
 |
|
|||||||
| Peer to Peer The 3rd millenium technology! |
 |
|
|
Thread Tools | Search this Thread | Display Modes |
|
|
#1 | |
|
Join Date: May 2001
Location: New England
Posts: 10,016
|
Since 2002
 In CONGRESS, July 4, 1776 The unanimous Declaration of the thirteen united States of America, When in the Course of human events, it becomes necessary for one people to dissolve the political bands which have connected them with another, and to assume among the powers of the earth, the separate and equal station to which the Laws of Nature and of Nature's God entitle them, a decent respect to the opinions of mankind requires that they should declare the causes which impel them to the separation. We hold these truths to be self-evident, that all men are created equal, that they are endowed by their Creator with certain unalienable Rights, that among these are Life, Liberty and the pursuit of Happiness. --That to secure these rights, Governments are instituted among Men, deriving their just powers from the consent of the governed, -- That whenever any Form of Government becomes destructive of these ends, it is the Right of the People to alter or to abolish it, and to institute new Government, laying its foundation on such principles and organizing its powers in such form, as to them shall seem most likely to effect their Safety and Happiness. Prudence, indeed, will dictate that Governments long established should not be changed for light and transient causes; and accordingly all experience hath shewn, that mankind are more disposed to suffer, while evils are sufferable, than to right themselves by abolishing the forms to which they are accustomed. But when a long train of abuses and usurpations, pursuing invariably the same Object evinces a design to reduce them under absolute Despotism, it is their right, it is their duty, to throw off such Government, and to provide new Guards for their future security. --Such has been the patient sufferance of these Colonies; and such is now the necessity which constrains them to alter their former Systems of Government. The history of the present King of Great Britain [George III] is a history of repeated injuries and usurpations, all having in direct object the establishment of an absolute Tyranny over these States. To prove this, let Facts be submitted to a candid world. He has refused his Assent to Laws, the most wholesome and necessary for the public good. He has forbidden his Governors to pass Laws of immediate and pressing importance, unless suspended in their operation till his Assent should be obtained; and when so suspended, he has utterly neglected to attend to them. He has refused to pass other Laws for the accommodation of large districts of people, unless those people would relinquish the right of Representation in the Legislature, a right inestimable to them and formidable to tyrants only. He has called together legislative bodies at places unusual, uncomfortable, and distant from the depository of their public Records, for the sole purpose of fatiguing them into compliance with his measures. He has dissolved Representative Houses repeatedly, for opposing with manly firmness his invasions on the rights of the people. He has refused for a long time, after such dissolutions, to cause others to be elected; whereby the Legislative powers, incapable of Annihilation, have returned to the People at large for their exercise; the State remaining in the mean time exposed to all the dangers of invasion from without, and convulsions within. He has endeavoured to prevent the population of these States; for that purpose obstructing the Laws for Naturalization of Foreigners; refusing to pass others to encourage their migrations hither, and raising the conditions of new Appropriations of Lands. He has obstructed the Administration of Justice, by refusing his Assent to Laws for establishing Judiciary powers. He has made Judges dependent on his Will alone, for the tenure of their offices, and the amount and payment of their salaries. He has erected a multitude of New Offices, and sent hither swarms of Officers to harass our people, and eat out their substance. He has kept among us, in times of peace, Standing Armies without the consent of our legislatures. He has affected to render the Military independent of and superior to the Civil power. He has combined with others to subject us to a jurisdiction foreign to our constitution and unacknowledged by our laws; giving his Assent to their Acts of pretended Legislation: For Quartering large bodies of armed troops among us: For protecting them, by a mock Trial, from punishment for any Murders which they should commit on the Inhabitants of these States: For cutting off our Trade with all parts of the world: For imposing Taxes on us without our Consent: For depriving us, in many cases, of the benefits of Trial by Jury: For transporting us beyond Seas to be tried for pretended offences: For abolishing the free System of English Laws in a neighbouring Province, establishing therein an Arbitrary government, and enlarging its Boundaries so as to render it at once an example and fit instrument for introducing the same absolute rule into these Colonies: For taking away our Charters, abolishing our most valuable Laws, and altering fundamentally the Forms of our Governments: For suspending our own Legislatures, and declaring themselves invested with power to legislate for us in all cases whatsoever. He has abdicated Government here, by declaring us out of his Protection and waging War against us. He has plundered our seas, ravaged our Coasts, burnt our towns, and destroyed the lives of our people. He is at this time transporting large Armies of foreign Mercenaries to compleat the works of death, desolation and tyranny, already begun with circumstances of Cruelty and perfidy scarcely paralleled in the most barbarous ages, and totally unworthy the Head of a civilized nation. He has constrained our fellow Citizens taken Captive on the high Seas to bear Arms against their Country, to become the executioners of their friends and Brethren, or to fall themselves by their Hands. He has excited domestic insurrections amongst us, and has endeavoured to bring on the inhabitants of our frontiers, the merciless Indian Savages, whose known rule of warfare, is an undistinguished destruction of all ages, sexes and conditions. In every stage of these Oppressions We have Petitioned for Redress in the most humble terms: Our repeated Petitions have been answered only by repeated injury. A Prince whose character is thus marked by every act which may define a Tyrant, is unfit to be the ruler of a free people. Nor have We been wanting in attentions to our British brethren. We have warned them from time to time of attempts by their legislature to extend an unwarrantable jurisdiction over us. We have reminded them of the circumstances of our emigration and settlement here. We have appealed to their native justice and magnanimity, and we have conjured them by the ties of our common kindred to disavow these usurpations, which, would inevitably interrupt our connections and correspondence. They too have been deaf to the voice of justice and of consanguinity. We must, therefore, acquiesce in the necessity, which denounces our Separation, and hold them, as we hold the rest of mankind, Enemies in War, in Peace Friends. We, therefore, the Representatives of the united States of America, in General Congress, Assembled, appealing to the Supreme Judge of the world for the rectitude of our intentions, do, in the Name, and by the Authority of the good People of these Colonies, solemnly publish and declare, That these United Colonies are, and of Right ought to be Free and Independent States; that they are Absolved from all Allegiance to the British Crown, and that all political connection between them and the State of Great Britain, is and ought to be totally dissolved; and that as Free and Independent States, they have full Power to levy War, conclude Peace, contract Alliances, establish Commerce, and to do all other Acts and Things which Independent States may of right do. And for the support of this Declaration, with a firm reliance on the protection of divine Providence, we mutually pledge to each other our Lives, our Fortunes and our sacred Honor. Signed, New Hampshire: Josiah Bartlett, William Whipple, Matthew Thornton Massachusetts: John Hancock, Samual Adams, John Adams, Robert Treat Paine, Elbridge Gerry Rhode Island: Stephen Hopkins, William Ellery Connecticut: Roger Sherman, Samuel Huntington, William Williams, Oliver Wolcott New York: William Floyd, Philip Livingston, Francis Lewis, Lewis Morris New Jersey: Richard Stockton, John Witherspoon, Francis Hopkinson, John Hart, Abraham Clark Pennsylvania: Robert Morris, Benjamin Rush, Benjamin Franklin, John Morton, George Clymer, James Smith, George Taylor, James Wilson, George Ross Delaware: Caesar Rodney, George Read, Thomas McKean Maryland: Samuel Chase, William Paca, Thomas Stone, Charles Carroll of Carrollton Virginia: George Wythe, Richard Henry Lee, Thomas Jefferson, Benjamin Harrison, Thomas Nelson, Jr., Francis Lightfoot Lee, Carter Braxton North Carolina: William Hooper, Joseph Hewes, John Penn South Carolina: Edward Rutledge, Thomas Heyward, Jr., Thomas Lynch, Jr., Arthur Middleton Georgia: Button Gwinnett, Lyman Hall, George Walton  "It's not clear that we really need patents in most industries." – Judge Richard Posner "After 15 years of loyalty, I’m done with Cisco/Linksys." – Joel Hruska "It's time to give [Acta] its last rites." – David Martin, European MP July 7th, 2012  Independence Day Acta: Controversial Anti-Piracy Agreement Rejected by EU BBC The European Parliament has voted to reject the Anti-Counterfeiting Trade Agreement (Acta). The proposed agreement sought to curb piracy, but internet campaigners said it posed a threat to online freedoms. The rejection vote followed a failed attempt to postpone the decision because of ongoing investigations into Acta by the European Court of Justice. Euro MP David Martin said: "It's time to give [Acta] its last rites." Twenty two EU member states, including the UK, had signed the Acta treaty - but it had not been formally ratified. Outside the EU, the treaty also had the support of the US, Australia, Canada, Japan, Morocco, New Zealand, Singapore and South Korea. However, following significant protests, several countries chose not to back the treaty. Wednesday's vote is seen by most observers as the final blow to the treaty in its current form. It means no member states will be able to join the agreement. A total of 478 MEPs voted against the deal, with 39 in favour. There were 165 abstentions. 'Hello democracy' EU Trade Commissioner Karel De Gucht said work into tackling piracy would continue. "Today's rejection does not change the fact that the European Commission has committed itself to seeking answers to the questions raised by the European public," he said. "The European Commission will continue to seek the legal opinion of the European Court of Justice on whether this agreement harms any of the fundamental rights of European citizens - including freedom of speech. "European citizens have raised these concerns and now they have the right to receive answers. We must respect that right." As the decision was made, some of those in attendance held banners reading: "Hello democracy, goodbye Acta". The UK's Pirate Party had campaigned against Acta since details of the treaty were first made public. In a statement, leader Loz Kaye said he was pleased that politicians "listened to the millions" of people who had sent messages in protest. "The European Parliament vote is a triumph of democracy over special interests and shady back-room deals," Mr Kaye said. "Without this opposition, our representatives would have waved this agreement through. It is now clear that it is becoming increasingly politically poisonous to be 'anti-internet'." http://www.bbc.com/news/technology-18704192  Speak Out Against Copyright Holders Destroying True Property Rights Mike Masnick For a while now, we've been following a series of very scary court cases that could take away your ability to sell physical products you own, by using a bizarre interpretation of copyright law by the courts. You can click back on that link to read some of the background, but the short version is that courts are suggesting that if a physical product is manufactured outside the US, but anywhere on it includes something covered by copyright (an etching, content, software, etc.) then the entire product cannot be sold without permission from the copyright holder. The reasoning makes so little sense as to be unbelievable. Basically, it says that those products weren't made under US copyright law -- so they don't get "first sale" rights -- but they are still covered by copyright law, so selling them is copyright infringement. This is nonsensical for any number of reasons. Unfortunately, the Supreme Court is about to hear the latest such case, after ending up with a split court the last time around. The reason it was split was because Justice Kagan recused herself, due to being involved in the case prior to becoming a Justice. Her involvement? Penning the filing of the US government against first sale rights. So it's very possible that she'll continue to retain that viewpoint on the court and basically kill off your ability to resell any good manufactured outside the US without permission. This is scary stuff. While the issue is before the court, it's still important to get people to speak out about this. A few public interest groups have put together a petition site called You've Been Owned: Don't Let Copyright Trolls Steal Our Property Rights! and Citizens for Ownership Rights. The goal is to get the Obama administration to actually recommend preserving first sale rights (contrary to its earlier position). And, failing that, get Congress to change the laws to fix this problem which will drive many American manufacturers to move overseas. This is, of course, part of the real problem: the language of the statute is awkward in a way that lets the court come to a completely nonsensical and contradictory result. What's important to recognize is that, for all the talk by copyright maximalists to falsely claim that copyright is no different than real property, and to insist we must "defend property rights" for copyright, here's a true case of property rights being under attack -- and it's because of an overly aggressive use of copyright. The idea that you don't actually own what you bought is an anathema to true property rights. That companies may be able to use copyright law to block you from selling used goods is a massive encroachment on individuals' property rights. If all those copyright maximalists truly believed in property rights (rather than the truth: that they support a government granted monopoly privilege that benefits themselves) they, too, would support this effort against the demolition of first sale rights. http://www.techdirt.com/articles/201...y-rights.shtml  Used Software Can Be Sold, Says EU Court of Justice Sique An author of software cannot oppose the resale of his "used" licenses allowing the use of his programs downloaded from the internet. The exclusive right of distribution of a copy of a computer program covered by such a license is exhausted on its first sale. This was decided [Tuesday] by the Court of Justice of the European Union in a case of Used Soft GmbH v. Oracle International Corp.. http://yro.slashdot.org/story/12/07/...urt-of-justice  Intellectual Property Rights: the Quiet Killer of Rio+20 Rory Crump U.S. Secretary of State Hillary Clinton speaks at the plenary of the Rio+20 United Nations Conference on Sustainable Development summit in Rio de Janeiro June 22, 2012.Richard Phillips, president of the Intellectual Property Owners Association, sent a powerful message to Washington the day before the Rio+20 UN Conference on Sustainable Development regarding the U.S. intellectual property community’s stance on sharing IPR with developing nations. Philips argued any language included in the Rio+20 final declaration compromising the existing IP regime would discourage investment and destroy trade secrets. “Any references to technology transfer should be clearly qualified and conditioned to include only voluntary transfer of IPR on mutually agreed terms.” The IPO has no interest in helping developing countries transition to a more sustainable economy if it means sacrificing valuable IPR. And the IPO’s chilly message set the tone for what many pundits and participants considered a disappointing Rio+20 conference yielding few substantive results. Owning the majority of climate-related patents, companies in North America, Western Europe and Japan view intellectual property as a key driver to commercial innovation, and an immeasurable advantage in the green marketplace. Developing countries lack the research base and viable technologies required to build a green economy and hoped Rio+20 would create a new mechanism for technology transfer. Developed nations hold the secrets and developing nations want access to them. And they don’t want to pay market rates. Both sides agree green innovation and technology are bridges to a more sustainable planet. But the U.S. and its Rio+20 allies remain defiant, not willing to surrender first-mover advantages in a nascent industry already subject to mercantilism and IP theft. So in a fruitless effort, negotiators from over 180 nations handed attendees -- including 100 or so heads of state -- a 49-page document called “The Future We Want.” Watered down and vague, the text included “reaffirm” 59 times and reflected the contentious nature of the event. Nothing much got accomplished, and the sour outcome left doubts to whether big global conferences focused on the environment still serve a purpose. “The Future We Want” is a placeholder for the next world gathering, and does not contain the future developing nations want.Brazil's President Dilma Rousseff (L) shakes hands with China's Premier Wen Jiabao after a meeting at Rio+20. If Rio+20 was dead on arrival then what are the prospects for developing nations needing green infrastructure and financing -- and also IPR. The Group of 77 plus China represents the developing nations, and is looking for international support and consensus. Some members claim wealthier nations controlling technology created an environmental crisis and should bear the burden of mitigating it. And countries like the U.S. control most of the patents, create most of the greenhouse gases, therefore should provide critical resources for sustainable development across the globe. And technology transfer is central to the Group of 77 plus China’s argument. Developing nations hoped Rio+20 would rouse the spirit of the 1992 Rio Earth Summit, considered at the time a boon for international collaboration and alignment on key environmental issues. Agenda 21 was a byproduct of the event and developing nations still rally around the technology transfer verbiage included in the document. However, using Agenda 21 as a baseline for climate-related technology transfer can devalue intellectual property rights as a barrier to success. Clean energy infrastructure requires capital, local capacity requires skill, and innovation requires a host of conditions including education and investment. If those elements were manufactured -- or aided -- through tangible, subsidized resources, then how does a developing country acquire intellectual property, the missing link? IP has become a blood sport in tech-driven industries and IBM, Samsung and Apple don’t use it for gifts. Assuming a green blueprint for a developing country, technologies in the public domain hold promise. Money, direction and joint planning from an international fund could power a startup industry or retrofit an old one. Future technologies could follow a similar path, with international support fostering an independent research environment, while allocating technology based on merit. But patents are complex, litigious and carry a certain level of sanctity. Patents are also expensive for a developing country to buy or develop. To remove these obstacles, savvy Group of 77 leaders point to flexible terms in the WTO TRIPS agreement for issuing compulsory licenses. Compulsory licenses, in a broader context, are typically associated with extraordinary circumstances like a health-related epidemic. But the TRIPs agreement contains language commensurate with a developing country’s desire for climate-related, cost-prohibitive technology. Follow this logic and you no longer have to declare an environmental state of emergency to receive a compulsory license. Just claim the patent holder’s price is out of your budget. This partisan strategy is an example of what makes the IPO go into isolation. Giving away any IPR that undermines the U.S. legacy of innovators and risk takers is taboo and threatens our competitive advantage of getting to market first and securing premium prices. Many climate-related technologies are immature, far from reaching market potential. For green investors and entrepreneurs, the financial upside is too great and the risk is exclusive. And green companies building industrial applications are not selling generic products. Wires are crossed in this debate. A disconnect exists somewhere between capitalism and egalitarianism. Yes, Rio+20 spoke to the environment on a grander scale and the U.S. delegation may have missed an opportunity to exploit its IP advantage in a public forum, but green lines have been drawn and technology transfer will remain a combative subject. The U.S. advocates investing in education, research, employees and -- of course -- embracing a free, open market buoyed by tempered regulation and protected intellectual property rights. The U.S. now becomes distant and noncommittal when met with global pressure from environmentalists, activists and events like Rio+20. In fact, President Obama chose campaigning over Rio while both German Chancellor Angela Merkel and British Prime Minister David Cameron stayed at home, too. Technology transfer, in its purest, most profitable sense is proving to be non-negotiable. And China posing as a developing country does not elevate the Group of 77’s position in the eyes of those holding all the technology. Among the developing nations’ protests, feelings of oppression by the oppressor are becoming more commonplace. Accusations of imperialist motives by imperialist nations are growing. All of this rhetoric and propaganda may eventually reveal a different reality, a different objective for developing nations hamstrung by a lack of green know-how. Everyone agrees certain targeted measures are necessary to ensure a more stable planet. And the U.S. does offer a solution rooted in private investment, market dynamics and self-reliance. But the U.S. thinks intellectual property and involuntary transfers of technology are incompatible, and the omission of more progressive text in “The Future We Want” takes climate-related technologies off the geopolitical stage for the foreseeable future. Making a case for sustainable development, international agreements may no longer be galvanizing, relevant or binding. Developing countries could use an amiable push. And a greener economy based on market forces is a hopeful alternative. But at what point does intellectual property simply become foreign aid? http://www.patexia.com/feed/intellec...io-20-20120702  Fastest Growing Segment of Piracy? Live TV Laura Hazard Owen A new Google study entitled “The six business models for copyright infringement,” just released with the UK’s PRS (Performing Right Society) for Music, finds that live TV is the fastest-growing segment of copyright infringement. (To see the others, click on the image at right.) Global pageviews of live TV sites were up 61 percent for the year ending May 2012. Live TV sites link to illegal streams of network and paid TV. The study looked at 51 live TV sites — it doesn’t mention any of them by name, but a couple of popular ones are Sidereel.com and TVDuck.com, which feature a mixture of legal and illegal content — and found that a third of them are based in the United States. Two-thirds of the sites are funded by advertisers, and “compared to the other segments Live TV Gateway has very high levels of direct access and referrals from social networks.” Live TV sites are more likely than the other business models to have mobile sites and social network presence “in the form of a social networking ‘action’ icon, for example Facebook ‘like’ buttons, Twitter ‘tweet’ button or similar.” P2P Sites Still Get the Most Visitors Researchers looked at 29 P2P sites; again, while they are not mentioned by name, the largest gets 2.1 million unique UK visitors per month (compared to 1.1 million unique UK visitors at the most popular live TV site). The UK-based study didn’t track monthly U.S. visitors by site, but did look at global page views across categories, using data provided by Google. P2P sites are the most dependent on advertising of any of the business models looked at: 86 percent of them are funded by advertising. Overall, “both Live TV Gateway and P2P Community sites, the two largest and fastest growing segments, tended to link to content on other sites or services rather than host the content,” the researchers found. To fight piracy, “follow the money” Theo Bertram, Google’s UK policy manager, said in a statement: Our research shows there are many different business models for online infringement which can be tackled if we work together. The evidence suggests that one of the most effective ways to do this is to follow the money, targeting the advertisers who choose to make money from these sites and working with payment providers to ensure they know where their services are being used. The research was conducted by BAE Systems Detica, and you can view the full report here (PDF) http://paidcontent.org/2012/07/03/fa...iracy-live-tv/  Megaupload Founder Goes From Arrest to Cult Hero Jonathan Hutchison Last month, a New Zealand software developer, Ben Gracewood, replied to a Twitter post from the Internet tycoon Kim Dotcom, founder of the Megaupload file-sharing site that had been shut down by the F.B.I. He asked whether “you guys just drive around in modified electric vehicles and pose for photos,” referring to an image Mr. Dotcom, 38, had just posted showing three of his associates with golf buggies and a Segway. “I could live like that,” Mr. Gracewood wrote. Twenty minutes later he got a surprising response: “Come over now!” So he took a friend and went to the most expensive house in the country — a mansion worth 30 million New Zealand dollars, or $30.7 million, rented by the German national — for a swim and some cupcakes. Twitter users across New Zealand watched with fascination as the group posted updates and photos of the visit. That evening, which was followed on Twitter under #swimatkims , was just the latest in a series of at times bizarre developments in a case that has turned Mr. Dotcom into something of a cult hero since his arrest. In January, two police helicopters landed on his lawn to raid the luxury property just north of Auckland. At that time, most of the country had never heard of Mr. Dotcom, despite his flamboyance and wealth. He had kept a low profile in the two years he had been living in this country of about 4.4 million people. The police operation — carried out under New Zealand’s extradition treaty with the United States — seemed designed to attract attention. It was accompanied by uncharacteristically detailed media releases describing the operation, including how officers had cut their way into a panic room to arrest Mr. Dotcom, who, they said, was found sitting near a shotgun. Mr. Dotcom and three others connected with Megaupload were arrested in connection with U.S. indictments on charges involving copyright infringement and money laundering. At the time, the U.S. Department of Justice said that in all, seven people had been arrested around the world in connection with the alleged online piracy of numerous copyrighted works, including music and films. The Department of Justice said the individuals and two companies — Megaupload and Vestor — had been charged with “engaging in a racketeering conspiracy, conspiring to commit copyright infringement, conspiring to commit money laundering and two substantive counts of criminal copyright infringement.” Later this month, Mr. Dotcom’s U.S. lawyers are set to appear before a Virginia judge in a bid to have the criminal case dismissed. According to a document on his lawyers’ Web site, they will argue, among other points, that the indictments are invalid because they must be submitted to a company’s U.S. office, which Megaupload has never had. The four men arrested in New Zealand are still on bail, awaiting an extradition hearing, which is scheduled to begin Aug. 6. Among the items seized by the police in the January raids were 18 luxury vehicles worth 6 million dollars — including a Rolls Royce Phantom Drophead Coupe and a 1959 pink Cadillac — computers and as much as 11 million dollars in cash. In an e-mail interview, Mr. Dotcom said he had been treated badly by the New Zealand police and the government, which he said he believed was simply kowtowing to U.S. requests. “Two helicopters and 76 heavily armed officers to arrest a man alleged of copyright crimes — think about that,” he wrote. “Hollywood is importing their movie scripts into the real world and sends armed forces to protect their outdated business model.” In February, the New Zealand police defended the operation, saying it had been in line with a risk assessment and there had been only “20 or 30” officers involved in the raid on the mansion. After a month of prison, Mr. Dotcom was eventually granted bail, despite prosecutors’ arguments that he was a serious flight risk. Over the following months his lawyers won a series of hearings to loosen the bail conditions and free up some of his confiscated cash to cover expenses. The biggest victory came Thursday, when a High Court judge ruled the New Zealand police had used the wrong type of search warrant, so the entire raid had been illegal. Mr. Dotcom’s lawyers are due back in the Auckland High Court Wednesday, seeking the return of seized assets and data. Dr. Gavin Ellis, a senior political studies lecturer at the University of Auckland, said that over time the public had become less supportive of the police operation. “Initially there was a sort of a ‘gee, whiz’ reaction. ‘Wow, look what the police have done, they’ve got this alleged master criminal,”’ Dr Ellis said. “But then, as the media perception of him and the media portrayal of him changed, looking backwards those things started to look heavy-handed.” While Mr. Dotcom’s lawyers were making steady progress in court, Mr. Dotcom was gaining the public’s favor. A headline on the news Web site Stuff.co.nz in May read, “Dotcom’s straight talk wins over Kiwis.” “There’s been a clear shift in the characterization of him, from this assumed criminality or alleged criminality, to a cult hero,” Dr. Ellis said. Mr. Dotcom gave his first television interview in March to the national current-affairs show Campbell Live, which dedicated its full half-hour program to the item. He appeared affable and composed, speaking articulately in near-perfect English, with a German accent that was noticeable but not strong. During that interview he described the U.S. indictment against him as “nothing more than a press release filled with things out of context, designed to make me look as bad as possible.” Speaking by e-mail on Monday, Mr. Dotcom said he was a “larger than life character,” but he said he had not sought fame or notoriety. “The people of New Zealand have made my family and me feel very welcome. They know that I have been treated unfairly. They know that the NZ leadership does anything to please the United States,” he wrote. “I used to respect the United States and the American dream,” he said. “Now I consider the United States the biggest threat to Internet freedom and peace in the world.” Three months after his arrest, Mr. Dotcom gained more public approval when he waded into the political arena himself. He disclosed a donation of 50,000 dollars that he had made to a right-leaning member of Parliament, John Banks, during Mr. Banks’s failed 2010 campaign for mayor of Auckland. Mr. Dotcom said Mr. Banks had phoned to thank him for the contribution, despite the donations’ listing as anonymous. The political storm that followed dominated the news for several days and threatened to upset the country’s coalition government, of which Mr. Banks is a small but strategically important part. All of this worked in Mr. Dotcom’s favor as well, Dr. Ellis believed, because many people “love to hate” Mr. Banks and his party. Mr. Banks’s press secretary, Shelley Mackey, said he maintained that the donations had been anonymous, that he had adhered to the law, and that he was looking forward to the outcome of a police investigation into the matter. But Mr. Dotcom said by e-mail he had considered Mr. Banks a friend and he wished the political fracas had never happened. “In terms of changing the perception of Kim Dotcom, you couldn’t pick a better politician,” Dr. Ellis said. “It’s all fitted into the increasing legitimization of Kim Dotcom, or the acceptability of Kim Dotcom. It was almost as if the gods were smiling on him,” he added. Until recently, Mr. Dotcom was forbidden to use the Internet under his bail conditions. After the court granted him access he began using Twitter on June 19, amassing more than 46,000 followers in just two weeks. John Key, New Zealand’s prime minister, has about 52,000. Mr. Dotcom has become a prolific user of social media, posting photos of his family as well as mocking the police operation and the legal case against him. He has also used Twitter and his newly relaxed bail conditions to increase his public profile, posting photos of himself at a popular concert, at the screening of a television show and attending a protest march against the closure of a state-funded television channel. Asked why he had become so active online, Mr. Dotcom said he was using the most efficient way to respond to all the good-will messages he had received. The day after #swimatkims, Mr. Dotcom said in a Twitter post that the event would return for “everybody.” “Need a big public pool,” he said. “Awesome DJ. Sound & lights. Who’s in?” https://www.nytimes.com/2012/07/04/t...cult-hero.html  FBI Continues To Insist There's No Reason For Kim Dotcom To Be Able To See The Evidence Against Him Mike Masnick We already noted that the New Zealand judicial system apparently isn't as willing as the US expected to rubberstamp approval of the extradition of Kim Dotcom. Part of that ruling was a requirement that the US turn over the evidence they're using against Dotcom, so that he can counter it in fighting against the extradition. However, it appears that the US is still fighting this, having the New Zealand prosecutor (who is fighting on their behalf) argue that Dotcom should only be allowed to see a single document out of the 22 million emails the FBI collected and that this really isn't a matter for the New Zealand courts to concern themselves with, as they should just let the Americans handle it. Crown lawyer John Pike argued that there was no need for Dotcom to have access because he was not being tried in New Zealand. The judge in the extradition case needed only to decide if there was a case for him to answer in the US, Mr Pike said, and that question was answered by the record of case. That's kind of amazing when you think about it. He shouldn't be allowed to even see the evidence against him... even if it might prove that there is no "case for him to answer to in the US." That's what's so troubling about the US position on cases like this one and the O'Dwyer/TVshack case. They seem to assume that it shouldn't be of any concern if they drag someone thousands of miles across oceans to face trumped up charges in the US. http://www.techdirt.com/articles/201...inst-him.shtml  BitTorrent Torque, JavaScript Interface to a Torrent Client Martin Brinkmann BitTorrent is without doubt the most popular file sharing solution on today’s Internet. While other file sharing solutions like Napster, Kazaa, Gnutella or eDonkey were either sued into oblivion, discontinued or turned into a commercial offering, BitTorrent thrived thanks to it not being dependent on a single website, service, tracker or software. Up until now, a BitTorrent client like uTorrent was needed to download and share files. The situation has become a bit better in recent times with web browsers like Opera implementing the torrent technology into the browser to make it more comfortable for users to download files. Yesterday BitTorrent Inc. announced the alpha release of BitTorrent Torque, a JavaScript interface to a torrent client that gives web developers the opportunity to go beyond traditional desktop clients. Btapp.js provides access to a browser plugin version of uTorrent/BitTorrent via a tree of Backbone Models and Collections. The intent of this project is to allow access to the extensive functionality of a torrent client, from web apps that are as simple as a single Backbone View. Btapp.js takes responsibility for getting the plugin installed as well, so you’re free to assume that its available. In addition to the local torrent client, you can also easily access a torrent client anywhere else in the world (assume you either configured it originally or have access to that client’s username/password). The company has released two demonstration applications: One Click is a Chrome plugin that turns torrents into regular browser downloads. For the user on the frontend, it looks like another download in the browser. Paddle Over is a web app that allows you to share torrent files with other users directly on the project website. This is also powered by a browser plugin that needs to be installed. The Torque Labs website highlights several other tech demos, including the streaming of video torrents directly in the browser or direct sharable links to files on the PC. Developers find information, including an introduction and getting started guide, here. Browser plugins need to be installed to get the tech demos to work. The One click app for instance is only available for Chrome, and appears to require a local executable to be loaded as well to work at all. A few questions are left unanswered right now as well. One of the foundations of Bittorrent is that downloaders are giving back to the community by seeding the files during downloads and afterwards. How will this be handled if users start downloading via a web browser and Torque? Also, will there be options to control and manage the downloads? For instance, can you modify the download or upload speeds (assuming that you are seeding while downloading)? http://www.ghacks.net/2012/07/07/bit...orrent-client/  VLC for Android Beta Finally Arrives, Plays Almost Anything on Your Android Device Alan Henry If you've been waiting for news on an Android version of VLC, wait no longer. The media player finally launched an Android beta today, and it brings VLC's trademark play-anything goodness, multi-track subtitle support, and even whole-library management tools to Android devices, but be warned: the developers make no bones about the fact that it's a beta, and there's a lot of work to be done on it. The first thing worth noting is that the VLC for Android beta is a port of the iOS version, largely to get a framework in place where the VLC mobile team can work from. They point out that everything about the app will change as it gets updated, including the UI and major features, and hardware decoding only works on a few devices at the moment. Even so, it's still VLC, can play just about anything (including network streams), supports multi-tack audio and video with subtitles, has a home-screen widget for audio control without launching the app, and it supports headsets with in-line audio controls. The developers point out that "It might kill your kitten, destroy your house and start the mayan apocalypse," and warn you to "Use at your own risk." They also point out that this version is for "power users and hackers," so while it worked great on the devices we tested, make sure your device is supported before trusting it with your media. It's definitely not as polished as our favorite media player for Android, MoboPlayer, but Android has no shortage of great media players, and hey—this is VLC! http://lifehacker.com/5922801/vlc-fo...android-device  Extra Millimeter on Google Nexus 7 Makes it More Repairable than iPad Jon Brodkin The sleek new Google Nexus 7 tablet is just a hair thicker than the iPad—but that's not a disadvantage at all for the tinkerers who like to pry gadgets open and fix them when things go wrong. According to the new iFixit teardown of the Nexus 7, it's an extra millimeter of thickness that makes all the difference in the world when it comes to repairability. While the iPad teardown gave Apple's tablet a repairability score of two out of 10 on the iFixit scale, the Android-based Nexus 7 received a score of, appropriately, seven, meaning it is much easier to repair. Opening the Nexus 7, if you have the right tool, is "like cutting through butter, thanks to its retaining clips around the perimeter of the device," iFixit wrote. "One millimeter. That's the difference in thickness between the 9.4 mm glued iPad and the 10.4 mm retaining-clipped Nexus," the iFixit team wrote. "That's the difference between being able to open a device and service all of its internals, and not. That's the negligible difference between extending the life of your device through repair, as opposed to tossing it in a landfill. And most of all, nobody will complain about that one millimeter difference in day-to-day use, but the user-serviceability it brings will make all the difference when the device breaks." For comparison's sake, the Kindle Fire is actually even easier to repair than the Nexus 7, with a score of 8. The Nook Tablet got a score of 6. So what's inside the Nexus 7? As you probably already know, the Nexus 7 has a 1.3GHz quad-core Tegra 3 processor, a 1280x800 IPS display, a 1.2-megapixel front-facing camera, 1GB of RAM, a 4235mAh battery, Bluetooth, WiFi, NFC, micro USB and 3.5 mm audio ports, and either 8GB or 16GB of storage depending on whether you want to spend $200 or $250. The battery, of course, takes up a large amount of space, iFixit found. The L-shaped motherboard is "littered with connectors and screws," but iFixit liberated it from the Nexus with its custom-made tools. 1GB of Hynix H5TC2G83CFR DDR3 RAM, the same model used in Apple's MacBook Pro with Retina Display, is on the motherboard as well as the Tegra 3 processor, GPS receiver, gyro and accelerometer, and more: The back side of the motherboard holds the Kingston brand flash storage and a few more chips and components. After being taken apart, the whole device looks like this: iFixit ran into a problem when it tried to separate the LCD from the front glass. "As is becoming a trend, the LCD is fused to the Corning glass.," iFixit said. 'Sadly, this fusion makes the cost of repairing shattered glass much higher, as it will require replacing the whole display assembly—LCD included." This problem knocked the Nexus 7 repairability score down a bit, but iFixit gave the device high marks for having an easily openable rear case, a battery that can be replaced without soldering or using a screwdriver, standard Phillips #00 screws, and various replaceable components including the I/O ports. While most people aren't likely to pry open a tablet, it is nice to know that the Nexus could potentially be repaired without shipping the whole thing back to Google. The Nexus is available for preorder and is scheduled to ship in two to three weeks. Look for our review soon. http://arstechnica.com/gadgets/2012/...ble-than-ipad/  Mobile Phone Firms Back Mozilla Firefox Rival to Android Tarmo Virki A new operating system for mobile phones akin to the Mozilla Firefox internet browser has got the backing of several major telecom companies, turning up the heat on Google and Apple in the smartphone market. Mozilla said on Monday that mobile network operators Deutsche Telekom, Sprint, Smart, Telecom Italia, Telenor and Etisalat are backing the Firefox platform. The non-profit organisation which evolved from Netscape after the internet browser wars 14 years ago, said phone makers ZTE and TCL Communication Technology will roll out the first Firefox OS phones using Qualcomm's Snapdragon processors in early 2013. Mozilla, which fosters the collective development of open-source Web applications, currently generates most of its income from a contract which makes Google the default search provider for Firefox users. Broad support from telecom companies and handset makers is crucial for any new smartphone platform to take off in a market increasingly dominated by Google's Android software, which has a market share of around 60 percent, while Apple's iPhones run on its proprietary iOS software. In addition to market leaders Android and Apple, a number of smaller players like RIM, Microsoft and Samsung's Bada are also competing for a share of the mobile software market. But Gary Kovacs, chief executive of Mozilla Corp, said he was confident there was room on the market for a Firefox platform, being an open Web-based alternative to the for-profit offerings from Google and Apple. "I think this will be very widely adopted," Kovacs told Reuters in an interview. After an initial launch with Telefonica's Vivo brand in Brazil early next year Firefox-powered phones will be launched on other emerging markets and then elsewhere, Kovacs said. Phone companies have tried before to create platforms to combat the growing dominance of Android, but have so far failed as they had to create from scratch the ecosystem around platform: developer tools, applications, developer community. "Success for any platform is dependent on the virtuous circle of scale and momentum. Manufacturer and operator commitment is essential to driving developer support and consumer interest which in turn strengthens demand for the platform," said Geoff Blaber, analyst at CCS Insight. The new Firefox platform aims to overcome the problem by tapping into a community of 3 to 5 million web developers and most of the apps are already created on HTML5, the preferred standard for creating mobile browser content. The sector has seen the demise of many rival platforms in the last few years, including operator-led initiatives like LiMo, and also Palm's WebOS and Nokia's Symbian operating systems which failed to win enough support from developers and device manufacturers. The free Firefox platform could put pressure on Microsoft and Google, which themselves are trying to attract handset manufacturers. But Microsoft collects licensing fees of up to $20 per Windows phone and also collects royalties from makers of Android devices. BOOMING MARKET TCL, which uses Alcatel brand for its phones, and ZTE are both hoping the new Firefox platform will help make up for their late entrance to the booming smartphone market. The growth in smartphone sales is slowing this year from the bumper years of 2010 and 2011 but is still expected to be running at some 40 percent from a year ago. Mozilla, which has been working with Telefonica on creating the software, demonstrated the platform and its key features in February at the Mobile World Congress trade show in Barcelona. The new platform combines HTML5 with some of the core elements of Linux technology, cutting the need for a separate operating system and enabling fast roll-out of new phone models. In competition with Mozilla's Firefox, Google has introduced its Chrome browser and browser-based operating system for personal computers. "The line between browser and operating system is getting blurred," Kovacs said. Cutting some layers of a traditional operating system allows the new platform to be used on smartphones with lower processing power and with lower cost materials. Telefonica has said the phone price will be significantly cheaper than the low-end Android models, meaning Firefox phones can be priced at levels around $50 excluding operator subsidies. This compares with price of around $200 for a typical smartphone. Ovum analyst Nick Dillon said pricing of the devices will be the key for their success, and questioned whether cutting out some layers of operating system would bring significant savings. "It is hard to see how you could make them much cheaper than comparable Android handsets," Dillon said. (Editing by Greg Mahlich) http://www.reuters.com/article/2012/...8610NP20120702  Microsoft Slashes Windows 8 Upgrade Pricing - Because It Can’t Afford Not To Antone Gonsalves Once again demonstrating the importance of Windows 8 to its future, Microsoft has cut the upgrade price by some 90% compared to previous versions of Windows. Rather than charge Windows 7 upgrade prices of up to $220, Microsoft plans to sell the upgrade for Windows 8 Pro for less than $40 - at least during a promotional period. The discount upgrade offer, announced Monday, is good for anyone currently using a legitimate version of Windows XP, Windows Vista or Windows 7. Once the upgrade is purchased online, Microsoft’s Windows 8 Upgrade Assistant tool will walk the customer through the process from download to installation. And customers can add Windows Media Center for no additional charge. Betting the Company on Windows 8 In dramatically lowering pricing for its latest Windows upgrade, Microsoft is both demonstrating how far it is willing to go to get customers to upgrade to Windows 8 - and ripping a page from Apple’s OS X upgrade playbook. Microsoft has apparently decided that getting people to upgrade en masse to an operating system that reflects a major shift in emphasis from PCs to tablets is more important than the additional profit it would make on each individual download. The most dramatic change in Windows 8, and the feature Microsoft is most counting on people to use, is the Metro interface, which will be the front-end for smartphones and tablets running the Windows 8 version for tablets. PC users will have the option of clicking through Metro to an update of the classic Windows interface, but Microsoft is hoping they’ll fall in love with the new interface. Metro uses what Microsoft calls “active” tiles to provide quick access to various applications and functions. Experts mostly agree that it is an effective and attractive method for making use of scarce real estate on the small screen of a smartphone or tablet. On the PC, it has gotten mixed reviews, with some experts saying that the sea of tiles on a large monitor look jumbled and confusing. [http://www.readwriteweb.com/archives...r-the-bus.php] Nevertheless, for Microsoft, Metro is the future. The company is counting on those tiles to steer users to the apps and services Besides, consumers are not flocking to desktops and notebooks like they once did. All-in-one PCs and ultrabooks have failed to excite consumers who continue to snatch up smartphones and tablets at a much faster rate than PCs. Microsoft is banking that Metro - in combination with Window 8 for mobile devices - will keep Windows users from turning to Apple iPads iPhones and Google Android smartphones and tablets. Breaking with it’s past history, Microsoft can no longer afford to let price be a barrier to Windows 8 adoption, no matter the short-term hit to the bottom line. If Microsoft fails to encourage Windows 8 adoption, Windows' overall importance will continue to fade - and so ultimately will the company’s profits. The company has been criticized in the past for making upgrades almost as expensive as new installations, and for not giving extra discounts to consumers who shelled out for the previous version. With Windows 7, for example, Vista users paid just as much to upgrade as XP users. Users of newer versions of Windows don’t get a break on Windows 8 either, but with pricing below $40, it shouldn’t matter much. Current buyers of Windows 7 PCs can upgrade for $15. For comparison, When Windows 7 came out, Microsoft offered promotional upgrades to Home Premium and Professional for $49 to $99, Today, those upgrades coss $199 for Windows 7 Professional and $120 for Windows 7 Home Premium. Following Apple’s Model Ironically, though, this new approach clearly follows Apple’s pricing lead. For years, Apple has made upgrading inexpensive for Mac customers, in order to get as many people as possible to use the new features on the latest platform. That helps Apple lead its customers in whatever direction the company is taking its products. Recently, that direction has pointed to the cloud with storage, music and video, along with tighter integration between its iPhone, iPad and Macs. Apple plans to ship the latest version of Mac OS X - Mountain Lion - this month, with upgrades costing just $20. Of course, some older PCs may not have the muscle to run Windows 8. Microsoft promises that the Upgrade Assistant will check to make sure it does. In addition, the tool will provide a detailed compatibility report that will warn customers of any potential software or device problems. People upgrading from Windows 7 will be able to carry over Windows settings, personal files and applications. Vista can share its settings and personal files, while XP users will be able to move only their personal files to Windows 8. And after the download is installed, users can add Windows Media Center for free via an “add features” option. If you want Windows 8 Pro on physical media, you’ll have to pay $70. The promotional pricing for downloads and DVDs runs through Jan. 31, 2013. No word on what the pricing will be after the promotional period. Windows 8 is expected to ship in the fall. http://www.readwriteweb.com/archives...ord-not-to.php  N.J. ACLU Unveils 'Stealth' App Allowing Citizens to Secretly Record Police Eunice Lee A new smartphone app, called Police Tape, allows citizens to have at their fingertips the ability to secretly digitally record law enforcement officials and upload the incident to the American Civil Liberties Union of New Jersey for review and to be saved to an external server. For years, the American Civil Liberties Union has aggressively tried to police the police, filing suit after suit against law enforcement agencies it believed crossed the line. Now, the ACLU’s New Jersey chapter has gone beyond the courtroom, introducing a smartphone application to allow state residents to secretly record police stops, protect the recordings from being deleted by displeased officers and report the incidents to civil rights groups. "This app provides an essential tool for police accountability," said Deborah Jacobs, executive director of the ACLU of New Jersey. The arrival of the app, called Police Tape, follows some high-profile cases in which police have clashed with citizens over their recording of officers. It also speaks to the notion that, anywhere, any time — whether it’s by a police department’s security camera or a motorist’s cell phone — everyone can be recorded. Citizens have been hassled and even arrested after recording police officers in public places, said Alexander Shalom, ACLU New Jersey’s policy counsel. At times, their phones have been taken away and recordings deleted, he said. "Police often videotape civilians and civilians have a constitutionally protected right to videotape police," Shalom said. "When people know they’re being watched, they tend to behave well." The app, which debuts only for Android devices but will be available for iPhones later this month, is simple to use and can be downloaded at aclu-nj.org/app. It opens to a screen with three buttons: video recording, audio recording and a tutorial on knowing your rights. The app’s signature feature is its ability to operate in "stealth mode" while recording. When you start video recording, the screen goes black, as if it's off. When recording audio, the app automatically minimizes and disappears. The issue of recording police on smartphones has drawn controversy in Newark, where then 16-year-old Khaliah Fitchette recorded two officers aiding a man on a public bus in March 2010. Police removed Fitchette from the bus and handcuffed her after she refused to stop filming, according to a lawsuit filed on behalf of the teen by the ACLU and the Seton Hall Center for Social Justice last March. After a three-hour ordeal, Fitchette was released to her mother, the lawsuit says. New Jersey is only the second state to have this type of app available to smartphone users, Shalom said. The app developer, a watchdog group called OpenWatch, calls these types of programs "reverse surveillance." New York Civil Liberties Union introduced a similar smartphone app last month called "Stop and Frisk Watch," a reference to the New York Police Department’s controversial search practices. Recordings are protected from erasure because it’s not readily apparent how to delete without going through a multi-step process. Incidents sent to the ACLU via the app get reviewed and also saved to an external server. The iPhone version will only have an audio recording option. Chris Tyminski, longtime president of Policemen’s Benevolent Association Local 183, which represents Essex County sheriff’s officers, said an app like this can "blindside" a law enforcement officer but maintained, "We have nothing to hide." "Guys are basically told, conduct yourself as if you’re always being recorded, that’s the safest way," he said. However, he said, it’s unfair when groups like the ACLU "judge a life or death split second decision that a cop makes, when they have days and days and roundtables to discuss what a cop should have done in those three seconds." James Stewart, president of the Newark Fraternal Order of Police, said people using the app also need to use common sense. "I also hope that if a police officer is attempting to stop an individual on the street, that person is not suddenly trying to pull a phone from his pocket in an attempt to film a police encounter," he said. Shalom agrees that the majority of law enforcement don’t need to worry about the app. "Police officers who break the rules, who don’t behave, are the exception not the rule," he said. "It’s only the minority of officers who are flouting the rules who should be concerned about the app." http://www.nj.com/news/index.ssf/201...th_app_al.html  Cisco’s Cloud Vision: Mandatory, Monetized, and Killed at Their Discretion Joel Hruska Last week, a number of Cisco customers began reporting problems with three specific Linksys-branded routers. When owners of the E2700, E3500, are E4500 attempted to log in to their devices, they were asked to login/register using their “Cisco Connect Cloud” account information. The story that’s emerged from this unexpected “upgrade” is a perfect example of how buzzword fixation can lead to extremely poor decisions. Cisco E4500According to Cisco, the Connect Cloud gives users “anytime, anywhere” access to their router, delivers free, new apps, and “will keep expanding with new apps to enrich your connected lifestyle.” The E2700, E3500, and E4500 all shipped with the “Automatic Firmware Update” option selected, which is why so many users found themselves asked to authenticate using a different account with no prior warning. Unplugging the router from the wall restored the old login/password function, but only offered a simplified menu structure that removed or obfuscated control of a number of advanced functions. The second major problem with Cisco’s Cloud Connect is its “supplemental privacy policy.” This policy is an addition to Cisco’s Privacy Statement. As of June 27, the fifth paragraph read as follows: When you use the Service, we may keep track of certain information related to your use of the Service, including but not limited to the status and health of your network and networked products; which apps relating to the Service you are using; which features you are using within the Service infrastructure; network traffic (e.g., megabytes per hour); Internet history; how frequently you encounter errors on the Service system and other related information (“Other Information”). This paragraph has been excised entirely from the current version of the Supplemental Privacy Policy, but that proves nothing — Cisco has the right to update its privacy policy at any time, without legal penalty. Both versions of the document contain a further statement that may raise a few eyebrows. The next-to-last sentence reads: “In some cases, in order to provide an optimal experience on your home network, some updates may still be automatically applied, regardless of the auto-update setting.” In a plot twist that could’ve been predicted by an eight-year old, users were enraged at having their routers stealth-updated, angry at being forced to register for a cloud service that provides no benefit whatsoever, concerned about privacy implications of the original Privacy Supplement, and unhappy at being initially told that there would be no way to roll back to the earlier firmware. Cisco has since retracted this and has provided a public link to the old firmware and a detailed guide on updating the router. Profound disconnect between company, users This botched attempt to capitalize on “the cloud” is Cisco’s latest attempt to sexify its product lines and build brand presence. Consumer routers, unfortunately, are neither inherently sexy nor big enough to drape a booth babe over. Even if you somehow manage the latter, it does terrible things to your wireless signal strength. Cisco Connect Cloud is somehow supposed to solve this problem, despite offering no new features compared to a traditional router. We’ll let the company tell you in its own images… Note that everything under “Built In Apps” are features that non-cloud routers have offered. Of the listed apps, only two “Block the Bad Stuff” and “NetProofer” are currently available. BtBS is described as “Easily add one of three levels of protective filtering to your wireless network” while NetProofer “empowers users to restrict the access of specific websites on their home network.” Shouldn’t those functions be part of the same dubious, ineffective program? This is nothing but a shameless attempt to cash in on the popularity of cloud computing, and it comes at a price. The Terms and Conditions of using the Cisco Connect Cloud state that Cisco may unilaterally shut down your account if finds that you have used the service for “obscene, pornographic, or offensive purposes, to infringe another’s rights, including but not limited to any intellectual property rights, or… to violate, or encourage any conduct that would violate any applicable law or regulation or give rise to civil or criminal liability.” It then continues “we reserve the right to take such action as we (i) deem necessary or (ii) are otherwise required to take by a third party or court of competent jurisdiction, in each case in relation to your access or use or misuse of such content or data. Such action may include, without limitation, discontinuing your use of the Service immediately without prior notice to you, and without refund or compensation to you.” Since the Service is the only way to access your router, killing one would effectively kill the other. Thoughtless, greedy, and consumer-hostile Linksys built its brand on reasonably priced, widely compatible routers with decent performance, idiot-proof setup, and a few frills at the upper end of its product mix. As of last week, buying a new Linksys router means being forced to adopt a “cloud” service that offers no benefits, allows Cisco to snoop your Internet history, and gives the company the power to control access to hardware you legally purchased. That’s not what users signed up for, and no collection of apps or GUI improvements is going to change that. The increasingly dubious Megaupload seizure and the way the government held dajaz1.com for an entire year are evidence that neither corporations nor the federal government can be trusted to perform due diligence in their investigations or in seizing evidence. In such a climate, it would be insane to buy into a service like this. After 15 years of loyalty, I’m done with Cisco/Linksys. http://www.extremetech.com/computing...eir-discretion  Indiana's Sewers: An Outpost on the Internet of Things David Strom An unlikely place to look for the latest trend for the Internet of Things is inside the sewers of the City of South Bend, Indiana. For the past six years, South Bend's city managers have been working with a group of consultants from IBM, nearby Notre Dame University and others to instrument the city's sewers as a means of delivering better service and saving hundreds of millions of dollars in capital improvements. South Bend was facing more than $600,000 in potential government Superfund fines to bring its system up to par and had also experienced a series of regular overflows. Rather than build expensive new capacity, the city embarked several years ago on a project to do a better job monitoring its sewer conditions in both dry and wet weather. To do this, it needed to invent cheaper and better sensor technology that it could literally insert into the pipes and connect to a real-time monitoring system. "We needed sensors which were more economical and higher-definition than our traditional systems," said Gary Gilot, a member of South Bend's Board of Public Works (BPW). The city eventually built a monitoring system of more than 100 sensors, conceptualized by city engineers and developed in Notre Dame's engineering school, and deployed them throughout South Bend's 500 miles of sewers. Like many sewer districts, the South Bend BPW had been using 50-year-old mechanical valve technology to operate the system and direct water flows through the city's pipes. The new technology (pictured above) enables the city managers understand the demands and actual real-time usage and flows. "At a glance, we can see in real time what is happening across our entire system," Gilot said. "We are also able to examine how our system behaved in previous years when we had an inch of rain, so we can be better prepared now." Spend $6 Million, Save $120 Million The annual sewer operating budget is about $30 million; South Bend invested about $6 million in the monitoring project and estimates it has saved $120 million in infrastructure improvements. Not a bad return on investment! The city is now able to do a better job predicting and responding to basement backups in low-lying areas; using its new residential basement “heat map,” South Bend can now direct utility cleaning crews to areas where they are most likely to be needed. And through the new monitoring capabilities, the city has also been able to reduce the flow of water through its treatment plants by up to 10 million gallons of water per day. The city didn't just decide to instrument its sewers overnight. "We had to convince the mayor, and it took some time," Gilot said. "We first set up our sensors in the lab and then next tried in the lakes near Notre Dame." When these demonstration projects were successful, the sewer department set up a trial at one place in the system that had some overflow problems. The trials allowed South Bend to work out problems before a full deployment. For instance, placing the sensors inside pipes buried in the ground meant that it was hard to get radio signals out of the sewers. "We had to use our manhole covers as transmitters so we could get the sensor data out of our pipes," Gliot said. The city also needed to work on parsing all of the sensor data and creating visualizations to make the information useful and actionable. The South Bend project represents the next stage of the Internet of Things - individual sewer pipe valves that can be tracked and controlled, with the added layer of data visualization to make it manageable and actionable. The city government is now looking beyond its sewers and seeing what else it can instrument to save money and deliver better services to its residents. That has certainly caught the eye of many other sewer and water districts facing similar circumstances. http://www.readwriteweb.com/enterpri...-of-things.php  A Love Letter to the Cable Guy, or How Really Fast Broadband Changes Everything Fredric Paul You might think your existing broadband Internet connection is fast enough. It’s not. When it comes to Internet speeds, more is always better. That’s why we all owe some sincere gratitude to the intrepid men and women who bring truly high-speed Internet into our homes. This post is a message of sincere appreciation - a love letter if you will - to the cable guy who recently upgraded the Internet connection in my San Francisco home. Whether you know it or not, you’ve made my life better in so many ways. I’ve had broadband access at my home since DSL came to San Francisco in the 1990s. So I didn’t think getting faster service would make all that much of a difference in my life. Boy was I wrong. My family and I just upgraded our cable Internet service from about 10 Mbps to 50 Mbps. And then we bought a new Wi-Fi router to extend that service to all our wireless devices. Now, 10Mbps isn’t that slow, and 50Mbps is far from the fastest service around (heck, ReadWriteWeb’s headquarters clocks in at an awesome 100Mbps). But I am still stunned at how much the change is affecting how we all use the Internet. And how much I want to hug the Astound cable guy who brought it to us. Easy Upgrade Compared to the early days of broadband, the process was amazingly simple. The Astound technician came out to our 115-year-old Victorian with a new Cisco DPC3010 cable modem (actually showing up in the first half hour of the promised 4-hour window!) The tech replaced our old unit and checked out the cabling in less than an hour. Bam, the speed of our hardwired connections instantly quintupled! No fuss, no muss. Except that the increase was only visible on wired connection, not the fleet of smartphones, tablets, laptops and other devices where we do most of our work (and play). They got a bump to about 20Mbps. Faster, but suddenly pokey next to the wired connections. Even though we had a relatively recent Belkin router using the modern 802.11n Wi-Fi specification, it simply couldn’t keep up. The tech - remember how much I love him? - recommended getting a new router that supported the DOCSIS (Data Over Cable Service Interface Specification) 3.0 standard. And because we have a mix of Apple, Windows and other devices in the house, my spouse decided to choose simplicity over economy and we splurged for an Apple AirPort Extreme Wi-Fi router. Although its $179 price is almost double that of competing devices with similar specs, it was by far the easiest router to install and configure that I’ve ever used. Everything was up and running within five minutes, with none of the false starts and geeky questions I’ve encountered setting up other wireless systems over the years. I wouldn’t have chosen it, but I can’t say I missed the headaches. More importantly, though, suddenly every device in the house was testing out at 50Mbps downloads. Faster Everything The conventional wisdom holds that just about any broadband connection is sufficient for browsing the Web, and that faster connections don’t really provide much benefit in this regard. Thanks to our cable guy, I can confidently state that conventional wisdom is dead wrong. Web browsing at 50Mbps is noticeably faster and less annoying than browsing at 10Mbps. In most cases, pages begin loading faster and images show up along with the text, not a second or two later. Downloading large files, from software applications to data sets to high-resolution images is now something we do in real time, rather than a process we start and let run in the background. If general browsing got a mild boost from the faster speeds, working with Software as a Service (SaaS) applications delivered over the Internet enjoyed a serious kick in the pants. Gmail and Google Docs suddenly seemed almost as fast as email or productivity software running on a local machine. Better Streaming Perhaps the biggest, most noticeable improvement came when consuming streaming content. At 50Mbps, YouTube and other online videos leap into action, instantly jumping ahead with plenty of buffer room. Nice to see on the desktop, but positively intoxicating on an iPad or other tablet, which now seems seamlessly connected to the entire Internet. (I murmur soft words of thanks to the cable guy every time I watch anything on a tablet.) I now find that I want to have the iPad close at hand at all times, because it’s just so darn easy to watch anything online as soon as I can type it in. Just as important, I’m now wondering why I need a tablet with 64GB of storage space when I can grab stuff from the Net just as quickly. (That makes my new Google Nexus 7 tablet seem more inviting.) Not surprisingly, that holds true when using streaming media services - whether on a computer, iPad or big-screen TV. Services such as Hulu or HBO Go perform almost as well as our satellite TV service - and our Apple TV box delivers a more TV-like experience than ever before. If it weren’t for live sports, I’d already be considering cutting the cord. (I worry that the cable guy wouldn't like that, though.) Better Backups and Sharing All of the members of my household rely on Dropbox to sync and share files, and some of us even pay for extra space. And one of us relies on Apple’s iCloud to sync huge chunks of data among many devices. But syncing all that data to new devices used to take hours, and it churned through much of our 100GB per month data cap. No more. At 50Mbps down and 6Mbps up, those syncs and backups happen much faster. Syncing and backing up to the cloud now seems like a much more reasonable option than it used to. Upload speeds are often the Achilles' heel of cloud services, but 6Mbps is fast enough to help ease the bottleneck. Still, if the cable guy wants me to buy him chocolates, it would be nice to have upload speeds closer to the downloads. Bigger Data Limits When you add up all this stuff, it’s pretty clear that my family is likely to churn through a lot more bandwidth every month - and we were already incurring fees by exceeding our old plan’s limit of 100GB per month. The new plan ups our data transfer limit to 300GB per month, but with the extra speed encouraging all these new uses, we’re actually worried we may blow past that figure as well! We made the switch because we cycle through a lot of data in our house, and it seemed to make sense. But I think we were all surprised at how much a five-times boost in speed changed the quality and quantity of our Internet usage. I’ve become an instant convert to the idea that the future of the Internet requires that everyone get not just broadband, but really fast broadband. I hear that Verizon FiOS now offers up to 300Mbps. A week ago, I would have said that’s ridiculous. Now I’m wondering if those speeds will ever be available in San Francisco (if not from FiOS, which apparently won't be built out any more than it already has been, then from another provider). Sorry cable guy, I appreciate how much you’ve done for me, but if the phone company guy shows up with six times faster service, I’m going with him. http://www.readwriteweb.com/cloud/20...everything.php  Verizon Urges Court to Scrap Net-Neutrality Rules Brendan Sasso Verizon filed a brief in federal court on Monday in its lawsuit to overturn the Federal Communications Commission's (FCC) net-neutrality rules. Verizon argued that the FCC had overstepped its authority when it adopted the rules in 2010. The telecom company also claimed the regulations are "arbitrary and capricious," as well as unconstitutional. The net-neutrality rules prohibit Internet service providers from blocking or slowing down access to legitimate websites. Supporters of the rules say they preserve competition and consumer choice, but opponents argue they are an unnecessary burden on businesses and amount to government control of the Internet. The D.C. Court of Appeals, which is hearing Verizon's challenge, ruled against the FCC when it tried to enforce the principle of net neutrality against Comcast in 2010. That setback led the FCC to enact its current regulation later that year. In Monday's filing, Verizon argued that instead of "proceeding with caution" in light of the Comcast ruling, the FCC adopted rules that "go even farther than its prior action and impose dramatic new restrictions on broadband Internet access service providers." "Here again, the FCC has acted without statutory authority to insert itself into this crucial segment of the American economy, while failing to show any factual need to do so," Verizon wrote. The company argued that Congress never authorized the FCC to regulate Internet access and that the agency acted without sufficient evidence to suggest the rules were necessary. Verizon claimed that the rules violate its First Amendment free speech rights. "Broadband networks are the modern-day microphone by which their owners engage in First Amendment speech," Verizon wrote. The company also argued the rules violate the Fifth Amendment by forcing broadband network owners to allow others to use their private property for free. MetroPCS is also suing the FCC over the rules and joined in many of Verizon's arguments. An FCC spokesman said the agency looks "forward to defending our open Internet rules in court." "This strong and balanced framework is helping ensure that the Internet continues to thrive as an engine for innovation, investment, job creation, and free expression,” the agency spokesman said in an email. The FCC's legal response is due in September. http://thehill.com/blogs/hillicon-va...utrality-rules  It Only Took the Army 16 Years and 2 Wars to Deploy This Network Spencer Ackerman Starting in October, some soldiers — represented by this dummy in the Pentagon courtyard — will carry a Motorola Atrix like the one strapped to the dummy’s chest, enabling them to send and receive data while dismounted in warzones. Photo: Spencer Ackerman/Wired.com In October, the Army will do something it’s wanted to do for more than a decade: send a pair of combat brigades to a warzone equipped with a new data network, and the hardware to operate it. It’ll let more than a thousand troops rapidly send voice, text, imagery and data across a warzone and to a soldier on patrol. It’s a milestone, following years of aspirations, setbacks and adjustments. And it arrives pretty much too late for the wars. When the 3rd and 4th Brigade Combat Teams of the 10th Mountain Division reach Afghanistan in October, between 1,200 and 1,400 soldiers will take with them a rejiggered Motorola Atrix running Android that’s the heart of a communications program called Nett Warrior. When they go out on patrol, their devices will load mapping applications layered with data about where they are and where their buddies are. When they encounter insurgents, homemade bombs or Afghan civilians, they’ll be able to record that information, which will appear on those digital maps as icons dotting layers of data. Using the Rifleman Radios plugged into their Motorola devices, they’ll be able to transmit that data in a series of relays from one radio to another, across their units, into their trucks and back to their company headquarters. When the data reaches the computers within a tactical operations center, their captain and first sergeant will be able to see their battlefields like never before, as they change, in near-real time. And those officers will be able to ping that picture up the chain of command, to the battalion and then brigade headquarters — and, should a colonel decide it’s necessary, onward and upward, all the way back to the Pentagon, thousands of miles away. And it works both ways. When the captain decides that there’s information at his or her level that a squad leader needs to know — say, a suspicious car moving at a high rate of speed toward the squad, captured on video from an Army drone overhead — the captain can send it out to the squad leader. A new icon will appear on the mapping app on the Atrix. “This is a capability we have never, ever been able to provide,” says Brig. Gen. John Morrison, one of the key figures behind the Army’s new data network, called the Warfighter Information Network-Tactical, or WIN-T. He’s not kidding: WIN-T has been in the works since 1996. For most of that time, it lived as the dream of Pentagon officials — and the frustrations of soldiers in confusing, arduous fights in Iraq and Afghanistan, who didn’t have the tactical information they needed when they needed it. Army colonels and generals who announced the deployment of WIN-T to Afghanistan at the Pentgon on Thursday used terms like “sea change” to describe it. Only that change may have come too late. In order to develop WIN-T, the Army had to tear up its playbook for how it develops, well, everything. When the Army wants a new tank, it determines the specifications it needs, figures out of those specs are realistically deliverable, picks a contractor to build it, tests it once it’s built, and then starts to buy it and send it out to the units who’ll drive it. You can’t buy IT gear this way. Nett Warrior is an example. It began life in the mid-1990s as a different program called Land Warrior. In order to connect dismounted soldiers to the data they needed, the Army’s idea was to strap them full of wearable computers, with dangling banana-shaped keyboards and monocles strapped to their helmets displaying maps, all cabled together in a cumbersome get-up that weighed over a dozen pounds. By 2010, when the renamed Nett Warrior had been panned by the few soldiers who used it, the program had less computational power than an iPhone, which could fit in a soldier’s pocket. And it still hadn’t gone to war. But developing Nett Warrior was hard enough. A different Army office developed the Rifleman Radios that were supposed to be how the wearable computers to the outside world. Another one worked on what waveforms the Army should use. Another one worked on providing deployed soldiers with the bandwidth necessary for them to communicate. The costs ballooned; the deadlines slipped; and the network never arrived. About 18 months ago, the Army decided — thanks in large part to its former vice chief of staff, Gen. Peter Chiarelli, an iPhone enthusiast — that it needed to develop the whole network, all at once, and test it all at once, so soldiers wouldn’t discover in the middle of a firefight that the network didn’t work as advertised. That led to a series of tests at the White Sands Missile Range in New Mexico and Fort Bliss, Texas, appropriately called Network Integration Exercises. Among the lessons: shrink Nett Warrior down to a smartphone loaded with apps. (Well, a smart device; the 3G/4G and the Wi-Fi capabilities of the device are disabled for data-security purposes and you can’t make a call on it.) Don’t demand the defense industry produce gear that will quickly become archaic; buy existing tech off the shelf instead. Hughes isn’t married to the Atrix: He envisions a newer smartphone forming the basis for Nett Warrior maybe every year or every other year. Design tactical operations centers, or TOCs, that can be boxed up and moved closer to the fight, so as to ease the strain on the network. Newer TOCs that the brigades from the 10th Mountain will take to Afghanistan this fall can be moved in three hours; when the Network Integration Exercises began, it took 12. The Army estimates these tests saved it $6 billion. “Just think of the power” that soldiers will be able to tap into, Morrison beams. Now comes the hard part — taking it to war. A closer view of the data displayed through the Army’s Warrior Information Network-Tactical, displayed on a giant flatscreen in a tactical operations center — this one on display in the Pentagon courtyard. Photo: Spencer Ackerman/Wired.com WIN-T works well at White Sands, swear Morrison and Col. Dan Hughes, the Army’s director for systems integration and an amateur app designer. But however accurate and exacting the training scenarios for the network have been, Afghanistan is an acid test. Even technology that tests perfectly has a habit of breaking in wartime — especially if that technology has lots of moving parts, like WIN-T and Nett Warrior. Then come the usage issues. A young, bored soldier with an Atrix in his hand might be tempted to send his buddy a funny video he shot. Stopping that, to some degree, is a matter of an alert sergeant growling at him to knock it off. But there’s also a technological solution: Back at the TOC, the captain’s staff will be monitoring for potential bandwidth hogs — especially if they seem to come from anomalous sources. More related to a mission, Hughes concedes that sending video out to a dismounted soldier’s Nett Warrior device is “harder to do,” given the file size and available bandwidth. That video might have to stay in the TOC, while the key bits of data become icons on the Atrix’s networked maps. Finally, there are issues that technology can’t solve. Brig. Gen. Randall Dragon, head of the Army’s Brigade Modernization Command, says that the key data soldiers need are “where are my buddies, where is the threat, and where do I put effective fires.” But in a counterinsurgency like Afghanistan, a soldier on patrol may not know if the Afghan giving him the thousand-mile stare is an insurgent or a civilian. That complicates his ability to create a red — enemy — icon on his mapping application. Hughes says the soldier can input an icon annotated to clarify that the Afghan’s status is unknown — but quickly concedes that technology can’t fix basic intelligence problems. Still, WIN-T has field-tested a number of anticipatable problems. Hughes says the data that soldiers send and receive is encrypted at multiple points, unlike drone video was in Iraq. The Army’s working on procedures to make sure that it isn’t bombarded with data, like the Air Force was when it started shooting terabytes’ worth of full-motion video from loitering drones. “The guys in the TOC, we don’t need to see everything,” says Maj. Shane Sims, another officer working on WIN-T. The most bittersweet part of the imminent WIN-T deployment is the calendar. The Iraq war was one of the longest in American history, and it came and went without a modern Army data network. Danger Room boss Noah Shachtman wrote a blog post speculating that WIN-T might be deployed ahead of schedule; that blog post was published in 2005. The Afghanistan war, the longest war in American history, is winding down. The Army wants to outfit a total of eight brigades with WIN-T over the next two years. They will probably be the last combat brigades of the war. Networking soldiers was a major priority of the Army before 9/11 in a labyrinth of programs called Future Combat Systems that proved to be an expensive failure. WIN-T will surely undergrow growing pains when it actually meets the trial by fire in Afghanistan. It might only truly be a mature network after the Army is done with the war — leaving open the question of how relevant will be in the next one. What remains foremost in the mind of the officers, themselves war veterans, that developed the network is how they and their soldiers needed something like WIN-T for the past decade and didn’t have it. “We took a lot of shortcuts,” says Maj. Gen. Gennaro Dellarocco, who runs the Army’s Testing and Evaluation Command. “We’ve paid for it, dearly, literally, with lives.” http://www.wired.com/dangerroom/2012...twork-war/all/  Hacker Claims to Have Breached & Backdoored Antivirus Software Firm Trend Micro A hacker claims to have breached and backdoored security and antivirus software firm Trend Micro due to 'pseudo-security' as well as SYKES which runs support services for Trend Micro. According to Pastebin and a dump for 'proof' of the breach, the hacker claims to still be in control of a backdoor into the security firm. Ms. Smith Antivirus and security firm Trend Micro was the latest victim in what seems like never-ending hacks, dumps and hacker wars. Also named was SYKES, a company that allegedly runs support services for Trend Micro. The SYKES site states that it is "a global leader in providing customer contact management solutions and services in the business process outsourcing (BPO) arena." Trend Micro & Sykes @OfficialComrade tweeted a Pastebin link that claims Trend Micro now has a backdoor that the hacker controls and the companies were targeted due to their "pseudo-security." It also linked to a 156MB dump that when unzipped is about 492MB and contains 28 DBX files. The Pastebin states: Quote:
Last week, the FBI arrested "24 suspected hackers in a sting operation spanning four continents that targeted online financial fraud of stolen credit card and bank information." Reuters reported that Islam "was charged with trafficking in 50,000 stolen credit card numbers. Authorities said Islam had admitted to helping emerging hacker outfit UgNazi, which said it had launched a cyberattack against the microblogging platform Twitter." https://www.networkworld.com/communi...box-backdoored  First iOS Malware Discovered in Apple App Store David Gilbert A Russian security company has uncovered what it claims is the first case of malware to be found in Apple's App Store. Kaspersky Lab has published a report on its Securelist blog about an app named 'Find and Call' which is a piece of malware which steals your phonebook details and sends spam SMS messages to all your contacts, claiming to be from you. Only last week the iPhone celebrated its fifth birthday and security experts were congratulating Apple on preventing malware from entering the App Store, thanks in the main to its walled-garden approach. Kaspersky Lab has contacted Apple regarding the malware but so far the app has not been removed from the App Store [as of 15:32 on 6 July]. Like us on Facebook The malicious Find and Call app was also found in the Android Google Play store, though instances of malware on the Android platform are altogether more common. The app description is very muddled, and doesn't really tell you what the app does: "Find and call is a new technology for your mobile phone. For the first time in the world, you may not only make calls from your mobile phone, but also search for subscribers you need. Free calls from your mobile phone to domains, email, Skype, social networks. Forget about numbers!!!" It seems to be a translation from another language into English. The app is aimed at smartphone users, and it was a tip from Russian mobile phone network Megafon which alerted Kaspersky Labs to the presence of the malicious app. Initially the security company believed it to be an SMS worm, spread via sending short messages to all contacts stored in your phonebook, with a URL linking to itself. Further inspection however revealed that both versions were pieces of malware known as Trojans which install themsevles on your phone and upload your phonebook details to a remote server. The server then generates spam SMS messages to send to all your contacts, but when the messages are received, it looks like they came from your mobile number. Once installed, if you launch the app you will be asked to register within the app using your emails address and mobile phone number, though both these input fields will not be checked for validity. If the users then asks to 'Find Friends in the phonebook', all the data will be secretly sent to a remote server. There is no terms of usage or notifications alerting you to this happening. Both Android and iOS apps are also able to upload the users GPS coordinates but this is something which legal as well as malicious apps do all the time. Once the phonebook details are uploaded, every one of your contacts will receive a spam message which looks like it is from your number. The message contains a URL which asks users to download the app themselves. Kaspersky Lab expert Denis Maslennikov did some checking on who is behind the app and discovered on the app's website that once you've signed in, it will ask you for your social network details and email address, which will also be used maliciously it seems, and even your Paypal details. Further investigation shows if you do add money from your Paypal account, you send the money to a company called Wealth Creation Laboratory, which has the motto "Let's create together the world of plenty and prosperity." http://www.ibtimes.co.uk/articles/35...-find-call.htm  Developers: Don’t Push Any Updates to the App Store Right Now, Cause It’s Apparently Kinda Busted Specifically, something funky is going on with updates and the approval process. Kelly Faircloth We leave the Internet for 24 hours, and this happens: Something is seriously wrong with Apple’s app store. As in, if you updated Instapaper or Angry Birds Space HD Free yesterday, there’s a good chance it just crashed upon launch. Users are having to perform clean installs, while developers are dealing with annoyed users who assume the fault lies with the app itself. No one wants to do either of those things while recovering from a holiday hangover. Instapaper creator Marco Arment kicked up the initial fuss with a rather disgruntled blog post. As he tells it, no sooner had Apple approved the latest Instapaper update than Mr. Arment received a flood of customer complaints that the app was no longer working. He wrote: This didn’t make sense — obviously, Apple had reviewed it, and it worked for them. My submitted archive from Xcode worked perfectly. But every time I downloaded the update from the App Store, clean or not, it crashed instantly. Lots of anxiety and research led me to the problem: a seemingly corrupt update being distributed by the App Store in many or possibly all regions. So much for that vaunted review process. Mr. Arment immediately emailed App Review and, while he hasn’t heard anything back, within a couple of hours anyone attempting a reinstall got a working version. The developers at GoodReader, a PDF-reading app, confirmed the troubles in a blog post and added, “It appears that Apple has recently changed something in their app distribution engine, and ever since that change there are ongoing problems at Apple’s end.” We’ve reached out to Apple for comment and will update if we hear anything. It’s not clear what created the problem, which means we’ve got no way of knowing whether it’s been fixed. Several apps now appear to be updating properly, but as of last night, the Verge found at least a couple of the apps on Mr. Arment’s list still demonstrating the aforementioned wonkiness. And as of this morning, Mr. Arment is still warning developers via Twitter that, “if you can help it, DO NOT release app updates today. The corruption is widespread and ongoing,” adding later than the list of corrupted apps currently stands at 73. Every developer that ever had problems getting an app approved is cackling so hard right now. http://betabeat.com/2012/07/develope...rently-busted/  The Business and Politics of Piracy Rory Cellan-Jones The subject of online piracy arouses strong emotions, both from the creative industries and from web libertarians. But the fierce debates about the extent of the problem and what should be done have been short of one thing - data. So there should be a welcome for a big piece of research into piracy sites and how they are funded. This study was undertaken by the security firm Detica on behalf of two organisations which might not seem natural bedfellows, Google and PRS for Music, which represents songwriters. And what it shows is exactly what you might have suspected - that piracy is big business. The study identifies six different business models for online copyright infringement, and finds that advertising and subscription are very professionally integrated into many of the sites. Often, you will see the logos of well-known payment services on sites. The study found that many featured adverts from leading brands, though Google was keen to point out that the vast majority of the ads were not provided by the recognised networks from the mainstream industry. According to a report which sometimes struggles to speak plain English, the two fastest growing business models are Live TV Gateway and P2P community. The first turns out to mean sites offering unauthorised access to live television streams, principally Premier League football. Traffic to these sites - as measured by page views - is up 61% over the last year, with many visitors arriving from a social network. P2P community refers to file-sharing sites providing, says the report, a "well-organised range of content types offered free to the user". This sector of the "industry" is heavily dependent on advertising and donations, with 86% of sites featuring adverts. The report is packed with charts and numbers, though disappointingly short on individual case studies or big figures for the overall size of the industry. I did though find one really interesting number buried deep in the document. In talking about some of the methodology used, the researchers describe one site in their study as having 15 times the ad revenue of a licensed advertising-supported service. It turns out that total advertising revenues for licensed music services in the UK have been flat for some time at around £12m per year. No wonder services like We7 have failed to make much headway. Will Page, chief economist at PRS for Music, says the research is a reminder of just how tough it is for legal services: "There are only so many willing advertisers with only so much ad-spend and only so many sets of eyeballs which they can reach. Advertisers are wanting to reach music fans, and both legal and illegal are competing for them." But what is really interesting about this piece of research is the politics behind it. Google is in a battle with the BPI, the body which represents the music labels, over the shape of government legislation on piracy. The BPI says many consumers find copyright-infringing material through a Google search. It says the company makes money from advertising around search results, and wants piracy sites to be pushed further down the results, below legitimate music offerings. Google isn't keen to play around with its search algorithm. The search company, the BPI, and other parts of the internet and creative industries are taking part in government roundtable discussions about the battle against piracy. The research on the piracy sites was commissioned to inform the roundtables. Now Google is stressing that the message from the study is "follow the money". If you want to do something about piracy, go after the advertisers and the credit card firms rather than worrying too much about search. PRS for Music, which takes a more moderate line on this issue than the BPI, said it hoped the research would "enable a more targeted and ultimately successful approach to tackling online copyright infringement." But I get the impression that the songwriters trade body is a bit nervous about the way that Google has spun the report as showing that search is not too relevant. The government has told both sides - the internet firms and the creative industries - that if they cannot come up with a voluntary code to tackle piracy there will have to be legislation. After the publication of this report, everyone seems to agree that copyright infringement is a very lucrative business - but they seem no nearer to an agreement on what exactly to do next. http://www.bbc.com/news/technology-18670734  For First Time Ever, US Seeking International Limits on Copyright Trans-Pacific Partnership proposal overturns years of precedent. Cyrus Farivar The United States Trade Representative (URTR) has proposed a new copyright provision that would address some intellectual property concerns found in the Trans-Pacific Partnership, a massive trade agreement currently being negotiated amongst nine Pacific Rim countries in San Diego this week. Canada was recently extended an invitation, but its formal membership has yet to be approved by the existing nine countries, including the United States. In a statement emailed to reporters on Tuesday, the USTR appears to be addressing exceptions to copyright restrictions, which had not been included in a TPP draft leaked a year ago. "For the first time in any US trade agreement, the United States is proposing a new provision, consistent with the internationally recognized ‘3-step test,’ that will obligate Parties to seek to achieve an appropriate balance in their copyright systems in providing copyright exceptions and limitations for purposes such as criticism, comment, news reporting, teaching, scholarship, and research," wrote Carol Guthrie, the spokesperson for the USTR, in an e-mail sent to Ars. "These principles are critical aspects of the US copyright system, and appear in both our law and jurisprudence. The balance sought by the US TPP proposal recognizes and promotes respect for the important interests of individuals, businesses, and institutions who rely on appropriate exceptions and limitations in the TPP region.” Historically, major intellectual property holders, such as the RIAA and MPAA—who both support the TPP—have called for stronger international copyright protection. Skeptical optimism That three-step test, which was established in international law in 1967, generally allows for exceptions to copyright restrictions that do not "conflict with a normal exploitation of the work and does not unreasonably prejudice the legitimate interests of the author." American IP law is, of course, imperfect. However, it does attempt to maintain a balance between strong enforcement mechanisms while also allowing for robust fair use and the public domain. But in IP treaties, all that tends to get exported from the American model are the restrictions, rather than the exemptions. As such, TPP watchers have cautiously applauded the move. "Recognizing the limitations and exceptions is generally a very positive development," said Rashmi Rangnath, a staff attorney at Public Knowledge, but she said that her and others' concerns would "depend on [the proposal’s] wording." Jonathan Band, a Washington, DC-based intellectual property attorney, concurred. "This is a very positive development," he wrote to Ars in an e-mail on Tuesday. "This is the first time that the US has sought language of this sort in an international agreement. From the blog one can't discern the precise language, which of course makes a big difference in how effective it will be on the ground. Nonetheless, this appears to be a big step in the right direction. Hopefully it will be well received by the other negotiating partners, and perhaps they will make it even stronger." The specific language here, like the entire treaty itself, has yet to be made officially public. Devil remains in the details Fundamentally, interested parties have generally criticized the TPP’s secrecy, as no official draft has ever been made public. The "intellectual property chapter" of the TPP was leaked last year, but no one is sure if the current draft being discussed matches it or not. Last week, a San Diego County congressman asked to sit in on this week’s round of negotiations—a request that was denied. However, the USTR did allow Rep. Darrell Issa (R-CA) to attend as a "stakeholder," the semi-public part of the talks, but not the negotiations themselves. A separate letter from 130 congressional Democrats illustrates political anxiety that many politicians have with such opaque free-trade agreements, despite the fact that, as Reuters points out, "Congress last year overwhelmingly approved three such pacts—with South Korea, Colombia and Panama." But beyond the secrecy of the treaty itself, experts have honed in on several problematic aspects to the leaked draft. Among the most important are a lack of definition of fair use and public domain rights, extension of copyright to "life plus 70" (putting it in line with American law), treating temporary copies (such as in a cache or a video buffer on streaming sites) as copyrightable, and a ban on the circumvention of digital locks, among others. Earlier this year, the Electronic Frontier Foundation (EFF) called it "ACTA-plus," referring to the oft-protested proposed copyright treaty that seems to be on its deathbed. Update: Parker Higgins, an activist at the EFF, wrote in to Ars to say that the organization "opposes this new proposal, which was made without allowing for input from public interest groups and other interested stakeholders. The USTR may try to paint the "3-step-test" in a positive light, but it actually imposes rigid constraints on the sorts of "fair use" provisions countries may enact." http://arstechnica.com/tech-policy/2...tional-treaty/  Alien Pirates, Copyrights to Reach Deep Space BSOD Voyager 1 Sometime within the next 5 years, the Voyager 1 space craft is expected to reach interstellar space. It will be the first man made object to cross the heliosphere, which is the final stop in our solar system. After being launched in 1977, Voyager 1 was the first probe to visit many of the outer planets. It has sent back countless original images from space, almost all of which have been released to the public. Although NASA does sell images, and many appear in copyrighted works (such as books); NASA is very good about releasing information into the public domain, almost all scientifically significant information from space is given to the public. Voyager 1, famously contained a gold phonographic record. The record was filled with iconic sights, images, and sounds from earth, and the prevailing message, "we come in peace". We think. Even though any alien that can figure out how to play a phonographic record, will have certainly already have received fox news, the contents of the actual gold record are not public domain. The disc was comprised by a man named Carl Sagan, and it contained many pieces of art, songs, and images, that are all copyrighted. Sagan had to secure the rights to include these items separately, at great expense. The special alien license does not allow the right to free copy and distribution to educators. In fact, it is unclear if an original copy of the entire disc still exists on earth at all. Some documentaries contain small snippets from the disc. However the closest thing you can find on the open market is a book and CDROM set published by Warner New Media in 1992, called Carl Sagan's Murmurs of Earth. The book shows and describes many of the images used, the cdrom contains the audio. According to NASA: Most of the material they used was copyrighted by the creators/owners and Sagan had to get copyright releases in order to assemble the original record. Subsequently, Warner Multimedia was able to obtain copyright releases for the 1992 version of "Murmurs of Earth" .. Unfortunately, the book and CDROM are no longer being published and are hard to find as a set. Some used copies still exist for sale, versions of Murmurs of Earth published before 1992 will not contain the CDROM. Used copies, are selling for quite a bit of money for information that should be public. A complete copy of the phonograph is not available on the open market and never has been. Perhaps our next interstellar probe should be sent using more open works, because first contact could be us suing the shit out of them for hearing our message. http://activepolitic.com:82/News/201...eep_Space.html  Judge Who Shelved Apple Trial Says Patent System Out of Sync Dan Levine The U.S. judge who tossed out one of the biggest court cases in Apple Inc's (AAPL.O) smartphone technology battle is questioning whether patents should cover software or most other industries at all. Richard Posner, a prolific jurist who sits on the 7th U.S. Circuit Court of Appeals in Chicago, told Reuters this week that the technology industry's high profits and volatility made patent litigation attractive for companies looking to wound competitors. "It's a constant struggle for survival," he said in his courthouse chambers, which have a sparkling view of Monroe Harbor on Lake Michigan. "As in any jungle, the animals will use all the means at their disposal, all their teeth and claws that are permitted by the ecosystem." Posner, 73, was appointed as a federal appeals court judge by President Ronald Reagan in 1981 and has written dozens of books, including one about economics and intellectual property law. Posner, who teaches at the University of Chicago, effectively ended Apple's lawsuit against Google Inc's (GOOG.O) Motorola Mobility unit last month. He canceled a closely anticipated trial between the two and rejected the iPhone maker's request for an injunction barring the sale of Motorola products using Apple's patented technology. Apple is in a pitched battle with its competitors over patents, as technology companies joust globally for consumers in the fast-growing markets for smartphones and tablet computers. Posner said some industries, like pharmaceuticals, had a better claim to intellectual property protection because of the enormous investment it takes to create a successful drug. Advances in software and other industries cost much less, he said, and the companies benefit tremendously from being first in the market with gadgets - a benefit they would still get if there were no software patents. "It's not clear that we really need patents in most industries," he said. Also, devices like smartphones have thousands of component features, and they all receive legal protection. "You just have this proliferation of patents," Posner said. "It's a problem." GENERATION SMARTPHONE The Apple/Motorola case did not land in front of Posner by accident. He volunteered to oversee it. Federal appellate judges occasionally offer to preside over district court cases. Posner had alerted the district judges of his interest in patents, so after part of the smartphone battle landed in Wisconsin federal court, the judge there transferred the case to him. When Posner began working on the smartphone case, he told the litigants he was "really neutral" because he used a court-issued BlackBerry made by Research In Motion Ltd (RIM.TO). He soon accepted an upgrade to an iPhone, but only uses it to check email and call his wife, he said. "I'm not actually that interested in becoming part of the smartphone generation," he said. Posner's corner office is filled with the requisite library of law tomes, and a row of books he wrote sits alongside his family photographs. He also has a signed photograph from the late Supreme Court Justice William J. Brennan Jr., for whom he clerked in the early 1960s. Judges rarely speak openly to the press, but Posner is outspoken on a range of topics. Last week in online magazine Slate, he penned a withering critique of U.S. Supreme Court Justice Antonin Scalia's recent dissent in the Arizona immigration case. "It wouldn't surprise me if Justice Scalia's opinion were quoted in campaign ads," Posner wrote. MOTOROLA V. APPLE Motorola sued Apple in October 2010, a move that was widely seen as a pre-emptive strike. Apple filed its own claims against Motorola the same month. In canceling the trial, Posner said an injunction barring the sale of Motorola phones would harm consumers. He also rejected the idea of trying to ban an entire phone based on patents that cover individual features like the smooth operation of streaming video. Apple's patent, Posner wrote in his June 22 order, "is not a claim to a monopoly of streaming video!" Not all judges in the patent wars share Posner's skepticism of injunctions. U.S. District Judge Lucy Koh in San Jose, California, granted Apple two critical pretrial injunctions against Samsung Electronics Co Ltd (005930.KS) last week: one against the Galaxy Tab 10.1, and the other against the Galaxy Nexus phone. In Friday's 101-page ruling barring the Galaxy Nexus, Koh cited the harms to Apple due to competition from phones that infringe its patent on the Siri search feature. Samsung is appealing both injunctions. Posner said he had not read Koh's orders. In his own ruling, Posner also barred Motorola from seeking an injunction against the iPhone because the company had pledged to license its patent on fair and reasonable terms to other companies - in exchange for having the technology adopted as an industry standard. Posner's idea of examining whether industries like software should receive patent protection is a mainstream one, especially in the computer industry, said John Allison, a professor at University of Texas at Austin who studies intellectual property rights. However, recent patent law reforms passed by the U.S. Congress did not directly address the issue, and Allison said classifying industries for the purposes of intellectual property protection - as Posner suggests - was "completely impractical" because talented lawyers could game the system. When it comes to the smartphone litigation wars, Posner said tech companies should not be blamed for jumping into court since they are merely taking the opportunities that the legal system offers. Given the large cash reserves in Silicon Valley, high legal fees are not a deterrent. Apple, for instance, had $110 billion in cash and securities as of March 31. "It's a small expense for them," Posner said. Posner said he had been looking forward to presiding over a trial between Motorola and Apple, but had no other choice than to toss the case. "I didn't think I could have a trial just for fun," he said. (Editing by Martha Graybow and Lisa Von Ahn) http://www.reuters.com/article/2012/...8640IQ20120705  Why the UK’s Porn Filter Plans are Just an Illusion Bobbie Johnson Britain is, once again, looking at the possibility of applying pressure on internet users to filter out pornography — a policy loved by politicians and disliked by internet providers that, like a cat with a hairball, comes up every few months. As the BBC reported last week, the U.K. government is circulating a discussion paper which looks at a range of censorship options, including full, mandatory adult content blocks for everyone. But the preferred option appears to be a system that is one step down from a total ban. The paper proposes a service that — by law — automatically puts a content filter into place for new internet subscribers, but gives them the option to lift the block later. The latest system, called “active choice-plus”, is aimed at reaching a compromise. It would automatically block adult content, but would set users a question, along the lines of whether they want to change this to gain access to sites promoting pornography, violence and other adult-only themes. This is partly based on “Nudge” theory, a US concept which states that persuasion, rather than enforcement, can be an effective way of changing behaviour. Downing Street has set up a unit to explore such ideas. The consultation had already been trailed earlier this year, but even so it has given some civil liberties advocates a reason to get their placards out to protest. “Giving parents tools is great, but ‘Nanny State’ filtering using government approved technologies is bound to fail the people it is designed to protect,” said Jim Killock, executive director of the Open Rights Group. “This is a Government looking for headline grabbing solutions to complex solutions. They need to think again.” It’s worth remembering that nobody here is suggesting that children should be forced to stare at hardcore adult videos online for hours on end. This isn’t some mirror of A Clockwork Orange. But still, the pro-censorship campaign has driven on with its family values message, circulating a petition in favor of mandatory blocks with that now has 100,000 signatures. Forget about the rhetoric or the controversy or the guiding philosophy, though. There is a much more simple — and much more real — problem facing the U.K.’s proposals to make porn filters opt-out. The porn filters they’re talking about are absolutely terrible at doing the job they’re being asked to. Here’s how it works Given that any filters which are put in place will need to be built and operated by ISPs, I contacted Britain’s four biggest internet providers to ask them about the filtering services they have in place already. And the reality is that their methods are all very similar — and widely criticized. BT, which has more than 6 million subscribers in Britain, told me that it uses already uses “active choice”, meaning it presents new users with an unavoidable choice over whether to apply parental controls or not. And if people do opt for controls, they’re subject to a software-based system developed by McAfee that runs alongside another ISP-level filtering system, Cleanfeed. “It filters out 35 categories of content, including porn, adult, suicide, anorexia etc,” said a spokesman. “The blacklist, as such, is developed by McAfee.” Sky also operates a McAfee-based system, while Virgin Media uses one developed by Trend Micro. TalkTalk, meanwhile, uses a network-level filtering system called Homesafe, which was launched a little over a year ago. It, too, works on a categorization basis. You can ask it to filter out all sorts of things, based on a range of broad subjects: websites about drugs and alcohol, gambling, games, pornography and more. The categorization and filtering is based on technology from Huawei Symantec, the joint venture between the Chinese electronics company and the American security company. But the problem with these services — and TalkTalk’s in particular — is that they are full of holes. Basic flaws Last December The Daily Telegraph reported how Homesafe failed to block access to Pornhub, the world’s third-largest pornography provider. And things haven’t improved: an investigation by PC Pro last week found “basic flaws” that meant it was still possible to access a wide range of pornographic images through nothing more complicated than a simple Google search. And other filters were equally ropey. TalkTalk’s filters are also hugely inconsistent in what they choose to blacklist. Social network controls bar access to Facebook, Twitter and LinkedIn, but not to Google+, StumbleUpon or reddit – including “subreddits” dedicated to sexual content. Likewise, photography site Flickr was banned, but not the “nude” section of fellow photography site 500px. The reality is not just that TalkTalk’s provisions are weak. It’s that category filters rarely work. They’re either too broadly applied, or not broadly applied enough. They’re arbitrary. They’re easily circumvented. And they’re unable to keep up with change. And it’s not just journalists fishing for gotchas, either. On an anecdotal basis, the same is true. @bobbiejohnson Have tried TalkTalk’s and it is underwhelming. Wrongly blocks sites as porn + poor at responding to reports of mistakes — Mark Pack (@markpack) June 30, 2012 As we discovered when we looked into the content filters used by Britain’s mobile operators, these categorizations are often haphazard and extremely broadly applied. It’s the kind of patchwork approach that ends up with GigaOM blocked (because all blogs get blocked as a matter of course) and yet leaves the door open to all kinds of unpleasant content. It’s a lottery. It’s Swiss cheese. So even if you think the mandatory filters are a good idea, the question has to be whether these filters are worthwhile. And if they are not, what is it exactly that you are advocating? An idea? An ambition? A hope that we can achieve better living through technology? Or are you just advocating vaporware that settles the mind without ever really fixing the problem? Nobody wants children to be subjected to inappropriate content, but a false sense of security is no security at all. http://gigaom.com/europe/why-the-uks...t-an-illusion/  ISP: BitTorrent Traffic Increased After Pirate Bay Blockade Ernesto After the Hollywood-funded anti-piracy group BREIN claimed victory against The Pirate Bay, Dutch Internet provider XS4All has spoiled the fun with a surprise announcement. The ISP claims that BitTorrent traffic increased after the Pirate Bay blockade was introduced, and adds that the entertainment industry’s witch hunt is alienating consumers. “Build a legal version of the Pirate Bay,” is their advice. This week anti-Piracy group BREIN celebrated a victory against The Pirate Bay. Now 90% of the Dutch Internet users can no longer access the BitTorrent site directly, the site’s Alexa traffic rank in the Netherlands tanked. The group conveniently forgot to mention that many people now use proxy sites to access the site, and didn’t mention the uptick that can be noticed at other BitTorrent sites. It was a win for Hollywood, they simply argued. However, XS4All, one of the Dutch providers that was sued by BREIN, has now burst this bubble. According to the ISP there is no sign that their subscribers are changing their downloading habits, on the contrary. “Since the Pirate Back blocking lawsuit began, BitTorrent traffic has not been reduced, it increased instead,” XS4All’s Niels Huijbregts states. The ISP looked at the traffic on its network and found that over the past year traffic increased on ports that are commonly used for BitTorrent. XS4all claims that all the news about the blockade may be one of the reasons for this increase. “I think that the increase is a result of all the media attention for the lawsuit and the blockade. Perhaps people who until then had never downloaded thought ‘I hear so much about downloading music and movies, let me try it!’.” “What I want to say to BREIN is this: your repressive policy does not work. You can block access to the Pirate Bay, but that clearly doesn’t result in the desired effect on the download behavior of the Dutch.” Instead of demanding more blockades and censorship, XS4All advises the entertainment industry to focus their energy on the positive. In other words, give consumers what they want instead of beating them into submission. “Put all that money and all that time and effort into something that has an effect. Invest in great new things. And do something about your image,” Huijbregts says. “With your witchhunt you’ve declared war on the biggest film and music fans. The people who could be your biggest customers hate the entire entertainment industry because of all the lawsuits and lobbying activities,” he adds. The ISP claims that the solution to piracy is not censorship, but innovation, and XS4All suggests that the entertainment industry should build their own version of The Pirate Bay. “Build a legal version of the Pirate Bay, where everyone can find and download content. Because that’s what people want: access to everything, anytime, anywhere. That is the reality of the Internet, so that’s what people expect. And unfortunately there are hardly any legal models to meet that expectation,” Huijbregts concludes. A Pirate Bay admin told TorrentFreak that the news about the traffic increase was to be expected. “We are not the only torrent site around, and with their high-profile blocking lawsuits they introduced tens of thousands of new users to BitTorrent,” TorrentFreak was told. “With very few exceptions, all the content that can be found on The Pirate Bay is available on hundreds of other sites.” Besides the Netherlands, The Pirate Bay is also being blocked by all of the major UK ISPs. Whether they have noticed a similar uptick in BitTorrent traffic recently remains the question, but it wouldn’t come as a surprise. https://torrentfreak.com/isp-bittorr...ockade-120705/  Opera Web Browser Unblocks The Pirate Bay Ernesto Back in 2006 Opera was the first major browser to include BitTorrent support. Today, however, it has another interesting feature for BitTorrent users. The browser offers a “Turbo” service which makes websites load faster for users on a slow connection. “When Opera Turbo is enabled, webpages are compressed via Opera’s servers so that they use much less data than the originals. This means that there is less to download, so you can see your webpages more quickly,” Opera explains. But this feature does more than that. It also unblocks Pirate Bay for those who can’t access it. Blocked Internet subscribers can simply click the “Turbo” button in Opera and TPB loads just fine. Totally secure, and perhaps even faster before. https://torrentfreak.com/unblock-the-pirate-bay-120705/  Anonymous Publishing Is Dead. Anonymous Person I know it is dead, because I have tried to do it, and I can assure you it is dead. Text is easy of course I can still blast a simple email out to a mailing list, I can lay my claims out in 7bit ASCII and let the world judge the merits solely on this simple medium. But media publishing a story with supporting images, scans, video or audio, it is dead, left only to the elites. And perhaps worst of all is the promise made by all of you that if you just ... try a little harder, if you just use this service over here, if you just think about it another way that it is still possible. It is not. Some time ago as an experiment I began the process to publish material fully anonymously no compromises. I obtained a prepaid line of credit, paid in cash, verified with a prepaid telephone, also paid in cash, and only turned on in an ambiguous physical location. And I set about to find a Virtual Private Server I could run a Tor Hidden Service on. My requirements throughout all of this were simple: use Tor for everything, pay cash or cash-equivalent for everything, leave no account on a service run by a US/UK/AUS/NZ/CA company, have the VPS hosted outside the same, pay a reasonable sum. I needed an email of course. Nymservers like http://isnotmy.name/ or http://mixnym.net should have been the solution but of course they didn't work. No amount of guesswork or trial and error got me a nym. Free webmail became the next goal. The more trustworthy (gmail), the less satisfactorily anonymous it was. The easier it was to register (in.com) the less trustworthy it was deemed. After signing up for a low-trust but easy-to-get email, I narrowed down my hosting options to a group of VPS in the price range, hosted outside the 'bad' countries, and whose company itself was also outside. There aren't a lot. The next problem became finding a VPS I could pay for.You see, most VPS sellers are small resellers and don't process their own credit cards they outsource it to a payment processor, usually Paypal. Paypal doesn't work. Paypal or AlertPay too stringent verification; Liberty Reserve blocks Tor; CashU not easily-found online merchant able to convert from a prepaid Credit Card; one after another all online payment methods fell by the wayside. You might think 'Bitcoin'. You would be wrong. No bitcoin service accepts any anonymous funding source; most only accept bank transfers. Apparently people performed chargebacks on credit cards to defraud the merchants. I can't blame them for this, but it certainly kills the idea of 'anonymity'. And I don't trust the blockchain to provide anonymity. After finding one of three or four VPS' I thought I could pay for, I encountered the next obstacle: MaxMind. MaxMind is a fraud detector built into WHMCompleteSolution which in turn is the VPS management tool used by every budget VPS. I set off every detector it had: proxy software, low trust email account, strange addresses, no valid phone number, etc etc. When I inquired to one company about this, I was laughed off. Even though I was willing to let them charge my card and sit on it for a month before providing service, no such luck. At this point, I needed to find a company large enough they processed their own credit cards, didn't block Tor, and didn't use fraud detectors. I found one, a competitor to Amazon EC2, that I thought I could fall through the cracks of. It didn't like my low trust email address, but after enough searching, I found an ISP I could get an account on without paying.After getting that, creating and verifying an account, and finally set up to make my payment ... the prepaid card is declined. There's no explanation, it just didn't work. I thought at this point, perhaps there was a service that could be used. There was an announcement recently: http://karelbilek.com/anontorrent/. Supposedly this guy will seed anything until it has 20 seeders of its own. Except the file limit is 50MB. And you can't upload copyrighted material. How about any of the much-acclaimed 'leak sites' that spun up after Wikileaks shuttered their wiki and submission system? Well, I went through all of these: leakdirectory.org/index.php/LeakSiteDirectory and all of them seemed to be either wannabes who had never published a thing or news organizations who were security illiterate and had no way to accept content. Anonymous Publishing Is Dead. You may seek to respond with the 'right way' to do it, the company you know will let me fall through the cracks, the trick you use to white-lie your way through the process. Don't bother. If there is a way through, and I'm not convinced there is, it is so difficult to find that a technically unsavvy user would never be able to; and even technically savvy users like myself who understand all the tricks of firewalling off my machine so nothing but Tor escapes are groping blindly for it, unlikely to find it. What can be done about this? What compromises are 'safe'? Is a Hidden Service sufficiently trustworthy to host any material, and have it stand up to investigation when the server running it is in your name? Is the correct approach not to publish anonymously at all, as cryptome.org does? Should we rely on the Streisand effect, bittorrent, newsgroups, something else? These are mostly rhetorical questions. My purpose in this email is to tell you that anonymous publishing is an unsolved problem. Any solution available today is not robust: it falls down in some situation: content, capacity, anonymity, or something else. What can be done about it? What will be done about it? Dear tortalk! Get Yourself a cool, short [at]in.com Email ID now! http://cryptome.org/2012/06/anon-pub-dead.htm  The Pauls' New Crusade: “Internet Freedom” Defending the Internet — and the corporations that invest in it — from government regulation is the new “End the Fed,” Paul advisors tell BuzzFeed exclusively. A new Paul manifesto: “This is our revolution.” Rosie Gray Ron and Rand Paul are set today to shift the central focus of their family's long libertarian crusade to a new cause: Internet Freedom. Kentucky senator Rand and his father Ron Paul, who has not yet formally conceded the Republican presidential nomination, will throw their weight behind a new online manifesto set to be released today by the Paul-founded Campaign for Liberty. The new push, Paul aides say, will in some ways displace what has been their movement's long-running top priority, shutting down the Federal Reserve Bank. The move is an attempt to stake a libertarian claim to a central public issue of the next decade, and to move from the esoteric terrain of high finance to the everyday world of cable modems and Facebook. The manifesto, obtained yesterday by BuzzFeed, is titled "The Technology Revolution" and lays out an argument — in doomsday tones —for keeping the government entirely out of regulating anything online, and for leaving the private sector to shape the new online space. "The revolution is occurring around the world," it reads. "It is occurring in the private sector, not the public sector. It is occurring despite wrongheaded attempts by governments to micromanage markets through disastrous industrial policy. And it is driven by the Internet, the single greatest catalyst in history for individual liberty and free markets." The manifesto quotes Austrian economist Ludwig von Mises and attacks not just the federal government, but also progressive groups that have called for similar measures to keep the Internet largely unregulated: "Today, the road to tyranny is being paved by a collectivist-Industrial complex -- a dangerous brew of wealthy, international NGO's, progressive do-gooders, corporate cronies and sympathetic political elites." The manifesto lays out five specific battles with government regulation and with liberals who state their goal of online liberty in similar terms, but who view corporate encroachment as a more immediate risk. The Paul manifesto seeks to rein in anti-trust actions against companies in new industries; to stop attempts to impose "Net Neutrality" rules on broadband providers; to prevent government control of online infrastructure; to broaden private control of the wireless spectrum, and shore up "private property rights on the Internet." The Pauls also take a stand for the growing industry known (and widely criticized) as "big data." They deride the notion that "private sector data collection practices must be scrutinized and tightly regulated inthe name of 'protecting consumers,' at the same time as government’s warrantless surveillance and collection of private citizens’ Internet data has dramatically increased." Paul's so-called "Audit the Fed" bill will soon be put to a vote in the House of Representatives, and the new campaign will kick off shortly thereafter. "We are going to bring to this project the same kind of intensity, resources and energy we brought to the Fed Audit," said one Paul adviser. The document is intended to serve as a conservative counterpoint to a Declaration of Internet Freedom released this week and hosted by the group FreePress, though the two share some goals. The earlier document, which sets out broad principles but does not take sides on divisive issues like Net Neutrality, was signed by groups including the American Civil Liberties Union as well as Internet companies such as Mozilla. The language of the document tries to reclaim the issue of Internet freedom from the strange bedfellows that have staked a claim to it: progressives and tech companies on one hand, and more traditional conservative politicians like California Rep. Darrell Issa. "Internet collectivists are clever," the manifesto says, accusing their foes of series of Orwellian linguistic twists. "They are masters at hijacking the language of freedom and liberty to disingenuously pushfor more centralized control. 'Openness' means government control of privately owned infrastructure.'Net neutrality' means government acting as arbiter and enforcer of what it deems tobe 'neutral'." "This is our revolution -- government needs to get out of the way," the manifesto concludes. This is also a new stage for what supporters refer to as the Ron Paul Revolution, and a way to make sure that Ron Paul's followers stay on board with the movement after the congressman's retirement from the House of Representatives. Paul supporters are already Internet-savvy, frequently launching digital campaigns of their own, and skew young. And the new cause gives his son Rand an easier way to connect with them, given that his relationship with his father's supporters has often been fraught. Internet freedom, Paul insiders say, is going to be Rand's end-the-Fed. Making Rand Paul the standard-bearer of Internet freedom "is one of the goals," said a Republican strategist close to the campaign. "As you may have noted he has been speaking out about Internet Freedom a fair amount including in his endorsement of Romney on Hannity," the strategist said in an email. "Freedom online and freedom and liberty offline are seamlessly linked and Senator Paul gets that." A Paul adviser told BuzzFeed that the full Campaign for Liberty Internet project will start about two weeks after the Fed bill vote. http://www.buzzfeed.com/rosiegray/th...ternet-freedom  Five Years After the iPhone, Carriers are the Biggest Threat to Innovation Nilay Patel Five years ago, the iPhone revolutionized the mobile business and kicked off a seismic shift in the technology industry that continues today. But the massive success of Apple's phone has overshadowed the grim reality of an American wireless marketplace that has become increasingly hostile to innovation — a market tightly controlled by carriers who capriciously pick winners and losers while raising prices and insisting that their use of valuable public spectrum remain free of any oversight. While the iPhone is a raging success, the wireless market is headed towards total failure. The evidence is everywhere, starting with the iPhone itself: Verizon famously passed on the device at first, and if not for Steve Jobs personally convincing AT&T to sell his phone sight unseen, the iPhone may never have existed. Jobs was well aware that he couldn't reach the market of cellphone consumers without carrier support — at the D3 conference in 2005, he famously called the carriers "orifices" and offered this withering assessment of the industry as it then stood: It's even worse. The carriers now have gained the upper hand in terms of the power of the relationship with the handset manufacturers. And they're starting to tell the handset manufacturers what to build. And if Nokia and Motorola don't listen to them, well, Samsung and LG will. So the handset manufacturers are really getting these big thick books from the carriers, telling them "here's what your phone's gonna be." "We're not good at that," Steve added. Two years later, he would ship the iPhone, turning the industry on its head. Apple had succeeded in building the phone customers wanted instead of the phone carriers wanted, and things would never be the same. And indeed, things are different — they've gotten dramatically worse. Instead of seeing the benefits of free competition at the consumer level, the carriers are now exerting more control than ever before as demand for mobile devices skyrockets. Getting a device on a major carrier can take up to 15 months and cost millions of dollars; carriers are notorious for demanding custom devices in order to create customer lock-in. "Exclusivity is the bane of my existence," says one source at a major phone manufacturer. "But it's the only way business gets done." ""Exclusivity is the bane of my existence," says one source. "But it's the only way business gets done."" It's even bad for Apple: one source close to the iPhone calls the carrier process "incredibly backward." But it's not just about frustrated manufacturers. Increased carrier control over customers and devices has stunted competition and stalled innovation — sometimes fatally so. Just look at the tragic story of Palm, which went from darling of CES 2009 to legendary failure in just 31 short months. The company initially wanted to ship its Pre smartphone on Verizon, but the carrier backed out and Palm was forced to languish on Sprint, where it was unable to compete directly against the iPhone. When Verizon finally picked up the Pre Plus the next year, the carrier ordered millions of devices and then flippantly refused shipment and decided to focus on the Motorola Droid, leaving Palm sitting on millions of unsold units that couldn't be used on any other carrier in the world. The decision cost Palm hundreds of million of dollars and led directly to the company selling itself to HP — and the once-promising webOS platform slowly dissipated into a puff of mismanaged open-source smoke. "If we could have launched at Verizon prior to the Droid, I think we would have gotten the attention the Droid got. And since I believe we have a better product, I think we could have even done better," said Palm CEO Jon Rubinstein in 2010, trying to explain why his company was failing. But his exclusivity deal with Sprint means he was never given the chance to fairly compete. "Even Google and Microsoft are avoiding the carriers" Even powerful and established companies like Google and Microsoft are now avoiding the carriers as they scramble to compete with Apple. Microsoft is radically upending the entire PC market with its Surface tablets, but they're Wi-Fi-only for now, and Redmond refuses to discuss carrier partnerships. Same with Google, which just announced the Nexus 7 tablet; it's designed for on-the-go content consumption, but it lacks a mobile broadband connection. Google won't comment about a 4G version of the Nexus 7 on the record, but it's fair to say relations between the search giant and carriers are strained: multiple sources say that Verizon purposefully delayed shipment on the LTE Galaxy Nexus after announcing the Motorola Droid RAZR, forcing Google to send US journalists unlocked HSPA+ review units to be used on AT&T when the phone launched internationally. And when Verizon did eventually release the Nexus, it was stripped of Google's Wallet functionality — forestalling the growth of Google's mobile payment system while Verizon works on its own solution. And while the big companies are happy to sidestep the carriers in order to reach consumers, the real tragedy is that smaller companies are deciding that innovating in mobile just isn't worth the cost of dealing with the carriers. LA-based Vizio has found consistent success in the cutthroat HDTV business against huge competitors like Sony and Samsung, but after the company introduced a phone at CES 2011 it quickly realized that the carriers were too formidable an obstacle and canceled its plans. ""The cell phone market in the United States is not set up to encourage innovation."" "The cell phone market in the United States is not set up to encourage innovation," Vizio CTO Matt McRae says. "The inability to sell product directly to the consumer means that companies can't experiment and iterate quickly." After canceling its phone, Vizio instead decided to build its own PCs — products which it can sell directly to consumers without carrier interference. McRae says Vizio is still interested in developing a "small screen device," but adds that "there is definitely a big opportunity to make the process more efficient and fair across vendors." But companies that depend on the carriers are forced to play along — and as a result, they're not allowed to compete on equal footing with giants like Apple and Samsung. The HTC One X is a high-end flagship device designed to compete squarely with the iPhone and Samsung's Galaxy S III, but Verizon and Sprint aren't carrying it: instead, Sprint offers a variant called the Evo 4G LTE, and Verizon is selling a downgraded device called the Droid Incredible 4G that simply doesn't match up to higher-end competition. How is HTC to compete for Verizon customers with a weaker device? Why should HTC depend on struggling Sprint to market and sell a custom phone when it could just leverage its existing One X campaigns to take on Apple directly? And because success in the wireless marketplace can only come with carrier support, innovation is stunted as companies design their future products around what they think carriers might want, not where the market or consumer behavior is heading. "Companies build phones that the carriers ask for instead of taking risks and testing new concepts in the marketplace," says Vizio's McRae. "The result is a collection of handsets that are fairly homogenous from a small number of brands." ""The carriers have always been wary of ‘excessive' innovation in the mobile space."" And carriers rarely want what's best for their customers. "The carriers have always been wary of ‘excessive' innovation in the mobile space because of the danger that it might make mobile service cheaper," says Columbia Law School professor and The Master Switch author Tim Wu. If companies like HTC and Samsung were able to compete directly at the consumer level, the carriers would turn into dumb pipes — and AT&T and Verizon would be forced to raise their service levels and lower their monthly fees to effectively compete against each other. That's good for consumers, but bad for carriers. "There's a business model that needs to be cared for," a Verizon spokesperson told us. But the wireless spectrum AT&T and Verizon use to build their networks is a scarce public resource literally leased from the people of the United States — shouldn't we have some say in how this market operates? Shouldn't the rules be set up to favor consumers instead of blocking innovation and increasing prices? There is a long string of answers to these questions that favors the current system and makes it seem logical. Different cellular technologies and wildly mismatched spectrum among carriers makes creating universal devices extremely difficult. Patent licensing costs, especially for LTE devices, are enormous. Carrier subsidies allow cutting-edge technology to hit the mass market years ahead of schedule. "I have no idea how you can make a $199 product with embedded data without subsidies," says one source with years of experience in the industry. ""What you see with all this stuff is the rebuilding of the walled garden."" But spiralling down this string of answers is a form of consumer Stockholm syndrome. We are spending billions of dollars each year on mobile broadband. It is the most disruptive enabling technology in recent memory and will soon be the primary way millions of Americans connect to the internet. Understanding why the industry is cheating us out of innovation is great, but a look at the landscape makes it clear that it's time for the cheating to stop. "What you see with all this stuff is the rebuilding of the walled garden," says one industry source. "Carriers have had control for so long they want to continue to feel like they're in control." The iPhone was a revolution five years ago because it was the first time an agile, consumer-focused company delivered the promise of mobile computing directly to its customers. But the success of the iPhone shouldn't cloud us from seeing the wireless market as it now stands: a market that is driving players big and small away from mobile broadband as the carriers tighten their grip. http://www.theverge.com/2012/7/5/313...tion-editorial  A Victory for the Internet Carl Bildt In a ground-breaking vote on an issue that affects all of us, the United Nations Human Rights Council on Thursday endorsed a resolution upholding the principle of freedom of expression and information on the Internet. The broad support for the resolution demonstrated that maintaining the free flow of information on the Internet is a global call and not something pushed only by a few Western states. In recent years I have frequently spoken about Internet freedom, an issue which is a priority to the Swedish government. I have condemned the harassment of bloggers and online activists and called for a strong global coalition of states to support the simple but salient fact that freedom of expression also is applicable to the Internet. The group of countries that presented this resolution — Brazil, Nigeria, Sweden, Tunisia, Turkey and the United States — truly represent a global coalition. And the support by other states (India, Egypt and Indonesia, to name a few of the more than 80 co-sponsors) and global civil society was overwhelming. Together, we are building a global alliance for the freedom of the Internet. As technology and the Internet evolve, so should the work in the United Nations. From a limited group of countries rallying behind a short statement on freedom of expression on the Internet two years ago, we have seen the interest and support soar. The vote in Geneva on Thursday was a breakthrough of fundamental importance. Beyond affirming that freedom of expression applies also to the Internet, the resolution also recognized the immense value the Internet has for global development and called on all states to facilitate and improve global access to it. We are rapidly entering into a new world of hyperconnectivity. Mobile data traffic alone is set to increase 15-fold in the next five years. It reaches everywhere, and we see the new networks challenging the old hierarchies everywhere. Just one example: In past decades, massive crimes could be committed in Syria and other countries without us even knowing. But we can now follow what is happening minute by minute, megabyte by megabyte. Today, with nearly the entire globe covered by mobile networks, the problem of physical access to the Internet is almost a forgotten issue. What is increasingly worrying is what kind of access people are being offered. We cannot accept that the Internet’s content should be limited or manipulated depending on the flavor-of-the-month of political leaders. Only by securing access to the open and global Internet will true development take place. The governments of the Human Rights Council now for the first time have confirmed that freedom of expression applies fully to the Internet. A global coalition for a global and open Internet has been formed. This is truly important, but we must not stop here. The challenge now is to put these words into action to make sure that people all over the world can use and utilize the power of connectivity without having to fear for their safety. This work is far from over. https://www.nytimes.com/2012/07/06/o...-internet.html  Announcing The Declaration Of Internet Freedom Mike Masnick A whole bunch of organizations and individuals are getting together today to launch the beginning of a process, the creation of an Internet Declaration of Freedom. We've seen how the internet has been under attack from various directions, and we recognize that it's time to make that stop. The internet is an incredible platform that we want to grow and to thrive, and thus, a very large coalition got together to produce the following document as a starting point, hoping to kick off a much larger discussion which we hope you'll join in. We've set up our own Step2 discussion page where you can vote on the principles, discuss them, add your own ideas... whatever you'd like. You can, of course, also discuss them below in the comments. There are a number of other organizations setting up pages as well. The folks at Free Press have put up a Declaration of Internet Freedom site that lists out many of the organizations and individuals who were involved in putting this together and who are supporting the effort. There's also a subreddit and a Cheezburger page. Lots of other groups have set up action pages where you can take part as well, including EFF, Access and Free Press. We believe that a free and open Internet can bring about a better world. But to keep the Internet free and open, we must promote these principles in every country, every industry and every community. And we believe that these freedoms will bring about more creativity, more innovation and a better society. We are joining an international movement to defend our freedoms because we believe that they are worth fighting for. Let’s discuss these principles — agree or disagree with them, debate them, translate them, make them your own and broaden the discussion with your community — as only the Internet can make possible. Join us in keeping the Internet free and open. 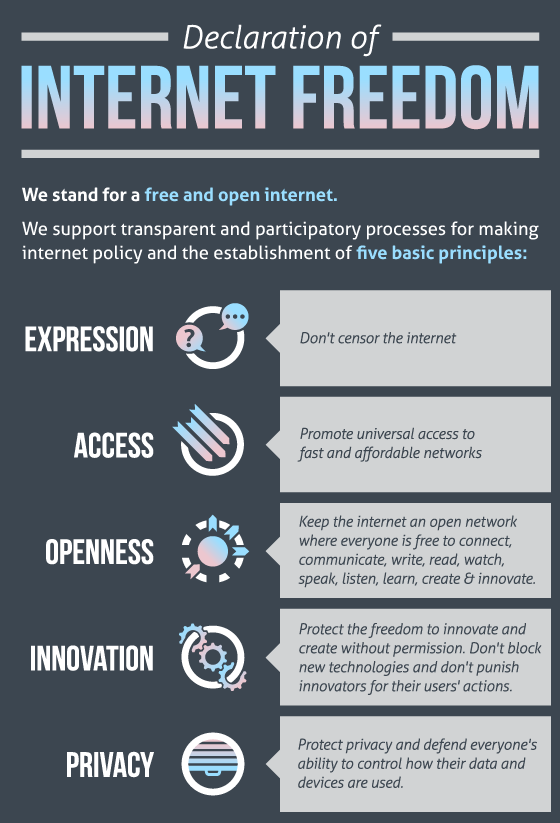 Embed This: <a href="http://www.techdirt.com/netdeclaration"><img src="http://cdn.techdirt.com/i/net-declaration.png" title="Declaration of Internet Freedom" /></a> In case you can't read the graphic, here's the text version: Declaration of Internet Freedom We stand for a free and open Internet. We support transparent and participatory processes for making Internet policy and the establishment of five basic principles: Expression: Don't censor the Internet. Access: Promote universal access to fast and affordable networks. Openness: Keep the Internet an open network where everyone is free to connect, communicate, write, read, watch, speak, listen, learn, create and innovate. Innovation: Protect the freedom to innovate and create without permission. Don’t block new technologies, and don’t punish innovators for their users' actions. Privacy: Protect privacy and defend everyone’s ability to control how their data and devices are used. http://www.techdirt.com/articles/201...-freedom.shtml  Until next week, - js.  Current Week In Review  Recent WiRs - June 30th, June 23rd , June 16th, June 9th Jack Spratts' Week In Review is published every Friday. Submit letters, articles, press releases, comments, questions etc. in plain text English to jackspratts (at) lycos (dot) com. Submission deadlines are Thursdays @ 1400 UTC. Please include contact info. The right to publish all remarks is reserved. "The First Amendment rests on the assumption that the widest possible dissemination of information from diverse and antagonistic sources is essential to the welfare of the public." - Hugo Black
__________________
Thanks For Sharing |
|
|
|

|
 |
| Thread Tools | Search this Thread |
| Display Modes | |
|
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| Peer-To-Peer News - The Week In Review - July 30th, '11 | JackSpratts | Peer to Peer | 0 | 27-07-11 06:58 AM |
| Peer-To-Peer News - The Week In Review - July 16th, '11 | JackSpratts | Peer to Peer | 0 | 13-07-11 06:43 AM |
| Peer-To-Peer News - The Week In Review - July 9th, '11 | JackSpratts | Peer to Peer | 0 | 06-07-11 05:36 AM |
| Peer-To-Peer News - The Week In Review - January 30th, '10 | JackSpratts | Peer to Peer | 0 | 27-01-10 07:49 AM |
| Peer-To-Peer News - The Week In Review - December 5th, '09 | JackSpratts | Peer to Peer | 0 | 02-12-09 08:32 AM |