
 |
|
|||||||
| Peer to Peer The 3rd millenium technology! |
 |
|
|
Thread Tools | Search this Thread | Display Modes |
|
|
#1 | ||||
|
Join Date: May 2001
Location: New England
Posts: 10,017
|
Since 2002
  "Let today be the pirates independence day! Today we celebrate the victories we’ve had and the victories that will come. Today we celebrate that we’re united in our efforts. Keep on seeding!" – The Pirate Bay "We’re not doing any more Windows. It is a security effort." – Google "Don’t blame Tor – it does what it says on the wrapper. It’s just that no one reads or understands the wrapper." – EthanZ "There are lots of battles to be fought, we can’t give them up. You folks in this room have the capacity to be some of the greatest ancestors anybody ever had." – John Perry Barlow QnA Q. How does Veetle work? I watched Shrek today, it was quite good A. Veetle is P2P-TV. They have money behind them, and they've solved a big problem for themselves, like the huge costs associated with all that video bandwidth. They’ve just done it by using yours. With P2P-TV (CNN used something similar for last years presidential inauguration), your upstream gets “borrowed” for the next guy down the viewing line. It’s sort of like Bittorrent in the sense that as you receive your program you broadcast it too. Ease of use is a major factor here, in that the user won’t need to know this is happening in order to enjoy a show, but when ISPs increasingly lean towards bandwidth caps, schemes like Veetle’s can bring unwelcome attention from providers. Maybe it's a big deal and maybe it isn't depending on the circumstances, but if you watch a lot of P2P-TV all that usage could become an issue. So something important to ask about before you install any P2P-TV app is the idling protocol, or what happens when you stop watching. Does the app continuing using your bandwidth, or does it disconnect you from the grid? Any stream-through should cease when you stop watching. Another consideration is picture quality. Because everyone essentially relys on everyone else, the program originator can't guarantee quality to the end user when they don't control the stream. In spite of these shortcomings I like P2P-TV. The idea of helping little pirates send home-made programs into the ether appeals to me. I’m just not as thrilled when business takes it up on locked platforms. They can do what they want privately of course, but they shouldn't surreptitiously rely on my unpaid participation while they chase profits. This seems to be Veetle's approach. Locked players streaming locked content that can't be recorded, or even paused. OTOH, some people think this is the future of television (even if similar protocols are already a decade old). Cringley is one such guy. I hope he's wrong (he often is) but you’ll find his take on it in this week’s issue. Enjoy, Jack June 5th, 2010  The Pirate Bay: Four Years After The Raid Ernesto Today, exactly four years have passed since The Pirate Bay was raided by the Swedish police. While the entertainment industries hoped that this would be the end of their troubles, in hindsight they’ve created a a multi-headed hydra that is impossible to kill. The events that unfolded could easily be turned into a Hollywood blockbuster. May 31, 2006, less than three years after The Pirate Bay was founded, 65 Swedish police officers entered a datacenter in Stockholm. The officers were tasked with shutting down the largest threat to the entertainment industry at the time – The Pirate Bay’s servers. While the policemen were carrying out their jobs, Pirate Bay founders Gottfrid and Fredrik learned that something was seriously wrong. In the months before the raid they were already being watched by private investigators day and night, but this time something was about to happen to their trackers. Fredrik recalls the day vividly: “I got a phone call like 10am in the morning, it was Anakata [Gottfrid].” He told Fredrik that there were police officers at their office, and asked him to get down to the co-location facility and get rid of the ‘incriminating evidence’, although none of it, whatever it was, was related to The Pirate Bay. As Fredrik was leaving, he suddenly realized that the problems might be linked to their tracker, so he initiated a full backup of the site. At the co-location facility there were 65 policemen, some in civilian clothing. Fredrik asked them: “Who are you? What are you doing here?” To which they responded, “Who are YOU? What are you doing here?” After questions back and forth, Fredrik eventually told them his name, and a police officer said, “Oh, we’ve been looking for you.” Although these events may seem almost comedic, Fredrik’s decision to start a backup of the site is probably the most pivotal moment in the site’s history. Because of this backup Fredrik and the rest of the Pirate Bay team were able to resurrect the site within three days. If there hadn’t have been a recent backup, things may have turned out quite differently. Technicalities aside, the determination to get the site online as soon as possible set the tone for the years that followed. Backups were spread over different countries to guarantee that the site would survive any attack. Although the site has gone down for 24 hours or more after the raid, this was usually caused by technical problems combined with laziness or wild parties. If they were shut down because of legal troubles, it usually took just a few hours to set up shop elsewhere. Now back to 2006 where the Swedish police confiscated 180 servers, most of which had nothing to do with The Pirate Bay. After all equipment was taken Peter, Fredrik and Gottfrid were escorted to the police station. During the subsequent questioning, the Pirate Bay trio gave up very little information. Gottfrid quickly confessed to his crime – of killing the Swedish prime minister when he was 2 years old, but that was all they got. After the raid it became clear that the US had threatened to put Sweden on the WTO’s black list if they refused to deal with the Pirate Bay problem. Even the MPAA was involved, with John Malcolm, Executive Vice President of the MPAA writing a letter to Sweden’s State Secretary in which he stated, “It is certainly not in Sweden’s best interests to earn a reputation among other nations and trading partners as a place where utter lawlessness with respect to intellectual property rights is tolerated.” The raid eventually resulted in a lengthy investigation where the police presented 4000 pages of evidence against the people involved. This was used by the prosecution during the Pirate Bay trial of last year, and we all know how that ended. The case is currently waiting to be appealed. The site, meanwhile, is still up and running and it is larger than ever before. Right before the raid the site welcomed its one millionth registered user, today they have well over 4 million. The Pirate Bay folks themselves continued to play Hollywood with their mockings and have declared May 31st to be the independence day of pirates. “Let today be the pirates independence day!,” they announced in 2008. “Today we celebrate the victories we’ve had and the victories that will come. Today we celebrate that we’re united in our efforts. Keep on seeding!” http://torrentfreak.com/the-pirate-b...e-raid-100531/  Anti-Piracy Law Test Case 'On its Way' to EU Court The first case tried since the passage of Sweden's anti-file sharing law (Ipred) in April 2009 looks destined for the EU Court of Justice after a ruling by the Supreme Court. This issue concerns a case between five audiobook publishers and the Swedish ISP ePhone which appealed a lower court ruling ordering the firm to hand over information about the users connected to certain IP-addresses. The Swedish Supreme Court (Högsta Domstolen - HD) has now taken up the case and has requested the parties involved to submit their view on whether it is necessary to send the matter for a preliminary ruling to the European Court - decision interpreted by experts to mean that it the case is headed for Luxembourg, a process that can take years. "I think so clearly. Apparently HD has made a preliminary assessment and concluded that most factors indicate that the issue be sent to Luxembourg," said Daniel Westman, a legal expert in file sharing at Stockholm University. The parties may also be given an opportunity to comment on a draft of the request in a decision which has surprised Magnus Nytell, CEO of audiobook publisher Bonnier Audio. "It has unexpectedly turned out this way. Granted, it is a new law and it is important that you put your foot down in various directions as it has implications for the future but we thought it was pretty clear that we would be given the Ipred-addresses (sic)," he said. Bo Wigstrand, president of ePhone, sees the Supreme Court decision as a victory. The firm has previously argued that the case should be considered by the EU court in Luxembourg. "We have drawn the conclusion that it is now clear that this issue will be sent to Luxembourg, and if the court does take this up it will mean a review of how the Ipred law is used in Sweden," he said. Wigstrand argued that the law provides for private surveillance in an area that should be the reserve of the police and he does not expect to be forced to hand over his customer's IP information to the publishers. "One should not claim success in advance but this shows that you can not have laws in which private investigators undertake these types of investigations. The police should do it." When the new Swedish law came into force on April 1st, the five publishers of audio books were the first copyright holders to file a case under the new measure. The publishers, which include 15 authors who suspected their work has been spread illegally over the internet, demanded to know who owned a server suspected of containing some 2,000 audio book titles. But ePhone refused to reveal who was using the IP-address in question, pointing out that a password was required in order to gain access to the works stored on the computer. As a result, the company argued, the sound files weren’t publicly accessible and thus the matter wasn’t a case of copyright infringement. The publishers then sought a court order which would force ePhone to divulge information about the users tied to the IP-address. The Solna district court first ruled in June 2009 in favour of the publishers but the the Court of Appeal (Hovrätten) upheld ePhone's appeal of the decision, ruling that the publishers were unable to prove whether the audio books on the server really had been available to the public. ePhone and the audiobook publishers are required to submit their response to HD before July 5th, with any decision over whether to proceed to Luxembourg expected to take some time. http://www.thelocal.se/27036/20100604/  Irish Music Body Sues O2 and 3 Ireland Over File Sharing The Irish Recorded Music Association (IRMA) has filed legal action against O2 and 3 Ireland seeking to force them to disconnect subscribers it alleges are sharing copyrighted content, reports the Irish Times newspaper. The IMRA says that it has engaged in talks with other, unspecified providers regarding the implimentation of a "three strikes" rule. Irish ISP Eircom launched a three-month pilot program earlier this month that will see those who share copyrighted files cut off from their Internet service after a third warning is ignored. The ISP only launched the trial after it was also sued by the IRMA. "O2 can confirm that it has been served with a plenary summons by solicitors acting on behalf of record labels EMI, Warner, Universal and Sony," the company said in a statement. "O2 is currently reviewing the issue, but does not believe it is legally liable in relation to illegal filesharing activities that any of its customers might seek to engage in." Hutchison 3G Ireland confirmed it had received legal papers but said it was too early to comment further. http://www.cellular-news.com/story/43568.php  Digital Economy Act: ISPs Criticise Ofcom Code for ‘Distorting the Broadband Market’ BT and TalkTalk are concerned that Ofcom’s draft code to curb illegal filesharing will ‘distort the broadband market’. Emma Barnett Both internet service providers (ISPs) have expressed their frustration that the media watchdog’s code excludes smaller internet service providers and mobile operators from the task of collecting customers’ details who have illegally downloaded copyrighted material. Last week Ofcom released its draft code, which sets out how and when ISPs should notify their subscribers of allegations that their accounts have been used for copyright infringement, following the previous government’s rushed passage of the Digital Economy Act. The code will initially only apply to ISPs with more than 400,000 customers, including BT, TalkTalk, Virgin Media, Sky, Orange, O2 and the Post Office. A BT spokesman said: “This is a detailed and complex document which we will be reviewing over the coming weeks. However our initial reaction is that Ofcom’s proposal to limit the obligations to just seven fixed operators and exclude mobile operators and fixed ISPs with less than 400k subscribers is concerning. “The UK currently boasts a highly competitive broadband market and we believe that such a move has serious potential to distort the market. We will be submitting our full response to Ofcom by the required deadline of 30th July 2010.” TalkTalk, which has vociferously opposed the letter-sending measures, since the previous government first suggested them, agreed with BT’s point. Andrew Heaney, executive director of strategy and regulation at TalkTalk, said: “The draft code exempts smaller ISPs’ and mobile operators, which seems arbitrary and could lead to market distortion.” Heaney added: “Ofcom's draft code of practice is a valiant attempt to implement the hospital pass it was given in the Digital Economy Act, but we think it has the potential to turn into a bureaucratic dog's breakfast. As the code stands, millions of customers would be at risk of being falsely accused of copyright infringement, being falsely put onto an 'offenders' register' and so potentially taken to court.” The Digital Economy Act decreed that a tiered approach is taken by the ISPs when attempting to curb illegal filesharing, which begins with warning letters and ends with practical measures – such as disconnection or bandwidth squeezing. Another part of the draft code which has caused controversy is the lack of detail surrounding the appeals process. It is not clear whether wrongly accused internet users will indeed have to pay for their own appeals, as The Telegraph revealed earlier this year. A Virgin Media spokesman said in response to this point: “It’s crucial that the appeals process is robust and does not penalise individuals, or ISPs, unfairly. We strongly believe that persuasion not coercion is the key to changing behaviour and a purely punitive regime risks alienating mainstream consumers.” However, Jim Killock, the executive director of the Open Rights Group, remained unconvinced, heavily criticising the draft code: “"This is another extremely rushed process, forced by the Digital Economy Act's absurd timetables. There are huge unanswered questions, not least whether innocent people will have to pay to appeal. "Government needs to draw a clear line between the notifications and potential disconnection regimes. Otherwise, Ofcom can't tell people what these accusations mean, which is absurd.” A Sky spokesman said the company was “still considering the implications of the proposals”. Ofcom has said the code will come into force early next year but a consultation on the proposal will run until July 30. http://www.telegraph.co.uk/technolog...nd-market.html  Rights Groups Call for a Fair File Sharing Code Rights groups call for a fair file sharing code Code should include independent appeals process A coalition of UK consumer and citizens' rights groups is calling on the Office of Communications (Ofcom) to develop an illegal file sharing code of practice which treats consumers fairly. The call, by the Communications Consumer Panel, was made on the same day Ofcom published a 10-week consultation on its Initial Obligations Code (IOC). The IOC sets out the framework for how copyright holders and internet service providers should treat customers they suspect of being guilty of infringing copyright laws. The Communications Consumer Panel, made up of members from the Citizens Advice Bureau, Consumer Focus, the Open Rights Group and Which?, is calling on Ofcom to use its Customer Protection Principles (CPP), as the basis for developing the IOC. This, the panel claims, would ensure that customers and citizens are properly protected. The CPP sets out the proposed rights customers should expect if a copyright holder accuses them of illicit file sharing. CPP key points * There should be sound evidence of wrongdoing before any action is taken against a consumer * Comprehensive and consistent information should be provided to all suspected repeat infringers and this should be written in plain English * Consumers must have the right to defend themselves * An independent and transparent appeals process is essential, at no cost to the customer * Information about affordable alternatives to online copyright infringement should be made widely available The Which? view Richard Hyde, Which?’s economic policy research assistant, said: 'Which? broadly supports the proportionate and graduated response to tackling illicit file sharing set out in the Digital Economy Act. ‘We think the principles we've agreed upon should ensure fairness and urge Ofcom to use these as the basis for its IOC proposals.’ http://www.which.co.uk/news/2010/06/...g-code--215878  LimeWire Judge Cuts Curious Note about EFF Lawyer Greg Sandoval U.S. District Judge Kimba Wood apparently goofed by suggesting that a prominent pro-technology attorney acted improperly in dealings with the firm that oversees LimeWire. Two weeks ago, Wood granted summary judgment in favor of the Recording Industry Association of America in the trade group's copyright case against Lime Group, parent of file-sharing service Lime Wire, maker of the LimeWire software. While Wood's decision generated enormous interest from file sharers, as it likely means the end of LimeWire, according to legal experts, Wood's written decision stirred controversy in legal circles by including a short note about lawyer Fred von Lohmann, a well-known champion of technology companies and Internet users. Wood wrote that some of the executives from Lime Wire gave sealed testimony that von Lohmann, senior staff attorney for advocacy group the Electronic Frontier Foundation, advised them to "purge incriminating information about LimeWire users' activities." Many of von Lohmann's critics from the pro-copyright side said it appeared Wood was calling out von Lohmann for offering Lime Wire execs a primer on how to break the law and get away with it. But on Tuesday, Wood amended her decision after receiving a written request to do so last week by Cindy Cohn, EFF's legal director. In Wood's amended decision, there is no explanation about what she meant with the phrase "purge incriminating information" or why she removed it. "We believe the materials in the record do not support the inclusion of the phrase 'to purge incriminating information,'" Cohn wrote in her request to Wood for a modification. "As you may imagine, Mr. von Lohmann and EFF are concerned that his professional reputation has been put at risk." Calls to von Lohmann on Friday were not immediately returned. Wood's rewrite won't come as a surprise to von Lohmann's colleagues and supporters, many of them lawyers who also tend to defend file-sharing companies and Internet services accused of copyright violations. Some of them said last week that von Lohmann, perhaps best known for being part of the legal team that defended file-sharing service Grokster in the landmark case, MGM Studios vs. Grokster , is a smart, respected and ethical attorney. http://news.cnet.com/8301-31001_3-20006285-261.html  RIAA Wants Court To Shut Down Limewire Ernesto The RIAA has asked a New York District Court to shut down the world’s most installed file-sharing application, Limewire. The record labels argue that the Gnutella-based download client might have caused billions of dollars in lost revenue and that it’s therefore one of the largest threats to the music industry’s revenue. limewireThe RIAA and the company behind Limewire have been fighting out a legal dispute since 2006, but in recent weeks the case seems to have been moving along faster than ever before. Last month, a US Court ruled that the Lime Group, the company behind Limewire, was liable for the copyright infringements committed by its users. Two weeks later the Lime Group asked the court to reconsider this judgment. This request was followed by one from the RIAA, asking the court to shut down Limewire via a permanent injunction. The RIAA argues that Limewire’s operation has to be stopped immediately, to avoid it doing any more harm to the music industry in the future. Interestingly enough, very little argumentation or evidence is given for any real losses suffered by the record labels. “It is patently obvious that the rampant illegal conduct that Lime Wire intentionally induced, and for which it has been adjudged liable, will continue uninterrupted day after day unless and until the Court issues an injunction to rein in this massive infringing operation,” RIAA’s lawyers wrote to the Court. “Every day that Lime Wire’s conduct continues unabated guarantees harm to Plaintiffs that money damages cannot and will not compensate,” RIAA’s legal team continues. “The scope of the infringements that Lime Wire induced – and that continue to this day – boggles the mind. The RIAA is right in saying that Limewire users have committed, and are committing many millions of infringements, but there is very little evidence for the massive damage that this has cost. Thus far, a real assessment of the claimed losses has been lacking in most file-sharing related legal cases. “It does not require sophisticated mathematics to calculate that the likely damage award in this case will run into the hundreds of millions, if not the billions of dollars,” the RIAA argues. However, one of the few academic papers (pdf) that looked at the relationship between actual downloads and lost sales to the music industry has found that there’s no direct correlation. With that said, the outcome of this case could potentially change the file-sharing landscape for good. Despite BitTorrent being the leading file-sharing protocol for several years already, Limewire is most likely the most installed P2P application on the market. In 2008 LimeWire was the most installed P2P application with an impressive market-share of 37%, compared to 14% for runner-up uTorrent. If the RIAA score a victory in court against Limewire, hundreds or millions of people will have to seek an alternative download client, which might mean a significant boost in user numbers for some of the major BitTorrent applications. http://torrentfreak.com/riaa-wants-c...mewire-100605/  The RIAA? Amateurs. Here's How You Sue 14,000+ P2P Users Nate Anderson The big music labels and movie studios have stepped back from the lawsuit business. The MPAA's abortive campaign against individual file-swappers ended years ago, while the RIAA's more widely publicized (and criticized) years-long campaign against P2P swappers ended over a year ago. So why have P2P lawsuits against individuals spiked dramatically in 2010? It's all thanks to the US Copyright Group, a set of lawyers who have turned P2P prosecution into revenue generation in order to "SAVE CINEMA." The model couldn't be simpler: find an indie filmmaker; convince the production company to let you sue individual "John Does" for no charge; send out subpoenas to reveal each Doe's identity; demand that each person pay $1,500 to $2,500 to make the lawsuit go away; set up a website to accept checks and credit cards; split the revenue with the filmmaker. The lawsuits are brought in Washington, DC's federal courthouse, and they all come from the same law firm: Leesburg, Virginia-based Dunlap, Grubb, & Weaver. In half a year, the group has proved surprisingly active and has managed the rare feat of making the RIAA campaign look slow-moving and small-scale. No one seems quite sure how large this new pool of lawsuits has become, so we scoured the DC federal docket to find out just how many of these cases were brought already in 2010, and have collected them below for convenience. With a major new case filed only a week ago, it's clear that this campaign is just ramping up. As it does so, the cries of those who say they have been wrongly targeted will grow—but most people will probably just pay up. January 2010 The Gray Man, 749 Does. Dunlap, Grubb, & Weaver went after its first set of targets in January, bringing suit on behalf of Worldwide Film Entertainment against 749 anonymous individuals. The Gray Man tells the story of an aging grandfather with a secret: "in actuality, he is a child murderer who tortures and cannibalizes his victims." The film's tagline reads, "A real-life Hannibal Lecter." Uncross the Stars, 195 Does. In the other case filed in January, G2 Productions brought suit against 83 Does over the film Uncross the Stars, a family-friendly flick starring Ron Pearlman (who also plays Hellboy) and Barbara Hershey. The plot involves a retirement community in Arizona, which may be why the National Senior Living Providers Network called the film "a rare treat...that makes the audience laugh and cry." The Uncross the Stars suit is notable for bring the first time that Dunlap, Grubb, & Weaver rolled out a strategy it would employ repeatedly over the following months: suing a few people first and then amending the complaint later to up the number significantly. Thus, while the case is headed "G2 PRODUCTIONS, LLC v. DOES 1-83," 195 Does are now targeted after an Amended Complaint was filed. March 2010 Far Cry, 4,577 Does. (In)famous German director Uwe Boll, best known for a series of mediocre video game films, got in on the lawsuit action two months later. In the middle of March, Boll's production company Achte/Neunte Boll Kino Beteiligungs GmbH filed suit against 2,049 Does over illicit distribution of the movie Far Cry based on the FPS of the same name. A few weeks later, the complaint was amended and it upped the number of targeted Does to 4,577. Call of the Wild, 1,062 Does. The 2009 3D adaptation of Jack London's "Call of the Wild" was independently funded by Call of the Wild LLC. The producers hitched themselves to the litigation dogsled, filing suit a day after the Far Cry case. While only 358 Does were targeted initially, that number jumped to 1,062 a few weeks later as more Does were added in the Amended Complaint. As for the movie itself, Christopher Lloyd starred in it, and a Variety review gave the picture decent marks apart from its use of the 3D gimmick. "Too bad the animal's protruding nose is the only feature that demands the third dimension," the review concluded. The Steam Experiment, 2,000 Does. A few days later, yet another suit hit the DC District Court. Production company West Bay One sued an even 2,000 Does over its film The Steam Experiment, also known as The Chaos Experiment. The film stars Val Kilmer. According to the Internet Movie Database plot summary, "A deranged scientist locks 6 people in a steam room and threatens to turn up the heat if the local paper doesn't publish his story about global warming." April 2010 Smile Pretty (aka Nasty) and others, 1,000 Does. Maverick Entertainment Group makes a host of low-budget films that will never make it to your local cineplex, including Army of the Dead, Border Town 2009, Buds for Life, Demons at the Door, Holy Hustler, and Smile Pretty (aka Nasty). In mid-April, the company went after 1,000 Does for sharing one or more of these films over the Internet. May 2010 The Hurt Locker, 5,000 Does. The most influential case was filed only recently. Thanks to its Oscar buzz, Voltage Pictures' The Hurt Locker is the best known of all films involved in these lawsuits. It's also the largest case to date, with 5,000 Does, and has attracted some significant publicity. Adding it up 14,583 Does have now been sued in federal court, with lawyers from Dunlap, Grubb & Weaver handling each case. The number is extraordinary; even after years of lawsuits, the RIAA campaign against file-swappers targeted 18,000 people (you can see the bump caused by RIAA lawsuits in the chart below between 2003 and 2008). Between January and May of this year, indie filmmakers have been persuaded to go after almost the same number of people, with most of that volume coming in only three months. 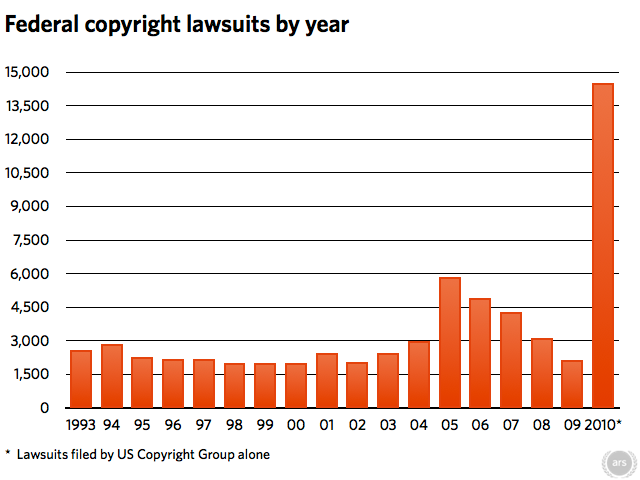 Data source: Administrative Office of the Courts, Wired The sheer volume suggests that these cases aren't designed for prosecution—and they don't need to be. As the RIAA lawsuits showed us, most people will settle. Data from the recording industry lawsuits, revealed in a court case, showed that 11,000 of the 18,000 Does settled immediately or had their cases dropped by the labels. Seven thousand either refused to settle or never responded to the settlement letter, but after the RIAA subpoenaed their identities and filed "named" lawsuits against them, nearly every one settled. After years of litigation, the number of people who have pursued a trial all the way to a verdict can be counted on one hand. The legal campaign has the potential to earn real money. Copies of the settlement letters and settlement contracts seen by Ars Technica show that Dunlap, Grubb, & Weaver generally asks for $1,500 to $2,500, threatening to sue for $150,000 if no settlement payment is forthcoming. Assuming that 90 percent of the current targets settle for $1,500, this means that the lawyers, studios, and P2P detection company would split $19.7 million. Once the infrastructure has been set up, this sort of system is simple to replicate, since it's built largely on sending out letters and collecting cash. If the lawyers can continue signing up indie film clients at the current rate, they could be on their way to filing nearly 30,000 lawsuits by year's end, which would double the potential cash on the table. http://arstechnica.com/tech-policy/n...-p2p-users.ars  A File-Sharing Suit with My Name On It? (FAQ) Greg Sandoval Suing people for illegal file sharing appears to have made a comeback. "The Hurt Locker" won six Oscars but made only $16 million in U.S. box office sales. Without file sharing, would the flick have made more? News that Voltage Pictures, producers of the Oscar-winning film "The Hurt Locker," filed a federal copyright complaint last week against 5,000 alleged file sharers caught many in the file-sharing community off guard. Hadn't the film and music industries dumped a litigation strategy in favor of a much more subtle approach, one that didn't drag fans into court where they stood to lose thousands of dollars? It's true, the trade groups for the major players in both these sectors, the Motion Picture Association of America and the Recording Industry Association of America, gave up suing file sharers. For the past couple years, they've tried to persuade Internet service providers to suspend service to first-time copyright offenders--and though they don't like talking about it much, the MPAA and RIAA would like chronic abusers to be permanently booted off the networks. None of this, however, would happen without the accused receiving plenty of warning. But the latest round of lawsuits isn't being brought by gargantuan entertainment conglomerates, with their legions of lawyers and deep pools of cash. A dozen or so little-known film companies, with far fewer resources than the big studios, have mounted their own legal challenge to file sharing. And these guys appear to be playing by their own rules. In a few short months, they've filed lawsuits against a combined 50,000 people. The RIAA in five years filed complaints against fewer than 40,000. Forget comparisons to the little guy being oppressed by "the man." The way these smallish filmmakers see it, they are the victims. To them this new chapter in antipiracy is David vs. David. It likely won't matter to those being sued that these smaller film companies aren't as big or rich. Some people are confused and nervous. Since Friday, when news of the Hurt Locker" suit spread, there's been a lot of speculation about where the lawsuits are headed. Here are a few facts: Question: I've received a letter from my ISP notifying me that Voltage Pictures, producer of "The Hurt Locker," has accused me of illegally sharing the movie. The company has requested that my ISP give up my name, home address, and IP and Media Access Control addresses. Can I do anything to prevent this? People would likely need to file a motion to quash the subpoena, meaning an attempt to convince the court that they shouldn't have to comply with the subpoena because they're protected by some legal privilege and complying would mean violating that privilege. Eva Galperin, referral coordinator for the Electronic Frontier Foundation, the advocacy group for tech companies and Internet users, advises those accused in a copyright suit to begin the process by consulting an attorney. For the past several weeks, EFF.org has been soliciting attorneys for help in defending people in the cases brought by Voltage and the other film companies. Galperin also suggested that people check the Web site subpoenadefense.org. Q: What are the U.S. Copyright Group and Dunlap Grubb Weaver? They appear to be one and the same. Thomas Dunlap, the founder of the Dunlap Grubb Weaver law firm, appears to have created the name U.S. Copyright for an antipiracy operation. By all appearances, Dunlap is attempting to turn a profit out of suing accused file sharers and represents the makers of at least 10 films in addition to "The Hurt Locker." According to reports, Dunlap is offering to work free of charge for the film companies in exchange for a large cut of whatever money the operation brings in. Q: I've been accused, but I'm innocent. What are my options? Again, consult an attorney or the EFF. It's true that the majority of people accused by the RIAA during the music industry's five-year litigation campaign chose to pay the RIAA and settle. There are instances in past cases of people being wrongly accused. Tanya Andersen was accused by the RIAA five years ago of illegal file sharing, but she refused to settle because she said she was innocent. In January, copyright expert and legal blogger Ben Sheffner wrote: "The labels took depositions and examined her computer, but couldn't definitively tie Andersen to the illegal downloading. And so they dropped the case." More recently, CNET reported that Cathi "Cat" Paradiso, a 53-year-old grandmother from Colorado, was accused of copyright infringement by several top studios for allegedly pirating such movies as "Zombieland," "Harry Potter," and "South Park." Eventually, her bandwidth provider, Qwest Communications, cleared her of any wrongdoing when employees there discovered Paradiso's network security wasn't set up properly and was compromised. Quest and other ISPs note that in most cases, customers are responsible for properly securing their Wi-Fi. Q: How can Voltage and Dunlap be so sure that someone on my network shared files? What about spoofing, dynamic IP addresses, and hacking? The debate over how accurately file sharing can be detected has raged for years. When it comes to an Internet protocol address--the number assigned to devices logged in to a computer network--everyone seems to be in agreement that accuracy depends largely on how well bandwidth providers keep track of this information. The same goes for dynamic IP addresses, a term used to describe when a computer is assigned a different address. A static address is one that is assigned and doesn't change. One expert in the content-protection area, who requested anonymity, said ISPs are supposed to know the IP address of any computer at any given time, but he said some ISPs keep better records than others and there is sometimes the possibility of error. Spoofing is a term used to describe the forging of an IP address, often attempted when a person is trying to cover his or her tracks online. The content-protection expert said that without knowing how Dunlap is collecting IP addresses, it's hard to say how susceptible the company's data is to spoofing. But "in theory" it shouldn't be a problem because "spoofs will not be routable IP addresses," he said. If Dunlap tried to make a connection to a spoofed IP address, it shouldn't be successful because the IP address isn't real. Q: If my IP address is among the 5,000 in Voltage's lawsuit, how long before I receive a settlement letter? Jon Harrison, a photographer from Irving, Texas, shared his experience with CNET on Monday. He provided documentation given to him by Verizon, his bandwidth provider, and by Dunlap. It shows that it was more than two months from the time he is alleged to have illegally shared a copy of the movie "Far Cry" until the time he heard from Dunlap. The company informed him last week that if he paid $1,500 before June 11, 2010, he could avoid being named in the lawsuit and possibly paying as much as $150,000 for each infringing act. No accused file sharer anywhere has been required to pay such an amount. http://news.cnet.com/8301-31001_3-20006528-261.html  EFF Asks Judges to Quash Subpoenas in Movie-Downloading Lawsuits Predatory Copyright Infringement Cases Violate Rights of Thousands The Electronic Frontier Foundation (EFF) asked judges in Washington, D.C., Wednesday to quash subpoenas issued in predatory lawsuits aimed at movie downloaders, arguing in friend-of-the court briefs that the cases, which together target several thousand BitTorrent users, flout legal safeguards for protecting individuals' rights. Public Citizen and the American Civil Liberties Union (ACLU) Foundation joined EFF on the briefs filed Wednesday. The lawsuits are the brainchild of a Washington, D.C., law firm calling itself the "U.S. Copyright Group" (USCG). USCG investigators have identified IP addresses they allege are associated with the unauthorized downloading of independent films, including "Far Cry" and "The Hurt Locker." To date, USCG has filed seven "John Doe" lawsuits in D.C., implicating well over 14,000 individuals, and has issued subpoenas to ISPs seeking the names and addresses of the subscribers associated with those IP addresses. Several ISPs have complied, but Time Warner Cable moved to quash the three subpoenas it received, arguing that USCG is abusing the discovery process. In briefs filed in support of the cable giant, EFF says the John Doe defendants are being deprived of a fair chance to defend themselves by the strategies adopted by the USCG. "By requiring those sued to defend these cases in D.C., regardless of where they live, and by having thousands of defendants lumped into a single case, the USCG has stacked the deck against the defendants," said EFF Senior Staff Attorney Corynne McSherry. "In addition, the First Amendment mandates that each defendant be given notice and opportunity to quash a subpoena and that the plaintiff offer sufficient evidence of infringement about each defendant individually." "If USCG wants to sue thousands of people, it needs to give each defendant a fair chance to fight the accusations," added EFF Civil Liberties Director Jennifer Granick. "Instead, USCG is taking shortcuts that will result in innocent people getting tangled up in the dragnet." USCG's strategy appears to be to threaten a judgment of $150,000 per downloaded movie -- the maximum penalty allowable by law in copyright suits and a very unlikely judgment in cases arising from a single, noncommercial infringement -- in order to pressure the alleged infringers to settle quickly for about $2,500 per person. USCG unapologetically explains this strategy on its website: "As a practical matter each individual infringer lacks the assets, net worth and earning capacity to make civil prosecution practical...until the SaveCinema.org efforts of the US Copyright Group." USCG has also said it plans to target thousands more individuals for legal action in the coming months. "We've long been concerned that some attorneys would attempt to create a business by cutting corners in mass copyright lawsuits against fans, shaking settlements out of people who aren't in a position to raise legitimate defenses and becoming a category of 'copyright trolls' to rival those seen in patent law," said EFF Legal Director Cindy Cohn. "We're asking the court to step in now and force USCG to follow the rules that apply in all other cases." For the full amicus brief: http://www.eff.org/files/filenode/us...0Final%20Brief... For more on this case: http://www.eff.org/cases/achte-neunte-v-does http://www.eff.org/press/archives/2010/06/02  Publishing Locations Of Pirate Movies Is The Same As Hosting Them enigmax A movie studio has won a lawsuit against Dutch Usenet community FTD. In a surprising decision, a court reasoned that by allowing the publication of the location of pirate movie stored on Usenet, FTD was effectively publishing the movie as if they had actually hosted it on their own servers. Earlier, Dutch movie studio Eyeworks applied for a court injunction to stop Usenet community FTD from “making available to the public” their movie Komt een vrouw bij de dokter (A Woman At The Doctor). In this case the “making available” wasn’t hosting or storing the movie, nor was it offering torrent or NZB links to it either. FTD allows users to report (or ’spot’) the locations of files which exist on Usenet. It is the publication of this information which Eyeworks was seeking to stop, an activity it believes is tantamount to publishing the movie itself. In early May the case was heard at a court in The Hague. FTD lost the case and the court issued an ‘ex parte injunction’ (one handed down without any FTD involvement) which banned the site from ’spotting’ the Eyeworks movie. Through its lawyer Arnoud Engelfriet, FTD filed an objection on the basis that the provisional measure should not have been issued under Dutch law. That objection was heard and the decision was delivered yesterday – FTD lost again. “I am flabbergasted by the court’s reasoning,” Engelfriet told TorrentFreak. “It is established caselaw that publishing hyperlinks or torrents (Mininova, Pirate Bay) is *not* the same as a publication. FTD does *less* than what Mininova or Pirate Bay does, but according to the court we are more liable than they are?” In coming to its decision, the court drew heavily on the earlier Newzbin case. “They say that FTD is doing the same thing, and since the English courts held Newzbin liable for infringement, FTD must be liable too,” Engelfriet explains. “This completely ignores the technical differences between Newzbin and FTD. Newzbin is an NZB search engine through which you find codes to directly download from Usenet. FTD is a forum where people ’spot’ movies using messages in ordinary Dutch.” FTD had argued that it was not guilty of “making available” because copyrighted files on Usenet are not under its control – it does not control the servers and it has no influence over potential downloaders. The court decided that this is irrelevant. What is important, it said, is “whether the behavior of FTD allows users to download copyrighted files (in an easier manner) and thus makes such files available to the public.” The court ruled that it did. “This is a collaboration between FTD and its users where they knowingly provide access to unauthorized files,” BREIN director Tim Kuik said in a comment. “It’s clear that this is more than just talking about files like FTD wants people to believe.“ In October this year FTD will face another court case. Dutch anti-piracy group BREIN says that FTD “organizes and promotes” Usenet content, most of which is illegal, and wants the entire site shut down. http://torrentfreak.com/publishing-l...g-them-100603/  Shouldn't the MPAA Crack Down on Ashton Kutcher for Promoting Piracy? Patrick Goldstein The Motion Picture Association of America is always talking tough about cracking down on piracy anywhere and everywhere, so much so that it has even been sending out its fabled "you are breaking the law" copyright infringement notices not just to slacker college kids, but soldiers stationed in harm's way on overseas military bases in Iraq, threatening them with suspension of their Internet service provider accounts if they continue to watch pirated movies. So if the MPAA is so serious about combating piracy, when is it going to go after Ashton Kutcher? In case you missed it, Kutcher (who has a huge following on Twitter, which in itself is a sad commentary on the taste level of the American public) has announced that he plans to "pirate" part of his upcoming film, "Killers," and put it online sometime this week. As he put it in Tweet-speak, he'll be "going live 2 the web & pirating the 1st 10 min of Killers from the premiere." He later told Ellen DeGeneres that he plans to "pirate the first 13 minutes of the movie." As the Hollywood Reporter's legal eagle Matthew Belloni shrewdly points out, this is all simply a way to hype "Killers" - and judging from its lackluster trailers, TV spots and weak early buzz, the movie needs all the hype it can get. As Belloni wrote Tuesday, "the free preview is a transparent marketing stunt by Lionsgate, the studio behind the film, which has decided to hide the movie from critics and instead put the first few minutes in front of its target audience during the run-up to its release. To that end, they've enlisted the movie's co-star, a genuine Internet phenomenon, to help promote that effort." So Kutcher isn't actually pirating the movie, he's simply marketing the movie by putting up brief snippets of the film, a scheme other studios have used in the past to drum up excitement for opening weekend audiences. But of course, the actor is calling it piracy because calling it piracy gets more attention than calling it a sneak peek or a free preview. It is a conscious effort to make the whole thing seem illicit. And that's why the MPAA, if it expects us to actually have any sympathy for its often clumsy, often overwrought, boot-heel-on-the-throats-of-its-most-loyal-customers-style enforcement efforts, should be cracking down on Kutcher and Lionsgate too. If Lionsgate, even if it isn't a MPAA signatory, is going to turn piracy into a marketing scam, it makes a mockery of the MPAA's efforts to treat piracy as a serious offense. If Kutcher can boast about pirating his own movie with impunity, then why should college kids be treated like criminals when they actually do the deed themselves? Either piracy is cool or it isn't. And if the MPAA is bent on persuading us that that isn't cool, then they should come down on Kutcher and Lionsgate like a ton of bricks. Lionsgate should certainly be hoping that some smart-aleck college kid doesn't put a pirated version of "Saw 7" up on the Web a month before the movie opens this fall because the studio won't get much sympathy from any enforcement officials or those of us in the media. Once you treat piracy like a gag, you don't get to treat it like a serious offense the next time around - which is why the MPAA should be figuring out some very public way to show its disapproval. Belloni concludes his post by cautioning Kutcher that he should "think twice next time about glamorizing theft in a cynical attempt to sell his movie." That goes double for Lionsgate, who should realize that cynical marketing leads to cynical moviegoers, who are exactly the kind of people most likely to view piracy as a perfectly acceptable response to the industry's recently jacked-up movie ticket prices. http://www.miamiherald.com/2010/06/0...k-down-on.html  uTorrent For Linux Is Coming, Finally Ernesto Five years after uTorrent was released for the Windows platform the development team has announced that it’s working on a Linux version of the torrent client. The massive demand from users is cited as one of the main reasons why Linux users will have a native uTorrent application this coming summer. utorrneuTorrent for Windows saw its first public release in September 2005 and soon became the most widely used BitTorrent application. Every month, more than 50 million people use uTorrent and this number continues to grow alongside BitTorrent’s ever-increasing user base. Ever since uTorrent was released, Mac and Linux users have begged the developers to release a version of the client designed to work on their computers. In 2006, when uTorrent was sold to BitTorrent Inc., the company announced that a Mac version was coming. In 2008, nearly two years after the announcement, it was finally released to the public. With the the release of the Mac version, Linux users were the only ones left out in the cold, but this is about to change. The uTorrent development team has just announced that they are working on a Linux version of the client. Further details on the time line and an eventual release date are not available at the moment. The Linux version is the most backed idea on uTorrent’s recently introduced Idea Bank. The Idea Bank is prominently featured on uTorrent’s website and allows users to submit and vote for ideas they want to see implemented. In just a few weeks the idea of a Linux version has been supported by 3254 people. This huge demand from users is one of the main reasons why the Linux version is now in progress. “Since launching our Idea Bank on uTorrent.com there has been significant demand for a native client for Linux,” BitTorrent Inc. spokesperson Jenna Broughton told TorrentFreak. “We obviously want to do our best to deliver whenever we see a good fit between our goals and capabilities and what our users say they want.” “We are committed to bringing a lightweight uTorrent client that embraces the usability and features of our Windows and Mac clients to Linux users,” Broughton said. The exact feature-set of the Linux client will remain a secret for now, but in common with other versions of uTorrent it wont be Open Source. The release date for the client is unknown at this point but unlike the Mac version it should come out relatively quickly. “While the exact specs as well as the timing are still being developed, we expect uTorrent for Linux to be available for download later this summer,” we were informed. Whether or not the uTorrent Linux release will ever reach the massive market share it has on Windows remains to be seen. The Mac version has been well received but it is by no means the most used BitTorrent client on the platform. Whatever happens, it’s definitely good to see that uTorrent will soon be available on all three major platforms. http://torrentfreak.com/utorrent-for...inally-100601/  Wikileaks Was Launched With Documents Intercepted From Tor Kim Zetter Wikileaks, the controversial whistleblowing site that exposes secrets of governments and corporations, bootstrapped itself with a cache of documents obtained through an internet eavesdropping operation by one of its activists, according to a new profile of the organization’s founder. The activist siphoned more than a million documents as they traveled across the internet through Tor, also known as “The Onion Router,” a sophisticated privacy tool that lets users navigate and send documents through the internet anonymously. The siphoned documents, supposedly stolen by Chinese hackers or spies who were using the Tor network to transmit the data, were the basis for Wikileaks founder Julian Assange’s assertion in 2006 that his organization had already “received over one million documents from 13 countries” before his site was launched, according to the article in The New Yorker. Only a small portion of those intercepted documents were ever posted on Wikileaks, but the new report indicates that some of the data and documents on WikiLeaks did not come from sources who intended for the documents to be seen or posted. It also explains an enduring mystery of Wikileaks’ launch: how the organization was able to amass a collection of secret documents before its website was open for business. Tor is a sophisticated privacy tool endorsed by the Electronic Frontier Foundation and other civil liberties groups as a method for whistleblowers and human rights workers to communicate with journalists, among other uses. In its search for government and corporate secrets traveling through the Tor network, it’s conceivable that WikiLeaks may have also vacuumed up sensitive information from human rights workers who did not want their data seen by outsiders. The interception may have legal implications, depending on what country the activist was based in. In the United States, the surreptitious interception of electronic communication is generally a violation of federal law, but the statute includes a broad exception for service providers who monitor their own networks for legitimate maintenance or security reasons. “The statutory language is broad enough that it might cover this and provide a defense,” says former U.S. federal prosecutor Mark Rasch. The New Yorker article did not indicate whether WikiLeaks continues to intercept data from the Tor network. Assange did not immediately return a call for comment from Threat Level. WikiLeaks uses a modified version of the Tor network for its own operations, moving document submissions through it to keep them private. WikiLeaks computers also reportedly feed “hundreds of thousands of fake submissions through these tunnels, obscuring the real documents,” according to The New Yorker. The intercepted data was gathered from Tor sometime before or around December 2006, when Assange and fellow activists needed a substantial number of documents in their repository in order to be taken seriously as a viable tool for whistleblowers and others. The solution came from one of the activists associated with the organization who owned and operated a server that was being used in the Tor anonymizing network. Tor works by using servers donated by volunteers around the world to bounce traffic around, en route to its destination. Traffic is encrypted through most of that route, and routed over a random path each time a person uses it. Under Tor’s architecture, administrators at the entry point can identify the user’s IP address, but can’t read the content of the user’s correspondence or know its final destination. Each node in the network thereafter only knows the node from which it received the traffic, and it peels off a layer of encryption to reveal the next node to which it must forward the connection. By necessity, however, the last node through which traffic passes has to decrypt the communication before delivering it to its final destination. Someone operating that exit node can therefore read the traffic passing through this server. According to The New Yorker, “millions of secret transmissions passed through” the node the WikiLeaks activist operated — believed to be an exit node. The data included sensitive information of foreign governments. The activist believed the data was being siphoned from computers around the world by hackers who appeared to be in China and who were using the Tor network to transmit the stolen data. The activist began recording the data as it passed through his node, and this became the basis for the trove of data Wikileaks said it had “received.” The first document WikiLeaks posted at its launch was a “secret decision” signed by Sheikh Hassan Dahir Aweys, a Somali rebel leader for the Islamic Courts Union. The document, which called for hiring hit men to execute government officials, had been siphoned from the Tor network. Quote:
WikiLeaks, whose website is hosted primarily through a Swedish Internet service provider called PRQ.se, never reveals the sources of its documents, and in the case of the Apache video, Assange has said only that it came from someone who was angry about the military’s frequent use of the term “collateral damage.” The New Yorker doesn’t identify the WikiLeaks activist who was the source for the documents siphoned from Tor, but the description of how the documents were obtained is similar to how a Swedish computer security consultant named Dan Egerstad intercepted government data from five Tor exit nodes he set up in 2007 — months after Wikileaks launched — in Sweden, Asia, the United States and elsewhere. Egerstad told Threat Level in August 2007 that he was able to read thousands of private e-mail messages sent by foreign embassies and human rights groups around the world by turning portions of the Tor internet-anonymity service into his own private listening post. The intercepted data included user names and passwords for e-mail accounts of government workers, as well as correspondence belonging to the Indian ambassador to China, various politicians in Hong Kong, workers in the Dalai Lama’s liaison office and several human rights groups in Hong Kong. Egerstad, who says he has no association with WikiLeaks and was not the source for the intercepted Tor documents the site received, told Threat Level at the time that he believed hackers were using the Tor network to transmit data stolen from government computers and that he was able to view the data as it passed through his node unencrypted. Egerstad was never able to determine the identity of the hackers behind the data he intercepted, but it’s believed that he may have stumbled across the so-called Ghost Net network — an electronic spy network that had infiltrated the computers of government offices, NGOs and activist groups in more than 100 countries since at least the spring of 2007. The Ghost Net network was exposed by other researchers last year who discovered that hackers — believed by some to be based in China — were surreptitiously stealing documents and eavesdropping on electronic correspondence on more than 1,200 computers at embassies, foreign ministries, news media outlets and nongovernmental organizations based primarily in South and Southeast Asia. It’s not known if the data the WikiLeaks activist siphoned was data stolen by the Ghost Net hackers. http://www.wired.com/threatlevel/201...aks-documents/  Plaintext Over Tor is Still Plaintext Recently, a few articles have been published regarding Tor, Wikileaks, and snooping data coming out of the Tor network. I write to remind our users, and people in search of privacy enhancing technology, that good software is just one part of the solution. Education is just as important. This is why there is a warning on the Tor download page about what Tor does and does not do. We also have a FAQ entry about this topic. Any plaintext communication over the Internet is open to intercept. This is true if the transport mechanism is email, http, tor, or carrier pigeons. Tor does not magically encrypt the Internet from end to end. Tor provides anonymity and privacy by hiding where your Internet traffic is going and where it came from, but users must protect the security of their traffic by using encryption. Once you exit the last relay, you are back on the open Internet. Some web email providers, banks, and other sites use encryption by default when you log in, something you can check by looking for "https://" at the beginning of a URL. For more information, check out Ethan Zuckerman's comments on this topic. For reference, these articles are unclear and blur concepts about Tor and Wikileaks. An article about Julian Assange of Wikileaks in The New Yorker is the source of the confusion. Ryan Sholin deliberates on one paragraph from the New Yorker story. Ethan Zuckerman responded to Ryan's thoughts about Tor here. We thanked EthanZ for the accurate response in an Identi.ca dent. It seems Slashdot and Wired Threat Level have picked up on just that one statement in the article by the New Yorker. We hear from the Wikileaks folks that the premise behind these news articles is actually false -- they didn't bootstrap Wikileaks by monitoring the Tor network. But that's not the point. The point is that users who want to be safe need to be encrypting their traffic, whether they're using Tor or not. https://blog.torproject.org/blog/pla...till-plaintext  Don’t Blame Tor EthanZ Brian – I thought the brief passage on Tor was the weakest aspect of what was otherwise an excellent piece in the New Yorker. I think the author wanted to be writing about two things: Hidden services, and exit node monitoring. Hidden services – which the author appears to refer to in the sentence – ” The entire pipeline, along with the submissions moving through it, is encrypted, and the traffic is kept anonymous by means of a modified version of the Tor network, which sends Internet traffic through “virtual tunnels” that are extremely private.” – is a long-established part of the Tor system, in place since 2004. It’s a way of publishing information so that it’s extremely difficult to trace the existence of content to a particular IP. It’s a very cool feature, though it’s hard for average users to access, which is why we generally don’t recommend it as a strategy for whistleblowers. But it’s a very reasonable tool for internal use within Wikileaks and suggests an appropriate degree of caution for what Wikileaks is doing. And it’s possible that they’re using a somewhat customized version of Tor to do this… but it’s also possible that this is a misunderstanding on the part of the journalist, as Hidden Services requires significantly more configuration than off-the-shelf Tor clients. The assertion that seemed to worry you was about exit node monitoring. In other words, a member of the Wikileaks project was running a Tor exit node, a part of the Tor network that interfaces with the public internet. The job of an exit node is to take a request from within the Tor network and route it to a webserver or a machine running another internet service (POP, IMAP email, FTP, etc.) It can be troublesome to run an exit node, as bad actions – defacing wikipedia, sending spam – are traceable back to that exit node, but not back to who actually made the request. That’s the beauty of Tor – it’s designed to hide the identity of the person requesting a webpage from the operator of the exit node, and therefore to the operator of the web server. Tor does this by passing a request between three nodes before sending it to a webserver. Node A (the entry node) knows where the user is (she’s requesting a page from her IP address) and where node B is, but not node C (the exit node) or the destination webserver. Node B knows A and C, but neither the user’s IP or her destination. Node C, the exit node, knows node B and the destination. Monitor node A and you get a list of IPs accessing Tor… but no sense for where they were trying to go using Tor. Monitor node C – as the Wikileaks participant says he was doing – and you get a very good sense of what users are doing through your node. In 2007, Swedish security expert Dan Egerstad ran a packet sniffer – a tool designed to look for specific strings within a stream of data – to monitor the traffic through five exit nodes his firm maintained. By sniffing for strings likely to identify email or web passwords, Egerstad was able to collect an impressive (scary, embarrasing) set of information. His project is well-described in an Ars Electronica article: http://arstechnica.com/security/news...-passwords.ars What Egerstad was able to do isn’t a bug in Tor, per se. Tor promises to obscure the connection between your originating IP address and the web server you are visiting – and it does, in all but a small set of esoteric, lab-based attacks. What Tor doesn’t do – and what Tor will happily tell you it doesn’t do, if you read their careful warnings closely enough – is protect you from being stupid online. Logging into a sensitive service using a http:// – rather than https:/// – interface is a stupid thing to do, and Tor won’t prevent you from making that mistake. To be safe and anonymous, you need to make changes in your behavior – use secure mail protocols, log into secure services via HTTPS interfaces – and understand what Tor does and doesn’t do. Andrew Lih has an excellent piece explaining the implications of Egerstad’s research, titled “Assume Tor Exit Nodes Are Monitored” – http://www.andrewlih.com/blog/2007/0...are-monitored/ . That’s good advice. Egerstad’s experiment evidently turned up precisely the sort of information that could be used to start a document collection like Wikileaks. See http://www.wired.com/politics/securi.../embassy_hacks , a Wired story which shoes Egerstad reading the correspondence of India’s ambassador to China, amongst others. What of the Chinese hackers? Egerstad conducted his experiment because he was worried that intelligence agencies might be running rogue Tor nodes – as he was – to monitor them – as he was doing. I don’t know of credible reports that this has happened, but I can see how a story about Egerstad monitoring Tor and intercepting passwords and documents to demonstrate that the Chinese could use this technique could morph into the situation described in the New Yorker article. Let me just make clear – I have no basis on which to suggest that Egerstad has any connection to Wikileaks. I am simply mentioning that there’s a well-documented story within the security community whose basic outlines are similar to the story told in this New Yorker piece. As for the ethical implications? Don’t blame Tor – it does what it says on the wrapper. It’s just that no one reads or understands the wrapper. Are there ethnical concerns about someone who’d run an exit node to spy on users? Yes, there are. But Egerstad’s point was a valid one – anyone running an exit node can spy as he did, and people need to understand that to use Tor safely. Entertain a theoretical for a moment, that Wikileaks received a cache of information obtained by Egerstad, who sniffed passwords and then used those passwords to enter systems, reading the email of the Indian ambassador to China and cacheing all documents found. Should Wikileaks delete those documents? Or selectively release some because they have political relevance? I’d be pretty uncomfortable defending widescale system intrusion and document perusal in that case. These wouldn’t be documents from whistleblowers – this would be the contents of filecabinets obtained through a (smart, sophisticated, non-destructive) form of breaking and entering. But that’s my read on the situation, and not necessarily the read you’d get from Julian… or at least, that’s what I got from the author’s piece. Hope some of that’s helpful. http://ryansholin.com/2010/05/31/wik...#comment-17691  Google Ditches Windows on Security Concerns David Gelles and Richard Waters Google is phasing out the internal use of Microsoft’s ubiquitous Windows operating system because of security concerns, according to several Google employees. The directive to move to other operating systems began in earnest in January, after Google’s Chinese operations were hacked, and could effectively end the use of Windows at Google, which employs more than 10,000 workers internationally. “We’re not doing any more Windows. It is a security effort,” said one Google employee. “Many people have been moved away from [Windows] PCs, mostly towards Mac OS, following the China hacking attacks,” said another. New hires are now given the option of using Apple’s Mac computers or PCs running the Linux operating system. “Linux is open source and we feel good about it,” said one employee. “Microsoft we don’t feel so good about.” In early January, some new hires were still being allowed to install Windows on their laptops, but it was not an option for their desktop computers. Google would not comment on its current policy. Windows is known for being more vulnerable to attacks by hackers and more susceptible to computer viruses than other operating systems. The greater number of attacks on Windows has much to do with its prevalence, which has made it a bigger target for attackers. Employees wanting to stay on Windows required clearance from “quite senior levels”, one employee said. “Getting a new Windows machine now requires CIO approval,” said another employee. In addition to being a semi-formal policy, employees themselves have grown more concerned about security since the China attacks. “Particularly since the China scare, a lot of people here are using Macs for security,” said one employee. Employees said it was also an effort to run the company on Google’s own products, including its forthcoming Chrome OS, which will compete with Windows. “A lot of it is an effort to run things on Google product,” the employee said. “They want to run things on Chrome.” The hacking in China hastened the move. “Before the security, there was a directive by the company to try to run things on Google products,” said the employee. “It was a long time coming.” The move created mild discontent among some Google employees, appreciative of the choice in operating systems granted to them - an unusual feature in large companies. But many employees were relieved they could still use Macs and Linux. “It would have made more people upset if they banned Macs rather than Windows,” he added. Google and Microsoft compete on many fronts, from search, to web-based email, to operating systems. While Google is the clear leader in search, Windows remains the most popular operating system in the world by a large margin, with various versions accounting for more than 80 per cent of installations, according to research firm Net Applications. http://www.ft.com/cms/s/2/d2f3f04e-6...44feab49a.html  Google Chrome OS Confirmed for Late-Fall 2010 Chris Davies Google has announced that it expects the first Chrome OS netbooks to launch in late fall, with Sundar Pichai – head of the Chrome project – using Computex 2010 to narrow down the previous “second half of 2010″ window. As the search giant has hinted at previously, they plan on being careful in how Chrome OS is delivered; “We will be selective on how we come to market because we want to deliver a great user experience,” Pinchai said, “we’re thinking on both the hardware and software levels.” While Microsoft has previously dismissed Google’s open-source OS ambitions, Pinchai reckons their reasoning – that developers would need to create new versions of apps, and may be reluctant to do so – is unfounded since Chrome OS has at its core a standards-compliant browser. ”You don’t need to redesign Gmail for it to work on Chrome. Facebook does not need to write a new app for Chrome” he suggested. It remains to be seen who will be the first netbook company to produce a machine running Chrome OS, though both Acer and ASUS have said they intend to release such models. http://www.slashgear.com/google-chro...-2010-0287952/  Adobe Warns of Flash, PDF Zero-Day Attacks Ryan Naraine Adobe issued an alert late Friday night to warn about zero-day attacks against an unpatched vulnerability in its Reader and Flash Player software products. The vulnerability, described as critical, affects Adobe Flash Player 10.0.45.2 and earlier versions for Windows, Macintosh, Linux and Solaris operating systems. It also affects the authplay.dll component that ships with Adobe Reader and Acrobat 9.x for Windows, Macintosh and UNIX operating systems, Adobe said. From Adobe’s advisory: This vulnerability (CVE-2010-1297) could cause a crash and potentially allow an attacker to take control of the affected system. There are reports that this vulnerability is being actively exploited in the wild against both Adobe Flash Player, and Adobe Reader and Acrobat. The Flash Player 10.1 Release Candidate “does not appear to be vulnerable,” the company said. Mitigation Guidance In the absence of a patch, Adobe recommends deleting, renaming, or removing access to the authplay.dll file that ships with Adobe Reader and Acrobat 9.x. This will mitigate the threat but users will experience a non-exploitable crash or error message when opening a PDF file that contains SWF content. The authplay.dll that ships with Adobe Reader and Acrobat 9.x for Windows is typically located at C:\Program Files\Adobe\Reader 9.0\Reader\authplay.dll for Adobe Reader or C:\Program Files\Adobe\Acrobat 9.0\Acrobat\authplay.dll for Acrobat. Adobe Reader and Acrobat 8.x are confirmed not vulnerable. Adobe security chief Brad Arkin said the company received the first malicious sample around 10:30 AM on Friday. There is no information on when a patch will be available. http://www.zdnet.com/blog/security/a...y-attacks/6606  Viral Clickjacking 'Like' Worm Hits Facebook Users Hundreds of thousands of Facebook users have fallen for a social-engineering trick which allowed a clickjacking worm to spread quickly over Facebook this holiday weekend. Affected profiles can be identified by seeing that the Facebook user has apparently "liked" a link: Girl gets owned after a police officer reads her status message Messages seen being used by the spammers include: "LOL This girl gets OWNED after a POLICE OFFICER reads her STATUS MESSAGE." "This man takes a picture of himself EVERYDAY for 8 YEARS!!" "The Prom Dress That Got This Girl Suspended From School." "This Girl Has An Interesting Way Of Eating A Banana, Check It Out!" Clicking on the links takes Facebook users to what appears to be a blank page with just the message "Click here to continue". However, clicking at any point of the page publishes the same message (via an invisible iFrame) to their own Facebook page, in a similar fashion to the "Fbhole" worm we saw earlier this month. The trick, which uses a clickjacking exploit, means that visiting users are tricked into "liking" a page without necessarily realising they are recommending it to all of their Facebook friends. Unfortunately, as we're all too aware, messages such as "LOL This girl gets OWNED after a POLICE OFFICER reads her STATUS MESSAGE.", "This man takes a picture of himself EVERYDAY for 8 YEARS!!", "The Prom Dress That Got This Girl Suspended From School." and "This Girl Has An Interesting Way Of Eating A Banana, Check It Out!" are exactly the kind of content that people will click on on Facebook. Sophos detects the offending webpages as being infected by Troj/Iframe-ET. If you believe you may have been hit by this attack, view the recent activity on your news feed and delete entries related to the above links. Furthermore, you should view your profile, click on your Info tab and remove any of the pages from your "Likes and interests" section. If you're regular user of Facebook, you should join the Sophos page on Facebook to be kept informed of the latest security threats. http://www.sophos.com/blogs/gc/g/201...acebook-users/  Mobile Game Trojan Calls the South Pole Freeware games can actually cost you more money than their pay-to-play cousins, as mobile gamers in the UK have learned. A “booby-trapped” version of a popular Windows Mobile game has been sneakily spending their money while they sleep – by dialling phone numbers in the Antarctic behind their backs. Described as a “mobile version of the classic Counter-Strike“, the pirated title contains hidden code which has been silently ringing numbers in the Antarctic block, the Dominican Republic, Somalia and other premium locations, simple calls which cost roughly 5 euro (more than US$6) per minute from a UK mobile phone. The original game – 3D Anti Terrorist Action – was released as a shareware demo, before Russian virus artists got a hold of it, made a few tweaks and then published a freeware version, containing their dialler – Trojan.WinCE.Terdial.a. The dodgy dialler was discovered back in March, but as the pirated game makes its way to more and more websites offering free Windows mobile applications, it’s still making calls, and taking advantage of people looking to get something for nothing. It seems that mobile phone tricks are gaining in popularity as virtually everything done on the phone will incur a charge – then it’s just a matter of siphoning part of that cash flow back to the developers… much better rate of return than Nigerian scam emails! In fact, Kaspersky Labs reports that the growth rate for PC viruses and trojans has been flattening in the past three years, but they have seen more than 200% growth in mobile threats. Obviously, common sense dictates a pretty simple way to avoid this – don’t play mobile games you’ve found on random sites, and make sure you’re completely informed about what you’re installing onto your handset. If you’re truly concerned, blocking international dialling from your mobile may also be a smart option. However, if this is all a bit late and you’re infected – the XDA developers forum contains a few tips on how to remove the trojan. …incidentally, we hear that the game itself is pretty rubbish, just so you know. http://www.gamepron.com/news/2010/05...he-south-pole/  Surveillance Software Knows What a Camera Sees Software offers a running commentary to ease video searching and analysis. Tom Simonite A prototype computer vision system can generate a live text description of what's happening in a feed from a surveillance camera. Although not yet ready for commercial use, the system demonstrates how software could make it easier to skim or search through video or image collections. It was developed by researchers at the University of California, Los Angeles, in collaboration with ObjectVideo of Reston, VA. "You can see from the existence of YouTube and all the other growing sources of video around us that being able to search video is a major problem," says Song-Chun Zhu, lead researcher and professor of statistics and computer science at UCLA. "Almost all search for images or video is still done using the surrounding text," he says. Zhu and UCLA colleagues Benjamin Yao and Haifeng Gong developed a new system, called I2T (Image to Text), which is intended to change that. It puts a series of computer vision algorithms into a system that takes images or video frames as input, and spits out summaries of what they depict. "That can be searched using simple text search, so it's very human-friendly," says Zhu. The team applied the software to surveillance footage in collaboration with Mun Wai Lee of ObjectVideo to demonstrate the strength of I2T. Systems like it might help address the fact that there are more and more surveillance cameras--on the streets and in military equipment, for instance--while the number of people working with them remains about the same, says Zhu. The first part of I2T is an image parser that decomposes an image--meaning it removes the background, and objects like vehicles, trees, and people. Some objects can be broken down further; for example, the limbs of a person or wheels of a car can be separated from the object they belong to. Next, the meaning of that collection of shapes is determined. "This knowledge representation step is the most important part of the system," says Zhu, explaining that this knowledge comes from human smarts. In 2005, Zhu established the nonprofit Lotus Hill Institute in Ezhou, China, and, with some support from the Chinese government, recruited about 20 graduates of local art colleges to work full-time to annotate a library of images to aid computer vision systems. The result is a database of more than two million images containing objects that have been identified and classified into more than 500 categories. To ensure that workers annotate images in a standard way, software guides them as they work. It uses versions of the algorithms that will eventually benefit from the final data to pick out the key objects for a person to classify, and it suggests how they might be classified based on previous data. The objects inside images are classified into a hierarchy of categories based on Princeton's WordNet database, which organizes English words into groups according to their meanings. "Once you have the image parsed using that system that also includes the meaning, transcription into the natural language is not too hard," says Zhu, who makes some of the data available for free to other researchers. "It is high-quality data and we hope that more people are going to use this," he says. The video-processing system also uses algorithms that can describe the movement of objects in successive frames. It generates sentences like "boat1 follows boat2 between 35:56 and 37:23" or "boat3 approaches maritime marker at 40:01." "Sometimes it can do a match on an object that has left and reentered a scene," says Zhu, "and say, for example, this is probably a certain car again." It is also possible to define virtual "trip wires" to help it describe certain events, like a car running a stop sign (see video). Although the system demonstrates a step toward what Zhu calls a "grand vision in computer science," I2T is not yet ready for commercialization. Processing surveillance footage is relatively easy for the software because the camera--and hence the background in a scene--is static; I2T is far from capable of recognizing the variety of objects or situations a human could. If set loose on random images or videos found online, for example, I2T would struggle to perform so well. Improving the system's knowledge of how to identify objects and scenes by adding to the number of images in the Lotus Hill Institute training set should help, says Zhu. The I2T system underlying the surveillance prototype is powerful, says Zu Kim, a researcher at the University of California, Berkeley, who researches the use of computer vision to aid traffic surveillance and vehicle tracking. "It's a really nice piece of work," he says, even if it can't come close to matching human performance. Kim explains that better image parsing is relevant to artificial intelligence work of all kinds. "There are very many possibilities for a good image parser--for example, allowing a blind person to understand an image on the Web." Kim can see other uses for generating text from video, pointing out that it could be fed into a speech synthesizer. "It could be helpful if someone was driving and needed to know what a surveillance camera was seeing." But humans are visual creatures, he adds, and in many situations could be expected to prefer to decide what's happening in an image or a video for themselves. http://www.technologyreview.com/computing/25439/?a=f  Are Cameras the New Guns? Are Cameras the New Guns?In response to a flood of Facebook and YouTube videos that depict police abuse, a new trend in law enforcement is gaining popularity. In at least three states, it is now illegal to record any on-duty police officer. Even if the encounter involves you and may be necessary to your defense, and even if the recording is on a public street where no expectation of privacy exists. The legal justification for arresting the "shooter" rests on existing wiretapping or eavesdropping laws, with statutes against obstructing law enforcement sometimes cited. Illinois, Massachusetts, and Maryland are among the 12 states in which all parties must consent for a recording to be legal unless, as with TV news crews, it is obvious to all that recording is underway. Since the police do not consent, the camera-wielder can be arrested. Most all-party-consent states also include an exception for recording in public places where "no expectation of privacy exists" (Illinois does not) but in practice this exception is not being recognized. Massachusetts attorney June Jensen represented Simon Glik who was arrested for such a recording. She explained, "[T]he statute has been misconstrued by Boston police. You could go to the Boston Common and snap pictures and record if you want." Legal scholar and professor Jonathan Turley agrees, "The police are basing this claim on a ridiculous reading of the two-party consent surveillance law - requiring all parties to consent to being taped. I have written in the area of surveillance law and can say that this is utter nonsense." The courts, however, disagree. A few weeks ago, an Illinois judge rejected a motion to dismiss an eavesdropping charge against Christopher Drew, who recorded his own arrest for selling one-dollar artwork on the streets of Chicago. Although the misdemeanor charges of not having a peddler's license and peddling in a prohibited area were dropped, Drew is being prosecuted for illegal recording, a Class I felony punishable by 4 to 15 years in prison. In 2001, when Michael Hyde was arrested for criminally violating the state's electronic surveillance law - aka recording a police encounter - the Massachusetts Supreme Judicial Court upheld his conviction 4-2. In dissent, Chief Justice Margaret Marshall stated, "Citizens have a particularly important role to play when the official conduct at issue is that of the police. Their role cannot be performed if citizens must fear criminal reprisals…." (Note: In some states it is the audio alone that makes the recording illegal.) The selection of "shooters" targeted for prosecution do, indeed, suggest a pattern of either reprisal or an attempt to intimidate. Glik captured a police action on his cellphone to document what he considered to be excessive force. He was not only arrested, his phone was also seized. On his website Drew wrote, "Myself and three other artists who documented my actions tried for two months to get the police to arrest me for selling art downtown so we could test the Chicago peddlers license law. The police hesitated for two months because they knew it would mean a federal court case. With this felony charge they are trying to avoid this test and ruin me financially and stain my credibility." Hyde used his recording to file a harassment complaint against the police. After doing so, he was criminally charged. In short, recordings that are flattering to the police - an officer kissing a baby or rescuing a dog - will almost certainly not result in prosecution even if they are done without all-party consent. The only people who seem prone to prosecution are those who embarrass or confront the police, or who somehow challenge the law. If true, then the prosecutions are a form of social control to discourage criticism of the police or simple dissent. A recent arrest in Maryland is both typical and disturbing. On March 5, 24-year-old Anthony John Graber III's motorcycle was pulled over for speeding. He is currently facing criminal charges for a video he recorded on his helmet-mounted camera during the traffic stop. The case is disturbing because: 1) Graber was not arrested immediately. Ten days after the encounter, he posted some of he material to YouTube, and it embarrassed Trooper J. D. Uhler. The trooper, who was in plainclothes and an unmarked car, jumped out waving a gun and screaming. Only later did Uhler identify himself as a police officer. When the YouTube video was discovered the police got a warrant against Graber, searched his parents' house (where he presumably lives), seized equipment, and charged him with a violation of wiretapping law. 2) Baltimore criminal defense attorney Steven D. Silverman said he had never heard of the Maryland wiretap law being used in this manner. In other words, Maryland has joined the expanding trend of criminalizing the act of recording police abuse. Silverman surmises, "It's more [about] ‘contempt of cop' than the violation of the wiretapping law." 3) Police spokesman Gregory M. Shipley is defending the pursuit of charges against Graber, denying that it is "some capricious retribution" and citing as justification the particularly egregious nature of Graber's traffic offenses. Oddly, however, the offenses were not so egregious as to cause his arrest before the video appeared. Almost without exception, police officials have staunchly supported the arresting officers. This argues strongly against the idea that some rogue officers are overreacting or that a few cops have something to hide. "Arrest those who record the police" appears to be official policy, and it's backed by the courts. Carlos Miller at the Photography Is Not A Crime website offers an explanation: "For the second time in less than a month, a police officer was convicted from evidence obtained from a videotape. The first officer to be convicted was New York City Police Officer Patrick Pogan, who would never have stood trial had it not been for a video posted on Youtube showing him body slamming a bicyclist before charging him with assault on an officer. The second officer to be convicted was Ottawa Hills (Ohio) Police Officer Thomas White, who shot a motorcyclist in the back after a traffic stop, permanently paralyzing the 24-year-old man." When the police act as though cameras were the equivalent of guns pointed at them, there is a sense in which they are correct. Cameras have become the most effective weapon that ordinary people have to protect against and to expose police abuse. And the police want it to stop. Happily, even as the practice of arresting "shooters" expands, there are signs of effective backlash. At least one Pennsylvania jurisdiction has reaffirmed the right to video in public places. As part of a settlement with ACLU attorneys who represented an arrested "shooter," the police in Spring City and East Vincent Township adopted a written policy allowing the recording of on-duty policemen. As journalist Radley Balko declares, "State legislatures should consider passing laws explicitly making it legal to record on-duty law enforcement officials." http://gizmodo.com/5553765/are-cameras-the-new-guns  We control the horizontal Lieberman Bill Gives Feds ‘Emergency’ Powers to Secure Civilian Nets Noah Shachtman Joe Lieberman wants to give the federal government the power to take over civilian networks’ security, if there’s an “imminent cyber threat.” It’s part of a draft bill, co-sponsored by Senators Lieberman and Susan Collins, that provides the Department of Homeland Security broad authority to ensure that “critical infrastructure” stays up and running in the face of a looming hack attack. The government’s role in protecting private firms’ networks is one of the most contentious topics in information security today. Several bills are circulating on Capitol Hill on how to keep power and transportation and financial firms running in the event of a so-called “cybersecurity emergency.” Last week, Deputy Defense Secretary William Lynn floated the idea of extending a controversial cybersurveillance program to hacker-proof the firms. Meanwhile, the military’s new Cyber Command is readying itself to march to these companies’ aid. Lieberman and Collins’ solution is one of the more far-reaching proposals. In the Senators’ draft bill, “the President may issue a declaration of an imminent cyber threat to covered critical infrastructure.” Once such a declaration is made, the director of a DHS National Center for Cybersecurity and Communications is supposed to “develop and coordinate emergency measures or actions necessary to preserve the reliable operation, and mitigate or remediate the consequences of the potential disruption, of covered critical infrastructure.” “The owner or operator of covered critical infrastructure shall comply with any emergency measure or action developed by the Director,” the bill adds. These emergency measures are supposed to remain in place for no more than 30 days. But they can be extended indefinitely, a month at a time. The DHS cybersecurity director has to ensure that the emergency measures “represent the least disruptive means feasible” and that “the privacy and civil liberties of United States persons are protected,” according to the bill. It also allows the private firms to handle network threats on their own — if DHS approves of the measures. Senate staffers familiar with the bill acknowledge that it grants broad powers over private businesses; the staffers couldn’t think of an analog in the physical world, except for the Federal Aviation Administration’s authority to ground air traffic after 9/11. But the staffers say that the emergency powers will only apply to a relatively small number of companies, and only in the most extreme cases — when an electronic exploit might cause “catastrophic regional or national damage” resulting in “thousands of lives or billions of dollars” lost. In order for the President to declare such an emergency, there would have to be knowledge both of a massive network flaw — and information that someone was about to leverage that hole to do massive harm. For example, the recent “Aurora” hack to steal source code from Google, Adobe and other companies wouldn’t have qualified, one Senate staffer noted: “It’d have to be Aurora 2, plus the intel that country X is going to take us down using that vulnerability.” A second staffer suggested that evidence of hackers looking to leverage something like the massive Conficker worm — which infected millions of machines and was seemingly poised in April 2009 to unleash something nefarious — might trigger the bill’s emergency provisions. “You could argue there’s some threat information built in there,” the staffer said. The Lieberman/Collins bill is hardly the the most extreme cybersecurity proposal that’s circulated on Capitol Hill in recent years. That dubious distinction belongs to a bill from Senators Jay Rockefeller and Olympia Snowe that empowered the feds to “order the disconnection of any Federal Government or United States critical infrastructure information systems or networks in the interest of national security.” That provision was neutered after a public outcry. Now, it calls on the U.S. government to “develop and rehearse detailed response and restoration plans” in the event of a major network threat. http://www.wired.com/dangerroom/2010...-civilian-net/  Surfers wanted Most U.S. Broadband Users Don't Know Connection Speeds Four of five U.S. broadband users are unaware of the speed of their connections, the Federal Communications Commission said on Tuesday. A similar survey conducted by Abt/SRBI and Princeton Survey Research Associates International from April 19 to May 2 also found that one in six American mobile phone users have been shocked by surprise fees and charges in their monthly bills. The FCC has increasingly focused on consumer protection issues surrounding broadband speeds and mobile phone charges, including fees associated with ending a contract early. "Speed matters," FCC Chairman Julius Genachowski said in a statement. "The more broadband subscribers know about what speeds they need and what speeds they get, the more they can make the market work and push faster speeds over broadband networks." In March, the FCC unveiled an Internet speed test tool at www.broadband.gov for consumers to clock the speed of their connection. The FCC said it is also seeking 10,000 U.S. volunteers to participate in a scientific study to measure home broadband speed in the U.S. Specialized hardware will be installed in the homes of volunteers to measure the performance of all the country's major Internet service providers across geographic regions and service tiers, the FCC said. The FCC said it is partnering with SamKnows Limited, the same firm that conducted a similar test in the United Kingdom, to carry out the U.S. study. The biggest U.S. broadband providers are Comcast Corp, Time Warner Cable Inc, AT&T Inc and Verizon Communications Inc. (Reporting by John Poirier, Editing by Leslie Gevirtz) http://www.reuters.com/article/idUSTRE6505R820100601  Iridium Pushes Ahead Satellite Project Gabriel Perna Iridium (IRDM) continues its push into the market for satellite data and telemetry services, as it announced the company that would build its second generation of satellites. Amid a great deal of pomp and circumstance including the ringing of the opening bell at Nasdaq, Iridium announced Thales Alenia Space, a joint venture between French owned Thales (67%) and Italian based Finmeccanica (33%), would be designing and building the new satellites. Iridium's old network of 66 satellites was designed for voice calls; the new satellites will also be able to handle data more efficiently, and include cameras as well. The company also plans to share the satellite platforms with some scientists for use in studying the Earth. Iridium's rapid growth - the company claims 360,000 subscribers - has put it in the top tier of satellite telephone providers. London-based Inmarsat, which provides maritime and airline communications, is one of Iridium's direct competitors. Inmarsat, which trades on the London Stock Exchange, has a market capitalization of GBP 3.473 billion (US$5.08 billion) and has long dominated the maritime and aviation markets. But Iridium has made inroads in telemetry from places such as offshore oil wells, as well as wining a contract from the U.S. Department of Defense. On top of that, Iridium's satellites are in low earth orbit, or about 485 miles (780 kilometers) up. That cuts down the time for the signal to reach the satellite, as well as the amount of power required. Inmarsat's constellation is in geosynchronous orbit - or 23,000 miles (35,700 km) above the earth's surface. At that distance a signal takes a full quarter of a second to get to the satellite and back - a perceptible lag when speaking. Glenn Tongue, managing partner at T2 Partners, is one investor who is bullish on Iridium's future - his fund has bought into the company. He adds that the company currently has no debt on its balance sheet and has $147 million in cash at the end of the first quarter of 2010. The smaller power requirements for its phones mean longer battery life and will help it compete in that market, he adds. In addition, the value of Iridium to the military, Tongue says, gives it an extra layer of protection as the Department of Defense would not want to see the company fail. Not all are so optimistic. Iridium is up against an entrenched competitor in Inmarsat, says Olivier Moral, an analyst at HSBC Bank in Paris. He notes that Inmarsat has only to do incremental spending - while they have satellite launches scheduled for 2011 they aren't replacing a whole constellation. Inmarsat has also demonstrated profitability for many years, and plans to offer its own new satellite phone and data services. Iridium's project will consist of 66 satellites, with six spares in low earth orbit, and nine more on the ground. According to Iridium CEO Matt Desch, the cost will total approximately $2.9 billion. Coface, the French government export credit agency, is set to guarantee 95% of a $1.8 billion credit facility for the project. That facility is being arranged with a group of international banks and is expected to be complete in the summer. The contract between with Thales allows work on the project to start immediately. The slated completion for Iridium NEXT is between 2015 and 2017, when Iridium's current satellites are no longer useful. Many remember Iridium from its first iteration in the late 1990s, when it was a poster child for financial hubris. At that time the company raised $5 billion in investment, including $1.5 billion in loans. In 1999 Iridium filed for bankruptcy protection. The company was re-formed in 2001 by a group of private investors. http://www.ibtimes.com/articles/2646...s-contract.htm  AT&T Warns Customer that Emailing the CEO Will Result in a Cease and Desist Letter Nilay Patel Sure, Steve Jobs might be a one-man email PR machine, but his pal Randall Stephenson at AT&T doesn't appear to be quite as gregarious -- as reader Giorgio Galante found out today, sending AT&T's CEO two emails in two weeks results in a phone call from AT&T's Executive Response Team and a warning that further emails will result in a cease and desist letter. What did Giorgio's emails say? The first was a request to bump up his iPhone eligibility date and a request for a tethering option, and today's outlined his displeasure with AT&T's new data rates and ultimate decision to switch to Sprint and the EVO 4G. That prompted "Brent" to call Giorgio back and thank him for the feedback, but also politely warn him that further emails would be met with legal action. Ouch. As you'd expect, AT&T just lost itself a customer. We've followed up with Ma Bell to find out exactly why they went the lawyer route instead of oh, say, filtering Randall's email -- we'll let you know what they say. P.S.- Amusingly, Giorgio says he emailed both Randall Stephenson and Steve Jobs last year about offering tethering and actually got a response from Steve -- maybe these two CEOs need to talk about more than data rates and service quality the next time they meet up. http://www.engadget.com/2010/06/02/a...lt-in-a-cease/  Venting Online, Consumers Can Find Themselves in Court Dan Frosch After a towing company hauled Justin Kurtz’s car from his apartment complex parking lot, despite his permit to park there, Mr. Kurtz, 21, a college student in Kalamazoo, Mich., went to the Internet for revenge. Outraged at having to pay $118 to get his car back, Mr. Kurtz created a Facebook page called “Kalamazoo Residents against T&J Towing.” Within two days, 800 people had joined the group, some posting comments about their own maddening experiences with the company. T&J filed a defamation suit against Mr. Kurtz, claiming the site was hurting business and seeking $750,000 in damages. Web sites like Facebook, Twitter and Yelp have given individuals a global platform on which to air their grievances with companies. But legal experts say the soaring popularity of such sites has also given rise to more cases like Mr. Kurtz’s, in which a business sues an individual for posting critical comments online. The towing company’s lawyer said that it was justified in removing Mr. Kurtz’s car because the permit was not visible, and that the Facebook page was costing it business and had unfairly damaged its reputation. Some First Amendment lawyers see the case differently. They consider the lawsuit an example of the latest incarnation of a decades-old legal maneuver known as a strategic lawsuit against public participation, or Slapp. The label has traditionally referred to meritless defamation suits filed by businesses or government officials against citizens who speak out against them. The plaintiffs are not necessarily expecting to succeed — most do not — but rather to intimidate critics who are inclined to back down when faced with the prospect of a long, expensive court battle. “I didn’t do anything wrong,” said Mr. Kurtz, who recently finished his junior year at Western Michigan University. “The only thing I posted is what happened to me.” Many states have anti-Slapp laws, and Congress is considering legislation to make it harder to file such a suit. The bill, sponsored by Representatives Steve Cohen of Tennessee and Charlie Gonzalez of Texas, both Democrats, would create a federal anti-Slapp law, modeled largely on California’s statute. Because state laws vary in scope, many suits are still filed every year, according to legal experts. Now, with people musing publicly online and businesses feeling defenseless against these critics, the debate over the suits is shifting to the Web. “We are beyond the low-tech era of people getting Slapped because of letters they wrote to politicians or testimony they gave at a City Council meeting,” said George W. Pring, a University of Denver law professor who co-wrote the 1996 book “Slapps: Getting Sued For Speaking Out.” Marc Randazza, a First Amendment lawyer who has defended clients against suits stemming from online comments, said he helped one client, Thomas Alascio, avoid a lawsuit last year after he posted negative remarks about a Florida car dealership on his Twitter account. “There is not a worse dealership on the planet,” read one post, which also named the dealership. The dealership threatened to sue Mr. Alascio if he did not remove the posts. Mr. Randazza responded in a letter that although Mr. Alascio admitted that the dealership might not be the worst in the world, his comments constituted protected speech because they were his opinion. While the dealership did not sue, that outcome is unusual, said Mr. Randazza, who conceded that sometimes the most pragmatic approach for a Slapp defendant is to take back the offending comments in lieu of a lawsuit. In the past, Mr. Randazza said, if you criticized a business while standing around in a bar, it went “no further than the sound of your voice.” Now, however, “there’s a potentially permanent record of it as soon as you hit ‘publish’ on the computer,” he said. “It goes global within minutes.” Laurence Wilson, general counsel for the user review site Yelp, said a handful of lawsuits in recent years had been filed against people who posted critical reviews on the site, including a San Francisco chiropractor who sued a former patient in 2008 over a negative review about a billing dispute. The suit was settled before going to court. “Businesses, unfortunately, have a greater incentive to remove a negative review than the reviewer has in writing the review in the first place,” Mr. Wilson said. Recognizing that lawsuits can bring more unwanted attention, one organization has taken a different tack. The group Medical Justice, which helps protect doctors from meritless malpractice suits, advises its members to have patients sign an agreement that gives doctors more control over what patients post online. Dr. Jeffrey Segal, chief executive of Medical Justice, said about half of the group’s 2,500 members use the agreement. “I, like everyone else, like to hear two sides of the story,” he said. “The problem is that physicians are foreclosed from ever responding because of state and federal privacy laws. In the rare circumstance that a posting is false, fictional or fraudulent, the doctor now has the tool to get that post taken down.” The federal bill, in the House Subcommittee on Courts and Competition Policy, would enable a defendant who believes he is being sued for speaking out or petitioning on a public matter to seek to have the suit dismissed. “Just as petition and free speech rights are so important that they require specific constitutional protections, they are also important enough to justify uniform national protections against Slapps,” said Mark Goldowitz, director of the California Anti-Slapp Project, which helped draft the bill. Under the proposed federal law, if a case is dismissed for being a Slapp, the plaintiff would have to pay the defendant’s legal fees. Mr. Randazza would not disclose specifics on the legal fees he has charged his clients, but he said the cost of defending a single Slapp suit “could easily wipe out the average person’s savings before the case is half done.” Currently, 27 states have anti-Slapp laws, and in two, Colorado and West Virginia, the judiciary has adopted a system to protect against such suits. But the federal bill would create a law in states that do not have one and offer additional protections in those that do, Mr. Goldowitz said. In Michigan, which does not have an anti-Slapp measure, Mr. Kurtz’s legal battle has made him a local celebrity. His Facebook page has now grown to more than 12,000 members. “This case raises interesting questions,” said the towing company’s lawyer, Richard Burnham. “What are the rights to free speech? And even if what he said is false, which I am convinced, is his conduct the proximate cause of our loss?” On April 30, Mr. Kurtz and his lawyers asked a judge to dismiss the suit by T&J, which has received a failing grade from the local Better Business Bureau for complaints over towing legally parked cars. Mr. Kurtz is also countersuing, claiming that T&J is abusing the legal process. “There’s no reason I should have to shut up because some guy doesn’t want his dirty laundry out,” Mr. Kurtz said. “It’s the power of the Internet, man.” http://www.nytimes.com/2010/06/01/us/01slapp.html  Can Schools Punish Students for Web Posts? Maryclaire Dale A U.S. appeals court heard arguments Thursday over whether school officials can discipline students for making lewd, harassing or juvenile Internet postings from off-campus computers. Two students from two different Pennsylvania school districts are fighting suspensions they received for posting derisive profiles of their principals on MySpace from home computers. The American Civil Liberties Union argued that school officials infringe on student's free speech rights when they reach beyond school grounds in such cases to impose discipline. "While children are in school, they are under the custody and tutelage of the school," ACLU lawyer Witold Walczak argued Thursday in the 3rd U.S. Circuit Court of Appeals. "Once they leave the schoolhouse gate, you've got parents that come into play." But a lawyer for the Hermitage School District in western Pennsylvania offered a different view. "It's not a matter of where you throw the grenade, it's where the grenade lands," Anthony Sanchez said. The appeals court agreed to rehear the two cases in a rare en banc session — with all 14 eligible judges on the bench — after its judges issued conflicting rulings in the two cases in February. One three-judge panel upheld a girl's suspension, while another found the suspension of a boy unconstitutional. Such disparities are common around the country as school districts wrestle with how to address online behavior that can range from pranks to threats to cyberbullying. Some school officials mete out discipline, opening themselves to lawsuits, or refer cases to police. Occasionally, a targeted school employee sues the suspected culprit for defamation. David L. Hudson Jr., a scholar at the First Amendment Center in Nashville, Tenn., has reviewed many such cases across the country and said the extent of school officials' jurisdiction remains unsettled. Legal experts hope the Supreme Court will soon clarify the limits of school discipline for online speech that is posted offsite. Hudson told The Associated Press many school officials "would welcome further elucidation by the courts." The two school districts argued Thursday that the postings can be disruptive at school, and said they need to be able to maintain order. "The profile did create an immediate disruption which required immediate action," argued lawyer Jonathan Riba, who represents the Blue Mountain School District in eastern Pennsylvania. A 14-year-old Blue Mountain student who had been cited for a dress-code violation created a fake profile of a principal purportedly from Alabama. She used her principal's photograph and described him as a pedophile and mentioned a sex act. The girl later apologized, took down the page and was suspended for 10 days. "For a school administrator, one cannot be called a worse thing than a sexual predator of young children," Riba argued. But Walczak said no one, including the principal, took the profile seriously, and that the parody is protected under the First Amendment. He suggested other remedies for such behavior, from talking with the student and parents to calling police or counselors. The student's mother has said punishing the girl should have been left up to her. In the other case, Hickory High School senior Justin Layshock created a parody that said his principal smoked marijuana and kept beer behind his desk. The Hermitage School District said it substantially disrupted school operations. Layshock was suspended and the principal sued him. On Thursday, the judges threw a barrage of hypotheticals at the lawyers, asking if it mattered if the student intended to harm the target or if the offending site was accessed at school. Chief Judge Theodore A. McKee suggested yet another response to the "buzz" among students about outrageous postings. "Teachers might say this is a teachable moment," McKee said. "Maybe in retrospect, that's the best way to deal with it, to get the students talking about the hurtfulness of the conduct." The court did not indicate when it would rule. http://skunkpost.com/news.sp?newsId=2535  Baseball Seeks Halt to Porn, Indecency on MLB.com[ Major League Baseball has asked a judge for a subpoena to help it identify people using Internet services provided by Charter Communications Inc to post pornography and other indecent material on the MLB.com website. According to papers filed Thursday in the New York State Supreme Court in Manhattan, one or more people have since July 2009 posted dozens of "threatening, abusive, obscene, vulgar, demeaning, offensive, pornographic, profane, sexually explicit, indecent and inappropriate" messages and images on MLB.com message boards. Some postings threatened a person named "McCabe" with unwanted sexual acts, while others included images of what the users described as their genitalia, the court papers show. Saying the objectionable postings violate "all reasonable standards of decency," Major League Baseball said it has several times tried and failed to ban them, and traced the Internet protocol addresses used to post them to Charter. It is seeking a court order requiring Charter to disclose the identities of people associated with these addresses, so it can pursue appropriate action. A Charter spokeswoman had no immediate comment, saying the St. Louis-based company had not been served with the court papers. A lawyer for Major League Baseball did not immediately return a call seeking comment. The case is In re: Application of MLB Advanced Media LP to Compel Disclosure of Charter Communications Inc, New York State Supreme Court, New York County, No. 107256/2010. (Reporting by Jonathan Stempel, editing by Gerald E. McCormick) http://www.reuters.com/article/idUST...technologyNews  M.I.A. Blasts New York Times Writer in Song Monica Herrera Recording artist M.I.A. takes aim at "journalists," "haters" and "racists" in a new song called "I'm a Singer," which she posted to her official website Sunday in response to a New York Times profile. "So you wanna hear about my politics? I can show you things that would make you sick," M.I.A. raps on the song. "And the story's always f***ed by the time it hits/And why the hell would journalists be thick as s**t?/'Cause lies equals power equals politics." Written by Lynn Hirschberg, the New York Times piece contrasts M.I.A.'s lifestyle with her politicized image and music, particularly her connection to a militant Sri Lanka group, the Tamil Tigers, that has led some to describe her as a terrorist. "'I kind of want to be an outsider,' she said, eating a truffle-flavored French fry," Hirschberg writes of M.I.A. in the story. "'I don't want to make the same music, sing about the same stuff, talk about the same things. If that makes me a terrorist, then I'm a terrorist.'" M.I.A. tweeted angrily about the piece last week, saying, "News is an opinion!" and posting Hirschberg's cellphone number. Callers were directed to Hirschberg's voicemail, and the writer later described the move as "infuriating and not surprising" as well as "fairly unethical." M.I.A. also promised to post her unedited interview with Hirschberg on her website but has since posted two brief audio excerpts, one of which suggests that it was the writer who ordered the French fries. The New York Times profile isn't the only M.I.A. story generating controversy. The singer has been speaking to several outlets to promote her July 13 album, "/\/\ /\ Y /\" ("Maya"), and in an interview with Nylon, she shares her thoughts on Google and Facebook. "(They) were developed by the CIA, and when you're on there, you have to know that," she says. M.I.A. also recently criticized Justin Bieber and Lady Gaga, telling U.K. magazine NME that Bieber's music videos are "more violent and more of an assault to my eyes" than her controversial "Born Free" (in which redheaded boys are rounded up and shot by officers) and that Gaga is "not progressive, but she's a good mimic ... none of her music's reflective of how weird she wants to be or thinks she is." http://www.reuters.com/article/idUSTRE65101X20100602  An Action Star Is Born? Not Just Yet in ‘Prince’ Brooks Barnes In the opening scenes of “Prince of Persia: The Sands of Time,” a wise man cautions the title character, played by Jake Gyllenhaal, not to take on too much. The warning: “You’re just not ready for this.” The words proved an omen for Mr. Gyllenhaal in real life over the weekend, as an effort to recast him as an action hero — a star capable of anchoring a big summer movie — ended in disappointment. “Prince of Persia” sold an estimated $37.8 million in tickets in North American theaters over the holiday weekend, a weak performance for a film that cost about $200 million to make and carried global marketing costs of more than $100 million. “Prince of Persia,” from the producer Jerry Bruckheimer and Walt Disney Studios, entered the market in second place. DreamWorks Animation’s “Shrek Forever After” was No. 1 in its second week, with a strong $55.7 million, an indication that positive word of mouth has followed the film’s so-so box office start. Premium-priced 3-D tickets also helped. Total domestic sales for “Shrek Forever After” now stand at $145.5 million. The other new release of note, “Sex and the City 2,” was third, with about $37.1 million, according to Hollywood.com, which compiles box office statistics. Warner Brothers released this R-rated sequel, which cost about $100 million to make, on Thursday to grab any fans who planned to travel over the holiday. Adding in Thursday sales, “Sex and the City 2” sold a total of $51.4 million. Scathing critical reviews for the latest installment of this long-in-the-tooth franchise may have dented its appeal. Sales for the first five days of “Sex and the City 2” were down 24 percent, compared with its predecessor. “Prince of Persia,” based on a video game, started rolling out in international markets on May 21. Its global box office take now stands at $133.3 million. “We had a sensational weekend overseas,” said Chuck Viane, Walt Disney Studio’s president of distribution, noting solid returns in Russia and China in particular. Mr. Viane said he hoped “Prince of Persia” would get a boost in North America as the school year concluded in coming days. “I think we’re going to have a pretty good ride,” he said. Even so, Prince of Persia” has a Herculean climb to profitability if you factor in supersize paychecks for Mr. Bruckheimer and others, and the 50 percent cut taken by theater owners. What went wrong? Theories abound. The sensitive Mr. Gyllenhaal dived into the role, growing his hair long and chiseling his physique. But he has primarily found success in movies tailored to a narrower audience. Films based on video games don’t have good track records. And, Mr. Viane said, “an unbelievable collision of sporting events” over the weekend may have hurt the picture too. Marketing may also have played a role. Feedback from test audiences before the film’s release was hugely positive. When turnout is poor after good test screenings, it often suggests that the public doesn’t like what it sees in the marketing materials. Disney fired its top marketing executives in a management overhaul late last year and has only recently installed a new team. “Prince of Persia” is the third box office letdown in a row from Mr. Bruckheimer, whose last two films were “G-Force” and “Confessions of a Shopaholic.” His next, a fantasy starring Nicolas Cage called “The Sorcerer’s Apprentice,” is to be released July 14. “Iron Man 2” (Marvel Entertainment) was fourth in earnings over the holiday weekend, with about $20.6 million, giving it a new domestic total of more than $279 million. “Robin Hood” (Universal Pictures) was fifth, with about $13.6 million, bringing its domestic total to $86.3 million. Over all, domestic ticket sales stood at $182.2 million for the weekend, a 15 percent decline from the same period last year, according to Hollywood.com. http://www.nytimes.com/2010/06/01/movies/01box.html  Mobile TV's Last Frontier: U.S. and Europe Kevin J. O'Brien When South Korea plays Greece on June 12 in its World Cup soccer opener in Port Elizabeth, South Africa, life will not necessarily grind to a halt back in Seoul. Many fans will instead follow a live broadcast of the match on their mobile phones. In South Korea, free-to-air mobile TV is a five-year-old fact of life. According to the country’s broadcasters, 27 million people — 56 percent of the population — watch regularly. While South Koreans are the world leaders in mobile TV viewing, the technology is also catching on in China, southeast Asia, India, Africa and Latin America, where 80 million people now have cellphones that can receive free, live TV broadcasts. “There have been a lot of hype cycles with mobile TV technology,” said Anna Maxbauer, an analyst at IMS Research in Austin, Texas. “But with recent advances in battery life, and consumer acceptance, there is real potential for widespread viewing.” At least 40 million people are watching live TV this year on mobile phones, Ms. Maxbauer said. Most live in emerging markets where operators, which prefer to sell TV programming for a fee through their wireless networks, do not control the sale of handsets. Free, on-the-go viewing is common just about everywhere except the United States and Europe, where operator resistance and a maze of conflicting technical standards and program licensing hurdles have kept the technology out of the global mainstream. But that may be about to change, according to one handset maker. “This technology has huge potential,” said Hankil Yoon, the vice president of product strategy at Samsung, the South Korean electronics maker and U.S. cellphone market leader. “Our experience shows that people like watching TV on mobile phones, even on smaller screens. And they like watching it for free. It is only a matter of time before this goes global.” In the complex world of wireless communication, free-to-air mobile TV technology is relatively simple. With a tiny receiver chip and telescoping antenna, a mobile phone can receive free digital or analog programming like any other television. In South Korea, 25 million people watch free digital terrestrial broadcasts on mobile handsets and two million pay to subscribe to satellite programming, according to Korean broadcasters. The typical screen made by Samsung is a three-inch, or 7.6-centimeter, diagonal. Batteries support three to six hours of viewing. In Korea, free mobile TV broadcasts are interspersed with ads. “In the markets where people use this, we have found that viewing tends to be pretty high,” said Diana Jovin, a vice president for corporate marketing and business development at Telegent Systems, the leading mobile TV chip maker, which is based in Sunnyvale, California. Telegent is shipping about 750,000 chips each month to handset makers, most designed for viewing analog broadcasts in markets like Brazil, Peru, Argentina, Russia, Nigeria, Thailand, Egypt and China. Brazil is one of Telegent’s biggest markets. In Rio de Janiero, Marcelo Mendonça Guimarães, a 42-year-old taxi driver, said he watched local and national TV news on his mobile handset through his operator, Claro. “My analog TV phone gives me the opportunity to watch television news while I’m waiting for a fare, or when I am on a break,” Mr. Guimarães said. “I actually have a digital TV in my cab, but I prefer to use the phone. The reception is much better.” Following a favorite team or soap opera on a cellphone may take longer to reach Western markets, where broadcasters and wireless operators have been slow to embrace the technology. In the United States and Europe, where operators tend to control what technology goes into handsets, a major hurdle to free-to-air broadcasting is, ironically, that it is free. That offers no incentive to operators focused on raising revenue per customer. “Ask anybody if they want to watch free TV on their phone. Everybody is going to want to say sure,” said Jim Oehlerking, the senior director for mobile TV business development at Motorola. “The challenge is getting the mobile media marketplace to the point where content owners, carriers and broadcasters work out a business model.” But with the level of data traffic surging on wireless networks around the world, some operators are beginning to look to free-to-air mobile TV — which operates independently and adds no additional traffic burden on an operator’s network — as a way to retain customers. In April, 12 broadcasters and television content owners in the United States, including Fox, NBC, Gannett Broadcasting, Hearst and Cox Media, formed a joint venture to pool their broadcasting spectrum and eventually deliver mobile TV to 150 million people. “We are excited about building a platform that makes mobile television universally available and economically viable,” Jack Abernethy, the chief executive of Fox Television Stations, said at the time of the announcement. “This venture is the first step in forging cross-industry and company partnerships to deliver content to consumers.” The U.S. effort is in its initial stages, and no deadlines have been set for adoption. Samsung, which includes mobile TV chips as standard technology in its high-end smartphones in South Korea, is making a handset for Sprint that works on the U.S. mobile broadcast standard, ATSC-M/H. Samsung also makes a DVB-H phone for Europe, two that work on Latin America’s ISDB-T standard and an analog handset for Southeast Asia. On May 24, Sprint and nine broadcasters in the Washington-Baltimore area began a four-month trial that will broadcast programming to mobile phones, netbook computers and portable DVD players made by Samsung, LG Electronics and Dell. Dave Lougee, the president of Gannett Broadcasting, said the organizers of the trial, a group of 900 U.S. television stations called the Open Mobile Video Coalition, were hopeful consumers would take to the technology. The trial is being supported by every facet of the U.S. television industry, including content owners, broadcasters, broadcast equipment makers and advertisers, represented by the Television Bureau of Advertisers and The Ad Council. “We are looking forward to hearing how consumers use the technology,” Mr. Lougee said in announcing the trial. If South Korea is a guide, U.S. consumers will use it just as much, if the price is right. http://www.nytimes.com/2010/05/31/te...1mobiletv.html  Streaming Video to Outpace P2P Traffic Growth Marguerite Reardon Video is still the killer app of the Internet, but peer-to-peer services like BitTorrent will no longer account for the bulk of traffic on the Net as streaming services grow at a quicker pace over the next few years. For 10 years, peer-to-peer traffic, such as BitTorrent, which includes some video, has been the largest type of traffic on the Internet. But according to Cisco Systems, streaming video will grow at a faster growth rate over the next few years. And starting this year, streaming video will account for more traffic on the Net than peer-to-peer traffic. According to Cisco's annual Visual Networking Index Forecast, Internet traffic will grow more than fourfold by 2014, and video will account for much of that growth. In fact, Cisco predicts that in the next four years, more than 90 percent of all content traversing the Net will be some form of video, whether it's peer-to-peer or streamed from servers. "It's not that peer-to-peer traffic is declining," said Doug Webster, senior director of worldwide service provider marketing for Cisco. "It's just growing at a slower rate compared to other types of video traffic. This could be because streamed video content is not so hard to find anymore. And because streaming preserves the quality of service, it's the method of choice for many commercial services." The forecast, which looks at traffic projections for 2009 through 2014, predicts that global Internet traffic will increase to 767 exabytes by 2014, a fourfold increase. This amount is 100 exabytes higher than the projected level in 2013, which is the equivalent of 10 times all the traffic traversing IP networks in 2008. To put this growth into perspective, the nearly 64 exabytes of global IP traffic per month projected for 2014 is equivalent to 16 billion DVDs; 21 trillion MP3s; or 399 quadrillion text messages, Cisco said. In total, Cisco said, video traffic will exceed 91 percent of all global IP traffic in the next four years. It would take more than two years to watch the amount of video that will cross global IP networks every second in 2014. And it would take 72 million years to watch all the video crossing the network in 2014, Cisco has said. Faster home broadband connections and the growing popularity of high-definition TV and 3DTV are key drivers of this growth. In just a decade, the speed of home Internet connections around the world has increased 35 times. In 2000 the average residential Internet connection download speed was 127 kilobits per second. In 2010 the average Internet download speed is 4.4 megabits per second. In addition to faster connections, consumers are also watching more high-definition and 3D video, which use more network resources. Cisco predicts that HDTV and 3D TV will increase 13 times between 2009 and 2014. In total, HDTV and 3D video will account for 42 percent of the video on the Internet by 2014. Even though data traffic over fixed connections will continue to outpace data originating from mobile devices on the Net, global mobile data traffic will also increase. In fact, Cisco predicts it will increase 39 times from 2009 to 2014. And by 2014, the annual global mobile data traffic will reach 3.5 exabytes per month, which works out to a run rate of more than 42 exabytes annually. The flood of network traffic is good for Cisco and other infrastructure companies, which make equipment that fuels this growth. Analysts and Internet experts have long predicted that video will be the killer app of the Internet over the next several years. Indeed, video of all stripes, whether it's streaming, corporate, consumer focused, or peer-to-peer will drive growth and demand for more infrastructure. http://news.cnet.com/8301-30686_3-20006530-266.html  TV after YouTube YouTube made two fascinating announcements recently: 1) viewers are now downloading an average of two billion videos per day on the service, and; 2) YouTube is almost showing a profit for Google, its owner. Think about the glorious inefficiency embodied in that latter statement: two billion downloads per day just to break even. And this is supposed to be the future of television? Hardly. I think the future of television is Veetle. Veetle, if you haven’t heard of it, is a Palo Alto-based startup that isn’t nominated for this summer’s Startup Tour. Veetle appears from my vantage point to be a peer-to-peer video distribution system that most closely parallels the current cable TV model except applied to the Internet. Veetle video channels can be viewed in a browser (32-bit plug-in required) and present — just like CNN — a continuous stream of programming that can’t be interrupted, paused, or changed and can’t be very easily recorded, either. In fact a Veetle channel very well could be CNN, because almost anyone can become a Veetle broadcaster by just grabbing a video feed from their DVD player or cable box and throwing it up on the web in glorious H.264. Veetle is an adolescent cesspool of intellectual property confusion but that’s part of what makes it so much fun. Now here is why I think Veetle is the future of television. I have been writing about this particular topic (the future of television) since 1997 and while a lot has changed much has not. Sure, bandwidth is a thousand times cheaper than it was. Sure, codecs are better as are PCs. But the two core issues of: 1) how to maintain intellectual property rights for web video, and; 2) how to make money with web video, are no more answered today than they were back in the days of broadcast.com when Mark Cuban suckered Yahoo into thinking he had all the answers when of course he did not. But in my view Veetle actually does have many of the answers. Here’s why. YouTube has those two billion downloads per day yet just manages to break even. Commercial TV has less than two billion viewers per day, yet manages to be a very profitable industry with at least $20 billion in annual sales. The question to ask is not why YouTube is so popular by why it is so unprofitable? It is unprofitable because most of the content is crap. It is unprofitable because distribution costs are still too high. It is unprofitable because the ad model isn’t clear. It is unprofitable because the average video is still less than four minutes long so this is not a medium for story telling in any strict sense. Oh, and did I mention that the content is crap? Commercial or even non-commercial TV, in contrast, may be too dumb, too simple, and too obvious for the most part, but not all of it is crap. Find a way to reach the non-crap while preserving the best of traditional TV and you’ll have something. You’ll have Veetle. Pre-Veetle, the video distribution models were buying or renting from iTunes, watching with commercials on Hulu or TV.com in a system subsidized by the writers and actors unions, watching with some ads on YouTube, or just plain watching (crap) on many different sites. None of those models, however, have Veetle’s key feature of being easy to watch but hard to hack, easy to attend but hard to ignore. You can’t pause it, you can’t record it, you just have to watch it, like broadcast or cable TV pre-TiVO. And that makes it an ideal commercial medium and one very good for preserving intellectual property rights, unlike all those others. The aha! moment with Veetle is when you realize it is just like having a cable TV system with a million channels. Along with the bad porn (Veetle really needs parental controls, guys) and European football on Veetle is a loop from some user running every episode of The Big Bang Theory, which of course I love. There are something like 66 episodes, but it could be just as easy with Veetle to have 66 channels each one episode deep. And of course there is the p2p aspect of the service, which lowers Veetle’s bandwidth to around 700 kbps-per-continuous channel. Compare that to YouTube with two billion 350 kbps downloads at 3:30 each for the calculated equivalent of 2.4 MILLION Veetle channels. No wonder YouTube barely makes a profit even with zero content cost. I could throw my 13 old episodes of NerdTV up on Veetle in full resolution, running them in a loop with a couple of commercials in each episode, and not only would I entertain people, I’d put my three kids through private schools on the proceeds. There is no way — no way– I could do that on YouTube. That’s where Veetle gets it and YouTube doesn’t, because this particular option isn’t really available on YouTube, which remains an expensive distribution system in search of a viable programming model. I can see how Veetle would grow to be a $20 billion replacement for traditional TV, but I can’t see how YouTube could ever do it. http://www.cringely.com/2010/05/tv-after-youtube/  iAd and the Apple Broadcast Network Richard Menta NBC head Jerry Zucker's oft repeated quote about trading analog dollars for digital pennies reflects the collapse of sponsor trust towards Internet advertising more than anything else. Publications that pulled $35.00 per thousand page views in 1998 were lucky to get $0.35 cents after the dot-com crash thanks to rampant abuse (click fraud, oppressive pop-ups, spam etc.). Nearly a decade later, Apple will attempt to elevate sponsor trust - and with it ad rates - with it's new iAd concept. They will support it through no less than a model that TV execs like Zucker are familiar and comfortable with. In 1959 5,749,000 television sets were sold in the US, bringing the cumulative total of sets sold since 1950 to 63,542,128 units. This number supported, through advertising, three national television networks, ABC, NBC, and CBS (a fourth, Dumont, folded in 1956) and numerous local independent stations. Television was big business by the start of the 1960's. Now here are another set of numbers. As of April this year Apple sold 75 million iPhone and iPod touch units, devices capable of delivering video via Wi-Fi and 3G connectivity. Add to that figure 2 million iPads and counting. By the end of the year Apple should have about 90 million smart mobile devices in the wild. That makes a proprietary amalgam greater than what the TV networks had in 1959 and one that easily serves as a foundation for a pending broadcast network that will be delivered not through tall radio towers, but through small wireless hubs and the Internet. Call it the Apple Broadcast Network. iAd is how Apple plans to pay for it. Apple's adept ability to exert strong control over its environment is why this can all work. iTunes and the Apple App Store serve as a compelling track record where even the valid complaints against Jobsian hegemony underscore Apple's success. Executives at content suppliers from the music, film and TV industries - Zucker chief among them - have sharp concerns when it comes to working with Apple as a distributor. But the fact is consumers trust Apple more than any other corporation that comes to mind and it was lack of trust that crippled Internet ad delivery past volume distributers like Google. If Steve Jobs can extend the Apple glow to iAd, Internet advertising could enter a new era. It's a feasible thought, because Apple will possess a means that overcomes a chronic problem. Apple has to bring everyone to the table first and it won't be an easy sell. The television networks won't own iAd so they won't get 100% of the revenues as they do now. But, 100% of Hulu is not providing Zucker with the sustainable revenue model he needs. On its own NBC can't seem to muster improved ad rates from even existing clientele. That opens the door for Apple. If iAd moves ad rates up to where it becomes a viable option Zucker is under due-diligence to consider it. It has been a couple of decades since viewers were limited to a handful of TV stations. The growth of cable has spread TV viewership over hundreds of stations while the rise of gaming and the Internet offer different options. The glory days of the major TV network are gone simply because today's consumer has much more choice. This has put network leadership under constant pressure to develop new revenue streams and that makes it all the harder to resist the Apple siren when Jobs and co. create something compelling. Should Apple achieves its objective to sharply raise the value of online advertising - raising digital pennies to digital dimes is a ten-fold start - network leadership will be hard-pressed to ignore it. Last April, Broadpoint AmTech analyst Brian Marshall mused that Apple could generate through a hybrid pricing model as much as $32 per 1,000 viewers. That's pure speculation, but if Apple comes anywhere close to Marshall's figure then it becomes just a matter of how large a cut Apple offers Zucker and his ilk to free up network programming. If that happens the Apple Broadcast Network becomes a reality. "If" is the key word here. http://www.mp3newswire.net/stories/2...t-network.html  Sonic Solutions To Acquire DivX In $323 Million Deal Robin Wauters Sonic Solutions and DivX, both listed on Nasdaq, this morning announced that they are to become one. Under the terms of the agreement, Sonic would acquire all the outstanding shares of DivX and merge DivX operations into those of Sonic. DivX stockholders would receive a combination of cash and stock equal to $3.75 in cash and 0.514 shares of Sonic common stock for each share of DivX they hold. The offer was worth $9.83 a share at Tuesday’s closing price, or around $323 million in total. The price is a 41% premium to Tuesday’s closing price for DivX shares. Sonic says the purchase could potentially double fiscal year 2012 earnings per share on a non-GAAP basis. Following completion of the merger, DivX stockholders will own approximately 35% of the combined company’s capital stock. The acquisition is expected to close in September 2010. Here’s how Sonic pitches the buy to shareholders and the press: Quote:
The current Sonic management team will lead the combined company, augmented with key managers and executives from DivX. Kevin Hell, DivX’s CEO, Dan Halvorson, DivX’s CFO and David Richter, DivX’s executive vice president, business & legal affairs and general counsel, will be leaving the combined company after the transaction is closed. http://techcrunch.com/2010/06/02/son...-million-deal/  Album Sales Plummet to Lowest Total in Decades Ed Christman Bad times just got worse. During the week ended May 30, the U.S. music industry sold a total of 4.98 million albums, according to Nielsen Soundscan. That figure, which includes new and catalog releases, represents the fewest albums sold in one week since Soundscan began compiling this data in 1994. By comparison, album sales for the week ended May 31, 2009, totaled 5.76 million. The highest one-week tally recorded during the Soundscan era is 45.4 million albums, in late December 2000. This past week's record low comes as the major record companies continue to reckon with a decade-long decline in sales, and as other prominent sectors of the industry, such as the touring business, go through sea changes of their own. While there's no exact way to compare the latest total against pre-Soundscan tallies, Billboard estimates that weekly album sales volume could, in fact, be at its lowest point since the early 1970s. "We think this is the lowest week ever, or at least of the Soundscan era," says Universal Music Group Distribution president Jim Urie. According to the Recording Industry Association of America, album shipments in 1973 totaled 388.2 million units, an average of 7.47 million per week. Because Soundscan measures albums sold (i.e. scanned) and not albums shipped, Billboard looked at the relationship between annual album shipments, as measured by the RIAA, and annual albums sold, as compiled by Soundscan, for the years 1992-2009. During that period, shipments exceeded scans by an average of 30 percent. By applying that 30 percent figure to the 1973 RIAA album shipment data, Billboard estimates that weekly album sales volume for that year may have totaled about 5.5 million units. That exceeds this past week's tally by 600,000 copies. (The RIAA began keeping figures on album shipments in 1973.) Veteran sales executives caution against putting too much stock into pre-Soundscan record-keeping. "Who the hell knows what weekly sales were back then," says Lou Dennis, who retired as Warner Bros. Records head of sales in 1996. Whatever the benchmark, industry executives agree that this week's album sales total of 4.98 million units is "pretty scary," in the words of Bruce Ogilvie, CEO of leading music wholesaler Super D. Digital track sales for the week totaled 21.7 million, and are distinct from the album sales tally. UMGD's Urie cites this week's album total as "all the more reason why everyone in the industry should be focused on getting the U.S. Congress to introduce legislation that makes the Internet service providers our allies in fighting piracy. Piracy is getting worse and worse, and the government needs to focus on that." Like Ogilvie, Urie thinks that the light release schedule is the main reason for the drop-off. "This week is likely a major aberration, with no big new releases out," he says. "June will be big. Look at all the big records coming out, including Sara McLachlan, Drake, Miley Cyrus, Eminem and Jack Johnson." http://www.reuters.com/article/idUSTRE65400320100605  Opera Diva Tries a Rock Album. Cue Controversy. Renée Fleming, a darling of the opera world, has a new album titled “Dark Hope,” on which she covers indie rock acts. The classical world scratches its head at the impulse. The recording’s promoters — and Ms. Fleming herself — shy away from labeling it a crossover album, calling it instead, “somewhat sheepishly,” as Anthony Tommasini, the chief classical music critic of The New York Times, wrote in Sunday’s Arts & Leisure section, a visit to a “parallel universe.” But why the defensiveness? Mr. Tommasini and Jon Pareles, the chief pop critic of The Times, who reviewed the album in Arts & Leisure, explore the venerable tradition of classical musicians and singers who dip into pop genres. Here are excerpts from their discussion; the full conversation is at nytimes.com/artsbeat. ANTHONY TOMMASINI I must admit, Jon, I felt out of my depth listening to this record. What do you think: is there appeal within the pop music world for this CD? JON PARELES Tony, that pop world is a wildly fragmented place at the moment, where it’s difficult to sell — or even get attention for — anything that’s not an oldie sung on “Glee” or “American Idol” or the latest work from an established band/brand. Renée Fleming is a huge name in the classical realm, but a virtual unknown outside it. In a way, she’s making a stealth approach into pop, sloughing off her recognizable self. She’s setting aside the high notes, trading orchestral backups for layers of electric and synthetic instruments, and relying on what’s in the tracks — melodies, hooks, interpretations — rather than some image campaign or YouTube stunt. Depending on the music — how old school! Yet someone — Q Prime, which manages Metallica and came to her with the project — thought there was enough appeal to make the album worthwhile. They may be counting on the Norah Jones - Susan Boyle audience: older listeners who still buy music legally and who want something soothing and melodic. The song selection on “Dark Hope” is split between the kinds of bands bloggers appreciate but TV soundtracks and commercials also use — Death Cab for Cutie, Band of Horses — and choices like Jefferson Airplane’s “Today” and Peter Gabriel’s “In Your Eyes” that boomers know. I’d guess there’s some demographic calculation along with the quality of the songs. But will anyone pay attention? There is a good story line here to promote: opera star explores a new (to her) repertory and takes it seriously enough to change her whole sound. That should put her on talk shows, NPR and other outlets that reach a general audience. Yet it helps every pop hopeful to have a core following to get momentum started. So my question back to you is, do you think her opera and lieder fans are going to follow her to “Dark Hope”? TOMMASINI If I had to guess, I’d say that Ms. Fleming’s core fans will not be interested. There was an audience for “Haunted Heart,” her jazz trio album. She may not be a great jazz singer, but she knows what she is doing, and the recording was a modest and tasteful project. And, she sounds like Renée! Her transformation in “Dark Hope” is too extreme for her fans, I think. Still, I appreciate your reaction to her singing, which was that she did not go far enough, that she sounds too reverential and cautious. What about when a pop artist performs classical music? What was the reaction in the pop sphere, for example, to “Songs From the Labyrinth,” Sting’s album of songs by John Dowland? And are Paul McCartney’s fans at all interested in his oratorios and classical concert pieces? I revere Mr. McCartney, but I can’t abide those pretentious scores. PARELES I don’t see Mr. McCartney’s orchestral offerings getting much traction among his rock fans. Pretty indigestible. I was more taken with “Il Sogno,” Elvis Costello’s ballet score, which really does grapple with what to do in a long form with motifs for various characters. But give me his three-minute songs any day. “Labyrinth” did reach some Sting fans — went to No. 25 on the Billboard pop chart — but it’s an easier prospect: a collection of songs and a dip into classical music with the trusty Sting as guide. Of course, pop composers have been raiding the classical melody storehouse forever, but I don’t think either of us is going to call Public Image Ltd.’s “Swan Lake” a crossover effort. The real crossover gem is Aretha Franklin’s “Nessun dorma,” which she first sang as a last-minute substitute for an ailing Pavarotti. She completely honors it as an aria, but lavishes it with soul. Which brings me to the big crossover quandary: respect. Classical music daunts some pop musicians. On “Labyrinth,” you can hear Sting straining to be proper, thinking his way through every precious phrase, when those melancholy Dowland love songs with their great tunes would benefit hugely from Sting’s being the same self-confident (yet still morose) guy who sang “King of Pain.” Coming from the other direction, the classical folks often seem to think that their virtuosity is the only kind of virtuosity, so of course it will work in every context. When opera singers deign to sing what, to them, are clearly trivial ditties, they often end up sounding silly and pretentious. And even when the impulse to mix is genuine, sometimes it just ends up stillborn. The last thing I want to be is the Border Patrol at Genre Junction. But different genres require different skills, which is why I appreciate that Ms. Fleming treated rock as a challenge, not a cash machine. It’s odd, though, how much she let herself be changed. It’s the Sting “Labyrinth” situation in reverse. Ms. Fleming (and the producer David Kahne) didn’t need to make the arrangements so layered and electronic; actual indie-rock can be also sparse and exposed, closer to what she did on “Haunted Heart.” And, of course, pop does make a place for giddy mock-operatic flourishes; hello, Lady Gaga. What makes the album so alien to you, Tony? Is it the production? How would you have felt hearing more or less the same vocals backed by a chamber ensemble? TOMMASINI I guess I was flummoxed because Ms. Fleming was so unrecognizable. It is so important to classical vocalists to know the true natures of their voices. So I’m not sure how I am supposed to treat her exploration of her “parallel universe.” But you are absolutely right that the issue of respect and attitude complicates many crossover projects. Aretha was really cool, and quite moving, singing “Nessun dorma” because she said, I’m going to make this song my own. And no one has to teach her anything about phrasing. Sometimes when classical musicians, especially instrumentalists, play jazz or rock, the problem comes with their approach to rhythm. They mimic the jazzy swing style but lack the requisite quality of relaxation. When Duke Ellington and Art Tatum played, no matter how complex and driving the rhythm, they sounded relaxed. Not so Itzhak Perlman when he tries to swing. PARELES Along with the quality of relaxation you brought up, I have to add bite. Classical training strives to control or eliminate the rough spots. But pop makes the rough spots some of the most expressive moments. It’s European versus African (or African-American) aesthetics: the friction that sparks American (and now the world’s) popular music. It’s intriguing that you mention the “true natures” of voices. To me — after years of listening primarily to pop/rock/jazz/traditional/world/etc. music — opera singing is athletic and superhuman, a feat of discipline and training. It’s not as natural as pop styles, which require their own discipline but usually place the voice in the performer’s speaking range. Ms. Fleming points out that on “Dark Hope” she’s singing where she talks (instead of up in that ethereal soprano range). So could this be the true nature of her voice, with an entire career built elsewhere because that’s where her taste and intellect led her? One last thing occurred to me about “Dark Hope” and the endless crossover paradoxes. Ms. Fleming made this album with a lot of guidance. Q Prime brought her the song suggestions; Mr. Kahne supplied the tracks. Presumably she had veto power, and of course her voice governs the other decisions. But when Sarah McLachlan or Annie Lennox makes albums, the guidance comes from them: They are writing the songs, and they choose the collaborators who will realize the sounds they want. They’re following musical instincts. That process can yield good, bad or indifferent music, but it’s a more direct artistic route. http://www.nytimes.com/2010/06/01/ar...crossover.html  For Musicians, Economy is the Mother of Invention Enterprising music makers are turning to the Internet and micro-financing through donations. BROKEN RECORD: MUSIC IN THE DOWNLOAD ERA Randy Lewis Los Angeles singer and songwriter Sam Phillips turned up recently for a small-scale show at Hollywood's Hotel Café. Playing for an intimate audience of several dozen, she was testing on a live audience new material she's been working on in her home recording studio. But for a select few regular visitors to her website, the new songs weren't so new — they'd been able to hear them weeks or months earlier as subscribers to her "Long Play" music and art project, an innovative way she's generating financial and emotional support for the creation of new music. With "Long Play," a website within her main site, Phillips has thrown open a virtual door to her creative world, inviting in fans over the course of a year to watch and participate as she writes and records a new album that she plans to release in the fall. She's not alone. As the traditional record business has turned topsy-turvy, artists as well as startup companies are developing ways to finance the making of music today. A couple of European websites, Sellaband.com and Slicethepie.com, act as revenue-generating conduits between musicians and fans. A few years ago, this "patronage model" was viewed as a potential replacement to the beleaguered major-label system. But with Sellaband on the rebound after filing for bankruptcy earlier this year — it's getting back on its feet with a new group of owners — the tactic is no longer viewed as the savior. Rather, it's one weapon in an ever-expanding arsenal. During a couple of decades as a major-label recording artist, Phillips got used to a ritual in which a record company would put up the money to record new songs she'd written. Once completed, she'd wait and watch for weeks, months, sometimes even years for those recordings to be released to the public. Phillips, named one of the 25 best-reviewed artists of the recently concluded decade by the review-aggregate website Metacritic.com, spent 13 years in the '80s and '90s with Virgin Records, before shifting over a decade ago to the boutique Nonesuch label. Recently, however, her Nonesuch contract came to an end. With the music business in disarray, she decided the time was right to launch an Internet-based forum for her back-alley cabaret pop songs and art. Visitors to her website can subscribe for $52 — $1 a week — which gives them access for one year to new music as she makes it as well as a slew of special audio and visual content aimed at her hard-core fans. "We did it exactly the opposite from iTunes," Phillips, 48, said with a laugh at the studio she's set up in a vintage house on the east side of Los Angeles. "We put no music up and asked for $52 for the year. And people responded, which is great." 'Art-and-music installation on the Web' Since going live with Long Play last fall, Phillips has pulled in about 1,000 subscribers who have provided her the budget she's using to keep working on the new album. But that's just the culmination of the year-long project. She's also letting subscribers download a series of five EPs — roughly one every two months — each containing four or five new songs that she has recorded since the previous one. Some tracks from those EPs may wind up on the album, many won't, but no one will know which of these works-in-progress make the cut until Phillips makes her final choices several months from now. She's also posting recorded conversations with some of the musicians she has invited in to play on the album, for a Long Play bonus feature called "Phone Booth." She writes a blog accessible only to subscribers, posts some of her art collages and short films she's shot, various ways of giving those who are most interested in closely monitoring her career a window into how she creates. "This isn't for everybody," said the woman who also scored the music for the long-running USA Network series "The Gilmore Girls" and who starred as a mute terrorist opposite Bruce Willis in the 1995 thriller "Die Hard With a Vengeance." "I don't feel this is the new business model — whatever that may turn out to be. To me, it's more of an art-and-music installation on the Web." Securing financing directly from fans has provided Phillips with a newfound sense of freedom to pursue her artistic impulses without artistic second-guessing that can come from corporate overseers. But reporting to subscriber-investors, with whom she has a greater sense of direct connection, "I feel more pressure to do something for them. It's not a [faceless] company and people out there that you don't know; it's Jill, it's Bruce, it's all these people who have sent their money to me. I've got to get something going for them, and I hope they like it. "That I'm not sure I like," she said with a laugh, "but they've been happy so far." "I couldn't be happier," said subscriber Jill Lorenz of Clayton, Calif., in the Bay Area. "I'm a big supporter of artists in general … and always wanted to know more about their creative process: what books they read and what they thought about. The Long Play gives us this rare access and insight into Sam's world, and I'm grateful that she's willing to share that with us. The $52 subscription price is a steal when you think about the price of one concert ticket to see a much less gifted musician at some gigantic venue these days." But there's also a risk in sharing more of her creative and personal life with the online community. "One of our Long Players wrote in, because I had said something about how we're going to expose the artistic process," Phillips said, smiling. "He wrote in and said, 'Yeah, the last time I heard that — about getting involved in the creative process — I wound up helping a poet move his couch." In late 2007, singer-songwriter Jill Sobule turned directly to fans, via her website, rather than jockeying for a new deal with a record label. "You guys are the Medici family," she wrote in her website pitch, "except I give you prizes for donations of certain amounts." For a $1,000 contribution, for instance, she promised to write a theme song for the donor. Fourteen people took her up on that one. Within about two months of launching the jillsnextrecord.com site in early 2008, she'd brought in $75,000, and later that year released "California Years — Part I," which she made with help from three-time Grammy-winning producer Don Was. One donor left a message saying that even though he didn't like her music, he admired her campaign and contributed $25 anyway. "That was one of my favorite comments," she told The Times recently. "The fun thing to me was that you're not trying to please a suit or an A&R guy, you're trying to please these people who are directly supporting you, and they're way more important." Southland drummer, singer and songwriter Josh Freese, a member of such bands as the Vandals, Nine Inch Nails, Guns N' Roses and A Perfect Circle, among others, cooked up a wacky guerrilla campaign for his 2009 solo album "Since 1972." His program opened the door to contributions after he'd recorded it, but it generated considerable media attention, and significant support from donors, for the wild perks he offered. "People are doing things right now similar to this but on a more serious note," he said at the time. "So why not go crazy with it, where I'm giving people foot massages, taking them to Disneyland and letting them take items out of my closet?" In fact one 19-year-old fan from Florida redirected money he'd been saving for a new car and ponied up $20,000 to spend several days hanging out with Freese and his rock-star pals. Not a perfect model Fan financing is an option that has become both more attractive and necessary as money has become harder to come by at traditional record companies. Slicethepie has registered about 15,000 acts, 28 of which have reached the $25,000 fundraising goal that releases funds that they use to record albums. Those ventures are different from the direct-to-fan outreach that Phillips and other U.S. musicians have done on their own. With the European programs, fans invest in musicians as they would in the stock market, with the expectation not only of helping acts whose music they may admire but also of generating a financial return on their investment. (U.S. fans, however, can only donate, not invest, because of federal regulations governing what are considered international stock transactions.) One band, Scars on 45, got a song from its Slicethepie-financed album placed in an episode of " CSI: New York," mainstream exposure that led to a major-label deal earlier this year with the Atlantic Records-affiliated Chop Shop Records label. Sellaband, however, hit a snag earlier this year. After collecting more than $3 million and paying for dozens of albums for participants since it opened in 2006, company officials still couldn't make ends meet, and filed for bankruptcy. A new group of owners took over in February, shifted the operation headquarters to Munich, Germany, and have vowed to continue the program as it was conceived. The highest profile act to hook up with Sellaband to date is veteran rap group Public Enemy, which signed on in October. The group was named Sellaband's ambassador to North America, where the service is far less known among musicians than in Europe and Asia. But in the seven months since aligning with the site, the rappers have collected only about $54,000 toward their original budget goal of $250,000 for recording and promoting their next album. That's prompted the rappers to downscale that figure. "We've been financing our own records for years," Public Enemy rapper Chuck D said. "The reason we hooked up with Sellaband was to do the kind of record we wouldn't normally do ourselves, with lots of guest artists. But we realize the economy is hard, and people have to pay their rent and buy food. So we're going to just try for $75,000 and do it a little differently than we'd planned on." As of now, they have Rage Against the Machine's Tom Morello, DJ Z-Trip and rock band Rise Against lined up for guest appearances. "Every band financed generates just a few thousand dollars of revenue for the financing platform and there is rarely significant income in the form of royalties," Slicethepie CEO David Courtier-Dutton told The Times by e-mail. "Fan financing should not be provided as a standalone service. It's just one — albeit critical — ingredient required to help an artist develop a career." Phillips certainly isn't ready to call it a viable long-term solution. "I don't know if I will go past the year," Phillips said. "It's been a fun idea, but it's a lot of music and a lot of content in a year. I'm trying to do that very spontaneously. I'm trying not to feel I have to have 'X' amount of little movies or Phone Booths. I'm trying to do it organically, as we record and as I do everything else too." For Phillips, Freese, Sobule and many others, it's about the adventure as much or more than the financial bottom line. "It's like you're in a Frontierland — you feel like a cowboy," Sobule said. "That's what's exciting to me: putting on a show, coming up with an idea — being able to survive." http://articles.latimes.com/2010/may...llips-20100509  Ray Charles' Copyrights a Lucrative Business Ed Christman Ray Charles is a music publisher's dream. Not only did he write songs that stand the test of time, but his interpretations of other songwriters' tunes could turn them into royalty-generating goldmines. Charles wrote classics like "What'd I Say?" and made other songwriters' tunes into hits as well. His version of "Georgia On My Mind," written by Hoagy Carmichael and Stuart Gorrel, went to No. 1 on the Billboard Hot 100 in 1960, even though it had been recorded by plenty of well-known performers before then. Besides Charles' own songwriting, and the tunes he owned through his own music publishing companies, "there are few, if any, recording artists who have impacted publishing houses around the country as has Ray Charles," says Tony Gumina, president of the Ray Charles Marketing Group, which handles the late artist's licensing affairs. "If you just look at the 11 different songs where Ray won a Grammy award you'll find 14 different publishers/co-publishers." Ahead of the 80th anniversary of Charles' birth on September 23, the Ray Charles Marketing Group is working with partners on numerous projects including a new documentary on the Biography Channel and the debut this fall of "Unchain My Heart: The Ray Charles Musical" set for November. Most of the songs that Charles wrote through 1962 are owned by Warner/Chappell Music, while the songs he wrote after that are published by Charles' own publishing operations, owned by the Ray Charles Foundation, and licensed by the Ray Charles Marketing Group, which was formed in 2005, to maximize opportunities from those rights. Beginning in 1962, three years after Charles left Atlantic and signed with ABC, every song he wrote, co-wrote or arranged and sometimes even recorded was owned by his own publishing companies, Tangerine Music Corp. and Racer Music Co. In the six years since Charles died of cancer, his publishing catalog has flourished. Income for his older copyrights has been propelled by more recent success. In 2004, Concord Records released Charles's Grammy-winning album "Genius Loves Company," which has since sold 3.2 million copies. In the same year, the film "Ray" was released featuring Jamie Foxx in the Oscar-winning lead role. Since 2004, Rhino's "Very Best of Ray Charles" has sold more than a million copies, according to Nielsen SoundScan, after selling only 143,000 units between its release in 2000 and mid-2004. "Between the 'Greatest Hits,' the movie, the soundtrack, and the new (Concord) records, and Kanye West's 'Golddigger,' (which uses the Ray Charles/Renald Richard composition 'I've Got A Woman,"), it's all kind of snowballed," says Brad Rosenberger, Warner/Chappell senior VP of catalog development and marketing. "Ray is definitely reaching a new generation of kids." But his reputation sometimes proved daunting to other singers. In other words, because Charles often did the definitive versions of his songs, "we don't get a lot of cover versions of the songs he recorded," Gumina says, and Rosenberger agrees. According to the Warner Music Group, the top Charles songs in its catalog include: "Hallelujah I Love Her So," "Hard Times (No One Knows Better Than I)," "Mary Ann," "What'd I Say," and "I've Got a Woman." While Charles has a substantial songwriting catalog post 1961, "what is interesting is he didn't like to write," says Gumina. "He wrote songs when he was on Atlantic because he didn't like what (Atlantic principals) Ahmet (Ertegun) and Jerry (Wexler) were giving him (to record). So his most prolific writing period was between 1948 and 1960. "As soon as he became big enough to record the biggest songs, he started recording the American songbook Rogers and Hart, Rodgers and Hammerstein, the Gershwins and Irving Berlin." That dovetailed nicely with the fact that once he became big enough singing star, listeners wanted to hear his version of popular songs like "Over The Rainbow," Gumina says. But just because he recorded other songwriters' songs, doesn't mean he was forsaking publishing. By the 1960s, Charles' stature was such that top songwriters were constantly pitching their songs to him to record, Gumina says. "He'd take the stance, if I am going to record it, I want to publish it." So he started Tangerine Music, which was named after his Tangerine Records label, and Racer Music. Percy Mayfield was among the songwriters whose music Charles published through his music publishing arms. Charles also capitalized on another publishing angle: he began recording a lot of public domain songs, like "America The Beautiful," and "Lift Every Voice and Sing," where he published the arrangement. Today, the Ray Charles Marketing Group represents about 500 songs from those companies, including about a dozen Charles wrote and another 30 or 40 where he is credited as co-writer. It also represents 80 of his songs where it can license both the songs and the master, which it is making available to film producers, directors, and advertising agencies. Since the release of the "Ray" biopic, Gumina says that synchronization of Charles songs has proven lucrative. But he also says performance royalties are on the upswing too. For example, when Charles first published "Hit The Road Jack," who could imagine the uses that would come its way. Nowadays, at any sporting event -- whether it's a player fouling out of a basketball game, a pitcher getting pulled from the mound, a hockey player getting sent to the penalty box -- when a player is pulled from the game, "Hit The Road Jack" will resound over the PA system. http://www.reuters.com/article/idUSTRE64U0OU20100531  Newspaper Enlists Startup To Police Web For Copyright Violations Wendy Davis As part of a copyright crackdown, a startup called Righthaven has filed five lawsuits against Web sites that allegedly lifted articles from the Las Vegas Review-Journal. In recent weeks, Righthaven has sued the nonprofit group NORML (the National Organization for the Reform of Marijuana Laws), the association Citizens for Responsibility and Ethics in Washington, real estate agent and blogger Matt Farnham, gambling site MajorWager.com and the company MoneyReign, which allegedly runs the site casinoreign.com. The lawsuits allege that the defendants reposted articles, or portions of them, from the Las Vegas Review-Journal. Righthaven asserts in court papers that it obtained exclusive rights to reproduce and distribute the newspaper's articles from its parent company, Stephens Media, owned by Las Vegas Review-Journal president Sherman Frederick. Righthaven is run by intellectual property attorney Steven Gibson, who previously brought other, unrelated cases on behalf of Stephens Media. While some newspaper executives have vocally complained about infringement online, copyright lawsuits over news items remain rare. What's more, when cases are filed, they tend to be against defendants who compete for readers, as happened when Gatehouse Media sued Boston.com or Dow Jones sued Briefing.com. The Righthaven cases, by contrast, are against companies that are not in the news business. The cases seemed to have come as a surprise to some of the defendants. Farnham, the realtor who was sued last week for allegedly posting portions of two articles to his blog, says no one ever asked him to remove the material. "I would have taken it down in a heartbeat," he says. Farnham adds that he was only trying to share items that he believed would interest people searching for real estate. "I thought it was a compliment to the paper that I wanted to get that information out," he says, adding that his posts linked back to the newspaper. "I had honest intentions." NORML executive director Allen St. Pierre says that the site has posted portions of articles and links back to the original sources for 10 years without receiving any previous complaints from publishers. "We really are flummoxed," he said, adding that no representatives of the Las Vegas Review-Journal asked him to remove the material before suing. "Had we received a notice we would have taken it down, we would have apologized, and we would have asked them what size NORML T-shirts they wanted," he says. St. Pierre adds that NORML plans to contest the lawsuit. "We think there's a much larger principle at hand here regarding access to information," he says. He also says the organization received no income or discernible traffic from the alleged infringement. In addition, he says, NORML's news items come from another drug reform organization, MAP Inc. The Digital Millennium Copyright Act does not require content owners to send publishers takedown demands before suing unless infringing content is uploaded by third-parties. The copyright statute also provides for damages ranging from $750 to $150,000 per infringement, regardless of whether the newspapers can show they lost money as a result. That holds true even if the infringement is relatively insignificant, says Seattle-based Internet law expert Venkat Balasubramani. "There's no de minimus exception," he says. While the Web sites could attempt to argue that they made fair use of the material, doing so could be an uphill battle if the sites reprinted significant portions of the articles verbatim, without adding original commentary. Frederick declined to comment on why Stephens Media transferred the copyrights to Righthaven or whether the company planned to do likewise for any of the other newspapers in its chain. But Righthaven's Gibson indicated that more lawsuits were on the way. "Righthaven's copyright ownership portfolio is increasing," he said. "It certainly is attuned to dealing with copyright infringement that occurs in the electronic environment." http://www.mediapost.com/publication...art_aid=126721  Author Joe Konrath Experiments With 'Piracy' To See How It Impacts Sales from the give-it-away dept Last week, we wrote about how author Joe Konrath felt that authors were going a bit overboard worrying about file sharing, noting that there was no way to stop it, and fighting it was just a waste of effort. Instead, he wanted to focus on providing more value for his fans. Joe has since followed up his original post with a bit of an experiment: purposely putting one of his ebooks online for free to see what happens, even though it's also available for sale: Quote:
Quote:
http://www.techdirt.com/articles/201...22219636.shtml  Book Publishers Agree Change Coming Mark Egan and Christine Kearney Giants and upstarts of publishing gathered at the annual BookExpo America here this week agreed e-books will transform the business, although exactly how it will all shake out remains unclear. From biggest publishers to newcomers there was agreement on one thing -- the big change will come when there is a standard format across which all e-books can be published and shared. The industry has been going through a tumultuous period as Apple and Amazon duke it out for dominance in the nascent market for electronic books. Both want their devices -- the iPad and the Kindle -- to be the one consumers use to read e-books, and each wants to be the biggest virtual store were such content is sold. For Michael Serbinis, chief executive of Kobo, a company that allows users to buy e-books and read them on most devices, that battle is a distraction to the real changes coming. "Today you can buy a book at Barnes and Noble and you can buy a book at Walmart and you don't have to keep them in separate rooms in your house," he said. "You buy a book from Apple and Amazon and you have got to keep it tied up with your Apple universe or your Kindle universe." Ultimately, consumers want freedom, said David Shanks, chief executive of leading publisher Penguin Group USA. "Our fondest wish is that all the devices become agnostic so that there isn't proprietary formats and you can read wherever you want to read," Shanks told Reuters. "First we have to get a standard that everybody embraces." The issue, he said, is the fear of piracy and how to set a common digital rights management system to thwart it. The battle over technology formats is a familiar one. A century ago, Edison and Victor made records that could not be played on each other's players. There was the Betamax/VHS videotape struggle and more recently Blu-ray beat out HD DVD. BookExpo showed traditional books are alive and well. There was buzz for the upcoming book from news parody king Jon Stewart and raucous Rolling Stones guitarist Keith Richard's memoirs as well as a book on home design by Barbra Streisand. Evidence of Innovation And there was evidence of change coming in the age of e-books, although the new format was displayed only in one small corner of the sprawling Javits Center convention halls. Among the digital companies here were Sideways, which helps authors and publishers transform text into multimedia content, adding video, pictures and features such as Twitter feeds. Another company, Ripple, allows adults to buy children's e-books and record their voices reading them. And there were gadgets such as the enTourage eDGe -- a twin-screened device which opens like a book to reveal an eReader on one side and a NetBook on the other. Eileen Gittins of Blurb, which helps authors and companies self-publish, predicts e-books will make up half of all sales in five years. In 2009, the global publishing business, including print and digital, was worth $71 billion, according to PriceWaterhouseCoopers. "We're seeing now in book publishing what had happened previously in the music publishing industry. And that is, a massive disruption of the business model," she told Reuters. The problem is that the cost of printing is a minor cost of publishing whereas developing work with an author and marketing it consume the lion's share of costs. That means, she said, that the book industry will become more like the movie business. "The book publishing industry is becoming more blockbuster focused," she said. Susan Petersen Kennedy, president of Penguin Group USA, said publishers will not make the same mistakes as the music industry, which had an epic struggle over electronic distribution and piracy and lost huge market share. "It's always treated as if the publishers are the Luddites," she told Reuters in an interview. "The devices have not caught up with the content. Contrary to popular opinion, the book is actually so far more flexible." Serbinis says the industry will see dramatic change. He predicted consolidation among publishers and said tablet computers will be common. He expects readers to eventually be able to lend e-books to each other. And books won't just be for bookstores any more as new distribution channels from mobile phone companies to gaming companies join the party, he said. "It won't only be the bookstores that have gone digital," he said. http://www.reuters.com/article/idUSTRE64R55W20100528  Book Asks: Is Internet Ruining Our Minds? Mark Egan When author Nicholas Carr began researching his book on whether the Internet is ruining our minds, he restricted his online access and e-mail and turned off his Twitter and Facebook accounts. His new book "The Shallows: What the Internet is Doing to Our Brains" argues the latest technology renders us less capable of deep thinking. Carr found himself so distracted that he couldn't work on the book while staying as connected, as is commonplace. "I found my inability to concentrate a great disability," Carr told Reuters in an interview. "So, I abandoned my Facebook and Twitter accounts and throttled back on e-mail so I was only checking a couple of times a day rather than every 45 seconds. I found those types of things really did make a difference," he said. After initially feeling "befuddled" by his sudden lack of online connection, Carr said, within a couple of weeks he was able to stay focused on one task for a sustained period and, thankfully, able to do his work. Carr wrote a 2008 Atlantic magazine piece that posed the controversial question "Is Google Making Us Stupid?" and wanted to dig deeper into how the Internet alters our minds. His book examines the history of reading and the science of how using different media changes our brains. Exploring how society shifted from an oral tradition to the printed word and to the Internet, he details how the brain rewires itself to adjust to new information sources. Reading on the Internet has fundamentally changed how we use our brains, he writes. Facing a torrent of text, photos, video, music and links to other web pages combined with incessant interruptions from text messages, e-mails, Facebook updates, Tweets, blogs and RSS feeds, our minds have become used to skimming, browsing and scanning information. As a result, we have developed sharper skills at making fast decisions, particularly visual ones, Carr says. But now most of us infrequently read books, long essays or articles that would help us focus, concentrate and be introspective and contemplative, Carr writes. Are We Librarians? He says we are becoming more like librarians -- able to find information quickly and discern the best nuggets -- than scholars who digest and interpret information. That lack of focus hinders our long-term memory, leading many of us to feel distracted, he said. "We never engage the deeper, interpretive functions of our brains," he said. To illustrate, he likens short-term memory to a thimble and long-term memory to a large bathtub. Reading a book is like filling the tub with water from one steadily flowing faucet with each thimble of information building upon the last. By contrast, the Internet is countless fast-flowing faucets, leaving us grasping for thimbles of disparate information to put in the tub and making it harder for our brains to draw connections and have cogent recall. "What we are losing is a whole other set of mental skills, the ones that require not the shifting of our focus but the maintaining of our focus," Carr said. "Contemplation, introspection, reflection -- there is no space or time for those on the Internet." Carr says for centuries books shielded our brains from distraction, focusing our minds on one topic at a time. But with devices such as Amazon's Kindle and Apple's iPad, which incorporate eReaders and web browsers, becoming commonplace, Carr predicts books too will change. "New forms of reading always require new forms of writing," he said. If writers cater to a society that is chronically distracted, they will inevitably eschew writing complex arguments that require sustained attention and instead write in pithy, bite-sized bits of information, Carr predicts. Carr has a suggestion for those who feel web surfing has left them incapable of concentration -- slow down, turn off the Internet and practice the skills of contemplation, introspection and reflection. "It is pretty clear from the brain science that if you don't exercise particular cognitive skills, you are going to lose them," he said. "If you are constantly distracted, you are not going to think in the same way that you would think if you paid attention." http://www.reuters.com/article/idUSTRE6523DV20100603  Study: 'Extreme Gamers' Play 48 Hours a Week Mike Smith Think you're a big gamer? According to a new study from market research firm NPD Group, to be considered among the real hardcore you'll need to play an average of 48.5 hours a week -- nearly seven hours a day. Even dedicated gaming blog Kotaku finds that "pretty extreme." So-called "Extreme Gamers" average 29 years old, and -- perhaps surprisingly -- one-third of them are female. They're more likely to play on consoles than on the PC, and on average they've purchased 24 titles in the past three months -- a bill that could easily run over a thousand dollars. But dedicated though they may be, the Extreme Gamers are just a small minority: a mere 4% of the U.S.'s 174-million-strong gaming public. And though seven hours a day seems like a lot, it's only a little more time than the average American spends watching TV. The figures come from a study which polled some 20,000 members of an NPD Group consumer panel. It broke the gaming population of the US into six other segments, including avid PC gamers (who tend to be older, and buy more games online) and young heavy gamers, the largest segment, who prefer portable systems like the Nintendo DS and Sony PSP. Overall, time spent playing games rose from an average of 12.3 hours per week last year to 13 this year, the survey found. Both console and PC games posted increases, with the PC growing significantly faster than the consoles -- but portable gaming hours, on the other hand, dove 16%. The most popular platform overall, in terms of time spent, was the good ol' PC -- and if that surprises you, you probably haven't looked at Facebook lately. http://videogames.yahoo.com/events/p...a-week/1400467  AT&T to End Unlimited Use Mobile Data Plan Sinead Carew AT&T Inc will stop offering an unlimited pricing plan for new subscribers to its mobile data services, in a move it says will cut prices for as many as 98 percent of its customers. The exclusive U.S. provider for Apple Inc's iPhone said the new metered pricing, which takes effect June 7, means the more customers use their phones for web surfing the more they will have to pay. While pricing for most data users will be $5 to $15 less than the current $30-a-month plan for unlimited usage, prices for AT&T's heaviest will be at least $5 a month higher. Analysts said the move would likely push bigger rival Verizon Wireless, a venture of Verizon Communications and Vodafone Group Plc, to follow suit shortly. Verizon Wireless declined to comment. Bernstein analyst Craig Moffett said the lower fees for light users was an important step "for public relations" but he noted that this would not help the heaviest users. "The low end price reduction for light users will reduce - but not eliminate - the inevitable firestorm of criticism from heavy users, who are certain to be the most vocal commentators," Moffett said. While some web commentators complained loudly about the new pricing, AT&T's mobile chief Ralph de la Vega told Reuters, "It's important we give customers the choice. There are some not signing up for smartphone data plans because they're too expensive," he said. De la Vega said the new plans would have little impact on its average monthly revenue per user (ARPU), an important measurement for wireless operators. Current customers can continue to use the company's $29.99-a-month unlimited data plan, but new customers will be shunted to the new plan. The new plans will start at $15 a month for downloads of 200 megabytes of data. That equals about 400 web pages, 1,000 e-mails with no attachments, posting 50 photos online or 20 minutes of video, according to AT&T. But if users exceed the 200 megabytes usage they will automatically be charged another $15 for another 200 megabytes. The company said 65 percent of its users use less than 200 megabytes of data per month. The next tier costs $25 for 2 gigabytes of data, which is ten times more downloads than the 200 megabytes plan. AT&T said 98 percent of its customers use less than 2 gigabytes of data today. The $25-a-month customers will be charged another $10 for each extra gigabyte of data they download per month. If the result is fewer downloads from very heavy users, the new pricing plan could potentially also ease capacity constraints that have caused network problems for the company in high usage areas such as New York. But de la Vega said the new pricing would not change AT&T's efforts to improve its network capacity. Only a month after its launch the new pricing plans will also impact buyers of Apple's iPad, for which AT&T is also the only U.S. service. Users of iPad will now be offered $25-a-month plans for 2 gigabytes of data, replacing the current $29.99 unlimited plan for these customers. AT&T shares were up 18 cents to $24.51 in morning trade on New York Stock Exchange. (Additional reporting by Ritsuko Ando and Franklin Paul; Editing by Derek Caney) http://www.reuters.com/article/idUSTRE6513H120100602  Steve Jobs Muses on All Things Apple Miguel Helft For Steven P. Jobs, the chief executive of Apple, the timing of his public appearance at the D8 conference could not have been better. Last week, Apple surpassed Microsoft to become the world’s most valuable technology company. A little more than a decade ago, Apple was struggling for its life, and many tech pundits were predicting its demise. So Mr. Jobs’s wide-ranging interview with conference hosts Walt Mossberg and Kara Swisher began, appropriately, with a softball question: How did it feel to stand at the top of the technology heap. “For those of us who have been in the industry a long time, it is surreal,” Mr. Jobs said. “But it doesn’t matter very much. It is not what’s important. It is not why any of our customers buy our products. I think it is good for us to keep that in mind. But it is a little surreal.” Mr. Jobs then hit on all the news that has surrounded Apple recently — the stolen iPhone prototype, the war over Flash with Adobe, the suicides at Chinese contract manufacturer Foxconn, AT&T’s network problems, the rivalry with Google and more. He didn’t make any news or announce any new products or partners, but he delivered some interesting tidbits. Perhaps most significantly, he said Apple has no plans to get rid of Google’s search and maps services on the iPhone or iPad. “We have some Google properties on our phone,” Mr. Jobs said. “Just because we are competing with somebody doesn’t mean you have to be rude.” Mr. Jobs also appeared to pour cold water on reports that Apple was about to unveil a new version of Apple TV, saying that the digital television business was plagued with a series of problems, including challenges in distributing new products. “That’s why when we said Apple TV is a hobby, that’s why we used that phrase,” he said. Mr. Jobs was far more circumspect when he was asked whether there might soon be an iPhone running on a network other than AT&T’s in the United States. Mr. Jobs bit his lip as we appeared to think how to answer. “There might be,” he said. After he was pressed about when that might happen, he added: “The future is long. I can’t talk about that stuff.” Speculation has been building that Apple may soon unveil a phone running on Verizon Wireless. Mr. Jobs said he didn’t set out to have a war with Adobe over the Flash, the Web technology that Apple has refused to include on the iPhone on and iPad. And he said that the success of Apple’s products suggests that consumers are doing fine without it. “We didn’t start off to have a war with Flash,” he said. Mr. Jobs said Apple simply made a technical decision not to invest in a technology that the company believes will decline as others, like HTML5, will rise to replace it. “It wasn’t until we shipped the iPad that Adobe started to raise a stink about it. We didn’t raise a stink about it.” he said. “We weren’t trying to have a fight. We just decided not to use one of their products in our platform.” When pressed on whether the absence of Flash was bad for consumers, he answered that consumers appeared to have spoken with their wallets. “If the market tells us we are making the wrong choices, we listen to the market.” Mr. Jobs said Apple has made a technological bet that flash is not necessary, and that customers, in essence, pay Apple to make such choices and deliver good products. “If we succeed, they’ll buy them, and if we don’t, they won’t,” he said. “People seem to be liking the iPad. We sold one every 3 seconds since we launched them.” Mr. Jobs also predicted that the ongoing shift in technology away from the PC and toward mobile devices will continue. But rather than disappear, the PC will become a niche product, he said. Mr. Jobs compared the role of the PC, the workhorse of computing for the past three decades, to the truck, when America was primarily an agrarian nation. “All cars were trucks because that’s what you needed on the farm,” he said. Now trucks are one in 25 to 30 vehicles sold, he said. “PCs are going to be like trucks. They will still be around.” He then added: “This transformation is going to make some people uneasy.” Mr. Jobs said that he believed the iPad would offer new opportunities for content creators, and especially for news organizations, to charge readers for their products. He advised media companies to price products low, just like Apple did with songs on iTunes. “As one of the largest sellers of content on the Internet today, Apple’s lesson is price it aggressively and go for volume,” he said. “I believe people are willing to pay content. I believe it in music. I believe it in media. And I believe in it in news content.” Mr. Jobs said he was concerned about the rash of suicides as Foxconn, but said the factory was not a “sweatshop” and noted that Apple is “over there trying to understand what is happening.” And he said that he believes that a lot of the problems with making calls on AT&T’s network with the iPhone will be resolved before the end of summer. Mr. Jobs, who is still gaunt, was not asked about his health problems and did not discuss them. But in the only allusion to those problems, at one point during the interview, he said. “The last few years have reminded me that life is fragile.” http://bits.blogs.nytimes.com/2010/0...-things-apple/  The Doctor Will See You Now. Please Log On. Milt Freudenheim ONE day last summer, Charlie Martin felt a sharp pain in his lower back. But he couldn’t jump into his car and rush to the doctor’s office or the emergency room: Mr. Martin, a crane operator, was working on an oil rig in the South China Sea off Malaysia. He could, though, get in touch with a doctor thousands of miles away, via two-way video. Using an electronic stethoscope that a paramedic on the rig held in place, Dr. Oscar W. Boultinghouse, an emergency medicine physician in Houston, listened to Mr. Martin’s heart. “The extreme pain strongly suggested a kidney stone,” Dr. Boultinghouse said later. A urinalysis on the rig confirmed the diagnosis, and Mr. Martin flew to his home in Mississippi for treatment. Mr. Martin, 32, is now back at work on the same rig, the Courageous, leased by Shell Oil. He says he is grateful he could discuss his pain by video with the doctor. “It’s a lot better than trying to describe it on a phone,” Mr. Martin says. Dr. Boultinghouse and two colleagues — Michael J. Davis and Glenn G. Hammack— run NuPhysicia, a start-up company they spun out from the University of Texas in 2007 that specializes in face-to-face telemedicine, connecting doctors and patients by two-way video. Spurred by health care trends and technological advances, telemedicine is growing into a mainstream industry. A fifth of Americans live in places where primary care physicians are scarce, according to government statistics. That need is converging with advances that include lower costs for video-conferencing equipment, more high-speed communications links by satellite, and greater ability to work securely and dependably over the Internet. “The technology has improved to the point where the experience of both the doctor and patient are close to the same as in-person visits, and in some cases better,” says Dr. Kaveh Safavi, head of global health care for Cisco Systems, which is supporting trials of its own high-definition video version of telemedicine in California, Colorado and New Mexico. The interactive telemedicine business has been growing by almost 10 percent annually, to more than $500 million in revenue in North America this year, according to Datamonitor, the market research firm. It is part of the $3.9 billion telemedicine category that includes monitoring devices in homes and hundreds of health care applications for smartphones. Christine Chang, a health care technology analyst at Datamonitor’s Ovum unit, says telemedicine will allow doctors to take better care of larger numbers of patients. “Some patients will be seen by teleconferencing, some will send questions by e-mail, others will be monitored” using digitized data on symptoms or indicators like glucose levels, she says. Eventually, she predicts, “one patient a day might come into a doctor’s office, in person.” Although telemedicine has been around for years, it is gaining traction as never before. Medicare, Medicaid and other government health programs have been reimbursing doctors and hospitals that provide care remotely to rural and underserved areas. Now a growing number of big insurance companies, like the UnitedHealth Group and several Blue Cross plans, are starting to market interactive video to large employers. The new federal health care law provides $1 billion a year to study telemedicine and other innovations. With the expansion of reimbursement, Americans are on the brink of “a gold rush of new investment in telemedicine,” says Dr. Bernard A. Harris Jr., managing partner at Vesalius Ventures, a venture capital firm based in Houston. He has worked on telemedicine projects since he helped build medical systems for NASA during his days as an astronaut in the 1990s. Face-to-face telemedicine technology can be as elaborate as a high-definition video system, like Cisco’s, that can cost up to hundreds of thousands of dollars. Or it can be as simple as the Webcams available on many laptops. NuPhysicia uses equipment in the middle of that range — standard videoconferencing hookups made by Polycom, a video conferencing company based in Pleasanton, Calif. Analysts say the setup may cost $30,000 to $45,000 at the patient’s end — with a suitcase or cart containing scopes and other special equipment — plus a setup for the doctor that costs far less. Telemedicine has its skeptics. State regulators at the Texas Medical Board have raised concerns that doctors might miss an opportunity to pick up subtle medical indicators when they cannot touch a patient. And while it does not oppose telemedicine, the American Academy of Family Physicians says patients should keep in contact with a primary physician who can keep tabs on their health needs, whether in the virtual or the real world. “Telemedicine can improve access to care in remote sites and rural areas,” says Dr. Lori J. Heim, the academy’s president. “But not all visits will take place between a patient and their primary-care doctor.” Dr. Boultinghouse dismisses such concerns. “In today’s world, the physical exam plays less and less of a role,” he says. “We live in the age of imaging.” ON the rig Courageous, Mr. Martin is part of a crew of 100. Travis G. Fitts Jr., vice president for human resources, health, safety and environment at Scorpion Offshore, which owns the rig, says that examining a worker via two-way video can be far cheaper in a remote location than flying him to a hospital by helicopter at $10,000 a trip. Some rigs have saved $500,000 or more a year, according to NuPhysicia, which has contracts with 19 oil rigs around the world, including one off Iraq. Dr. Boultinghouse says the Deepwater Horizon drilling disaster in the Gulf of Mexico may slow or block new drilling in United States waters, driving the rigs to more remote locations and adding to demand for telemedicine. NuPhysicia also offers video medical services to land-based employers with 500 or more workers at a site. The camera connection is an alternative to an employer’s on-site clinics, typically staffed by a nurse or a physician assistant. Mustang Cat, a Houston-based distributor that sells and services Caterpillar tractors and other earth-moving equipment, signed on with NuPhysicia last year. “We’ve seen the benefit, ” says Kurt Hanson, general counsel at Mustang, a family-owned company. Instead of taking a half-day or more off to consult a doctor, workers can get medical advice on the company’s premises. NuPhysicia’s business grew out of work that its founders did for the state of Texas. Mr. Hammack, NuPhysicia’s president, is a former assistant vice president of the University of Texas Medical Branch at Galveston, where he led development of the state’s pioneering telemedicine program in state prisons from the mid-1990s to 2007. Dr. Davis is a cardiologist. Working with Dr. Boultinghouse, Dr. Davis and other university doctors conducted more than 600,000 video visits with inmates. Significant improvement was seen in inmates’ health, including measures of blood pressure and cholesterol, according to a 2004 report on the system in the Journal of the American Medical Association. In March, California officials released a report they had ordered from NuPhysicia with a plan for making over their state’s prison health care. The makeover would build on the Texas example by expanding existing telemedicine and electronic medical record systems and putting the University of California in charge. California spends more than $40 a day per inmate for health care, including expenses for guards who accompany them on visits to outside doctors. NuPhysicia says that this cost is more than four times the rate in Texas and Georgia, and almost triple that of New Jersey, where telemedicine is used for mental health care and some medical specialties. “Telemedicine makes total sense in prisons,” says Christopher Kosseff, a senior vice president and head of correctional health care at the University of Medicine and Dentistry of New Jersey. “It’s a wonderful way of providing ready access to specialty health care while maintaining public safety.” Georgia state prisons save an average of $500 in transportation costs and officers’ pay each time a prisoner can be treated by telemedicine, says Dr. Edward Bailey, medical director of Georgia correctional health care. With data supplied by the California Department of Corrections and Rehabilitation, which commissioned the report, NuPhysicia says the recommendations could save the state $1.2 billion a year in prisoners’ health care costs. Gov. Arnold Schwarzenegger wants the university regents and the State Legislature to approve the prison health makeover. After lawsuits on behalf of inmates, federal courts appointed a receiver in 2006 to run prison medical services. (The state now runs dental and mental health services, with court monitoring.) Officials hope that by putting university doctors in charge of prison health, they can persuade the courts to return control to the state. “We’re going to use the best technology in the world to solve one of our worst problems — the key is telemedicine,” the governor said. WITHOUT the blessing of insurers, telemedicine could never gain traction in the broader population. But many of the nation’s biggest insurers are showing growing interest in reimbursing doctors for face-to-face video consulting. Starting in June, the UnitedHealth Group plans to reimburse doctors at Centura Health, a Colorado hospital system, for using Cisco advanced video to serve UnitedHealth’s members at several clinics. And the insurer plans a national rollout of telemedicine programs, including video-equipped booths in retail clinics in pharmacies and big-box stores, as well as in clinics at large companies. “The tide is turning on reimbursement,” says Dr. James Woodburn, vice president and medical director for telehealth at UnitedHealth. Both UnitedHealth and WellPoint, which owns 14 Blue Cross plans, are trying lower-cost Internet Webcam technology, available on many off-the-shelf laptops, as well as advanced video. UnitedHealth and Blue Cross plans in Hawaii, Minnesota and western New York are using a Webcam service provided by American Well, a company based in Boston. And large self-insured employers like Delta Air Lines and Medtronic, a Blue Cross Blue Shield customer in Minneapolis, are beginning to sign up. Delta will offer Webcam consultations with UnitedHealth’s doctor network to more than 10,000 Minnesota plan members on July 1, says Lynn Zonakis, Delta’s managing director of health strategy and resources. Within 18 months, Webcam access will be offered nationally to more than 100,000 Delta plan members. Dr. Roy Schoenberg, C.E.O. of American Well, says his Webcam service is “in a completely different domain” than Cisco’s or Polycom’s. “Over the last two years, we are beginning to see a side branch of telemedicine that some call online care,” he says. “It connects doctors with patients at home or in their workplace.” Doctors “are not going to pay hundreds of thousands of dollars for equipment, so we have to rely on lower tech,” he adds. The medical records are stored on secure Web servers behind multiple firewalls, and the servers are audited twice a year by I.B.M. and other outside computer security companies, Dr. Schoenberg says. In Hawaii, more than 2,000 Blue Cross plan members used Webcams to consult doctors last year, says Laura Lott, a spokeswoman for the Hawaii Medical Service Association. Minnesota Blue Cross and Blue Shield started a similar Webcam service across the state last November. Doctors who use the higher-tech video conferencing technology say that Webcam images are less clear, and that Webcams cannot accommodate electronic scopes or provide the zoom-in features available in video conferencing. “If they are not using commercial-grade video conferencing gear, the quality will be much lower,” says Vanessa L. McLaughlin, a telemedicine consultant in Vancouver, Wash. Last month, Charlie Martin, the crane operator, was back in the infirmary of the Courageous for an eye checkup. In Houston, his face filled the big screen in NuPhysicia’s office. After an exchange of greetings, Chris Derrick, the paramedic on the oil rig, attached an ophthalmological scanner to a scope, pointed it at Mr. Martin’s eye, and zoomed in. “Freeze that,” Dr. Boultinghouse ordered, as a close-up of the eye loomed on the screen. “His eyes have been bothering him. It may be from the wind up there on the crane.” http://www.nytimes.com/2010/05/30/bu...30telemed.html  Seeking an Objective Test for Attention Disorder Katherine Ellison I’m sitting in front of a gray plastic console that resembles an airplane cockpit. Each time I move, a small reflector on a makeshift tiara resting on my forehead alerts an infrared tracking device pointing down at me from above a computer monitor. Watching the screen, I’m supposed to click a mouse each time I see a star with five or eight points, but not for stars with only four points. It’s a truly simple task, and I’m a college-educated professional. So why do I keep getting it wrong? Halfway into the 20-minute session, I find myself clicking at a lot of four-point stars, while sighing and cursing with each new mistake and stamping my feet, sending further unflattering information to the contraption via tracking straps taped to my legs. Dr. Martin H. Teicher, the Harvard psychiatrist who invented the test, has an explanation for my predicament. “You have some objective evidence for an impairment in attention,” he said — in other words, a “very subtle” case of attention deficit hyperactivity disorder. (Indeed, I had already received a diagnosis three years earlier.) Not only did I click too many times when I shouldn’t have, and occasionally vice versa, but subtle shifts in my head movements, tracked by the device’s motion detector, suggested that I tended to shift attention states, from on-task to impulsive to distracted and back. Dr. Teicher’s invention, the Quotient A.D.H.D. System, is only one of several continuing efforts to find a biomarker — i.e., distinctive biological evidence — for this elusive disorder. Most mainstream researchers consider A.D.H.D. to be an authentic neurological deficit that, left untreated, can ruin not only school report cards, but lives. Nonetheless the quest for objective evidence has gained new urgency in recent years. Many critics say the disorder is being rampantly overdiagnosed by pill-pushing doctors in league with the drug industry, abetted by a culture of overanxious parents and compliant educators. These critics say that the standard treatment — stimulant medications like Ritalin and Adderall — carries a high risk for side effects and abuse in children whose attention problems might have no biological cause. Yet despite the perils of faulty diagnosis, the most common way of detecting the disorder has nothing directly to do with biology. Instead, patients — along with their parents and teachers, in the case of children — are asked to respond to a checklist of questions about symptoms that most mortals suffer at one time or another. Do you (or your child) often make careless mistakes? Do you often seem not to listen when spoken to directly? Do you often not follow through on instructions? This method, similar to the way doctors diagnose most mental illnesses, is so subjective that the answers, and the diagnosis, may depend on how distressed a patient, a parent or a teacher is feeling on a given day. Moreover, parents and teachers, and indeed mothers and fathers, can disagree, obliging a doctor to choose whom to believe. All this helps explain why an objective test has become “the holy grail” for many researchers, said Stephen Hinshaw, chairman of the psychology department at the University of California, Berkeley. Still, he and other experts are not convinced that any one test developed so far has proved better than the prevailing checklist method. Many psychologists who offer comprehensive testing of children with undiagnosed learning problems include some variation of the Continuous Performance Test, a computerized assessment that measures distractibility; it is similar to Dr. Teicher’s invention, but without the motion detector. In Southern California, meanwhile, Dr. Daniel G. Amen has built a business empire on his assertion that he can detect A.D.H.D. with a brain scan using a technology called Spect, for single photon emission computed tomography — a claim still unestablished in peer-reviewed reports of clinical trials. In contrast, Dr. Teicher has reported on trials of his test’s efficacy in the Journal of the American Academy of Child and Adolescent Psychiatry. The Food and Drug Administration approved sales of the device in 2002, and several insurers, including Aetna and Blue Cross, now cover the test, according to Carrie Mulherin, a vice president at BioBehavioral Diagnostics, a startup company in Westford, Mass., that is marketing Dr. Teicher’s system (and paying him royalties; the list price is $19,500). To date, more than 70 clinicians in 21 states have bought or leased a Quotient system, Ms. Mulherin said. Dr. M. Randall Bloch, the Walnut Creek psychiatrist who was demonstrating the program for me recently, has been leasing it since last September, while considering a purchase. “I think it’s really cool,” he said. “It would be great to have more objectivity.” In addition to his lease payments, Dr. Bloch pays BioBehavioral Diagnostics $55 for each patient taking the test, while charging insurance companies as much as $200. While he says he wouldn’t diagnose the disorder on the basis of test scores alone, he has found the system a useful way to seal the diagnosis with patients or their parents who may be reluctant to try medication. The Quotient system has also helped Dr. Bloch discourage patients who have claimed to have attention problems but who, he suspects, were merely interested in taking stimulants for fun, or in hopes of more productivity. “You can tell if they’re trying to game the test,” he told me, pointing to a colored graph on my own assessment denoting attention states. Green marks attentive, yellow is impulsive, red is distracted and blue is “disengaged.” A lot of blue might lead to the suspicion that someone is failing on purpose. While I switched among green, red and yellow, I didn’t have any blue on my graph. “You were working hard,” Dr. Bloch said, approvingly. “It’s how I cope,” I muttered. Dr. Teicher said the Quotient system offered an efficient way to figure out the most helpful kind and dose of medication to treat attention problems. “The stimulants work very quickly,” he explained. “So once we’ve tested a child, we could give him a dose, wait 90 minutes, and if he’s a responder, his performance will improve enormously. If not, we can bring him back the following week and try a different medication. This is a process that normally takes months or years.” The key to his system, he said, is what he suspects will eventually be confirmed as a valid biological marker for A.D.H.D.: an unstable control of head movements and posture, particularly while paying attention to a boring task. Last fall the National Institutes of Health awarded Dr. Teicher a $1 million grant from the federal stimulus package to delve further into the quest for a definitive test or biomarker for the disorder. He plans to focus his research on three detective strategies: his Quotient system, magnetic resonance imaging to compare blood flows in different brain regions, and the ActiGraph, an activity monitor widely used by medical researchers. James M. Swanson, a developmental psychologist and attention researcher at the University of California, Irvine, praised Dr. Teicher’s research, echoing his concerns about the need for a more objective test to detect the disorder. But he questioned whether the Quotient system produces more reliable diagnoses than a doctor’s dogged questioning of a child’s parents and teachers, and also whether it is an appropriate way to figure out the right dose of medication. “It’s essentially a dull, boring task,” he said of the Quotient system, “so do you want to medicate your child to pay attention to dull, boring tasks?” As I left Dr. Bloch’s office with my printed-out assessment, I pondered some questions of my own. How much of my supposed impairment is rooted in my brain, and how much in a culture that daily trains me to yank my focus between e-mail and cellphone calls? Do I need Ritalin or a meditation retreat — or just more interesting work, or maybe more peaceful children? I could use an objective test for this one. Is anyone working on it? http://www.nytimes.com/2010/06/01/he...attention.html  For Very Young, Peril Lurks in Lithium Cell Batteries Tara Parker-Pope Last fall, 13-month-old Aidan Truett of Hamilton, Ohio, developed what seemed like an upper respiratory infection. He lost interest in food and vomited a few times, but doctors attributed it to a virus. After nine days of severe symptoms and more doctor visits, the hospital finally ordered an X-ray to look for pneumonia. What they found instead was totally unexpected. The child had ingested a “button” battery, one of those flat silver discs used to power remote controls, toys, musical greeting cards, bathroom scales and other home electronics. The battery was surgically removed the next day, and Aidan was sent home. But what neither the doctors nor his parents realized was that the damage had been done. The battery’s current had set off a chemical reaction in the child’s esophagus, burning through both the esophageal wall and attacking the aorta. Two days after the battery was removed, Aidan began coughing blood, and soon died from his injuries. To this day, Aidan’s parents don’t know where the battery came from. “This is something I would never want another parent to live with,” said Michelle Truett, Aidan’s mother. “I was oblivious as to how dangerous they were, and I want more people to know the danger.” Such deaths are extremely rare. There were fewer than 10 documented during the last six years. But ingestion of lithium cell batteries, which children may mistake for candy and elderly adults for medication, is a surprisingly common problem, documented this week in two reports in the medical journal Pediatrics. About 3,500 cases of button cell battery ingestion are reported annually to poison control centers. But while swallowing batteries has occurred for years, the development of larger, stronger lithium cell batteries has increased the risk of severe complications. Data from the National Capital Poison Center in Washington found a sevenfold increase in severe complications from button cell ingestions in recent years. Moderate to severe cases have risen from less than a half percent (about a dozen cases per year) to about 3 percent (nearly 100 cases per year), based on a review of 56,000 cases since 1985. Among the serious complications, the chemical reaction triggered by the batteries can damage vocal cords, leaving children with a lifelong whisper. Damage to the gastrointestinal tract means some children require feeding tubes and multiple surgeries. “The injuries are so much more serious,” said Dr. Toby Litovitz, director and lead author of both articles in Pediatrics. “It’s like drain opener or lye. It’s not something you want in the esophagus of your child.” The batteries that pose the greatest risk are those that begin with the number 20, which stands for 20 millimeters. They are newer and stronger than older models. Batteries numbered 2032, 2025 and 2016 are responsible for more than 90 percent of serious injuries. “Industry has shifted to this battery, and it has very popular appeal,” Dr. Litovitz said. “There are a lot of reasons why we want to use this battery, but the problem is we’ve got to use it in a safer way.” Federal safety rules require toys that use the batteries to have battery compartments that are locked with screws. But devices intended for adults — like bathroom scales and remote controls — often hold the batteries in with a simple plastic cover that can fall off or be removed easily. That’s what happened when 13-month-old Kaiden Vasquez of Bristow, Va., picked up the remote control to his parent’s iPod docking station. Somehow, he dislodged the battery and swallowed it. But his parents did not notice the missing battery when he began crying hysterically and could not be calmed. Emergency room doctors diagnosed a stomach flu, but a week later the child’s pediatrician took an X-ray and saw what he thought was a quarter. When the round item was removed, doctors discovered the battery and kept Kaiden for observation. The battery had burned a hole in his esophagus and trachea and he required a feeding tube and two months of home nursing care. Kaiden, who will be 3 in July, has recovered, although severe reflux after the incident damaged his teeth. “I don’t allow any of those disc batteries into my home,” said Kaiden’s mother, Amy Vasquez, who has three other young children. “I never thought a remote would do so much damage to my child.” Battery ingestion is also a problem among the elderly, who often mistake hearing aid batteries for medication. But in those cases, the battery typically doesn’t get stuck because the digestive tract is larger and the battery used in hearing aids is smaller. When children ingest batteries, it’s usually not because they found one loose in the home. In 60 percent of the cases involving children under age 6, the child has removed the battery from the electronic device. The problem is that most parents are not even aware when it happens, yet studies show the battery begins to cause severe damage within just two hours of ingestion. “It’s really a tight timeline, because a lot of these cases aren’t witnessed,” Dr. Litovitz said. “Children present with symptoms that are nonspecific, the parent doesn’t know the battery was ingested — that makes it difficult for the doctor to diagnose.” Dr. Litovitz said the problem needed to be addressed by manufacturers of electronic products, who should secure the battery compartments in all devices, not just toys. “Children have ready access to remote controls, watches, garage door openers,” she said. “Our major pitch is to get the industry to do something about the battery compartment, but parents also need to know that they need to be dealing with these batteries with a lot more vigilance and keeping them out of reach of the child.” Cara George of Littleton, Colo., has been working to raise awareness about lithium batteries ever since her 18-month-old daughter, Brenna, died after ingesting one nearly two years ago. “I want to raise awareness for parents, for doctors, for the community,” she said. “I think there should be warnings on every item the batteries are in. They are in greeting cards and children’s books that talk. They’re everywhere.” http://well.blogs.nytimes.com/2010/0...batteries/?hpw  France Cracks Down on Pop-Up Drinking Parties Grant Rosenberg It sounds like a quintessentially French problem: rogue cocktail parties. Over the past year, France has seen a growing trend in large unlicensed, outdoor gatherings organized through Facebook — and attended by thousands of young drinkers — popping up across the country. Now, as alcohol abuse continues to rise among French youth, the recent death of a reveler has prompted the government to try to find a way to keep the parties safe without shutting them down completely. Called apéros géants, or giant aperitifs, after the traditional pre-dinner drink (although attendees drink whatever they bring), the pop-up parties are often anonymously planned and — since they have no permit from local authorities — illegal. To date, nearly 60 have taken place in public parks around France, with organizers competing to see which cities can draw the largest crowds. But the party turned tragic in mid-May, when a 21-year-old man attending a 10,000-person apéro in the western city of Nantes took a fatal fall from a bridge after reportedly consuming a large amount of alcohol. Another 57 people at that party were hospitalized for excessive alcohol consumption. Binge drinking, long considered a comparatively minor problem in France, has been on the rise among young people in recent years, and many point to it as the reason that apéros have escalated from rebellious fun to potentially lethal gatherings. Since the Nantes death, the French government has been wrestling with ways to deal with the problem without exacerbating it. Concluding that an all-encompassing ban would lead to more hastily arranged apéros in unsuitable locations that could be even more dangerous, French Interior Minister Brice Hortefeux declared on May 19 that apéros would be required to follow the regulations for events like outdoor concerts. That means organizers must identify themselves, submit a permit request in advance and allow the presence of health and safety officials at the festivities. Hortefeux said that whether an apéro could be held would be evaluated on a case-by-case basis. France got to see this new policy in action last Saturday night, in the northern city of Lille, when two parties were scheduled to take place simultaneously. Back in March, a local event-planning company called 4NOX launched a Facebook page for an apéro géant to be held in the Place de la République on May 29. Then a second apéro was called by an anonymous Facebook organizer for the same night in a separate location in the city, with the goal of attracting between 5,000 and 10,000 people. But on May 27, Lille police issued an order banning any apéro that evening, leading 4NOX to cancel its party with a message on the event's Facebook page stating its disappointment with how the situation was being handled by authorities and saying that its party's only objective was "a cultural, religious and intergenerational intermingling in an architecturally pleasant locale." Meanwhile, the anonymous organizers behind the second apéro posted a message on that event's Facebook page maintaining that theirs would go on despite the ban — though as a concession, they discouraged people from bringing alcohol. They then moved the location to the site where 4NOX had planned to hold its apéro. As the French papers reported that Lille police were hastily pulling together crowd-control measures, France's Youth and Active Solidarity Minister, Marc-Philippe Daubresse, made a personal appeal directly on the event's Facebook page, asking that it be postponed until late June when it could be organized officially and carried out in a safe manner. "Just because my office writes up a press release doesn't mean the young people are going to read it," he tells TIME. "So posting my own message on the page of the event is a more efficient way to communicate with those already interested." Daubresse's pleas, though, were quickly deleted from the page by the organizers. "Not exactly great proof of tolerance on their part," he says sardonically. In the end, only a few people showed up. One attendee posted a photo at 9:22 p.m. on Saturday showing what looks like a handful of people standing around, and called the event "a big emptiness, with small groups quickly sent away by police as soon as they took out a bottle." But Beyram Marouchi, events coordinator for 4NOX, says alcohol isn't the point. He says these gatherings aren't about excessive drinking as much as they are about bringing big groups of people together to socialize. "I think there is a certain malaise in France these days and a need for people to meet up in a large way that simply can't be done in small cafés," he says. Daubresse sees the apéros as a way for kids to assert their independence. "It's a reaction to adults," he says. "It's a way to say, 'You don't have confidence in us, so we're going to show you that we can organize something by ourselves.' " Whatever the motivation behind the apéros, the government still faces the challenge of transitioning them into safe and legal gatherings. To help, Daubresse announced on May 26 a plan to set up a rapid-response safety cell that could arrive at the location of an apéro within 72 hours of the event's announcement, bringing with it medical and security personnel as well as representatives from youth and health organizations. But before any of that can happen, authorities are learning to use social-networking sites to keep track of apéro invites and reach out to their organizers. Because the party planners rarely identify themselves, authorities can only monitor the events pages as they are created, then entreat the organizers to get in touch so that together they can make arrangements for the event's safety. Daubresse claims that illegal apéros are already on the decline, the result of more and more organizers' choosing to consult with authorities. Still, as much as France's government wants to turn apéros géants into officially approved and monitored events, for some the illicit element is part of the appeal. With summer beginning and more invitations popping up on Facebook for apéros in cities across the country, the party could just be getting started. http://www.time.com/time/world/artic...992982,00.html  Bridge Ratings: Social Marketing Boosts Radio Listening FMQB Bridge Ratings has conducted a new study called Social Network Hierarchies and their Impact on Business, and the key finding shows that not only does social marketing work, if done with field-tested tactics and messaging, the impact on corporate growth over-reaches and out-performs any other marketing strategy. Bridge says the use and social aspect of media marketing is accelerating faster than previously forecast, and that radio is one of the top businesses to benefit from this growth. Users of social media progress through a general path of social networking types or hierarchies, and the concept of this social network hierarchy behavior is evident through each demographic group and serves as a more effective strategy for reaching consumer targets with brand messages. For example, young girls age 6 to 17 start out with social networks like Club Penguin, Poptropica and Stardoll, but over time they graduate to more interactive sites such as Twitter or gaming sites such as Habbo.co.uk. While this group of young people are turning their backs on sites such as Facebook and MySpace, the number of 35- to 54-year-olds using such sites has rocketed by 25 percent in the last year. According to Bridge, there are four categories of business where the "hierarchy process" of social marketing yielded note-worthy results, and those include radio listening, digital downloads, Internet radio and financial services. One terrestrial radio company with stations in large and medium markets conducted a four-week test of the social marketing Hierarchy process in four of the company's market clusters. A total of 22 stations participated. The average number of listening occasions for this group of stations was 16 per week. After four weeks of social marketing, the stations realized a 75 percent increase in listening occasions to 28 per week, Bridge reported. Secondly, the report says that one record label compared its average weekly digital download activity on four of its mainstream acts to a four-week social marketing campaign based on the hierarchy marketing method. By way of capturing targeted consumers through the three most common social media, promotions, social network conversations and other marketing techniques unrelated to file cost, boosted activity significantly. Over the course of the four week test downloads increased 34 percent compared to the average activity. Bridge also pointed to an Internet radio company that offers a variety of music streams and has averaged approximately 620,000 session starts per week. With a social media marketing campaign flighted per the hierarchy model, session starts over six weeks improved 20 percent. More details on the Social Media Network Hierarchy study are available here. http://www.fmqb.com/article.asp?id=1824768  Disney Puts Movie Tickets on a Facebook Site Brooks Barnes The Walt Disney Company has created what it believes is a first-of-its-kind application allowing Facebook users to buy tickets to “Toy Story 3” without leaving the social-networking site and while, at the same time, prodding their friends to come along. The application, called Disney Tickets Together, could transform how Hollywood sells movie tickets by interweaving purchases with the powerful forces of social networking. When you buy a ticket through Disney’s application, for instance, it alerts your Facebook friends and prompts you to invite them to buy tickets of their own. Disney quietly introduced the service on May 26 with a simple post on the site’s official “Toy Story 3” page, which has over 732,000 fans. While many theaters won’t make tickets available for the Pixar film for another week – its release date is June 18 – early results indicate that people are using the application to buy tickets in groups as large as 80, according to Disney. “The whole idea is that no friend gets left behind,” said Oliver Luckett, senior vice president and general manager of DigiSynd, a Disney subsidiary that manages the entertainment giant’s presence on social networking platforms. Disney Tickets Together, which has been in development for months, works in conjunction with ticket-buying sites like Fandango.com and covers the majority of movie theaters in North America, according to Mr. Luckett. Facebook receives no cut of the ticket sales but does, in theory, get more eyeballs on its site. For now, only “Toy Story 3” tickets are available. But Mr. Luckett said other Disney movies will follow if the application is deemed a success. Facebook, which is approaching 500 million users around the world, has become a crucial marketing tool for entertainment companies. Disney alone operates hundreds of promotional pages on the site for its various products – motion pictures, theme park attractions, consumer products, television shows – that cumulatively reach tens of millions of people. But Disney Tickets Together represents a deepening relationship between businesses and Facebook users, according to Dan Rose, the site’s vice president of partnerships and platform marketing. “What Disney is doing moves beyond just creating awareness to using the platform to acquire customers directly,” Mr. Rose said. “This is the first time that a movie studio has tried this, which we think makes a lot of sense because moviegoing is one of those activities that is inherently social.” Buying movie tickets in advance via the Web is becoming more common, especially in cities where screenings routinely sell out. But most ticketing is still done the old-fashioned way: people show up at the box office at an appointed time. At most, online ticketing sites currently account for about 20 percent of the box office for a wide-release movie. Anything that boosts ticket sales is likely to be warmly embraced by studio executives and theater owners, who are struggling with declining attendance. Although higher ticket prices have propped up sales, moviegoing is on the decline. About 23.4 million people went to the movies over the Memorial Day weekend, a 22 percent decline from last year and the lowest total since 1993, according to Hollywood.com, which compiles box office statistics. Disney is distinctly positioned to innovate on the Web. Steven P. Jobs, the Apple chief executive, joined the Disney board with the 2006 acquisition of Pixar and became Disney’s largest shareholder. Sheryl Sandberg, Facebook’s chief operating officer, joined Disney’s board six months ago. The entertainment conglomerate has had difficulties figuring out its approach to its own Web site, Disney.com, largely because of management stumbles within the Disney unit that oversees that businesses, analysts say. But the company – notably its television group, which includes ABC and ESPN – has been aggressive about online video and Apple’s iTunes store and iPad. Disney Tickets Together works in the same manner as other Facebook applications. Users click on the “go to application” button and give authority for the service to access personal information in their profiles. A page then loads ticket times at nearby theaters based on their profile location settings. A Disney Tickets Together search in the Los Angeles ZIP code of 90004 on Tuesday served up 88 screenings at 12 theaters. The application provides an option for inviting friends who are not members of the site. The slogan: “‘Toy Story 3’ arrives in theaters on June 18! Who are you bringing with you?” http://www.nytimes.com/2010/06/02/bu.../02disney.html  Digg is Deadd It was a good run, Digg.com. You certainly had a great idea and funneled plenty of Web traffic to opportunitstic and manipulative publishers. Alas, the run is over. And it's not coming back. According to the latest Compete.com data (April, 2010) Digg lost an astounding 13.8 million unique visits from March to April, 2010 -- a near 36 percent drop. Apparently sensing impending doom, Digg founder Kevin Rose has made several announcements of retooling Digg, but nothing has materialized. In fact, the announcements might have been the worst thing Digg founder Kevin Rose could have done. It's been over a year since Rose announced that changes would come. In the mean time, Facebook and Twitter have soared and it appears the Digg crowd grew tired of waiting. While the changes seem to be close to a reality now, it's too late. A recently released video demonstrates what will change with the new Digg. And, by all accounts, it's another social network. An unnecessary one. The main focus is to make friends (starting by importing your social graph from sites like Facebook) and Digg stories. Then, your new Digg page will show the stories Dugg most by all your friends. Sound like something your friends "liked" on Facebook? Or perhaps something retweeted on Twitter? The biggest problem with Digg in the past was that unless you devoted serious time to it and knew how to work the system, you had little hope of ever making the front page. The only stories that made the front page were typically those voted up by voting blocs; networks of like-minded individuals attempting to send streams of traffic to each others' sites no matter the content of the story. And if you didn't make the front page, the benefits were very little, if any. Now, you still will need to dedicate serious time to the site -- only this time you won't receive near the level of exposure. That is, unless your "friends" vote up your stories at a breakneck pace. Which, for all intents and purposes, puts us right back where we started with Digg. In other words, there's no innovation here and the real value proposition of Digg hasn't changedm, it's just become more labor intensive. In the soon-to-be end, Digg will become known as the first network to die from social fatigue. Facebook and Twitter are booming, LinkedIn is holding steady and even MySpace seems to have settled into a niche. But Digg is in a deadly, unrecoverable tail spin. The fact is, people -- real people -- are beginning to tire. Submit this, upload that, vote on this, "like" that, be my "friend", check in here, suggest this, retweet that ... there's already so much to do. The only thing left to "Digg" is a grave. http://www.websitemagazine.com/conte...-is-deadd.aspx  Opinion: Why the Web Benefits Liberals More than Conservatives Gregory Ferenstein Editor's note: Gregory Ferenstein is an author and educator who writes about the intersections of technology, business and politics. He teaches at the University of California, Irvine, and is a fellow at the University of California Center for the Study of Democracy. From the micro-donation platform first popularized by Howard Dean in 2003 to the million-strong Barack Obama Facebook page to the huge audience of the Huffington Post, liberals have been the dominant political force on the internet since the digital revolution began. Now, research out of Harvard University's Berkman Center for Internet and Society suggests that the reason behind this imbalance may be the liberal belief system itself. Liberals, the research finds, are oriented toward community activism, employing technology to encourage debate and feature user-generated content. Conservatives, on the other hand, are more comfortable with a commanding leadership and use restrictive policies to combat disorderly speech in online forums. All of this suggests that the internet may benefit liberals more often than conservatives -- at least for now. The different approaches of the top two political blogs may illustrate the correlation between ideology and online strategy. The Huffington Post's closest conservative competitor, Hotair.com, has only a fraction of its audience size and is tightly controlled by an inner circle of three authors. A leading right-wing blog, Hot Air was founded by Michelle Malkin, an author who is known for her support of wartime loyalty oaths and racial profiling as a defense against terrorism. In criticizing Obama's 2009 address to the United Nations, she said, "he solidified his place in the international view as the great appeaser and the groveler in chief." Indeed, Malkin's hard-line national security views are matched by Hotair's unusually restrictive comment policy. The site permits comments only by registered users; currently, registration is closed to any new users. The site states, "We may allow as much or as little opportunity for registration as we choose, in our absolute discretion, and we may close particular comment threads or discontinue our general policy of allowing comments at any time." By contrast, the left-leaning Huffington Post, the most visited blog on the Internet, has thousands of bloggers and invites active users to become featured authors and comment facilitators. Founder Arianna Huffington herself supported working diplomatically with the international community to deal with Saddam Hussein and recently endorsed Jeremy Rifkin's book "The Empathic Civilization," which she says "allows humanity to see itself as an extended family living in a shared and interconnected world." Thus, from just a snapshot of the top political bloggers, one catches a glimpse of an emerging pattern: leadership and control from the right, and equality and community on the left. Harvard professor Yochai Benkler finds that these differences are representative of the broader political web. "The left not only chooses more participatory technology, but also uses the available technological tools to maintain more fluid relations between secondary or user-contributed materials and those of primary contributors," he writes. "The left is more egalitarian in opportunities for speech, more discursive, and more collaborative in managing the sites." By contrast, Hot Air's prohibitive policies, and Malkin's support of strong leadership, seem consistent with Benkler's conclusion that the right is more "hierarchical" in its approach. While any definitive statements about a technology still in its infancy are premature, the inclusiveness of the liberal approach does seem to have its advantages. Obama's Internet strategy is credited with giving grass-roots supporters space to find unique ways to reach their more apathetic peers and motivate them through user-generated content. This openness to outsiders gave rise to surprising internet sensations such as the iconic "Hope" poster and enormous gatherings coordinated by social-networking activists. Indeed, conservative Scott Brown's stunning victory in a Massachusetts Senate race took its strategy from Obama's playbook. Instead of micromanaging the campaign message, Brown permitted an unknown universe of latent conservative activists to contribute as they saw fit. "An engaged following is more likely to retweet, to comment on blogs, to respond to unfounded criticism," Boston political consultant John LaRosa told Wired. Of Brown's campaign, he said, "it became a movement, and it just fed on itself." But even if more conservatives adopt Brown's online strategy, right-wing constituents overall may be less comfortable with grass-roots activism. Russell J. Dalton, a political science professor at the University of California, Irvine, says that among politically active youth, liberals are substantially more likely to donate money, attend a rally and participate in online discussions. Republicans tend to see a "limited participatory role" for citizens, Dalton writes in his book "The Good Citizen: How a Younger Generation Is Reshaping American Politics." The conservative philosophy of ironclad loyalty to a singular message does have decided advantages. In Congress, strong party loyalty has allowed Republicans to vote as a bloc, giving them formidable strength despite their minority status. However, the internet is less predictable. And, from what we have observed from the short life of the web, opening one's site to the capricious innovations of grass-roots users can be enormously beneficial but hard to control. Conservatives may one day embrace the participatory web en masse. However, the very structure of the internet as a decentralized grouping of communities may never appeal to the large portion of right-wingers who prefer military-style hierarchies and commanding leaders. And, as years go by without a conservative social-media pioneer or a top-ranked website, it looks as though the internet has already chosen a side. http://www.cnn.com/2010/TECH/web/05/...ex.html?hpt=C2  John Perry Barlow: Internet has Broken Political System Gautham Nagesh The deluge of information available on the Web has made the country ungovernable, according to Electronic Frontier Foundation co-founder John Perry Barlow. "The political system is broken partly because of Internet," Barlow said. "It's made it impossible to govern anything the size of the nation-state. We're going back to the city-state. The nation-state is ungovernably information-rich." Speaking at Personal Democracy Forum in New York on Thursday, Barlow said there is too much going on at every level in Washington, D.C., for the government to effectively handle everything on its plate. Instead, he advocated citizens organizing around the issues most important to them. Barlow also said that President Barack Obama's election, driven largely by small donations, has fundamentally changed American politics. He said a similar bottom-up structure is needed for governing as well. "It's not the second coming, everything won't get better overnight, but that made it possible to see a future where it wasn’t simply a matter of money to define who won these things," Barlow said. "The government could finally start belonging to people eventually." The former Grateful Dead songwriter said those disppointed in Obama are disregarding the extent to which the political system is broken. He blamed the Beltway establishment, which he said is loathe to give up any accumulated influence. "There is a circle of fat around the Beltway that is incredibly thick" Barlow said. "We can no longer try to run this country from the center. We've got to run it, just like the Internet, from the edges." A longtime advocate of individual's rights online, Barlow also had some harsh words for the world's leading search firm. "Google’s capacity to control human thought makes the Catholic church jealous, I bet," Barlow said. "They wish they’d thought of it." Despite his concerns, Barlow remains optimistic about the Internet's ablitity as a force for good in politics, describing himself as a techno-utopian. "There are lots of battles to be fought, we can’t give them up," Barlow said. "You folks in this room have the capacity to be some of the greatest ancestors anybody ever had." http://thehill.com/blogs/hillicon-va...litical-system  The Pirate Bay Couples With Meezoog Belowdecks To Launch Dating Site Leena Rao In a bizarre move, The Pirate Bay, the world’s largest BitTorrent tracker, is partnering with social dating site Meezoog to launch an online dating site PirateDate.com, to take on Match.com, Zoosk and others. The Pirate Bay, which has had a tumultuous year, is launching a dating network around sharing. PirateDate will allow singles to share and assist their social connections in finding potential dates, while getting recommendations and referrals from their friends. Pirate Date is utilizing Meezoog’s technology to provide users with “social proximity” measurements, that allow people to efficiently filter their cyber connections. According to the site, personal information added by members is immediately visible to their friends (through Facebook connect), encouraging users to be honest with their information. Pirate Date’s ‘Social Radius’ technology exposes members to singles who are socially connected to them, as well as displays how they are connected. The site will also share users’ ‘Trust Paths’ to every member, showing people’s social graph. And the site’s ‘Social Proximity Gauge’, calculates how close you are to people you find interesting on Pirate Date. It’s unclear who would actually want to join this site considering the Pirate Bay’s brand. It seems more oriented towards men than women, considering the homepage of Pirate Date includes a picture of an attractive woman in a pirate’s costume. And why would you join this site over Match.com, E-Harmony or others that already have a considerable user base? While a dating site seems like an odd departure for a file sharing site, it makes sense that the Pirate Bay would want to focus on other verticals considering the legal troubles the site has been involved in with sharing content. A few weeks ago the site was shut down thanks to an injunction obtained by the film studios which halted bandwith to the site due to pirated content. The Pirate Bay just announced a new bandwith host, the Swedish Pirate Party. http://techcrunch.com/2010/06/01/the...h-dating-site/ Until next week, - js.  Current Week In Review  Recent WiRs - May 29th, May 22nd, May 15th, May 8th Jack Spratts' Week In Review is published every Friday. Submit letters, articles, press releases, comments, questions etc. in plain text English to jackspratts (at) lycos (dot) com. Submission deadlines are Thursdays @ 1400 UTC. Please include contact info. The right to publish all remarks is reserved. "The First Amendment rests on the assumption that the widest possible dissemination of information from diverse and antagonistic sources is essential to the welfare of the public." - Hugo Black |
||||
|
|

|
 |
| Thread Tools | Search this Thread |
| Display Modes | |
|
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| Peer-To-Peer News - The Week In Review - February 13th, '10 | JackSpratts | Peer to Peer | 0 | 10-02-10 07:55 AM |
| Peer-To-Peer News - The Week In Review - January 30th, '10 | JackSpratts | Peer to Peer | 0 | 27-01-10 07:49 AM |
| Peer-To-Peer News - The Week In Review - January 23rd, '10 | JackSpratts | Peer to Peer | 0 | 20-01-10 09:04 AM |
| Peer-To-Peer News - The Week In Review - January 16th, '10 | JackSpratts | Peer to Peer | 0 | 13-01-10 09:02 AM |
| Peer-To-Peer News - The Week In Review - December 5th, '09 | JackSpratts | Peer to Peer | 0 | 02-12-09 08:32 AM |