and perhaps even buy the studio versions. But for many of the performers at South by Southwest, the ambitions are on a smaller scale: just to be heard. Casey Dienel is the 23-year-old songwriter, pianist and wispy-voiced singer of White Hinterland; her gentle melodies carry tales of visionary transformations. She said she was at the festival just hoping that “if you put yourself out there authentically, you’re going to attract people who think like you.” Looking at her rapt audience of perhaps three dozen people, she smiled shyly. “There are so many of you!” she said. http://www.nytimes.com/2008/03/15/ar...hp&oref=slogin  SXSW: Lou Reed, No Fan of MP3s Jon Pareles Lou Reed has been writing songs for at least four decades and counting. But in his keynote address at South by Southwest, a casual onstage interview with his producer Hal Willner, he said he still doesn’t know how. “I don’t know how it works or why it works or what it has to do with anything,” he said. “The thing I’ve got going for me is instinct. I can feel it; I try not to think. Thinking won’t get me where I want to go.” He talked about his song “Rock Minuet,” which has a gruesome scenario of violence and kinky sex, saying people had asked, “Is this stuff real?” Mocking the idea that a songwriter needed “qualifications for lyrics,” he said, “I have a B.A. in dope.” He paused. “And a Ph.D. in soul.” Mr. Reed, who has long been a perfectionist about sound quality, has no love for the ubiquitous mp3. “You have the world open to you now,” he said. “You can get almost any song in the world as an mp3. Then you can try and find a version of it that you can actually listen to if you like good sound.” He added, “The technology is taking us backwards. It’s making it easier to make things worse.” http://artsbeat.blogs.nytimes.com/20...o-fan-of-mp3s/ Until next week, - js.  Current Week In Review  Recent WiRs - March 8th, March 1st, February 23rd, February 16th Jack Spratts' Week In Review is published every Friday. Submit articles, press releases, questions and comments to jackspratts (at) lycos (dot) com in plain text English. Submission deadlines are Thursdays @ 1400 UTC. Please include contact info. The right to publish all remarks is reserved. "The First Amendment rests on the assumption that the widest possible dissemination of information from diverse and antagonistic sources is essential to the welfare of the public." - Hugo Black |
||
|
|

|
 |
| Thread Tools | Search this Thread |
| Display Modes | |
|
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| Peer-To-Peer News - The Week In Review - September 22nd, '07 | JackSpratts | Peer to Peer | 3 | 22-09-07 06:41 PM |
| Peer-To-Peer News - The Week In Review - May 19th, '07 | JackSpratts | Peer to Peer | 1 | 16-05-07 09:58 AM |
| Peer-To-Peer News - The Week In Review - December 9th, '06 | JackSpratts | Peer to Peer | 5 | 09-12-06 03:01 PM |
| Peer-To-Peer News - The Week In Review - September 16th, '06 | JackSpratts | Peer to Peer | 2 | 14-09-06 09:25 PM |
| Peer-To-Peer News - The Week In Review - July 22nd, '06 | JackSpratts | Peer to Peer | 1 | 20-07-06 03:03 PM |