
 |
|
|||||||
| Peer to Peer The 3rd millenium technology! |
 |
|
|
Thread Tools | Search this Thread | Display Modes |
|
|
#1 | ||
|
Join Date: May 2001
Location: New England
Posts: 10,017
|
Since 2002
  "I download illegally quite a lot and I encourage people to do the same to my own films. Basically, the studio system is just there to rinse money out of the public and the filmmakers. Why give another dollar to Steve Jobs? That 99c isn't going to the artist, it's going to Sony, or Warners, or whoever." – Chris Atkins "As for accessing blocked resources -- we do not comment on that." – Opera Software spokesman Vladimir Isayev April 17th, 2010  Digital Economy Act Likely to Increase Households Targeted for Piracy Fears increase that law firms may home in on innocent web users who don't illegally download Dan Sabbagh Gill Murdoch and her husband, Ken MacKinnon, were surprised when a threatening lawyer's letter came through the door of their Inverness home. It demanded that they pay £500 immediately because they had allegedly made available a copy of a computer game – Risk II – so that it could be pirated across the internet. The pair, 56 and 68 respectively, were stunned, not least because neither plays computer games. "We're not into things like that," Murdoch says. "We like to walk our dog, or cycle or garden – we don't use the internet for anything other than for Googling information." She had been accused of making Risk II available on a peer-to-peer basis – a filesharing system allowing anybody to make a copy of the game. "I didn't even know what peer-to-peer was," Murdoch adds, admitting she had to ask a friend to explain what she had been accused of. Her first reaction was to call the law firm that had sent the letter. "I rang Davenport Lyons almost immediately, and spoke to a man who refused to give me his name. I never found out who he was," says Murdoch. "What happened is that I was told it didn't matter whether we did it or not. I was told we must have Wi-Fi and somebody else used our connection – but we don't have Wi-Fi. Then I was told we must have failed to protect our computer with Norton – but we had. He seemed not to care whether we did it or not," she recalls. Worried by the call, she "thought for a moment I'd lost the house – because of all the legal bills I might have to pay". Hostile correspondence Sure of their innocence, the couple consulted various people. The council's trade standards watchdog suggested they save up for a lawyer, but eventually, with the help of Which?, the consumer organisation, the claim was fought off after several months of hostile correspondence. But they were hardly alone in receiving an unexpected demand through the post. Over the past two years, three law firms, Davenport Lyons, ACS:Law, and Tilly Bailey & Irvine, have been targeting individuals accused of downloading or sharing pirate material – typically demanding between £500 and £700, amid accusations that the homeowner has been pirating copyright material. What Murdoch's case and others like it demonstrate are the problems inherent in trying to suppress internet piracy by identifying individuals who have supposedly engaged in the illegal filesharing of music, television, film or games – and seeking some form of legal redress. Until now this has been a minority sport, but the Digital Economy Act will make the targeting of households more likely. The act could mean that serial pirates have their internet connections cut off, if they can be accurately identified. Andrew Heaney, the director of regulation at Talk Talk, the internet provider most concerned about the repercussions of disconnection, says that cases such as Murdoch's show the difficulties with the planned legislation. "The essential flaw is always the same: copyright holders can link piracy to IP addresses, and these can be matched to a household's internet account. But there could be tens of people using an IP address – members of your family, visitors, neighbours, or somebody more unscrupulous." He says the most determined pirates – the criminals – will cover their tracks, hijacking other people's internet connections if they can. "What the digital economy bill proposes is to place a burden of responsibility on the person owning the internet connection – you have to prove it wasn't you who pirated that film, otherwise you risk being disconnected," Heaney says. The indications so far are that hundreds and possibly thousands of people have been wrongly identified, on the basis of flawed evidence – judging by the "hundreds of people" that Deborah Finch, the head of legal affairs at Which?, says she is aware of. Others may, of course, be guilty, but there will also be instances in which the sum demanded has been paid because people want a quick resolution, or because they decide to avoid awkward conversations and causing tension in the family if there are suggestions that somebody in the home has been watching pornographic material. "We think there could be tens of thousands of letters that have gone out, in a practice that amounts to little more than speculative invoicing," says Finch. Robert Cox, who lives in Northamptonshire and works in information technology, was accused by ACS:Law of making a computer game called Two Worlds available for others to copy via peer-to-peer networks. ACS:Law's nine-page letter said its client, a little-known games company called Reality Pump, had "retained forensic computer analysts" from a company called Logistep, and their work showed that his home internet connection had been used to distribute the computer game illegally. Specialist knowledge But these forensic techniques all adopt essentially the same approach that will be used under both current copyright law to launch civil claims, or under the new act where the punishment could culminate in the loss of a home's domestic internet use. Fortunately for Cox, he had enough specialist knowledge to reject ACS's demands, and eventually the law firm went away. Major media groups have been careful to avoid suing clients – they saw the problems that it caused music giants in the US when they took action against Briana Torres, a 12-year-old girl, and pursued Gertrude Walton, an 83-year-old woman who had died two months before the writ arrived. Other, smaller media companies are behind the current spate of legal actions, as an examination of the legal papers shows; and there is concern that there will be opportunistic, unscrupulous companies that try to use the threat of disconnection to force people to pay up. When Davenport Lyons targeted Murdoch in 2008, the firm represented a medium-sized computer games firm, Atari. However, after the adverse publicity caused by the campaign, Atari pulled out, and sent letters of apology to wrongly targeted customers a year later, saying it regretted the distress caused. In November, ACS:Law applied to the Royal Courts of Justice requesting that several internet providers give up details of customers linked to suspect IP addresses. It was acting on behalf of a little-known company called MediaCAT, which had the right to pursue legal actions against anybody pirating any one of 291 pornographic films owned by five companies, including two controlled by David Sullivan, the adult entertainment magnate who is also the co-owner of West Ham football club. Andrew Crossley runs ACS: Law, where he is the sole principal. Last year his firm sent out about 6,500 demands for payment, taking over some of Davenport Lyons's caseload, but a major expansion of his activity means that he plans to send out 50,000-60,000 during 2010. He says "a sizeable percentage" of people targeted pay up, and there have only been occasional cases of mistaken identity. "We are very confident in our technology," he says, adding that "our objective is to reduce the infringment of our clients copyright" and that "anecdotally, there is evidence to suggest that what we are do works". ACS:Law plans to continue with its letter writing campaign when the disconnection provisions in the Digital Economy Act come into force, arguing that the threat of a fine is a greater deterrent than disconnection. But Crossley says that the measure "gives the whole area of digital copyright enforcement greater credibility, because it works under the same principles" - using individual IP addresses to identify suspect filesharers. Yet not all the law firms are so comfortable with their letter writing approach. Davenport Lyons declined to comment on its activities, but it abandoned letter writing last year, transferring staff and work to ACS:Law. On Friday evening, Tilly Bailey & Irvine, which had sent out about 250 letters, said it would drop its work, after a complaint made by Which? to the Solictors' Regulation Authority. TBI had said previously that it "vehemently [denies] any allegations that our letters are bullying or heavy-handed", but the reactions of the scared and unsettled recipients of these letters tell a different story. The worry has to be that those keenest to use the act to threaten people with disconnection will be ruthless operators who act for owners of content that nobody would describe as mainstream. If past experience is anything to go by, the number of complaints will rise, and miscarriages of justice will increase too. The law now – and after the Digital Economy Act Law firms sending threatening letters to homes today are taking advantage of the existing Copyright, Designs and Patents Act 1988. That allows media companies to take civil action – and seek damages – against people allegedly breaching their copyrights. However, to find out who to chase after, the copyright holders need to identify the individuals they believe are guilty. Online investigators discover the "IP address", the unique address of every connection to the internet, linked to somebody who is offering a song, film, television programme or computer game for others to copy. They then present this address to the relevant internet service provider, such as BT, Sky or Virgin Media, with evidence of the alleged piracy. Internet providers typically only hand over their information after a court order – which finally links the IP address to a customer's name and address. Critics say this process is complicated and expensive, and that the only penalty that can be levied is a fine. The idea behind the digital economy bill is to make it clear that ISPs have to notify users of alleged infringement if they are presented with a valid request, and to introduce a tough penalty. That is to "temporarily" disconnect internet connections in the case of repeat offenders – which at the same time avoids the cumbersome need to seek damages through the courts. Disconnection will only be introduced on the decision of the culture secretary if penalties that stop short of it have been tried and assessed for at least a year first. It is widely expected that disconnection will eventually be introduced by whichever party wins the election. http://www.guardian.co.uk/media/2010...seholds-piracy  Ofcom Starts Anti-Piracy Code Consultation Ian Grant Communications regulator Ofcom has issued a consultation on a code of conduct that aims to cut online copyright infringement by up to 70%. It is also asking for input to set up the initial obligations that copyright holders and internet service providers (ISPs) will have to meet to comply with the Digital Economy Act rushed through parliament this month. The act requires qualifying ISPs to notify alleged online pirates that they are breaking the law, and to keep a record of the accused who do not challenge the allegations. The act also gives the secretary of state the power to ask courts to get ISPs to apply technical measures such as bandwidth throttling, blocking and disconnection against persistent pirates and websites that host copyright content without permission. It requires ISPs to give subscribers enough information to challenge the allegations, and access to a "robust and effective appeals mechanism". Courts can order ISPs to give rights holders enough personal details of blacklisted subscribers for them to take legal action against infringers. Any processing of subscriber data must comply with relevant data protection laws, Ofcom said. Ofcom will have to approve and enforce the code of conduct that governs use of the measures, as well manage a dispute resolution procedure. Ofcom has to report quarterly to the government on estimated levels of unlawful file sharing and legal actions by copyright owners. It will report annually on other factors, such as consumer education campaigns and the availability of lawful alternative services. Ofcom must implement the initial obligations code within eight months. This includes three months for approval by the European Commission. "We intend to begin work immediately on establishing a robust subscriber appeals mechanism, and a framework for handling disputes," Ofcom said. It would also set up a way to estimate levels of unlawful file sharing so that it had a baseline against which it can assess the impact of the measures. The draft code will be published for consultation no later than May 2010, followed the final code by the end of September 2010, A simultaneous draft statutory instrument embodying the approved code will go to the European Commission for consideration. Ofcom said it would invite consumer groups, ISPs and copyright owners to give their ideas and feedback on proposals, and would set up stakeholder liaison groups to provide regular input. http://www.computerweekly.com/Articl...nsultation.htm  Digital Economy Bill: Nine Things You Can't Do Any More Rich Trenholm The Digital Economy Bill has a number of clauses that, if taken to their logical extremes, could see some pretty horrible outcomes. It's completed its whistle-stop tour of the legislative process, sprinting from Commons to Lords with barely a pause for breath before getting the nod from Her Maj. MPs decided to get the bill into law first and worry about the details later. Until Ofcom hammers out the mechanics of the processes outlined in the bill, it's impossible to say how we'll be affected. We take a look at some of the worst-case scenarios. Watch copyrighted content No shizzle, Sherlock. Accessing copyrighted movies and music is illegal already, but with just a minimal amount of know-how it's easier than falling off a slippery log in the rainy season. The bill aims to make it more difficult to access copyrighted content, by blocking Web sites built around sharing such material. From the other side, the bill creates sanctions that can be applied to you, the user, should you be caught with your fingers in the copyright cookie jar. Download from us Download.com is part of the big happy CNET family. Among the available software are peer-to-peer file-sharing tools. The bill specifically states that Web sites such as Download.com can be blocked if they're providing tools that infringe copyright. Use Napster In the same clause, the bill targets sites that have infringed copyright in the past. That theoretically includes sites such as Napster, which have cleaned up their act since their early days under the Jolly Roger of copyright piracy. This may overturn the recently set legal precedent in which a high court judge ruled against a blanket ban of Usenet-indexing Web site Newzbin. Use WikiLeaks But most worrying is that the same clause also specifically allows for blocking sites deemed 'likely to' infringe copyright. We don't yet know how the government will divine whether a site is 'likely to' do anything, unless Ofcom is going to start employing soothsayers. There's also a clause relating to national security, which could see legal restrictions on material 'they' don't want us to see. This may even extend to gagging sites that currently do a bang-up job of making a mockery of 'super-injunctions'. Mash and mod File-sharing services host thriving communities transforming copyrighted content in mash-ups and mods. These could be targeted. Use free open Wi-Fi The bill distinguishes between subscribers -- you -- and Internet service providers (ISPs). Some networks could be considered to be both, however. If a network is a subscriber -- the actual Wi-Fi is provided by someone else, such as BT Openzone in Starbucks -- then it faces liability for the actions of users. If it's an ISP, it faces bureaucracy, cost and legal obligations to hand over information about users. Either way, the bill will make anyone running or thinking of running open Wi-Fi think twice. The bill specifically exempts libraries and universities, but not small businesses or local co-operatives. At worst, we could see the end of public Wi-Fi because nobody wants the risk or the headache. At best, we'll have the hassle of registering our details every time we want to log on in public. Watch YouTube YouTube wouldn't be what it is today without a critical mass of copyrighted material. Liberal Democrat peer Lord Clement-Jones told our sister site ZDNet that YouTube is unlikely to be affected as Google is jolly decent about taking down copyrighted material when asked nicely. Yet YouTube -- and most video sites -- are stuffed to the gills with copyrighted material. The bill makes provision to nuke them all. Change ISPs French law prevents suspended users from switching to another ISP, and Ofcom is expected to come up with a similar provision. It's unclear who will be in charge of this blacklist -- a copyright offender register, if you will. How long will suspended users be kept on the list? Will it lapse after a set period of time, like a police caution? Will you be able to see your record, like a credit record? Either way, ISPs may find themselves forced to check each new user, which could make the process of signing up to a new ISP even more of a chore than it already is. Google stuff Google searches torrents and is therefore, by government logic, a file-sharing tool. Will Google be banned? Rupert Murdoch probably hopes so: he already accuses Google News of stealing News International content. There will probably be a bunch of test cases to establish the legal boundaries of the bill, and we'd bet our favourite trousers Murdoch will be all over that like Tiger Woods on a cocktail waitress. This is all speculation until the mechanics are worked out over the next year. Let us know your best -- and worst -- case scenarios in the comments. Oh, and remember: there's an election coming. http://crave.cnet.co.uk/gadgets/0,39...9305426,00.htm  How File-Sharers Will Bypass UK’s Anti-Piracy Act Ernesto In an apparent attempt to stop piracy from bankrupting the music industry, the UK Government passed the Digital Economy Bill last week. Despite their good intentions, the lawmakers have come up with a legislative equivalent of DRM that will not have the slightest effect on seasoned file-sharers. Last Wednesday the Digital Economy Bill was forced through by the UK Government. Under the new law copyright holders have the power to spy on those who infringe their rights, which may ultimately lead to file-sharers being disconnected from the Internet. In addition, copyright holders can urge the Government to close websites without the hassle of going through the courts. Despite these new powers awarded to copyright holders, it is unlikely that they will stop heavy file-sharers from continuing what they’ve been doing for so long. The problem with using technology to fight technology is that it’s only a matter of time before the latter catches up with the former. It has already been shown numerous times that DRM has not prevented anyone from sharing files, and the Digital Economy Act – with all the extra powers it gives to copyright holders – wont be successful either. For those who don’t want to give up their habit of downloading copyrighted material, there are simply dozens of ways to download music and movies without being at risk. Much like DRM, the Act will not stop tech savvy file-sharers, it will only change the rules of the game. Listed below are a few ways how file-sharers will easily avoid the measures that have been introduced by the new legislation. A Simple Trick For those who use BitTorrent to share files, there is one really simple trick to avoid being tracked by many copyright holders. Since all of the tracking software we’re aware of today use BitTorrent trackers to gather data, one can simply remove the tracker(s) before downloading and rely on DHT and PEX instead. DHT and PEX are supported by all the major BitTorrent clients nowadays and users will be able to download just as quickly as they are used to. Instead of going through a central tracker, DHT and PEX allow BitTorrent users to get all the information they need from the swarm, and avoid the prying eyes of many anti-piracy outfits by doing so. Although monitoring DHT is harder than using the BitTorrent trackers to gather ‘evidence’, it is not impossible. But since the leading BitTorrent tracking organization Dtecnet has no clue about DHT, we assume that it might take a while before their evidence gathering techniques are updated. Buying Anonymity For a few pounds a month file-sharers can circumvent the Digital Economy Act entirely with a VPN. These services offer an encrypted tunnel between your home connection and an external server and will exchange your IP-address for one in another country where UK laws don’t apply. Besides avoiding being tracked by anti-piracy outfits, a VPN will also allow access to all of the sites that may be blocked under the new legislation. There are thousands of VPN services available on the Internet. Itshidden is a popular one among BitTorrent users, but Hidemyass and Swiss VPN have received positive reviews as well. The Pirate Bay folks offer one of the cheapest solutions, they launched their Ipredator VPN a year ago after Sweden passed their new anti-piracy law. Ditch BitTorrent What hasn’t been mentioned too often is that the Digital Economy Act only targets a select group of file-sharers – those who upload material. It is expected that BitTorrent and Gnutella-based applications such as Limewire will be the main targets, simply because they are the easiest to monitor. However, there are several other ways to download copyrighted content on the Internet. Usenet providers offer premium download services that cannot be monitored easily, and as we mentioned in a previous article, there are also hundreds of MP3 search engines that allow users to download files directly on their computers without being tracked. The bottom line is that no matter what legislation governments introduce, it is doubtful that it will have an effect on heavy file-sharers or those that can be bothered to spend 30 minutes using Google. It might deter some novice file-sharers, but the question is at what expense? As The Guardian rightfully notes today, the Act might lead to hundreds or thousands of people losing their connection based on false evidence. Is that worth it? http://torrentfreak.com/how-file-sha...cy-act-100412/  Geist: Talks on Secret Anti-Counterfeiting Treaty Spring a Leak Michael Geist Negotiations on the Anti-Counterfeiting Trade Agreement resume today in Wellington, New Zealand, with Canada, the United States, the European Union, and a handful of other countries launching the eighth round of talks. While even the most optimistic ACTA supporters do not expect to conclude an agreement before the end of the year, the next five days may prove to be a pivotal point in the negotiations since over the past several weeks, there have been two major leaks that could dramatically alter the still-secret discussions. The first leak was an internal Dutch government document chronicling the positions of each ACTA participant on treaty transparency. The level of ACTA secrecy is highly unusual for an agreement focused on intellectual property issues, leading to a steady stream of parliamentary resolutions and political demands for transparency coming from around the globe. The standard response to transparency criticisms from many governments (including Canada) was to claim that they favoured releasing the ACTA text to the public, but that other unnamed countries did not. Since there was no consensus, the text could not be released. The Dutch leak succeeded in blowing the issue wide open by identifying precisely which countries posed barriers to transparency. The document identified the U.S., Singapore, South Korea, and a trio of European countries as the remaining holdouts. Once publicly identified, the European countries quickly reversed their positions. The EU now unanimously supports releasing of the text, alongside Canada, Australia, New Zealand, Japan and Switzerland. With the outing of the transparency issue, it will fall to the U.S., which is widely viewed as the critical stumbling block, to justify its insistence on keeping the treaty secret. Maintaining support for secrecy also faces a second pressure point – the second major leak was a copy of the draft agreement itself. In other words, while countries maintain official positions of treaty secrecy, a draft is readily available for anyone with Internet access. Because the text has not been officially released, however, government officials have refused to comment on substantive provisions revealed by the leaked document. Identifying the opposition to transparency may have been welcome news, but the availability of the leaked text was more bittersweet. On the one hand, ACTA watchers were grateful for the opportunity to see first-hand what has been discussed behind closed doors for the past three years. On the other, the text confirmed many fears about the substance of ACTA. If adopted in its current form, the treaty would have a significant impact on the Internet, leading some countries to adopt three-strikes-and-you're-out policies that terminate subscriber access due to infringement allegations, increasing legal protection for digital locks, mandating new injunction powers, implementing statutory damages provisions worldwide, and engaging in widespread data sharing across national borders. Moreover, ACTA may live as an institution that potentially replaces some of the responsibilities currently performed by the United Nations' World Intellectual Property Organization. Canada drafted the institutional chapter, which envisions an oversight council, secretariat, dispute resolution, and technical assistance to developing countries. While some countries insist ACTA will not change their domestic laws, the leaked text suggests that this is very unlikely since there remains considerable disagreement on some provisions. In fact, the New Zealand round of talks may mark the first time countries seriously begin to bargain on key provisions, setting up a week that may go a long way to determine the future scope of the treaty. http://www.thestar.com/news/sciencet...-spring-a-leak  PublicACTA Hammers Out 'Wellington Declaration' Critics of intellectual property treaty call for independent national impact analysis Stephen Bell About 120 attendees at the PublicACTA conference gave up nine hours of Saturday to hammer out “The Wellington Declaration” — intended to be a constructive criticism of the Anti-Counterfeiting Trade Agreement ACTA). The Declaration stresses the need for an independent impact analysis of ACTA’s operation in New Zealand before this country signs the treaty. A national impact analysis is provided in the ACTA process but this is likely to be performed by officials from the Ministries of Foreign Affairs and Economic Development who have assisted in the negotiations, said a former public servant at the meeting; they are unlikely to be very critical of something they helped put together, he suggested. ACTA is an international treaty being negotiated between major powers the US, EU and Japan as well as others including Canada, Australia. Mexico and New Zealand. Its original focus was on counterfeit goods, but leaked drafts have revealed a much broader scope, raising concerns of an intellectual property crackdown online. The Declaration also promoted the World Intellectual Property Oragnisation (WIPO) as the most appropriate venue for any such treaty negotiation. "We note that the World Intellectual Property Organisation has public, inclusive and transparent processes for negotiating multilateral agreements on (and a committee dedicated to the enforcement of) copyright, trademark and patent rights, and thus we affirm that WIPO is a preferable forum for the negotiation of substantive provisions affecting these matters." The Declaration urges that ACTA must address exceptions and limitations to copyright, such as fair use and fair dealing, "to maintain the balance that is fundamental to copyright". It also says that technical protection measures (TPMs) should not themselves be protected in the treaty and that TPMs should not infringe on or limit rights to use or access copyright material in a manner that would otherwise be permitted. It was crucial, said PublicACTA keynote speaker Michael Geist, that the declaration avoid taking too oppositional an attitude. That, he told delegates, would make PublicACTA too easy to dismiss as a fringe lobby, pro-counterfeiting, opposed to copyright and in league with pirates, terrorists and other groups alleged by ACTA champions to benefit from loose legislation. Canadian lawyer Geist and fellow keynoter Kimberlee Weatherall, senior lecturer at Melbourne University’s School of Law, tackled some of the hot-buttons such as the three-strikes procedure for punishing repeat offenders — it may only be a footnote in leaked drafts, but “if you dig deeper, it’s there,” Geist said — and less well-canvassed aspects, such as ways in which ACTA materially extends provisions under the TRIPS agreement, rather than merely strengthening enforcement of the existing provisions. Secondary liability of intermediaries such as ISPs has not been a feature of international treaties to date, says Weatherall. She suggested that in view of existing protection under TRIPS, adoption of ACTA would not give copyright owners material additional protection, while it would impose major strictures on consumers and intermediaries. Strict control of methods for circumventing technological copyright protection measures on digital media threatens to affect freedom to do legal acts such as research and review on copyright works, the keynoters pointed out. ACTA, the keynoters and others said, should return to its original purpose and leave copyright, trademark and patent protection to existing laws and treaties. The meeting als called strongly for more transparency and the release of drafts of the ACTA text. The official ACTA Wellington meeting has discussion of transparency set down for its last day, Friday, April 16. The keynotes were followed by general discussion among the delegates and a four-person panel (consultant Julian Carver, InternetNZ policy director Jordan Carter, InternetNZ Victoria University Cyberlaw Fellow Jonathan Penney and the Creative Freedom Foundation’s Bronwyn Holloway-Smith). After a break for lunch, groups of delegates at the dozen tables were each handed two topics on which to formulate concise position statements. Each of the statements was then critiqued by the whole body of attendees. Moderator Nathan Torkington managed the process efficiently: “any more amendments for this section? Going once…going twice…Yes Michael [Geist] you have a suggestion?…Right, looks like we’re finished with that one.” The Wellington Declaration was in its final form not long after the 6pm deadline originally set down. Disclosure: Stephen Bell took a small active part in the debate, as a member of the table that drafted the parts of the Wellington Declaration dealing with technological protection mechanisms and privacy protection. He also offered criticism of some of the wording of other sections. http://computerworld.co.nz/news.nsf/...on-declaration  Secretive Counterfeiting Treaty Talks Open up Paul Meller A controversial plan to crack down on online piracy and counterfeiting will be opened up to public scrutiny for the first time next week, when the negotiating text of a secret international copyright treaty will be made public, the European Commission said Friday. Negotiations over the past two years have been conducted in secret. Leaks of the draft text have sparked a public outcry, mainly because of how the text deals with online copyright infringement. Countries involved in talks on the Anti-counterfeiting Trade Agreement (ACTA) agreed unanimously to make the documents available to the public at a meeting in New Zealand this week, the Commission said in a statement. However, they don't plan to reveal their individual negotiating positions. "In agreeing to release publicly this draft text in the particular circumstances of this negotiation, participants reaffirmed the importance of maintaining the confidentiality of their respective positions in trade negotiations," the Commission said. The Commission has never commented directly about the leaked copies of the ACTA draft text but it has refuted claims that the treaty would force signatory countries to introduce a so-called graduated response rule that would ban copyright offenders from the Internet after a series of warnings. In leaked texts seen by IDG, the draft treaty doesn't mandate the graduated-response approach but it does suggest that countries adopt such laws. It also calls for Internet service providers to become liable for the content being distributed on their networks. Under existing E.U. laws, ISPs should not be held responsible for content such as illegally copied music or movies that are commonly distributed via peer-to-peer networks. The Commission has always denied that the treaty would go this far. In Friday's statement it said ACTA "will not interfere with a signatory's ability to respect its citizens' fundamental rights and liberties." The participants in the ACTA talks next meet in Switzerland in June. They aim to conclude the talks "as soon as possible in 2010." The Commission said that making the draft text public will help the countries to reach a final conclusion. Participants include the U.S., E.U., Japan, Canada, Australia and South Korea, New Zealand and Switzerland. http://www.pcworld.com/article/19438...s_open_up.html  Feds Raise Questions About Big Media's Piracy Claims Greg Sandoval After spending a year studying how piracy and illegal counterfeiting affects the United States, the Government Accountability Office says it still doesn't know for sure. Congress tasked the GAO in April 2009 with reviewing the efforts to quantify the size and scope of piracy, including the impacts of Web piracy to the film and music industries. In a 32-page report issued Monday, the GAO said most of the published information, anecdotal evidence, and records show that piracy is a drag on the U.S. economy, tax revenue, and in some cases potentially threatens national security and public health. But the problem is, according to the GAO, the data used to quantify piracy isn't reliable. "Three widely cited U.S. government estimates of economic losses resulting from counterfeiting cannot be substantiated due to the absence of underlying studies," the GAO said. "Each method (of measuring) has limitations, and most experts observed that it is difficult, if not impossible, to quantify the economy-wide impacts." In what appears to be a setback for Hollywood and the recording industry, the government said that it sees problems with the methodology used in studies those sectors have long relied on to support claims that piracy was destructive to their businesses. The accountability office even noted the existence of data that shows piracy may benefit consumers in some cases. "Some experts we interviewed and literature we reviewed identified potential positive economic effects of counterfeiting and piracy," The GAO wrote. "Some consumers may knowingly purchase a counterfeit or pirated product because it is less expensive than the genuine good or because the genuine good is unavailable, and they may experience positive effects from such purchases." "Consumers may use pirated goods to 'sample' music, movies, software, or electronic games before purchasing legitimate copies," the GAO continued. "(This) may lead to increased sales of legitimate goods." To be sure, the GAO found evidence that piracy is large and harmful. But if leaders of the media world were hoping for a government document that proved their many claims that piracy and counterfeiting cost it billions every year and cost the U.S. economy jobs and revenue, then they will be disappointed because this report wasn't that document. The GAO did not say assertions by media companies were wrong, but it did point out what it considered weaknesses with how they measured piracy's impacts. At the very least, the GAO report hands file-sharing proponents some valuable ammo in their long-running debate with entertainment sector over file sharing. "The GAO study confirms that piracy of all sorts is rampant," said a spokesman for the Motion Picture Association of America (MPAA). "Getting a firm handle on the problem in terms of dollar estimates is complicated." What is most compelling about the report is where it comes from. The GAO is not known for being a radical free-content group. Once known as the General Accounting Office, it is the audit and investigative arm of Congress. In 2008, lawmakers were seeking ways to strengthen efforts to protect intellectual property, and tasked the GAO with conducting the study. The review went far beyond digital music, movies, and software. Among the sectors the GAO reviewed were toys, clothing, automobile parts, and medicine. The GAO said it examined "research on the effects of counterfeiting and piracy on consumers, industries, government, and the U.S. economy." The organization also wanted to learn about efforts to quantify piracy. The GAO said it during the past year that it found most of the "information and views" on the subject focused on the negative effects of piracy. "Americans are the world's leading innovators, and our ideas and intellectual property are a key ingredient to our competitiveness and prosperity," the GAO wrote. "Negative effects on U.S. industry (from piracy) may include lost sales, lost brand value, and reduced incentives to innovate. However, industry effects vary widely among sectors and companies. The U.S. government may lose tax revenue, incur (intellectual property) enforcement expenses, and face risks of counterfeits entering supply chains with national security or civilian safety implications. "The U.S. economy as a whole may grow more slowly because of reduced innovation and loss of trade revenue," the report concluded. Some media outlets have reported that counterfeit goods can be traced to organized crime and groups that support terrorism. Consumers may face danger when counterfeit and unsafe toys and medicine enter the marketplace. Fake airplane parts have also been discovered in the aviation industry, according to the GAO's report. The GAO said most of the experts and literature available concluded that piracy caused more harm than good but after stating this, the GAO waded into a long explanation of why the problem of measuring piracy's impacts with any degree of accuracy may be impossible. One example of this is how experts disagree over the potential impacts of piracy on jobs. One leader in the field told the GAO that piracy kills jobs, while another said "any effects are unclear" because job loss in one sector may result in a "rise in other industries as workers are hired to produce counterfeits." When it came to previous studies or surveys on piracy, the GAO noted that it had questions and concerns with data produced by both the film and music industries to support financial loss claims. Jonathan Lamy, a spokesman for the Recording Industry Association of America, said he hadn't read the report and didn't know what studies the GAO referred to but said plenty of studies have reached the same conclusion. "There's no doubt that the music industry has declined significantly over the last 10 years," Lamy said. "Countless studies have blamed this on the fact that millions of people have been getting their music for free online. That has translated to thousands of lost jobs in the industry and that's undeniable." What Congress plans to do with this report is unclear. http://news.cnet.com/8301-31001_3-20002304-261.html  Ireland Is Latest With Plan to Cut Into Copyright Violations Eric Pfanner A judge in Ireland on Thursday cleared the way for the implementation of a crackdown on Internet piracy, dismissing the Irish Data Protection Commissioner’s concerns that the plan could result in the invasion of privacy. The judge upheld the legality of an agreement between Eircom, the largest Internet service provider in Ireland, and the music industry. Under the deal, Eircom has agreed to suspend digital pirates’ Internet connections if they ignore repeated warnings to stop the unauthorized copying of music. In his ruling, the judge, Peter Charleton, issued a strong defense of the rights of copyright owners. “The Internet is only a means of communication,” he wrote. “It is not an amorphous extraterrestrial body with an entitlement to norms that run counter to the fundamental principles of human rights. There is nothing in the criminal or civil law which legalizes that which is otherwise illegal simply because the transaction takes place over the Internet.” The music industry has been urging Internet service providers to take stronger action against piracy, though they have generally resisted measures like those agreed to by Eircom. In France and Britain, governments have approved laws authorizing suspension of pirates’ Internet accounts, though these measures have not yet gone into effect. The International Federation of the Phonographic Industry hailed the decision in Ireland. “This sends a strong message to governments that are now considering how to help their creative industries address the threat of mass online piracy,” the group said. http://www.nytimes.com/2010/04/17/te.../17eircom.html  New Copyright Fee Will See Students Pay More for Learning Materials Government considering $45-per-student charge, which will apply to all manner of copying, even if the material is free to use Rory McGreal The price of education is poised to rise again. Access Copyright has just published a fee proposal with the Copyright Board of Canada that will substantially increase the fees that college and university students pay for their learning content. Titled the Access Copyright Post-Secondary Educational Institution Tariff, this levy of $45 per student, if accepted by the board, would cover all manner of copying by students and teachers, whether digital or print, video or audio, online or offline, coursepacks or class handouts, in the library or at home, in the classroom or e-learning. A Powerful Force Access Copyright, a copyright licensing agency created to support the interests of publishers and some creators, carries a big stick. Institutions are liable for "statutory damages" of thousands of dollars for each and every infringement, even if no real damages can be proven and even if the teacher or student is acting in good faith. A university or college could be held liable for more than $100,000 for distributing an unauthorized article or book chapter to just one class. Access Copyright have sued users in the past and can be expected to continue and even ramp up their legal enforcement. Universities are already paying for the use of course content through text book purchases, library licences and other means. Much content is also available for free as open education resources or in the public domain. This type of course content is not controlled by Access Copyright. At many institutions, this free or library-licensed content represents more than 50 per cent of the material used in teaching. Yet, according to the Access Copyright fee proposal, students at these institutions would pay the same rate per student as an institution that only uses Access Copyright controlled content. In effect, colleges and universities will have to pay twice for using the same materials. Bookkeeping Nightmare If the money grab were not enough, Access Copyright also wishes to burden institutions with the responsibility for monthly reporting on every page that is made available to students, including not only extensive bibliographic data, but also information on the number of students in every class, the number of staff, the term dates, the course names and codes, and electronic addresses. And, their agents will have the right of full access to secure institutional computer systems to spy on teachers and students use of all content. More significantly, this tariff will serve as a disincentive for institutions that want to increase their use of free materials. With a per-student levy, there is no advantage in accessing and using the growing free educational content available on the Internet. Today, there are thousands of free full university courses and millions of other open content resources that can be used for education. Yet with this tariff, an institution that uses this content extensively will still pay the same as an institution that uses only proprietary content. Worse, the tariff will serve as a positive incentive for institutions to make even more use of Access Copyright content, thus providing that agency with an argument for raising their fees even higher in the future. This type of intervention is not possible in the U.S. and other countries where the fair use of content for learning is allowed free of any charges. U.S. teachers circulate handouts and articles to their students as a copy right. Double Standard Canada stands out in not allowing such fair use for education. It is interesting that publishers and agencies like Access Copyright are strongly supporting the adoption in Canada of U.S.-like restrictions on copyright, such as laws protecting digital locks, but are strongly opposed to bringing in U.S.-like flexibility for educational uses of content. A new copyright bill is being considered and it is time now for Parliament to extend our fair dealing exceptions to teaching and learning like in other countries. In Canada, provincial ministries of education and school boards are liable for $40 million in retroactive payments to Access Copyright based on previous rulings regarding elementary and high school activities. This money grab only serves to highlight the importance of open educational resources in the future of learning in Canada and internationally. Are taxpayer financed public institutions going to continue financing the creation of learning materials and then buying them back from artificially created private entities? Or are we going to begin opening up our content and sharing it with each other so that we can bypass them and take full advantage of our own work? Access Copyright uses its funds to support its interests and distributes other funds to administrators, publishers and creators. According to its annual report, of the nearly $35 million it collected in revenues from Canadian public educational institutions in 2009, more than $6 million -- or 23.6 per cent -- was paid out in salaries and other administrative costs, and an additional $2 million -- or six per cent -- was spent on travel, lobbying and other business, including more than $900,000 for applications to Copyright Canada. Canadian taxpayers are paying for Access Copyright through these onerous levies on our students and educational institutions. Do we really want to pay more to support a superfluous bureaucracy of unaccountable collective managers? http://www.edmontonjournal.com/busin...884/story.html  Liam Gallagher: Musicians Should Take Illegal Downloading as A Compliment Liam Gallagher, Oasis' former frontman, has always displayed a ‘fuck off!” attitude and never censored his views or his language for that matter when asked (or not) about a certain issue. Recently he shared his opinion about file-sharing which he compared to taping songs broadcast during the weekly chart show as a youngster. Moreover, he criticized artists who desperately claim file sharing must be stopped insteadof being grateful that people take interest in their music. In an interview to Shortlist magazine Gallagher said: “Downloading’s the same as what I used to do – I used to tape the charts of the songs I liked [off the radio]. I don’t mind it. “I hate all these big, silly rock stars who moan – at least they’re fuckin’ downloading your music, you c*nt, and paying attention, know what I mean?” His attack to established musicians who complain about those who download their music using file sharing sites was pretty straightforward: “You should fuckin’ appreciate that – what are you moaning about? “You’ve got fuckin’ five big houses, so shut up.” The singer currently working on his debut solo album, which he said was scheduled for release in 2011. http://www.p2pon.com/2010/04/12/liam...-a-compliment/  Law Firm to Quit Chasing File Sharing Pirates TBI bows out of illegal file sharing business Tilly, Bailey and Irvine Solicitors (TBI) has said it will stop sending out letters of claim, accusing people of illegally sharing copyrighted material, because it fears the adverse publicity generated by the work could impact negatively on its business. In a letter sent to the Solicitors Regulation Authority (SRA) on April 1, TBI wrote: ‘We have been surprised and disappointed at the amount of adverse publicity that our firm has attracted in relation to this work and the extra time and resources that have been required to deal solely with this issue. ‘We are concerned that the adverse publicity could affect other areas of our practice and therefore following discussions with our clients, we have reluctantly agreed that we will cease sending out further letters of claim. TBI concluded: ‘We should stress that this decision is based on purely commercial reasons and does not alter our view that our conduct has always complied with the Solicitors Code of Conduct (SCoC).' Readers' complain to Which? about TBI Earlier this year, Which? received a number of complaints from readers who had received letters from TBI accusing them of illegally sharing pornography via the internet. The readers were threatened with legal action unless they agreed to pay £700 in compensation within 14 days. After reviewing the letters, Which? asked the SRA to investigate TBI’s conduct, which it considered to be in breach of the SCoC. Commenting on TBI’s decision to quit the illegal file sharing arena, Deborah Prince, Which’s head of in-house legal, said: ‘This is fantastic news. I’m really pleased to hear that TBI has seen sense and has decided to move out of the volume file-sharing litigation business. ‘Hopefully, other law firms thinking of going down a similar route will begin to realise that although this work can generate vast financial rewards for law firms and their clients, it can also bring a lot of adverse publicity simply because the practice is inherently unfair and unethical. ‘The letters of claim that we have seen from three law firms [ACS Law Solicitors, Davenport Lyons and TBI] have been disproportionate responses to the alleged illegal file sharing activity. We also believe they were bullying in tone and that the behaviour of these firms breached the SCoC.' Which?'s view on illegal file sharing activity? Dr Prince added: ‘With regards to any alleged illegal file sharing activity, Which? favours the proportionate and graduated response advocated by the Digital Economy Bill not simply scaring people, many of whom are innocent, into out of court settlements because they feel disempowered financially to fight the claim in court. In light of TBI’s decision to stop sending out further letters of claim, the SRA said it was considering whether any further action against the firm was necessary. http://www.which.co.uk/news/2010/04/...pirates-210736  Anti-Piracy Firm Defends Net Hunt Jane Wakefield Anti-piracy firm DigiProtect, which has teamed up with UK law firm ACS:Law to send thousands of letters to alleged net pirates, has defended its actions. It follows widespread condemnation of their methods, which involves mass-mailing alleged file-sharers asking them to pay a fine or face court. UK consumer magazine Which? has received complaints from people saying they have been wrongly accused. DigiProtect told the BBC it is just protecting its rights-holders. The German-based firm refused to divulge the names of its clients, saying only that they were "musicians or producers". It has no UK-based clients although the firm said it was about to start marketing its service in Britain. The service works by mutual agreement with rights holders. DigiProtect identifies when its clients' content is being shared illegally on file-sharing networks. Armed with IP (internet protocol) addresses - which identify the computer used in any copyright infringement - its lawyers can then apply for a court order to get the physical address of a computer from the service provider whose network has been used for the file-sharing. Wrongly identified A letter is then sent to the alleged pirate, asking them to either pay a one-off fee of around £700 per infringement or face court action. Customers of service provider O2 have been among those targeted and the ISP has condemned attempts to "bully or threaten our customers", a charge DigiProtect and ACS: Law deny. "The approach we use is the only proven effective proceeding," the firm said in an exclusive statement for the BBC. It admitted that much of the monitoring of file-sharing networks that it does in order to identify illegal content is an "automated process". "With the infinite number of products offered on file-sharing networks, no other process would even be possible, this is just another example of the astronomical dimensions that file-sharing has taken on," it said. It also conceded that some people may have been wrongly identified. "In some cases the subscriber is not the rule breaker, but as they own the internet access they are our initial point of contact. We make an enquiry of them as to how the infringement occurred and progress with the matter in an appropriate way depending on the response given," it said. Consumer magazine Which? has been contacted by a number of people who say they have been wrongly accused of downloading material. Some, including pensioners, said they had no idea how to share files. DigiProtect made no apology to those wrongly accused. "You have to regard the damages that are caused by illegal file-sharing. The ones who are traumatised are the content providers," it said. Adverse publicity Illegal file-sharing has been a huge problem for music and film industry and a recent industry study, by economics firm TERA Consultants, estimated that the UK's creative industries experienced losses of £1.2bn in 2008 due to piracy. The Digital Economy Bill has just become law and it allows rights-holders to pursue file-sharers and, in extreme cases, temporarily cut their internet access. The BPI, which represents the British music industry and lobbied hard to push the bill through parliament, has been keen to distance itself from the methods used by DigiProtect and ACS: Law. It told the BBC that legal action should be reserved for the worst offenders rather than "widely used as a first response". But DigiProtect defended its method. "Our rights holder clients prefer the methods we adopt, together with the positive and direct benefits they derive from them," the statement said. It added that it "pays the rights holder at least 50% of the amount that remains after deducting all costs". Last week, law firm Tilly, Bailey and Irvine (TBI) which had been sending similar letters, said it would end its campaign. "We have been surprised and disappointed by the amount of adverse publicity that our firm has attracted in relation to this work," John Hall, managing partner at TBI said in a statement. "Following discussions with our clients we have reluctantly agreed that we will cease sending out further letters of claim," it added. Deborah Prince, head of legal affairs at Which? said she was pleased that TBI had decided to stop the practice. "Hopefully, other law firms thinking of going down a similar route will refrain as we believe the practice is inherently unfair and unethical," she said. http://news.bbc.co.uk/go/pr/fr/-/2/h...gy/8619407.stm  Malware Threatens to Sue BitTorrent Downloaders David Kravets A new malware scam is trying to dupe BitTorrent users into coughing up serious cash for illegally downloading copyrighted material.  The code displays a box with the message “Warning! Piracy detected!” and opens a web page purportedly run by a Swiss company “committed to promoting the cultural and economic benefits of copyright.” The fake company, the ICCP Foundation, also claims to be backed by the Recording Industry Association of America, the Motion Picture Association of America and others. “It appears to scan the user’s hard drive for .torrent files and displays these as ’evidence’ of an earlier infringement,” wrote TorrentFreak, which first disclosed the malware. Quote:
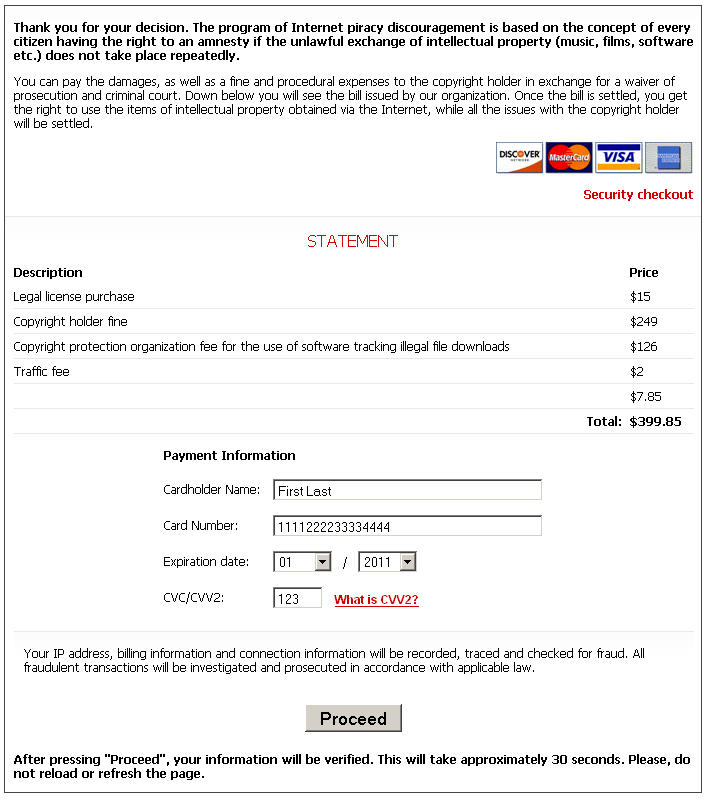 Security researcher Dancho Danchev quipped Monday that the scam “is perhaps the first recorded case of cybercriminals ignoring the basics of micropayments, and emphasizing on profit margins by attempting to extort the amount of $400.” He thinks those behind the latest malware are associated with the Koobface worm and a money-mule recruitment campaign. As F-Secure Labs advises: “Refuse to pay money to these clowns!” http://www.wired.com/threatlevel/2010/04/ransomware  Porn Virus Blackmails its Victims BBC A new type of malware infects PCs using file-share sites and publishes the user's net history on a public website before demanding a fee for its removal. The Japanese trojan virus installs itself on computers using a popular file-share service called Winni, used by up to 200m people. It targets those downloading illegal copies of games in the Hentai genre, an explicit form of anime. Website Yomiuri claims that 5500 people have so far admitted to being infected. The virus, known as Kenzero, is being monitored by web security firm Trend Micro in Japan. Masquerading as a game installation screen, it requests the PC owner's personal details. It then takes screengrabs of the user's web history and publishes it online in their name, before sending an e-mail or pop-up screen demanding a credit card payment of 1500 yen (£10) to "settle your violation of copyright law" and remove the webpage. Held to ransom The website that the history is published on is owned by a shell company called Romancing Inc. It is registered to a fictitious individual called Shoen Overns. "We've seen the name before in association with the Zeus and Koobface trojans. It is an established criminal gang that is continuously involved in this sort of activity," said Rik Ferguson, senior security advisor at Trend Micro. Kenzero is a twist on ransomware, he added, which infects a computer and encrypts the documents, pictures and music stored on it, before demanding a fee for a decryption key. "Interestingly we've seen a separate incident that focuses on European victims," he said. A fictitious organization calling itself the ICPP copyright foundation issues threatening pop-ups and letters after a virus searches the computer hard drive for illegal content - regardless of whether it actually finds anything. It offers a "pretrial settlement" fine of $400 (£258) payable by credit card, and warns of costly court cases and even jail sentences if the victim ignores the notice. However rather than take the money, the outfit sells on the credit card details, said Mr Ferguson. "If you find you are getting pop-ups demanding payments to settle copyright infringement lawsuits, ignore them and use a free online anti-malware scanner immediately to check for malware," was his advice. "And if there's online content that you want to get hold of, get it from a reputable website - if that means paying that's what you have to do." http://news.bbc.co.uk/go/pr/fr/-/2/h...gy/8622665.stm  Viacom: Google Used Piracy to Coerce Content Owners Greg Sandoval Viacom says newly released documents in its copyright fight with Google over the search engine's YouTube subsidiary help prove its case. We've heard these kinds of sweeping declarations from both sides throughout the legal standoff, which began when Viacom filed a $1 billion lawsuit against Google in 2007, claiming YouTube encouraged users to commit intellectual property theft. A review of the documents filed with the court on Thursday shows that much of the material, such as Google employees making critical statements about YouTube's "rogue" business model before buying the video sharing site in October 2006 have been well covered. But Viacom said in a statement that the new documents show Google "made a deliberate, calculated business decision not only to profit from copyright infringement, but also to use the threat of copyright infringement to try to coerce rights owners like Viacom into licensing their content on Google's terms." "It's revealing that Viacom is trying to litigate this case in the press," said a YouTube representative. "These documents aren't new. They are taken out of context and have nothing to do with this lawsuit." Viacom has indeed alleged many times in the past that Google very early had the ability to prevent pirated content from going up at YouTube but chose not to do so. Viacom suggests that Google told film, TV, and music companies that if they wanted their content protected at YouTube, they would have to license that content to YouTube under favorable terms. Despite Google's claims that the revelations Thursday aren't new, Viacom did produce a previously undisclosed slide from a Google presentation from 2006. The document appears to outline a potential strategy for handling content and entertainment companies and some of the contents raise questions. On a page titled "Overall Recommendations" Google managers list a series of bullet points: • Change terms with premium content providers. • Pressure premium content providers to change their model towards free. • Adopt "or else" stance (regarding) prosecution of copyright infringement elsewhere." • Set up "play first, deal later" around "hot content." The date on the presentation was March-May 2006, at least five months before Google acquired YouTube. At that point Google's video-sharing site, Google Video, was falling behind YouTube, which was becoming synonymous with online video. So, does the document Viacom produced signal that Google decided to adopt a more aggressive approach to content and entertainment companies, one that mirrored YouTube's? Or was this an outline for a policy that Google wanted content creators to adopt? For instance, the line about adopting an "or else stance" regarding copyright infringement could have been Google's plan to get studios and music companies to force YouTube to do more to stop piracy. Viacom has already produced numerous documents that show many at Google--before it acquired YouTube--believed the video site wrongly benefited from the unauthorized film and TV clips posted to the site. On Thursday, Viacom offered more of these statements. "[W]e should beat YouTube by improving features and user experience, not being a 'rogue enabler' of content theft," said one Google senior employee, according to court documents. As for the line about "play first, deal later around hot content," it's harder to determine what message Google might have wanted to convey to the studios with that statement. Some content creators will likely read that and believe Google was preparing to adopt a policy they claim many technology companies have embraced over the years: ask forgiveness, not permission. Media companies have long accused start-up online music and video services of deliberately using their material without permission in order to build audiences, and later, after establishing their businesses, request licensing deals. Critics of the start-ups say that this is done to improve their bargaining power. A studio or music label may find it harder to say no to a licensing deal when a service already boasts millions of followers, or so the theory goes. Neither Google nor Viacom commented directly on the slide. Google has always said that it respects copyright owners, has numerous partnerships with progressive-thinking film and music providers, and is protected by the Digital Millennium Copyright Act. The DMCA says that Internet service providers are protected from liability for copyright violations committed by users. The case is expected to go to trial sometime this year, but that won't likely be the end of the fight. Whoever loses this round will undoubtedly appeal. In May 2008, Schmidt said he is prepared to fight Viacom all the way to the Supreme Court. http://news.cnet.com/8301-31001_3-20002620-261.html  The Entertainment Industry's Dystopia of the Future Richard Esguerra We're not easily shocked by entertainment industry overreaching; unfortunately, it's par for the course. But we were taken aback by the wish list the industry submitted in response to the Intellectual Property Enforcement Coordinator's request for comments on the forthcoming "Joint Strategic Plan" for intellectual property enforcement. The comments submitted by various organizations provide a kind of window into how these organizations view both intellectual property and the public interest. For example, EFF and other public interest groups have asked the IPEC to take a balanced approach to intellectual property enforcement, paying close attention to the actual harm caused, the potential unexpected consequences of government intervention, and compelling countervailing priorities. The joint comment filed by the Motion Picture Association of America (MPAA), the Recording Industry Association of America (RIAA) and others stands as a sharp contrast, mapping out a vision of the future where Big Media priorities are woven deep into the Internet, law enforcement, and educational institutions. Consider the following, all taken from the entertainment industry's submission to the IPEC. "Anti-infringement" software for home computers “There are several technologies and methods that can be used by network administrators and providers...these include [consumer] tools for managing copyright infringement from the home (based on tools used to protect consumers from viruses and malware).” In other words, the entertainment industry thinks consumers should voluntarily install software that constantly scans our computers and identifies (and perhaps deletes) files found to be "infringing." It's hard to believe the industry thinks savvy, security-conscious consumers would voluntarily do so. But those who remember the Sony BMG rootkit debacle know that the entertainment industry is all too willing to sacrifice consumers at the altar of copyright enforcement. Pervasive copyright filtering “Network administrators and providers should be encouraged to implement those solutions that are available and reasonable to address infringement on their networks. [This suggestion is preceded by a list of filtering methods, like protocol filtering, fingerprint-based filtering, bandwidth throttling, etc.]” The entertainment industry loves widespread filtering as a "solution" to online copyright infringement — in fact, it has successfully persuaded Congress to push these technologies on institutions of higher-education. But this "solution" is full of flaws. First, even the "best" automated copyright blocking systems fail to protect fair use. Worse, these techniques are unlikely to make any lasting dent on infringing behavior, but will instead just invite the use of more encryption and private "darknets" (or even just more hand-to-hand sharing of hard drives and burned DVDs). But perhaps the most pernicious effect may be that copyright protection measures can be trojan horses for consumer surveillance. In an age of warrantless wiretapping and national censorship, building more surveillance and inspection technologies into the heart of the Internet is an obviously bad idea. In the words of the Hollywood movie, "if you build it, they will come." Intimidate and propagandize travelers at the border “Customs authorities should be encouraged to do more to educate the traveling public and entrants into the United States about these issues. In particular, points of entry into the United States are underused venues for educating the public about the threat to our economy (and to public safety) posed by counterfeit and pirate products. Customs forms should be amended to require the disclosure of pirate or counterfeit items being brought into the United States.” Does that iPod in your hand luggage contain copies of songs extracted from friends' CDs? Is your computer storing movies ripped from DVD (handy for conserving battery life on long trips)? Was that book you bought overseas "licensed" for use in the United States? These are the kinds of questions the industry would like you to answer on your customs form when you cross borders or return home from abroad. What is more, this suggestion also raises the specter of something we've heard the entertainment industry suggest before: more searches and seizures of electronic goods at the border. Once border officials are empowered to search every electronic device for "pirated" content, digital privacy will all but disappear, at least for international travelers. From what we've learned about the fight over a de minimis border measures search exclusion in the latest leaked text, ACTA might just try to make this a reality. Bully countries that have tech-friendly policies “The government should develop a process to identify those online sites that are most significantly engaged in conducting or facilitating the theft of intellectual property. Among other uses, this identification would be valuable in the interagency process that culminates in the annual Special 301 report, listing countries that fail to provide adequate and effective protection to U.S. intellectual property rights holders. Special 301 could provide a focus on those countries where companies engaged in systematic online theft of U.S. copyrighted materials are registered or operated, or where their sites are hosted. Targeting such companies and websites in the Special 301 report would put the countries involved on notice that dealing with such hotbeds of copyright theft will be an important topic of bilateral engagement with the U.S. in the year to come. (As noted above, while many of these sites are located outside the U.S., their ability to distribute pirate content in the U.S. depends on U.S.-based ISP communications facilities and services and U.S.-based server farms operated commercially by U.S.-based companies.)” Some background: the Special 301 process is a particularly unpleasant annual procedure by which the United States Trade Representative (USTR) pressures other countries to adopt tougher intellectual property laws and spend more for IP enforcement. In the Special 301 report, the USTR singles out particular countries for their "bad" intellectual property policies, placing them on a watch list, and threatening trade sanctions for those that deny "adequate and effective protection" for US IP rightsholders or restrict fair and equitable market access for US intellectual property. Before this year, the US Trade Representative only sought input from the entertainment and pharmaceutical industries for these rankings, resulting in unbalanced assessment criteria. Countries have been listed for failing to sign on to controversial international treaties or for not mirroring certain parts of US law. For example, Chile was named for considering fair use-style exceptions to its copyright law; Canada was listed for requiring that its customs officers have a court order before seizing goods at the border; and Israel was highlighted for refusing to adopt DMCA-style anti-circumvention provisions after legislative debate concluded that anti-circumvention laws would have no effect on copyright infringement. The creative communities' proposal imagines that the US Trade Representative should become a glorified messenger for Big Media, using its resources to pressure countries that "harbor" websites and Internet services that facilitate copyright infringement. In other words, they believe that the USTR should put US IP rightsholders' interests at the center of its foreign policy, ignoring other foreign policy goals such as regional security, and promoting innovation and competition. Federal agents working on Hollywood's clock “The planned release of a blockbuster motion picture should be acknowledged as an event that attracts the focused efforts of copyright thieves, who will seek to obtain and distribute pre-release versions and/or to undermine legitimate release by unauthorized distribution through other channels. Enforcement agencies (notably within DOJ and DHS) should plan a similarly focused preventive and responsive strategy. An interagency task force should work with industry to coordinate and make advance plans to try to interdict these most damaging forms of copyright theft, and to react swiftly with enforcement actions where necessary.” This is perhaps the most revealing of the proposals: big Hollywood studios deputizing the FBI and Department of Homeland Security to provide taxpayer-supported muscle for summer blockbuster films. Jokes have been made about SWAT team raids on stereotypical file-sharers in college dorm rooms — but this entertainment industry request to "interdict...and to react swiftly with enforcement actions" brings that joke ridiculously close to reality. What next? Of course, these comments are just an entertainment industry wishlist, an exercise in asking for the moon. But they reveal a great deal about the entertainment industry's vision of the 21st century: less privacy (with citizens actively participating in their own surveillance), a less-neutral Internet, and federal agents acting as paid muscle to protect profits of summer blockbusters. http://www.eff.org/deeplinks/2010/04...ystopia-future  An Internet for Everybody Susan Crawford LAST week, a federal appeals court in Washington ruled that the Federal Communications Commission lacks the legal authority to tell Comcast not to block certain uses of its Internet access services. This decision has become a rip-the-Band-Aid-off moment for the regulatory agency, forcing it to reconsider its effort to impose “network neutrality” by requiring that Internet access providers treat all content equally. It also puts a substantial roadblock in the path of the commission’s National Broadband Plan, which proposes to spend billions of dollars to help provide Internet access, rather than phone access, for people in rural areas. But the F.C.C. needn’t change either strategy. It can regain its authority to pursue both network neutrality and widespread access to broadband by formally relabeling Internet access services as “telecommunications services,” rather than “information services,” as they are called now. All the commission needs to do is prove it has a good reason. It wouldn’t be the first time that the F.C.C. relabeled Internet access services — and certainly not the first time it addressed the need for equal access. Until August 2005, the commission required that companies providing high-speed access to the Internet over telephone lines not discriminate among Web sites. This allowed innumerable online businesses — eBay, Google, Amazon, your local knitter — to start up without asking permission from phone and cable companies. There was nothing unusual about this legal requirement; for more than 100 years, federal regulators had treated telegraph and telephone service providers as "common carriers," obligated to serve everyone equally. But under the Bush administration the F.C.C. deregulated high-speed Internet providers, arguing that cable Internet access was different from the kind of high-speed Internet access provided by phone companies. Cable Internet access providers, the commission said, really offered an integrated bundle of services — not just Internet connection but also e-mail, Web hosting, news groups and other services. So the F.C.C. declared that high-speed Internet access would no longer be considered a “telecommunications service” but rather an “information service.” This removed all high-speed Internet access services — phone as well as cable — from regulation under the common-carrier section of the Communications Act. This was a radical move, because it reversed the long-held assumption that a nondiscriminatory communications network was essential to economic growth, civic welfare and innovation. At the same time, the F.C.C. said that it would retain the power to regulate Internet access providers if the need arose, under another section of the Communications Act. The Bush F.C.C. hoped that deregulation would prompt greater competition in Internet access services. But a wave of mergers instead reduced it. Prices stayed high and speeds slow. And eventually the carriers started saying that they wanted to be gatekeepers — creating fast lanes for some Web sites and applications and slow lanes for others. In its decision last week, the appeals court said that the “information services” label given to high-speed Internet access providers means the F.C.C. cannot prohibit companies like Comcast from engaging in discriminatory activities. But if the F.C.C.’s labeling of high-speed Internet access providers undermines its ability to tell them what to do, how can it ensure that consumers get the information they need about real speeds and prices? How can it ensure that basic communications services — which, these days, means Internet access — are widely available? The F.C.C. has the legal authority to change the label, as long as it can provide a good reason. And that reason is obvious: Americans buy an Internet access service based on its speed and price — and not on whether an e-mail address is included as part of a bundle. The commission should state its case, relabel high-speed Internet access as a “telecommunications service,” and take back the power to protect American consumers. http://www.nytimes.com/2010/04/11/op...1crawford.html  Consumer 10.0: Once-Blocked User Urges Net Neutrality Jeff Gelles Use the Internet much? If you're like most Americans, the answer is probably: more and more every day. You rely on programs and Web sites - maybe even one where you're reading this column - to work as promised. If they don't, you're likely to be momentarily frustrated, and then move on. On the Internet, there's always someplace else to go. Unless you're a geek or wonk, there's little reason to dwell on what went wrong. Here's the thing: If you want the Internet to stay as free and open and fascinating as it seems today, you may want to stop surfing for a moment. Take the time to listen to one of those geeks, Robb Topolski, a former Intel network products engineer, who was blocked by Comcast Corp. from using BitTorrent and other file-sharing sites. Comcast says what happened was pretty much no big deal - certainly nothing worth the loud slap on the wrist the Philadelphia cable giant got in 2008, when the Federal Communications Commission ruled that the company had violated "federal Internet policy" in handling Topolski's and others' Internet usage. Comcast first denied interfering with BitTorrent and similar sites. Eventually it admitted doing so, but said it was a mistake driven by legitimate concerns about network congestion. Still, Comcast went to court to clear its name and establish that the FCC had no legal basis to interfere. Comcast won its battle last week when a federal appeals court ruled that the FCC's "open Internet" principles, a weak regulatory approach taken during the Bush administration, were essentially unenforceable. But Comcast and its cable- and phone-industry brethren could still lose their larger fight for commercial control of the Internet. The key question is whether the FCC, now led by Obama appointee Julius Genachowski, and Congress if necessary, will stand behind the principle of "network neutrality": the crucial idea that network operators not be allowed to discriminate as they handle Internet data flows. What happened to Topolski offers a useful window on what's at stake, and why. Before he learned Comcast was to blame, this former Air Force senior airman actually wondered if he'd run up against the "Great Firewall of China" - geekspeak for the elaborate system the Chinese use to control access to forbidden Web sites and censor politically unwanted content. Topolski's story begins back in fall 2006, when he was on medical leave from Intel. Not used to down time, Topolski decided to experiment with peer-to-peer file sharing, a technology that's often demonized for its use in sharing copyrighted files but that also has plenty of legal applications. Topolski was interested because of peer-to-peer's potential value - including, ironically, as a tool to limit network congestion. But as a software developer concerned about piracy, he was also scrupulous in choosing what to share. He settled on a personal passion: barbershop-quartet recordings and sheet music, all in the public domain. Then he set up his computer, capping his upload speeds to limit network demand, and watched as a slow but steady stream of fellow aficionados downloaded his songs. All went smoothly until Topolski shut down his file sharing as his health worsened - he was eventually diagnosed with colon cancer. And then a bizarre thing happened: When he was feeling well enough in early 2007 to resume, his uploads all failed. He found no reason to suspect Comcast, especially after seeking help on tech-support message boards frequented by Comcast staffers. "I was told authoritatively that Comcast does not interfere with peer-to-peer uploads or interfere with connectivity in any way," Topolski, now 46, recalled Friday. "They said that Comcast could not be the source of my problem." He worked for weeks seeking an answer, and eventually traced the problem to Comcast with an ingenious technique: He set up a "virtual private network" with a friend in Brazil - a data tunnel that allowed him to run his computer via his friend's Internet connection. Outside Comcast's reach, his uploads were suddenly "going gangbusters." It was suddenly clear who was responsible. Three years later, it would be easy to draw the wrong lesson from Topolski's experience: that Comcast got caught, apologized, and said it was committed, as the company said last week, to "delivering the quality open-Internet experience consumers want." Topolski, now chief technologist for the New America Foundation, a Washington advocacy group, says his experience illustrates something else: that the cable and phone companies that control most access to the broadband Internet have the means and motive to do things many consumers would reject - if they knew about them. Topolski says clear and enforceable net-neutrality rules are crucial because of the financial incentives against neutrality - especially as Web distribution of video poses competition for the core business of cable television. Companies such as Comcast won't need to block sites, or anything so ham-handed. Instead, they can profit simply by making side deals with some sites in a category - search, travel, video - and then make those sites work consistently better than others. "You'll never understand that the real reason it's not working is that your ISP has made a deal," Topolski says. "Your choice is being manipulated without your knowledge." Call it the invisible hand of the market. Just not the one Adam Smith envisioned. http://www.philly.com/philly/busines...eutrality.html  Rockefeller Vows Congressional Support for FCC on Broadband Cecilia Kang Sen. John D. Rockefeller (D-W.Va.) said he would take up legislation to protect the authority of the Federal Communications Commission over broadband services, after a court ruling put the agency's position into flux. "In the longer term, if there is a need to rewrite the law to provide consumers and the FCC and the industry with a new framework, I as chairman will take that task on," Rockefeller, chairman of the Senate commerce committee said during a hearing on the FCC's broadband plan Wednesday afternoon. "I think that is probably where we're going to end." A federal appeals court sided last week with Comcast, which disagreed with sanctions put on it for slowing the BitTorrent application on its network. The court determined that the FCC didn't properly use its "ancillary authority" over broadband in its action against Comcast. That decision has thrown the future of the FCC into flux, with a growing debate over how the agency can proceed as a regulator of broadband service providers and create a so-called net neutrality policy that would prevent online discrimination such as that that Comcast did with BitTorrent. Lawmakers all weighed in on the question of how the FCC would respond to the court decision. Some Democrats called for the agency to more clearly mark its authority over broadband by reclassifying the service as a telecom service. Republicans disagreed. Ranking member Kay Bailey Hutchison (R-Tex.) meanwhile cautioned the FCC against considering reclassifying broadband services as a telecom service. She didn't mention in her opening remarks whether she would support a congressional mandate that would clarify the FCC's authority to regulate broadband services. "Without a directive from Congress and without a thorough analysis … the legitimacy of agency would be seriously compromised," Hutchison said. Rockefeller's comments come after Senators John Kerry (D-Mass.) and Byron Dorgan (D-ND) assurances to the FCC that it can reclassify broadband services as a common carrier service that is clearly under the agency's control. "Of course Congress has the opportunity to address this but before now and the end of the year, I don't think Congress is likely to do it," Dorgan said. "So I think we have to look at the FCC to do it because the FCC unraveled it in the first place." FCC Chairman Julius Genachowski, the sole witness at the hearing, said attorneys at the agency are still deliberating on how they would proceed after the federal appeals court decision. "I haven't made a decision yet," Genachowski said, after one lawmaker asked his opinion of what the agency should do. But he said the court decision raised questions about its ability to fulfill its objective to bring broadband services to rural areas through the $8 billion universal service fund. "It potentially raises question in a number of areas, including universal service to rual areas, public saftey and cybersecuirty," Genachowski said. "That’s why it's important to make sure eveything we do has a solid legal foudnaiton." For Rockefeller, the question of a federal agency's power to regulate broadband services is personal and the importance of broadband is personal. Rockefeller said a tragedy at a mine in his home state in recent days was aggravated by the lack of cellphone service in the area, crippling communications for family members and others at the site. And he credited Comcast for creating added complexity to the FCC's goal of fulfilling its broadband deployment goals because of its court case against the agency on a net neutrality sanction. "A lot of people sitting in this room representing industry love deregulation. … There is a history of the recent FCC of non-action when a lot of action was needed. I want to say that this is a committee, as long as I'm chairman, that is here to protect consumers," Rockefeller said. "Most of the rest of the world can take care of itself. Consumers can’t. People without cellphones can’t make phone calls to the mother of a deceased miner. That’s how I see my responsibility," he said. http://voices.washingtonpost.com/pos...feller_d-.html  FCC Chairman Seeks Broadcaster Support Marguerite Reardon Federal Communications Chairman Julius Genachowski tried to convince broadcasters to support his plans to reauction TV wireless spectrum during a speech he gave Tuesday at the industry's annual trade show sponsored by the National Association of Broadcasters in Las Vegas. Genachowski said the additional spectrum is needed to ensure that U.S. wireless operators can meet the growing demand for wireless broadband services. He said new smartphone devices, such as the Apple iPhone and the Motorola Droid, are causing a 40-fold increase in demand compared to a three-fold increase in spectrum for mobile broadband coming online. He said the problem will only get worse as other wireless connected devices, such as Apple's new iPad, are introduced into the market. "Our nation's ability to lead the world in innovation and technology is threatened by the lack of sufficient spectrum for wireless broadband applications and services," he said, according to the text of his speech. "This is not a theory or idle speculation. It's math and physics." He assured broadcasters that the auctions proposed in the National Broadband Plan, which was presented to Congress last month, are voluntary and will result in a win-win situation for broadcasters and the public. Broadcasters could benefit financially by sharing the proceeds from the auctions, and consumers would benefit from more wireless spectrum made available to enhance and create new services. The National Broadband Plan (PDF), which is a blueprint for policy makers, legislators, and the Obama administration to bring affordable broadband service to every American, calls for the FCC to make 500MHz of new wireless spectrum available within 10 years for licensed and unlicensed use. The plan recommends that 300MHz of that spectrum should become available within the next five years. And about 120MHz of spectrum will come from broadcasters. But Genachowski said it would only take a few stations in mostly urban regions to reach this goal. He said that consumers would not see any degradation in over-the-air TV service and that mobile DTV services would continue to be rolled out. He emphasized that rural broadcasters would not be affected since the real wireless bandwidth crunch is in the dense urban areas. He also said broadcasters would be able to set their own floor price on the auction. And he tried to reassure the audience that the incentives would be so appealing that the agency would not be forced to resort to plan B, which would force unwilling broadcasters to give up spectrum. The chairman tried to dispel myths about the plan that have been swirling among the industry. "A lot has been said and written about this auction proposal, including at this conference, that just isn't accurate," he said. Earlier this week, NAB President Gordon Smith likened the FCC's tactics to those of the mafia, shaking down broadcasters to accept deals they couldn't refuse. "Either your signature or your brains will be on the contract," the Los Angeles Times quoted him as saying, paraphrasing the "Godfather" mafia don, when talking about Genachowski's pitch. But Genachowski argued that broadcasters who want to contribute half their capacity and share with another broadcaster should not be denied that opportunity. He also said the FCC is not looking to drive broadcasters out of business, and he applauded broadcasters for their public service. NAB Executive Vice President Dennis Wharton said in a statement following the chairman's speech that the group was reassured by the FCC's efforts to work with the industry. "We welcome an ongoing dialogue with Chairman Genachowski," he said. "His remarks on the National Broadband Plan as related to television spectrum reclamation were reassuring, and we will reach back to work with the chairman." http://news.cnet.com/8301-30686_3-20002398-266.html  Justice Stevens Leaves Mark on Internet Law Declan McCullagh U.S. Supreme Court Justice John Paul Stevens, who announced his retirement on Friday, is arguably the most liberal member of the court. What's less open to debate is that a pair of his opinions written over a decade ago outlined the legal environment that gave rise to today's Internet. Amazon.com, Newegg.com, Overstock.com, and other major Internet retailers can trace much of their growth in the last decade to Stevens' 1992 opinion that said, unambiguously, that they cannot be required to collect sales taxes on out-of-state sales. That gave them a competitive advantage over traditional rivals like Borders and Best Buy that did charge sales taxes--while irking state tax collectors immeasurably. In Quill v. North Dakota, Stevens wrote that such "vendors are free from state-imposed duties to collect sales and use taxes." He was talking about a catalog retailer named Quill Corporation that sold about $200 million of office supplies a year, but the decision swept in future e-commerce sales as well. Stevens' opinion on behalf of a unanimous court did stress that the U.S. Congress is "free to decide whether, when, and to what extent the states may burden interstate mail-order concerns" by requiring sellers to collect taxes. That presaged a political battle on Capitol Hill, pitting governors against Internet firms, that has lasted at least nine years, with no resolution so far, and shows no sign of abating anytime soon. In a letter to President Obama on Friday, Stevens said his retirement would be effective when the next term of the court begins this fall, in order to give enough time "to have my successor appointed and confirmed well in advance of the commencement of the court's next term." Sen. Arlen Specter, the Pennsylvania Democrat, told Fox News on Sunday that if Stevens retires this year, "I think the gridlock in the Senate might well produce a filibuster which would tie up the Senate about a Supreme Court nominee. I think if a year passes, there's a much better chance we could come to a consensus." Because the court's majority favors executive power, "I think we need the kind of balance that Justice Stevens has provided to offset the majority." The other Stevens opinion to have a far-reaching impact came in 1997, after Congress enacted a law called the Communications Decency Act, which made it a federal crime to post anything "indecent" on a public Web site where a minor might be able to read it. "The interest in encouraging freedom of expression in a democratic society outweighs any theoretical but unproven benefit of censorship." --Supreme Court Justice John Paul Stevens If upheld, the CDA would have levied broadcast-style regulations on the Internet, making it a felony for even a news organization to post certain four-letter expletives of the sort that landed the late comedian George Carlin in trouble with the Federal Communications Commission. The Internet would have been left heavily censored, while DVDs, magazines, newspapers, and satellite radio, and TV were not. And online porn? That would have been completely verboten--unless every single salacious image or video stayed behind a pay wall requiring credit card verification for proof of age. (If the CDA had remained in effect, the Internet porn industry may have moved offshore instead of being headquartered in California's San Fernando Valley.) "The record demonstrates that the growth of the Internet has been and continues to be phenomenal," Stevens wrote for the majority. "As a matter of constitutional tradition, in the absence of evidence to the contrary, we presume that governmental regulation of the content of speech is more likely to interfere with the free exchange of ideas than to encourage it. The interest in encouraging freedom of expression in a democratic society outweighs any theoretical but unproven benefit of censorship." In a 2002 case dealing with Congress' second attempt to restrict sexually explicit material, Stevens was more willing than his colleagues to find problems with the law. Stevens said he was happy to ban certain kinds of "hard-core pornography" and perhaps restrict teaser images on the Web "that serve no function except to invite viewers to examine hardcore materials." But, he wrote in a dissent, the federal law unreasonably sweeps in "a wide range of prurient appeals in advertisements, online magazines, Web-based bulletin boards and chat rooms, stock photo galleries, Web diaries, and a variety of illustrations encompassing a vast number of messages." Stevens' record on high-tech issues didn't always jibe with, say, the ACLU's position. In a 2001 dissent, he said police could constitutionally use thermal imagers to peek inside Americans' homes without obtaining a warrant first. (Justice Antonin Scalia's majority opinion declared such a practice to be unconstitutional.) http://news.cnet.com/8301-13578_3-20002145-38.html  Could Federal Ruling on Comcast Open the Door for ISP's to Become Content Providers Edward Carter Last week the federal appeals court ruled against the Federal Communications Commission (FCC) on stopping Comcast from throttling the downloads on file sharing websites. The appellate court's ruling basically states that the FCC has no legal authority to mandate to Comcast because Internet access is defined as an information service and not a telecommunications, over which the FCC has legal authority. The FCC had previously order Comcast to stop it throttling practices, which Comcast stated was needed to ensure that users downloading files from file sharing or peer-to-peer networks were not hogging too much bandwidth and slowing down Internet access for its other customers. This ruling, like an octopus, has many many different tentacles that reach down many different avenues such as net neutrality, national broadband plan, and how the FCC classifies the Internet . However it seems that if Comcast or any high-speed ISP (Internet service provider) can restrict or influence how a user interacts with a website, like slowing down file sharing, than certain organizations might be willing to a pay a premium for ensuring their service are not restricted or at least unencumbered. In essence, these ISP's are now content drivers. They are essentially driving traffic to certain websites; those that pay to allow their users premium access, versus those that don't and are being throttle or just given normal access. http://www.examiner.com/x-31174-Alle...tent-providers  JDownloader Turbocharges File Sharing Sites JDownloader Turbocharges File Sharing SitesJDownloader Turbocharges File Sharing SitesWindows/Mac/Linux: If you're a frequent visitor to popular file sharing sites like Rapidshare you'll want to grab a copy of JDownloader, a java-based tool that completely automates the downloading process. JDownloader takes all the most irritating things about downloading from popular sharing sites like Rapidshare and Megaupload and either outright negates them or makes them more tolerable. Feed links, even links to multi-part downloads into JDownloader and it will automate the process, circumvent captcha, tweak wait times, auto-reconnect, and even run on a schedule. JDownloader works as a stand-alone application or with Firefox through integration with the popular Flashgot extension. JDownloader is free, java-based, and available for Windows, Mac, and Linux. http://lifehacker.com/5513415/jdownl...-sharing-sites  More than 50 Million BitTorrent Users a Day Robert Briel New York based Jumpwire Media has announced the launch of its content monitoring system, called Torrent Tracker Reports. “Downloading content from the internet is a mass-market reality,” the company claims and “Torrent Tracker Reports reveals what content is most popular online; acting as a market signal for all types of media.” Jumpwire Media’s Deep Torrent Tracker software provides its television clients the opportunity to use this data to better understand their global audiences and monetise their content. Torrent Tracker Reports has been accumulating television user trend data for every TV show in the world since June 2008. “Most television distribution companies see piracy as a loss instead of a gain, but we feel that piracy is a market signal that shows us where the demand is and where the opportunities are. There are more than 50 million users on BitTorrent each day and consumers are becoming their own programmers finding the content they want to watch, when they want to watch it. This trend is rapidly changing the TV environment and challenging how traditional broadcasters and advertisers go about capturing a greater market share,” said Gavin McGarry, president of Jumpwire Media, in a statement. “By identifying key user trends including geographical locators we can signal potential new markets for programming and empower media and entertainment companies to meet the needs of their audiences.” http://www.broadbandtvnews.com/2010/...t-users-a-day/  Chris Atkins: 'Sometimes I Want to Punch People Who Make Technology' The Starsuckers filmmaker often finds himself frustrated by obsolescence What's your favourite piece of technology, and how has it improved your life? Without question, my favourite piece of technology is my Nokia n900 phone. It is super amazing and pisses all over the iPhone. The ingenious bit about it is that it's open source, so you can program it to do whatever you want. I used to do some work with Linux when I ran a post-production house, so we've worked out how to make it do all sorts of funky things. Some boffins who we do some work with have connected it up to a Rollodex, so as you spin through your contacts, a motor spins through the rollodex. And they canibalised an old Speak & Spell, so you can send texts that sound like ET. It's the best thing ever. Buy it from amazon.co.uk 1. Buy the DVD 2. When was the last time you used it, and what for? I use the phone 24/7 – my friends joke about me growing a phone-shaped cancer on the side of my head. What additional features would you add if you could? I would want it to talk to my Mac better, but I don't think that's going to happen. Do you think it will be obsolete in 10 years' time? Of course – everything is. However, the Speak & Spell and Rollodex were supposed to be obsolete but now they are coming back, so never say never! What always frustrates you about technology in general? I think people make new devices in such a way as to make them obsolete very quickly. Sometimes I want to punch people who make technology. Is there any particular piece of technology that you have owned and hated? The motor car, of course, because I was a danger to myself and others when I drove – I was crashing all the time. And the car itself is just fucking up the planet. If you had one tip about getting the best out of new technology, what would it be? To never, ever, ever buy the first of anything that comes along – always wait. Do you consider yourself to be a luddite or a nerd? I'm an utter nerd. I try to pretend that I'm a cool, funky director of documentaries, but I'm a complete and utter geek. What's the most expensive piece of technology you've ever owned? I used to run a post-production company for a few years and the most expensive thing in that was an HDD5 deck, which cost us £80,000. It's now an obsolete format, and I sold it two-and-a-half years later for just £16,000. Mac or PC, and why? Macs, for video editing – I edit all my films using Final Cut Pro, and Avid is the most pointlessly shit platform ever invented. Do you still buy physical media such as CDs and DVDs, or do you download? I download illegally quite a lot and I encourage people to do the same to my own films. Basically, the studio system is just there to rinse money out of the public and the filmmakers. Why give another dollar to Steve Jobs? That 99c isn't going to the artist, it's going to Sony, or Warners, or whoever. Robot butlers – a good idea or not? I filmed an event last month with robot pole dancers. I tried to take one home with me, but she wouldn't have a bar of me. So yes, I think replace humans with robots wherever possible. What piece of technology would you most like to own? It's just got to be hover boots – we were promised back in the 80s that we'd have them by now. But where are they? http://www.guardian.co.uk/technology...ns-starsuckers  Trying to Live Long and Prosper How about a hard drive loaded with movies? AP Paramount Pictures is exploring a new frontier by participating in an offer to sell Seagate Technology hard drives with a copy of the latest "Star Trek" movie and 20 other films already on board. The one-month offer, which both companies on Monday called an industry first, would combine a 500-gigabyte hard drive with a free version of 2009's "Star Trek" for an online promotional price of $100. An empty 500 GB Seagate hard drive usually sells for $140. The other movies distributed by Paramount, including "GI Joe," ''Nacho Libre" and "Jimmy Neutron: Boy Genius" come pre-loaded with a digital lock that requires a code that can be purchased online for $10 to $15 each. Even watching "Star Trek" requires registration. The pre-loaded movies come with a Windows-based digital rights management system that prevents file sharing. They take up about 50 GB of the drive itself. The special sale comes as Hollywood is struggling with falling DVD sales in the face of piracy and is looking for new ways to sell movies from its library. Other companies such as Wal-Mart Stores Inc. have used heavy discounts on DVDs as a way to lure shoppers. Both companies declined to say if they were taking a loss on the promotional price. Both could be using the offer as a way to lure buyers for other related products they're selling. Paramount, a unit of Viacom Inc., is selling its other movie titles, while Seagate Technology is selling a device that enables movies stored on hard drives to be played on television sets for $130. http://skunkpost.com/news.sp?newsId=2118  Does Anybody Own Fellini's "La Dolce Vita"? Eriq Gardner A New York District Court judge has dismissed a lawsuit against the creator of a two-part pornographic remake of Frederico Fellini's classic film, "La Dolce Vita." In the process he's raised questions about whether anybody controls the legendary original. In 2007, International Media Films sued Lucas Entertainment over "Michael Lucas' La Dolce Vita," an adult remake that garnered 14 awards at the gay porn industry's equivalent of the Oscars (honors included best picture, best actor and best threesome). IMF alleged copyright and trademark infringement. Fellini's classic is famous for popularizing the orgy, so it would have been interesting to see a court examine the derivative nature of a porn film. Alas, the case took an unexpected direction that's just as steamy. Both parties disputed the chain of title on Fellini's "La Dolce Vita." According to IMF, the original producers of the film assigned the rights in 1962 to Cinemat, S.A., which transferred rights in 1980 to Hor A.G., which transferred rights the following year to Oriental Films, which transferred rights in 1998 to Cinestampa, which then transferred rights in 2001 to IMF. A year later, IMF filed a registration with the US Copyright Office on a restoration copy of the Fellini film. The defendant argued for an alternative chain of custody that resulted in the picture being controlled by Paramount Pictures. Questions were also raised about the authenticity of the Cinemat-Hor, Hor-Oriental, and Oriental-Cinestampa agreements, pointing to inaccuracies in dates and signatures. Experts on Italian copyright law were meticulous in examining the details. Interestingly, the film was briefly in the public domain in the mid-1990s and may still be there today. IMF claims it was restored to copyright protection thanks to legislation enacted as part of an international treaty, but the court is dubious. "In fact, it is possible for the Fellini film to be in the public domain," writes Judge John Koeltl in his opinion, issued March 31. "It is the plaintiff who bears the burden of proving that its chain of title is valid." Judge Koeltl says IMF has failed to show sufficient admissible evidence that it is in fact the copyright owner of the Fellini film. Naturally, the question becomes whether anybody can show indisputable evidence now. http://www.reuters.com/article/idUSTRE63D0LX20100414  Sharp to Join 3D TV Battle with Advanced Display Kiyoshi Takenaka Japan's Sharp Corp said it would begin selling 3D-capable LCD TVs in Japan this summer, the latest consumer electronics maker to enter the market for what is expected to be the industry's next growth driver. The maker of Aquos brand flat TVs plans to launch 3D TVs in China, Europe and the United States by December, joining larger rivals such as Samsung Electronics Co Ltd and Sony Corp. Sharp's new products will be the world's first 3D TVs using four-primary-color technology, which utilizes yellow on top of the three conventional primary colors of red, green and blue, enabling the TV sets to offer brighter, more vivid images. "We are now one step closer to such things as 3D displays with the world's best quality or the ultimate display," Sharp Executive Vice President Masafumi Matsumoto told a news conference on Monday. Consumer electronics makers are scrambling to launch 3D TVs this year, betting the technology will be as big a boost for the industry as the transition to color TVs from black and white. Panasonic Corp and Samsung have already released 3D models, while Sony plans to start offering 3D TVs in June. Electronics makers have high hopes that growing interest in 3D movies sparked by the sci-fi blockbuster "Avatar" will drive 3D TV sales. Demand for 3D TVs will likely grow more than 10-fold to 27 million units in 2013 from an estimated 2.5 million units this year, according to research firm DisplaySearch. Sharp said high response speeds of its 3D TV use LCD panels help eliminate double-contour ghost images known as "crosstalk", which often occur with 3D images. "Crosstalk ruins 3D pictures. We have managed to lower this phenomenon to extremely low levels," Matsumoto said. Sharp plans to start making advanced 3D displays for cellphones and other mobile devices this year that do not require special glasses, betting that demand for 3D images will grow beyond movie theatres and living rooms to portable machines. Viewers, however, need to wear special glasses to watch Sharp's new 3D LCD TVs. Sharp expects 3D TVs to account for 5-10 percent of its total LCD TV sales in the business year ending in March 2011, he said. Matsumoto did not disclose how many LCD TVs Sharp aims to sell this financial year, but he said the company had achieved its LCD TV sales target of 10 million units for the year that ended on March 31, and plans to boost LCD TV output substantially this year. Sharp is considering bringing its flagship LCD panel plant in western Japan to full capacity earlier than originally planned October, Matsumoto said. Separately, rival Panasonic announced on Monday that it has started operating a new LCD plant in Japan three months ahead of schedule to capitalize on a recovery in the global flat TV market. The western Japan factory has an initial a monthly output capacity equivalent of 405,000 32-inch displays, which will be doubled by March next year. Following the announcements, shares of Sharp closed down 1.3 percent at 1,188 yen and Panasonic ended down 0.7 percent at 1,413 yen, underperforming the Tokyo stock market's electrical machinery index, which edged up 0.1 percent. (Additional reporting by Nobuhiro Kubo and Taiga Uranaka; Editing by Michael Watson) http://www.reuters.com/article/idUSTRE63B1MB20100412  Google CEO Says Apple Helped AdMob Deal Apple's plunge into the advertising market announced this past week gave Google a big boost in arguing for regulators to approve its acquisition of mobile advertising leader AdMob, Google CEO Eric Schmidt said on Sunday. U.S. antitrust enforcers are apparently concerned the AdMob purchase could hurt applications developers, who often sell their apps for very little and make their money by selling advertising space on them. But Schmidt, speaking after a speech at the American Society of News Editors, said Apple's plan to make a foray into the advertising market with iAd, was "evidence of a highly competitive market." "It just seems obvious to me," said Schmidt. "I hope it (Google's purchase of AdMob) gets approved." Apple's new advertising platform for the iPhone and iPad -- dubbed iAd -- marks Apple's first move into a small but growing market. With iAd, applications developers will pocket 60 percent of the revenue. Apple will sell and host the ads. Apple's entry into the mobile ad arena had been widely expected. It paid $270 million for Quattro Wireless, an advertising network that spans both mobile websites and smartphone applications. Google, the online search leader, announced a $750 million deal in November to buy AdMob, which controls about one-third of the market for putting ads on mobile applications and web pages. FTC staff have been canvassing app developers to try to line up support to fight the deal, said one developer, who asked to remain unidentified because he had been interviewed by FTC attorneys. "It's been really interesting talking to them because they are so dead set against this," said the developer. "They have been clearly positioning to try to stop this." Google, which generated 97 percent of its $23.7 billion in 2009 revenue from advertising, has faced growing antitrust scrutiny. The company walked away from a search deal with Yahoo in 2008 when the Justice Department said it would challenge the tie-up. And Schmidt was forced to step down from Apple's board last year after his dual roles came under FTC review. The U.S. Department of Justice has been sharply critical of Google's settlement with book publishers and authors' groups that would allow the search giant to create an online digital library. (Reporting by Diane Bartz; Editing by Valerie Lee) http://www.reuters.com/article/idUSTRE63B0F820100412  News Execs Pessimistic, but Don't Want Handouts AP Although news executives know their industry is in trouble, most are unwilling to turn to the government or interest groups for help. Three quarters of editors and news directors polled say they have ''serious reservations'' about government funding of journalism, and 78 percent say the same thing about interest groups, primarily for fear that independence can be compromised, according to a study by the Pew Research Center's Project for Excellence in Journalism. Pew surveyed members of the American Society of News Editors and Radio Television Digital News Association and found that less than half of them believed their organizations would be solvent in 10 years without the discovery of a significant new revenue stream. ''One thing they say is that we've got to figure this out for ourselves,'' said Tom Rosenstiel, Pew's director. ''We can't wait for Big Brother to help us.'' Fifteen percent of the news executives said they believed setting up ''pay walls' so much of their content can no longer be viewed for free would be bringing in significant revenue over the next three years. There was even less confidence in the idea of surcharges placed on monthly Internet bills as a way of raising money. Nearly two-thirds of the executives say that the Internet is changing journalism by loosening standards. By a nearly 2-to-1 ratio, broadcast executives are pessimistic about their industry's future. It's about an even split among newspaper editors. Rosenstiel suggested the disparity may be because newspaper executives have been dealing with the financial problems for a longer time than the broadcasters, and many are being creative in trying to fight back. Pew's nonrandom survey, taken in December and January, had 353 participants. ''The feeling isn't defeatist,'' he said. ''The feeling is the defeatist ones have left. Those of us who remain are going to fight.'' http://www.nytimes.com/aponline/2010...ws-Survey.html  Google CEO's Advice for ASNE Jake Sherman The chief executive of Google has a message for the staggering newspaper industry: Things will get better. And Google CEO Eric Schmidt told a group of newspaper executives Sunday evening that his growing company will be an integral part of those changes. Newspapers will make money once again, he said, but it will be from online advertisements and an altered subscription model. Schmidt said his firm is working on new ways to tailor advertisements and content for consumers, based on what stories they read. "We have a business model problem, we don’t have a news problem," Schmidt said. Speaking to the American Society of News Editors’ annual convention at the J.W. Marriott in downtown Washington, Schmidt showered praise on the industry, calling journalism an “art.” Schmidt said he reads three newspapers, and called their work indispensible. And he blasted blogs, saying that any questions about the value of newspaper editors can be answered: "Look at the blog world." "High quality journalism will triumph," he said. But along with that praise came his advice about how the business should change: Organizations should refocus their attention on personalizing content and disseminating news through mobile devices – businesses in which Google is heavily involved. Schmidt told the mostly full ballroom that “new forms of making money will develop,” and that Google is working on those forms. But he declined to divulge many details about that work. “The web can ultimately be very good for news,” Schmidt said. “Think about it: You have more readers than ever, you have more sources than ever, for sure you have more ways to report and new forms of money. New forms of making money will develop.” Schmidt, who hovered at the side of the lectern throughout his 25-minute speech, was firm that there is a robust future for both display advertisements and subscriptions — revenue streams that have shrunk as dramatically as the volume of free content online has expanded. Google, of course, has a stake in that free content. It aggregates news through its search engine, directs users to sites with free content and has made the universe of free information much more accessible, even as the company has profited by displaying its own advertisements beside that information. Much of Schmidt’s advice seemed to point to changes that might emerge from forms of technology that Google is developing, has developed or could foreseeably develop. Some of those advances in technology, he said, could create new revenue streams for news organizations. News sites should use technology to predict what a user wants to read by what they have already read, he said – technology his company has. Schmidt said he doesn’t want “to be treated as a stranger” when reading news online. He also said he wants to be challenged through technology that directs readers to a story with an opposing view. Google, he said, can uncover why a news organization doesn't have readers in specific areas. Personalized technology for news could help in tailoring advertisements for individual readers. The collaborative nature of the Internet – something that Schmidt thinks could save journalism – also has its downside, he said. The barriers for entry are “basically zero,” which makes everyone at once a potential competitor and partner. “Figuring out when to compete, when to collaborate, when to go solo, when to work in a group strikes me as one of the sort of key questions for all of you to think about,” Schmidt said. “I don’t know the answer, by the way, but I know you’ll have a combination answer to make it right.” One way newspapers can become commercially successful, he said, is to emulate Google: “Prototype early and often,” gather and analyze data and make decisions based off of hard data. Boston Globe Editor Martin Baron told POLITICO after Schmidt's speech that Google is "already a big part of our presence": "The reality is all newspaper Web sites get a lot of traffic with Google." Baron, whose newspaper has been hit particularly hard in recent years, said Google is having a "dramatic impact" on the news industry, which he said needs to "adapt quickly" to the fast-changing media environment. "What we need to do is probably sweat, but sweat from hard work, figuring it all out," Baron said. "I think that’s why people are here, and that’s why they invite somebody like Eric Schmidt. If we can learn something, and apply those lessons to the way we do business, then all the better." Staci D. Kramer, the co-editor of ContentNext Media, which covers the economy of news online, said that Schmidt's talk was "non-adversarial" to an industry that views his company with skepticism. "What he said was 'you’re right to worry, but don’t write your own epitaph yet,''" she told POLITICO. "He’s not saying you’re wrong to worry, but don’t worry about the wrong things. It’s all about the business model, it’s not whether you’re a valued or not-valued service, it’s how do you get people to pay for that service. Do you pay through advertising, subscriptions or a mix? That's something we're all working on." It’s an equation that’s not easily solved, Schmidt said. "The fact of the matter is there are not simple answers to any of these questions. And in order to really find them, you’re going to have to run some experiments." http://www.politico.com/news/stories/0410/35649.html  Why Newspapers Shouldn't Be Scared of Huffington Post Shauna Miller Two years ago, board membership to the American Society of News Editors wasn't even open to online publications. Last year, their annual conference was scrapped entirely as newsroom belts tightened. But this year, veteran newspaper editors from around the country packed a hotel ballroom in Washington, D.C. to hear from online publishers why they shouldn't fear the reaper. They came to hear panels on publishing for e-readers, considering government subsidies, and keeping afloat with a skeleton-crew staff in the 24/7 news cycle. They even (for the most part) politely listened Tuesday to Arianna Huffington talk up her mammoth site's aggregation-based model—something still seen as a major threat by traditional papers. But Huffington's lede appealed to the roomful of reporters in varying stages of employment: Stories are still what readers want. They may come for entertainment gossip, but they stay for news that they didn't otherwise know to look for. Aggregation allows a publication to centralize more information and present the bigger picture, she said, and that allows for context no traditional publication can match. She pointed to the Huffington Post's coverage of the West Virginia mine collapse—which an editor from the Morgantown, West Va., Dominion Post noted was done without HuffPo reporters on the ground. But Huffington warned the editor not to hate the players in this new game. Linking to small papers gives them major traffic, she said. It's then their responsibility to "monetize" the opportunity. The Huffington Post's citizen journalism initiative tells a similar new-media tale. The project has produced some great, personal stories on how the recession is hitting people all over the country. But it takes advantage of free content by "citizen bloggers"—an industry trend laid-off local reporters may find increasingly exasperating. "We would have needed hundreds of reporters all over the country to get those stories," Huffington said. She said this type of reporting is really a new form of reader entertainment and media engagement. "People ask, why would someone tweet or write for no money," she said. "But no one's asking why they are watching seven hours of bad T.V. a day for no money." Whether you call the HuffPo's model threatening, opportunist or groundbreaking, it's certainly working—at least from the point of view of struggling newspapers. New York Times columnist David Carr said HuffPo has "the tools of the insurgency" into the new media landscape, and media institutions like the New York Times are trying to keep up. "Arianna is marching toward us, we are marching toward her. But we are at a disadvantage because we don't have a source of free content," Carr said. But even if newspaper publishers feel lost in the online wilderness, they had better learn some survival tactics quickly, said James M. Brady, Digital Editorial Consultant for Allbritton Communications, which owns Politico and will soon be launching a new D.C.-based local-news site. In terms of keeping a news outlet solvent and relevant, Brady said, those tactics might not include the much moaned-about content paywall. Brady said paywalls could be "more on the side of folly than fix," successful in the short term while stunting the growth of more radical approaches to finding support streams for content. Instead, he said, publishers of all forms of media should be looking at what reader will pay for, not what they should. The answer there is mobile content, says Brady. People will pay to access things through apps when they are disconnected from their laptops, according to Brady, capturing an audience far beyond the half-hour at breakfast that a newspaper can keep their attention. This is where development energy and dollars should be spent. A later panel debated whether some of those dollars could come from government subsidies—but don't call it a "bailout." Frank A. Blethen, publisher of The Seattle Times, argued that government support would take control of the media out of the hands of "the elite"—large corporate owners that exert control over content. "Bankers are poised to become the major owners of our newspapers and broadcast," he said. We are seeing...a chill over whether you're going to write stories your employer is not going to like." But the question of how far the government's arm would reach into journalism is, of course, troublesome. Susan S. DeSanti, director of the Federal Trade Commission's policy planning office, said that an outright "bailout" for newspapers was unlikely, but that government funding could remove expensive barriers to accessing information for journalists. "We certainly don't want to bail out the current owners," she said. "But how can we lower the cost of journalism?" John Nichols, a correspondent for The Nation, poked fun at the idea that any government involvement would reduce journalism to a state-run propaganda machine. "Why don't we make comparisons to really scary places...like Norway, or Holland?" he joked, noting that those heavily subsided countries continue to have a healthy and competitive newspaper and broadcasting industry. He said a government-supported "Write for America" program similar to Teach for America could be one way to give young journalists opportunities while covering issues in poorer parts of the country that often go unreported. Blethen, a fourth-generation member of the family that founded The Seattle Times in 1896, said the concept of the newspaper itself isn't what's broken, the ownership model is. On that, anyone working in—or laid off from—the media industry might agree. The backbone of the newspaper industry has always been relevant, local content that readers trust. Blethen and Brady might be disagree on what shape that will take in three years or five, but whatever is left standing will be the model that works. http://www.theatlantic.com/culture/a...on-post/38883/  News Sites Rethink Anonymous Online Comments Richard Pérez-Peña From the start, Internet users have taken for granted that the territory was both a free-for-all and a digital disguise, allowing them to revel in their power to address the world while keeping their identities concealed. A New Yorker cartoon from 1993, during the Web’s infancy, with one mutt saying to another, “On the Internet, nobody knows you’re a dog,” became an emblem of that freedom. For years, it was the magazine’s most reproduced cartoon. When news sites, after years of hanging back, embraced the idea of allowing readers to post comments, the near-universal assumption was that anyone could weigh in and remain anonymous. But now, that idea is under attack from several directions, and journalists, more than ever, are questioning whether anonymity should be a given on news sites. The Washington Post plans to revise its comments policy over the next several months, and one of the ideas under consideration is to give greater prominence to commenters using real names. The New York Times, The Post and many other papers have moved in stages toward requiring that people register before posting comments, providing some information about themselves that is not shown onscreen. The Huffington Post soon will announce changes, including ranking commenters based in part on how well other readers know and trust their writing. “Anonymity is just the way things are done. It’s an accepted part of the Internet, but there’s no question that people hide behind anonymity to make vile or controversial comments,” said Arianna Huffington, a founder of The Huffington Post. “I feel that this is almost like an education process. As the rules of the road are changing and the Internet is growing up, the trend is away from anonymity.” The Plain Dealer of Cleveland recently discovered that anonymous comments on its site, disparaging a local lawyer, were made using the e-mail address of a judge who was presiding over some of that lawyer’s cases. That kind of proxy has been documented before; what was more unusual was that The Plain Dealer exposed the connection in an article. The judge, Shirley Strickland Saffold, denied sending the messages — her daughter took responsibility for some of them. And last week, the judge sued The Plain Dealer, claiming it had violated her privacy. The paper acknowledged that it had broken with the tradition of allowing commenters to hide behind screen names, but it served notice that anonymity was a habit, not a guarantee. Susan Goldberg, The Plain Dealer’s editor, declined to comment for this article. But in an interview she gave to her own newspaper, she said that perhaps the paper should not have investigated the identity of the person who posted the comments, “but once we did, I don’t know how you can pretend you don’t know that information.” Some prominent journalists weighed in on the episode, calling it evidence that news sites should do away with anonymous comments. Leonard Pitts Jr., a Miami Herald columnist, wrote recently that anonymity has made comment streams “havens for a level of crudity, bigotry, meanness and plain nastiness that shocks the tattered remnants of our propriety.” No one doubts that there is a legitimate value in letting people express opinions that may get them in trouble at work, or may even offend their neighbors, without having to give their names, said William Grueskin, dean of academic affairs at Columbia’s journalism school. “But a lot of comment boards turn into the equivalent of a barroom brawl, with most of the participants having blood-alcohol levels of 0.10 or higher,” he said. “People who might have something useful to say are less willing to participate in boards where the tomatoes are being thrown.” He said news organizations were willing to reconsider anonymity in part because comment pages brought in little revenue; advertisers generally do not like to buy space next to opinions, especially incendiary ones. The debate over anonymity is entwined with the question of giving more weight to comments from some readers than others, based in part on how highly other readers regard them. Some sites already use a version of this approach; Wikipedia users can earn increasing editing rights by gaining the trust of other editors, and when reviews are posted on Amazon.com, those displayed most prominently are those that readers have voted “most helpful” — and they are often written under real names. Hal Straus, interactivity editor of The Washington Post, said, “We want to be able to establish user tiers, and display variations based on those tiers.” The system is still being planned, but he says it is likely that readers will be asked to rate comments, and that people’s comments will be ranked in part based on the trust those users have earned from other readers — an approach much like the one The Huffington Post is set to adopt. Another criterion could be whether they use their real names. But experience has shown that when users help rank things online, sites may have to guard against a concerted campaign by a small group of people voting one way and skewing the results. A popular feature on The Wall Street Journal’s site lets readers decide whether they want to see only those comments posted by subscribers, on the theory that the most dedicated readers might make for a more serious conversation. Few news organizations, including The Times, have someone review every comment before it goes online, to weed out personal attacks and bigoted comments. Some sites and prominent bloggers, like Andrew Sullivan, simply do not allow comments. Some news sites review comments after they are posted, but most say they do not have the resources to do routine policing. Many sites allow readers to flag objectionable comments for removal, and make some effort to block comments from people who have repeatedly violated the site’s standards. If commenters were asked to provide their real names for display online, some would no doubt give false identities, and verifying them would be too labor-intensive to be realistic. But news executives say that merely making the demand for a name and an e-mail address would weed out much of the most offensive commentary. Several industry executives cited a more fundamental force working in favor of identifying commenters. Through blogging and social networking sites like Facebook and Twitter, millions of people have grown accustomed to posting their opinions — to say nothing of personal details — with their names attached, for all to see. Adapting the Facebook model, some news sites allow readers to post a picture along with a comment, another step away from anonymity. “There is a younger generation that doesn’t feel the same need for privacy,” Ms. Huffington said. “Many people, when you give them other choices, they choose not to be anonymous.” http://www.nytimes.com/2010/04/12/te...2comments.html  Court to Decide Web Posters' Ability to Remain Anonymous Don Butler In a case with implications for online privacy and free expression, a panel of Ottawa judges is considering whether websites named in libel actions should be required to identify people who post anonymous defamatory comments. Their decision could chill whistleblowers and others who use pseudonyms to post controversial comments, say civil libertarians. And, they maintain, if the judges support unmasking anonymous posters, that could erode their privacy by allowing others to piece together vast amounts of personal information. The case arises from a 2007 defamation suit filed by Ottawa lawyer Richard Warman, who is reviled by the far right for his efforts to use human rights law to shut down hatred on the Internet. Warman's suit names Mark Fournier and Connie Wilkins-Fournier, a Kingston, Ont.-area couple who operate a conservative website, freedominion.com, and eight "John Does" who posted anonymous comments about Warman to the site. It accuses them of making 62 posts that falsely disparage Warman's personal and professional reputation. In a ruling last year, Judge Stanley Kershman of the Ontario Superior Court ordered the Fourniers to disclose the e-mail and IP addresses of the eight John Doe posters to Warman. Under the rules of civil procedure, the judge said, defendants in lawsuits are obliged to disclose all relevant documents in their possession. The Fourniers appealed, arguing people who post to message boards do so with the expectation of anonymity. Three Divisional Court judges in Ottawa heard the appeal last week but reserved their decision. The appeal drew interventions in support from the Canadian Civil Liberties Association and the University of Ottawa's Canadian Internet Policy and Public Interest Clinic. Both argue the courts should order disclosure only after the party seeking it has demonstrated a prima facie (or self-evident) case, and when the public interest favouring disclosure outweighs concern for freedom of expression and privacy. "We think the judge here made a mistake because he did not apply the right test, did not look at the impact on freedom of expression," said Nathalie Des Rosiers, the CCLA's general counsel. In its factum, the CCLA argues anonymous expression on the Internet "fosters a veritable 'marketplace of ideas' online. "Anonymity reduces the possibility of identification and fear of reprisal and encourages individuals to engage in legitimate, even unpopular, expression," the civil liberties group says. "It permits participation in public debate by those who would otherwise remain silent out of fear of persecution, loss of status or ostracism." Under current procedural rules, anyone who sues a website has an almost automatic right to information that can identify people who posted defamatory comments anonymously, said Des Rosiers. "It's very easy to sue people and present a case that would meet a very minimal threshold," observed Tamir Israel, who argued the case for the CIPPIC. That could prompt spurious claims designed to uncover the identity of whistleblowers and others who post anonymously, Israel said. Unmasking anonymous posters could put people's security at risk, said Des Rosiers, or make it easier for employers to fire employees they consider "troublemakers." And it could connect previously anonymous individuals to other postings they have made on the Internet, added Israel. "We think the privacy concerns are very high, especially since so much information is stored online these days." If the Divisional Court upholds the Fourniers' appeal, it will be more difficult for people to protect themselves against online defamation, said James Katz, Warman's lawyer. "Instead of having an automatic disclosure, you'd have to meet some sort of initial burden that you wouldn't have had to do before." But if the court requires litigants to show a prima facie case before disclosure, Katz said, "I don't think we'll have much trouble meeting that new test. "You can't go around calling someone a neo-Nazi Stalinist brownshirt. That's prima facie defamation." Four of the eight John Does have since been identified through "Internet sleuthing" by Warman and others, Katz said. The four have been added to the lawsuit and plan to defend themselves. Connie Wilkins-Fournier said it has never been her position that people "should be able to hide behind anonymity and break the law." If Warman can show that the anonymous posters defamed him, "then of course, we're going to turn over the information." Absent that, she and her husband felt they had a duty to protect the identities of the John Does. "The way it stands, all you have to do to find out somebody's identity online is to sue the person that runs the website. http://www.canada.com/Court+decide+p...088/story.html  International Man of Mystery Bernard Lagan The founder of WikiLeaks lives a secret life in the shadow of those who blow the whistle, writes Bernard Lagan. On the Al Jazeera television network, an overbearing host was grilling Julian Assange, one of the founders of WikiLeaks, the online drop zone for whistleblowers. Assange, an Australian who rarely makes public appearances and shuffles around the world with little more than a rucksack and a laptop, quickly dealt with his haughty inquisitor. Lean and tall with a handsome, distant face, long grey locks and dressed in a a dark suit, Assange, in his late 30s, is a commanding presence. He has a deep broadcaster's voice and gave measured, drum-tight answers about the blow he had just dealt the US military with WikiLeak's release of footage of an American helicopter gunship killing Iraqi citizens and two Reuters journalists on a Baghdad street in July 2007. The video, shot from the helicopter, includes the voices of soldiers urging a gravely wounded Reuters photographer to pick up his weapon (they apparently did not realise it was a camera) so he could be lawfully finished off with the aircraft's deadly 30mm cannon. When a beaten-up van slithers to a halt and its passer-by occupants tumble out to aid the wounded, they too are gunned down. Only two maimed children survive. It becomes clear why the military has resisted the demands of Reuters and others for the release of the video; the military had long claimed it did not know how the Reuters journalists had died and it initially withheld the fact that children were present. Assange resisted Al Jazeera's invitation to savage US authorities for their years of dissembling, remarking simply: ''There was certainly spinning the message and it does seem like there has been a cover-up.'' He didn't need to say more; by week's end the video had been viewed 4.8 million times. Its impact upon the reputation of US servicemen in Iraq is devastating. Another US military video - showing last year's bombing of Afghan villages as they siphoned fuel from a tanker hijacked by the Taliban - is also coming to WikiLeaks. Clearly someone inside the military has begun leaking, elevating WikiLeaks and Assange overnight from mainstream journalism's fringes to a must-see news breaker. ''This is a whole new world of how stories get out,'' declared Sree Screenivasan, a professor of digital media at the Columbia University journalism school in New York. Yet for all its ideals in support of openness and freedom of information, those behind WikiLeaks - especially its key founder, Assange - dwell in shadows and intrigue. They have no headquarters, no offices and the barest of a formal structure. Assange is particularly elusive, part obviously through necessity and part mercurial make-up. Home - or the nearest he has to one - is said to have been eastern Africa for the past two years or so. He has rarely spoken of his upbringing in Australia or life outside of his work, arguing that to do so may assist those who want him and WikiLeaks silenced. But the trail of his life is across the internet, as coded and mysterious as the man he is today. It begins - publicly at least - in October 1991 when Assange, then a teenager, was charged with 30 computer hacking offences. Prosecutors alleged he and others hacked the systems of the Australian National University, RMIT and Telecom. They had even managed to remotely monitor the Australian Federal Police investigation into their activities, Operation Weather. Assange admitted 24 hacking charges and was placed on a good behaviour bond and ordered to pay $2100. The investigation in Australia began after an audacious attack on NASA's computers in 1989. The word ''WANK'' appeared in big letters on NASA monitors, an acronym for Worms Against Nuclear Killers. Underneath was an Australian connection - lines from a Midnight Oil song. Whoever did it was never identified. In 1997 an astonishing book was published in Melbourne. It sold a respectable 10,000 hard copies but, when it was made available free on the internet it was downloaded 400,000 times within two years. Underground told the riveting inside story of the city's computer hackers and Assange was prominently billed in it as a researcher for the book's author, Dr Suelette Dreyfus, now an academic researcher. It opened with a detailed account of the NASA attack. Dreyfus wrote glowingly of Assange's efforts: ''Julian had worked thousands of hours doing painstaking research; discovering and cultivating sources, digging with great resourcefulness into obscure data bases and legal papers - not to mention providing valuable editorial advice.'' The book did not name the Melbourne hackers but used their online identities and told their story. The records of Assange's court case and his biographical details on WikiLeaks match the story of Mendax - one of the hacker's online identities in Underground. Mendax is described as a super intelligent child who never knew his father and was dragged from state to state by his mother who pursued a series of turbulent relationships. In 1988, Mendax was 16 years old and living in Emerald in central Queensland - the age Assange was at that time. Dreyfus wrote: ''For a clever 16-year-old boy the place was dead boring. Mendax lived there with his mother; Emerald was merely a stopping point, one of dozens, as his mother shuttled her child around the continent trying to escape from a psychopathic former de facto.'' Dreyfus continued: ''Sometimes Mendax went to school. Often he didn't. The school system didn't hold much interest for him. It didn't feed his mind … The computer system was a far more interesting place to muck around in.'' She also wrote that Mendax had a deep voice for his age. Assange has a distinctively deep voice. Mendax fathered a son in his teens. Assange has said he has a son at university. Mendax suffered a breakdown after he was arrested by the police, and after a period in hospital he lived rough in the Dandenong Ranges outside Melbourne. When he finally appeared in court on the hacking charges, Assange was living in the Dandenongs. Was this the story of Assange's life? Was he Mendax? Dreyfus will not say, citing the promise she made to the young hackers who had helped her with her book, that she would not disclose their identities. She is protective of and still obviously close to Assange. She told the Herald this week: ''He is not politically motivated. He is more concerned with truth and the quest for it. He is certainly not party political. I think he sees that there are good people on both sides of politics and definitely bad people. He is a very brave person. He is absolutely convinced that it is worth taking high personal risks in exchange for getting truth out to the community.'' Among WikiLeaks' volunteers, those who are close to Assange are similarly protective and reluctant to speak on the record. They described on background this week a man whose traits would not be unexpected if they evolved from Mendax's turbulent and nomadic formative years. Assange, they say, is noticeably self reliant, self contained, resourceful and apt to keep a distance from others. After his conviction, he stayed in Melbourne and built up his computer skills as programmer and as a developer of freeware. He read widely on science and maths - he is largely self taught in most of his endeavours. He did enrol for a period at Melbourne University but did not complete his studies in mathematics. Less convincingly answered by those who know him is whether Assange's quest to reveal secrets is the destiny of man moved by social conscience, or the natural progression of a highly intelligent child raised on the run, who found solace alone on a computer and anonymous camaraderie in cyber space. For his epigraph in the online edition of Underground, Assange used an Oscar Wilde quote: ''Man is least himself when he talks in his own person. Give him a mask, and he will tell you the truth.'' Is Mendax the real Julian Assange? http://www.smh.com.au/technology/tec...0409-ryvf.html  Gates: Wikileaks ‘Irresponsible’ for Releasing Video Laments that watchdog will 'not be held accountable' Jason Ditz With growing concerns over the massive number of civilians being killed in America’s assorted wars, Secretary of Defense Robert Gates took time out to publicly condemn Wikileaks for its release of a July 12, 2007 video showing US helicopters massacring civilians in Iraq. Gates insisted it was “irresponsible” of Wikileaks to release the classified video and that it showed only a “soda straw” view of the overall war. He also lamented that Wikileaks “can put out anything they want and not be held accountable.” The video was leaked a week ago and showed the Apache helicopters killing at least a dozen civilians, including two Reuters employees. The military had previously claimed the incident was a result of “combat operations against a hostile force,” though the video clearly shows no action taken by any of the people killed. Gates’ comments came as he attempted to shrug off the recent attack on a busload of civilians in Afghanistan and several other US attacks on civilians there, urging people to “face the reality that we are in a war.” http://news.antiwar.com/2010/04/13/g...leasing-video/  Former N.S.A. Official Is Indicted in Leak Case Scott Shane In a highly unusual legal action against an alleged leaker of government secrets, a federal grand jury on Thursday indicted a former senior National Security Agency official on charges of providing classified information to a newspaper reporter in hundreds of e-mail messages in 2006 and 2007. The official, Thomas A. Drake, 52, was also accused of obstructing justice by shredding documents, deleting computer records and lying to investigators who were looking into the reporter’s sources. “Our national security demands that the sort of conduct alleged here — violating the government’s trust by illegally retaining and disclosing classified information — be prosecuted and prosecuted vigorously,” Lanny A. Breuer, the assistant attorney general in charge of the Justice Department’s criminal division, said in a statement. The F.B.I. executive assistant director in charge of national security, Arthur M. Cummings II, said the bureau would continue to aggressively pursue such leak investigations. But Lucy Dalglish, executive director of the Reporters Committee for Freedom of the Press, a press advocacy group, called the indictment “unfortunate.” “The whole point of the prosecution is to have a chilling effect on reporters and sources, and it will,” she said. The indictment does not name either the reporter who received the information or the newspaper, but the description fits articles written by Siobhan Gorman, then a reporter for The Baltimore Sun, that examined in detail the failings of several major N.S.A. modernization programs and problems with supplying its huge electric power demands. Some of her articles were honored with a top prize from the Society for Professional Journalists. The N.S.A., which monitors phone calls, e-mail messages and other electronic communications, had spent hundreds of millions of dollars to update its systems to collect and sort the huge amount of data it was collecting. The modernization programs were plagued with technical failures and cost overruns, and Ms. Gorman, who now works for The Wall Street Journal, was the reporter who most aggressively covered the problems. Ms. Gorman, who has not been charged with wrongdoing, could not immediately be reached for comment. The Baltimore Sun articles that appear to be referred to in the indictment dealt with mismanagement and did not generally focus on the most highly protected N.S.A. secrets — whose communications it focuses on and what countries government and military codes it has broken. That may make a prosecution more feasible, from the point of view of protecting secrets during a trial. But because the articles in question documented government failures and weaknesses, the prosecution could raise questions about whether the government is merely moving to protect itself from public scrutiny. If Ms. Gorman’s articles were indeed those involved in the case, Ms. Dalglish said, they exposed “a multibillion-dollar boondoggle that was of great interest to Congress.” She called the articles “important public-interest reporting.” Mr. Drake, a high-ranking N.S.A. official from 2001 to 2008, is charged with 10 counts, including retention of classified information, obstruction of justice and making false statements. The retention counts each carry a maximum penalty of 10 years in prison and a $250,000 fine. Only a handful of prosecutions have been brought against government officials in recent decades for leaking information, and such cases often provoke a public debate over the tradeoff between protecting government secrets and covering up government wrongdoing or incompetence. The Justice Department spent several years investigating leaks to The New York Times after the newspaper disclosed in December 2005 the existence of the Bush administration’s warrantless eavesdropping program, run by the N.S.A. No government official was charged in that case. News reports based on classified information are common, and they are often followed by a referral of the leak by the intelligence agency to the Justice Department for investigation. But prosecutions remain rare, in part because of the difficulty of identifying leakers and in part because spy agencies often fear a trial will do more damage to national security than the original leak. http://www.nytimes.com/2010/04/16/us/16indict.html  Cyberwar Nominee Sees Gaps in Law Thom Shanker The Army intelligence officer nominated to lead the Pentagon’s new command devoted to warfare in cyberspace has warned Congress that policy directives and legal controls over digital combat are outdated and have failed to keep pace with the military’s technical capabilities. The officer, Lt. Gen. Keith B. Alexander, wrote to members of the Senate Armed Services Committee that computer network warfare was evolving so rapidly that there was a “mismatch between our technical capabilities to conduct operations and the governing laws and policies.” As he prepared for a confirmation hearing on Thursday as the first head of the Cyber Command, he pledged that the White House and Pentagon were “working hard to resolve the mismatch.” In a 32-page response to questions from senators, General Alexander sketched out the broad battlefield envisioned for the computer warfare command and acknowledged the kind of targets that his new headquarters could be ordered to attack. The target list included traditional battlefield prizes — command-and-control systems at military headquarters, air defense networks and weapons systems that require computers to operate. But he agreed with a question submitted by the Senate that asked whether the target list would include civilian institutions and municipal infrastructure that are essential to state sovereignty and stability, including power grids, banks and financial networks, transportation and telecommunications. General Alexander promised that the Cyber Command would be sensitive to the ripple effects from this kind of warfare, and would honor the laws of war that govern traditional combat in seeking to limit the impact on civilians. “It is difficult for me to conceive of an instance where it would be appropriate to attack a bank or a financial institution, unless perhaps it was being used solely to support enemy military operations,” he wrote. General Alexander did not note it in his response, but the Bush administration considered exactly that kind of network attack on Iraq’s banking system before the invasion of 2003, but rejected the idea, fearing an unintended impact on global financial markets. The confirmation hearing will be the public’s first opportunity to hear General Alexander describe the computer warfare command’s proposed objectives and responsibilities — and what safeguards he will pledge to protect privacy in the United States and to respect the interests of allies and neutral nations. He is the first chief of the Pentagon’s newest global combatant headquarters, and the first whose sole mission is cyberspace. If confirmed, General Alexander would receive a fourth star and be the first career military intelligence officer to lead a global combatant command. He would, in military jargon, be dual-hatted, a term to describe his role in charge of the Cyber Command while continuing to lead the National Security Agency, which specializes in electronic intelligence, including phone and computer espionage. The N.S.A.’s role in intercepting international calls to and from the United States since the Sept. 11 attacks, first approved by secret orders from President George W. Bush and largely continued by President Obama with the blessing of Congress, generated intense contention — and scrutiny by Congress and the courts. Because the agency spies on the computer systems of foreign governments and terrorist groups, General Alexander would, in effect, be put in charge of both finding and, if need be, neutralizing cyberattacks in the making, as well as defending military computer networks. “If confirmed, I will operate within applicable laws, policies and authorities,” General Alexander wrote to the senators. “I will also identify any gaps in doctrine, policy and law that may prevent national objectives from being fully realized or executed.” The military is moving into uncharted territory as it seeks to defend national interests and carry out offensive operations inside computer networks, he wrote, with nations of the world not even agreeing on what constitutes a computer attack or the appropriate response. He wrote that there was no theory of deterrence to guide planning for cyberwarfare similar to strategies that guided nuclear planning in the cold war, and that it remained difficult to assess exactly who carried out an attack over computer networks. The new Cyber Command was announced last year, and the unusually long delay in scheduling a confirmation hearing for its proposed leader is evidence of the intense behind-the-scenes debate over the command’s role, missions, authorities and safeguards. Another challenge highlighted by General Alexander is the role that the military’s Cyber Command would play on American soil, since it has far greater capabilities than the Department of Homeland Security. By tradition and law, the military only operates within the United States if ordered by the president. But a computer network attack on targets in the United States could happen instantaneously and with little warning. General Alexander reiterated that a presidential order would be required for the Defense Department and the Cyber Command to take the leading role in responding to a computer network attack on American soil. The world of computer network warfare remains highly secret, and many of General Alexander’s answers to the senators were excised from the 32 pages of responses, and placed in a separate classified addendum. http://www.nytimes.com/2010/04/15/world/15military.html  Military Asserts Right to Return Cyber Attacks Lolita C. Baldor The U.S. must fire back against cyber attacks swiftly and strongly and should act to counter or disable a threat even when the identity of the attacker is unknown, the director of the National Security Agency told Congress. Lt. Gen. Keith Alexander, who is the Obama administration's nominee to take on additional duties as head of the new Cyber Command, also said the U.S. should not be deterred from taking action against countries such as Iran and North Korea just because they might launch cyber attacks. "Even with the clear understanding that we could experience damage to our infrastructure, we must be prepared to fight through in the worst case scenario," Alexander said in a Senate document obtained by The Associated Press. Alexander's answers reflect the murky nature of the Internet and the escalating threat of cyber terrorism, which defies borders, operates at the speed of light and can provide deep cover for assailants who can launch disruptive attacks from continents away, using networks of innocent computers. The three-star Army general laid out his views on Cyber Command and the military's role in protecting computer networks in a 32-page Senate questionnaire. He answered the questions in preparation for a Senate Armed Services Committee hearing Thursday on his nomination to head Cyber Command. U.S. computer networks are under constant attack, and President Barack Obama last year declared that the cyber threat is one of nation's most serious economic and national security challenges. Alexander offered a limited but rare description of offensive U.S. cyber activities, saying the U.S. has "responded to threats, intrusions and even attacks against us in cyberspace," and has conducted exercises and war games. It's unclear, Alexander added, whether or not those actions have deterred criminals, terrorists or nations. In cyberspace, he said, it is difficult to deliver an effective response if the attacker's identity is not known. But commanders have clear rights to self-defense, he said. He added that while "this right has not been specifically established by legal precedent to apply to attacks in cyberspace, it is reasonable to assume that returning fire in cyberspace, as long as it complied with law of war principles ... would be lawful." Senators noted, in their questions, that police officers don't have to know the identity of a shooter in order to shoot back. In cyberspace, the U.S. may be able to counter a threat, rebuff an electronic probe or disable a malicious network without knowing who is behind the attack. The nation's ability to protect its networks and launch counterattacks, however, is shrouded in secrecy. Alexander gave the panel a separate classified attachment that provided more details on how and when the military would launch cyber attacks and under what legal and command authorities. Among the classified responses was his answer to whether the U.S. should first ask another government to deal with a cyber attack that came from within its borders. He repeatedly stressed that any U.S. response to a cyber attack must be authorized by the president and must conform to international law and guiding military principles. Those guidelines require that the reaction be deemed militarily necessary and in proportion to the attack. Noting that there is no international consensus on the definition of use of force, in or out of cyberspace, Alexander said uncertainty creates the potential for disagreements among nations. Alexander echoed other experts who warn that the U.S. is unprepared for a cyber attack. He said the first priority is to make sure the nation can defend its networks, which are now a "strategic vulnerability." Alexander said the biggest challenge facing the development of Cyber Command will be improving the defense of military networks, which will require better real-time knowledge of intrusions. He added that it will be difficult for the military to gain superiority in cyberspace, but the goal is "realistic." Alexander, 58, is a native of Syracuse, N.Y., and a graduate of the U.S. Military Academy. http://news.yahoo.com/s/ap/20100414/...pentagon_cyber  The Obama DOJ's Warrantless Demands for E-Mails Glenn Greenwald A very significant case involving core privacy protections is now being litigated, where the Obama Justice Department is seeking to obtain from Yahoo "all emails" sent and received by multiple Yahoo email accounts, despite the fact that DOJ has never sought, let alone obtained, a search warrant, and despite there being no notice of any kind to the email account holders: In a brief filed Tuesday afternoon, the coalition says a search warrant signed by a judge is necessary before the FBI or other police agencies can read the contents of Yahoo Mail messages -- a position that puts those companies directly at odds with the Obama administration. As part of a case conducted largely under seal and thus hidden from public view, the DOJ demanded these emails from Yahoo without any effort to demonstrate probable cause to believe the email user was involved in the commission of any crime, but instead merely based on the vague claim that there is "reasonable grounds to believe" the emails "are relevant and material to an ongoing criminal investigation." If the DOJ position were accepted, Americans would have substantially less privacy protections in their email communications. Federal law is crystal clear that a search warrant is required for the Government to obtain any emails that have been stored less than 180 days -- one that requires a showing of probable cause and that the documents sought to be described with particularlity. In contrast to the nation's largest telecoms' eager cooperation with Bush's illegal surveillance programs, Yahoo -- to its credit -- refused to turn over any such emails to the Government without a search warrant. As a result, the DOJ is now seeking a federal court Order compelling the company to comply with its demands, and a coalition of privacy groups and technology companies -- led by EFF and including Google -- have now filed a brief supporting Yahoo's position. Both Yahoo and that coalition insist that federal law as well as the Fourth Amendment's search and seizure protection bar the Obama DOJ from acquiring these emails without a search warrant. The law in question -- the Stored Communications Act, 18 U.S.C. sec. 2703 -- could not be clearer: A governmental entity may require the disclosure by a provider of electronic communication service of the contents of a wire or electronic communication, that is in electronic storage in an electronic communications system for one hundred and eighty days or less, only pursuant to a warrant issued using the procedures described in the Federal Rules of Criminal Procedure by a court with jurisdiction over the offense under investigation or equivalent State warrant. The DOJ's blatantly twisted argument is that an email should be considered to be "in electronic storage" only for as long as it is unopened by the recipient; once it is opened, it is no longer "in electronic storage," and no warrant is required for the Government to obtain and read it. Based on this rationale, the DOJ argues in its Brief that "a previously opened subscriber email is not 'in electronic storage'." In other words, claims the DOJ, the search warrant requirement protects your emails only to the extent you never read them, but as soon as you read them, the Government no longer needs a search warrant to obtain and read them; instead, it merely needs to claim to a court that the emails are somehow "relevant" to a criminal investigation, and then they must be turned over without any notice to you. The DOJ insists upon this power notwithstanding a 2003 decision from the 9th Circuit Court of Appeals which explicitly rejected the claim that emails once read or downloaded are no longer "in electronic storage" under the Act. Worse, a separate provision of the law -- 18 U.S.C. sec. 2510(17) -- explicitly defines "electronic storage" to include "any storage of such communication by an electronic communication service for purposes of backup protection of such communication": exactly what one does when one reads an email and leaves it on the server. The Obama DOJ's position is as radical as it is invasive; as Yahoo explained, it "is an attempt to reverse seven years of established precedent requiring law enforcement to follow carefully proscribed rules when seeking to obtain email content from providers like Yahoo." At least as important, Yahoo and the coalition of privacy groups and technology firms are arguing for the application of the seminal 1967 Fourth Amendment case of Katz v. U.S. to email communications. In Katz, the Supreme Court held that the Fourth Amendment protects against government eavesdropping on telephone calls even though such calls are not technically "houses, papers [or] effects"; even though eavesdropping does not constitute a physical search of the individual's property; and even though the telephone lines themselves are the property of the telephone company and not the individual. That is because, explained the Katz Court, "the Fourth Amendment protects people, not places." Moreover, telephone calls had become such a common means of private communications by 1967 that there was a reasonable expectation of privacy as to their contents; thus, "to read the Constitution more narrowly is to ignore the vital role that the public telephone has come to play in private communication." That such reasoning extends at least as much to email communications is self-evident, as is the danger of allowing Government acquisition of emails without a search warrant. According to a 2003 Pew survey, "102 million Americans were email users in December 2002" and "more than nine in ten online Americans have sent or read email." Those numbers were from 7 years ago and are obviously much higher now. By itself, according to its Brief, Yahoo is used by 30 million people to send and receive email. To allow the Government to access without search warrants the contents of one's private email communications -- as opposed to, say, merely information showing from whom one received or to whom one sent email -- is as central a violation of the Fourth Amendment's guarantee as can be imagined. Of course, the FISA Amendments Act of 2008 -- which passed with Obama's support and was designed to legalize much of the Bush NSA surveillance program -- already legalized warrantless surveillance of most emails sent internationally without any real court oversight, but the Obama DOJ's position here would result in a far lower protections being applied to purely domestic emails (albeit with some minimal court involvement). The Fourth Amendment threats are obvious. As the Katz Court said: "The Government's activities in electronically listening to and recording the Petitioner's words violated the privacy upon which he justifiably relied." And numerous courts, including the Sixth Circuit Court of Appeals in a 2007 decision, have explicitly invoked this reasoning to extend Katz's Fourth Amendment protections from telephone calls to email communications: It goes without saying that like the telephone earlier in our history, email is an ever-increasing mode of private communication, and protecting shared communications through this medium is as important to Fourth Amendment principles today as protecting telephone conversations in the past. I don't want to oversimplify the Fourth Amendment questions raised by this case. There are exceptions to the Constitutional warrant requirement which the DOJ likely will argue applies here [such as the claim that an individual has no "reasonable expectation of privacy" when communications are turned over to a third party, as emails technically are when they're in the possession of service providers such as Yahoo (though no more so than a letter is "turned over" to the U.S. Postal Service)]. Whatever else is true, there is simply no viable way to distinguish the telephone conversations which the Katz court protected under the Fourth Amendment and the emails which most Americans now use on a daily basis for their most private communications. If nothing else, consider the implications of allowing the U.S. Government to obtain and read emails simply by a vague showing of "relevance" to a criminal investigation, all without (a) any demonstration of probable cause, (b) a warrant from a court, (c) any notice provided to you that they're doing so, and (d) any Fourth Amendment protections. As the brief filed by EFF, Google and others puts it, granting the Government such authority would have "extremely significant implications for the privacy of Americans' communications." Yet that is exactly the power the Obama DOJ is claiming it possesses. UPDATE: I want to be clear about one point based on some of the discussion in the comment section: the Obama administration did not invent the statutory argument that an opened emailed is no longer a "stored communication" under the Act. That's an argument that has been advanced over the years by various parties in different contexts (though it was explicitly rejected by the 9th Circuit in the case I cited). But to use that claim to try to obtain emails from Yahoo and similar providers without a search warrant is most certainly a departure from the protocol which has governed how emails are obtained by the Government, which is why Yahoo, Google, EFF and others reacted so strongly. And the notion that emails are not subject to Fourth Amendment protections, whether new or not, is one of the most privacy-destroying claims that has arisen in the past several years. http://www.salon.com/news/opinion/gl...2010/04/15/doj  Aga Khan Files Lawsuit Against Toronto Lawyer Philanthropist alleges his works were reproduced and sold without permission Betsy Powell The Aga Khan, spiritual leader of Ismaili Muslims, is suing a Toronto lawyer and Montreal businessman for copyright infringement. The France-based philanthropist is seeking punitive and exemplary damages and an injunction against two of his own lay followers. The 10-page statement of claim, filed last week in federal court, alleges the two men and other unnamed parties infringed on his copyright by selling “literary works and readings” he wrote. The document alleges the defendants engaged in commercial ventures using unauthorized reproduction of material. The material in question consists of a collection of written messages and speeches delivered by the Aga Khan between 1957 and 2009. “The infringing materials were produced, published, distributed or sold by the defendants,” the statement of claim says. “The plaintiff … has not authorized the production, publication, distribution or sale of the infringing materials in Canada or anywhere in the world.” Ismailis live around the world, the suit states. “It is the mandate of the Imam to interpret to his community the faith of Islam” and “lead the effort to improve the security and quality of life of his community and the wider societies among which the Ismailis live. “The Aga Khan’s communications to his community are conveyed in this privileged context and, hence, he is concerned that their integrity should be safeguarded.” The suit names Toronto lawyer Alnaz Jiwa and Montreal businessman Nagib Tajdin, and unnamed other persons and/or companies that have also sold what it deems infringing material. A statement of defence has not yet been filed on behalf of Jiwa, the lawyer told the Star. When it is, “the (statement of) defence will speak on my behalf,” Jiwa said, declining further comment. The lawsuit says he has operated a website that promotes the sale of a book and MP3 without the Aga Khan’s knowledge or authorization. Prince Karim Aga Khan succeeded his grandfather to become the 49th hereditary imam of the Ismaili Muslims in 1957. Last year, Prime Minister Stephen Harper granted the Aga Khan honorary citizenship for his humanitarianism and long friendship with Canada. http://www.thestar.com/news/gta/arti...toronto-lawyer  Key Figure in 'Webcamgate' Invokes Fifth William Bender Lower Merion School District's information-systems coordinator invoked her Fifth Amendment right against self-incrimination yesterday at a deposition for the federal invasion-of-privacy lawsuit that sparked the "Webcamgate" scandal earlier this year. Carol Cafiero, who had previously sought to quash a subpoena ordering her to testify, refused to answer questions pertaining to the district's controversial practice of remotely activating webcams on Apple MacBooks issued to high-school students. "To each and every question I would ask her, other than her name, she asserted the Fifth, even after I told her that everybody else had come in and fully cooperated and provided complete testimony as to what took place," said attorney Mark Haltzman, who represents Blake Robbins, the Harriton High School sophomore who is suing the district. Cafiero was one of two school district officials authorized to remotely activate the cameras. District officials have said the "security feature" was used only to track stolen or missing laptops, but the FBI and Montgomery County District Attorney's Office are investigating whether a crime might have occurred. Robbins, 15, claims he was reprimanded for activity that his laptop webcam captured inside his Penn Valley home. Cafiero's attorney, Charles Mandracchia, has previously said she had done nothing wrong. Mandracchia could not be reached for comment yesterday. http://www.philly.com/philly/news/20...kes_Fifth.html  Masters Tournament Look at the photo with this column. It’s of an audio microcassette I found in my desk drawer yesterday while madly looking for something else in my overgrown office. As you may be able to read on the picture, it is an interview with Bill Gates from June, 1998. That’s the interview I did for my ill-fated Vanity Fair piece on the relationship between Bill Gates and Steve Jobs. It is almost sixty minutes entirely devoted to Bill talking about Steve. Quite a historical document, especially since its contents have never been published. And they won’t be here, either, except for one short quote that stood out when I listened to the tape today after almost 12 years. “What I can’t figure out is why he (Steve Jobs) is even trying (to be the CEO of Apple)? ” wondered Bill. “He knows he can’t win.” It is easy to see what Gates meant if you look at a comparison of the two companies in June, 1998. Microsoft stock was around $29 with a market capitalization of $250 billion. Apple’s stock was at $7.25, triple what it had been a year before when Microsoft had stepped-in to bolster Apple with a $150 million investment, but still worth a market cap of only $6 billion. In terms of products, market share, cash flow, and general strategy Microsoft had it all over Apple in 1998 and the idea that Jobs would ever catch up to Gates was, at the time, ludicrous. But look at the two companies today. Jobs is still running Apple despite cancer and a liver transplant while Gates has moved on to saving the world at the Gates Foundation. Microsoft is worth $240 billion, a tiny drop from 12 years ago, with the shares now around $27 (down from $29). Nothing gained in more than a decade. Apple shares, on the other hand, have gone from $7.25 to almost $240, Apple’s market cap has risen more than 33X from $6 billion to $220 billion. And Cupertino’s cash hoard today is almost exactly the same as Microsoft’s at around $40 billion. It’s pretty easy to argue that Jobs did win. Certainly Apple has the mojo lately with its string of home run products like the iMac, iPod, iPhone, and now the iPad. Even Mac market share is up in the double digits and Apple’s profit margins are the best in the industry. The trend line is definitely up for Apple and mildly down for Microsoft. What Bill Gates didn’t count on when he declared Jobs a loser back in 1998, was the Californian’s tenacity. It took 12 years to do it, but Apple is well positioned now to take Microsoft’s crown. I mean it. Look at the downward price erosion of Microsoft Office caused by a combination of Open Office and iWork, which is down to $30 on the iPad. How long will it be until Apple is giving iWork away to sell hardware — an option Microsoft doesn’t have? Not long. By then a bit more of Redmond’s goose will have been cooked. Digital market leadership is now Apple’s — not Microsoft’s — to lose. http://www.cringely.com/2010/04/masters-tournament/  Arbitron: Young Consumers Want Radio On Mobile Devices FMQB Arbitron and Edison Research just released a new national survey called The Infinite Dial 2010: Digital Platforms and the Future of Radio. The study touches on consumer use of the Internet and digital platforms and their impact on radio, and one of the things it found is that three in ten 12- to 24-year-olds are "very interested" in online radio in the car and on mobile devices. Among those age 12 to 24, 30 percent are "very interested" in listening to online radio in-car, while 28 percent are "very interested" in listening to online radio on mobile devices. The study also found that nearly one in four Americans has listened to audio from an iPod or other MP3 player connected to a car stereo. "Americans continue to hold radio in high regard, with nearly eight in ten saying they plan to listen to as much AM/FM radio in the future as they do now – despite advances of technology," said Arbitron’s SVP of Marketing, Bill Rose. Consumers also say radio station websites have improved as nearly half of people age 12 and older give credit to radio for improvements in their sites. Forty-eight percent say that radio station sites have gotten more interesting, compared to 17 percent believing them to be worse or less interesting. Additionally, the percentage of Americans age 12 and older who have a profile on one or more social networking sites has reached almost half (48 percent) of the population in 2010 – double the level from two years ago. The study also reveals that consumer use of social networking is not just a youth phenomenon. While nearly eight in ten teens (78 percent) and 18 to 24s (77 percent) have personal profile pages, almost two-thirds of 25 to 34s (65 percent) and half of 35 to 44s (51 percent) also have personal profile pages. "The use of social networking sites has expanded beyond younger consumers, with substantial numbers of Americans over the age of 35 now using social media," said Rose. Edison's Tom Webster added, "Social networking has become a part of mainstream media behavior." http://www.fmqb.com/article.asp?id=1763352  Study Examines Music Streaming By Smartphone Users FMQB A new study from Vision Critical looks at smartphone users in the U.S., U.K. and Canada and their different habits when it comes to streaming radio on their devices. The survey showed that U.S. smartphone owners are more likely to be using apps to stream web-only radio and other streaming services, while U.K. and Canadian users more likely listen to AM/FM radio simulcasts. Among adults in the U.S. who have listened to online-only radio in the past month, Pandora was far and away the most popular online music service (42 percent having listened in the past year), followed by Rhapsody (6 percent), last.fm (5 percent) and Yahoo! (5 percent). The findings come from Vision Critical’s "Radio Futures 2010" study, conducted in February and March. Further survey results will be shared at next Monday’s RAIN Summit West conference in Las Vegas. During the survey, 31% of U.S. smartphone and iPod Touch users said they had listened to Internet radio or a music streaming service on their device in the past week. In contrast, just 19 percent reported listening to an AM or FM station on the same platform. In the U.K., where Spotify is the most popular streaming service, broadcast radio is the more popular choice. A total of 31 percent of U.K. smartphone and iPod Touch users said they listened to broadcast radio in the past week using the apps on their device, compared to 21 percent who reported listening to web-only radio or streaming services. In Canada, where neither Pandora nor Spotify is available yet, 14 percent of smartphone and iPod Touch users said they had listened to AM or FM stations on the platform in the past week, while only seven percent reported listening to web-only radio or streaming services. "This speaks to the kind of transformational impact that Pandora is having in the U.S. marketplace," says Jeff Vidler, SVP/Managing Director of Vision Critical’s Radio practice. "It’s no coincidence that the one market where we see web-only services trump broadcast radio on smartphone apps is the only jurisdiction where Pandora is legally available – and it speaks to the need for U.S. broadcasters to step up to the plate with their own streaming apps before Pandora owns the distribution channel." http://www.fmqb.com/article.asp?id=1763028  Spotify Slammed by Songwriters A songwriters' association has criticised the Spotify streaming service over 'tiny' payments to musicians Dan Martin Last year it was claimed that 1m Spotify plays of Lady Gaga's hit Poker Face earned her just $167. Photograph: Axel Heimken/AP An association of songwriters has hit out at Spotify, casting fresh doubt on the streaming service's capacity to generate income for musicians. The British Academy of Songwriters, Composers and Authors (Basca), which represents 2,000 songwriters, claimed yesterday that the payments generated are "tiny" and called for the company to be more transparent about the nature of its business. At the moment, Spotify does not disclose details of its deals with labels and publishers, and Basca chairman Patrick Rackow says this is leading to a climate of fear and distrust. He told the BBC: "At the moment, the amounts of money that are actually being received are tiny. That might be because there is no money there. But there is no clear trail that can be established so that the songwriter can trace back what they ought to have got. These things are behind a blanket of secrecy, and that is extremely worrying. "The danger is that these deals all become so secret that the mist that descends creates uncertainty, creates fear. That allied to the fact that the sums being paid through are very small creates a climate of suspicion. I think it harms Spotify, it harms the writers' perception of Spotify and this is a service they want to support." The Swedish-owned company has been hailed in some quarters as a saviour of the music industry, offering users free streaming of a huge catalogue of music punctuated by short adverts. A monthly premium of £9.99 gets users uninterrupted access to the catalogue. But last year it was claimed that over a five-month period, 1m plays of Lady Gaga's hit Poker Face – one of the most popular songs on the site – earned her just $167. With record labels themselves owning a stake in Spotify, Rackow reckons that returns are "unlikely to filter down into payments to the artists". He continued: "It is pretty tough for the average successful songwriter to make a living. It is hard to say that anyone has a right to make a living out of writing songs but if you write songs that people actually want to hear then I think that does give you a right to get some renumeration back." Spotify would not comment on the Basca claims, but has continued to insist that as more subscribers sign up and advertising revenue increases then that money will trickle down to the people who make the music. http://www.guardian.co.uk/music/2010...fy-songwriters  SoundExchange Paid Out $51.7 Million In Q1 FMQB SoundExchange, the non-profit performance rights organization appointed by Congress to pay digital royalties to artists and copyright holders, announces that the first quarter of 2010 resulted in its largest-ever payout. A total of $51.7 million in royalties from digital transmissions, including Internet radio, satellite radio, and cable TV music channels, are being paid out currently. The unprecedented amount represents a 135 percent increase over first quarter payments last year, and surpasses the previous record distribution by nearly $10 million. "This was the result of a lot of hard work by our staff, and also represents a new commitment by our registrants to help increase these amounts," said SoundExchange's Executive Director John Simson. "In addition to our usual distribution amounts, this total includes millions of dollars which were freed up by our commitment to cleaning up the bad data which is often reported to us by services." During this quarter, SoundExchange staff have worked with registrants to resolve thousands of entries reported as "label unknown" or attributed incorrectly, by encouraging owners and artists to claim the tracks individually. SoundExchange staff also put in many man-hours of research to correct data so that funds could be distributed properly. The independent label community received its largest-ever portion of digital revenues this quarter. Many individual recipients received their largest checks to date. "In this time of shrinking revenues from so many other sources, our SoundExchange income was large enough to have paid the production costs of a new album and more," said Bruce Iglauer, owner/operator of Alligator Records, "Absolutely every label and every recording artist should be a member. It's simply all positives and no negatives." Simson also credited his organization's outreach to artists who had not previously received royalties with a portion of the growth. When artists and copyright holders register with SoundExchange, they receive lump sums of the royalties they have accrued since 1996. A flood of new registrations, fueled by SoundExchange's ramped-up awareness efforts in mid-2009, meant lots of those checks were issued in Q1. "We're extremely proud of what we do here," Simson added. "It's a challenge and a privilege to be a part of the process that sees the creators of music fairly paid for their invaluable work." http://www.fmqb.com/article.asp?id=1764472  The Barriers of Music Consumption: Past and Present Kyle Bylin, Associate Editor -- Edited by: Refe Tuma of Creative Destruction There was a time when songs were songs. When there were the albums that you owned and those that you did not. When there was a distinct difference between the music that you liked and the artists that you didn't care for at all. There was a time when the music you that collected was actually a physical thing; it represented your identity and served as a mirror of your taste. When the albums you had access to, beyond those that you owned, were limited to that of your friends and families. When the only way you could expand your collection was to purchase more music or temporarily borrow a copy of theirs. There was a time -- one I barely remember -- where these boundaries defined my music experience, but those days are gone now, and we can never get them back. Once the album format fractured and individual songs became the focal point of music consumption, companies like Pandora, iLike, Last.FM, iMeem, and others began the process of discerning the unique characteristics of each song, and building recommendation engines around them. In effect, what happened as a consequence of their efforts is that each song transformed into a portal. These “gateways" that could be opened up, which enabled fans to travel almost effortlessly from one sphere of musical influence, to another similar sphere. From that particular sphere on, if traveled, it would take them to spheres of musical influence that existed outside of their current taste. Here, individual songs not only became the primary way that fans consumed music, but songs also became a vehicle for music discovery. Prior to this shift -- brought forth by the MP3 format -- individual songs only existed within the context of the other songs on the mix tape, radio playlist, or album. Since, more often than not, the singles from the album were the only songs that existed outside of the album, most of the casual fans of an artist never listened to or came into to contact with the other songs on it. In the pre-MP3 era, the act of collecting music consisted solely of the ownership of the whole album, of the stack of jewel cases that sat next to your stereo. If a fan wanted to grow their music collection, the only barriers that prevented them from doing so related to the the location of the nearest record store and money. Since music was a relatively costly thing to collect on a per-album basis, most people had relatively small collections -- in comparison to the more diehard or “true" fans, if indeed they collected any music at all. Barriers of Music Then, in the span of a about 10 years, the proliferation of the personal computer; the shift from Dial-Up to high-speed Internet; the increased processing power and hard drive space in computers; the falling cost of blank media and external hard drives; the widespread use of CD burners; the social phenomenon of the iPod and iTunes; and the epidemic of file-sharing occurred. And, with these societal and technological shifts, all of the barriers that defined music experiences of previous generations and the act of collecting it fell. To anyone who had access to and was literate in these digital technologies and services, or simply knewsomeone who did, music became 'democratized.' Here, the act of collecting music shifted from being limited to the access that a fan had to music and the money they had to buy it, to the amount of time or number of social connections that they had. There were no longer the albums that they owned and those that they did not, but those that they had, those that they aspired to have, and those that they just didn't have yet. Let alone, the song that they heard on the Pandora five minutes ago -- which they then downloaded onto their computer, listened to, told their friend about over IM, and shared it. And now -- within a few mouse clicks -- both of them are listening to that same song. It's a part of their both collections. The barriers of music consumption between the two friends are gone. Essentially, with these shifts, anyone who truly wanted to engage in the act of collecting music could. And, in the matter of a month, or even days, they could amass their own collection, one that, by comparison, dwarfed those that previous generations considered to be substantial. Soon enough, the process of burning downloaded music onto blank media could be skipped, and it could be transferred to their iPod in the matter of minutes, or an hour. And, once this barrier fell, file-sharing was “reduced to a frenzy of acquisition that [had] less to do with the sharing of music than it [did] with filling the ever-expanding hard drives of successive iPods."1 At first, it was the matter of filling an iPod with 5 to 10 gigs of music, but today, it's a matter of acquiring upwards of 40,000 songs on the average iPod. Fractured Collections With the barriers to the act of collecting music set so low, if not nonexistent, another subtle but significant shift occurred: the psychology behind the acquisition of music changed. For those of previous generations, they collected music with the notion of longevity in mind, as it best reflected their taste in music at that moment. In contrast, for those who engaged in the act of acquiring music through other means, like file-sharing, their taste encompassed past, present, and future interests. Their collections reflected not only their inherent taste and disposition towards certain types of music, but that of their peer group and those whom they surrounded themselves with. Thus, distinct difference between the music that they liked and the artists that they didn't care for at all became increasingly blurred, and so did the contents of their music collections. In a sense, though, the collections of those who were born digital are not complete. They're fractured, consisting of bits and pieces of everything, of songs divorced from their origins and physical packaging. These songs stand alone -- void of everything but the artist's name, the album's title, and the digital cover art. Where the jewel case, booklet, and liner notes served to embody culture, to communicate its identity, and to mirror the taste of its owner -- the iPod is merely a container for culture. Its contents reveal the personality of the owner, but say little about the soul of the music. While it may seem like strangers greet physical music collections and iPods with a similar sense of awe and reverence, it's important to recognize the disparity between the two. As the emotions that they experience in the presence of unique works of art, and those that they feel while holding an iPod-- that happens to contain art -- shouldn't be confused as if they are the same thing. Especially since one relates to the “aura" of the music, and the other to a piece of technology. In the first scenario, when those of previous generations encountered a physical collection, they poured over it, investigated it, and held the works of art in their hands -- works, which, weren't of their own, but still provoked meaning and were intrinsically tied to their story. Now, those who were born digital don't hold the works of art, they embrace the iPod. And, when they encounter the collection, while they do still pour over it, and investigate it -- as they scroll through it -- that sense of awe and reverence is lost. The music in the collection is presented devoid of its aura, “it has been removed from its context -- from the material processes of its creation."2 Their emotional experience relates not to being in the presence of unique works of art, but solely of the moment of social connection and identification with the other person. This understated difference -- in how works of art are experienced -- relates to yet another shift in music culture that separates those who were born digital from those of previous generations. Internet is Freedom For some, these shifts mean the dawning of a whole new era. For others -- having come of age during the proliferation of digital technologies; the social epidemic of file-sharing; the explosion in music choices; the splintering of genres into niches; the rise of the personalized music experience; and the increased emphasis on recommendation engines and social filters -- this is the reality they've come to know. But, for the rest, those who've lived cradle to grave in the digital era, this is the only reality they've ever known. To them, there is no before file-sharing and the Internet -- only these societal and technological shifts, and their aftermath. Those who were born digital don't remember a world in which there were the albums that they owned and those that they did not. The music that they collect isn't a physical thing anymore, it's just files. Sure, they represent their identity and serve as a mirror of their taste, but also of everyone that they surround themselves with. Initially, they may have been limited to their friends and families collections, but as they became literate these digital technologies and services, they were only limited to their imaginations, curiosity, and desire to explore. To them, the Internet is freedom. And, the record industry won't beat them. The industry can't keep trying to rebuild all of the barriers that defined music experiences of previous generations and the act of collecting music, as if, once restored, those who were born digital will revert back to “normal." To them, the way in which they consume music is normal. In the digital era, the record industry has tried to enforce ever more vigorously the barriers to music that defined the experiences of previous generations upon those who were born digital. And, in turn, they have only resisted ever more destructively. But, before we attempt to deny the very nature of the barriers to music in the present by changing them back to the past, we need to recognize that those born digital -- those who immersed themselves in the social ecology of music culture that's forming online -- are, in fact, different now. And, to understand why that is, we must first examine the biases of the traditional music consumption system, and the specific delivery mechanisms that govern it. Then, compare them with those of this “other" music consumption system that those born digital also experienced. Only after we've done this, will we be able to come to terms with the truth, that, it's not those who were born digital that are “broken." Rather, it's our traditional music consumption system that's broken. And, it's about time that the record industry stops pretending that its barriers still define the way they experience music. http://www.allaboutjazz.com/php/news.php?id=53635  So Big It Fails Big vendor frustrations, disempowered librarians, and the ends of empire Barbara Fister This week Meredith Farkas asked “Has EBSCO Become the New Evil Empire?” at her blog. Its name, Information Wants To Be Free, is a phrase that publishers have called “absurd” and “fatuous,” but is actually a defining irony of libraries. Everyone who uses libraries uses them because—hey! libraries give us what we need for free! This is great! Because our users have a voracious appetite for information and couldn’t possibly afford to buy all that they might need, it’s up to librarians to work with complicated equations that divide our budgets by desired resources, factoring in local politics and vendor constraints, to yield the maximum freedom of information possible. Most of that work is done behind the scenes. We make it seem so effortless, indeed, that faculty increasingly think of libraries as purchasing agents, not as enduring and significant cultural institutions. Unfortunately, there are a lot of invisible strings attached as we license information in order to set it free, and sometimes those invisible strings get hopelessly tangled. Farkas was provoked to criticize EBSCO because, after a series of unfortunate events, her Rubicon was crossed: a scholarly society that publishes a journal essential for her community of users signed an exclusive deal with EBSCO that pulls its content out of other databases, including any future contributions to JSTOR. To further complicate things, it has disappeared from EBSCO’s Swiss army knife of a database, Academic Search Premier. It appears that you have to subscribe to not one, but two pricey databases to get electronic access because there are two history database superpowers (recently purchased by EBSCO) that have divided the world of history into two regions. Society members will have access to the whole shebang, but not libraries; they can’t become members. Farkas offers a synonym for “exclusive”: extortion. She also, in an incisive analysis worthy of von Clausewitz, surmises that the society has found a nifty way to increase their membership by removing its journal from most libraries that had it through the nearly-ubiquitous Academic Search Premier. You want the journal? Join the club. Out of this situation, librarians tend to arrive at three conclusions: * Articles published in this journal have deliberately been made into an artificially scarce resource. * The society involved and/or EBSCO stand to make more money because of this new scarcity. * Fewer people will have access to the information—and parties to the exclusive agreement think that’s great! What’s interesting in all this is that the major providers of access to this journal—libraries—were not consulted at all. In fact, Farkas only found out about it because links through Serials Solution that used to point her patrons to access points in JSTOR and Academic Search Premier had simply vanished. Who’s got the ransom note? Here’s where I think the word “extortion” doesn’t quite work. Usually, extortionists communicate with their victims: “pay us, or else.” In this case, libraries have had to stumble across the “or else” before they could do some frantic research to find out where to send the ransom and what it will cost while patrons stand at the reference desk or wait on the phone, rolling their eyes at stupid librarians. Are we so insignificant that nobody even bothered to copy us on the ransom note? This has the Librarian in Black hopping mad, and not just at EBSCO. “Why do we in libraries tolerate this kind of arrogant behavior from a vendor? We’re the ones with the money. They should be doing what we want. We need to vote with our wallets and choose to work with vendors who provide the best possible products for the money, are fast to respond to technology trends, do not engage in shady business practices, and treat their customers with respect. I encourage everyone to make your vendors aware that you are not happy with their behavior (it’s not like they’re going to smack you in the face for saying so). I also encourage everyone to vote with your wallets the next time you get to make a vendor choice—pick the one that does what you want, how you want it, and who has a good reputation with your peers. Don’t automatically go for the lowest price. You’ll pay for it in different ways later, believe you me.” All of this is complicated in so many ways. Working with complexity First of all, we aren’t getting these materials for ourselves; we’re getting them for patrons who don’t really care what the terms are so long as they get the journals they want (and each patron wants a different set). The fact that they line up to publish in journals that are library-unfriendly is proof of their contempt for our situation. Ignorance is no excuse; we’ve been trying to explain the problem for a couple of decades, and you guys have advanced degrees; it’s not that hard to understand. Why do we tolerate this arrogant behavior from our clientele? Because we’re a service profession. Their wish is our command; it’s our problem that the budget isn’t big enough to carry them all out. And, our collections are now a moving target. There’s no telling whether what we subscribed to last Tuesday will be there today. Things disappear and pop up in databases so frequently it’s like a giant game of whack-a-mole trying to keep up. When a consortium strikes a deal on our behalf, the content they have licensed for several years can change without the price being affected. What buying power? Database vendors are also working with complexity. Each publisher makes its own demands. They can pull out of a deal or change their minds about the length of embargoes. EBSCO may appear to be the evil empire, but there are a lot of local warlords in the publishing world throwing their allegiance to whichever side is most favorable. We’re the peasants whose fields get trampled in the fighting. Sure, they need us, but they won’t turn to us as advisors in the art of war. Another area of concern for some librarians is that EBSCO has been doing everything it can to consolidate its market power by offering libraries sweet deals for products that directly compete with established databases, such as the venerable Public Affairs Information Service, founded way back in 1915. Librarians complain they can’t get a simple answer about a product without first suffering through a hard sell for mass conversion to the EBSCO religion. Because we’re constantly recalculating the magic formula that makes things free while teetering on the brink of financial disaster, most of us can’t pass it up. The trouble is that, though we’re the ones with the money, we can’t make a market correction by taking our business elsewhere. This is not a free market. If faculty say they need the Journal of Military History we can’t talk them into accepting the Journal of Peace Research instead. Besides, since SAGE handles that journal’s electronic distribution, it’s not going to save us any money. We’re mad as hell, but . . . Vendors can make a good case that they’re doing exactly what we ask them to do: aggregate and funnel as much full text content as possible through a single familiar interface. When Amy Fry, Julie Gilbert, and I surveyed librarians’ attitudes toward general interdisciplinary databases such as Academic Search Premier in 2007, more than 90 percent of the 565 librarians who responded said they were satisfied or extremely satisfied with these databases. We speculated “it may be the case that vendors have aligned the development of their products to customer feedback very successfully.” We also looked at two years’ worth of actual use of the most common product—Academic Search Premier—at 14 college libraries and discovered that 40 percent of the full text journal titles had not had a single article downloaded even once at all of the 14 libraries combined. Yet librarians, though generally satisfied with the product, expressed interest in having even more full text. We want more; we don’t always know if our patrons are really going to use it. A dispatch from the empire Yesterday, I decided to shoot off an email to Sam Brooks, senior VP of sales and marketing at EBSCO. I didn’t think he’d have time to respond, but I hoped he might be able to point me to an official statement. He couldn’t, but told me he’d get me something by morning. And indeed he did, as soon as his schedule permitted (which happened to be around 2 a.m.). I wanted to know the dirt on publishers’ role in setting conditions, but he answered diplomatically, as one must when dealing with warlords. “We can't have good relations with publishers if we say or do things that are harmful to them. We believe that it is in the best interests of our customers for EBSCO to have the best possible long-term relationships with publishers. We are in the unique position of having to attempt to satisfy the wants and needs of both publishers and libraries. We value both greatly. After many discussions with librarians via advisory board meetings and focus groups, and after looking carefully at usage statistics, ranking studies, impact factors, Eigenfactor, etc., we believe we have a pretty good idea about which publications are most important to our customers. We are determined to retain stability of active full text for these titles on behalf of our customers. Accomplishing this is not easy and has required significant investment. We have a service for customers that alerts them to title coverage changes and we pride ourselves on keeping the databases as stable as possible.” I suspect that I’m like many librarians; with so many titles serving so many different interests, keeping abreast of title changes that will hurt my patrons (but may be a total yawn at other libraries) is hard; it would be nice if an alarm would be built into the database, some kind of Doppler radar for titles that get a lot of use at our library and would warn us when a storm is approaching. Of course, early warning would depend on societies informing their members, who would spread the word among colleagues—but transparency is not in societies’ financial interest. Their finances are anchored in an era when publication revenue could be counted on to fund their operations. Too much access threatens an organization dedicated to spreading knowledge. (Remember when I said this gets hopelessly tangled?) I asked about two other issues that seem to raise librarians’ blood pressure regularly: embargoes (or what in JSTOR terms is known as a “rolling wall”) and exclusive deals (controlled vocabulary for “extortion”). He gave me his perspective. “Every situation is different and unique, and confidential by contract. This is one reason why librarians see fewer comments from EBSCO on this than some would like. Rarely do publishers comment publicly on the issue of exclusives, but in one case, a publisher recently did so in an interview with Library Journal and that interview speaks for itself. The owners of the content (the publishers) control their content and make the decisions regarding exclusivity. With regard to embargoes, these are sometimes required in order to be able to include full-text journal content in our databases. We have accepted these in cases where the alternative is that we would not be able to secure a license to include the full text in our database . . . most publishers do not require embargoes (and of course, we never add an embargo unless the publisher requires it).” Relationship status: it’s complicated Steve Lawson ruminates over a host of complexities in his wonderfully-titled blog post “Jailbreak Your Library” including these provocative snippets: “Libraries are hindered in any negotiations with “content providers,” because we aren’t their real customers. Library patrons are their customers and we write the checks. Why should libraries worry about solving this issue? Refuse to apologize or mitigate crises that you did not create. Librarians need a more compelling story than “we hate you.” “ We do, indeed. We need to think about some big-picture issues, such as how we let ourselves become purchasing agents for faculty. If we’re not okay with that, how do we redefine libraries in a way that tells our communities a compelling story? “Journals cost too much” doesn’t seem to be holding them spellbound, and information literacy, though a valuable cause, teaches students to cope with the status quo and does not include handing out hardhats and lessons on “the system is about to collapse around us and needs repair right now.” Just how urgent is the problem to librarians, really, if as recently as 2007, such an overwhelming number of libraries expressed satisfaction with a product from a company now replacing Elsevier on dartboards in libraries across the country? We need a compelling story that explains why it’s time to stop seeking ransom notes among a blizzard of vendor emails and temporarily buying our way out of trouble. We need to stop accommodating the magical thinking that scholars can have whatever information they want and don’t have to alter their publication practices or confront the fact that tenure and promotion decisions are the seal of approval on a Faustian bargain. We need to make a case for sustainability, or simply admit that we’ve abandoned curation to support binge-and-purge gluttony. Or, we could just say we’ve done our best but it’s not working—and find a strong doorway to stand under as the whole thing falls apart. Empires fall A week ago, Clay Shirky wrote a riff on Joseph Tainter’s book The Collapse of Complex Societies in which Shirky proposed that complex business empires may face the same end as the Roman Empire or ancient Mayan civilization. Their complex societies fell in on themselves because they were too complicated. We’re about to see that happen in scholarly communications. We don’t quite know how we’ll keep the light of culture going in the resulting dust and rubble, but we’d better be ready. He ends his essay with this advice. “When ecosystems change and inflexible institutions collapse, their members disperse, abandoning old beliefs, trying new things, making their living in different ways than they used to. It’s easy to see the ways in which collapse to simplicity wrecks the glories of old. But there is one compensating advantage for the people who escape the old system: when the ecosystem stops rewarding complexity, it is the people who figure out how to work simply in the present, rather than the people who mastered the complexities of the past, who get to say what happens in the future.” We long ago realized we can’t afford the current impulse for reckless productivity and consumption based on the glory that was scholarly publishing. We should strive to become masters of simplicity rather than ingenious servants of complexity. It’s time to get your Zen on, and while you’re at it, lay in some matches and candles. We’re going to need them when the system fails. http://www.libraryjournal.com/article/CA6725617.html  Review Ubuntu on a Dime author James Floyd Kelly pages 280 publisher Apress rating 9/10 reviewer AussieNeil ISBN 1-4302-1972-6 summary takes you on a tour of the very best, but low-cost hardware, while only using zero-cost software in each of the many categories that matter to the typical PC user. AussieNeil Alternate histories aside, Ubuntu on a Dime is a tribute both to the skills of the author and to the decades of effort by those that have developed user friendly software and hardware, so that this 280-page book gives anyone with a reasonable level of self-confidence the recipe to build their own computer, install all the software needed for common activities, and quickly become productive. James Kelly, spends just 30 pages in the first chapter explaining how to purchase the required computer parts and assemble a Ubuntu PC or "U-PC" computer and does it in a relaxed, easy-to-follow style. Mind, the task is simplified by choosing a motherboard with integrated sound and video, but that is exactly what you'll find in the standard corporate office PC. (Personally, I would have recommend purchasing a SATA hard drive to avoid the not-touched-on master/slave complications of using a shared IDE cable for the hard drive and CD/DVD drive.) The book is illustrated throughout with frequent, excellent screen shots as the author steps you through hardware assembly, then operating system and application installation, configuration, and use. In chapter 2, the author explains how to install the Ubuntu operating system and keep it updated. Wisely, he has chosen the Long Term Supported 8.04 version, but has omitted mention of the different Ubuntu support periods. He has also missed an opportunity here to expand on the growing list of Ubuntu variants, in particular Kubuntu, which I would see as an easier migration choice for those familiar with Microsoft Windows. Chapter 3 is dedicated to a definition of what the author means by "free software" and covers the costs (including the relevant security risk costs) associated with the four software categories; Pay-to-Use, Open Source, Cloud Computing, and Freeware. The remaining 9 chapters look at how to use free software — software either included in the default Ubuntu installation, or available via cloud computing — to complete common computing tasks. In chapter 4, email using Evolution is covered and word processing, spreadsheets, and presentations using the OpenOffice.org suite is covered in chapters 5 to 7. The Cloud Computing Google Docs Office Suite alternative, with the advantages of everywhere access to your documents and collaborative working is covered in chapter 11. Web browsing using Firefox is covered in chapter 9, with most of the chapter dedicated to finding and installing useful add-ons. Google gets another couple of chapters when photo management with Picasa is covered in chapter 8 and Google Email and Calendar configuration and use are explained in chapter 10. The last chapter looks at a few other useful applications found in Ubuntu: Calculator, Text Editor, Notes, Disk Burning, Movie Playing, and Music Playing. The three appendices cover the computer parts list, three ways to obtain an installation disk for Ubuntu, and finally a bibliography of web sites, books, and must-have apps so you can extend the use of your new Ubuntu PC. The 9-page index is fairly comprehensive, considering the wealth of illustrations throughout the book. I liked this book because it covered tasks seen daunting by many (PC building, operating system and software installation, configuration, and upgrading) in an light, easy-to-follow manner, supported with excellent illustrations. Further, the author covers a lot of ground without overwhelming the reader, taking you to a level where you can start using your computer productively and showing you how to use help files and online resources to extend your use of your excellent hand-built investment. While extolling the benefits of open source software, he hasn't labored the point. Vendor lock-in costs associated with proprietary office suites aren't mentioned, nor are the lower security risks associated with open source usage. If you are looking for a way to reduce your computing costs, or know someone that would appreciate a gift that can help them achieve this, then Ubuntu on a Dime is well worth considering — particularly for anyone that gets satisfaction from learning via do-it-yourself. http://books.slashdot.org/story/10/0...untu-on-a-Dime  Can Android Overtake the iPhone? Tim Bajarin Five or six years ago, I had a number of meetings with some of the big PC manufacturers. I suggested they take a close like at Danger and the innovative interface used for the company's Hiptop handset. At the time, most cell phones had very simple e-mail interfaces. Very few even attempted to connect to the Internet. But Danger had a clear vision of what phone could become, creating what I would consider the granddaddy of today's smartphone interfaces. By that point, it was becoming clear to some of us analysts that smartphones were actually small computers. If PC companies were going to stay ahead of the curve, they would have to add a handset to their line soon. At the time, I was very intrigued by Danger's interface. It was so well designed that it could be deployed on a TV, PC, smartphone, or just about any other digital device. Such a UI could help one of these companies deliver a similar experience across devices. And people would only have to learn to use the interface once. Ironically, Microsoft ultimately purchased Danger. To date, the company has not employed this smart UI on any of its products. The genius behind Danger was a guy named Andy Rubin. He left the company before it was acquired by Microsoft, in order to begin working on a secret phone OS that would eventually get Google's attention. Google bought Rubin's small startup. The mobile OS eventually became Android, which, as you know, has since become the hottest OS in the smartphone space, having been adopted by dozens of handset vendors around the world. I was reminded of Android's power while walking the CTIA show floor in Las Vegas. The show should have been called Android World. A good number of the handset companies I met with had some version of Android on their smartphones, and a number showed me new product behind the scenes that use the OS. I also saw at least five tablets (most behind the scenes) running Android that are set to come out in the next six months. The most innovative products I saw at the show were based on Android. Take the Samsung Galaxy S, which runs the OS and sports a four inch AMOLED screen. It's the best screen that I have ever seen on a smartphone. Images on the phone are crisp and bright and are even clear out in the sunlight. Samsung won't say when it is coming to the US, but it could be one of the more important Android phones to launch this year. The Motorola i1 is a new rugged and sleek push-to-talk handset that runs Android. At the press conference, Motorola let people play shuffleboard with the handset to show just how rugged it is. Kyocera also announced an Android handset—the ZIO. The phone has a beautiful 3.5 inch screen, 3.2 megapixel camera, and stereo Bluetooth. It will cost $250 unlocked. If CTIA had a Best of Show award, it would have gone to Sprint's EVO 4G WiMax phone. The handset has a 4.3 inch screen, 1 GHz SnapDragon processor, 1GB of internal storage, WI-FI, HDMI out, and the ability to act as a WI-FI router for up to eight devices. It's a stunning phone that uses a version of Android that looks more like a Pocket PC OS than a cell phone OS. Dell debuted the Mini-Tablet 5, the company's first Android tablet for the US. It has a five inch screen perfect for Web browsing. However, even though Dell says that the device will fit in your pocket, it's really not a smartphone. You wouldn't hold it up to year ear to talk. A Bluetooth headset makes more sense for conversations. The product is what I call a "tweener." It's not really a smartphone, and it's not really an iPad-like tablet. I'm not really sure who the audience will be on this one. On the other hand, the tablet has a really cool design and its light weight, compact design could be of interest to some users. Android is steadily becoming the go-to OS for smartphones and tablets. It's even showing up on some set-top boxes and smart Blu-Ray players. But it's in the smartphone and tablet spaces that the mobile OS will have its greatest impact. Although Nokia and RIM were well represented and Microsoft and Palm each had booths at the show, most other major handset manufacturers like Samsung, HTC, and LG were in the Android camp. It's clear why many market research firms believe that Android will be the number one or two smartphone OS in the next two years. It's also clear why Android is at the heart of the Apple/Google battle. Apple should be keeping at Windows Phone 7, sure, but it's Android that is likely to be the biggest threat to the iPhone OS in the near future. When Steve Jobs invited Google CEO Eric Schmidt to join Apple's board, he likely didn't expect Schmidt to go to school on Apple's strategy by launching its own iPhone challenger. No one Jobs is upset at Google. http://www.pcmag.com/article2/0,2817,2362469,00.asp  Opera Hits 100 Million Users Browser maker singing from the rooftops about landmark Patrick Goss Opera is celebrating after hitting the 100 million mark in global users of its browsers. Opera has been boosted by the Windows ballot screen, which was brought in by Windows following the company's high-profile complains to the European Commission. And with a 50/50 split between PC users and people who use Opera on mobile devices, the company is celebrating a 30 per cent year-on-year growth for its flagship desktop browser, according to March figures. On the right track? "Opera's record growth shows that we are on the right track, and that as user needs grow, we are growing right along with them," said Lars Boilesen, CEO, Opera Software. "Opera for Desktop delivers the fastest browsing experience on the planet, with a visionary approach to features and a user-friendly design." Opera's total percentage of the global browser market remains small, although its place in the top six browsers means that it gets a prized place on the first ballot screen from Microsoft. The company's strong mobile presence and, of course, deals with the likes of Nintendo where Opera is used as the browser on the Wii console, certainly help the company's profile. http://www.techradar.com/news/softwa...n-users-682824  Web Browser that Bypasses Big Brother a Kazakh Hit Olzhas Auyezov A browser that bypasses censors has become the most popular way to access the Internet in Kazakhstan, a Central Asian state where sites critical of the government are often blocked, a Web statistics firm said. The Norwegian developed Opera browser made by Opera Software has increased its market share sharply in the ex-Soviet state since it began to allow downloads of compressed web pages via a server outside the country -- a feature designed to speed browsing. The Opera browser is now the most popular in the country with a market share of 32 percent, beating out rival products from Google, Microsoft and Apple, according to statistics for March from Web analytics firm StatCounter. The browser has increased its popularity by 60 percent in the past year alone, Opera Software said. Kazakhstan introduced a law last year allowing local courts to block access to Web sites whose content has been deemed "illegal," a step that human rights groups say amounts to censorship. Some of the most popular blogging websites such as Livejournal.com and Google-run Blogger.com are now inaccessible to most of Kazakhstan's 3.2 million Internet users. Both Livejournal.com and Blogger.com host blogs run by opponents of Nursultan Nazarbayev, Kazakhstan's leader for 20 years who wields sweeping powers and is never criticized by domestic mainstream media. However, the new edition of Opera introduced last year, Opera 10, allows users to view otherwise inaccessible Web pages using its Opera Turbo feature designed to speed up browsing over slow connections. Kazakhstan ranked among the world's top 10 countries by the number of Opera Turbo users in January, according to a report by Opera Software. The Norwegian software developer, however, does not advertise the "anti-censorship" feature of its product or see it as its key to success in Kazakhstan. "We link such growth to the release of several new versions of Opera 10.x within the last year that perform significantly better than our earlier products," Opera Software spokesman Vladimir Isayev said in an email. "As for accessing blocked resources -- we do not comment on that." (Editing by Paul Casciato) http://www.reuters.com/article/idUSTRE63C37N20100413  Approved! Opera Has Made It Into The App Store Brad McCarty Approved! Opera Has Made It Into The App StoreOpera just announced that their popular Mini mobile browser is now finally available for the iPhone and iPod Touch. Opera has been tearing up the mobile browsing market, with more than 50 million users at present, and millions more now sure to come. Lars Boilesen, CEO of Opera Software is quoted as saying “”We are delighted to offer iPhone and iPod touch users a great browsing experience with the Opera Mini App”. For those of you pinching pennies, or on a data package that isn’t unlimited, you’ll be pleased to know that Opera uses compression methods that allow you to view a full website, yet download noticeably less data. This also serves as great information for those unlucky enough to be stuck on AT&T’s Edge connection, which is notoriously slow with large data transmissions. So get to the App Store, grab the free Opera Mini (it will be available in the next 24 hours) and let us know what you think of it. We expect to see some great comments about this! http://thenextweb.com/mobile/2010/04...ini-app-store/  Browser Speed Tests: iPhone's Mobile Safari vs. Opera Mini Browser Speed Tests: iPhone's Mobile Safari vs. Opera MiniThis morning Apple surprised everyone by approving the Opera Mini web browser for the iPhone and iPod touch, bringing one of the most popular mobile browsers to the most popular smartphone. So how does it stack up? First of all, it's worth pointing out that Opera Mini has one big roadblock for iPhone and iPod touch users: Apple doesn't allow you to set any other application as the default for web browsing, so if you're opening links from other applications, like Mail, you'll still launch Mobile Safari when you click that link. (To use Opera Mini, you'd have to copy the link, close Mail, open Opera Mini, and paste the link.) That's a pretty big hurdle, but it's not the end of the world, especially since more and more apps display links in-app unless you explicitly choose to open a link in Safari. All that aside, you probably still open Safari directly when you want to do a lot of basic web browsing, so nothing's standing in the way of just launching Opera Mini in those instances instead. So let's talk speed and performance. I don't have all the same options for testing these as we have when we do our normal browser performance tests (most notably, memory use is missing, but since multitasking isn't on the iPhone yet anyway, that doesn't much matter), but we'll try to tackle as many of the same tests as we can. (Also like our other performance tests, these aren't exactly scientific, but we do follow our own set of guidelines to get as accurate of results as we can on limited equipment. For these tests, I'm using my iPhone 3G.) • Browser Boot Up/Load Time; Split Decision... Probably Mobile Safari This is a little bit of a tricky category. What I found when pitting the two against each other in launch time is that, while the Mobile Safari took significantly longer to launch from a cold start—that is, after having rebooted my iPhone entirely—it apparently resides in the iPhone's system memory from that point forward, meaning subsequent launches are nearly instantaneous. Opera, on the other hand, had a better cold startup time, but it doesn't have the benefit of sitting in the system memory, so every launch for Opera Mini is a "cold" launch. Browser Speed Tests: iPhone's Mobile Safari vs. Opera Mini • Page Load Time; Winner: Opera Mini To measure page load times, I timed five or so page loads on several popular sites over Wi-Fi, threw out the highest and lowest for each site, and then averaged them all out. In this category, Opera Mini absolutely pummeled Mobile Safari, especially on full versions of web sites like the New York Times front page (which partially rendered in Mobile Safari before it finished loading, but continued loading for over 40 seconds time and again). Browser Speed Tests: iPhone's Mobile Safari vs. Opera Mini • JavaScript, DOM, CSS Speed; Winner: Mobile Safari We used Mozilla's very cool Dramaeo browser performance testing tool to pit Mobile Safari's JavaScript, DOM, and CSS chops against Opera Mini's. Unfortunately, we learned pretty quickly that, while Mobile Safari slowly chugged through the test (slowly compared to desktop browsers, that is), Opera Mini failed to run with any of them. That's not necessarily a huge black mark against the speed of Opera Mini, per se, since we couldn't actually pit the two against each other, but it speaks pretty loudly about which browser is currently capable of offering a more desktop-like experience, and that's Mobile Safari. Keep in mind that we're not saying that a more desktop-like experience is necessarily preferable; you're on a mobile device, after all, and that desktop performance does seem to come with some trade-offs—like the page load times mentioned above. Takeaway It's pretty clear that, while Opera Mini features seriously impressive page load times, it's still behind Mobile Safari on several levels—some of its disadvantages are due to Safari's advantaged position as the system default, some of them probably have more to do with the youth of Opera Mini on the iPhone platform. You will, however, notice the considerably faster page loads when you're using Opera Mini, and with the web, speed is everything. If Opera could keep the speed and fix some of the rough edges, it could be really impressive. Speed aside, use Opera Mini for a while and you'll quickly miss the smooth zooming of Mobile Safari and the nice font rendering. (When you're looking at a desktop version of a site zoomed all the way out on Opera Mini, the type renders as big blocks of color and is generally unreadable.) Still, I'm holding out hope for Opera Mini. The speedy page loads alone make it an ideal browser for a quick lookup, and its tabbed browsing interface is, in my opinion, superior to Mobile Safari's. http://lifehacker.com/5516038/browse...-vs-opera-mini  Opera Says 1 Million Downloads of iPhone Browser Day 1 Opera Software's Internet browser for Apple's iPhone was downloaded more than one million times during the first day when it was available to consumers, the Norwegian firm said on Thursday. On April 13 Apple accepted distribution of Opera's browser for its iPhone after a long review, opening a new and potentially lucrative market it has so far closely guarded. "Apple said 'Yes', and iPhone users around the world said, 'Yes, please'," Opera said in a statement. Opera's browser promises up to six times faster download speeds than Apple's own browser, and to cut data traffic by up to 90 percent. Massive data traffic from iPhone mobile phones has caused problems for many operators' networks. (Reporting by Tarmo Virki) http://www.reuters.com/article/idUSTRE63E1T920100415  Apple Places New Limits on App Developers Jenna Wortham Apple is tightening its already firm grip on what software can run on the iPhone and its other mobile devices, as shown by its recent changes to the rules that outside programmers must follow. The company is locked in a battle with other cellphone makers, particularly those using Google’s Android operating system, for the latest and best applications that add functions to a phone. The new rules, released last week, say in part that app developers may only use Apple’s programming tools. That is a problem for Adobe Systems, which announced a new package of tools on Monday that were meant to let developers create apps once and then automatically generate versions for the iPhone and other companies’ devices. Developers will also no longer be permitted to use outside services to measure how their applications are performing. The company says it will refuse to distribute any apps in the iTunes store that violate the new agreement. “Apple is doing everything to encourage app development, as long as it’s on their platform,” said Gene Munster, an analyst with Piper Jaffray. “The risk Apple runs is ticking off developers and causing them to want to develop on other platforms,” he said. But until competing mobile platforms gain more traction, he said, “there’s no other place for developers to go, so Apple can call the terms however they want.” The changes leave many start-ups and apps developers in limbo, waiting to find out whether their businesses, many of which have built a substantial clientele and taken money from venture capitalists, can still operate under the new rules. “The truth is that right now, we don’t know a lot,” said Peter Farago, vice president of Flurry, an analytics company with offices in New York and San Francisco. “We have a list of questions.” Flurry’s software tracks how smartphone applications are used. It has become a popular tool among developers, who have access to details like how long it takes to complete a game or to finish reading a chapter of an electronic book. Mr. Farago said his company had asked Apple for clarification, but had not heard back. “We think we can be compliant by doing some modifications,” he said. “We’ll do what we need to do to get that to happen.” Even so, the company is aware that it may have to rethink its business model, Mr. Farago said. Henry Balanon, lead developer at an iPhone development company called BickBot, said he had no immediate plans to remove Flurry’s software from his applications. “We’d have to roll our own analytics into the software, which is just a pain,” Mr. Balanon said. “But if we start getting rejections because of the analytics, we may have to reconsider.” Industry experts like Al Hilwa, an analyst with the research firm IDC, say that Apple is tightening its grip on applications in an attempt to keep rivals at bay. “There will be a big fistfight for developers and applications over the next few years,” he said. “This is just the early stages of the battle for mobile telephony. Apple’s financial radar is up, and they are trying to close all the holes.” Mr. Munster, the Piper Jaffray analyst, said that the broader shift in Apple’s core revenue streams, to mobile from desktop computing, was a chief reason for the company to pressure developers. “It’s not about making money on the apps,” he said. “It’s about making money off the hardware.” Mobile devices with more apps, he said, are more attractive to buyers. By the end of 2011, Mr. Munster said, nearly 50 percent of Apple’s total revenue will come from sales of the iPhone and iPod Touch. In 2001, 80 percent of Apple’s revenue was from its line of Mac laptops and desktop computers. That figure will slip to about 27 percent in 2011, he said. Apple did not respond to requests for comment. But an iPhone developer named Greg Slepak sent an e-mail message to Apple’s chief executive, Steven P. Jobs, saying that the new rules were “limiting creativity.” “We’ve been there before,” Mr. Jobs wrote in reply. “Intermediate layers between the platform and the developer ultimately produces substandard apps and hinders the progress of the platform.” The prohibition on the use of non-Apple programming tools prompted a sharp response from an Adobe employee. Lee Brimelow, an Adobe evangelist, wrote on his blog last week: “This is a frightening move that has no rational defense other than wanting tyrannical control over developers and more importantly, wanting to use developers as pawns in their crusade against Adobe.” http://www.nytimes.com/2010/04/13/te...s/13apple.html  Mark Fiore Can Win a Pulitzer Prize, but he Can’t Get His iPhone Cartoon App Past Apple’s Satire Police Laura McGann This week cartoonist Mark Fiore made Internet and journalism history as the first online-only journalist to win a Pulitzer Prize. Fiore took home the editorial cartooning prize for animations he created for SFGate, the website for the San Francisco Chronicle. I spoke with Fiore about his big win and plans for his business. Fiore is not on staff at the Chronicle, or anywhere else; since 1999, he’s run a syndication business, selling his Flash animations à la carte to TV, newspaper, and magazine websites for about $300 a piece. (The price varies by size of the outlet.) In a typical month, he might have about eight clients. Before 1999, he ran a similar syndication business for his print cartoons, using a lower-price-per-image, higher-volume model. When I asked about the next phase of his business, curious if it will include a mobile element, Fiore said he’s definitely hopeful about mobile devices. “I think the iPads and anything iPod to iPhone — to maybe a product not made by Apple — will be good or could be good for distributing this kind of thing,” he said. But there’s just one problem. In December, Apple rejected his iPhone app, NewsToons, because, as Apple put it, his satire “ridicules public figures,” a violation of the iPhone Developer Program License Agreement, which bars any apps whose content in “Apple’s reasonable judgement may be found objectionable, for example, materials that may be considered obscene, pornographic, or defamatory.” Here’s the email Fiore received from Apple on December 21, 2009: Quote:
Fiore isn’t the first editorial cartoonist to clash with Apple. Last year, an app called Bobble Rep app, which used political caricatures by Tom Richmond, was initially rejected by Apple. After an online uproar, a few days later Apple changed its position, allowing the app into the store. (Fiore’s rejection landed in his inbox just a month later.) Daryl Cagle, who runs a cartoon syndication site with 900 newspaper subscribers, had a similar battle with Apple last year, waiting around for months before eventually being allowed in. And while Apple eventually ruled in those cartoonists’ favor, the company went on an app-banning spree in February targeting apps with bikini-level sexual content. (Although a few established news brands like Sports Illustrated were allowed to remain.) It’s also an example of the alarm bells some critics of the app store system were sounding in the lead-up to the release of the iPad. Brian Chen at Wired warned publishers to consider questions of independence, in light of a controversy over Apple’s vague policy on sexual content. And several German news orgs like Bild and Stern have already seen Apple get into the business of banning certain editorial content from the App Store. Fiore has not resubmitted his app, saying he’d heard about the experiences of others cartoonists and wasn’t in a position to get into a fight with Apple. Still, he has a hunch Apple will eventually change its mind on him, as it has with other cartoon apps. “They seem so much more innovative and smarter than that,” he told me. Apple did not respond to my request for comment on its satire policy, or Fiore’s case in particular. http://www.niemanlab.org/2010/04/mar...satire-police/  Beware at Customs: Gov't has Banned iPad Imports Bar Ben Ari and Zohar Blumenkrantz If you had thought to buy Apple's new iPad tablet computer any time soon and bring it to Israel, you may have to change your plans: Starting yesterday, the Communications Ministry has blocked the import of iPads to Israel, and the customs authority has been directed to confiscate them. The decision follows the refusal of the ministry's engineering staff to compromise on testing the device's suitability and compliance with Israeli wireless networks. It seems however that the engineers made their decision without notifying Communications Minister Moshe Kahlon in advance - and caused an uproar within the ministry. For now, the ministry has not given the device categorical approval required for wireless devices; and ministry officials say its wireless technology is not compatible with Israeli standards. "The iPad device sold exclusively today in the United States operates at broadcast power levels [over its WiFi modem] compatible with American standards," explained the officials. "As the Israeli regulations in the area of WiFi are similar to European standards, which are different from American standards, which permit broadcasting at lower power, therefore the broadcast levels of the device prevent approving its use in Israel," said the officials. The ministry has requested all the relevant information on the iPad from Apple's Israeli distributor, iDigital, so as to approve importing iPads. An Israeli who returned from the U.S. yesterday told TheMarker that when he tried to declare his new iPad at customs, it was confiscated. He was told to apply to the Communications Ministry to have it returned. When he spoke to the ministry, he was told: "It is forbidden to bring iPads into Israel; send it back overseas." In the meantime, he says the device is in a customs warehouse, and he is being charged for every day it remains there. The head of customs at Ben-Gurion International Airport said yesterday they have confiscated 10 iPads, including those their owners declared and on which they offered to pay the 16% VAT required by law. http://www.haaretz.com/hasen/spages/1162992.html  Please Do Not Change Your Password You were right: It’s a waste of your time. A study says much computer security advice is not worth following. Mark Pothier To continue reading this story, enter your password now. If you do not have a password, please create one. It must contain a minimum of eight characters, including upper- and lower-case letters and one number. This is for your own good. Nonsense, of course, but it helps illustrate a point: You will need a computer password today, maybe a half dozen or more — those secret sign-ins that serve as sentries for everything from Amazon shopping carts to work files to online bank accounts. Just when you have them all sorted out, along comes another “urgent” directive from the bank or IT department — time to reset those codes, for safety’s sake. And the latest lineup of log-ins you’ve concocted won’t last for long, either. Some might temporarily stay in your head, others are jotted on scraps of paper and stuffed in a wallet. A few might be taped to your computer monitor in plain view (or are those are from last year’s batch? Who can remember?). Now, a study has concluded what lots of us have long suspected: Many of these irritating security measures are a waste of time. The study, by a top researcher at Microsoft, found that instructions intended to spare us from costly computer attacks often exact a much steeper price in the form of user effort and time expended. “Most security advice simply offers a poor cost-benefit trade-off to users,” wrote its author, Cormac Herley, a principal researcher for Microsoft Research. Particularly dubious are the standard rules for creating and protecting website passwords, Herley found. For example, users are admonished to change passwords regularly, but redoing them is not an effective preventive step against online infiltration unless the cyber attacker (or evil colleague) who steals your sign-in sequence waits to employ it until after you’ve switched to a new one, Herley wrote. That’s about as likely as a crook lifting a house key and then waiting until the lock is changed before sticking it in the door. Herley also looked at the validity of other advice for blocking security threats, including ways to recognize phishing e-mails (phony messages aimed at getting recipients to give up personal information such as credit card numbers) and how to deal with certificate errors, those impossible-to-fathom warning messages. As with passwords, the benefits of these procedures are usually outweighed by what users must do to carry them out, he said. It’s not that Herley believes we should give up on protecting our computers from being hijacked or corrupted simply because safety measures consume time. The problem, he said, is that users are being asked to take too many steps, and more are constantly being added as new threats emerge or evolve. Security professionals have generally assumed that users can’t have too much knowledge in the battle against cyber crime. But that fails to take into account a crucial part of the equation, according to Herley: the worth of users’ time. “A lot of advice makes sense only if we think user time has no value,” he said. The study was first presented by Herley at a security workshop at Oxford University last fall, and began generating wider discussion last month after an essay about it appeared on TechRepublic, a popular technology website. In the paper, Herley describes an admittedly crude economic analysis to determine the value of user time. He calculated that if the approximately 200 million US adults who go online earned twice the minimum wage, a minute of their time each day equals about $16 billion a year. Therefore, for any security measure to be justified, each minute users are asked to spend on it daily should reduce the harm they are exposed to by $16 billion annually. It’s a high hurdle to clear. Herley’s paper gives “normal users a voice,” said Michael P. Kassner, a technology writer and IT veteran who wrote the TechRepublic piece. For too long, users have been asked to follow security instructions without being told why they are worth the time investment. “I’ve been a proponent of prioritizing” security measures, Kassner said. “The whole purpose of IT is to make people’s lives easier.” The computer security community has long puzzled over why so many users fail to snap to attention when alerted to news about the latest threats, such as viruses, worms, Trojan horses, malware, and spyware. At countless conferences and seminars, experts have consistently called for more education and outreach as the answer to user apathy or ignorance. But the research of Herley and others is causing many to realize most of the blame for noncompliance rests not with users, but with the experts themselves — the pros aren’t able to make a strong case for all their recommendations. Some advice is excellent, of course. But instead of working to prioritize what efforts are effective, government and security industry officials have resorted to dramatic boldface statements about the horrors of poor passwords and other safety lapses, overwhelming the public. For instance, the federal government’s website for computer safety tips, www.us-cert.gov, includes more than 50 categories under the heading of “Cyber Security Tips.” Each category leads to complex sets of instructions. “It’s nice to see the industry starting to grapple with these issues,” said Bruce Schneier, the author of “Secrets and Lies,” a book about computer and network security. In a blog posting last year, Schneier recalled a security conference at which a speaker was baffled by the failure of workers at his company to adhere to strict computer policies. Schneier speculated that the employees knew following those policies would cut into their work time. They understood better than the IT department that the risks of not completing their assignments far outweighed any unspecified consequences of ignoring a security rule or three. “People do what makes sense and don’t do what doesn’t,” he said. To prompt them to be more rigorous about computer protection, he said, “You want actual studies, actual data.” That poses a challenge for the security industry, Herley said. While doctors can cite statistics showing smoking causes cancer, and road-safety engineers can produce miles of numbers supporting seat belt use, computer security professionals lack such compelling evidence to give their advice clout. “Unbelievable though it might seem, we don’t have data on most of the attacks we talk about,” he said. “That’s precisely why we’re in this ‘do it all’ approach.” His paper argues for advice that incorporates more information, and less hyperbole. Security professionals need to consider that user education costs everyone (in time), but benefits only the small percentage who are actually victimized, he wrote. Advice must be based on an estimate of the victimization rate for a particular security issue, not a worst-case scenario risk analysis. It’s a start to quantify in a rough way the value of user time, he said, but more study is required. The central question that remains to be answered: Given all the threats, what steps produce results that outweigh the price for society at large? Costs can come in unexpected ways, he suggests. One example he studied was phishing. Banks and other investment companies often guarantee to reimburse customers if unauthorized withdrawals are made from their online accounts, so the customer does not pay a direct price. The banks face losses, but they are relatively modest — the annual cost nationwide as a result of phishing attacks is $60 million, Herley estimated. By instructing users to take measures against them (such as by scouring URLs to make sure they lead to legitimate websites), “we’re imposing a cost that is orders of magnitude greater than the problem it addresses,” he said. For banks, the greater potential for damages comes not from a phishing attack itself, but indirect expenses. Herley used Wells Fargo as an example. He wrote that if a mere 10 percent of its 48 million customers needed the assistance of a company agent to reset their passwords — at about $10 per reset — it would cost $48 million, far surpassing Wells Fargo’s share of the $60 million in collective losses. No one is saying computer security threats are not a serious matter. Attacks multiply daily and are becoming more effective, having risen far beyond the sophistication level of the Nigerian prince looking to unload $12 million. Check your in-box — within the last few hours a criminal probably sent you an invitation to be victimized. Herley’s paper cites a report that said an unprotected PC will be invaded within 12 minutes of being connected to the Internet, on average. And last month, Justice Department Inspector General Glenn A. Fine warned the government isn’t keeping pace with cyber crooks in its efforts to combat the fastest-growing crime in the United States — identity theft. About 10 million Americans are affected each year. With all that scary stuff in mind, it is easy to appreciate the sincerity of those pushing us to be more vigilant, even if their methods are muddled. So which security measures offer a reasonable return on time and effort? Although coming up with a sensible list of security actions was not a goal of Herley’s research, he does have some suggestions based on personal experience. Start with bullet-proof passwords, he said, even if your employer requires you to periodically reinvent them or use too many (he juggles about three dozen as part of his work). Beyond that, he is big on one-time measures that offer ongoing benefits, like installing the latest software to shield against viruses and spyware (set it to automatically update). Two-thirds of computers have outdated software protection, according to a Microsoft spokesman. The company also recommends activating a firewall, which “functions like a moat around a castle.” Combined, such measures shouldn’t take more than 30 minutes, it said, and offer insulation from what is perhaps the biggest security menace of all: users. “One of the main ways people get compromised is that they open the door to an attacker themselves,” said Herley. Someone might load software promoted as offering protection when it is actually spyware in disguise, he said, or they “open an e-mail attachment with a malicious payload....If this happens, it can be very bad. A piece of malicious keylogging software on your machine can grab all of your passwords: It makes no difference at that point whether they are strong or weak.” After all this trash talk about security, you might wonder what Microsoft chief executive Steve Ballmer thinks about one of his key researchers challenging much of the advice the industry giant dispenses like gospel. Herley insists there has not been any blowback. Microsoft encourages its researchers to “push against fixed beliefs, even when some of the ideas can be controversial,” he said. And from outside Redmond, Wash., he added, “the reaction has been tremendous.” “Maybe I’m just saying out loud what is rather obvious — we seem to be causing lots of unnecessary misery.” http://www.boston.com/bostonglobe/id...your_password/  OCZ Combines Monstrous Capacity with a Monstrous Pricetag for New SSDs John Gillooly The revamped Colossus LT series Solid State Drives come in capacities up to 1TB. Unfortunately it comes with the price tag 400 times that of a 1TB hard disk Over recent years Solid State Drives (SSDs) have moved from luxury to affordable additions to one's PC. The cost of an SSD depends largely upon the capacity of the drive, which has meant that mechanical hard drives still dominate when it comes to storage, with SSDs more suited to storing one's operating system and frequently used applications. For example, a 128GB SSD will set you back $300-$400 depending on manufacturer. For the same amount of cash you can get a four or five Terrabytes worth of normal hard drive space. Because of this huge disparity we don't usually see massive capacities quoted for SSDs. While a 128GB SSD might be ample storage for a netbook, it is a fraction of what one expects on a desktop PC. This is changing with the overnight announcement of the OCZ Colossus LT series of drives. This is an update to a product line that eschews the sleek 2.5in stylings commonly used for SSDs. Instead use the more common desktop 3.5in form factor. OCZ takes advantage of this extra physical size to pack more memory in, with 128GB, 256GB, 500GB and 1TB models. While 1TB of SSD space hits right at the heart of the traditional hard disk market, it comes at a high price. Despite the fact that the new models bring MLC NAND flash to bear, the new drives still sit at the extreme luxury end of the PC hardware spectrum. 1TB models will set the end user back around $US4000. Which keeps these drives in the realm of aspirational rather than practical. http://www.pcauthority.com.au/News/1...-new-ssds.aspx  The Pirate Party of Canada Is Official Wasme The Pirate Party of Canada has become the first Pirate Party outside of Europe to become an official political party. Elections Canada confirmed with the party that the PPCA has gained "eligible for registration" status, and can run in elections starting June 14. From the PPCA's official announcement: "We are pleased to announce that as of April 12, 2010, the Pirate Party of Canada is officially eligible for Party Status. After 10 months of dedication and hard work, we have reached eligible status, which only leaves a 60-day 'purgatory' period. After that, we will field candidates in subsequent federal elections, and begin the real work of a political party." http://politics.slashdot.org/story/1...da-Is-Official  The Amazing Media Habits Of 8-18 Year Olds Kids are leading the world's transition to digital media. This is in part because kids aren't afraid of technology, and, in part, because kids haven't spent years getting use to anything else. So if you want to get a sense of where the world's media habits are headed, it makes sense to watch what kids are doing. The Kaiser Family Foundation did just that in a comprehensive survey released in January. Kaiser surveyed more than 2,000 families, and turned up all sorts of interesting information about the media habits of 8-18 year olds. Some key points: * Kids consume a hell of a lot of media--and more all the time. Basically, if kids are awake, they're consuming media. And, increasingly, they're consuming multiple forms of media at the same time. * Kids' print media consumption is tiny and falling. * Kids' digital media consumption is going through the roof. No big surprise there. What is a surprise is how little parents seem to care about this. (Or, alternatively, how much parents encourage this media consumption by consuming a huge amount of media themselves.) * In 2/3 of households, TVs are on during meals * In 75% of households, TVs are on when no one is watching them. * More than 70% of kids have TVs in their bedrooms * Only 1/3 of households have media-consumption rules No surprise, more media is consumed in households in which TVs are always on, where there are no rules, and where kids have TVs in their bedrooms. And, no surprise, kids who consume the most media get the worst grades (is this cause or effect?) It's a long presentation, but it's awesome. Flip through the presentation here > http://www.businessinsider.com/media...8-18-year-olds  Facebook: Home to Wanna Be Porn Stars Mary Kelly I went to a professional conference. They said I needed to get a Facebook account. So I did. I started getting “friends”. Then my children added me as friends. This was good. The best thing about Facebook is the pictures loved ones and friends can exchange. The birth of a baby, an anniversary celebrated, a vacation earned. Shortly, my children’s friends started adding me as friends. I thought this a little odd. I mean, why would they want their friends’ parents looking at their updates? I mean…isn’t a little separation, a little unfamiliarity between generations a good thing? I’m an open person. Fine…they want me as a friend, they’ve got me as a friend. I wish I wasn’t their friend. My big question is this: WHY ARE ALL THESE YOUNG WOMEN PRETENDING TO BE PORN STARS? Seriously! I can’t take this anymore. I don’t get it. I don’t want to get it. This “wanna be a slut look” starts in middle school and apparently continues well into the 20’s. You know what I’m talking about. And these girls have HUNDREDS of pictures of themselves and others in these degrading poses. Picture after picture of girls at parties, girls drinking, girls looking at the camera with the “pursed up lips” (this is so not a good look), girls grabbing other girl’s breasts, girls drinking out of beer bongs and…the V SIGN. The V SIGN is everywhere. Someone enlighten me about the V SIGN. Is this a generational thing or what? I’m pretty sure I know what the V SIGN is, pretty sure, but WHY? Is vulgar the new sexy? Is crude and exhibitionist the new normal? Is objectification the new feminism? Jane Fonda and Gloria Steinem are rolling over in their graves and they’re not even dead. AND THE TONGUES. What’s with the tongues? Everywhere the tongues. And the smiles. These girls are perpetually ecstatic. Pictures of special note are the ones where the girls are lap dancing for adolescent pimply-faced boys. Or they are bumping and grinding up against them. The boys look awkward but happy. The girls look desperate. Do they at least get paid for this? My .02: Leave the porn to the professionals. You girls are way in over your heads. I wonder about these girls and how they are going to feel about all these pictures that are now circulating the Internet for all eternity. How are they going to feel when they actually grow up and raise the bar of expectation for themselves? When they realize that someday their daughter may ask them, “Mom, what were you doing in those pictures? Gross Mom!” It’s all disturbing but especially disturbing are the pictures of the pre-16 year olds. We’re worried as we all should be with the economy and the drop of the stock market. But what about the drop in expectations and core values? Where are all the mothers who burned their bras in protest to the sexualization and objectification of women? Are they not scratching their heads when they see their daughters burning their bras for the pure titillation value to attract the attention of young men? Is this the only way they can rebel against parents who were part of free love, sex, drugs and rock and roll? Call me a prude if you must. Mothers and Fathers: Deprogram your sons and daughters. Stop buying your 10-year-old daughter a padded bra (yes, Limited Express sells them). Stop letting them see every reality show that normalizes lewd behavior. Tell them they have a brain that is going to serve them much more in the long run than their breasts. And take their frigging computers and cell phones away from them until they can behave like a lady. A what? Look it up in the dictionary. I hope it’s still there. http://open.salon.com/blog/marytkell..._be_porn_stars  Getting Off on Facebook Amanda Marcotte For reasons of bet-settling, I recently found myself on a bender of asking male friends a simple question: How many straight men do they believe look at porn on a regular basis? Most of the answers fell right into the 99-to-100 percent zone, but one friend startled me by saying, “At least 60 percent,” a number I found to be a tad low. He quickly clarified his position by noting that it would be 100 percent if many men, at least some of the time, weren’t logging onto Facebook instead of seeking out a porn site. “On Facebook you can stare as long as you want to—nobody's going to get mad because it's not them, it's just a picture.” But my friend told me guys aren’t looking for dirty pictures on Facebook, they’re looking at ordinary pictures of women, the kind that you and I associate with Facebook. Women partying with friends. Women goofing off in the park. Women sitting at home trying on a pose that’s serious and deep. At worst, they’re looking at women in Facebook-approved sexy poses, or pictures from the beach. “I think the theory is that the women on Facebook are, if nothing else, real,” he explained, “and often people that you might have a real-life attraction to.” Statistically speaking, many men do appear to be using Facebook to look at women. Seventy percent of activity on social networking sites is people looking at pictures. Two thirds of pictures looked at are of women, and the single most common activity on Facebook is men looking at pictures of women. Facebook did not return a call querying about men using the social networking site to jump-start their fantasizing. The researcher Mikolaj Jan Piskorski, who discovered all this, suggested men in relationships might be weighing their options. But another explanation is that they're just fantasizing about an acquaintance. “Most [women I look at on Facebook] I have some history of at least fooling around with, but never going all the way,” one man told me. Another man, age 41, saw it in a slightly different light. He noted that he would love to stare at sexy women on the street, especially if they’re showing a lot of cleavage, but that he refrains out of respect. “But on Facebook,” he says, “you can stare as long as you want to—nobody's going to get mad because it's not them, it's just a picture.” He adds, noting that his interest goes beyond the platonic: "I can print out, bookmark and/or download the images I see on Facebook to look at again and again and again.” It’s the G-rated version of another trend that’s already causing those who make money off porn to sweat: the explosion of amateur porn sites on which people post videos of themselves in sexual situations for the sheer thrill of it. FoxyTube, YouPorn, and XTube are filled with such videos; the idea that the women in them are “real” draws tons of traffic. As one man told me, “Everyone involved is having a genuine sexual experience, and what's hotter than that?” Sex educator Heather Corinna, founder of the popular website Scarleteen, pointed out that none of this should be surprising. "I'd say that's pretty common behavior that happens inside people's heads all the time. It’s just that not everyone always has digital imagery to utilize as part and parcel of that." On one hand, it’s hard not to feel optimistic if so many men are having fantasies about “real” women. Many straight women are plagued by the fear that the endless supply of photographed sex objects offered to men as fantasy fodder means guys are losing their taste for boring, everyday women with imperfect human bodies. In The Washington Post, Pamela Paul suggested that the stream of porn men expose themselves to may ruin them for sex with their own wives and girlfriends. She worried that real sex might be a letdown after countless hours of looking at porn. The men I talked to, though, said they felt increasingly dissatisfied with porn. One man, age 29, said, “Porn seems impersonal and gross,” while looking at pictures of women on Facebook feels “semi-enlightened, in a way.” On the other hand, there’s an undeniable ick factor to the idea of men getting off to pictures you posted for your friends to platonically peruse. No one wants to think of their male friends (or worse, their coworkers or bosses) projecting them into sex fantasies. Complicating matters, Facebook is rife with pictures of very young women experimenting with ribaldry, probably unaware of how those pictures might be read by men. But outside of concerns about older men ogling pictures of underage women, it seems that women with Facebook profiles would do well to believe that what we don’t know about our male friends’ Facebook habits won’t kill us. Still, you could be forgiven for combing over your Facebook pictures to delete any that might seem a little provocative. http://www.thedailybeast.com/blogs-a...rn-stash/full/  Facebook Announces New Safety Measures but no Panic Button The social networking site will introduce a 24-hour police hotline, awareness campaign and a new system of reporting abuse Jemima Kiss Child safety charities, anti-bullying groups and political parties have all called for the addition of a 'panic button'. Photograph: Dominic Lipinski/PA Facebook has responded to calls for increased online safety by announcing a range of new measures including a 24-hour police hotline, a £5m education and awareness campaign and a redesigned abuse reporting system, but has declined to add a logo linking to the Child Exploitation and Online Protection Centre. The site is also calling for the government to introduce ways of sharing strategic data on offenders with other social networking sites, following a similar initiative in the US. Facebook came under renewed scrutiny last month after the conviction of the serial rapist Peter Chapman, who posed as a young boy on the site and later murdered 17-year-old Ashleigh Hall. "The investments and partnerships we've announced today will transform social networking safety and security," said Elliot Schrage, vice-president of global communications and public policy at Facebook. "They represent the most comprehensive public/private safety initiative since social networking began in the UK almost a decade ago." Child safety charities, anti-bullying groups and political parties have called for Facebook to introduce a so-called 'panic button' to the site, but Facebook has resisted. A spokesperson said the company had looked closely at safety solutions on other sites and concluded that a single reporting button would be less effective for users, and also create an overload of work for the police and the Child Exploitation and Online Protection Centre (Ceop). Facebook's existing reporting procedure handles around 10,000 requests in the UK alone that include password requests and problems with profile pictures, as well as more serious problems. Instead of a single contact button or Ceop logo, Facebook has developed a reporting procedure accessible from the bottom of every profile, which asks the user to block a contact for nudity, racism, bullying or unwanted contact. "We are testing and we are open to ideas, refinements and improvements, but we fundamentally feel that ours is the right approach. No other sites have one 'panic button' and we would not be doing our job properly if we added one button that sent all reports to Ceop," said the spokesperson. "We know about web design and Ceop knows about child protection. We want to marry those skills – not argue about web design. We have some of the best engineers in the world creating for our platform." Facebook, which has 23 million users in the UK, is also dedicating £5m of advertising space for safety campaigns. Ads by charities including the NSPCC, Beatbullying and the Family Online Safety Institute will be displayed to all Facebook users, the site said, aiming to raise awareness of online safety not just to younger users but to parents and other users. Ceop's chief executive, Jim Gamble, last week criticised Facebook for failing to "understand prevention or deterrence", but after extensive talks with the firm in Washington he said the new initiative was "one small step from doing the right thing" and is still insisting on a single, Ceop-branded button. "There is no doubt they are looking to improve their position around child safety and we recognise that. What I am looking for is turning words into action," said Gamble. "In our view they are experts at creating a fantastic online environment but they are not experts in law enforcement, the power of deterrents and the reassurance it brings for mums and dads." Gamble also claimed Facebook had not passed on any reports directly to Ceop, though the firm claimed this was down to US legal restrictions. MySpace includes a "report abuse" link at the bottom of every profile, which links to an email contact form where users can detail cyberbullying, phishing, inappropriate content or a page that mentions suicide. Every Bebo profile has a similar link, which asks users to chose between reporting site abuses such as hacking or explicit content to Bebo, or to send reports to Ceop. http://www.guardian.co.uk/technology...acebook-safety  Wikifounder Reports Wikiparent to FBI Over 'Child Porn' 'Something I helped start has come to this' Cade Metz Wikipedia co-founder Larry Sanger has reported the site's parent organization to the Federal Bureau of Investigation, saying he believes the Wikimedia Commons "may be knowingly distributing child pornography." Earlier this week, Sanger disclosed his FBI report with a post to a public mailing list and later an open letter to a member of the Wikimedia Foundation's board of trustees. In the letter, he also says he notified his Senators and Congressional representatives over the images in question. Sanger - who parted ways with Wikipedia in 2002 over what he calls "disagreements about editorial and management policy" - tells The Reg that he filed his report through the FBI's website. "I believe Wikimedia Commons (http://commons.wikimedia.org/), owned and hosted by the California-based Wikimedia Foundation, may be knowingly distributing child pornography," reads his letter to the bureau and his Senators and representatives, before providing specific weblinks, one to a "pedophilia" category that includes a limited number of images. "I don't know if there is any more, but I wouldn't be surprised if there is - the content on the various Wikimedia projects, including Wikipedia and Wikimedia Commons and various others, are truly vast." Sanger goes on to say that that in his "non-lawyer's opinion," he believes that the images violate a US law against "obscene visual representations of the sexual abuse of children" (18 USC §1466A(2)(A)). Wikimedia general counsel Mike Godwin did not respond to a request for comment. But he dismisses Sanger's claims with a public post to the web. "As is commonly the case when non-lawyers attempt to invoke a statute without adequately researching the relevant law and legal categories, Sanger has confused and conflated a number of legal doctrines," Godwin begins, saying that 18 USC 1466A is not a child-pornography statute but an obscenity statute. He points to 18 USC 2252 and 2252A as the statutes covering child pornography. He also defends the Foundation's position by citing a court case, Miller v California, that he says emphasizes "the importance of community standards in defining what qualifies as obscenity." And yes, he points out that Wikimedia's projects are not built by the Foundation itself but by web users, citing section 230 of the Communications Decency Act. "Federal obscenity and child-pornography statutes make similar distinctions [to Section 230]," he says. "As Sanger seems to have forgotten, the Wikimedia Foundation does not originate or develop Wikipedia content or Wikimedia Commons content. This was true in Sanger's day as well as is in the present day." Whatever claims Godwin makes over "community standards" or section 230, federal law (18 USC 2258A) also says that if an electronic service provider is made aware of child pornography on its servers, it must report it to the CyberTipline operated by the National Center for Missing & Exploited Children (NCMEC). "The law doesn't mandate that they look for it or that they monitor for it, but if they become aware of it, they have to report it," Michelle Collins, the vice president of the organization's exploited children division, tells The Reg. Justin Fitzsimmons, a senior attorney with the National District Attorneys Association, tells The Reg that his reading of the statute is that it does apply to the Wikimedia Foundation. This is not the first time the Wikimedia Foundation has been accused of hosting child pornography. In May of 2008, an unfinished story on Wikimedia's own Wikinews project repeated a report that the FBI was investigating Wikipedia for hosting the image of a mid-1970s record album cover from German heavy metal band the Scorpions. But the story was removed and the image remained, and in December of that year, the image turned up on a blacklist maintained by the Internet Watch Foundation UK, which meant that access to the site was filtered by at least six British ISPs. In bizarre fashion, the filtering also resulted in Wikipedia admins banning large swaths of the United Kingdom from editing the site. The IWF later pulled Wikipedia from its blacklist, and the site continues to host the album cover. Famously, Larry Sanger founded Wikipedia in tandem with current site figurehead Jimmy "Jimbo" Wales - though, just as famously, Wales prefers to think of himself as the sole founder. While the pair were working on Nupedia, a Wikipedia predecessor, Sanger sent a seminal email to the project's staff. "Let's make a wiki," he wrote. "No, this is not an indecent proposal. It's an idea to add a little feature to Nupedia. Jimmy Wales thinks that many people might find the idea objectionable, but I think not." He now runs Citizendium.org, an online encyclopedia that does not allow anonymous editing and takes greater pains to avoid conflicts of interest, and WatchKnow.org, a teacher-edited non-profit directory of preK-12 educational videos. Sanger tells us he reported the Wikimedia Commons images to FBI reluctantly, but believes he ultimately did the right thing. "If I don't report this - and it's been up for years, apparently - who will? As the co-founder of the project, I believe I have a special personal obligation to rein in egregious wrongdoing when I see it. Or at least try," he says. "It bothers me that something I helped start has come to this." http://www.theregister.co.uk/2010/04...ia_to_the_fbi/  South Korean Children Face Gaming Curfew BBC The South Korean government is introducing policies aimed at curbing the amount of time children spend playing online games. The first involves barring online gaming access to young people of school age between 12am (midnight) and 8am. The other policy suggests slowing down people's internet connections after they have been logged on to certain games for a long period of time. The Culture Ministry is calling on games providers to implement the plans. It is asking the companies to monitor the national identity numbers of their players, which includes the age of the individual. Parents can also choose to be notified if their identity number is used online. "The policy provides a way for parents to supervise their children's game playing," Lee Young-ah from the Ministry of Culture, Sports and Tourism told Reuters. The Korea Herald reports that Barameui Nara, Maple Story and Mabinogi, three popular virtual worlds, will introduce the blackout later this year. Meanwhile role playing games "Dungeon and Fighter" and "Dragon Nest" will pilot the connection slowing scheme. A total of 19 role playing games will eventually be included - a huge proportion of the online gaming market in the country. South Korea has sophisticated high speed broadband connections and online gaming is enormously popular. But there has been growing concern over the amount of time its citizens spend in virtual worlds and playing online games. A couple whose baby daughter starved while they spent up to 12 hours a day in internet cafes raising a virtual child online have made headlines around the world. They were charged with negligent homicide and are due to be sentenced on 16 April. http://news.bbc.co.uk/2/hi/technology/8617372.stm Until next week, - js.  Current Week In Review  Recent WiRs - April 10th, April 3rd, March 27th, March 20th Jack Spratts' Week In Review is published every Friday. Submit letters, articles, press releases, comments, questions etc. in plain text English to jackspratts (at) lycos (dot) com. Submission deadlines are Thursdays @ 1400 UTC. Please include contact info. The right to publish all remarks is reserved. "The First Amendment rests on the assumption that the widest possible dissemination of information from diverse and antagonistic sources is essential to the welfare of the public." - Hugo Black |
||
|
|

|
 |
| Thread Tools | Search this Thread |
| Display Modes | |
|
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| Peer-To-Peer News - The Week In Review - February 13th, '10 | JackSpratts | Peer to Peer | 0 | 10-02-10 07:55 AM |
| Peer-To-Peer News - The Week In Review - January 30th, '10 | JackSpratts | Peer to Peer | 0 | 27-01-10 07:49 AM |
| Peer-To-Peer News - The Week In Review - January 23rd, '10 | JackSpratts | Peer to Peer | 0 | 20-01-10 09:04 AM |
| Peer-To-Peer News - The Week In Review - January 16th, '10 | JackSpratts | Peer to Peer | 0 | 13-01-10 09:02 AM |
| Peer-To-Peer News - The Week In Review - December 5th, '09 | JackSpratts | Peer to Peer | 0 | 02-12-09 08:32 AM |