
 |
|
|||||||
| Peer to Peer The 3rd millenium technology! |
 |
|
|
Thread Tools | Search this Thread | Display Modes |
|
|
#1 |
|
Join Date: May 2001
Location: New England
Posts: 10,016
|
Established 2002
  "If you are a file-sharer, you know that the likelihood of you being caught is very similar to that of being hit by an asteroid." – Mark Mulligan "I can take any machine and make it look guilty, or not guilty. Whatever I want." – Vincent Liu "There's no extortion going on. They're not demanding to the Ministry of Finance, the Ministry of Agriculture, 'Pay us $50 million, or we keep this up.' They're not trying to disrupt e-commerce--they're making a political statement." – Jose Nazario "A billion customers in the world are waiting for a $2 pair of eyeglasses, a $10 solar lantern and a $100 house." – Dr. Paul Polak "I noticed he has a purse, but I didn't realize he's a boy." – Ewa Sowinska "They’re famous, pretty and all the boys like them." – Arielle Urvater "The barrier to get into the industry is so low: you need a video camera and a couple of people who will have sex." – Paul Fishbein "Azerbaijan comes out on top." – The Economist "Tear gas, pot and patchouli were the scents of the 1960s." – Holland Cotter June 2nd, 2007  Why I'm File-Sharing, Again Lauren Patrizi I started with Napster, moved to Gnutella, and now I'm operating on ITunes. Our generation certainly was the most feared by the music industry as we sat in our dorm rooms endlessly downloading every song from old school Salt 'N Pepa to random bootlegs of the Grateful Dead. Whether we liked it or not, we were downloading illegally. Well I've stopped downloading illegally--momentarily, anyways--and I'm now paying a dollar for each song. Today I joined PodFitness, which is a website that takes your MP3s and records a personal trainers' directions (faster! one more crunch!) with my music. Well, I learned something quite distasteful after having downloaded the program. Apparently I have more access to the songs I possess illegally than the songs I actually paid for! Because of a controversial practice by the music industry called Digital Rights Management, I can basically do little to nothing with the music I purchased via ITunes. The program will not allow me to incorporate the music I own with my PodFitness. I also learned that I cannot take my songs and mix them into videos I made for personal use. The record companies should realize that making videos, mixing our songs, and transferring them to our mp3 players is what we do. If they still want our business they should allow us to do what we want with the music we own. I'm about to download LimeWire so that I may use the songs as I wish. This works out doubly well. I'm again no longer paying for my music and if I wish to mix my music I can do so. I may need bail money and after which I'll be accepting any monies through PayPal. http://www.campusprogress.org/page/c...roup/main/C2D7  DRM-Free iTunes Set This Week? Apple is prepared to launch its DRM-free catalog of music from EMI this week, according to French sources familiar with negotiations for multiple online music stores. The seeming delay for introducing the new tier of content has been primarily attributed to a desire to offer the entire catalog at once in the unprotected format rather than a gradual rollout. The companies' technicians are simply in the later stages of encoding and hosting the files before they go live, the contact says. Apple's terms will require that whole albums be offered as a second tier of 256Kbps AAC files without the iTunes-only FairPlay copy protection scheme, necessitating that the company revisit existing master copies on an individual basis. The iTunes Store itself was not described as an issue with the upgrade. Legal issues may also have contributed to the relatively late debut, with Apple and EMI having reportedly signed a final deal only last week following negotiations of similar contracts with both the just-announced Amazon store and Europe's VirginMega service. Both Apple and EMI are nevertheless hoping to "ideally" have the change implemented before the end of the month, the report says. Whether or not this will meet Apple's regular Tuesday update schedule is currently unknown. http://www.macnn.com/articles/07/05/...nes.this.week/  TUAW Tip: Don't Torrent That Song... Erica Sadun  Sure, you can now download music from the iTunes store without DRM but that doesn't mean you should just willy nilly start sharing that music with your friends. For one thing, it's illegal. For another, your account information is embedded into that m4a music file. Don't believe me? Try this yourself. 1. Launch Terminal. You'll need to be comfortable at the command line to perform this check. 2. Navigate to one of your iTunes plus downloads. If you have a US iTunes account, you can download the iTunes plus "Ooh La" single of the week. 3. Use the UNIX "strings" command to look at the text in your data and grep to search for your name. e.g. strings 01\ Ooh\ La.m4a | grep name Alternatively, open all the strings in TextEdit: strings 01\ Ooh\ La.m4a | open -f. Bottom line: DRM-free doesn't mean that Apple suddenly supports piracy. http://www.tuaw.com/2007/05/30/tuaw-...ent-that-song/  Qnext 3.0 Publisher: Qnext Corp Size: 34.8 MB OS: Windows 2000/XP/2003 Linux Mac OS X License: Freeware Price: Free Updated: 2007-05-27 Qnext is the easiest way to share all of your music, photos, and files with anyone, instantly. You can also use it to talk to IM and Email contacts from a single list. And now you can talk and share with anyone, even if they don't have Qnext. In seconds, you can broadcast and share an unlimited amount of your music, photos, and files to your friends and family. http://www.mp3cdsoftware.com/qnext--...oad-33091.html  Good advice Dance Music Trends Mizz Dragon Music has been popular for centuries, but the styles, technology and manner in which people find music has changed. Music can now be accessed more easily by a wider group of people than ever before. Downloadable Music Thanks to the increasing popularity of the internet, dance music is now easier than ever to find online. With just a computer and a modem, you can conduct an internet search and find your favorite artists or song in a few minutes. Many sites offer songs or albums for a set fee. You could spend hours just perusing their extensive list of artists. Peer To Peer Programs You might also want to consider downloading a P2P or Peer To Peer program to find new sources of music. After installing a program such as eMule, LimeWire or Gnutella, you can share your vast collection of music with other users. You can search for a specific artist, album title or song and download music from connected users all over the world. Internet Radio More and more radio stations now offer online programs. If you search for online stations, you may be very surprised at the wide variety of musical genres and stations available worldwide. You can find your favorite station from Chicago, Brazil or Spain and listen to it from the comfort of your own home. This is a great way to discover new world music that is popular in other countries. Music Technology People still listen to dance music on their car or home radio and at clubs, concerts and festivals. However, technology has expanded the availability and portability of music. Music lovers can now download music in a condensed format to their portable MP3 players. Thousands of songs will fit on a device smaller than a stick of gum so you can listen to music while exercising or commuting. Many of the latest cell phones also allow owners to download and listen to music. In fact, you can even watch music videos on some of the newer models! Another current trend is to download your favorite music and use it as a ringtone for your cell phone. http://www.dragonsofsound.com/2007/0...-music-trends/  France Tightens Noose on P2P Music Telecom Paper (subscription), Netherlands French government legal body Conseil d'Etat has tightened the noose on Peer to Peer music. It overturned the national commission on IT and liberties' (CNIL) ... http://www.telecom.paper.nl/site/new...ract&id=169656  File Sharers Auto-Tracked in France p2pnet.net In France, record companies can now automatically track p2p users who share more than 50 files within 24 hours, "and keep their records for further legal proceedings," says the country's Council of State. "The decision comes as a blow to the French National Commission for Data protection and the Liberties who ruled in the fall of 2005 that automatic surveillance of P2P networks violates local privacy laws," says P2P Blog. But French file sharers aren't taking it lying down. They've launched 51 fichiers (51 files) as a protest against the "systematic criminalisation of the Peer-to-peer networks and their users". French Net users who want to speak against the ruling should, "share at least 51 files that are freely distributable (e.g.: published under a Creative Commons license, or that are public domain) and keep them on the P2P system until 'something happens'," says the site. Following an article on Scoopeo, and comments from "other channels," it looks like the auto-monitoring would be based on entries on a list of 10,000 files, Clubic states on the protest page. "That means that, most probably, if you are fan of Johnny Halliday and that you download his music, you have more chance ... than if you are fan of a dark regional group of rock'n'roll-garage," says the post. Only files which can be shared and distributed legally should be used, emphasises 51 files, also pointing out the limit can easily be circumvented because p2p file sharing applications can be pre-set to automatically limit files to 49. Meanwhile, there are all kinds of questions relating to the auto-monitoring process, 51 files points out. Exactly what's included on the list? - for example. By what means are files checked? By name or by some kind of signature? http://p2pnet.net/story/12371  P2P Sites Partner For Online Broadcast Hattie Lee Chinese peer-to-peer (P2P) streaming media provider PPStream announced a partnership with download accelerator and peer-to-peer (P2P) file sharing software Xunlei (Thunder) to jointly broadcast the new movie "Ming Ming" on May 29. Users can watch the movie on PPStream for free or download the movie from Xunlei for two Yuan. Ming Ming is directed by Hong Kong director Susie Au. Beijing Poly-Bona Film Publishing Company Limited owns the exclusive online publishing rights to the movie. Xunlei told Pacific Epoch that it has received permission from Poly-Bona to offer the film. http://www.pacificepoch.com/newsstories/98010_0_5_0_M/  IFPI: Ten "Inconvenient Truths" About File-Swapping Nate Anderson The EU has just released its latest figures about counterfeit products seized at European borders in 2006, and the music industry's international trade group (IFPI) has jumped on those numbers to call for increased action against Chinese pirates. Of the 23 million counterfeit CDs and DVDs seized by police last year, 93 percent of them originated in China. The EU is worried enough about the numbers that it is contributing to a US-led WTO case against China over the matter. But does purchasing one of these discs mean that you could be supporting terrorism? According to the IFPI, it does. The group yesterday released a list of 10 "inconvenient truths" about music, and it makes for interesting reading. Here they are: 1. Pirate Bay, one of the flagships of the anti-copyright movement, makes thousands of euros from advertising on its site, while maintaining its anti-establishment "free music" rhetoric. 2. AllOfMP3.com, the well-known Russian web site, has not been licensed by a single IFPI member, has been disowned by right holder groups worldwide and is facing criminal proceedings in Russia. 3. Organized criminal gangs and even terrorist groups use the sale of counterfeit CDs to raise revenue and launder money. 4. Illegal file-sharers don’t care whether the copyright-infringing work they distribute is from a major or independent label. 5. Reduced revenues for record companies mean less money available to take a risk on "underground" artists and more inclination to invest in "bankers" like American Idol stars. 6. ISPs often advertise music as a benefit of signing up to their service, but facilitate the illegal swapping on copyright infringing music on a grand scale. 7. The anti-copyright movement does not create jobs, exports, tax revenues and economic growth–it largely consists of people pontificating on a commercial world about which they know little. 8. Piracy is not caused by poverty. Professor Zhang of Nanjing University found the Chinese citizens who bought pirate products were mainly middle- or higher-income earners. 9. Most people know it is wrong to file-share copyright infringing material but won't stop till the law makes them, according to a recent study by the Australian anti-piracy group MIPI. 10. P2P networks are not hotbeds for discovering new music. It is popular music that is illegally file-shared most frequently. It's a strange mix of the obvious and the bizarre. Point four, for instance, is probably true, and it won't come as a surprise to anyone who reads point eight that impoverished Chinese farmers are not the ones doing most of that country's illegal downloading. Point three is an odd one; certainly, somewhere in the world, someone with terrorist intentions has made a few bucks from the sale of counterfeit discs. But every other point on the list concerns digital file-swapping, not the purchasing of counterfeit CDs on Parisian street corners. It looks like a subtle attempt to elide the distinctions between the two. Point five is an attempt to turn the "innovation" argument on its head. For years, pundits outside the music industry have accused labels of pandering to teens through boy bands and "manufactured" celebrities instead of being concerned with finding, producing, and releasing art. The IFPI suggests that the labels could (and would) be doing exactly that if file-swapping went away. And then there's point seven, which isn't an "inconvenient truth" at all but more of a rant against those who prefer giving copyright holders less than absolute control over reproduction rights. An "anti-copyright movement" does exist, but most of the critical voices in the debate recognize the value of copyright—and actually produce copyrighted works themselves (Lawrence Lessig, etc.). The second part of the accusation ("pontificating on a commercial world about which they know little") is hardly a statement of fact; it comes across as angry retort to those outside the music business who would dare to criticize its methods and goals. It's too bad that groups like the IFPI resort to such dubious statements to make their point. Unauthorized file-swapping of copyrighted works is already illegal in most countries; if people are continuing to engage in it, they are unlikely to be swayed by broadsides against "anti-copyright" crusaders or accusations of funding terrorists. When it comes to stopping commercial piracy, we applaud the IFPI for its work. When it comes to disparaging those who favor a softer copyright policy, Ars has an inconvenient truth of our own to share with the music industry: these are the sort of tactics that only entrench consumer opposition. http://arstechnica.com/news.ars/post...-swapping.html  Lazy Western pirates not even on list 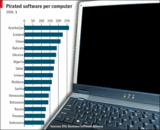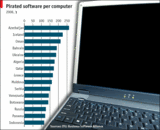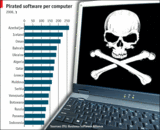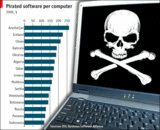 Free Loaders TECH firms constantly moan about software piracy and no wonder. Last year it accounted for 35% of the worldwide market and cost the industry $39.6 billion according to the Business Software Alliance, a trade body. America and China lead the world in terms of total losses from piracy at $7.2 billion and $5.4 billion respectively. But when calculated according to the number of computers in each country a different picture emerges. Cash-strapped countries dominate the leader board. In Azerbaijan, which comes out on top, computers are loaded with $262-worth of pirated software on average. But Iceland is the surprise second-placed nation: although software to the tune of $32m is pirated it is spread over only a few computers. http://www.economist.com/research/ar...ory_id=9248524  P2P Writer's Block Thomas Mennecke There was a time when it seemed there were dozens upon dozens of P2P networks floating about. Scour Exchange, iMesh, Napster, CuteMX, WinMX, FileShare, Gnutella, QtraxMax, eDonkey2000, FastTrack, EarthStation5, and the list goes on. Many of these networks have either died out or succumbed to the pressures of commercialization. Some are still alive, and surprisingly, still producing new versions of their software. P2P development, for the most part, has suffered from an incredible case of writer's block for the better part of two years. This isn't to say that P2P development has ceased - far from it. However, in terms of diversity, P2P creativity has been virtually non-existent. Instead, most development has concentrated around the de facto representative of file-sharing, BitTorrent. If a new client or version of an existing client crops up, chances are it has something to do with BitTorrent technology. While BitTorrent is an incredible technology, some are uneasy with this protocol replacing all need for other forms of file-sharing. In the last two years, there hasn't been a viable, widespread, or mainstream P2P network developed that comes close to the ubiquity of BitTorrent. Is this good news or bad? In many ways, BitTorrent's dominance as the premier file-sharing program is perhaps the very reason that file-sharing still exists. Its dual role as both the people's P2P protocol and a tool the music/movie industry can take advantage of has most likely helped maintain its longevity and fostered innovation. Others have not been so lucky. Take FastTrack, for example. If a diehard Kazaa fan of 2007 were to be transposed by some file-sharing/time-space vortex to the height of FastTrack's dominance in 2003-2004, the end-user experience would not be exceptionally different. Plagued by a barrage of legal difficulties, declining reputation, and a 100 million dollar judgment, Sharman Networks has been dormant in the P2P innovation field. Yet the client and network still exist and are being used by an untold number of people - a testament to the viability of decentralized P2P. The same can't be said about its brethren Grokster, who was made an example out of by the US entertainment industry. Moving onto Gnutella, this network once had a multitude of viable clients connecting to this community. The juggernauts of this venture were BearShare and Limewire. Gnucleus was also an important player, as were many other smaller developers. Yet the legal climate in the United States has had a chilling effect on Gnutella development for most programmers. Backed by the wealthy Lime Group umbrella, LimeWire has been the exception and has been able to stave off attacks by the RIAA (Recording Industry Association of America.) BearShare's future wasn't as fortunate as LimeWire's. Like many P2P applications, they too were forced to settle for an astronomical pricetag. With BearShare out of the picture, and the lack of a Gnucleus update since June of 2004, LimeWire is the only Gnutella application keeping this network afloat. A truly revolutionary change, however, is eagerly awaited. eDonkey2000 was once a dual client network - a much larger portion run by the open source project eMule, and the other run by the official eDonkey client developed by MetaMachine. eMule is still developing clients; however, the eDonkey2000 network, like FastTrack, has remained virtually unchanged save for the introduction of the Kademlia overlay several years ago. Regardless, eDonkey2000 remains an important force in the P2P world, and by some estimates is the protocol of choice in some countries. The Manolito P2P network, accessible via the Blubster and Piolet clients, was at one point surging to file-sharing stardom. Developer Pablo Soto's time was deferred from these projects however, and the population remained stagnant at ~250,000 individuals. Yet interestingly enough, not all is lost. Pablo's work may be considered the exception to the P2P writer's block rule, as he has been feverishly working on his latest project, OMEMO (Ownership Masquerading Explorable Metadata Overlay). If the beta testing proves successful, this virtual hard drive project may be the first innovative network in some time. Ares Galaxy, created by Alberto Treves, nearly achieved divine status after his decision to release the client's source code in September of 2005. This decision was made instead of capitulating to the RIAA's cease and desist demand. Although updates are still being produced, the Ares Galaxy of today is much like its predecessors. It is unknown whether Alberto will reinvigorate his client in the near future. The list of P2P clients that have remained virtually unchanged goes on. Is DC++ much different today than it was 5 years ago? Has KCeasy knocked anyone off their feet recently? Where are the great anonymous P2P networks? The only network where one can objectively notice substantial changes over the course of time is BitTorrent. From DHT (Distributed Hash Tables) to uTorrent to browser integration to advances in tracker technology, BitTorrent is a different animal than it was three years ago. Perhaps consolidation has led developers to simply give up on other proposed ideas or projects. Or perhaps because of this, it may stimulate creativity and innovation for the next great leap forward in P2P technology. http://www.slyck.com/story1475.html  Peer-to-Peer Networks Co-Opted for DOS Attacks Robert Lemos A flaw in the design of a popular peer-to-peer network software has given attackers the ability to create massive denial-of-service attacks that can easily overwhelm corporate websites, a security firm warned last week. Over the past three months, more than 40 companies have endured attacks emanating from hundreds of thousands of Internet Protocol addresses (IPs), with many of the attacks producing more than a gigabit of junk data every second, according to security solutions provider Prolexic Technologies. The sheer number of internet addresses has caused problems for routers and firewalls, burying solutions that rely on some form of blacklisting, said Paul Sop, chief technology officer for the firm. "It's like asking how fast can you bail your boat?" Sop said. "If you stop for a minute you get overwhelmed." Unlike past attacks, which use tens of thousands of compromised computers to deluge a web server (http://www.securityfocus.com/brief/195) or network with data, the latest attacks came from a collection of computers running peer-to-peer software known as DC++ (http://dcplusplus.sourceforge.net/). The software is based on Direct Connect, a protocol which allows the exchange of files between instant messaging clients. While the file-sharing network is distributed, the directories of where to find certain files resides in a few servers, known as hubs. Older versions of the hub server software have a flaw that allows an attacker to direct clients to get information from another server, said Fredrik Ullner, a developer for the DC++ project and an computer-science undergraduate at Sweden's Lund Institute of Technology (http://www.es.lth.se/). Maliciously redirecting those client results in a large number of computers continuously demanding data from the victim's web server, overwhelming it with requests. The attacks were used against DC++ own developers and hub directories as early as 2005. The first attacks targeted the project's directory of hubs, known as Hublist.org. Rogue DC++ users had created tools to flood a hub, and when Hublist.org removed the rogue users' servers, the group responded by attacking Hublist.org, Ullner said. The site is no longer accessible. The rogue group also hit DCPP.net, the project's main site, forcing the developers to move to SourceForge. "These attacks are, unfortunately, getting more common," Ullner stated in an email interview with SecurityFocus. The technique proved so effective that attackers have turned it on other companies. In March, companies started seeking out Prolexic to help them stave off some devastating denial-of-service attacks. In many of the attacks, more than 150,000 computers would open a handful of connections each, burying the Web server in a avalanche of network data. The largest attacks seen by the company involved more than 300,000 computers, said Prolexic's Sop. "We had millions and millions of connections in. We could identify the attacks with zero difficulty but new IPs were hitting us faster than we could block them." While many of the attacks were part of an extortion attempt - a common way in the past to turn denial-of-service capabilities into cash - about three quarters of the attacks were motivated by industrial espionage, Sop said. "The amount of money involved is pretty large," Sop said. "If you have a good internet business in Europe, and you can knock out your competitor, why spend money on marketing?" The firm announced on Wednesday that it had developed a way to defend against the attacks. A general solution is unlikely to appear from the DC++ project. While the problem has already been fixed in the DC++ hub software, it's hard to force everyone to adopt the fix, said developer Ullner. "The attackers take advantage of people's reluctance to upgrade." Moreover, even if all the hub administrators upgraded their systems, the attackers could run their own hubs until they commanded enough DC++ clients to attack a target. "It's difficult to impossible to restrict this," said Ullner. http://www.securityfocus.com/news/11466  Six State File-Sharing Cases Tossed Amy Dalrymple Lawsuits against six North Dakota college students accused of illegally sharing music online have been dismissed. But that doesn’t necessarily mean all the students are off the hook. The Recording Industry Association of America filed a civil complaint in April against six students within the North Dakota University System, accusing each of copyright infringement. The RIAA identified the students as John Doe and subpoenaed university officials for the students’ names. U.S. District Judge Rodney Webb granted the RIAA’s request on Tuesday to dismiss the cases without prejudice. Jonathan Lamy, a senior vice president for communications for the RIAA, said he could not comment on the North Dakota cases. Generally, a case is dismissed after the university responds to a subpoena and provides the student’s name, or the case is settled, Lamy said. Once receiving each student’s name and address, the RIAA sent each a letter offering another settlement opportunity, Lamy said. If a settlement offer is rejected, the RIAA will file a new lawsuit against the student by name, Lamy said. Rick Johnson, general counsel for North Dakota State University, said he heard at least some of the students settled, but he didn’t know about all of them. Three students are from NDSU. North Dakota State College of Science, Mayville State University and Valley City State University each have one student involved. NDSU, which provides computer administration services to five other campuses, acted as a facilitator by responding to the subpoena, Johnson said. Beyond that, NDSU is not involved with the lawsuit and hadn’t been informed about the request for dismissal, Johnson said. William Harrie, a Fargo attorney representing the RIAA, said he’s not allowed to comment on the case. In February, the RIAA sent about 20 letters to North Dakota college students offering them a chance to avoid a lawsuit and settle. Nationally, the settlements averaged about $4,000. The students who didn’t settle at that point were targeted with the John Doe lawsuits. Lamy would not comment on the size of settlement the North Dakota students could pay, but he said settlement rates typically go up as the process moves forward. The lawsuits are part of a crackdown by the RIAA against music piracy on campus, affecting hundreds of college students across the country. http://www.in-forum.com/News/articles/167081  Illinois Raids Welfare to Pay for Failed Video Game Violence Legislation Ken Fisher When the State of Illinois was tardy in paying its legal bills after attempting to defend a law that regulated the sale of violent and sexually explicit video games, the Entertainment Software Association wondered about the reasons for the delay. Now they know: the state was scouring department budgets, looking for the $1 million it cost to defend the unconstitutional legislation in court. Yes, you read that right—the State of Illinois spent one meeeellion dollars of taxpayer money on the litigation even as the state budget was starved for cash in other, more pressing areas. And worse yet, they spent it on a bill which, when introduced, was plainly unconstitutional. The grand total was reported this week in a Quad Cities Online article which revealed that "the governor raided funds throughout state government to pay for the litigation. Some of the areas money was taken from included the public health department, the state's welfare agency and even the economic development department." A state representative who attended recent hearings on the issue said that Gov. Blagojevich's staff simply spread the legal bills around by sticking them to agencies which had funds left in their budgets—even if the agencies had nothing to do with the issue or the litigation. The Illinois law in question was struck down by both a federal court and an appeals court. In the final decision on the case, the justices noted that the law used a set of simplistic criteria to evaluate video games. They even used God of War as an example of the law's failings. "Because the (Illinois law) potentially criminalizes the sale of any game that features exposed breasts, without concern for the game considered in its entirety or for the game’s social value for minors, distribution of God of War is potentially illegal, in spite of the fact that the game tracks the Homeric epics in content and theme," the judges wrote. Spending this sort of money on important causes is one thing; spending it on video game regulation approaches that have been repeatedly ruled unconstitutional in other states is quite another. The situation might be more understandable were it not for the fact that Illinois could have easily seen this coming, either by paying attention to what other states are encountering or by opening a dialogue with the likes of the ESA. Instead of taking that cautious approach, the Governor decided to press on, and now the taxpayers will bear that burden. The fact that some of the money was pulled from public health and welfare only makes the situation worse. http://arstechnica.com/news.ars/post...gislation.html  Wayne Crookes Reportedly Sues Me Over My Blogroll Michael Geist There are several reports that Wayne Crookes, who previously launched suits against a wide range of parties including Wikipedia, Yahoo, and a domain name registrar, has sued me in B.C. courts for defamation. I have not been served with the suit, but the reports indicate that I am being sued for an allegedly defamatory third party comment on my site that I took down and for writing about, and linking to, P2PNet.net, which in turn linked to another site that allegedly contained a defamatory posting. In other words, I'm reportedly being sued for maintaining a blogroll that links to a site that links to a site that contains some allegedly defamatory third party comments. http://www.michaelgeist.ca/content/view/1987/125/  Parking Tunes Online Illegal: Japanese Court Translated by Google Music retention service: As for storage utilization infringement of copyright Tokyo district court The conceptual drawing of the music service which utilizes the portable telephone The data is retained making use of “storage”, the user retains the music data of its own CD and the like on Internet, with anytime downloads in the portable telephone and whether or not offer of the service which can be heard undertakes infringement of copyright with decision of the lawsuit which is disputed, Tokyo district court (the high section Makiko President of the Court) judgment was shown that on the 25th, it undertakes infringement of copyright. As for service of problem, information communication company “image city” (the Tokyo Taito Ku) it began from November of 05, “MYUTA”. The user from the personal computer retains the music data in the server of the same company, can download to the portable telephone only main person of the user. Vis-a-vis this service, the Japanese music copyright association (JASRAC) it points out that it is infringement of copyright. The same company after discontinuing service, seeking the verification of the thing which does not undertake infringement of copyright in the partner had sued the same association. With lawsuit as for the same company “as for substantially doing data duplication and transmission user itself. Transmission to many and unspecified persons had not done, insisted copyright that it does not infringe”, but “the server who is center of the system the same company having owned and managing decision, for the same company as for the user the unspecific person. Duplication and the public (many and unspecified persons) to behavior subject of transmission is the same company”, that it judges. If permission of association is not received, when copyright is infringed, it recognized. http://translate.google.com/translat...language_tools  Research Shows Illegal File-Sharing Directly Hits Music Sales A third of Italian illegal file-sharers have cutback on their purchase of physical music products. Three-quarters of all Italians who download music have used copyright infringing peer-to-peer networks. eMule is most used illegal file-sharing network in Italy. Italy’s Luigi Einaudi Foundation (1) has published new research about the illegal file-sharing of digital content that shows how the habit reduces consumers’ purchasing of physical music products (2). The research shows that nearly a third of illegal file-sharers (30%) have cutback on the amount of physical music products, such as CDs and DVDs, they buy. Only six per cent of those surveyed said that illegal file-sharing increased their propensity to buy CDs, while 64 per cent of respondents said their habit did not change their music buying habits. A massive 77 per cent of all those who said they download music have used illegal peer-to-peer (P2P) networks to obtain music, while only 23 per cent have used a legal online service. The research showed that 31 per cent of those questioned had downloaded music or video from the internet in the last month. Nine-in-ten of the tracks downloaded were singles (91%), predominantly current chart hits. The most popular device for playing this material was a music player (84%), followed by hi-fis and MP3 players (39%). The ability to obtain music for free was the main attraction for people who illegally file-shared music, followed by the ease of searching and availability of catalogue. eMule is P2P software most used in Italy by illegal file-sharers (51%), followed by WinMX (25%) and Kazaa (13%). Only 2.7 per cent of illegal file-sharers said they use BitTorrent. Three-in-five of those interviewed (61%) said the bought less than one CD a month and more than 30 per cent of this group buy no physical copies of recorded music at all. 1) http://www.fondazione-einaudi.it/Pagine/Default.asp 2) The full study is available from this link: http://www.libercom.it/ Researchers interviewed wide cross-section of Italians, with 50 per cent of respondents aged between 15 and 34 years old, 25 per cent between 35 and 44 years old and 25 per cent between 44 and 54 years old. Nearly a third of those interviewed were office workers (29%), a quarter were students (25%) and the remainder were blue collar workers, managers, sole traders and retired people. Most of those interviewed use internet at home (84%) and 77 per cent of respondents had used the internet for at least two years. Despite this, 68 per cent of the internet users questioned said they had only a basic ability in the “technology world”. http://www.assodigitale.it/news_sito...0070 5248651/  Plunge in CD Sales Shakes Up Big Labels Jeff Leeds “Sgt. Pepper’s Lonely Hearts Club Band,” the Beatles album often cited as the greatest pop recording in music history, received a thoroughly modern 40th-anniversary salute last week when singers on “American Idol” belted out their own versions of its songs live on the show’s season finale. But off stage, in a sign of the recording industry’s declining fortunes, shareholders of EMI, the music conglomerate that markets “Sgt. Pepper” and a vast trove of other recordings, were weighing a plan to sell the company as its financial performance was weakening. It’s a maddening juxtaposition for more than one top record-label executive. Music may still be a big force in pop culture — from “Idol” to the iPod — but the music business’s own comeback attempt is falling flat. Even pop’s pioneers are rethinking their approach. As it happens, one of the performers on “Sgt. Pepper,” Paul McCartney, is releasing a new album on June 5. But Mr. McCartney is not betting on the traditional record-label methods: He elected to sidestep EMI, his longtime home, and release the album through a new arrangement with Starbucks. It’s too soon to tell if Starbucks’ new label (a partnership with the established Concord label) will have much success in marketing CDs. But not many other players are. Despite costly efforts to build buzz around new talent and thwart piracy, CD sales have plunged more than 20 percent this year, far outweighing any gains made by digital sales at iTunes and similar services. Aram Sinnreich, a media industry consultant at Radar Research in Los Angeles, said the CD format, introduced in the United States 24 years ago, is in its death throes. “Everyone in the industry thinks of this Christmas as the last big holiday season for CD sales,” Mr. Sinnreich said, “and then everything goes kaput.” It’s been four years since the last big shuffle in ownership of the major record labels. But now, with the sales plunge dimming hopes for a recovery any time soon, there is a new game of corporate musical chairs afoot that could shake up the industry hierarchy. Under the deal that awaits shareholder approval, London-based EMI agreed last week to be purchased for more than $4.7 billion by a private equity investor, Terra Firma Capital Partners, whose diverse holdings include a European waste-conversion business. Rival bids could yet surface — though the higher the ultimate price, the more pressure the owners will face to make dramatic cuts or sell the company in pieces in order to recoup their investment. For the companies that choose to plow ahead, the question is how to weather the worsening storm. One answer: diversify into businesses that do not rely directly on CD sales or downloads. The biggest one is music publishing, which represents songwriters (who may or may not also be performers) and earns money when their songs are used in TV commercials, video games or other media. Universal Music Group, already the biggest label, became the world’s biggest music publisher on Friday after closing its purchase of BMG Music, publisher of songs by artists like Keane, for more than $2 billion. Now both Universal and Warner Music Group are said to be kicking the tires of Sanctuary, an independent British music and artist management company whose roster includes Iron Maiden and Elton John. The owners of all four of the major record companies also recently have chewed over deals to diversify into merchandise sales, concert tickets, advertising and other fields that are not part of their traditional business. Even as the industry tries to branch out, though, there is no promise of an answer to a potentially more profound predicament: a creative drought and a corresponding lack of artists who ignite consumers’ interest in buying music. Sales of rap, which had provided the industry with a lifeboat in recent years, fell far more than the overall market last year with a drop of almost 21 percent, according to Nielsen SoundScan. (And the marquee star 50 Cent just delayed his forthcoming album, “Curtis.”) In other genres the picture is not much brighter. Fans do still turn out (at least initially) for artists that have managed to build loyal followings. The biggest debut of the year came just last week from the rock band Linkin Park, whose third studio album, “Minutes to Midnight,” sold an estimated 623,000 copies, according to Nielsen SoundScan data. But very few albums have gained traction. And that is compounded by the industry’s core structural problem: Its main product is widely available free. More than half of all music acquired by fans last year came from unpaid sources including Internet file sharing and CD burning, according to the market research company NPD Group. The “social” ripping and burning of CDs among friends — which takes place offline and almost entirely out of reach of industry policing efforts — accounted for 37 percent of all music consumption, more than file-sharing, NPD said. The industry had long pinned its hopes on making up some of the business lost to piracy with licensed digital sales. But those prospects have dimmed as the rapid CD decline has overshadowed the rise in sales at services like Apple’s iTunes. Even as music executives fret that iTunes has not generated enough sales, though, they gripe that it unfairly dominates the sale of digital music. Partly out of frustration with Apple, some of the music companies have been slowly retreating from their longtime insistence on selling music online with digital locks that prevent unlimited copying. Their aim is to sell more music that can be played on Apple’s wildly popular iPod device, which is not compatible with the protection software used by most other digital music services. EMI led the reversal, striking a deal with Apple to offer its music catalog in the unrestricted MP3 format. Some music executives say that dropping copy-restriction software, also known as digital-rights management, would stoke business at iTunes’ competitors and generate a surge in sales. Others predict it would have little impact, though they add that the labels squandered years on failed attempts to restrict digital music instead of converting more fans into paying consumers. “They were so slow to react, and let things get totally out of hand,” said Russ Crupnick, a senior entertainment industry analyst at NPD, the research company. “They just missed the boat.” Perhaps there is little to lose, then, in experimentation. Mr. McCartney, for example, may not have made it to the “American Idol” finale, but he too is employing thoroughly modern techniques to reach his audience. Starbucks will be selling his album “Memory Almost Full” through regular music retail shops but will also be playing it repeatedly in thousands of its coffee shops in more than two dozen countries on the day of release. And the first music video from the new album had it premiere on YouTube. Mr. McCartney, in announcing his deal with Starbucks, described his rationale simply: “It’s a new world.” http://www.nytimes.com/2007/05/28/ar...ic/28musi.html  Record Companies Win £41m Damages Online retailer CD-Wow must pay £41m to British record companies after breaking a deal to stop selling illegally imported cheap albums in the UK. The High Court in London ruled in March that the site's owners, Music Trading Online, were "in substantial breach" of a 2004 agreement to stop importing CDs. It has now ordered Hong Kong-based CD-Wow to pay £37m plus interest to the British Phonographic Industry (BPI). CD-Wow says it will still sell cheap CDs and may appeal against the ruling. "Other bigger sites doing the same thing have been left alone." "CD-Wow is no consumer champion," countered the BPI's chief executive, Geoff Taylor, who said the company had undermined "the legitimate businesses of UK retailers and record companies". "The vibrancy of British music depends on a fair return on the investments that allow British talent to shine. "This decision is an important step in ensuring that British music has a bright future." The Entertainment Retailers' Association (Era), which represents companies like HMV, Fopp and Amazon, also welcomed the ruling. "It is vital that all retailers compete on a level playing field," said director general Kim Bayley. "Illegal imports threaten that level playing field and threaten British jobs." Frozen assets With retail sales of £21.7m in the UK in 2005, CD-Wow was the third largest online music retailer in the UK after Amazon and Play. The company denied deliberately breaking its 2004 court undertaking to stop buying CDs in places like Hong Kong and passing them on to consumers in the UK at discounted prices. It put any breach of copyright down to human error, but the High Court rejected its argument. The BPI, which represents the major record labels in the UK, said the ruling was a "significant legal victory" for the music industry. It said it had already obtained a freezing order against CD-Wow, meaning that all of its assets and bank accounts are frozen. 'Brute force' "The courts have lost patience," said BPI lawyer Roz Groome, who added the body would use the ruling to pursue other retailers which exploit parallel imports. In a statement, CD-Wow said the British courts had set a "dangerous precedent". "I fear what is happening is an attempt to use the combined brute force of the record industry to force the retailers and, in turn, our clients, to keep lining the pockets of the fat cat executives," said Mr Wesslen. "It shouldn't matter whether we are buying from an official distributor in the UK, Europe or the Far East, what is important is that we are buying legitimate products from the record companies themselves." The retailer is now calling for a full review of copyright law. http://news.bbc.co.uk/go/pr/fr/-/2/h...nt/6700639.stm  Studies: Music Industry Overstating Threat of P2P Piracy Nate Anderson Unauthorized sharing of digital music remains a huge issue for the global music business, but is most of that sharing taking place on peer-to-peer networks? For years, peer-to-peer was the bogeyman, the red Communist music monster than was going to devour the industry's revenues. But new research suggests that sneakernets may be as big a problem as darknets. A recent study from the NPD Group found that legal music downloads surged in 2006, and the company predicts that legal services will have more users than peer-to-peer networks by the end of 2007. But that doesn't mean the music industry isn't threatened. "Unfortunately for the music labels," said Russ Crupnick, vice president and entertainment industry analyst for the NPD Group, "the volume of music files purchased legally is swamped by the sheer volume of files being traded illegally, whether on P2P or burned CDs sourced from borrowed files." Note the reference to "burned CDs." The EFF points out that NPD thinks this sort of old-fashioned sharing is actually a massive threat. According to NPD, "The 'social' ripping and burning of CDs among friends—which takes place offline and almost entirely out of reach of industry policing effort—accounted for 37 percent of all music consumption, more than file-sharing." If true, that's a huge number. So why aren't we hearing more about CD swapping from the RIAA? For one thing, lending a CD to a friend is not illegal, and it's all but impossible to keep people from ripping borrowed CDs. Hence, the RIAA's focus has largely been on peer-to-peer sharing instead, with the music industry going so far as to pressure colleges to cut off all peer-to-peer access. This level of attention to peer-to-peer networks makes less sense if CD swapping and ripping is actually a bigger issue. Regular readers might remember our coverage of Media Rights Technologies, which threatened Apple, Microsoft, Adobe, and Real in early May, claiming that the companies were not using enough DRM. MRT claims that, based on internal studies, streamripping (saving the bitsream from Internet radio or other streaming services) is actually the number one source of infringing copies. I spoke with MRT CEO Hank Risan last week, and he confirmed the claim, saying that streamripping was also one of the reasons behind the recent decision to raise rates on Internet webcasters. (The company has said that it would file lawsuits against Apple, Microsoft, Adobe, and Real within 10 days if they did not license MRT technology; 20 days later, there has been no announcement). If streamripping truly is a bigger threat than CD-swapping and P2P use, it must account for at least 38 percent of all music consumption, leaving only a maximum of 25 percent for both legal and P2P acquisition of music. If true, it seems downright amazing that the music industry has spent so much time focused on peer-to-peer file-sharing. Or perhaps it's not all that amazing. A more likely explanation is that the numbers aren't even right. As Canadian law professor Michael Geist showed a few weeks ago, claims about piracy rates can be wildly variable and downright fictional. High numbers are often used to support legal threats or calls for Congressional action, as in the MRT case. MRT has a lot to gain by overstating the threat of streamripping and, so far, has not showed its numbers. Both MRT and NPD agree, though, that P2P is hardly the music industry's biggest problem. http://arstechnica.com/news.ars/post...2p-piracy.html  Contact Information For 50 Politicians Who Take Campaign Money From The RIAA When you voted the RIAA the worst company in America you gave us an assignment. But how can we improve the customer service of a recording industry trade group? It's not an easy task. Couldn't you have voted for Home Depot? U-Haul? Anyway... One of the ways the RIAA operates is by donating money to politicians who then enact favorable legislation on their behalf. Don't let the optimist in you believe that this doesn't work. It does. But wait, aren't these representatives supposed to work for you? Sure. That's why we've compiled a list of 50 congresspeople who took campaign contributions from the RIAA in the last election cycle. We've linked their contact information so that you, as their constituents, can inform them that they're taking money from the "Worst Company in America," and that's going to cost them your vote. If your congressperson isn't on the list, try writing Barack Obama or Hillary Clinton, both of whom are running for President and have national interest. Don't be afraid to tell your representatives how you feel. How else are they going to know? Good luck. Congressperson Receiving Contributions From The RIAA Amount Contact Information (Hotlinks at parent – Jack.) Dist 19-FL WEXLER, ROBERT DEM $9,000 Click Here Dist 21-TX SMITH, LAMAR REP $7,500 Click Here Senate-UT HATCH, ORRIN G REP $6,000 Click Here Senate-PA SPECTER, ARLEN REP $5,000 Click Here Senate-AK STEVENS, THEODORE F REP $5,000 Click Here Senate-NE NELSON, E BENJAMIN DEM $5,000 Click Here Senate-CA FEINSTEIN, DIANNE DEM $4,000 Click Here Dist 45-CA BONO, MARY REP $4,000 Click Here Senate-FL NELSON, BILL DEM $4,500 Click Here Dist 08-FL KELLER, RICHARD A REP $4,054 Click Here Dist 07-NJ FERGUSON, MIKE REP $4,000 Click Here Dist 28-CA BERMAN, HOWARD L DEM $3,500 Click Here Dist 29-CA SCHIFF, ADAM DEM $3,000 Click Here Dist 30-CA WAXMAN, HENRY A. DEM $3,000 Click Here Dist 07-MO BLUNT, ROY REP $3,100 Click Here Dist 06-TN GORDON, BARTON JENNINGS DEM $3,000 Click Here Dist 06-VA GOODLATTE, ROBERT W. REP $3,500 Click Here Senate-IL OBAMA, BARACK DEM $2,000 Click Here Dist 14-IL HASTERT, DENNIS J. REP $2,000 Click Here Dist 07-MA MARKEY, EDWARD J MR. DEM $2,000 Click Here Dist 05-MD HOYER, STENY HAMILTON DEM $2,000 Click Here Dist 14-MI CONYERS, JOHN JR. DEM $2,000 Click Here Dist 03-MS PICKERING, CHARLES W REP $2,000 Click Here Senate-NY CLINTON, HILLARY RODHAM DEM $2,000 Click Here Senate-TN CORKER, ROBERT P JR REP $2,000 Click Here Dist 07-TN BLACKBURN, MARSHA REP $2,000 Click Here Dist 06-TX BARTON, JOE LINUS REP $2,000 Click Here Senate-AL SHELBY, RICHARD C REP $1,000 senator@shelby.senate.gov Click Here Senate- AR PRYOR, MARK LUNSFORD DEM $1,000 Click Here Dist 10- CA TAUSCHER, ELLEN O DEM $1,000 Click Here Dist 22- CA MCCARTHY, KEVIN REP $1,000 Click Here Dist 49-CA ISSA, DARRELL EDWARD REP $1,000 Click Here Dist 14-FL MACK, CONNIE REP $1,500 Click Here Dist 05-IL EMANUEL, RAHM DEM $1,000 Click Here Senate-LA VITTER, DAVID REP $1,000 Click Here Dist 06-MI UPTON, FREDERICK STEPHEN REP $1,000 Click Here Senate-MS LOTT, TRENT REP $1,000 Click Here Dist 06-NC COBLE, JOHN HOWARD REP $1,000 howard.coble@mail.house.gov Click Here Dist 09-NC MYRICK, SUE REP $1,000 Click Here Dist 02-NE TERRY, LEE REP $1,811 Click Here Dist 07-NY CROWLEY, JOSEPH DEM $1,000 write2joecrowley@mail.house.gov Click Here Dist 10-NY TOWNS, EDOLPHUS DEM $1,500 Click Here Dist 28-NY SLAUGHTER, LOUISE M DEM $1,000 Click Here Dist 05-OH GILLMOR, PAUL E REP $1,000 Click Here Dist 01-OK SULLIVAN, JOHN REP $1,000 Click Here Dist 02-OR WALDEN, GREGORY PAUL REP $1,000 Click Here Dist 01-WA INSLEE, JAY R DEM $1,000 Click Here Senate-SD THUNE, JOHN REP $1,000 Click Here Dist 05-TN COOPER, JAMES H. S. DEM $1,500 Click Here http://consumerist.com/consumer/wors...iaa-264638.php  Through Rose-Colored Granny Glasses Holland Cotter  Tear gas, pot and patchouli were the scents of the 1960s. You can almost detect the last two, spicy and pungent, wafting through “Summer of Love: Art of the Psychedelic Era” at the Whitney Museum of American Art. But tear gas, with its weird-sweet burn, is missing in a show that remembers a lot, but forgets much more, about what was happening 40 years ago, when America was losing its mind to save, some would say, its soul. The so-called Summer of Love was a local event with national repercussions. Word spread that a “Human Be-In” would convene at Golden Gate Park in San Francisco in January 1967. Young people from across the country poured into the city, and by the summer they had filled the hippie neighborhood of Haight-Ashbury and were crashing in parks and streets. The party went off as planned, and you can revisit it at the Whitney in Jerry Abrams’s “Be-In, 1967,” a funny, hopped-up film with a jamming soundtrack by Blue Cheer. The news media were all over the photogenic counterculture, with its jangly music, exotic drugs and outlandish mores. This was the Flower Power instant, and it was over in a flash. But for many people it is what the ’60s were all about. The Whitney show, which is great fun and half-baked history, will not persuade them otherwise. The decade was the furthest thing from laid back. It was wired, confused and confusing, with constant clashes around race, class, gender and politics, idealism and ideology. That’s why, for anyone who wasn’t around then, the period is all but impossible to know. And for anyone who was around, it’s hard to describe without sounding either nostalgic or bitter. Music still gives the best sense of it all. Say you were a middle-class American white kid in 1964. What were you listening to? Jan and Dean, the Shangri-Las. Surfers and bikers. Then you and some friends see the Beatles on their first American tour. They’re so new: four skinny, pale, dandyish guys with femme haircuts singing “Love me do.” The girls in the audience scream. The boys cheer. Ringo shakes his mop and the boys scream too. Hysteria. It’s a high. Four years later the Beatles are in India, and you’re in college, at a concert, smoking grass and this truly unusual woman named Janis is swinging her hair across the stage. She’s commanding you to take a little piece of her heart. She’s white but sounds black, and she’s reckless, eyes closed, right at the edge of the stage. She’ll fall! Does she care? Outside there’s a war, and the world feels weird, but not in here, tonight. Then you’re tripping, and Jimi Hendrix is up there on some other stage with this tremendous light show cued to the pulse of the cosmos exploding behind him. No flowers now. No mellow. He strangles the national anthem, then ignites his guitar. Someone behind or beside you whispers: Detroit is on fire. A Buddhist monk torched himself in Saigon. People are making draft-card bonfires. Flames are spilling out of the music, spreading off the stage and into life. You don’t know where acid stops and reality starts. The Whitney show has a fair amount of music, most of it emanating from recreated light shows. One flashes out at you when you step off the third-floor elevator, a projection of seething, bubbling color, like primordial ooze on the boil or a brain being fried. The original design was by the Joshua Light Show, one of many light teams hired by concert halls or clubs, even by individual bands; Jefferson Airplane had a team of its own. Light shows were an intriguing medium, organic but programmed, like Abstract Expressionism done by machine. They had a passive-aggressive energy of so much 1960s art and music. Like the wrong drug at the wrong time, they could make you crazy. But basically they were for pleasure, for entertainment. Timothy Leary, among others, pontificated about how we should change the world by changing our heads. But as drugs became widely available, the activist dimension of getting high faded. Tripping was something you did on Saturday night. Most of the art in the show — mass-produced posters, broadsides, book covers, magazine graphics, record album jackets — also comes under the entertainment category. It wasn’t made to be framed and revered. It was stuff people bought cheap, and lived with for a while, and that museums rarely show. It makes sense that the predominating ’60s pop aesthetic was distilled from art and artists distained by High Modernism: decorative styles like Jugendstil and Art Nouveau; decadent artists like Aubrey Beardsley and Alphonse Mucha; riffs from Victorian fairy-tale illustration or Saturday morning TV. Kitsch, in other words, but hallucinated kitsch. The result was a crisp but sensuous look, intricate and curvy, easy to see but hard to read and adaptable to any context or use, from the covers of potboiler novels (“Sin Street Hippie”) to architecture (the visionary drawings of the Archigram collective) to home design (Verner Panton’s rainbow-colored sit-in foam-rubber environment of undulating curves). “Summer of Love” is stuck on the style, or rather stuck on the effort to make one style the whole ’60s story. It pushes hard, covering wall after Whitney wall with posters for concerts at rock emporiums like the Fillmore West and East, or British clubs like UFO and the Fifth Dimension. (The show has a substantial British section; it was organized by Christoph Grunenberg, director of the exhibition’s originating museum, the Tate Liverpool.) But the net effect is less to reveal a depth and variety of creativity than to demonstrate that the main function of alternative art was advertising, that the counterculture started as a commercial venture, which soon became a new mainstream and ended up an Austin Powers joke. Possibly this view represents the show’s critical edge, but if so, it is sharpened at the expense of accuracy. To many people who came of age between 1963 to 1972 political intensity was the defining feature of the period and its most interesting art. It never let up. In 1965 antiwar protests started — 25,000 students marched on Washington that year — and they grew larger and more frequent. By 1967, more than 400,000 troops have been sent to Vietnam. Che Guevara was killed that year; the Black Panthers had formed the year before. In 1968 the Rev. Dr. Martin Luther King Jr. and Robert F. Kennedy were assassinated. Racial uprisings spread across the country. The Democratic convention brought the war home to the Chicago streets. In 1969: university takeovers, Altamont. In 1970: Jimi dead. Janis dead. Cambodia. Kent State. You will learn almost nothing about any of this from the show. Or about the gay liberation movement. Or about the gathering women’s movement, although militant feminism makes total sense given the relentless sexism of psychedelic art, in which all women are young, nude, available “chicks,” and very rarely artists. Nor would you have any inkling that, for Americans at least, pop culture during these years meant black culture. Apart from Hendrix’s presence, the show is overwhelmingly white. Aretha Franklin’s first big hits — “Respect,” “Chain of Fools” and “Natural Woman” — were all 1967. You won’t find her here. Nor will you find Marvin, or Smokey, or Otis, or Fontella or Ray. Again, take one style for the whole picture, you leave most of the picture out. Hints of what’s missing come through in a handful of works, most of them added by Henriette Huldisch, an assistant curator at the Whitney in charge of the New York installation. They include one of Robert Rauschenberg’s news-collages that compresses images of racism, war and the conquest of space into an everything-is-connected time capsule. Ronald L. Haeberle’s much-reproduced print of the My Lai massacre is here, with its two-phrase overlay of text: “Q: And babies? A: And babies.” The outstanding addition, though, is from the Whitney’s permanent collection, a blistering 1967 painting by Peter Saul. Titled “Saigon,” it’s a flame-red, half-abstract, bad-trip vision of mass sexual violation. So, we discover in 40-year retrospect, love was never all you needed; in the 1960s, in fact, it was barely there. “Summer of Love” doesn’t feel like a particularly loving show, and the ’60s, as seen through its lens, isn’t a loving time, unless by love you mean sex, which was plentiful, as it tends to be in youth movements. But altruism, selflessness? Young people are by definition narcissistic, all clammy ego. They want what they want. There is no past that matters; the future isn’t yet real. Some might say — I would say — that American culture in general is like this, though not all of it. And if the kids in “Summer of Love” are stoned on self-adoration, there were also an extraordinary number of young people during the Vietnam era who engaged in sustained acts of social generosity. And they made art. I mention this in light of the Flower Power revivalism of the past few years, in contemporary art and elsewhere. Psychedelia and collectivity are back (and already on their way out again). But the revival is highly edited; a surface scraping; artificial, like a bottled fragrance. No one these days is thinking, “Turn on, drop out.” Everyone is thinking, “How can I get into the game?” The Whitney show, maybe without intending to, suggests that this was always true, and makes such an attitude seem inevitable and comprehensible. So, let’s have another ’60s show, an incomprehensible one, messier, stylistically hybrid, filled with different countercultures, and with many kinds of music and art, a show that makes the “Summer of Love” what it really was: a brief interlude in a decade-long winter of creative discontent. “Summer of Love: Art of the Psychedelic Era” remains at the Whitney Museum of American Art, 945 Madison Avenue at 75th Street, through Sept. 16. http://www.nytimes.com/2007/05/25/ar...gn/25love.html  Design That Solves Problems for the World’s Poor Donald G. McNeil Jr. “A billion customers in the world,” Dr. Paul Polak told a crowd of inventors recently, “are waiting for a $2 pair of eyeglasses, a $10 solar lantern and a $100 house.” The world’s cleverest designers, said Dr. Polak, a former psychiatrist who now runs an organization helping poor farmers become entrepreneurs, cater to the globe’s richest 10 percent, creating items like wine labels, couture and Maseratis. “We need a revolution to reverse that silly ratio,” he said. To that end, the Cooper-Hewitt National Design Museum, which is housed in Andrew Carnegie’s 64-room mansion on Fifth Avenue and offers a $250 red chrome piggy bank in its gift shop, is honoring inventors dedicated to “the other 90 percent,” particularly the billions of people living on less than $2 a day. Their creations, on display in the museum garden until Sept. 23, have a sort of forehead-thumping “Why didn’t someone think of that before?” quality. For example, one of the simplest and yet most elegant designs tackles a job that millions of women and girls spend many hours doing each year — fetching water. Balancing heavy jerry cans on the head may lead to elegant posture, but it is backbreaking work and sometimes causes crippling injuries. The Q-Drum, a circular jerry can, holds 20 gallons, and it rolls smoothly enough for a child to tow it on a rope. Interestingly, most of the designers who spoke at the opening of the exhibition spurned the idea of charity. “The No. 1 need that poor people have is a way to make more cash,” said Martin Fisher, an engineer who founded KickStart, an organization that says it has helped 230,000 people escape poverty. It sells human-powered pumps costing $35 to $95. Pumping water can help a farmer grow grain in the dry season, when it fetches triple the normal price. Dr. Fisher described customers who had skipped meals for weeks to buy a pump and then earned $1,000 the next year selling vegetables. “Most of the world’s poor are subsistence farmers, so they need a business model that lets them make money in three to six months, which is one growing season,” he said. KickStart accepts grants to support its advertising and find networks of sellers supplied with spare parts, for example. His prospective customers, Dr. Fisher explained, “don’t do market research.” “Many of them have never left their villages,” he said http://www.nytimes.com/2007/05/29/sc...826&ei=5087%0A  The Known World Steven Pinker THE CANON A Whirligig Tour of the Beautiful Basics of Science. By Natalie Angier. 293 pp. Houghton Mifflin Company. $27. A baby sucks on a pencil and her panicky mother fears the child will get lead poisoning. A politician argues that hydrogen can replace fossil fuels as our nation’s energy source. A consumer tells a reporter that she refuses to eat tomatoes that have genes in them. And a newsmagazine condemns the prospects of cloning because it could mass-produce an army of zombies. These are just a few examples of scientific illiteracy — inane misconceptions that could have been avoided with a smidgen of freshman science. (For those afraid to ask: pencil “lead” is carbon; hydrogen fuel takes more energy to produce than it releases; all living things contain genes; a clone is just a twin.) Though we live in an era of stunning scientific understanding, all too often the average educated person will have none of it. People who would sneer at the vulgarian who has never read Virginia Woolf will insouciantly boast of their ignorance of basic physics. Most of our intellectual magazines discuss science only when it bears on their political concerns or when they can portray science as just another political arena. As the nation’s math departments and biotech labs fill up with foreign students, the brightest young Americans learn better ways to sue one another or to capitalize on currency fluctuations. And all this is on top of our nation’s endless supply of New Age nostrums, psychic hot lines, creationist textbook stickers and other flimflam. The costs of an ignorance of science are not just practical ones like misbegotten policies, forgone cures and a unilateral disarmament in national competitiveness. There is a moral cost as well. It is an astonishing fact about our species that we understand so much about the history of the universe, the forces that make it tick, the stuff it’s made of, the origin of living things and the machinery of life. A failure to nurture this knowledge shows a philistine indifference to the magnificent achievements humanity is capable of, like allowing a great work of art to molder in a warehouse. In “The Canon: A Whirligig Tour of the Beautiful Basics of Science,” Natalie Angier aims to do her part for scientific literacy. Though Angier is a regular contributor to the Science Times section of this newspaper, “The Canon” departs from the usual treatment of science by journalists, who typically cover the “news,” the finding that upsets the apple cart, rather than the consensus. Though one can understand why journalists tend to report the latest word from the front — editors’ demand for news rather than pedagogy, and the desire to show that science is a fractious human activity rather than priestly revelation — this approach doesn’t always serve a widespread understanding of science. The results of isolated experiments are more ephemeral than conclusions from literature reviews (which usually don’t fit into a press release), and the discovery-du-jour approach can whipsaw readers between contradictory claims and leave them thinking, “Whatever.” Angier’s goals are summed up in two words in her subtitle: beautiful basics. “The Canon” presents the fundamentals of science: numbers and probability, matter and energy, the origins and structure of living things, and the natural history of our planet, solar system, galaxy and universe. These are, she judges, the basics that every educated person should master, and a prerequisite to a genuine understanding of the material in any newspaper’s science coverage. And she presents these basics as beautiful: worthy of knowing for their own sake, even if they won’t help us save the planet, age successfully or compete with the Chinese. “The Canon” begins on an engaging note, lamenting what is one of my pet peeves as well — the idea that science is something for kids. When their children turn 13, Angier notes, many parents abandon their memberships in zoos and science museums for more “mature” institutions like theaters and art museums. And who can blame them, when visiting a modern science museum, in her priceless description, consists of a “mad pinball pinging from one hands-on science exhibit to the next, pounding on knobs to make artificial earthquakes, or cranking gears to see Newton’s laws in motion, or something like that; who bothers to read the explanatory placards anyway? And, oops, hmm, hey, Mom, this thing seems to have stopped working!” Many new science museums seem to be built on the dubious theory that a person’s life interests are formed in childhood — that “just as the twig is bent, the tree’s inclined.” Instead they may be conveying the message “When I was a child ... I thought as a child: but when I became a man, I put away childish things.” Angier’s first chapter, “Thinking Scientifically,” makes the case for scientific literacy and portrays the mind-set of scientists. Anyone who knows a boffin (as the British affectionately call the women and men in white coats) will recognize the passionate and irreverent voices of her subjects. (“Most of the time,” one of them tells her, “when you get an amazing, counterintuitive result, it means you screwed up the experiment.”) Thankfully, she does not try to render something called “the scientific method” (a phrase that never passes the lips of a real scientist) but conveys the idea that science is just the attempt to understand the world with a special effort to ensuring that the things you say about it are true. The remaining chapters cover probability, large and small numbers, physics, chemistry, evolutionary and molecular biology, geology and astronomy. Though the material is up-to-date, Angier stays clear of cutting-edge discoveries and in-house controversies. She also wisely avoids the dreary peace-and-ecology sermon with which so many scientists feel they must conclude their popular books. Every author of a book on science faces the challenge of how to enliven material that is not part of people’s day-to-day concerns. The solutions include the detective story, the suspenseful race to a discovery, the profile of a colorful practitioner, the reportage of a raging controversy and the use of a hook from history, art or current affairs. The lure that Angier deploys is verbal ornamentation: her prose is a blooming, buzzing profusion of puns, rhymes, wordplay, wisecracks and Erma-Bombeckian quips about the indignities of everyday life. Angier’s language is always clever, and sometimes witty, but “The Canon” would have been better served if her Inner Editor had cut the verbal gimmickry by a factor of three. It’s not just the groaners, like “Einstein made the pi wider,” or the clutter, like “So now, at last, I come to the muscle of the matter, or is it the gristle, or the wishbone, the skin and pope’s nose?” The deeper problem is a misapplication of the power of the verbal analogy in scientific exposition. A good analogy does not just invoke some chance resemblance between the thing being explained and the thing introduced to explain it. It capitalizes on a deep similarity between the principles that govern the two things. When Richard Dawkins, discussing the evolution of aggressive standoffs between animals in “The Selfish Gene,” wanted to explain that any signal of a wavering will should be disfavored by natural selection, he wrote, “The poker face would evolve.” Dawkins intends the poker face not simply as a metaphor that conveys a visual image (say, like the one a writer might use to depict a sphinx), but as an allusion to a deeper principle, an allusion that allows one to understand the phenomenon. Just as a poker player actively tries to hide his reactions, natural selection may select against features of an organism that would otherwise divulge its internal state. And just as it would do no good for the poker player to lie about his hand (because the other players would learn to ignore the lie), selection would not favor an animal giving a false signal about its intentions (because its adversaries would evolve to ignore the signal). Moreover, the analogy allows one to make a prediction: that just as an adversary in poker will develop increasingly sensitive radar for any twitch or body language that leaks through — the “tell” — animals may evolve increasingly sensitive radar for any tells in their rivals. A good analogy helps you think: the more you ponder it, the better you understand the phenomenon. But all too often in Angier’s writing, the similarity is sound-deep: the more you ponder the allusion, the worse you understand the phenomenon. For example, in explaining the atomic nucleus, she writes, “Many of the more familiar elements have pretty much the same number of protons and neutrons in their hub: carbon the egg carton, with six of one, half dozen of the other; nitrogen like a 1960s cocktail, Seven and Seven; oxygen an aria of paired octaves of protons and neutrons.” This is showing off at the expense of communication. Spatial arrangements (like eggs in a carton), mixed ingredients (like those of a cocktail) and harmonically related frequencies (like those of an octave) are all potentially relevant to the structure of matter (and indeed are relevant to closely related topics in physics and chemistry), so Angier forces readers to pause and determine that these images should be ignored here. Not only do readers have to work to clear away the verbal overgrowth, but a substantial proportion of them will be misled and will take the flourishes literally. (Trust me: I’ve graded exams.) Still, “The Canon” is never dull or obscure, and despite the distracting wordplay, most of Angier’s explanations are anything but superficial. She conveys the real substance of field after field, without distortion or dumbing down, and often her sensual descriptions (of the interior of a cell, a star or the Earth, for instance) leave the reader with images both vivid and useful. “The Canon” is an excellent introduction (or refresher) to the beautiful basics of science, and I hope it is widely read. It could make the country smarter. http://www.nytimes.com/2007/05/27/bo.../Pinker-t.html  CBS Buys Music Network Last.fm CBS on Wednesday said it has paid $280 million in cash for music social network Last.fm. CBS said in a statement that the online service has more than 15 million active users in more than 200 countries and would fit well with its plans to attract younger viewers and transform it from a content company to an audience company. The Last team will continue to run the online network under the terms of the deal and work with CBS to apply its community-building and technology expertise to extend CBS businesses online, the media conglomerate said. Last has earned glowing praise for its system, which recommends songs by tracking listeners' music-playing habits and linking them to fans with similar tastes. The group, based in London, has also recently signed deals with music majors Warner Music Group and EMI Group to play their music. Last launched in 2002 and has its largest concentration of users in the United States, Britain, Germany, Poland, Brazil and Japan. "Last.fm is one of the most well-established, fastest-growing online community networks out there," said Leslie Moonves, President and Chief executive of CBS. "Their demographics play perfectly to CBS' goal to attract younger viewers and listeners across our businesses," Moonves said. "Last.fm adds a terrific interactive extension to all of our properties and also is a huge step in CBS Corporation's overall strategy of expanding our reach online to transition from a content company into an audience company." http://news.zdnet.com/2100-9588_22-6187408.html  Take Note: Computing Takes Up Pen, Again Miguel Helft For more than two decades, the dream of controlling a computer with a pen has seduced and, more often than not, frustrated some of the biggest luminaries in the technology pantheon, including Bill Gates and Steve Jobs. Now Jim Marggraff, an entrepreneur with a long string of successful innovations, say he thinks he has figured out the secret of pen computing — and he has done it by playing with toys. Mr. Marggraff, a longtime executive at the toy maker LeapFrog, is the inventor behind a string of talking books, smart pens and other educational toys that have made their way into millions of American homes. His new company, Livescribe, which he plans to introduce today at the D: All Things Digital technology conference in Carlsbad, Calif., has taken some of those technologies several steps further. It has created an ambitious new type of pen-based computer system that, if successful, could bridge the gap between paper and the digital world and perhaps even change the way millions of people interact with the Internet. “I think there is tremendous potential,” said Rodney Brooks, director of the Computer Science and Artificial Intelligence Laboratory at M.I.T. Mr. Brooks is not affiliated with Livescribe but said he might become a consultant for the company. “The challenge, like with all technologies, is to package it in a way that people will want to use,” he said. History suggests that the challenge will not be easily overcome. The promise of computing with a pen has led to some of the best-known failures in Silicon Valley’s history, including Apple’s hand-held Newton, and the Go Corporation. Go was a pioneering pen computer company that attracted some of the technology industry’s most famous executives, spent $75 million of the investors’ money and ended up with little to show for it. And while pen computing has finally gained a degree of acceptance with consumers through devices like the Palm line of personal digital assistants and tablet PCs, those remain niche products, not the general-purpose machines that some pen computer pioneers envisioned. Mr. Gates, for instance, predicted five years ago that 2007 would be the year when tablet PCs became the most popular form of PC sold in America, yet they still represent less than 1 percent of the market, according to the NPD Group, a market research firm. Mr. Marggraff is familiar with this history, and that, in part, is why he has turned the very notion of pen computing on its head. Instead of forcing users to write with a stylus on a computer’s slippery display, Livescribe put the computer inside a plump ballpoint pen that is used on paper imprinted with nearly invisible miniature dots. As a user writes, a tiny camera near the pen’s tip watches those dots go by, recording what is being written. Mr. Marggraff said calling it pen computing is a misnomer. “We are creating paper-based computing,” he said. In addition to the camera, the pen, which is about the size and weight of a fat Montblanc pen, has two microphones to record sound, a speaker for playback, a small display that Mr. Marggraff calls a pixel bar, and, of course, a hidden computer chip and other sophisticated electronics. It fits into a docking station, where it can upload or download programs and data files to and from a PC. The Livescribe pen is a more advanced version of the LeapFrog Fly Pentop Computer, which itself has some impressive abilities, even if it is intended for children. Fly users can draw a calculator on paper and make it work by tapping the keys with the pen; a speaker in the pen plays back the results. Users can also draw a piano keyboard on a piece of paper and play a tune on it. The same technology, which is licensed by Anoto, a Swedish company, has made its way into pens that can be used to write notes and upload them onto a PC, but not much else, and hence has failed to become popular. But Mr. Marggraff, who left LeapFrog to form Livescribe when the Fly hit store shelves during the 2005 holiday shopping season, has taken the technology several steps further. He also plans to open up the technology to others, in hopes that Livescribe will attract content creators and third-party programmers who will develop many new uses for it, including some not yet envisioned by Livescribe’s team of about 45 employees. For now, Mr. Marggraff plans to market the pen, which will be available in the fall for less than $200, to college students, and he has some very specific ideas for how they will use it. The pen, he said, will revolutionize the way millions of students take notes. To demonstrate, Mr. Marggraff jots down some notes while talking with a visitor. As he speaks, the digital recorder inside the pen captures his voice. Once done, he taps the pen on a word he scribbled halfway down the page. The pen immediately begins to replay the conversation, starting from the point in time when Mr. Marggraff had written that word. He then skips back and forth in the audio simply by tapping the pen on different places on the page. Finally, he docks the pen, and uploads the notes and the audio to his laptop computer. From there, Mr. Marggraff said, he can organize the notes, search through them, play them back and send them to others. Additional software can translate the written notes into text. Mr. Marggraff said these features could also be useful to professionals like journalists, doctors, job interviewers or lawyers who want to share with associates notes of a business negotiation. “Anyone that is writing notes on paper, wants to capture the information, they want to access the information,” Mr. Marggraff said. “We are giving a way for people to essentially forget about forgetting.” Mr. Marggraff said the pen could also provide a powerful new way for people to upload words, pictures and audio to their Web sites, blogs or social networking pages. To generate excitement about the future potential of the Livescribe technology, Mr. Marggraff performs a nifty stunt: he reaches into his pocket, pulls out his business card and hands it to someone saying that if the person jots down a note on the back of it with a Livescribe pen, the note could soon land in Mr. Marggraff’s e-mail in-box. “It’s the first interactive business card printed on self-addressing paper,” Mr. Marggraff said. By the end of the year, he said, similar paper with unique dot patterns associated with particular e-mail addresses will be available. Once notes written on such paper are uploaded to a PC, they will automatically forward to the address, opening many business applications. A drug company, for example, could use the technology to gather data from patients during late-phase clinical trials. For Mr. Marggraff, this is as close as he has been to fulfilling a 10-year quest to make paper interactive. It began even before he joined LeapFrog in the late 1990s, when his company, Explore, built a globe, which at the touch of a stylus, would call out capitals. After LeapFrog bought Explore, Mr. Marggraff helped create the LeapPad, a touch-sensitive plastic surface that with the help of a stylus, turns paper books into talking books that can help kids learn to read and write. The LeapPad became the best-selling toy in America in 2000 and 2001, a first for an educational toy. After a series of other hits, Mr. Marggraff helped conceive the Fly. LeapFrog will not say how many Flys it has sold, but Mr. Marggraff said it had been the company’s best-selling product. Mr. Marggraff, who said he was about to get $22 million in financing from a group of venture capitalists led by Vantage Point Venture Partners, has even bigger plans for Livescribe, based in Oakland, Calif. He will not talk about them in detail now. But in the past, Mr. Marggraff has described a vision for what he calls “the paper Internet.” In it, many of the things currently done on a computer, say, buying a book or sending an e-mail message, could be done with Livescribe’s pen. Write the words “shop,” “Amazon.com” and the name of a book on a piece of paper, then dock the pen, and the computer would take care of the rest. Few people have seen the Livescribe so far, but veterans of the pen computing world say that while the technology sounds impressive, success is far from guaranteed. “I hope the product matches the hype,” said Jerrold Kaplan, a co-founder of the pen computing pioneer Go in 1987. “It has to work really well. It’s such a new concept, and often the execution of new concepts requires several iterations before the quality is acceptable.” Another challenge is that Livescribe is being introduced into a world where young people are spending more time typing text messages on cellphone keypads and writing less in longhand. Paul Saffo, a longtime technology forecaster who teaches at Stanford’s School of Engineering, said, “Ironically, the big behavior change may be to get this younger generation to pick up this unfamiliar instrument called the pen.” http://www.nytimes.com/2007/05/30/technology/30pen.html  Heaven, Hell and Purgatory, Encased in Glass Nicolai Ouroussoff  It’s almost daunting to note how many young architectural talents are flourishing today in the Netherlands. If Rem Koolhaas, the profession’s reigning intellectual prince, casts a long shadow, it’s clear that plenty of emerging architects have managed to assert strong creative voices of their own. Willem Jan Neutelings and Michiel Riedijk stand out from the usual Koolhaas clones. Still relatively unknown in the United States, their firm has steadily built a reputation in Europe for bold designs that draw on everything from primitive temples to comic-book illustration and the decorative ephemera of Andy Warhol. They also have something as rare in architectural circles as raw talent: a sense of humor. The completion of their Netherlands Institute for Sound and Vision here can only elevate their status. Wrapped in a luxurious skin of colorful cast-glass panels, it is their most gorgeous work to date. Yet beneath the glittering surfaces they have fashioned a serious critique of a world saturated in advertising and marketing images, and reaffirmed architecture’s heroic stature. A leafy suburban hamlet southeast of Amsterdam, Hilversum is best known as the center of the Dutch television industry. Yet it has quietly amassed an impressive array of architectural works. The folded concrete forms of the Villa VPRO, the offices of a private broadcast authority designed by the Dutch firm MVRDV, are visible from a distance; Willem Marinus Dudok’s low, graceful brick town hall, a landmark of early-20th-century Modernism, is a short drive away. The Netherlands Institute for Sound and Vision, the home of the national broadcasting archives, was conceived as a perfect cube, half of it buried underground. In addition to the archives and offices, it houses a museum, making it a new cultural focal point for the city. Standing on an isolated lot flanked by a small garden, its glowing glass shell recalls the translucent exterior of Gordon Bunshaft’s 1963 Beinecke Rare Book Library at Yale . Like many architects of their generation, Mr. Neutelings and Mr. Riedijk have been heavily influenced by postwar architects like Bunshaft: the brutal directness of his buildings carries particular appeal when so much architecture is corrupted by fairy-tale images straight from Disney. Both buildings are taut, confident structures. But Mr. Neutelings and Mr. Riedijk’s building is rooted in pop culture rather than in the ethos of postwar corporate America. Conceived in collaboration with the 65-year-old artist Jaap Drupsteen, the structure’s panels are imprinted with famous images from Dutch television: the justice minister riding his bicycle, say, or Johan Cruyff scoring a goal. Using computer technology, Mr. Drupsteen ran the images together and baked them into the glass. The effect is mesmerizing. The images are only barely discernible from certain angles, as if the building were imprinted with the faint traces of shared memories. But the exterior facades are also a sly critique of contemporary culture. The blur of images conveys the daily bombardment from the Internet, television, movies and newspapers, yet here they seem frozen in time, as if temporarily tamed. Inside the building that tranquillity gives way to a comic-book version of Dante’s “Divine Comedy,” with strict divisions between various worlds. Visitors enter via an internal bridge that crosses over an underground atrium. From here, a vast hall conceived on the scale of a piazza leads to a cafeteria overlooking the calm surface of a reflecting pool. On one side of the hall looms the ziggurat form of the museum; on the other, a wall of glass-enclosed offices. Here the spectral glow of the interior of the cast-glass skin evokes the stained-glass windows of a medieval cathedral. It’s a stunning space whose power lies in the contrast between the various architectural experiences within. Clad in cold gray slate, for instance, the underground atrium is a striking counterpoint to the heavenly glass walls above. Mr. Neutelings and Mr. Riedijk call the atrium their “inferno.” It also evokes a tomb: big, square openings are cut through the atrium’s walls, revealing a series of corridors painted a hellish red. The archives are tucked behind these corridors, where researchers and scholars, you suppose, toil away with the concentration of monks. Neither fiery nor blissful, the offices are something closer to purgatory. Arranged in neat little rows, they open onto long, narrow corridors that overlook the bustling main hall. The office interiors are more contemplative, the colored cast-glass panels alternating with more conventional strip windows. The colored glass emits a soft glow that is strangely soothing. But the true inferno, in visual terms, is the museum. Mr. Neutelings and Mr. Riedijk set the entry stairs off to one side of the main hall, as if they were trying to avoid it. There are hints of the architects’ presence inside: the walls of the museum auditorium are covered in an elegant, diamond-shaped pattern, and two small openings pierce the darkness at the top of the stairs to the museum’s upper floors, offering sudden glimpses of the colorful glass skin. But the architects had no control over the design of the exhibitions, and what little architecture there is here is completely overwhelmed by a nauseating mix of interactive installations, reproductions of stage sets and tchotchkes from old Dutch television shows. The effect is cringe-inducing. Like many architects, Mr. Neutelings and Mr. Riedijk are struggling to come to terms with a society that is on the verge of being completely consumed by global advertising and marketing images. More often than not, architecture is becoming a tool of those interests. By sealing off these competing forces in distinct worlds and then juxtaposing them, the architects have subtly reasserted the dignity of the public realm, while providing a potent commentary on where our culture is heading. http://www.nytimes.com/2007/05/26/ar...26visi.html?hp  Beware of DMCA Scammer Tyler Cruz I’ve written many important and useful articles in the past, but this will be one of the most important ones I’ve ever written, so I highly suggest you read it in it’s entirity. This evening was interesting. I received a DMCA, followed later by harassment and even death threats. Let me start at the beginning. Several days ago I had contacted the owner of Starcraft2.net to try to purchase the domain. After a couple days of declining my increasing offers, Eric, the previous owner, contacted me again and said he would, after all, agree to my offer. It turned out that his previous declinations were stemmed from the fact that he had received a very authentic-looking DMCA and didn’t want to sell the domain to me as it’d under false pretenses. However, Eric had done the smart thing and contacted Blizzard to inquire on the matter more. Blizzard responded by basically stating to ignore the e-mail as it didn’t come from them. And this would make sense, since the e-mail came from the address: howardgspinks@gmail.com and not a Blizzard or even attorney’s office. So, Eric had informed me of his incounter and had warned me that the scammer may try to contact me when the WHOIS information passed to my name. Several hours ago, I received a DMCA from howardgspinks@gmail.com. Even though I had been warned by Eric about this, it was still very uncomfortable. Even with the suspicious Gmail e-mail account, the DMCA is as authentic looking as you’re going to get; in fact, it probably is authentic, only Blizzard never sent it; the scammer “Howard G Spinks” did. Here is a copy of the DMCA e-mail sent to me: dmca email A few minutes after receiving the e-mail, Howard G Spinks (Alfred E. Neuman?) added me to MSN. Here is a copy of the entire chat transcript with him. It’s a very entertaining read so I highly recommend reading it: piratereports.rtf As you can see, I was very strong and held my ground from the beginning. This guy really does try hard to scare people into giving them their domains, or perhaps he is hired by competitors to try to thwart competition; that thought did cross my mind, but I think he really just tries to score good domains and probably sells them quickly thereafter. You see that I ask the gentleman for his phone number, and he responds with “1-800-kiss my ass”. I guess he’s too afraid to continue his scam over the phone. I was also ready to record it for the police. I can’t believe he threw so many threats at me, I think he did this because I held my ground so well and his scam didn’t phase me. In the chat transcript, you can see the longer it goes on, the more his immaturity comes out, such as the use of the word “owned”. It’s lucky that I had talked to Eric first, as that did help prepare me for this enslaught, which is partly why I wrote this article: BE AWARE OF SUCH SCAMMERS. If you ever receive a DMCA , C&D, or similar type of e-mail or even phone call, don’t immediately hand your domain over and surrender. While it’s very important to comply with such legal matters, make sure first that they are authentic legal entities. You may even want to contact a lawyer if you don’t already have one on speed-dial and have them handle it for you. You’ll notice that Howard G. Spinks states he is from PirateReports.com. Well, if you visit the Contact Us page on their site you’ll notice they clearly states: “If you receive an email purporting to be from any member of Pirate Reports and a digital signature is not included please forward a copy to us for a response and not our ISP. It is very likely a “spoof” from a pirate to damage our reputation.” Guess what. I never received any such digital signature in my e-mail from him. A Google search of “Howard G Spinks” returns a lot of results of people who have had similar problems with this scammer. Now, for a bit of revenge. While notifying the public of his scams will undoubtedly be revenge enough, here are a couple of his contact details MSN: piratereport@hotmail.com E-mail: howardgspinks@gmail.com So feel free to give him a hard time. http://www.tylercruz.com/beware-of-dmca-scammer/  Arnie to Automakers: 'Get Off Your Butts' CBC News California Gov. Arnold Schwarzenegger brought his environmental message of "active optimism" to Ontario Wednesday, along with a thinly veiled warning to the province's automakers to prepare for the "green, clean" revolution. And along with trading hockey sweaters with Prime Minister Stephen Harper, he secured a pledge that Ottawa will crackdown on movie piracy. Earlier in the day, speaking at the Toronto Economic Club luncheon, the former movie star turned leading voice on combating climate change said he had no doubts America would become the "best chance" to solve global warming. "I came to say to you, do not be discouraged," he told the crowd. "Your neighbour may be late in coming to the front, but we are coming." He joked that before he took office in 2003, he was vilified by environmentalists for his extensive use of private jets and love of huge Hummer vehicles, only to be later dubbed the "Green Giant" for his anti-climate change initiatives in office. "I had five," he said in reference to the notorious gas-guzzlers, noting that one of his Hummers now runs on biodiesel and another runs on hydrogen. During his speech, Schwarzenegger issued a warning to automakers spreading "doom and gloom" messages over California's tail-pipe emissions standards, citing a billboard in Michigan that read, "Arnold to Michigan: 'Drop dead.' " "What I am really saying to them is, 'Arnold to Michigan: Get off your butts,' " Schwarzenegger said to the Ontario audience, whose province's auto sector has been the No. 1 auto producer in North America for three years running. "We're pushing them to make the changes necessary so they can sell cars that can be driven in our state. If they don't, someone will." 'Governator' meets with Harper Earlier Wednesday, Schwarzenegger and Ontario Premier Dalton McGuinty signed an agreement that includes low-carbon fuel standards for vehicles. The deal requires cars in Ontario to have 10 per cent fewer emissions by 2020, equivalent to a reduction of 700,000 cars, the province said. Schwarzenegger said he was "very, very happy" to sign the deal, even though it stopped short of California's tough new tail-pipe emission standards. "We're all partners," he said, adding that the agreement would create "additional momentum" for tougher standards across North America. Schwarzenegger is in Canada for a three-day trade mission to promote tourism in his state. He said the purpose of his trip was not only to promote Californian exports in Ontario, but also to discover Canadian goods. He later met with Harper at his office on Parliament Hill. In public, they only discussed the Stanley Cup, and who would end up wearing the other team's colours. Harper gave Schwarzenegger an Ottawa Senators' jersey, and the governor returned the favour with an Anaheim Ducks sweater. But sources on both sides of the border told the Canadian Press Harper raised the issue of movie piracy in a closed-door meeting. One U.S. official said Schwarzenegger was pleased to hear Canada address a problem plaguing his state's film industry. "We think it's a good first step," said one American official. The government said it will introduce legislation that helps police charge people who use camcorders in theatres to tape movies, which are later distributed on the internet or sold as DVDs. http://www.cbc.ca/canada/story/2007/...ger-green.html  Why Hollywood Is Getting Serious About 3-D Richard Siklos IT’S kind of fitting that the first live-action 3-D movie expected to find its way to the modern multiplex after a preview at the Cannes Film Festival last week is a U2 concert film. The band’s lead singer, Bono, is known for wearing shades, so it might seem downright participatory for the audience to don 3-D spectacles in order to have, as The Times’s Sharon Waxman put it last week, “the palpable experience of being present” while U2 rocks out. In a more mainstream way, Hollywood bigwigs like James Cameron, Jeffrey Katzenberg, Steven Spielberg, Peter Jackson and Robert Zemeckis all have new 3-D projects in the works and are proclaiming the beginning of a bold new era for cinema. Obviously, 3-D is not exactly a post-modern idea, and for most people it first brings to mind thoughts of wacky, red-lens-blue-lens cardboard glasses —or even of the headgear that Imax offered when it started showing 3-D flicks on its giant screens in the 1980s. But 3-D is clearly coming into its own, and its cinematic aspect is just one element of technology’s broader march toward a new era of make-believe super-realism. Part of the enthusiasm for 3-D is what it will mean for creative expression and story-telling. And part of it is Hollywood’s response to changing technologies — you can be sure that James Cameron’s aptly named feature “Avatar,” scheduled for release in 2009, will look a whole better in a movie theater than it will on a laptop or iPod. Last week, I sat in a nearly empty Times Square theater and watched “Meet the Robinsons,” the animated, 3-D Walt Disney feature that has taken in a solid $150 million since its premiere on March 30. Like many other 3-D offerings that studios are bringing to the screen, it was projected on a digital system called Real D that a growing number of theaters are installing. It’s doubtful that even the current generation of glasses —simple black plastic frames with clear lenses — would satisfy Bono’s tastes. But they are fairly unobtrusive and, without them, the image on the screen is a blur. With them, the 3-D illusion enhances the experience, making a robot’s head seem to extend to the seatback in front of you, and streams of peanut butter and jelly fly past your face. It’s more than a gimmick, but to my eyes it’s hardly a revolution, either — it’s a device that can make a good story better, but can’t make a dull story good. (The same goes for high-definition, the current rage of home video and television programming: watching LeBron James live in HD is spectacular; it’s less exhilarating when Tony Soprano is biting into a cannoli.) Whether it is the savior of the cinema-going experience or a nice add-on like surround sound and comfy chairs is yet to be seen, but there is palpable excitement around 3-D. Equally intriguing, 3-D is coming not just to the theater, but also to the living room and potentially to anywhere your eyeballs might happen to wander. In addition to retooling his “Star Wars” series in 3-D, George Lucas is working on a new 3-D television show. All sorts of TV and display companies, including Philips, are working on a next generation of 3-D HD monitors that might not even require viewers to wear glasses. If you believe the theory that TVs and computers will merge into one utility, 3-D offers intriguing interactive possibilities — especially the use of avatars in everything from PlayStations and Xboxes to virtual worlds for grown-ups like Second Life and virtual playgrounds for children like Club Penguin. For the uninitiated, avatars are digital representations of yourself in video games or as alter egos in the online world. At first blush, they may seem like something for geeks and under-30s, but a lot of people are trying to figure out ways of bringing avatars into the mainstream — the idea being that a virtual world like Second Life is just a three-dimensional version of the Internet. There are already longstanding and impressive avatar applications for people with disabilities and, of course, the military. Instead of going to a typical two-dimensional Web site like, say, Yahoo, maybe one day there will be a 3-D version where you and your friends can hang out, or visit online shopping malls, cooking classes, foreign lands and just about anything else that exists in the real (or imaginary) world. Just as the U2 film gives audiences a front-row experience without going to the live show, much of the online excitement around 3-D involves letting people explore the real world in an immersive way. By now, for instance, many people have already had the fleeting thrill of using a piece of software known as Google Earth. It uses automated satellite imagery to give an up-to-date rendering of the world, through which users can zoom in on their blocks, homes or any other landmark. But one of the more interesting tangents that Google is pursuing is the use of 3-D modeling to attach buildings and structures to satellite maps so that landscapes can eventually be viewed (and explored) from any perspective. Google uses a software it acquired last year, SketchUp, to allow people to create digital renderings of objects, their homes or entire city blocks, which are then kept in something called the 3D Warehouse — from which the most accurate renderings are grafted onto the Google Earth database. JOHN V. HANKE, who runs Google Earth, told me a few months ago that Google’s approach to recreating the world in 3-D was initially for “purely utilitarian” uses like real estate searches and finding the nearest Wal-Mart, whereas the 3-D tack that Hollywood and video game companies are taking is born out of “pure fun.” But he acknowledged that the two were destined to intersect. In one interesting educational use, the cable-channel operator Discovery Communications has been providing streaming video to Google Earth since last year: when you visit Yellowstone Park using the service, you can view documentary footage that Discovery provides. The accelerating blurring of real and artificial is sure to raise warning flags about how we interact. One hopes that such activities as “going outside to play” and “talking face to face” would still hold some appeal in our 3-D future. And it doesn’t take mathematical genius to calculate that 3-D + porn = $$$. But Hollywood’s 3-D foray also demonstrates that the idea is to improve existing media experiences like going to the pictures (or doing research), rather than replacing real-life endeavors. While there’s no question that the entertainment and information industries are destined for some kind of 3-D future, Mr. Hanke said, “there’s no master plan sitting on the shelf on how it’s all going to happen.” For now, we just have to slide on the specs or click the mouse and enjoy the show. http://www.iht.com/articles/2007/05/...g/frenzy28.php  Gassing Off Apparently 150 billion cubic metres of gas are burnt off every year - enough gas to power the United States for three months. Even worse - the 390 million tonnes of carbon dioxide released while doing this is more than the reduction of CO2 emissions from many of the carbon offseting projects of the Koyoto protocol. Nigeria alone burns off enough gas to power half of Africa for a year. Writer, producer and director (and co-author of the first funding book), Caroline Hancock, has just completed a documentary on the subject and apparently almost got shot when shooting in Nigeria. While the screening on BBC World has passed it may well appear online at some point or be replayed on the channel - and either way sounds like a pretty important contribution to an ever more urgent problem. http://www.netribution.co.uk/2/content/view/1202/182/  Life in the Sprawling Suburbs, if You Can Really Call It Living Matt Zoller Seitz “In some ways a suburban city can be understood as an intolerant city.” If that loaded quotation from the Calgary-based architect Marc Boutin doesn’t tell you exactly where “Radiant City” stands on the issue of suburban sprawl, the filmmakers have plenty more just like it. Blending documentary elements and some dramatic material (you don’t realize which is which until the movie springs its best surprise), “Radiant City” is an acerbic position paper on the cultural damage done by postwar architectural fads. The film unfavorably contrasts early-20th-century suburbs, which were built around shared public spaces and more conducive to pedestrian life, with their postwar successors, which lured inhabitants by promising huge amounts of space and no obligation to care about what happened beyond your property line. The directors, Gary Burns (who has plumbed this territory many times, most notably in the comedy “Waydowntown”) and Jim Brown, depict sprawling, antiseptic housing developments and the culture of long commutes as a recipe for alienation and an impediment toward building a real sense of community and, especially, consensus. The cast of characters mixes academic experts and supposedly regular citizens. Their ranks include a theater troupe working on a musical about suburban life, a tightly wound mother who micromanages each day on a refrigerator scheduling board, and a young teenager who observes the vastness of his personality-free exurb from the top of a cellphone tower. (He says he’s careful not to stay up there longer than a few minutes because he doesn’t want to get a brain tumor.) James Howard Kunstler, a critic of suburbanization, appears throughout “Radiant City” and helps define its tone, which could be described as one of incredulous lament. The cinematographer Patrick McLaughlin’s eerie, sometimes monumental images italicize the experts’ statements, making the suburbs seem like an asphalt-and-Sheetrock dreamscape where democracy goes to die. RADIANT CITY Opens today in Manhattan. Written and directed by Gary Burns and Jim Brown; director of photography, Patrick McLaughlin; edited by Jonathan Baltrusaitis; music by Joey Santiago; produced by Shirley Vercruysse; released by the National Film Board of Canada. At the Two Boots Pioneer Theater, 155 East Third Street, at Avenue A, East Village. Running time: 85 minutes. This film is not rated. WITH: Daniel Jeffery (Nick Moss), Bob Legare (Evan Moss), Jane Macfarlane (Anne Moss), Ashleigh Fidyk (Jennifer Moss), Curt McKinstry (Ken) and Karen Jeffery (Karen). http://movies2.nytimes.com/2007/05/3...es/30radi.html  Local news Yo, Vermont, What Up? These 3 Dudes, for Starters Katie Zezima Vermont has long been a muse for poets and painters, but rappers have never been known to draw inspiration from its bucolic landscapes and postcard-perfect small towns. Until now. The quiet streets and low crime rates of Vermont have worked their way into the hip-hop world, thanks to a rap video called “802,” made by three students at Montpelier High School. “Up in Vermont, this is how we do, we got one area code, and it’s 802,” rap Colin Arisman and Luke Martin, who wear white polo shirts and start the video by hopping out of a white Toyota Scion. The rap, at www.youtube.com/watch?v=GL7uW4TYqbs, pokes fun at Vermont institutions and stereotypes like dairy products and snowplows. “Green Mountain State, where we roll on skis, don’t mess with our cows or we’ll break your knees,” go the rappers, who perform under the name X10. Colin, Luke and their main man Kevin Hartmann wrote “802” in September after tossing around verses with a group of friends after school. They shot the video in the fall but did not post it on the Internet until early May. It has been viewed more than 55,000 times since then. “It went crazier than we ever thought,” said Kevin, 16, who shot, produced and posted the video, and calls himself Dr. K. The boys had planned to pen a rap only about Montpelier, the state capital, where just a handful of establishments are open past 10 p.m., cars stop for pedestrians along clean streets, and teenage loitering on Main Street is the only thing that comes even close to outward flouting of the law. Instead, they decided to rap about all of Vermont, having concluded that the state could not get by on street cred alone. They included lines about Cabot cheese (they like cheddar “extra sharp,” which they rhymed with “roof tarp”), local pizza places and the Vermont State House, where, along with the streets of Montpelier, most of the video was shot. “Our state capitol might be 200 years old, but our dome is so blingin’ that it’s plated with gold,” goes “802,” which is set to the beat of a Mobb Deep rap. The most prominent employee in the building, Gov. Jim Douglas, has seen the video. “We’re down with that,” said Jason Gibbs, a spokesman for Mr. Douglas. X10 plans to make a political statement with its next rap, in support of a global warming bill currently before the overwhelmingly Democratic state legislature. Mr. Douglas, a third-term Republican, may not enjoy that video as much; he has said he will veto the measure. Colin, 17, whose moniker is C$ (pronounced C money), likened the creating of “802” to writing a term paper. The rappers, who are all in the midst of SAT preparation, said they had taken something of an intellectual turn in their video, using words like “fustigating” and avoiding profanity. “I don’t think a big SAT vocabulary is what a lot of rappers are looking for,” Colin said, “but if it enhances your writing, that’s good.” In any case, the goal was to show that Vermonters can poke fun at themselves. “We’re small, we might be a little boring, but we can have fun,” Kevin said. “We have a sense of humor.” http://www.nytimes.com/2007/06/02/us/02vermont.html?hp  Anyone for a Gathering of Introverts? Tammy La Gorce ALEX ROSENZWEIG, 41, has a problem: People are tired of hearing him talk about “Star Trek.” “At work they complain incessantly,” said Mr. Rosenzweig, 41, an editor at an environmental consulting firm who is wearing a polo shirt with spaceship insignia. His colleagues give him guff about the 2-foot-by-3-foot “Star Trek” poster he displays prominently. And at home in North Brunswick, he knows better than to greet neighbors with a Vulcan salute. But once a month, Mr. Rosenzweig feels free to indulge his passion, when he gets together with other members of the Morris County New Jersey Star Trek Meetup at the Empire Diner in Parsippany. The group, which now has 39 members, gathers to talk TV and dissect its own home-produced “Star Trek” series. Mr. Rosenzweig and his friends found each other on the Web site Meetup.com, which has helped create about 2,000 social groups in the suburbs of New York City in the last five years, according to Andres Glusman, a spokesman for the site. The size of the groups ranges from a handful of people to hundreds, Mr. Glusman said. Many meet monthly. In Trumbull, Conn., 30 pug owners come together to walk and talk. Over in Fairfield, a handful of vegetarians swap recipes at a meat-free restaurant. A dozen proud Subaru owners gather to talk engines and bodywork in Paramus, N.J. And a couple of amateur golfers who stash six-packs of beer in their carts hope to add to their number in White Plains. Judging by the 3,500 topics currently represented on the five-year-old site, no interest is too narrow. Mah-jongg enthusiasts have found one another on the site, and so have marriage arrangers. Meetup.com was credited with playing a huge role in helping to transform Howard Dean from a little-known governor to an early front-runner for the Democratic nomination in the 2004 presidential campaign, when groups organized by his supporters proliferated on the site. Over all, the more than 22,000 Meetup groups bring together 3 million people worldwide, Mr. Glusman said. Other Web sites, including Craigslist, offer similar opportunities for people to get together, but Meetup’s strength is its focus on club-forming. Unlike dating sites, it unites broad clusters of people. And unlike MySpace and Friendster, it emphasizes the rewards of meeting in real time, face to face. “You could try to accomplish something similar with Yahoo! Groups, but that’s primarily a mailing list,” Mr. Glusman said. “It doesn’t provide the local people, tools and training to organize an offline community group.” In suburbs across the region, much of the Meetup activity revolves around singles mingling and stay-at-home moms arranging playgroups. The site indicates the number of members in each meetup, and the region’s largest, with 744 members, is the NJ Over 30, Over 40, Over 50, Sexy and Sassy group. It meets monthly at different restaurants and bars around the state. “My hunch is that in large cities like New York, there are more established institutions helping people meet each other,” Mr. Glusman said. “In the suburbs, with the sprawl, you can see people every day in the grocery store but never know that they’re extremely passionate about flying or want to practice their Spanish. We’re probably more useful to people in the suburbs.” Suzie Calo, 40, a bookkeeper and a former party planner from Eastchester, N.Y., has helped organize two Westchester County-based meetups: a ghost-tracking group, with 81 members; and a divorce support group, which has 86 members. Ms. Calo said many people formally join groups by posting personal profiles but don’t necessarily show up at gatherings. The divorce group has about a dozen core members, she said, and the ghost trackers about half a dozen. Meetup groups don’t cost anything to join, but organizers pay the site $12 to $19 a month, based on their specific Web needs. Ms. Calo said the value of the groups is the opportunity they offer to meet people with similar interests and in similar situations. “In the divorce group, we’re there recommending lawyers and listening to each other’s Jerry Springer nightmares,” she said. “And the ghost trackers — I’ve had experiences with paranormal phenomenon, and so have the others. We get together at a diner, and we talk.” Some organizers say the site has helped them promote causes. “I was anxious to do something to elect a candidate,” said William Kransdorf, a 49-year-old lawyer who heads an 18-member group, the Essex County Barack Obama Meetup, which gathers monthly. On a recent Tuesday night, 11 people showed up at the Goat Cafe in South Orange, N.J., to discuss Mr. Obama’s presidential chances. A couple of students from Seton Hall University and several men and women in their 30s and 40s attended. “I had to get involved in this campaign,” Mr. Kransdorf said. “This meetup is just my way of doing it.” On Long Island, the Web site has helped reinvent the potluck dinner. Pat Maiti, 54, who produces a cable television show called “A Taste of New York,” recently organized a gathering at her Syosset home for the Long Island Social Chef Dinner Party Meetup. Of the group’s 113 members, about 40 showed up with different dishes to share. “I came tonight because I wanted to meet people and make connections,” said Gail Giunta, 37, the owner of a reiki massage studio. Ms. Giunta had traveled to Ms. Maiti’s house from her home in East Hampton. Larry Katz, 42, an administrator at a medical imaging center from Fort Salonga, said the group draws a diverse crowd. “The food is great, but it’s also a very good way to meet interesting people,” he said. The allure of simple friendship motivates many participants. Every other week, 3 to 10 members of Andrea Berman’s New Haven French-language group meet over crepes at a cafe. “I’ve always been interested in language and culture, but this is also a way to socialize,” said Ms. Berman, a 36-year-old engineer. “For the people who come regularly, it’s a really nice feeling.” One worth building on, by Meetup’s reckoning. On June 9 at a still-undisclosed field near White Plains, the Web site plans to hold its first NYC Suburb Meetup Olympics and barbecue. “The idea is to pit Meetup groups against each other in fun and games,” Mr. Glusman said. “It’s going to be a big, fun picnic.” http://www.nytimes.com/2007/05/27/ny...27Rmeetup.html  The Many Tribes of YouTube Virginia Heffernan WHAT do you think of the latest video on YouTube? Wait. Don’t answer that, or at least don’t answer with words. Because almost the instant you start to talk about one of the beautiful, puzzling videos that pervade the site that Google acquired last fall for $1.65 billion, you reveal that you’re missing the point. Really the only authentic response to a YouTube video is another YouTube video — the so-called “video response.” YouTube appeared in February 2005, when it was modestly billed as a site on which people could swap personal videos. Since then, however, its video-response feature, which essentially allows users to converse through video, has managed to convene partisans of almost every field of human endeavor, creating video clusters that begin with an opening video, and snowball as fans and detractors are moved to respond with videos of their own. In answer to a lousy, stammering video, say, a real YouTuber doesn’t just comment, “You idiot — I could do that blindfolded!” He blindfolds himself, gets out his video-capable Canon PowerShot and uploads the results. There are music-making videos about music, dance videos about dance, and architecture videos about architecture. Music people respond to musical performances by filming a musical performance of their own. The same principle holds for dancers, athletes, pundits, pedants, comedians, film editors, poets, stunt people, propagandists and showoffs of every stripe. What’s more, YouTube’s interface allows users to track the history of anything they watch, as well as to pursue video responses to it. As a further inducement to stay on the site, YouTube proposes a half-dozen works that might interest you whenever you’re streaming a video. When you enter the site, then, be warned: before you know it, you’ve entered one of YouTube’s great unmarked communities — the shred guitarists, the torch singers, the Christopher Walken impersonators. Each community is filled with so many small obsessive pursuits colliding and colluding with one another that it’s awfully tempting to skip your lunch break — or take the day off — and watch them all. What follows, then, is not a list of the top videos on YouTube. That would be too simple, too old-Web. Instead, here are five of the most fascinating worlds to get lost in on YouTube. Every single one of them is worth a detour. 1. PETER OAKLEY, A K A GERIATRIC1927 Last August Peter Oakley, a British pensioner, posted a video that he promised would contain grumbling and griping under the screen name geriatric1927. In fact, it was a love letter to YouTube, and an expression of hope that the video blogs he was planning to post regularly would interest users of the site. In record time the entries, which tell the story of a widower, blues fanatic and former radar technician in the British Army, inspired a tribute video from a hipster admirer, who dubbed Mr. Oakley “The OG of Blogging” — that’s original gangsta. A grandpa who knows about radar? What techie kid doesn’t dream of that? Then came the imitators: Right, I’ll have a go myself, resolved jimsan1, another YouTuber who appeared close to Mr. Oakley’s own age. (Mr. Oakley turns 80 in August.) Before long, Mr. Oakley’s videos were attracting a million views and more, and his series of videos are among YouTube’s 10 most heavily subscribed to. Now the senior-citizenry of YouTube regularly posts video oral histories in serial form, talking straight into the camera without pyrotechnics or theatricality in tribute to the understated style of the master. Mr. Oakley can now be heard singing with the Zimmers, a vast rock group formed of elderly retirees and overseen by Mike Hedges, the U2 producer. The band releases its first album, “My Generation,” on Monday, but its first music video — a performance of the Who’s “My Generation” with Pete Townshend — was uploaded to YouTube last month. 2. TIME-LAPSE PAINTING Just as YouTube has made room for producers and consumers like Mr. Oakley who have been shut out of earlier pop-culture revolutions, it also accommodates art forms that other media have threatened for years to make obsolete; witness the many origami how-to videos on the site, as well as lute and gamelan recitals, polka dancing and happenings of the Dada-Yoko Ono kind. It should come as no surprise, then, that the august art of portrait painting has made modest inroads into the consciousnesses of the MySpace generation. Of course, painting is typically appreciated face-to-face, but painters on YouTube have added drama by creating time-lapse films of themselves at their easels. The videos, which move too fast to be instructive, nonetheless address both the most childlike questions we have for realist painters (How did you do that?) and the most suspicious (Did you do it yourself?). They also exude infectious bravado, as the painter accomplishes a day’s work in three or four minutes, without anxiety or second thoughts. Laura Karetzky, a figurative painter in New York, was drawn to the time-lapse portraits because she thought they might provide a window into the private agonies and ecstasies of other painters. They did. In one video, titled “Heather Paints Melissa,” a hobbyist paints and repaints a child’s face, each time unintentionally deepening the portrait’s flaws. “I find myself hanging on the edge of my seat clasping my hand to my forehead,” said Ms. Karetzky. “I’m actually rooting for her in the end not to make the same mistakes she just painted out three or four times earlier.” 3. PARKOUR Speaking of performance art and mysterious spectacles, parkour — a form of extreme gymnastics invented in France — thrives on YouTube. What good, after all, is scaling buildings, leaping down staircases and jogging over cars if no one is around to see you pull it off? That’s where videos, and their international dissemination, come in. Some parkour videos are professionally made programs about the art of movement, in which the whole world is an obstacle course and no structure is insurmountable. These gorgeous minifilms feature muscled figures, often shirtless, looking like jewel thieves or Spiderman, atop buildings where they skip and leap with such death-defiance and frank grace that it’s hard to keep from calling their sport dance. But no: parkour is meant to be martial, efficient and tough. Amateurs from all over the world have also shared their stunts on YouTube. The homemade spinoffs mimic professional ones in that they strew together scenes from disparate places and times, cherry-picking only the players’ best stunts and supplying no clear course trajectories. But many of the participants in the amateur videos look like teenagers, their jangly movements plainly influenced by hip-hop and skateboarding as much as by dance, circus art and gymnastics. And unlike the pros — who really appear to risk their lives — the copycats wisely use jungle gyms and rubber surfaces for soft landings. After a pileup of decidedly self-serious parkour offerings, a comedy team called the Suggestibles posted a parody response, “Pour Quoi,” in which two Englishman (naturally) talk in phony French accents and struggle to get through a revolving door. 4. BLASPHEMY Individual religious testimony abounds on YouTube, as do sermons from miscellaneous (and sometimes extinct) religious institutions, but these are posted to fire up discussion, not to lay down any laws. Versions of the last sermon of the prophet Muhammad are posted — one runs “Star Wars”-style with the words receding into outer space — as are Christian sermons on sexual purity and Palestinian sermons that contain anti-Semitic slurs. Viewers are urged to discuss them, and they do. Curiously, the religious group that makes the most imaginative and despotic use of YouTube are atheists. The Rational Response Squad, a furtive organization devoted to curing theism, has challenged YouTubers to post videos of themselves denying the existence of the Holy Spirit and thereby — in the group’s reading of Mark 3:29 — damn themselves for eternity. More than 1,200 people have posted blasphemy videos as of this writing. In each one, a single person speaks the line, “I deny the Holy Spirit.” Sometimes he or she adds more: a name, a speech, a further denial of Easter Bunny-like entities. Some blasphemers are jaunty, some are insolent, some are scary, some are nervous. But all of them (young and old, mostly English-speakers, but with a range of accents and ethnicities) seem to believe they are making a statement of some gravitas — issuing a reproof to doctrine, possibly risking their salvation. On the face of each participant is both a wonderful purity of purpose — the mandate is so simple, the one-line script so unforgettable — and a clear vulnerability. Will anyone regret taking the so-called Blasphemy Challenge? If so, can they retract their videos? 5. FAT RANTS Joy Nash became this spring’s latest YouTube star for her Fat Rant, in which she flaunted her plus size, bashed retail chains for not stocking XXL and ran down her fellow Americans for their hypocrisy about weight. Ms. Nash performed much of this rant in various costumes with a high-spirited stage manner that suggested self-confidence, humor and a refined sense of glamour. Ms. Nash, who gave her weight at 224 pounds, said that she ate what she wanted, watched her health and had stopped considering her weight the prime mover of every event in her life. YouTubers loved it. Watch “A Fat Rant” these days and thumbnail images from response videos run down the middle of the page. A typical one is called YES!!!!!!!!!!! Unlike the glossily produced original, the responses to “A Fat Rant” are ad-libbed solo soundoffs with minimal stagecraft. They are new fat rants, then, delivered by Ms. Nashs fans and semi-fans, people with equally piquant opinions about obesity, appearance and American doublespeak about weight. Though each video pretends to particular clarity to on the subject, many run into versions of the same conundrum: being fat is O.K., except when its unhealthy. But when is that, again? And should fat people try to be skinny? Or be happy with how they are? The video responders are less ideologically resolute than Ms. Nash, with some resolving to diet; still others manage to outdo Ms. Nash in fat-power-speak. In general, the video-responders are profoundly moved by “A Fat Rant,” and take Ms. Nash’s video as an occasion, paradoxically, to expose their bodies, as if inviting comment. This being YouTube, with its emphasis on responses, both taunts and catcalls arrive, ready for worldwide consumption, right on cue. http://www.nytimes.com/2007/05/27/ar...on/27heff.html  Pretty Faces With Plenty of Troubles, and Secrets Ginia Bellafante “Hidden Palms,” the new series from Kevin Williamson making its debut tonight on CW, may be the first teenage soap opera visually dedicated to mid-20th-century Modernism. Remove the sex, sociopathology and possible filicide, and you will still be left with a quite inspiring home design show. Set in Palm Springs, the last patch of Southern California this genre hasn’t yet trammeled, the look is all Eames benches, Barcelona chairs and geometric patterns. The mood is severe, but the colors are happy. Mr. Williamson has created a sick world, but one for which you wouldn’t mind having the swatches. The clichéd aesthetic choice of so many single art directors, midcentury Modern isn’t necessarily the easiest signifier of typical American family life, and that is precisely the point. The families on “Hidden Palms” don’t convene at the table or watch movies together or talk about SAT scores or college admissions. The show is set during the summer, but still there is no evidence that any of the 17-year-olds in it actually go to school. What kind of people decide to bring up children in Palm Springs anyway? As the resident satanic charmer explains to the newcomer in town, “It’s all retired grays, gays and streets named after dead people,” he says. “People come here to die.” The charmer is a high school junior named Cliff Wiatt, played by Michael Cassidy, an actor so good at conveying sham authenticity that even when he sniffs, it doesn’t quite feel as if he means it. His mission is to keep at bay the new arrival, the economically named Johnny Miller (Taylor Handley, who, like Mr. Cassidy, is a veteran of “The OC.”) Johnny begins to suspect that Cliff might have had a hand in the death of Eddie, a teenager who once lived in Johnny’s new house. And it isn’t as if Johnny doesn’t have a whole big pasta bowl of problems already. In another life he wore crew-neck sweaters and his hair neatly combed back. He cared about math and lived someplace where it rained. But then his sweaty, gin-drinking father killed himself, sending Johnny down the road to addiction, then rehab, then unbuttoned shirts and a coiffure in the mode of Jarvis Cocker. “Hidden Palms” is high soap opera, a kind of “Masterpiece Theater” of unjustifiable television, which means that there won’t be anything quite so much fun to watch all summer. It takes its suspense seriously. It doesn’t tease your attentions so much as kidnap them, with many of the tropes of Mr. Williamson’s auteurism: the love triangles, suspicious deaths, bloody Halloween costumes and nods to gag horror. For the uninitiated, Mr. Williamson created the “Scream” films and “Dawson’s Creek,” and “Hidden Palms” seems the inevitable hybrid of his opposing impulses toward satire and sincerity. “How does it look?” Cliff’s mother asks him when he’s removing the bandages from her plastic surgery. “It’s bruised,” he responds. “But it looks like the noses two noses ago.” If I were watching “Hidden Palms” as a 16-year-old, I’d be grateful for whatever parents nature gave me, their refusal to let me drive the Jeep Cherokee be damned. It is hard to think of another television show of this kind that has portrayed mothers and fathers so perversely. Ultimately, “Hidden Palms” derives its creepy tension from the question of how morally debased the show’s parents will actually prove themselves to be. At best they are dangerously attached or uncommunicative; at worst, criminal, lecherous and pedophilic. It is a good thing, then, that they haven’t aggressively reproduced. The show is certainly true to the demographic realities of Palm Springs: not a single one of the young people appears to have a sibling. In some sense, “Hidden Palms” marks a radical departure in popular culture’s depiction of only children, who for the better part of the last two decades have been depicted as self-reliant superstars or geniuses (Harry Potter, Buffy the Vampire Slayer, Rory Gilmore.) The teenagers on “Hidden Palms” make a strong case for benighted arguments that only children are socially maladjusted, neurotic, disturbed. It seems fairly certain that “Hidden Palms” received no subsidies from the Population Council. HIDDEN PALMS CW, tonight at 8, Eastern and Pacific times; 7, Central time. Kevin Williamson and Scott Winant, executive producers. A Lionsgate Televison production in association with Outerbanks Entertainment. WITH: Taylor Handley (Johnny Miller), Gail O’Grady (Karen Hardy), Sharon Lawrence (Tess Wiatt), D. W. Moffett (Bob Hardy), Amber Heard (Greta Matthews), Michael Cassidy (Cliff Wiatt), Ellary Porterfield (Liza Witter), Tessa Thompson (Nikki Barnes) and J. R. Cacia (Travis). http://www.nytimes.com/2007/05/30/ar...on/30bell.html  For Lohan, a Cocktail of Sympathy and Scorn Sharon Waxman It’s already fairly clear which image of Lindsay Lohan will be most indelible in the summer of 2007, and it’s not a promotional still from her new movie, “Georgia Rule.” Instead it’s a paparazzi photograph of this flame-haired actress passed out in a car in the wee hours of Sunday morning, sprawled across the passenger seat, her hair peeking out from a gray hooded sweatshirt, her mouth slack-jawed. That image shouted from the cover of tabloid newspapers on Monday as if to herald the umpteenth public wipeout for the 20-year-old actress, who was arrested here Saturday for driving under the influence after she crashed her Mercedes into a tree along the residential strip of Sunset Boulevard. On Monday she checked into a Malibu rehabilitation facility called Promises. And quick as a shot (no, not that kind), all of Hollywood was a-clatter with the sound of clucking tongues over advice not taken. So sad, everyone said, such a waste: so pretty, so talented — so uninsurable. Like Britney Spears before her, and Marilyn Monroe too, the spectacle of a young woman’s self-destruction seemed to demand expressions of sympathy along with the requisite scorn. But hard reality was also quickly setting in. Across this close-knit town, decision makers were mentally wiping Ms. Lohan from their short lists. One studio chief who has worked with Ms. Lohan said that he would not hire her until she proved herself healthy and reliable. (Confident at least of this possibility, he would only comment anonymously.) “My hope for her would be that her growing pains get sorted out,” said Valerie Van Galder, president for marketing for Columbia Tristar. “The wild child used to be a phase you grew out of. This feels different. I think now there’s more attention to minutiae, and you’re stalked everywhere you go.” To be hired again, some said, Ms. Lohan might have to be more than sober. She would need perhaps to post her salary as bond, or pay for her own insurance, even on an independent film. Ms. Lohan was meant to start a new movie this week, an independent production titled “Poor Things,” about two female con artists, also starring Shirley MacLaine. The film’s producers met on Wednesday to decide whether to replace Ms. Lohan or hold off while she spent a month under wraps. Many could say they saw this coming. Ms. Lohan has already worn out her welcome at Disney, where she made four films, including the hits “Parent Trap,” when she was a precocious 11-year-old, and “Freaky Friday,” in 2003, in which she played a thoroughly credible middle-aged mom. But by the time she starred in “Herbie: Fully Loaded,” in 2005, she was already a paparazzi fixture, and Disney was worried enough to sit her down for a talking-to. “I told her before the movie began, ‘This is the moment in your career where you either become Kristy McNichol or Jodie Foster,” recalled Nina Jacobson, who ran the studio at the time and is now a producer at DreamWorks. And while filming went fine, Ms. Lohan went missing during the international press junket in Europe. “The image issue aside, professionalism-wise we were disappointed,” Ms. Jacobson said. “And I was sad, because she’s so charismatic and appealing on screen. It’s a very sad thing to see it go to waste this way.” Those in Ms. Lohan’s camp find all this hand wringing to be disingenuous. One person close to Ms. Lohan pointed out that Disney handed the actress a $1 million bonus check for “Freaky Friday,” an invitation for her , then a 16-year-old, to indulge irresponsible impulses. And James G. Robinson, a producer of “Georgia Rule” who had a letter sent to Ms. Lohan at her Chateau Marmont hotel room last year calling her “a spoiled child” for failing to show up for her scheduled call times (the letter was conveniently leaked to the news media even as it was delivered), later invited the actress to be his date to a George Clooney tribute. At Sony the hope was that Ms. Lohan would right herself, and soon. The studio has a thriller starring Ms. Lohan, “I Know Who Killed Me,” out in late July. Ms. Lohan’s publicist, Leslie Sloane-Zelnick, said her client intended to do the publicity for the film, but admitted that things were in limbo. “She will work for that film, she wants to work for that film,” Ms. Sloane-Zelnick said. “But we’re waiting on her situation, in general. At the end of the day, her talent will prevail. Someone will take a chance on her.” http://www.nytimes.com/2007/05/31/movies/31loha.html  Grade-School Girls, Grown-Up Gossip Stephanie Rosenbloom  WHEN Britney Spears shaved off her signature blond locks, Alexis Gursky, 9, found herself wondering not why Ms. Spears picked up a razor in the first place, but why she did not do more with the hair she shaved off. “I just thought it was a little weird to just do it and not to give it to people who have cancer,” said Alexis, a third grader in Manhattan. And while scores of people were petitioning Gov. Arnold Schwarzenegger of California to keep Paris Hilton from having to report to jail on June 5, Jessie Urvater, 8, could not muster any sympathy. “I don’t like Paris,” said Jessie, of Manhattan, who was quick to point out that hotel heiresses are not above the law. “I think she should go to jail.” Well before they experience puberty, children today are deeply immersed in the dirty laundry of celebrities — their eating disorders, bouts with drinking and drugs, and run-ins with the law (and one another). The gritty details are all around them: on the Web, on cable, at the top of the network news and splashed across the covers of magazines. The prevailing wisdom is that exposure to vast amounts of gossip, particularly about Hollywood’s so-called bad girls — Ms. Hilton, Ms. Spears and Lindsay Lohan, to name the most frequently chastised — is leading America’s impressionable 8-to-12-year-old girls into the gutter. But the reality is more complex. In interviews, tweens tend to be highly judgmental of the much-publicized antics, turning them into age-appropriate morality tales that would make their parents proud and bring comfort to those who fear the next generation will be made up of pantyless party girls known more for their D.W.I.s than their G.P.A.s. Ms. Hilton, said Jamie Barton, 10, of Mobile, Ala.: “spends all this time acting like everyone else doesn’t mean anything. It’s just me, me, me.” Said Diamond Martin, 12, of Parlin, N.J.: “I don’t see her as a role model. I’m not sure what she’s really ever done, actually.” That tweens are not traipsing after the drunken pied pipers who erupt in the gossip headlines is not surprising to child behavior experts. “I would be shocked if they did,” said Dr. Ritch C. Savin-Williams, a professor and chairman of the human development department at Cornell University. After all, he said, 8- to 12-year-olds are by and large “really heavily under the influence of their parents.” That does not mean, though, that gossip culture is harmless. “There may be a delayed effect,” said Dr. Richard Gallagher, the director of the Parenting Institute at the Child Study Center of New York University. “When kids know that some behavior is possible and that it doesn’t lead to total ruination of your life, they may, as they get older, be willing to entertain that.” But until then, many children view the unseemly behavior through a lens of common sense that some celebrities themselves appear to lack. “They should really do good things that they want other people to do,” said Rachel Steir, 11, of Manhattan, “not smoking, taking drugs, thinking that they need to lose so much weight.” That children today are exposed to much more scandal than those of previous generations is not in dispute. Like many girls, Courtney Barton, 12, of Mobile, Ala., said she does not seek out celebrity gossip, but encounters it everywhere: “I hear these things about all of them on the radio, Internet and TV.” According to the Pew Research Center for the People and the Press, the death of Anna Nicole Smith, on Feb. 8, constituted 9 percent of news coverage the week she died (she died midweek). That same week, 8 percent was devoted to the 2008 campaign and 3 percent to the Super Bowl. Pew also found that in the two days following Ms. Smith’s death, “nearly a quarter of the news from all sectors (24 percent) was devoted to this story, and fully half of cable news.” Of course, Ms. Smith’s accidental drug overdose is old news by now. Children have moved on to Us magazine, where they can read about Ms. Lohan reportedly snorting cocaine, or to People.com, where they are informed that the estranged husband of Anne Heche, the actress, “craves porn, poker and money.” Gone are the days when children who wanted to learn the meaning of a naughty word or slang term had to find a dictionary or a more worldly pal. Today, Wikipedia can explain in a matter of seconds that badonkadonk is a term for a woman’s buttocks. Michelle Dale, a second-grade teacher in Brooklyn who works with the youngest of the tweens, said she is “always blown away” by all the things her students know about. “The movies that these little second graders have come in and watched,” she said, “I’m like, ‘Oh, my goodness.’ ” In interviews, children expressed their detailed knowledge of Angelina Jolie’s penchant for adoption (though they never mentioned her previous marriage to Billy Bob Thornton or the vial of his blood she wore around her neck). They knew about Ms. Hilton’s sex tape, Ms. Lohan’s dramatic weight loss and Ms. Spears’s underwear-free club outing. Saturated with such gossip, they had formed some very strong opinions about what is good, bad and just plain weird. Caroline Lee, 11, of Greenwich, Conn., pointed out Ms. Spears’s public parenting blunders, including driving with a baby in her lap: “I feel kind of like she’s a little young and she’s not the right kind of mom,” Caroline said. But Ms. Jolie, Caroline said, is “a good mother. She takes care of her kids.” “She’s not as strange and bad as Britney and Paris and Lindsay,” she said, adding that “she adopted so many kids and she also helped places that needed help.” Of Ms. Lohan, Sophia Ambrosino, 12 , of Manhattan, lamented the passing of the young actress’s red-haired, reproach-free “Parent Trap” days. Now, she said: “There are things that she does just to be on the cover of something. I liked her when she was little.” Arielle Urvater, 11, also said while once she was a fan of Ms. Lohan and Ms. Spears, she is no longer. “We’re well educated,” she said. “We know that drugs aren’t good and that smoking isn’t good.” Tweens often think in moralistic terms, especially if they have a solid family support system or role models, Dr. Savin-Williams said. But around 12 or 13, it is not unusual for a child’s individual values to give way to peer pressure, some child experts said, and children may be influenced by what they perceive to be cool, not what they instinctively know to be right. “The younger kids are a little freaked out by Paris,” said Susan Schulz, editor in chief of CosmoGirl. “For the most part they’re still very good kids at that age.” But, said Ms. Schulz, when they are teenagers, “every kid is trying to have a Paris Hilton kind of night at their prom.” And that is exactly what some adults fear. “I don’t think there’s any question that kids are getting more and more information at a younger and younger age,” said Dr. David Walsh, a psychologist and the founder of the National Institute on Media and the Family. “And there are very few filters available.” The result, he said, is the “adultification of youth.” “Kids have information but not necessarily the emotional maturity to absorb the information,” he said. “We’ve got kids who are at the simple arithmetic phase in terms of their emotional maturity dealing with quadratic material.” Dr. Gallagher of N.Y.U. suggested parents discuss celebrity misbehavior with their children. “You have to talk about it before someone else does,” he said. “That helps the kids digest it more effectively.” Most of those conversations will likely be with and about girls. “The bad boys have been replaced by the bad girls,” said Ted Harbert, the president and chief executive of the Comcast Entertainment Group, which includes E! Entertainment Television, Style Network and G4. “You just don’t hear as much of these guys who get in trouble as much as we used to in the ‘St. Elmo’s Fire’ generation.” “The girls don’t want to just leave it to the boys to get in trouble,” he said. “They want their fair share of time in the principal’s office.” But what about all those thoughtful things tweens say about celebrities’ bad behavior and their embrace of good clean role models? Dr. Walsh said: “A kid can write a well-thought-out essay about why a behavior is not good, but that doesn’t mean it’s going to carry over to their behavior. Thinking ability is right on track but emotionally ability lags.” Yet the girls interviewed cited wholesome-seeming celebrities as their favorites: Miley Cyrus, Ashley Tisdale, Hilary Duff, Dakota Fanning, Anne Hathaway and Ms. Spears’s younger, scrubbed sister, Jamie Lynn. Is it possible that today’s tweens have seen enough to inoculate them against the pressures of their teenage years? “As I grow older I see more and more how bad they are,” Arielle Urvater said. And yet kids her age cannot help but be interested, she said. “They’re famous, pretty and all the boys like them.” http://www.nytimes.com/2007/05/27/fashion/27gossip.html  OMG! Cute Boys, Kissing Tips and Lots of Pics, as Magazines Find a Niche Elizabeth Olson Above the neon-orange lettering that promotes the issue’s “love blogs” and other content, Zac, Corbin and Miley smile winningly on the cover for the May/June issue of J-14. No need for the preteen magazine to spell out that they are Zac Efron, Corbin Bleu and Miley Cyrus because its devoted readership already knows this from watching the Disney Channel. Disney and Nickelodeon have been pumping out youthful stars whose careers, outfits and “faves” are dissected by every issue of J-14 and its brethren, which include Twist, M, Tiger Beat, Bop and Popstar. With a faithful audience in the millions, these magazines for the early teenage years are in overdrive, bolstered by last year’s enthusiasm for new stars from the Disney Channel’s hit “High School Musical,” which made household names not only of Zac Efron and Corbin Bleu, but also of Ashley Tisdale and Vanessa Anne Hudgens. Miley Cyrus, the daughter of the singer Billy Ray Cyrus, is the star of the Disney series “Hannah Montana.” Some tween magazines say they have seen circulation rise by as much as 25 percent on the strength of “High School Musical,” and another increase in demand is coming soon. “High School Musical 2” is scheduled to begin in August, and is eagerly being awaited by the flavored lip gloss and fuzzy pencil set. “It’s the synergy,” said Molly MacDermot, the editor in chief of Twist and M, which along with J-14 are published by privately owned Bauer Publishing. “It’s ‘High School Musical’ and what continues from it that drives the interest. For example, Corbin Bleu stars in the musical, then he comes out with a music album and then a video. So the interest is sustained. “And it really hits these girls on an emotional level,” she said of her readers, who are nearly all female and younger than 15. After the boy bands from the 1990s like ’N Sync and the Backstreet Boys grew up, the tween fan magazines saw some drop in readership. But the genre — which commands impressive shelf space on newsstands and in checkout aisles — seems to have made a strong comeback, which contrasts with the retrenchment at more mainstream titles like TeenPeople, YM and ElleGirl. None of those magazines are still in print. For girls from 8 and 14, J-14 and M are two of the country’s best-read magazines, according to an annual survey by Experian Simmons Research of Fort Lauderdale, Fla. Last year’s survey found that J-14 tied with Nickelodeon magazine, with 32 percent of preteens reading or looking at each magazine and 30 percent reading or looking at M magazine. Nickelodeon has elements of a fan magazine, but also runs features and comics related to shows on the network, like SpongeBob SquarePants. “I love reading about celebrities that are my age,” said Mallory D. Levy, 15, of Boynton Beach, Fla., a Popstar subscriber for four years. She said that she takes four or five such magazines to school every day. But the Paris Hiltons of celebrityville do not regularly appear in these fan magazines. Nor do Britney Spears or Lindsay Lohan now that they have exhibited less-than-exemplary behavior. “Our content is 100 percent positive,” explained Matthew Rettenmund, the editor in chief of Popstar, published by Leisure Publishing. “We do not pick apart girls’ appearances and clothing choices,” he said. “We do not make fun of stars who are out of favor. We believe in keeping kids kids.” Mr. Rettenmund said that Popstar, which began publishing in 1998, experienced a 25 percent rise in audited circulation to 217,183 an issue last year, helped by the “High School Musical” craze. The magazine expects to top 300,000 readers for each of its monthly summer issues. Ms. MacDermot of Twist said that her magazine also is expecting a big circulation uptick this summer because of “High School Musical 2,” the new Harry Potter book and movie, and the latest sequel to “Pirates of the Caribbean.” Twist, Popstar and their counterparts have been closely tracking the activities of the six “High School Musical” actors as well as Miley Cyrus, who plans to release her first CD in June. The universe of stars the magazines cover is somewhat larger — it includes singers like Avril Lavigne and the “American Idol” finalists — but largely dominated by people who made their names in television, like Hilary Duff (formerly of “Lizzie McGuire”). As stars like Ms. Duff graduate to more adult markets, younger performers hit adolescence and turn into heartthrobs. Two of the latest are the twins Dylan and Cole Sprouse, who star on Disney’s “The Suite Life of Zack and Cody” and have become usual suspects on the magazine covers. Their show, which has the brothers living in a fancy hotel in Boston, gave Ashley Tisdale of “High School Musical” her start. Nickelodeon Channel has its hits like “Unfabulous,” “Drake and Josh” and “Zoey 101,” but the Disney juggernaut is a prime driver of the current crush on the young stars. Disney invites the magazines to visit movie sets and gives them access for interviews, photo shoots and brief videos that the magazines post on their Web sites. The magazines say that they are attracting readers by posting celebrity videos on social networking sites. Some of the publications, like J-14, have sites on MySpace; Twist and others keep their own Web sites fresh with daily quizzes, games and sweepstakes. Ms. MacDermot said that she receives instant feedback from blogging. Like competing publications, Twist posts videos on MySpace from “interviews with stars, from photo shoots or wherever the stars sit down with us.” Several magazines, including Popstar, also are on YouTube, with videos, Mr. Rettenmund said, “that are short, but they get our name out there.” Even with television, computers and iPods competing for their time, tweens are still reading magazines because they “tell them what’s hot, give them fashion looks and tell them stories,” said Jane Buckingham, the president of the Intelligence Group, a market research firm based in New York that tracks the age group. “And portability is important,” said Michael Wood, a vice president of TRU, a market research group in Northbrook, Ill. “You can throw a magazine in a backpack, take it on the bus, pull it out in study hall and share it anywhere with your friends.” Still, it is not all unalloyed sweetness on the teenager magazine scene. Longstanding magazines like TeenPeople, YM and ElleGirl pulled the plug on their print editions in the last two years. TeenPeople, which Time Inc. began in 1998, ended its print version last summer, and, like YM and ElleGirl, went solely online. TeenPeople’s electronic effort was merged on April 26 into People.com. The print version of TeenPeople, part of the 1990s wave of teenage magazine start-ups, had a slip in circulation with the arrival of entertainment weeklies, because readers did not have to wait a month to find out the latest doings of Ms. Spears or ’N Sync. Mark Golin, the editor of People.com, said that the larger site drew more traffic so “why duplicate efforts?” Magazines for early teenagers rely overwhelmingly on newsstand sales, and their $2.99 or $3.49 price makes them an easy impulse buy. According to Mediamark Research Inc.’s annual readership survey of youths from 12 to 19, called MRI Teenmark 2006, there were 22.7 million readers of J-14 last year along with 17 million readers of M and almost 9 million readers of Twist, all of which are published by Bauer Publishing. Bauer, which is based in New York, said its 2006 revenues were $13.7 million, compared with $11.9 million in 2005. Privately held Leisure Publishing and Laufer Media of Glendale, Calif., publisher of Tiger Beat and Bop, do not disclose revenues. With the advent of MySpace and celebrity gossip sites like tmz.com, and the shift of advertising spending from video-game makers and cosmetic companies to the Internet and away from magazines, analysts say teenager magazines face new challenges. “Gossip is available online immediately,” said Barry Parr, an analyst at of Jupiter Research, which surveys teenage Internet usage. “It makes you wonder about the long-term viability of some of these magazines.” Tinkering with the tween formula can be a tricky business, as the popular Sprouse twins discovered last summer. A new magazine aimed at boys in the preteen age group — the Sprouse Bros. Code — closed after the first issue. “Tween boys are a totally separate audience,” said Mr. Rettenmund of Popstar, who oversaw the test magazine. http://www.nytimes.com/2007/05/28/bu...28fanzine.html  The Lost Beach Boy Band's original member tells his side of story Robert Miller David Marks was one of the first Beach Boys and was instrumental in developing their early sound. A book has been written about his years with the group. For two years, David Marks got to ride on the rock 'n' roll express. He was present at the creation of the Beach Boys, playing and singing on their first slew of surf-and-muscle-car hits -- everything from "Surfin' USA" to "Little Deuce Coupe" and "Fun, Fun, Fun." At their best, they were as good -- and as American -- a rock band as the country has ever produced. Because he was so young when he got off the ride -- all of 15 years old -- he admits he didn't always understand what it meant or that those heady days would never come again. For a long time, he denied it even mattered. "I spent 30 years or more disassociating myself from the Beach Boys so I could make it on my own," Marks, 58, said at his home in North Salem, N.Y. "But one day, I realized I'd never get away from it. I decided to embrace it." Embracing doesn't mean just retelling the old stories that surround the band. In his new book "The Lost Beach Boy" written with Jon Stebbins -- to be released by Virgin Press Tuesday -- Marks talks at great length about how the group actually came to be. "It's the most truthful account of the early days of the band that's ever been written," said Stebbins, who has written extensively about the Beach Boys. "You get a really good sense of the of the band." But the book also clears away some of the junky myths that surround the group, including the tale that the three Wilson brothers rented instruments on vacation and, somehow, miraculously came up with the Beach Boys sound. It also establishes Marks as one of the founders of the group -- the kid who started trading twangy electric guitar licks with Carl Wilson when they were still in grade school. It also tries to tells how Murry Wilson, the Wilsons' domineering father and business manager, played an instrumental part in getting Marks to leave the band, to cut him out of the band's profits, and then successfully misled the press about the part Marks played with the band. Hence the book's name. Murry Wilson's influence lives on. In the Rock and Roll Hall of Fame's synopsis of the Beach Boys' history, Marks is mentioned once in a parenthesis, as a temporary replacement for band member Al Jardine. "Murry did a really good PR job," Stebbins said. "He wanted to slam the door shut on Dave and he did." But, in fact, it was Jardine who left the band for two years, from 1961 to 1963, to go to college. When he returned, there were six Beach Boys -- five who toured, including Marks, and Brian Wilson, the group's leader, songwriter, arranger and all-round genius, who stayed home and wrote the song book. Both Marks and Stebbins said that Brian Wilson's current persona -- as a troubled, drug-addled, somewhat reclusive artist -- bears little relationship to the Brian Wilson of the early 1960s. "He was a normal kid," Marks said. "He was bright and focused and very interesting. He organized us, and sometimes bullied us. But he got a bunch of unruly kids to perform our music." "Brian was totally the leader -- everybody wanted to be around him," Stebbins said. "But he had stage fright. He was very funny and charming, but that all melted away when he got before a crowd." What's so remarkable about the Beach Boys was how young they were. When they started, Mike Love, the oldest member of the band and the man who now owns the rights to tour as the Beach Boys, was just 21. The rest were in their teens. Marks was 13. "We had no idea what was happening," he said. "I was old enough to know we were popular. But I was too young to understand that being a Beach Boy would be a big business deal and that the band would be worth millions." Marks actually started playing electric guitars with next-door neighbor Carl Wilson around 1958. Their idols were Chuck Berry, Richie Valens and instrumental surf bands like the Ventures and Dick Dale and the Deltones. While Brian Wilson was already thinking of a group with tight vocal harmonies, his first attempts to create a group were more like folk music. "Brian got interested in what we were doing, and that was what did it -- the combination of electric guitars and Four Freshmen harmonies," Marks said. "How much did Dave contribute to the Beach Boys sound? Five percent? Ten percent? Twenty percent?" Stebbins asked. "I don't know. But he was there." While the surfing songs put the Beach Boys on the top of charts, Marks said it was the car songs -- "409,""Shut Down,""Little Deuce Coupe" -- that really made them a great American band. "Surfing was a coast thing," he said. "But every little town in the United States had kids with cars. I think the car songs are what really took the Beach Boys to the top of the country." But Marks said there was little glamour to the band's early days of touring. "There were no groupies, no four-star hotels, no limos." Added to that was Murry Wilson's animosity toward Marks -- in large part, Marks said, because Wilson wanted to confine the band's fortunes to the Wilson family (the three Wilson brothers and Mike Love, their cousin). "He knew how to push all my teenage buttons," Marks said. In 1964, at age 15, after two years of playing rhythm guitar, singing background harmonies and getting harassed by Murry Wilson, he quit. "I was a 15-year-old punk," he said of his heedless, arrogant youth. When Marks signed his original contract with Capitol Records, it made him a one-fifth partner in the band until 1967, getting 20 percent of the proceeds. When he quit, Murry Wilson had him sign away his future royalties to the band he helped created. Marks gets royalties on the songs from the Beach Boys' first four albums. But between 1964 and 1967 -- using hired studio musicians to play and sing Marks' parts -- they recorded 14 more albums, with many, many more hits He's estimated that if he had kept his 20 percent rights, those songs would have earned him $10 million over the years. "Murry gave me a piece of paper to sign," he said of his leaving. "What I didn't know was that a 15-year-old's signature isn't legally binding. It was totally bogus." After the Beach Boys, Marks started his own band -- Dave and the Marksmen -- which played, he said, "a bizarre combination of British invasion and surf music." Although the band signed with a major label, A&M, it went nowhere. Instead of becoming a teen star, Marks became a highly respected, albeit anonymous, guitarist in the Los Angeles studio scene. He played with other groups -- The Moon and Dot -- and toured with disc jockey Casey Kasem. He became a full-time father, raising daughter Jennifer alone when the girl's mother left him. Along the way, he got the Beach Boys organization to pay him royalties on hit records he performed on. He never saw his one-fifth share. He kept in touch with the band members and finally rejoined Mike Love's touring Beach Boys band from 1997 to 1999 at Love's urging. It was on on tour with the band that he met his wife, Carrie. Because her family lived in North Salem, the couple decided to settle there. Marks has recorded CDs of his own music. He performs regularly with the Surf City All-Stars, along with former Beach Boys member Al Jardine and Dean Torrence of Jan & Dean fame. That's forced him to relearn a lot of the Beach Boys' repertoire and made him more aware than ever of the verve and complexity of Brian Wilson's songs. He's become an outspoken advocate of better care and research for people with hepatitis C -- the chronic liver disease Marks was diagnosed with in 1999. After treatment in 2004, he's now virus-free. He looks back on his two years of fame with a certain amount of philosophical rue. "All I can say today is 'Oh, nuts,'" Marks said of the lost fame and money. "But I have a beautiful wife, a beautiful daughter and a great life. All I can do is look back and be grateful." When he's on tour, he gets a full appreciation of what the Beach Boys' music still means to people. "I've played in Germany and New Zealand before crowds of 150,000 people," Marks said. "I've had people come up and tell me they sang their babies to sleep with 'Surfer Girl.' "I had no idea that the music would sustain itself and still be so popular. It's universal, from generation to generation. "That's one of the things I've learned -- what it means to be part of something that big. It's mind-blowing." http://www.newstimeslive.com/news/st...&source=tabbox  Will ISPs Spoil the Online Video Party? Steve O'Hear With an ever greater amount of video being consumed online, many Internet users are in for a shock. There’s a dirty little secret in the broadband industry: Internet Service Providers (ISPs) don’t have the capacity to deliver the bandwidth that they claim to offer. One way ISPs attempt to conceal this problem is to place a cap of say 1GB per-month per user, something which is common in the UK for many of the lower-cost broadband packages on the market. Considering that a mere three hours viewing of Joost (the new online video service from the founders of Skype — see our review) would all but use up this monthly allowance, it’s clear that lots of Internet users aren’t invited to the party. But what about those who (like me) pay more for ‘unlimited’ broadband access? There shouldn’t be a problem, right? Wrong. Unlimited doesn’t always mean unlimited, as many ISPs impose a ‘fair use’ policy which masks a monthly cap. Others employ bandwidth throttling, where under certain circumstances download speeds are reduced significantly. The intent, the ISPs claim, is to stop users who exhibit ‘abnormal’ behavior — industry-speak for accessing illegal peer-to-peer file sharing networks — from degrading the service at the expense of others. Even if we take ISPs at their word, and presume they’re not being disingenuous in the reasons given for bandwidth throttling, it’s becoming increasingly difficult to distinguish between illegal and legitimate use of peer-to-peer technology — particularly when it comes to online video. Last week, in an article titled ‘Channel 4’s 4oD hamstrung by UK ISPs‘, CNet reported on the problems faced by the UK television channel’s new on-demand video service, which, along with Joost (and a number of other services), uses peer-to-peer technology similar to that used by ‘illegal’ file sharing networks. In an attempt to restrict how much illegal sharing can be done on their network, ISPs use a technique called ‘packet shaping’. Packet shaping examines what you’re downloading — or more specifically, how you’re downloading — and restricts your download speed by up to 500 per cent… The problem is that packet shaping technology can’t easily tell the difference between different kinds of peer-to-peer traffic. … if you’re planning on using Channel 4’s 4oD service to download your favorite shows while you travel home from work, make sure you’re not on an ISP that treats you like dirty rotten thieving scum. Video on-demand is the way of the future, so it’s important that legitimate, efficient technology can make it happen. A recent new policy introduced by my ISP, UK cable company Virgin Media (previously NTL/Telewest), goes one step further. Instead of trying to distinguish between different kinds of traffic, throttling is employed during peak times (between 4pm and midnight) for individual users after they’ve consumed a set amount of bandwidth. So for example, customers paying for the top package (approx. $70 per month) will see their download speeds halved — from 10Mb/s to 5Mb/s — after they’ve consumed just 3GB. Which, The Register notes, could theoretically take as little as 20 minutes. Overall, things are likely to get worse before they get better (while we wait for Telcos or companies like Google to build out the next-generation networks). In the meantime, there’s nothing like the online video revolution to reignite the net neutrality debate. http://www.last100.com/2007/05/28/wi...e-video-party/  Apple’s Lesson for Sony’s Stores: Just Connect Randall Stross RETAIL is supposed to be hard. Apple has made it seem ridiculously easy. And yet it must be harder than it appears, or why hasn’t the Windows side of the personal computer business figured it out? Of the many predictions in the world of technology that have turned out to be spectacularly wrong, a prominent place should be made for what the pundits said in 2001 when Apple opened its first retail store in Tysons Corner, Va. “It’s completely flawed,” one analyst said, and that was the conventional wisdom. Commercial rent and furnishings would be expensive, inventory tricky and margins slim. Experienced computer resellers were struggling, and no computer manufacturer had ever found success operating its own branded stores. Analysts predicted at the time that Apple would shut down the stores and write off the huge losses in two years. That assuredly would have been the Apple store’s fate had Steve Jobs permitted aesthetic and design considerations to trump all else. But while guiding the planning for the stores in 2000 and 2001, Mr. Jobs took on a more ambitious challenge than building freestanding museums of design that would show the Apple flag and do little else. He set out to create the conditions most likely to convert museum visitors into actual customers, and then to make those customers feel that they were being pampered long after the sale was consummated. At the time, retail stores seemed passé. Gateway Country Stores were trying to make a go of a combination of old and new, inviting customers to come in, touch, order — and then go home and wait patiently, because the stores did not carry any inventory. Dell’s build-on-demand model dispensed with stores altogether and seemed to embody the future. Mr. Jobs understood, however, that his stores would sell not merely products but also gratification. He told the trade magazine Chain Store Age Executive in 2001: “When I bring something home to the kids, I want to get the smile. I don’t want the U.P.S. guy to get the smile.” The stores were born fully formed and have not required any fundamental changes. The best innovation was present on Day One: the “Genius Bar,” with a staff of diagnostic wizards whose expertise is available in one-on-one consultations — free. Pure genius. More than half of the retail store’s staff is assigned to post-sales service. Customer response is told in the numbers. Last month, Apple released results for the quarter ended March 31. More than 21.5 million people visited its stores, which now number more than 180. Store sales were $855 million, up 34 percent from the quarter a year earlier, and they contributed more than $200 million in profits. For perspective, look at the parallel story of Sony, which in 2004 began its attempt to create a branded retail chain. That was the same year Gateway closed the remnants of its 188-store chain. Today, Sony has 39 Sony Style stores, built out from the flagship stores in New York and San Francisco. The company’s breadth of product lines in consumer electronics and related accessories, as well as computers, would seem to give it a significant advantage over Apple. But because Sony does not release data on the stores’ sales or profits, it is hard to assess how its retail venture is doing. Last Sunday, I set out to have a look for myself. I began at Sony’s flagship in San Francisco, at the Metreon Center, the shopping and entertainment complex. The mall was crowded, but Sony’s store, measuring an enormous 20,000 square feet, was all but deserted. The two uniformed members of the store security staff matched the number of customers I could see browsing the store’s wares. Then I headed for the Stanford Shopping Center in Palo Alto, where I could see a Sony Style store compete almost directly across from an Apple retail store. The weather was gorgeous, drawing the usual weekend throng to the shopping center. Sony’s mall store was long and large — 6,000 square feet — and filled with curvy panels and chirpy taglines like “My Style” on the walls and plush theater nooks. Here, too, the sales staff seemed to outnumber customers. A group of five young salesmen and saleswomen who stood near the door when I entered were so engaged in a private, and apparently amusing, discussion that my imploring presence failed to draw anyone’s attention. The only other customers in the store were at the far other end, near the PlayStations. I suppose that the employees near me had become accustomed to busying themselves with their own entertainments. A few yards away was the Apple store, which is one of Apple’s newer “mini” stores, introduced in 2004 and only about an eighth the size of Sony’s Stanford store. It was simplicity itself: a rectangular space with products lining the two sides, laptops placed on a small table, open space taking up most of the room, and, of course, the Genius Bar. The store was packed, yet the sales people were alert and attentive. Last week, I shared these impressions with Dennis Syracuse, senior vice president for Sony Retail, who assured me that Sony’s stores drew an average of 350,000 visitors annually per store. Mr. Syracuse rejected the idea that his store concept could be compared to Apple’s. His stores were conceived, he said, as a “fashion boutique for women and children” that incidentally happened to carry electronics instead of clothing. When describing how Sony had entered a new retail world as “fashion merchants,” he pointed with pride to the choice spot he had secured for the first store, next to Gucci and across from Versace. Indeed, if you would like to accessorize an outfit with a color-coordinated laptop, the Sony Style store offers models in pink, violet, champagne and many more. But Sony’s offerings have not impressed retail consultants with whom I spoke. Willard Ander, a senior partner at McMillan Doolittle in Chicago, was unsparing in his assessment: “Sony doesn’t get retail. The stores are not energized and not shop-able.” Apple stores extend an “emotional connection” to their customers that Sony’s do not, Mr. Ander said. The absence of such a connection, he said, was a common failing of manufacturers who venture into retail on their own. (Dell, meanwhile, announced last week that it would soon begin selling its computers in stores — but not its own. It will offer its machines in 3,000 Wal-Mart stores.) Wendy Liebman, the founder of WSL Strategic Retail in New York, was equally critical of the Sony Style store, which she faulted as being merely “a place of stuff.” She said that a successful brand excites a passionate attachment, the way Starbucks or Target do, and that Apple’s stores exemplify “emotional connection.” “People can just walk in, absorb the fumes and feel like the smartest technophile in the world,” she said. Let’s add that there is only one place to buy computers that features Geniuses at all times. IT may be that as long as personal computer makers stick with Windows, no amount of merchandiser ingenuity will be able to gin up passion matching a Mac enthusiast’s. But the proposition really has not been put to a fair test in a store. Imagine having the opportunity to test-drive a high-performance Windows machine made by a boutique manufacturer like Voodoo, based in Calgary, Alberta. Voodoo offers a variety of configurations for different kinds of uses and varying performance levels that it labels as medium, high, extreme and insane. What’s “insane”? A Voodoo Omen, configured for serious graphics work — two dual-core processors, liquid cooling, four 15,000-RPM hard drives — costs more than $16,000. No Apple retail store carries anything like it. Then again, no store selling Windows machines does, either. You have to go online to order it. Hewlett-Packard acquired Voodoo last year but has not expanded distribution channels to allow customers to test-drive these babies out on the road. I don’t think I can point my spousal unit to the Voodoo Web site and persuade her that a $5,563 Voodoo configured for the home office is just what we need: “You see, dear, we’ll actually be saving $3,500 by going ‘extreme’ rather than ‘insane.’ ” Come to think of it, I’m not ready to make the purchase, either. That’s a sale that has no chance without a family visit to a store for a hands-on trial. Sony already has the stores. What it lacks among its offerings is a machine so extraordinary that people would come just to gawk at it, and then, perhaps, would notice surrounding products that shine in the reflected light. Mr. Ander says he believes that any company, if clever enough, can use intangibles to attract retail customers. “If Payless ShoeSource can reposition itself as a place that markets ‘cool,’ ” he asked, “then why can’t Sony?” http://www.iht.com/articles/2007/05/...erg/digi28.php  Apple Now Valued at Over $100 Billion Slash Lane Apple Inc.'s market capitalization broke the $100 billion barrier for the first time on Wednesday, as shares of the company surged above $116 following a bullish research report from investment bank Morgan Stanley. That puts the Cupertino-based company's perceived market value at nearly twice that of long-time rival Dell, which was valued at $59.8 billion as of noon eastern time, and approximately a third of that of Microsoft, which has been teetering around $295 billion. Coincidentally, it will be ten years this October since Dell founder Michael Dell weighed in with his thoughts on how he would fix the then beleaguered Mac maker. "What would I do? I'd shut it down and give the money back to the shareholders," he told a crowd of several thousand IT executives at the time. Shares of Apple were helped Wednesday by a research report from Morgan Stanley analyst Katy Huberty, which asserted that the Mac maker's operating leverage remained underappreciated by investors. In the report, Huberty raised her price target on shares of the company by more than 35 percent, from $110 to $150, but also laid out a "bull case" scenario that could see shares rising as high as $225 over the next twelve months. Under that best case, the analyst said, U.S.-based Mac market share would need to appreciate to 5 percent in 2007 and 6 percent in 2008, while iPhone would need to see strong global penetration to 24 million units in 2008. The bull case scenario would also hinge on Apple introducing an ultraportable Mac device by next January that would sell 3 million units within its first year, the analyst said. Shares of Apple were trading up $2.62 (or 2.29 percent) to $116.97 in afternoon trading on the Nasdaq stock market. http://www.appleinsider.com/articles...0_billion.html  Peer-To-Peer Maverick Takes On Tune Biz Mark Gorton is drawing a line in the sand. The trained engineer and financial services entrepreneur is calling out the music business to a fistfight over the issue of peer-to-peer (P2P) music distribution via the Internet. In this month's online story "The Music Industry Wants to Kill LimeWire" from our entertainment industry columnist David Kushner, we meet the man who wants personal sharing of music to be a right for consumers—not a criminal offense. Kushner explains that Gorton originally studied at Stanford and Yale to become an electrical engineer but figured he couldn't go wrong by returning to school at Harvard to earn an MBA. Armed with his business degree, though, he soon heard the siren song of Wall Street calling and ended up working for Credit Suisse First Boston. In 1998, he ventured out on his own and founded Tower Research Capital, which conducts trades based on statistical analysis. As a sideline, he dabbled in the software that was making a big buzz in New York in the late '90s, P2P distributed file sharing, figuring that it could help facilitate financial transaction decision-making. By 2000, Gorton had a new tool in hand called LimeWire, a free software client that could be used over the open-source Gnutella file-sharing network. However, he soon noticed that subscribers weren't using the free service to trade advice on trades. They were trading tunes. While he was still making money offering a robust fee-based version of his P2P client, he didn't see anything wrong with allowing the free service to continue unfettered. Then, as Kushner notes, the lawyers showed up at his door. Following the landmark Supreme Court decision in 2005 known as MGM v. Grokster, attorneys for the big recording companies descended on the online P2P services to either get their consent in creating royalty schemes for songs shared among users or shut down their operations altogether. The result has been a social phenomenon—pitting millions of consumers against a handful of music monoliths—that continues to unfold to this day. All the while, Gorton has continued to keep his powder dry and fight for his users. He believes that the lawyers for the big media companies don't understand the realities of the Internet age. After meeting with a group of them in his Manhattan offices, Kushner writes, he came away thinking, "[T]hese people are all on drugs." Even after offering to set up his own file-sharing royalty system, the lawyers sued him anyway. So last September, Gorton got his own attorneys to sue them back. His complaint alleges that the goal of the music business is: "to destroy any online music distribution service they did not own or control, or force such services to do business with them on exclusive and/or other anticompetitive terms so as to limit and ultimately control the distribution and pricing of digital music, all to the detriment of consumers." Today, Kushner states Gorton is considered to be the most prominent holdout in the record labels' ongoing battle against online piracy. For his part, though, we learn, Gorton still wants to compromise, to find a solution that balances the old business model of the music companies and a new model of engaging his "customers" in an open and "productive way." "The core focus of the music industry has been shutting down individual file-sharing programs, and that has proven to be a failure," Gorton told Kushner. His legal battle is still in the discovery phase, so it will be quite a while before the fists start flying, with plenty of time in between for cooler heads to prevail. But Gorton seems committed to finding an alternative that could lead to a new era for consumers purchasing and sharing their favorite songs. It's a test case that will have a lot of people in the new media and old media worlds tuning in. http://www.spectrum.ieee.org/may07/comments/1820  StreamCast Adds Joost to Lawsuit Over Peer-to-Peer Technology Mark Hefflinger San Francisco - Joost, the ad-supported, peer-to-peer streaming TV service created by the founders of Skype and Kazaa, has been added as a defendant to a year-old lawsuit filed by StreamCast Networks over the rights to the service's underlying FastTrack peer-to-peer technology, CNET News.com reported. StreamCast, which developed the Morpheus file-sharing application, says in the suit that Skype/Joost developers Janus Friis and Niklas Zenstromm improperly transferred technology rights from StreamCast in a breach of contract. The StreamCast suit also names eBay -- which acquired Skype in 2005 -- as a defendant, along with 21 other parties. "We are taking action because we believe the rights to the Skype and FastTrack technologies were swept out from under our feet, and our 28 million Morpheus users were stolen from us," Michael Weiss, CEO of StreamCast Networks, said in a statement at the time the original lawsuit was filed last May. The lawsuit seeks an injunction against the sale and marketing of Skype, as well as "billions of dollars" in unspecified damages. http://www.dmwmedia.com/news/2007/05...eer-technology  Cellphone Raid Roils Manhattan School Julie Bosman The authorities confiscated hundreds of cellphones and other electronic devices yesterday in an unannounced sweep, with metal detectors, at Middle School 54 in Manhattan. Few subjects have stirred up New York City public school parents more than the ban on cellphones in schools that Mayor Michael R. Bloomberg is determined to enforce. Yesterday morning brought another random sweep with metal detectors, this time at Middle School 54, which yielded an unusually heavy load of contraband. The cellphone-to-student ratio at this Upper West Side school was particularly high: 961 students are currently enrolled, according to the Education Department, and 404 cellphones were confiscated. (Along with 69 iPods, 23 assorted electronic devices, two knives and one imitation gun.) After the closing bell at M.S. 54 yesterday, parents confronted administrators about the surprise cellphone check, while students milled around and gossiped. Students whose cellphones had been confiscated were given quarters to call home at the end of the day, one parent said — a foreign concept to some cellphone users. “A teacher gave one of the boys a quarter to use a pay phone, and he was like, ‘What do I do with this?’” the parent said. Despite a full year of parent complaints and a lawsuit, Mr. Bloomberg is not backing down from the cellphone ban, sticking to his position that the phones are disruptive to learning. http://empirezone.blogs.nytimes.com/...hattan-school/  Manitoba Chiefs Want Cellphone Revenue CBC News Manitoba First Nations are seeking compensation from Manitoba Telecom Services for every cellphone signal that passes through First Nations land, saying the airspace should be considered a resource like land and water. At a recent economic development summit, the Assembly of Manitoba Chiefs resolved to negotiate revenue sharing with MTS for transmissions signals that cross the land, water and air space of their reserves and traditional territories. "[The request is] based on the understanding that we do have some fundamental rights as indigenous people to land, water and airspace," said Chief Ovide Mercredi of the Grand Rapids First Nation. "When it comes to using airspace, it's like using our water and simply because there's no precedent doesn't mean that it's not the right thing to do," he said. Mercredi says that signals over a significant area of the province would be affected, noting that the Cree Nations claim rights to a large portion of the north. Proposal may inspire more negotiations Anna Hunter, a University of Saskatchewan professor of political studies specializing in aboriginal governance, says the AMC's request is unique but she says other First Nations groups across the country will likely follow suit. Continue Article "On a provincewide basis, this is definitely an innovative approach but I think it's an approach that other provinces' First Nations groups will probably take forward," she said. MTS officials have declined to comment on the issue until they see the group's proposal. http://www.cbc.ca/consumer/story/200...cellphone.html  Pirates Of Caribbean Sequel Sets New World Record Pirates Of The Caribbean: At World's End has smashed the record for the biggest worldwide opening in history - the movie raked in a massive $401 million (£200.5 million) in its first six days of release. The second sequel in the Walt Disney-made series has already broken box office records in the U.S. for the best Memorial Day weekend debut, after making $142.1 million (£71.05 million). At World's End beat the previous record for best opening set by the release of Spider-Man 3 earlier this year (07), which made a total of $382 million (£191 million) in its first few days. Walt Disney Studios spokesman Mark Zoradi says, "We knew that audiences all over the world were excited to see Johnny Depp and the rest of the fantastic Pirates cast in this latest adventure. "But this record-setting response at the global box office has been nothing short of incredible. "Pirates Of The Caribbean: At World's End now has the biggest opening in movie history, and we're extremely proud of that achievement." http://www.postchronicle.com/news/en...21283530.shtml  Sony: Disney 'Pirates' Figures are Wrong Dave West Sony has accused Disney of "irregularities" in its claims for Pirates of the Caribbean 3's opening-week box office performance. The movie house has called into question its rival's claims to have set a new record in its first six days release on the world box office. Disney said it had made $251 million (£126.9 million) outside North America and $404 million (£204.4 million) overall. However, Steve Elzer, corporate communications chief at Sony, rejected the claim in an unusual release to the media. He began: "While Disney and the filmmakers of Pirates of the Caribbean: At World's End deserve their due on a remarkable opening worldwide, there are some irregularities in their claim regarding record-setting. "There are at least two territories - Italy and France - where Buena Vista International opened the film on Tuesday - in essence adding a seventh day of grosses into Pirates' 'six day record.'" Elzer appeared to claim that, on a similar measure, its recently-released Spider-Man 3 did better than Pirates. "For the record, Spider-Man 3 grossed $418.1 million in its first seven days of release worldwide with $256.7 million generated from territories overseas." Disney has so far offered no comment and official figures are due to be released in coming days. http://www.digitalspy.co.uk/movies/a...are-wrong.html  The Top 20 Movies at U.S. and Canadian Theaters Friday Through Monday: 1. "Pirates of the Caribbean: At World's End," Disney, $139,802,190, 2. "Shrek the Third," DreamWorks Animation-Paramount, $67,010,012, 3. "Spider-Man 3," Sony, $18,112,261, 4. "Bug," Lionsgate, $4,015,846, 5. "Waitress," Fox Searchlight, $4,005,008, 510 locations, 6. "28 Weeks Later," Fox Atomic, $3,280,306, 7. "Disturbia," DreamWorks-Paramount, $2,433,028, 8. "Georgia Rule," Universal, $2,407,910, 9. "Fracture," New Line, $1,646,761, 10. "Wild Hogs," Disney, $1,586,929, 11. "The Invisible," Disney, $1,102,840, 457 locations, 12. "Away From Her," Lionsgate, $947,459, 13. "Delta Farce," Lionsgate, $649,713, 14. "Blades of Glory," DreamWorks-Paramount, $643,146, 15. "Hot Fuzz," Focus, $636,457, 16. "Paris Je T'aime," First Look, $550,796, 17. "Once," Fox Searchlight, $435,958, 18. "300," Warner Bros., $435,414, 19. "Next," Paramount, $414,505, 20. "Black Book," Sony Pictures Classics, $411,891, http://www.sohood.com/1/content/view/2015/66/  'Pirates' Outsells 'Matrix' in Blu-Ray, HD DVD Showdown Last week's sales estimates are in, and in terms of sheer unit sales, Disney's Blu-ray-only release of the first two "Pirates of the Caribbean" flicks handily beat Warner's HD DVD-only release of the two "Matrix" box sets. According to market research estimates from Home Media Magazine, the two "Pirates" films sold a combined total of a little less than 47,000 units, while the "Matrix" sets sold about 13,900 units. Since the "Matrix" sets sold at an cost of nearly three times that of the "Pirates" flicks, there's slighly more parity in terms of gross sales, but even there (as Blu-ray supporters have been quick to point out), "Pirates" gets the edge. In comments first published in The Hollywood Reporter, Bob Chapek, worldwide president of Buena Vista Home Entertainment, called the week's win by "Pirates" a "strong and significant trend toward consumer preference for the Blu-ray Disc format." "We are thrilled by the critical and industry response to 'Pirates' on Blu-ray disc," Chapek said. "But more importantly, the consumer has spoken loud and clear. This is only the beginning, but it was certainly a significant and explosive indicator of things to come." http://www.highdefdigest.com/news/show/675  The Pirate Bay: One year After the Raid Ernesto Today it’s exactly one year since the controversial raid on The Pirate Bay. Unlike the MPAA would have wanted, TPB is still online, more poular than ever. Let’s look back at last years events. First of all, the attack against The Pirate Bay was highly unsuccessful. The site was only offline for a couple of days before they were back in full force. Stronger than ever thanks to the widespread media attention. Soon after the raid several sources reported that the MPAA initiated the attack. Apparently they directly influencing Swedish authorities to intervene in this specific case, which is considered illegal in Sweden (the term is “minister rule”). To make it even worse, it turned out that the US had threatened to put Sweden on WTO’s black list because they didn’t take the Pirate Bay down. This threat should have have made the Swedish government move even quicker. It is assumed that Swedish authorities hinted to the prosecutor to take action, and even though the prosecutor wrote a PM a before the raid in which he stated that it was impossible to convict the Pirate Bay, the letters from the MPAA probably changed his mind. It later became public that John Malcolm, Executive Vice President of the MPAA wrote (PDF) to Sweden’s State Secretary in which he stated, “It is certainly not in Sweden’s best interests to earn a reputation among other nations and trading partners as a place where utter lawlessness with respect to intellectual property rights is tolerated.” Following the raid the Swedish pirate party got thousands of new members in a matter of weeks. Suddenly, they were the largest party without parliament seats. This success has also led to pirate parties forming in a number of other countries: France, Italy, USA, Belgium, Austria, and very recently also Germany, Spain and Russian. There is also one forming in the UK. Together, they have founded PP-International, which is an international collaboration forum/group to exchange experiences, ideas and such, and Sweden has a very important role here. In August 2006, three months after the raid the documentary “Steal This Film” was published. This excellent documentary gives some more insight in the events that took place May 31, 2006, In this documentary The Piratebay admins tell how the raid went down, what happened after the raid, how the MPAA was involved, how the US had threatened to put Sweden on WTO’s black list, the Pirate demonstration, and how they were harassed by police officers and more. Up until now the servers of The Pirate Bay are still in custody, and prosecutor Håkan Roswall announced earlier this month that he will press charges against the Pirate Bay admins. However, The Pirate Bay said it’s not impressed by the announced prosecution, and according to a leak within the Swedish police, they don’t have much to be afraid of. http://torrentfreak.com/the-pirate-b...fter-the-raid/ |
|
|

|
|
|
#2 |
|
Join Date: May 2001
Location: New England
Posts: 10,016
|
Pirates Still Have All the Best Tunes
File-sharing has holed the record industry below the waterline. So why does private equity guru Guy Hands want to buy EMI? Richard Wachman On a blazing hot day in California five years ago, the boss of Yahoo, Terry Semel, rose to his feet to address a technology conference in which he lambasted record companies for being 'paralysed' by the threat of online music. Semel's words were met with rapturous applause from an audience made up largely of new media executives from Silicon Valley with a vested interest in the digitalisation of music. The timing of his words was significant: the music industry had just succeeded in shutting down Napster after a court ruled it should stop offering pirated music over the net. The Napster case infuriated Semel and others who believed that the music majors were showing a lack of imagination about how the market could expand via new technologies. Far from grasping opportunities, the companies were still reeling from the impact of MP3 files, a format that compresses music into data that can be quickly downloaded over the internet, and which Napster was exploiting with phenomenal success. As one analyst remembers: 'Executives were running around like headless chickens because they sensed that here was a technology that would destroy existing channels of distribution. How right they were.' Critics say that instead of embracing the internet by hiring visionary and innovative individuals, the firms turned to their lawyers in a fruitless attempt to crush illegal downloading before it could get off the ground. Chris Parry, founder of radio group Xfm and Fiction Records, says: 'Of course the industry has a duty to protect copyright, but for too long executives were fixated by the idea of selling CDs via a retail distribution network. Legal challenges are legitimate, but the majors should also have taken the initiative by recruiting people who were internet-savvy. Few did so at the time.' It has taken this long for the record companies to fight back by collaborating with legal downloading sites such as iTunes in a bid to offset lost revenue from plummeting CD sales. But internet piracy is still costing them billions a year and the recorded-music arms of the majors look to be in terminal decline. According to the IFPI, the international music industry lobby group, 40 songs are being downloaded illegally for every legal download. Put another way, they say 20 billion songs were downloaded illegally in 2006 and the situation is set to worsen following the spread of broadband to eastern Europe and other emerging markets. The effect of piracy on the industry has been to spur consolidation as the big players scramble to cut costs by merging with each other. There are now only four major music groups: Universal, Sony/BMG, EMI and Warner Music. Last week, British-based EMI, which has been struggling with falling profitability for years, said it was recommending to shareholders a takeover approach from Terra Firma, the private equity group headed by Guy Hands, which only last month tried unsuccessfully to bid for Alliance Boots. The idea of private equity getting involved with the topsy-turvy world of the music business surprised observers. But the attraction of EMI for Hands is that about 60 per cent of a music company's income is derived from publishing. The publishing arm collects royalties when a track by one of the firm's artists is played live, on the radio or via any other medium, offering private equity a reliable stream of revenue. EMI has an enviable roster of artists including the Beatles, Robbie Williams, Norah Jones and Coldplay. But what will Hands do with EMI's recorded music arm? His associates say he could keep it, and that there are plans to extend its reach, but exactly how remains to be seen. 'Perhaps he has in mind a business model that pays more attention to the internet than EMI's previous owners,' says Lorna Tilbian, an analyst at Numis Securities. But within the music industry there are those who suspect that Terra Firma will sell on the record company to America's Warner, which this weekend is weighing whether to launch a counter-bid for EMI, headed by Eric Nicoli. Tilbian says: 'Actually, none of this is rocket science. People still want good music: the thing that is different is the distribution platform, not people's appetite for entertainment. That's the challenge for EMI's management, private equity or otherwise.' But Paul Brindley, head of digital music research consultancy Musically, thinks the outlook 'is not terribly encouraging'. 'There are no easy solutions while piracy remains rife,' he warns. But his advice to the record companies is not to repeat the mistake they made with Napster by failing 'to grasp the internet nettle'. He suggests that the industry should 'rewire itself' by creating more web subscription services, as well as look to advertising for revenue streams by launching free or nearly free web networks of their own, or forging alliances with new players. He says: 'The real challenge is to capture business in a market where many consumers believe that they should be able to download what they want, when they want, free of charge.' In the interim, legal challenges to protect copyright continue: US and UK trade bodies have reached a settlement with Sharman Networks, which distributes software applications that are believed to account for 15 per cent of music file-sharing. Under the terms of the deal, Sharman was ordered to pay the four majors $100m, the biggest settlement so far in any music piracy lawsuit. Some 18 months ago, there was a landmark US Supreme Court ruling in the MGM-Grokster case, which undermined the legal status of file-sharing networks by stating that they could be held responsible for copyright violations committed by their users. Following the hearing, Grokster ceased operating, while other networks agreed to install filter technology to curb abuses. But piracy remains rampant: the industry is currently pursuing cases against services such as Limewire and eDonkey. A US study has found that, while there is evidence that the number of American homes involved in illegal downloading has held steady, the amount of content they are taking has increased. Also, as file-sharing services are closed down, new ones spring up. Mark Mulligan, of Jupiter Research, says: 'If you are a file-sharer, you know that the likelihood of you being caught is very similar to that of being hit by an asteroid.' But Geoff Taylor of the British Phonographic Industry says the primary motivation behind legal action is to raise consciousness: 'We want to establish that file-sharing is illegal.' The problem has been exacerbated by the fact that a lot of song swapping on the net now takes place on closed social networks or blogs. Brindley says it is hard to know 'which business model will fly and which won't'. If he is right, the future owner of EMI's recorded music division will quickly discover that running the business is not a whole lot different from pushing water uphill. You need Hands: whizz-kid's progress Guy Hands, pictured, the head of private equity group Terra Firma, is known as a financial whizz-kid after turning around the fortunes of businesses that include the UCI cinema chain and energy group WRG. As an undergraduate at Oxford, he shared a home with future Conservative leader William Hague before joining Goldman Sachs. He made his name as head of a London-based buyout group owned by Japanese banking giant Nomura, becoming the country's biggest pub landlord and buying the betting chain William Hill and assets such as Angel Trains and army housing estates. Setbacks include failing to acquire Thames Water and Alliance Boots. Whether he will succeed in purchasing EMI is open to question. His 265p a share cash bid is seen as gutsy, but Edgar Bronfman's Warner Music is poring over EMI's books with a view to making a higher offer. Rival private equity groups, as well as former EMI music boss Jim Fifield, are also circling. But Hands is a man who will be reluctant to let it slip through his fingers. http://observer.guardian.co.uk/busin...088830,00.html  EMI Strikes a Deal With YouTube EMI has signed a deal with YouTube that will allow its users to access videos by EMI artists. It means all four of the world's major music firms are now YouTube partners. The terms of the agreement should eventually allow users to incorporate recordings by EMI artists into their own projects. The deal follows a string of lawsuits by companies who accuse YouTube of allowing its users to pirate their copyrighted works. The biggest threat comes from entertainment giant Viacom Media which is suing YouTube for $1bn (£505m). The US group - which owns MTV and Nickelodeon - claims that the website uses its shows illegally. User generated content "We're excited to add EMI Music's stellar roster of artists' content to our site and make it available to our community," said Chad Hurley, chief executive of YouTube. Eric Nicoli, chief executive of EMI Group, said the deal would "offer consumers the best possible entertainment experiences" by using "innovative business models that will generate revenues for our business and our creators". "Through this agreement EMI Music and its artists will be fairly compensated for their work," Mr Nicoli said. EMI and YouTube have agreed to work together to develop ways in which EMI-owned recordings can be incorporated into user generated content by YouTube users. News of the deal comes just 10 days after EMI agreed to be taken over by private equity group Terra Firma for £2.4bn. Google bought the video-sharing website for $1.65bn (£883m) in October 2006. http://news.bbc.co.uk/go/pr/fr/-/2/h...ss/6709209.stm  Venezuela's Counter-Revolution Won't be Televised... But it Will be on YouTube Nate Anderson When YouTube CEO Chad Hurley told a Congressional committee that his company "advances democracy," perhaps this was the sort of thing he had in mind. An opposition Venezuelan television station whose broadcast license has not been renewed by the government is now turning to YouTube to get its message out after its transmitter was taken over by a state-run channel. Hugo Chavez's "Bolivarian Revolution" has no time for media groups that criticize his government; Radio Caracas Televisión (RCTV) is now off the air, and another channel, Globovision, could be next, according to CNN. RCTV journalists and producers have not been arrested or stopped from working, but their main link to the public has been removed. Rather than giving up, the station has turned to YouTube, where it now has its own channel for the show El Observador. A Colombian channel is also broadcasting RCTV content into Venezuela. El Observador clips have been seen 175,000 times since May 28, and the channel is currently the most-subscribed channel of the week. While putting the station's shows on YouTube is an excellent idea, YouTube still lacks anything near the reach of over-the-air broadcasts. But the use of the site to avoid censorship is growing, and it's not hard to imagine a day in the near future when the site (or sites like it) becomes as essential as local TV stations. As that happens, YouTube will come into even more conflicts with governments that have an interest in controlling what their citizens see, It's already happening—Thailand's king, for instance, has a thing for iPods but isn't too keen on YouTube. Will Hugo Chavez show more tolerance? Update: Some readers are concerned that Chavez is getting a bad rap here; RCTV has been accused of supported the earlier coup against him and of calling for the overthrow of the current government. It's a complicated situation, but the fact remains that RCTV was a main opposition outlet and that its replacement is a state-run channel. Given Chavez's long history of attacks on the press and his current ability to rule by decree, he doesn't look like a man interested in a robust and critical press, though he has not instituted mass arrests or official censorship of journalists. Chavez's concern for government stability and threats against the state are a recent development, too; Chavez participated in a coup attempt of his own back in 1992. http://arstechnica.com/news.ars/post...n-youtube.html  Exetel Mulls P2P Caching Phil Sweeney Exetel has declared its P2P shaping trial a success, and says it is investigating the expansion of the program with a P2P caching solution. The popular ISP began shaping P2P in November last year, with users reacting strongly to the announcement. But Exetel said it was the only ISP being completely up front about its shaping policies. "It's interesting that only Exetel has been quite open about its purchase and deployment of a P2P control process", it said, stating it was "by no means the first Australian ISP to purchase from Allot and certainly a lot of other ISPs had purchased similar devices from Allot's competitors." After running the existing system for six months, Exetel believes that users were not significantly affected, and felt it could be further improved. "Some time between early August and late October we will gradually phase out the [Allot] NE 2020 and replace it with a P2P caching solution", said the announcement. The caching solution would work by "delivering P2P data that has previously been retrieved by another customer directly from an Exetel "mirror" and only using external sources for data that isn't available from the local disks." A successful implementation would see bandwidth usage drop and possibly even increased speeds for customers. Peer to Peer caching is not new to Australia however, with Optus using PeerCache technology on and off since 2003. PeerCache support is built into many popular P2P clients such as Azureus and eMule, and they discover the ISP's cache using DNS (cache.p2p.optusnet.com.au still exists today). Exetel has not revealed which caching solution it is investigating, however. But the biggest issue with implementing a P2P cache is of the legal kind. With ISPs likely to distribute a significant amount of copyright material through the cache, will the content industry pursue them? Although existing laws cater for "temporary caching" of content by ISPs, it could be seen as waving a red flag in front of a bull. Exetel has not given an estimate for when the caching solution might become available. "Like all things that 'sound too good to be true' it may well not prove itself during the extensive testing we plan to do but, at this time, it looks very promising", said the announcement. http://whirlpool.net.au/article.cfm/1734  DVR Viewers Push Ad Ratings Up Laura Petrecca and Theresa Howard After a six-month delay, The Nielsen Co. on Thursday released the commercial ratings data that has been much-awaited by ad and media companies. The new data rates just the commercials in the show and also now includes viewing on the digital video recorders now found in 17% of U.S. homes. The immediate impact of the data will be on ad price negotiations in the "upfront" in progress. It's the annual spring period in which TV networks sell the bulk of their ad time for the fall season. In the past, network ad prices have been based on a show's traditional Nielsen rating, which counted how many people watched a show when it aired. Nielsen's new commercial data include an average viewer total for all of a show's commercials when it airs, as well as averages for those who watch commercials on a DVR up to seven days later. With billions of dollars in ad spending at stake — 2006 upfront sales were about $9 billion — networks want to make sure that every ad viewer is counted. Likely to be the most-discussed tally in the upfront negotiations will be the "live-plus-three" data in today's report: commercial viewing for a show when its airs, plus up to three days later via a DVR. About 95% of all broadcast prime-time DVR viewing is done within three days of the live telecast, according to Nielsen. Among things the report revealed is that many DVR viewers do not fast-forward through ads. The viewer total for broadcast network ads goes up 32% when DVR watchers within three days are included, according to Nielsen. For some prime-time shows, it means that DVR viewing, long seen as a threat to advertising, could even bring higher ad prices. NBC's The Office, for example, had a "live-plus-three" Nielsen commercial rating of 3.36 — higher than the 3.11 it got for the week of May 6 under the traditional Nielsen program rating system. The Nielsen data come as ad buyers and sellers clamor for better measurements of results for all advertising. "The way people are using media is changing, and we just need to have our measurement keep up with that," says NBC Research President Alan Wurtzel. Many media buyers say the new Nielsen data don't go far enough. "This is a step in the right direction, but we're not quite there," says Steve Kalb, director of broadcast media at ad agency Mullen's buying unit MediaHUB. "Our goal is to get to average commercial rating (for each) commercial," says Larry Novenstern, head of the NewCast division of media buying firm Optimedia. "We want our clients to know what they're paying for." http://www.usatoday.com/money/media/...ens-usat_N.htm  MLB Says Slingbox Illegal, CEA Thinks Otherwise Matt Whitlock MLB's recent comments that Slingbox owners streaming home games when traveling is illegal has raised quite a stir over the last few days. MLB's argument is that Slingbox allows consumers to circumvent geographical boundaries written in to broadcast deals. "...if a league can't protect the rights they (sell), that doesn't bode well for future contracts when they want to resell the rights at higher margins," says George Kliavkoff, who was vp business development at MLBAM before becoming chief digital officer at NBC. As always, Sling Media CEO Blake Krikorian is siding with consumers. "Maybe they should be paying us," he told Sports Business Journal. "Seriously. I'm still failing to see how we're hurting them or their brand. We're allowing more people to see more baseball, with all the same commercials, and stay connected to their teams. How is that bad? It's additive to what they're doing. They've paid for our device and they've paid their cable bill." Sling Media also stands firm that Slingbox is intended to be a one-to-one connection, and that it's a violation of their license agreement to allow a third party to access a Slingbox. If anything, allowing users to watch their home teams creates a tighter bond between a fan and their local sports and broadcasting teams. The Consumer Electronics Association agrees with Blake, and seems to be siding with Sling Media and consumers on the issue. "This is a classic instance of copyright owners trying to suppress innovation purely because it empowers consumers," says CEA President Gary Shapiro." There is no infringement or piracy here--consumers are simply watching content they lawfully purchase..." "We and other leagues have formed a group to study the issue and plan our response," said MLB general counsel Michael Mellis. "A lot depends on ongoing discussions. Plus, there's no guarantee that Slingbox will be around next year. It's a start-up." With baseball fans, Sling Media, and the CEA all opposed to MLB's claims, you think they'd back down. Two solid years in business and a rabid customer base puts Sling Media far from "start-up" status. From this Editor's point of view, as long as they continue to strive for empowering consumers, I'd be willing guarantee they'll still be around next year... and for several more to come. http://www.slingcommunity.com/blog/1...nks-Otherwise/  Box.net application becomes available on Facebook platform. Press Release Today, Box.net announced its File Sharing App built on Facebook Platform, a platform that enables companies and developers to build applications for the Facebook website. "Facebook Platform creates an ecosystem for developers to build applications that deeply integrate into Facebook and use its social graph," said Mark Zuckerberg, founder and CEO of Facebook. "By enabling developers to make applications within Facebook, we're working together to create a better utility for millions of people." Box.net adapted their File Sharing App for use on Facebook. Already serving more than 300,000 apps daily from a vast collection of Internet locations, the Box.net File Sharing App allows users to display any file directly on their own sites. From music and video streaming to document collaboration, the app allows for a broad array of functionality utilized by individuals, bloggers, enterprises and recording artists. "Our main goal in participating in Facebook's new launch is to help people recognize the diverse ways in which they can share their personal media with others," explained Aaron Levie, CEO of Box.net. "Box's Sharing App is unique in both its versatility and its simplicity, traits that fit seamlessly into the clean, yet contagious, nature of Facebook." Facebook appealed to Box.net "not only because of its prominence as a social utility," Levie said, "but also because its users are the people Box.net wants to reach. We see Facebook as having a very complementary audience and compatible service. They are a people platform; we're building a data platform." Founded in 2005, Box.net provides secure online file sharing and storage to almost a million registered individuals and companies worldwide. Redefining file transfer, the Box platform allows personal and commercial content to be accessible, sharable and storable in any place and in any format. Applications and services that have partnered with Box include RCA Small Wonder, Wordpress.com and Netvibes. Box.net also provides online media sharing for a wide range of high profile artists, including 311, Bright Eyes and Eve. http://www.emediawire.com/releases/2007/5/emw528763.htm  The IT Department as Corporate Snoop Layer 8 As if we needed more proof that insiders are a seriously worse threat to your corporate jewels than any malicious hacker, a study released today says that one in three of IT employees snoop through company systems and peek at confidential information such as private files, wage data, personal emails, and HR background. The survey, which claims to reveal "the hidden scandal of IT staff snooping," is from Cyber-Ark Software, a company that, naturally specializes in password protection As if that weren’t bad enough, the survey found that more than one-third of IT professionals admit they could still access their company’s network once they’d left their current job, with no one to stop them. More than 200 IT professionals participated in the survey with many revealing that although it wasn’t corporate policy to allow IT workers to access systems after termination, still almost 25% of respondents knew of another IT staff member who still had access to sensitive networks even though they’d left the company long ago. "Gone are the days when you had to break into the filing cabinet in the personnel department to get at vital and highly confidential information. Now all you need to have is the administrative password, and you can snoop around most places, and it appears that is exactly what's happening," said Calum Macleod, European director for Cyber-Ark, said in a statement. The study also showed that over 50% of workers still keep their passwords on a Post-It note, in spite of all the education the IT security industry to do it differently. And in the don’t do-as-I do-dept., more than 50% of respondents admitted to using Post-It notes to store passwords to administrator accounts. One-fifth of all organizations admitted that they rarely changed their administrative passwords with seven percent saying they never change administrative passwords. This would help explain how one-third of all people questioned would still have access to their network even if they'd left the company. Eight percent of respondents noted that they still use the manufacturer's default admin password on critical systems. This remains the most common way for hackers to break into corporate networks, Cyber –Ark said. http://www.networkworld.com/community/?q=node/15731  Computer Hackers Steal Carson Funds Cyber-thieves make off with $45,000 after shifting nearly $450,000 from the city's coffers. Hector Becerra If Carson Treasurer Karen Avilla had had a nagging feeling she was being watched whenever she got on her laptop computer, she would have been right. Cyber-thieves were able to shift nearly $450,000 from the city's general fund last week by using a program that was able to mimic the computer strokes made by Carson's financial officer. Each time Avilla logged on to her city-provided laptop in the morning, someone was — virtually — looking over her shoulder, recording every single keystroke. Armed with the spyware program, the hackers obtained bank passwords. They wired $90,000 to a "Diego Smith" in North Carolina. One day later, on May 24, the thieves got bolder and wired $358,000 from the city's bank account to a bank in Kalamazoo, Mich. Avilla and her deputy discovered the theft just in time to have all but $45,000 of the funds frozen. But the experience left city leaders rattled. "As I sat there with the detectives and the forensic folks from the bank, I thought, 'I don't even want to touch a computer,' " Avilla said Thursday. "I felt violated. It made me think, 'Who's out there?' " The crime raised concerns about the security of municipal coffers, especially when wireless networks are used. Although such city hacking cases have been isolated, some experts said many municipalities lack the large information technology staffs and large budgets for computer security. "If you go after a local municipality, they're more likely to have fewer people dedicated to computer security," said Eric Schultze, chief security architect for Shavlik Technologies in Minnesota and a widely cited expert in anti-hacking circles. Avilla said she still doesn't know how her computer was targeted. She said she doubts it had the latest security software patch protections — something sheriff's detectives and bank investigators told her is essential in safeguarding her computer. She said that as soon as word got out, Carson fielded calls from officials in other cities, asking how they could protect themselves. South Gate City Manager Gary Milliman said he has seen all sorts of fraud perpetrated against cities in 32 years, but nothing like this. "I think it's a concern," Milliman said. "It's something we're going to check into to make sure there isn't a vulnerability in our system." Earlier this year, the finance director of the Northern California city of Willows discovered that a hacker had taken $4,000 from a city fund. Avilla said cities may not always notice smaller thefts. "One thousand dollars. You think a bank is going to bat an eye?" Avilla said. "It's not an inexpensive enterprise to have a full team that goes around checking every laptop ever used. I think we can use more IT folks, but when a lot of these departments were created, a few people had computers. Now everyone does. On top of that, almost everyone has a laptop." Experts said that without up-to-date security software, such a computer could be especially vulnerable if people who use it visit websites that contain spyware. But hackers also send mass e-mails which, if opened on vulnerable computers, can allow installation of "keystroke loggers." "It automatically sends all keystrokes logged to a hacker, via e-mail or another form of communication," Schultze said. "So a hacker sitting halfway around the world can log into your bank account, enter your user name and do what they want to do." Kevin Overcash, vice president of product management for Breach Security in Carlsbad, Calif., said that when organizations started installing a lot of wireless networks, hackers devised ways to breach them through what is called "drive-by hacking." In trying to provide a service to their residents — by allowing them to check their water bills via the Web, for example — municipalities sometimes make themselves vulnerable, he said. "That kind of access opens you up to hackers. It opens the door for people to have access to data if you do not have good security," Overcash said. Avilla said she noticed a problem when she found she was unable to log on to the city's bank account. She thought she must have been typing the password incorrectly. On May 22, the bank gave her a new password. But unbeknownst to her, the cyber thieves got that password as soon as she tapped it into her computer. On May 24, Avilla and her deputy checked bank balances and discovered the previous day's $90,000 wire transfer to someone in Wilson, N.C. Avilla checked with the bank and discovered the $358,000 transfer that day through National City Bank in Kalamazoo. "I thought, 'We got a problem,' " Avilla said. She called the bank and filed a police report, leading to the freezing of the city's funds. No one has been arrested, authorities said. L.A. County Sheriff's Capt. Todd Rogers said the department's high-tech crimes unit is on the case. The Secret Service is also helping in the investigation, he said. Avilla said the experience has made her angry and determined to seek legislation that would address the problem. "There's got to be more than one way to fight this," she said. "They get us in so many ways. There's got to be a way for us to get them." http://www.latimes.com/news/local/la...=la-home-local  How Online Criminals Make Themselves Tough to Find, Near Impossible to Nab Scott Berinato, CSO Forensic investigations start at the end. Think of it: You wouldn’t start using science and technology to establish facts (that’s the dictionary definition of forensics) unless you had some reason to establish facts in the first place. But by that time, the crime has already happened. So while requisite, forensics is ultimately unrewarding. A clear illustration of this fact comes from the field investigations manager for a major credit services company. Sometime last year, he noticed a clutch of fraudulent purchases on cards that all traced back to the same aquarium. He learned quite a bit through forensics. He learned, for example, that an aquarium employee had downloaded an audio file while eating a sandwich on her lunch break. He learned that when she played the song, a rootkit hidden inside the song installed itself on her computer. That rootkit allowed the hacker who’d planted it to establish a secure tunnel so he could work undetected and “get root”—administrator’s access to the aquarium network. Sounds like a successful investigation. But the investigator was underwhelmed by the results. Why? Because he hadn’t caught the perpetrator and he knew he never would. What’s worse, that lunch break with the sandwich and the song download had occurred some time before he got there. In fact, the hacker had captured every card transaction at the aquarium for two years. The investigator (who could only speak anonymously) wonders aloud what other networks are right now being controlled by criminal enterprises whose presence is entirely concealed. Computer crime has shifted from a game of disruption to one of access. The hacker’s focus has shifted too, from developing destructive payloads to circumventing detection. Now, for every tool forensic investigators have come to rely on to discover and prosecute electronic crimes, criminals have a corresponding tool to baffle the investigation. This is antiforensics. It is more than technology. It is an approach to criminal hacking that can be summed up like this: Make it hard for them to find you and impossible for them to prove they found you. The concept is neither new nor foolproof, but in the past 12 months, forensic investigators have noticed a significant uptick in the use of antiforensics. This is not because hackers are making more sophisticated antiforensic tools, though some are. Rather, it’s because antiforensic tools have slid down the technical food chain, from Unix to Windows, from something only elite users could master to something nontechnical users can operate. What’s more, this transition is taking place right when (or perhaps because of) a growing number of criminals, technically unsophisticated, want in on all the cash moving around online and they need antiforensics to protect their illicit enterprises. “Five years ago, you could count on one hand the number of people who could do a lot of these things,” says the investigator. “Now it’s hobby level.” Researcher Bryan Sartin of Cybertrust says antiforensic tools have gotten so easy to use that recently he’s noticed the hacks themselves are barely disguised. “I can pick up a network diagram and see where the breach occurred in a second,” says Sartin. “That’s the boring part of my job now. They’ll use FTP and they don’t care if it logs the transfer, because they know I have no idea who they are or how they got there.” Veteran forensic investigator Paul Henry, who works for a vendor called Secure Computing, says, “We’ve got ourselves in a bit of a fix. From a purely forensic standpoint, it’s real ugly out there.” Vincent Liu, partner at Stach & Liu, has developed antiforensic tools. But he stopped because “the evidence exists that we can’t rely on forensic tools anymore. It was no longer necessary to drive the point home. There was no point rubbing salt in the wound,” he says. The investigator in the aquarium case says, “Antiforensics are part of my everyday life now.” As this article is being written, details of the TJX breach—called the biggest data heist in history, with more than 45 million credit card records compromised—strongly suggest that the criminals used antiforensics to maintain undetected access to the systems for months or years and capture data in real time. In fact, the TJX case, from the sparse details made public, sounds remarkably like the aquarium case on a massive scale. Several experts said it would be surprising if antiforensics weren’t used. “Who knows how many databases containing how many millions of identities are out there being compromised?” asks the investigator. “That is the unspoken nightmare.” The Obfuscator’s Toolkit If you were making a movie about a computer crime, the bad guys would use antiforensics. And since it’s a movie, it should be exciting, so they’d use the clever and illicit antiforensic tools, the sexy ones with little or no legitimate business purpose. Liu has developed such tools under the Metasploit Framework, a collection of software designed for penetration testing and, in the case of the antiforensic tools, to expose the inherent weaknesses in forensics in hopes that the forensics industry would view it as a call to action to improve its toolset. One of Liu’s tools is Timestomp. It targets the core of many forensic investigations—the metadata that logs file information including the times and dates of file creation, modification and access. Forensic investigators poring over compromised systems where Timestomp was used often find files that were created 10 years from now, accessed two years ago and never modified. Transmogrify is similarly wise to the standard procedures of forensic investigators. It allows the attacker to change information in the header of a file, a space normally invisible to the user. Typically, if you changed the extension of a file from, say, .jpg to .doc, the header would still call it a .jpg file and header analysis would raise a red flag that someone had messed with the file. Transmogrify alters the header along with the file extension so that the analysis raises no red flags. The forensic tools see something that always was and remains a .doc file. Slacker would probably be in the movie too. It breaks up a file and stashes the pieces in the slack space left at the end of files. Imagine you stole the Dead Sea Scrolls, ripped them into thousands of small pieces, and then tucked those pieces, individually, into the backs of books. That’s Slacker, only Slacker is better because you can reassemble the data and, while hidden, the data is so diffuse that it looks like random noise to forensic tools, not the text file containing thousands of credit card numbers that it actually is. Another tool, Sam Juicer, retrieves encrypted passwords but leaves behind no evidence it was ever run, allowing you to crack the passwords later offline. KY stuffs data into null directory entries, which will still look null to the outside world. Data Mule infiltrates hard disk drives’ normally off-limits reserved space. Randomizers auto-generate random file names to evade signature-based inspection. There are tools that replace Roman letters with identical-looking Cyrillic ones to avoid suspicion and inspection. In other words, you need explorer.exe to run your computer, but you don’t need explorer.exe, which looks the same but actually starts with a Cyrillic “e” and is a keylogger. If you want to go full-out cloak-and-dagger in your movie, you’d show off antiforensic tools that have gone solid-state. Diskless A-F is the state of the art; it avoids logging of activity all together. “There’s nothing on the disk that can’t be messed with,” says Liu. “So the arms race has left the disk and is moving into memory. Memory is volatile storage. It’s a lot more difficult to understand what’s going on in there. Disk layout is documented; you know where to look for stuff. In memory, stuff moves around; you can’t track it down.” MosDef is one example of diskless antiforensics. It executes code in memory. Many rootkits now load into memory; some use the large stockpiles of memory found on graphics cards. Linux servers have become a favorite home for memory- resident rootkits because they’re so reliable. Rebooting a computer resets its memory. When you don’t have to reboot, you don’t clear the memory out, so whatever is there stays there, undetected. “You’ve got 128 megs of RAM in network printers that are never shut off!” exclaims Michael Davis, CEO of incident response company Savid Technologies and a veteran security researcher who worked on the Honeynet Project. “It’s an old technique, but a common one.” Antiforensics Tools That Appear Legitimate on First Blush Perhaps less sexy—but just as problematic to the forensic investigator—are antiforensic tools that fall into a gray middle on the spectrum of legitimacy. These include tools like packers, which pack executable files into other files. In the aquarium case, the criminal most likely used a packer to attach his rootkit to the audio file. Binders bind two executables into one, an especially dangerous tool when one of the executables is legitimate. I might have no concern clicking on firefox.exe, for example, but it could very well be bound to keylogger.exe. Virtualization is a popular trend in IT now, because it allows one machine to run many environments. Hackers simply apply the principle to their jobs; one of the virtual environments borrowing the hardware becomes theirs. Steganography—hiding data in other data—has legitimate uses for the privacy conscious, but then criminals breaking into systems are privacy conscious too. A great way to transport data you’re not supposed to have is to hide it where it will generate no suspicion, like in photos of executives that the marketing department keeps on the network. (Disagreement reigns over the prevalence of steganography as an antiforensic technique in practice; no one disputes its capabilities or increasing ease of use, though). Disk wiping systems are valuable for refreshing and decommissioning hard disks on machines, and boosting performance. But they also serve the criminal who needs to erase his digital tracks. Some data wiping programs have been tuned to thwart the specific programs that criminals know are popular with forensic investigators, like EnCase, and they are marketed that way. The most prosaic antiforensic tools are also the most common. Security software like encryption and VPN tunneling serve as foundations of the criminal hacker’s work once he’s infiltrated a system. “In one case, we found a large retail database that was compromised,” says Sartin. “And the first thing the hackers did when they got there was install a client VPN,” and at that point, they became virtually invisible. Another classic antiforensic technique is to partition a hard drive and encrypt one section of it, then partition that partition and encrypt a subsection of that. “Any data in that second partition I can deny ever existed,” says Henry. “Then the bad guy who is caught gives up the password or key for the first partition, which typically contains only moderately bad stuff. The really bad stuff is in the second partition, but the investigators have no clue it’s there. Forensic tools wouldn’t see the second partition; it would look like random trash.” These techniques are not sexy—they might not make it into the movie—but in some ways they’re actually the most problematic antiforensic tools, because there are excellent reasons to continually improve encryption, secure remote access, disk partitioning and virtual environments. Better encryption stands to protect data and privacy. Secure tunnels make remote business over the Internet feasible. Virtualization is an efficiency boon. And yet, improving these products also happens to improve the criminal’s antiforensic toolkit in lockstep. This list is only a sample of the tools used for antiforensics. Many others do clever things, like block reverse engineering of code or purposefully leave behind misleading evidence to send forensic investigators down the wrong path, wasting their time and money. Taken at its most broad, antiforensics even extends to physical techniques, like degaussing hard drives or taking a sledgehammer to one. The portfolio of techniques available, for free or for a low cost, is overwhelming. An antiforensic pioneer and hacker who calls himself the Grugq (sounds like “grug”) says he once presented this kind of primer on antiforensics to the police’s largest computer forensics unit in London. “It was packed with all these mean-looking coppers,” he recalls. “And here I am, this computer security guy saying, ‘You’re all [screwed] and there’s nothing you can do about it.’ When I finished, it was quiet. Only one person raised his hand. Scary geezer. Six-two, shaved head. Tattoos all over his arms. I thought he might thump me. “But he stood up and looked like he was about to cry. All he said was, ‘Why are you doing this?’” Why Are They Developing Antiforensic Tools? As long as five years ago, Grugq was creating antiforensic tools. Data Mule is one in his package that he calls the Defiler’s Toolkit. Likewise, Liu developed Timestomp, Slacker and other tools for the Metasploit Framework. In fact, a good portion of the antiforensic tools in circulation come from noncriminal sources, like Grugq and Liu and plain old commercial product vendors. It’s fair to ask them, as the overwhelmed cop in London did, why develop and distribute software that’s so effective for criminals? Grugq’s answer: “If I didn’t, someone else would. I am at least pretty clean in that I don’t work for criminals, and I don’t break into computers. So when I create something, it only benefits me to get publicity. I release it, and that should encourage the forensics community to get better. I am thinking, Let’s fix it, because I know that other people will work this out who aren’t as nice as me. Only, it doesn’t work that way. The forensics community is unresponsive for whatever reason. As far as that forensic officer [in London] was concerned, my talk began and ended with the problem.” Antiforensics Tools Reveal Vulnerabilities in Computer Forensics Tools Liu agrees but takes it further. He believes developing antiforensics is nothing less than whistle-blowing. “Is it responsible to make these tools available? That’s a valid question,” he says. “But forensic people don’t know how good or bad their tools are, and they’re going to court based on evidence gathered with those tools. You should test the validity of the tools you’re using before you go to court. That’s what we’ve done, and guess what? These tools can be fooled. We’ve proven that.” For any case that relies on digital forensic evidence, Liu says, “It would be a cakewalk to come in and blow the case up. I can take any machine and make it look guilty, or not guilty. Whatever I want.” Liu’s goal is no less than to upend a legal precedent called the presumption of reliability. In a paper that appeared in the Journal of Digital Forensic Practice, Liu and coauthor Eric Van Buskirk flout the U.S. courts’ faith in digital forensic evidence. Liu and Van Buskirk cite a litany of cases that established, as one judge put it, computer records’ “prima facie aura of reliability.” One decision even said computer records were “uniquely reliable in that they were computer-generated rather than the result of human entries.” Liu and Van Buskirk take exception. The “unfortunate truth” they conclude, is that the presumption of reliability is “unjustified” and the justice system is “not sufficiently skeptical of that which is offered up as proof.” It’s nearly a declaration that, when it comes to digital information, there’s no such thing as truth. Legally anyway. As Henry likes to put it, “Antiforensic tools have rendered file systems as no longer being an accurate log of malicious system activity.” Computer forensics in some ways is storytelling. After cordoning off the crime scene by imaging the hard drive, the investigator strings together circumstantial evidence left at the scene, and shapes it into a convincing story about who likely accessed and modified files and where and when they probably did it. Antiforensics, Liu argues, unravels that narrative. Evidence becomes so circumstantial, so difficult to have confidence in, that it’s useless. “The classic problem already with electronic crimes has been, How do you put the person you think committed a crime behind the guilty machine they used to commit the crime?” says Brian Carrier, another forensic researcher, who has worked for the Cerias infosecurity research program at Purdue University. Upending the presumption of reliability, he says, presents a more basic problem: How do you prove that machine is really guilty in the first place? “I’m surprised it hasn’t happened yet,” says Liu. “But it will.” Under the current computing infrastructure, data is untrustworthy, then. The implications of this, of courts limiting or flat-out denying digital forensics as reliable evidence, can’t be understated. Without the presumption of reliability, prosecution becomes a more severe challenge and thus, a less appealing option. Criminals reasonably skilled with antiforensics would operate with a kind of de facto legal immunity. Making It Not Worth It Despite all that, casting doubt over evidence is just a secondary benefit of antiforensics for criminals. Usually cases will never get to the legal phase because antiforensics makes investigations a bad business decision. This is the primary function of antiforensics: Make investigations an exercise in throwing good money after bad. It becomes so costly and time-consuming to figure out what happened, with an increasingly limited chance that figuring it out will be legally useful, that companies abandon investigations and write off their losses. “Business leaders start to say, ‘I can’t be paying $400 an hour for forensics that aren’t going to get me anything in return,’” says Liu. “The attackers know this. They contaminate the scene so badly you’d have to spend unbelievable money to unravel it. They make giving up the smartest business decision.” “You get to a point of diminishing returns,” says Sartin. “It takes time to figure it out and apply countermeasures. And time is money. At this point, it’s not worth spending more money to understand these attacks conclusively.” One rule hackers used to go by, says Grugq, was the 17-hour rule. “Police officers [in London’s forensics unit] had two days to examine a computer. So your attack didn’t have to be perfect. It just had to take more than two eight-hour working days for someone to figure out. That was like an unwritten rule. They only had those 16 hours to work on it. So if you made it take 17 hours to figure out, you win.” Since then, Grugq says, law enforcement has built up 18-month backlogs on systems to investigate, giving them even less time per machine. “Time and again I’ve seen it,” says Liu. “They start down a rat hole with an investigation and find themselves saying, ‘This makes no sense. We’re not running a business to do an investigation.’ I’ve seen it at Fortune 100s. The company says, ‘We think we know what they got and where. Let’s close it up.’ Because they know that for every forensic technique they have, there’s an antiforensic answer. Unfortunately, the converse isn’t true.” The Rise of Antiforensics Tools Will Force Computer Investigators to Change By now, it should be clear why Henry of Secure Computing has been giving a presentation called “Anti-Forensics: Considering a Career in Computer Forensics? Don’t Quit Your Day Job.” The state of forensics certainly sounds hopeless, and Henry himself says, “The forensics community, there’s not a hell of a lot they can do.” But in fact there’s some hope. Carrier says, “Yes, it makes things a lot harder, but I don’t think it’s the end of the world by any means.” What can start to turn the tables on the bad guys, say these experts and others, is if investigators embrace a necessary shift in thinking. They must end the cat-and-mouse game of hack-defend-hack-defend. Defeating antiforensics with forensics is impossible. Investigations, instead, must downplay the role of technology and broaden their focus on physical investigation processes and techniques: intelligence, human interviews and interrogations, physical investigations of suspects’ premises, tapping phones, getting friends of suspects to roll over on them, planting keyloggers on suspects’ computers. There are any number of ways to infiltrate the criminal world and gather evidence. In fact, one of the reasons for the success of antiforensics has been the limited and unimaginative approach computer forensic professionals take to gathering evidence. They rely on the technology, on the hard disk image and the data dump. But when evidence is gathered in such predictable, automated ways, it’s easy for a criminal to defeat that. “I go back to my background as a homicide detective,” says the investigator in the aquarium case. “In a murder investigation, there is no second place. You have to win. So you come at it from every angle possible. You think of every way to get to where you want to go. Maybe we can’t find the source on the network with a scanning tool. So you hit the street. Find a boss. His boss. His boss. You find the guy selling data on the black market. The guy marketing it on [Internet Relay Chat]. You talk to them. They’re using stego? Maybe we drop some stego on them. The techniques used in physical investigations are becoming increasingly important.” Indeed, if one looks back on some of the major computer crimes in which suspects were caught, one will notice that rarely was it the digital evidence that led to their capture. In the case of Jeffrey Goodin of California, the first ever under the Can-Spam Act, it was a recorded phone call with a friend who had flipped on the suspect that led to the conviction. In the case of the Russian botnet operators who had extorted millions from gaming sites, it was an undercover operation in which a “white hat” hacker befriended the criminals. In the United Kingdom, says Grugq, the police are using social modeling to try to penetrate antiforensics used on mobile phones for drug dealing. “The police’s goal is to get a confession,” he says. “They don’t care if they have compelling evidence off the disk.” In the TJX case, the only arrests made to date are based on purchases of exorbitant gift cards at the company’s retail stores, caught on tape. It will be the interviews with those people, and not system analysis, that will lead to more information and, potentially, more arrests in the case. “Every successful forensics case I’ve worked on turned into a physical security investigation,” says Bill Pennington, a researcher at White Hat Security and veteran technical forensics investigator. “In one case, it was an interview with someone who turned on someone else. You layer the evidence. Build it up. He sees the writing on the wall, and he cracks. But if we had to rely on what the computer evidence told us, we would have been stuck.” Moving Targets Behind the portfolio of easy-to-use Windows-based antiforensic tools, criminal hackers are building up a next-generation arsenal of sophisticated technical tools that impress even veterans like Grugq. “There are now direct attacks against forensic tools,” he says. “You can rootkit the analysis tool and tell it what not to see, and then store all your evil stuff in that area you told the analysis tool to ignore. It is not trivial to do, but finding the flaw in the analysis tool to exploit is trivial.” Another new technique involves scrambling packets to avoid finding data’s point of origin. The old-school way of avoiding detection was to build up a dozen or so “hop points” around the world—servers you bounced your traffic off of that confounded investigations because of the international nature of the traffic and because it was just difficult to determine where the traffic came from, really. The state-of-the-art antiforensic technique is to scramble the packets of data themselves instead of the path. If you have a database of credit card information, you can divvy it up and send each set of packets along a different route and then reassemble the scatterlings at the destination point—sort of like a stage direction in a play for all the actors to go wherever as long as they end up on their mark. The aquarium attack, two years later, already bears tinges of computer crime antiquity. It was clever but today is hardly state of the art. Someday, the TJX case will be considered ordinary, a quaint precursor to an age of rampant electronic crime, run by well-organized syndicates and driven by easy-to-use, widely available antiforensic tools. Grugq’s hacking mentor once said it’s how you behave once you have root access that’s interesting. In a sense, that goes for the good guys too. They’ve got root now. How are they going to behave? What are they going to do with it? “We’ve got smarter good guys than bad guys right now,” says Savid Technologies’ Davis. “But I’m not sure how long that will be the case. If we don’t start dealing with this, we’re not even going to realize when we get hit. If we’re this quiet community, not wanting to talk about it, we’re going to get slammed.” http://www.cio.com/article/114550  China Crafts Cyberweapons The Defense Department reports China is building cyberwarfare units and developing viruses. Sumner Lemon The People's Liberation Army (PLA) continues to build cyberwarfare units and develop viruses to attack enemy computer systems as part of its information-warfare strategy, the U.S. Department of Defense (DOD) warned in a report released on Friday. "The PLA has established information warfare units to develop viruses to attack enemy computer systems and networks," the annual DOD report on China's military warned. At the same, Chinese armed forces are developing ways to protect its own systems from an enemy attack, it said, echoing similar warnings made in previous years. These capabilities are part of China's ongoing military modernization efforts, which have seen the country add dozens of high-tech fighters and ballistic missiles to its arsenal. China isn't alone in building the capability to attack an enemy's computer systems. The U.S. and other countries have developed similar abilities. The PLA's virus-writing efforts have been underway for years, reflecting the importance that China apparently attaches to information warfare. As early as 2000, the DOD warned, "China has the capability to penetrate poorly protected U.S. computer systems and potentially could use CNA [computer network attacks] to attack specific U.S. civilian and military infrastructures." In recent years, the PLA has begun training more seriously for computer attacks, including them as part of larger military exercises in 2005. The main focus of China's military modernization efforts are Taiwan, an island nation that China views as a renegade province. The two separated in 1949 after a civil war between the Communist and Nationalist armies, with the Nationalist forces retreating to Taiwan. China has long threatened to attack Taiwan if the island formally declares independence, and the expansion of China's military capabilities are largely geared towards a possible attack against Taiwan. "A limited military campaign could include computer network attacks against Taiwan’s political, military, and economic infrastructure to undermine the Taiwan population’s confidence in its leadership," the report said. But the U.S., which would likely intervene in a Chinese attack on Taiwan, is also a potential target, it said. http://www.pcworld.com/article/id,13...icle.html(News)  Cyberattack in Estonia--What it Really Means Robert Vamosi When it comes to denial-of-service attacks, Jose Nazario has seen just about everything. As senior security researcher at Arbor Networks, Nazario closely monitors network attacks. A denial-of-service, or DoS, attack occurs when someone directs a large number of requests to a target URL so quickly that the Web server can't respond, and the site becomes inaccessible. A distributed denial-of-service, or DDoS, attack occurs when hundreds or thousands of compromised computers are enlisted. Arbor Networks has a tool called the Active Threat Level Analysis System that enables Nazario to collect information on DoS attacks worldwide. On April 27, officials in Estonia relocated the "Bronze Soldier," a Soviet-era war memorial commemorating an unknown Russian who died fighting the Nazis. The move incited rioting by ethnic Russians and the blockading of the Estonian Embassy in Moscow. The event also marked the beginning of a large and sustained distributed denial-of-service attack on several Estonian national Web sites, including those of government ministries and the prime minister's Reform Party. Nazario was one of the first to publish information about those cyberattacks. He spoke with CNET in the wake of the events in Estonia. Q: Have there been any previous attacks comparable to the cyberattack situation in Estonia? Nazario: Compared to larger, higher-profile attacks, it isn't necessarily larger than the rogue DNS (domain name system) server attack this past winter, no larger than the attacks resulting from the Olympics a few years ago with the Apolo Ohno controversy. (In 2002 at the Salt Lake City Games, Ohno won the gold medal in the 1,500-meter speed-skating race after South Korean Kim Dong-Sung was disqualified; soon after, several United States-based servers were hit with a DDoS attack from machines that appeared to be based in South Korea.) The Estonia attacks certainly are overwhelming and crippling many of those sites in Estonia based upon the resources that they have. But it's the background nature of those attacks that's novel, in comparison to other denial-of-service attacks. There's no extortion going on. They're not demanding to the Ministry of Finance, the Ministry of Agriculture, "Pay us $50 million, or we keep this up." They're not trying to disrupt e-commerce--they're making a political statement. So the size isn't necessarily groundbreaking. We're talking about 100 or 200 megabits per second. Looking at our infrastructure surveys that we have published--and we have one going on currently for release later this year--we have seen that this is on the low side of an average size of attack on providers that we talk to, who run our products or don't run our products, who participate in our survey. It's kind of a common-size attack. Would the Estonia event be comparable to the India-Pakistan cyberconflict of a few years ago? I recall volleys of nationalistic viruses sent between the two countries with some DoS attacks thrown in. Nazario: Yes, definitely, though it's probably more applicable to the Apolo Ohno situation, where you have a nationalistic driver behind the DDoS attack. We saw some specific tools created (for the Olympic attack), as well as some botnets that were under the control of people who were emotionally attached to the events. Attacks were launched against a specific target based upon national interests or based upon geopolitical interests. A recent blog of yours suggested that a variety of different DoS methods were used on the Estonia sites. Does that support the theory that random sympathetic individuals, say in Russia, may be behind the attacks, as opposed to an organized, coordinated attack? Nazario: Not necessarily. While we do think the Estonian attacks are due to multiple, different kinds of botnets, or different tools or different groups, all with sort of a same angle behind them, the fact that the attacks are different in their nature isn't necessarily the indication there that comes from other kinds of analysis. We have, in the past, seen DoS attackers interested in keeping their attack effective by changing the tactics as they go along. And they will keep on changing the attack as it goes on. They'll change locations, if they have a big enough botnet; sources, if they can overwhelm the defenses that selectively look at different kinds of sources; or the individual traffic types or packet types to overwhelm protocol-based defenses on the perimeter of the network. That said, we have seen evidence suggesting that there were multiple botnets and tools--both botnet-related and not botnet-related--behind the Estonian attacks. We have seen this based upon some analysis of existing botnets that we and others are tracking, as well as monitoring forums and software releases where people are encouraging others to show their displeasure with Estonia--in this case, by launching these attacks. Might we see other DDoS attacks in the very near future? Or is the Estonian situation just a one-off, a response to a specific event? Nazario: I don't think it's a one-off. You mentioned the India-Pakistan issues; I mentioned the South Korean Olympic issues from several years ago. We have seen this kind of thing before. You look around the globe, and there's basically no limit to the amount of skirmishes between well-connected countries that could get incredibly emotional for the population at large. In this case, it has disrupted the Estonian government's ability to work on online, it has disrupted a lot of its resources and attention. In that respect, it's been effective. It hasn't brought the government to a crippling halt, but has essentially been effective as a protest tool. People will probably look at this and say, "That works. I think we're going to continue to do this kind of thing." Depending on the target within the government, it could be very visible, or it could not be very visible. Some countries are probably better equipped to handle this than others. We monitor thousands of DoS events each day in our ATLAS system that comes from our installations around the world and our sensors around the world. The bulk of them are things that are against people you wouldn't even know or existed--just random people, people on broadband lines--where someone gets upset with them online and says "I'm going to make your life uncomfortable for the next hour or two." We do see attacks against big corporations and big governments, and if you look at those attacks, some of them are probably politically motivated as a way of speaking out. I don't think this is going to become as common as seeing people on the streets. But it's something that some governments have to consider much more than I think they needed to five years ago. You mentioned distractions. Is it a matter of the Estonian government sites filtering their traffic? Nazario: It's not just within the Estonian government but also within their providers. The Estonian providers are, of course, working with a much larger community--the European providers, the North American providers (and) Asian providers that give them inbound traffic as well as the attack traffic. They're working with people to identify the root cause of these attacks and shut them down, as well as push the traffic back even further to alleviate those problems without disrupting normal service. The number of people required to help them do this is rather high, given the size of the staff that they have and that they don't normally see those kinds of things. A couple of Estonian service providers have been under denial-of-service attack for the past six months to a year, by a virus called Allaple, and we're not clear as to what the author's trying to do other than upset some people in Estonia. It doesn't appear to have as clear a cause or reason behind it as these recent attacks against the Estonian government sites. We know that they're scrambling, and we're working with folks from the Estonian Computer Emergency Response Team and the region, as well as the Estonian providers, to deal with it. We know that they've been working on this for quite a while, a number of weeks, really reaching out, and it is a very high-focus, high-priority item for them. The attacks haven't stopped, have they? Nazario: We know they haven't stopped, but we're not seeing them with such intensity right now. http://news.com.com/Cyberattack+in+E...3-6186751.html  Noise Keeps Spooks Out of the Loop D. Jason Palmer SPYING is big business, and avoiding being spied on an even bigger one. So imagine if someone came up with a simple, cheap way of encrypting messages that is almost impossible to hack into? American computer engineer Laszlo Kish at Texas A&M University in College Station claims to have done just that. He says the thermal properties of a simple wire can be exploited to create a secure communications channel, one that outperforms quantum cryptography keys. His cipher device, which he first proposed in 2005, exploits a property called thermal noise. Thermal noise is generated by the natural agitation of electrons within a conductor, which happens regardless of any voltage passed through it. But it does change depending on the conductor's resistance. Kish and his collaborators at the University of Szeged in Hungary say this can be used to securely pass information, or an encryption key, down any wire, including a telephone line or network cable. In their device, both the sender Alice and the receiver Bob have an identical pair of resistors, one producing high resistance, the other low resistance. The higher the total resistance on the line, the greater the thermal noise. Both Alice and Bob randomly choose which resistor to use. A quarter of the time they will both choose the high resistor, producing a lot of noise on the line, while a quarter of the time they will both choose the low resistor, producing little noise. If either detect a high or a low amount of noise in the line, they ignore any communication. Half the time, however, they will choose differently, producing an intermediate level of thermal noise, and it is now that a message can be sent. If Bob turns on his high resistor, and records an intermediate level of noise, he instantly knows that Alice has chosen her low resistor, in essence sending a bit of information such as 1 or 0. Kish's cipher does this many times, sending a random series of 1s and 0s that can form the basis of an encryption key, the researchers say (http://www.arxiv.org/abs/physics/0612153). That message is also secure. For a start, as Kish notes, it takes an "educated eavesdropper" to even realise information is being sent when there seems to be just low-level noise on the line. If they do try to eavesdrop, they can only tell a message is being sent, not what it is, because it's impossible to tell whether Alice has a high or low resistor turned on, and whether the bit of information is a 1 or a 0. What's more, eavesdropping on the line will naturally alter the level of thermal noise, so Alice and Bob will know that someone is listening in. Kish and his team have now successfully built a device that can send a secure message down a wire 2000 kilometres long, much further than the best quantum key distribution (QKD) devices tried so far. Tests show a signal sent via Kish's device is received with 99.98 per cent accuracy, and that a maximum of just 0.19 per cent of the bits sent are vulnerable to eavesdropping. The error rate is down to the inherent resistance of the wire, and choosing a larger wire in future models should help reduce it further. However, this level of security already beats QKD. What's more, the system works with fixed lines, rather than the optical fibres used to carry photons of light at the heart of quantum encryption devices. It is also more robust, as QKD devices are vulnerable to corruption by dust, heat and vibration. It is also much cheaper. "I guess it's around a hundred dollars, at most," Kish says. "This is a system that should be taken seriously," says security specialist Bruce Schneier, who founded network security firm BT Counterpane. He says he was seduced by the simplicity of the idea when it was first proposed by Kish, and now wants to see independent tests of the working model. "I desperately want someone to analyse it," he says. "Assuming it works, it's way better than quantum." http://www.newscientisttech.com/chan...mg19426055.300  The Corporate Takeover of U.S. Intelligence The U.S. government now outsources a vast portion of its spying operations to private firms -- with zero public accountability. Tim Shorrock Jun. 01, 2007 | More than five years into the global "war on terror," spying has become one of the fastest-growing private industries in the United States. The federal government relies more than ever on outsourcing for some of its most sensitive work, though it has kept details about its use of private contractors a closely guarded secret. Intelligence experts, and even the government itself, have warned of a critical lack of oversight for the booming intelligence business. On May 14, at an industry conference in Colorado sponsored by the Defense Intelligence Agency, the U.S. government revealed for the first time how much of its classified intelligence budget is spent on private contracts: a whopping 70 percent. Based on this year’s estimated budget of at least $48 billion, that would come to at least $34 billion in contracts. The figure was disclosed by Terri Everett, a senior procurement executive in the Office of the Director of National Intelligence, the agency established by Congress in 2004 to oversee the 16 agencies that make up the U.S. intelligence infrastructure. A copy of Everett's unclassified PowerPoint slide presentation, titled "Procuring the Future" and dated May 25, was obtained by Salon. (It has since become available on the DIA's Web site.) "We can't spy ... If we can't buy!" one of the slides proclaims, underscoring the enormous dependence of U.S. intelligence agencies on private sector contracts. The DNI figures show that the aggregate number of private contracts awarded by intelligence agencies rose by about 38 percent from the mid-1990s to 2005. But the surge in outsourcing has been far more dramatic measured in dollars: Over the same period of time, the total value of intelligence contracts more than doubled, from about $18 billion in 1995 to about $42 billion in 2005. "Those numbers are startling," said Steven Aftergood, the director of the Project on Government Secrecy at the Federation of American Scientists and an expert on the U.S. intelligence budget. "They represent a transformation of the Cold War intelligence bureaucracy into something new and different that is literally dominated by contractor interests." Because of the cloak of secrecy thrown over the intelligence budgets, there is no way for the American public, or even much of Congress, to know how those contractors are getting the money, what they are doing with it, or how effectively they are using it. The explosion in outsourcing has taken place against a backdrop of intelligence failures for which the Bush administration has been hammered by critics, from Saddam Hussein's fictional weapons of mass destruction to abusive interrogations that have involved employees of private contractors operating in Iraq, Afghanistan and Guantánamo Bay, Cuba. Aftergood and other experts also warn that the lack of transparency creates conditions ripe for corruption. Trey Brown, a DNI press officer, told Salon that the 70 percent figure disclosed by Everett refers to everything that U.S. intelligence agencies buy, from pencils to buildings to "whatever devices we use to collect intelligence." Asked how much of the money doled out goes toward big-ticket items like military spy satellites, he replied, "We can't really talk about those kinds of things." The media has reported on some contracting figures for individual agencies, but never before for the entire U.S. intelligence enterprise. In 2006, the Washington Post reported that a "significant majority" of the employees at two key agencies, the National Counterterrrorism Center and the Pentagon's Counter-Intelligence Field Activity office, were contractors (at CIFA, the number was more than 70 percent). More recently, former officers with the Central Intelligence Agency have said the CIA's workforce is about 60 percent contractors. But the statistics alone don't even show the degree to which outsourcing has penetrated U.S. intelligence -- many tasks and services once reserved exclusively for government employees are being handled by civilians. For example, private contractors analyze much of the intelligence collected by satellites and low-flying unmanned aerial vehicles, and they write reports that are passed up to the line to high-ranking government officials. They supply and maintain software programs that can manipulate and depict data used to track terrorist suspects, both at home and abroad, and determine what targets to hit in hot spots in Iraq and Afghanistan. Such data is also at the heart of the National Security Agency's massive eavesdropping programs and may be one reason the DNI is pushing Congress to grant immunity to corporations that may have cooperated with the NSA over the past five years. Contractors also provide collaboration tools to help individual agencies communicate with each other, and they supply security tools to protect intelligence networks from outside tampering. Outsourcing has also spread into the realm of human intelligence. At the CIA, contractors help staff overseas stations and provide disguises used by agents working under cover. According to Robert Baer, the former CIA officer who was the inspiration for the character played by George Clooney in the film "Syriana," a contractor stationed in Iraq even supervises where CIA agents go in Baghdad and whom they meet. "It's a completely different culture from the way the CIA used to be run, when a case officer determined where and when agents would go," he told me in a recent interview. "Everyone I know in the CIA is leaving and going into contracting whether they're retired or not." The DNI itself has voiced doubts about the efficiency and effectiveness of outsourcing. In a public report released last fall, the agency said the intelligence community increasingly "finds itself in competition with its contractors for our own employees." Faced with arbitrary staffing limits and uncertain funding, the report said, intelligence agencies are forced "to use contractors for work that may be borderline 'inherently governmental'" -- meaning the agencies have no clear idea about what work should remain exclusively inside the government versus work that can be done by civilians working for private firms. The DNI also found that "those same contractors recruit our own employees, already cleared and trained at government expense, and then 'lease' them back to us at considerably greater expense." A Senate Intelligence Committee report released on Thursday spells out the costs to taxpayers. It estimates that the average annual cost for a government intelligence officer is $126,500, compared to the average $250,000 (including overhead) paid by the government for an intelligence contractor. "Given this cost disparity," the report concluded, "the Committee believes that the Intelligence Community should strive in the long-term to reduce its dependence upon contractors." The DNI began an intensive study of contracting last year, but when its "IC Core Contractor Inventory" report was sent to Congress in April, DNI officials refused to release its findings to the public, citing risks to national security. The next month, a report from the House Permanent Select Committee on Intelligence rebuked the DNI in unusually strong language, concluding that U.S. officials "do not have an adequate understanding of the size and composition of the contractor work force, a consistent and well-articulated method for assessing contractor performance, or strategies for managing a combined staff-contractor workforce." U.S. intelligence budgets are classified, and all discussions about them in Congress are held in secret. Much of the information, however, is available to intelligence contractors, who are at liberty to lobby members of Congress about the budgets, potentially skewing policy in favor of the contractors. For example, Science Applications International Corp., one of the nation's largest intelligence contractors, spent $1,330,000 in their congressional lobbying efforts in 2006, which included a focus on the intelligence and defense budgets, according to records filed with the Senate's Office of Public Records. The public, of course, is completely excluded from these discussions. "It's not like a debate when someone loses," said Aftergood. "There is no debate. And the more work that migrates to the private sector, the less effective congressional oversight is going to be." From that secretive process, he added, "there's only a short distance to the Duke Cunninghams of the world and the corruption of the process in the interest of private corporations." In March 2006, Randy "Duke" Cunningham, R-Calif., who had resigned from Congress several months earlier, was sentenced to eight years in prison after being convicted of accepting more than $2 million in bribes from executives with MZM, a prominent San Diego defense contractor. In return for the bribes, Cunningham used his position on the House appropriations and intelligence committees to win tens of millions of dollars' worth of contracts for MZM at the CIA and the Pentagon's CIFA office, which has been criticized by Congress for spying on American citizens. The MZM case deepened earlier this month when Kyle "Dusty" Foggo, the former deputy director of the CIA, was indicted for conspiring with former MZM CEO Brent Wilkes to steer contracts toward the company. U.S. intelligence agencies have always relied on private companies for technology and hardware. Lockheed built the famous U-2 spy plane under specifications from the CIA, and dozens of companies, from TRW to Polaroid to Raytheon, helped develop the high-resolution cameras and satellites that beamed information back to Washington about the Soviet Union and its military and missile installations. The National Security Agency, which was founded in the early 1950s to monitor foreign communications and telephone calls, hired IBM, Cray and other companies to make the supercomputers that helped the agency break encryption codes and transform millions of bits of data into meaningful intelligence. By the 1990s, however, commercial developments in encryption, information technology, imagery and satellites had outpaced the government's ability to keep up, and intelligence agencies began to turn to the private sector for technologies they once made in-house. Agencies also turned to outsourcing after Congress, as part of the "peace dividend" that followed the end of the Cold War, cut defense and intelligence budgets by about 30 percent. When the National Geospatial-Intelligence Agency was created in 1995 as the primary collection agency for imagery and mapping, for example, it immediately began buying its software and much of its satellite imagery from commercial vendors; today, half of its 14,000 workers are full-time equivalent contractors who work inside NGA facilities but collect their paychecks from companies like Booz Allen Hamilton and Lockheed Martin. In the late 1990s, the NSA began outsourcing its internal telecommunications and even some of its signals analysis to private companies, such as Computer Services Corp. and SAIC. Outsourcing increased dramatically after 9/11. The Bush administration and Congress, determined to prevent further terrorist attacks, ordered a major increase in intelligence spending and organized new institutions to fight the war on terror, such as the National Counterterrorism Center. To beef up these organizations, the CIA and other agencies were authorized to hire thousands of analysts and human intelligence specialists. Partly because of the big cuts of the 1990s, however, many of the people with the skills and security clearances to do that work were working in the private sector. As a result, contracting grew quickly as intelligence agencies rushed to fill the gap. That increase can be seen in the DNI documents showing contract award dollars: Contract spending, based on the DNI data and estimates from this period, remained fairly steady from 1995 to 2001, at about $20 billion a year. In 2002, the first year after the attacks on New York and Washington, contracts jumped to about $32 billion. In 2003 they jumped again, reaching about $42 billion. They have remained steady since then through 2006 (the DNI data is current as of last August). Because nearly 90 percent of intelligence contracts are classified and the budgets kept secret, it's difficult to draw up a list of top contractors and their revenues derived from intelligence work. Based on publicly available information, including filings from publicly traded companies with the Securities and Exchange Commission and company press releases and Web sites, the current top five intelligence contractors appear to be Lockheed Martin, Northrop Grumman, SAIC, General Dynamics and L-3 Communications. Other major contractors include Booz Allen Hamilton, CACI International, DRS Technologies and Mantech International. The industry's growth and dependence on government budgets has made intelligence contracting an attractive market for former high-ranking national security officials, like former CIA director George Tenet, who now earns millions of dollars working as a director and advisor to four companies that hold contracts with U.S. intelligence agencies and do big business in Iraq and elsewhere. Congress, meanwhile, is beginning to ask serious questions about intelligence outsourcing and how lawmakers influence the intelligence budget process. Some of that interest has been generated by the Cunningham scandal. In another recent case, Rep. Rick Renzi, a Republican from Arizona, resigned from the House Intelligence Committee in April because he is under federal investigation for introducing legislation that may have benefited Mantech International, a major intelligence contractor where Renzi's father works in a senior executive position. In the Cunningham case, many of MZM's illegal contracts were funded by "earmarks" that he inserted in intelligence bills. Earmarks, typically budget items placed by lawmakers to benefit projects or companies in their district, are often difficult to find amid the dense verbiage of legislation -- and in the "black" intelligence budgets, they are even harder to find. In its recent budget report, the House Intelligence Committee listed 26 separate earmarks for intelligence contracts, along with the sponsor's name and the dollar amount of the contract. The names of the contractors, however, were not included in the list. Both the House and Senate are now considering intelligence spending bills that require the DNI, starting next year, to provide extensive information on contractors. The House version requires an annual report on contractors that might be committing waste and fraud, as well as reviews on its "accountability mechanisms" for contractors and the effect of contractors on the intelligence workforce. The amendment was drafted by Rep. David Price, D-N.C., who introduced a similar bill last year that passed the House but was quashed by the Senate. In a statement on the House floor on May 10, Price explained that he was seeking answers to several simple questions: "Should (contractors) be involved in intelligence collection? Should they be involved in analysis? What about interrogations or covert operations? Are there some activities that are so sensitive they should only be performed by highly trained Intelligence Community professionals?" If either of the House or Senate intelligence bills pass in their present form, the overall U.S. intelligence budget will be made public. Such transparency is critical as contracting continues to expand, said Paul Cox, Price's press secretary. "As a nation," he said, "we really need to take a look and decide what's appropriate to contract and what's inherently governmental." http://www.salon.com/news/feature/20...l_contractors/  Advisers Fault Harsh Methods in Interrogation Scott Shane and Mark Mazzetti As the Bush administration completes secret new rules governing interrogations, a group of experts advising the intelligence agencies are arguing that the harsh techniques used since the 2001 terrorist attacks are outmoded, amateurish and unreliable. The psychologists and other specialists, commissioned by the Intelligence Science Board, make the case that more than five years after the Sept. 11 attacks, the Bush administration has yet to create an elite corps of interrogators trained to glean secrets from terrorism suspects. While billions are spent each year to upgrade satellites and other high-tech spy machinery, the experts say, interrogation methods — possibly the most important source of information on groups like Al Qaeda — are a hodgepodge that date from the 1950s, or are modeled on old Soviet practices. Some of the study participants argue that interrogation should be restructured using lessons from many fields, including the tricks of veteran homicide detectives, the persuasive techniques of sophisticated marketing and models from American history. The science board critique comes as ethical concerns about harsh interrogations are being voiced by current and former government officials. The top commander in Iraq, Gen. David H. Petraeus, sent a letter to troops this month warning that “expedient methods” using force violated American values. In a blistering lecture delivered last month, a former adviser to Secretary of State Condoleezza Rice called “immoral” some interrogation tactics used by the Central Intelligence Agency and the Pentagon. But in meetings with intelligence officials and in a 325-page initial report completed in December, the researchers have pressed a more practical critique: there is little evidence, they say, that harsh methods produce the best intelligence. “There’s an assumption that often passes for common sense that the more pain imposed on someone, the more likely they are to comply,” said Randy Borum, a psychologist at the University of South Florida who, like several of the study’s contributors, is a consultant for the Defense Department. The Bush administration is nearing completion of a long-delayed executive order that will set new rules for interrogations by the Central Intelligence Agency. The order is expected to ban the harshest techniques used in the past, including the simulated drowning tactic known as waterboarding, but to authorize some methods that go beyond those allowed in the military by the Army Field Manual. President Bush has insisted that those secret “enhanced” techniques are crucial, and he is far from alone. The notion that turning up pressure and pain on a prisoner will produce valuable intelligence is a staple of popular culture from the television series “24” to the recent Republican presidential debate, where some candidates tried to outdo one another in vowing to get tough on captured terrorists. A 2005 Harvard study supported the selective use of “highly coercive” techniques. But some of the experts involved in the interrogation review, called “Educing Information,” say that during World War II, German and Japanese prisoners were effectively questioned without coercion. “It far outclassed what we’ve done,” said Steven M. Kleinman, a former Air Force interrogator and trainer, who has studied the World War II program of interrogating Germans. The questioners at Fort Hunt, Va., “had graduate degrees in law and philosophy, spoke the language flawlessly,” and prepared for four to six hours for each hour of questioning, said Mr. Kleinman, who wrote two chapters for the December report. Mr. Kleinman, who worked as an interrogator in Iraq in 2003, called the post-Sept. 11 efforts “amateurish” by comparison to the World War II program, with inexperienced interrogators who worked through interpreters and had little familiarity with the prisoners’ culture. The Intelligence Science Board study has a chapter on the long history of police interrogations, which it suggests may contain lessons on eliciting accurate confessions. And Mr. Borum, the psychologist, said modern marketing may be a source of relevant insights into how to influence a prisoner’s willingness to provide information. “We have a whole social science literature on persuasion,” Mr. Borum said. “It’s mostly on how to get a person to buy a certain brand of toothpaste. But it certainly could be useful in improving interrogation.” Robert F. Coulam, a research professor and attorney at Simmons College and a study participant, said that the government’s most vigorous work on interrogation to date has been in seeking legal justifications for harsh tactics. Even today, he said, “there’s nothing like the mobilization of effort and political energy that was put into relaxing the rules” governing interrogation. The director of the science board project, Robert A. Fein, a forensic psychologist at Harvard, declined to speak on the record. In a prologue to the December report, the first of a planned series, Mr. Fein said the shortage of research meant that many American interrogators were “forced to ‘make it up’ on the fly,” resulting in “unfortunate cases of abuse.” But associates say Mr. Fein does not want to antagonize intelligence officials, whom he hopes to persuade to bring the reality check of research to bear on interrogation practices. Defenders of the harshest interrogations, particularly as practiced by the C.I.A. at secret overseas sites, say they were carefully devised and have produced valuable intelligence. An agency spokesman, Paul Gimigliano, said the program “has generated a rich volume of intelligence that has helped the United States and other countries disrupt terrorist activities and save innocent lives.” He said the agency’s interrogators were “seasoned, well trained, and have the linguistic resources they need,” and added, “The agency learned terrorist interrogation after 9/11, but — based on the effectiveness of this fully legal program — it learned it well.” A. B. Krongard, who was the executive director of the C.I.A., the No. 3 post at the agency, from 2001 to 2004, agreed with that assessment but acknowledged that the agency had to create an interrogation program from scratch in 2002. He said officers quickly consulted counterparts in Egypt, Saudi Arabia, Israel and other countries to compile a “catalog” of techniques said to be effective against Arab and Muslim prisoners. They added other methods drawn from those that American troops were trained to withstand in case of capture. Mr. Krongard even recalls receiving a proposal for help with questioning Qaeda suspects from an American dentist who said he “could create pain no human being could withstand.” The agency rejected such ideas as ludicrous. But administration lawyers approved a list of harsh methods that have drawn widespread condemnation. In an April lecture, Philip D. Zelikow, the former adviser to Ms. Rice, said it was a grave mistake to delegate to attorneys decisions on the moral question of how prisoners should be treated. Mr. Zelikow, who reviewed the C.I.A. detention program as the executive director of the Sept. 11 commission, said the “cool, carefully considered, methodical, prolonged and repeated subjection of captives to physical torment, and the accompanying psychological terror, is immoral.” Many of the techniques that have come in for such criticism were based on those used in the military’s Survival, Evasion, Resistance and Escape training, or SERE, in which for decades American service members were given a sample of the brutal treatment they might face if captured. Because the training was developed during the cold war, the techniques later adopted by the C.I.A. and Special Operations officers in Iraq were based, at least in part, on how the Soviet Union and its allies were believed to treat prisoners. Such techniques included prolonged use of stress positions, exposure to heat and cold, sleep deprivation and even waterboarding. A report on detainee abuse by the Defense Department’s inspector general, completed in August but declassified and released May 18, gives new details of how the military training was “reverse engineered” for use by American interrogators. It says that as early as 2002, some SERE trainers and some military intelligence officers vehemently objected to the use of the techniques, but their protests were ignored. Senator Carl Levin, a Michigan Democrat and chairman of the Senate Armed Services Committee, said he found the report “very troubling” and intended to hold hearings on how the SERE training methods became the basis for interrogation. “They were put to a purpose that was never intended,” Mr. Levin said. Mr. Kleinman, the former Air Force interrogator who took part in the “Educing Information” study, said the mistakes of the past five years “have made interrogation synonymous in many people’s minds with torture.” But he said the group wanted to redirect the debate toward the future of interrogation. “Our intention is not to point fingers at anyone,” he said. “We’re just saying we have to bring interrogation up to the level of professionalism in other intelligence disciplines.” http://www.nytimes.com/2007/05/30/wa...terrogate.html  Senate Panel Questions C.I.A. Detentions Scott Shane The Senate Intelligence Committee on Thursday questioned the continuing value of the Central Intelligence Agency’s secret interrogation program for terrorism suspects, suggesting that international condemnation and the obstacles it has created to criminal prosecution may outweigh its worth in gathering information. The committee rejected by one vote a Democratic proposal that would essentially have cut money for the program by banning harsh interrogation techniques except in dire emergencies, a committee report revealed. “More than five years after the decision to start the program,” the report said, “the committee believes that consideration should be given to whether it is the best means to obtain a full and reliable intelligence debriefing of a detainee.” It added: “Both the Congress and the administration must continue to evaluate whether having a separate C.I.A. detention program that operates under different interrogation rules than those applicable to military and law enforcement officers is necessary, lawful and in the best interests of the United States.” The sweeping report, which accompanies the annual bill authorizing the activities of all of the spy agencies, reflects a striking reassertion of aggressive oversight since Democrats took control of Congress this year. Some Republicans joined in the skeptical language about several spying programs, and the report as a whole was approved 12 to 3, with the backing of all eight Democrats and four of the seven Republicans. The committee declared that it would block changes sought by the Bush administration in the law governing domestic eavesdropping by the National Security Agency unless it received long-sought administration documents on the secret surveillance program, including orders signed by President Bush. The report criticized the intelligence agencies’ ballooning use of contractors, saying the outsourcing had created conflicts of interest because some major purchasing programs are themselves run by contractors, some of which have ties to vendors. It said a government employee cost taxpayers $126,500 a year on average, or half the $250,000 price tag for a worker supplied by a contracting company. “People are leaving the intelligence agencies for more lucrative job offers with contractors, who send them back to the agencies at far higher cost,” said Andy Johnson, the committee’s staff director. The committee said half of space-related programs, mostly involving spy satellites, had shown cost overruns of 50 percent or more. Such overruns do “severe damage” to the intelligence effort, the committee said, and its proposed bill would require that the president personally certify the necessity of such programs when costs grow more than 40 percent above original estimates. But the most novel element of the report is the assessment of the C.I.A. detention program, which the committee has rarely discussed in public. While only the chairman and the vice chairman were briefed on the program during the first five years after it was created following the 2001 terrorist attacks, all committee members have now been briefed for the first time, the report said. The report acknowledged that the secret detention program “has led to the identification of terrorists and the disruption of terrorist plots.” But it says that achievement must now “be weighed against both the complications it causes to any ultimate prosecution of these terrorists, and the damage the program does to the image of the United States abroad.” Mr. Johnson, the staff director, said the committee’s chairman, Senator John D. Rockefeller IV, Democrat of West Virginia, was concerned that the program might be hurting the battle against terrorism by “alienating moderate Muslim and Arab communities around the world.” Elisa C. Massimino, Washington director of Human Rights First and a longtime critic of the C.I.A. program, said the panel’s statement showed that Congress “is no longer willing to blindly accept the assertion that the C.I.A. secret interrogation program using unlawful techniques serves the national interests of this country.” But the committee stopped short of using its budget authority to shut down the program. In a closed session on May 23, two Democrats, Senators Sheldon Whitehouse of Rhode Island and Dianne Feinstein of California, proposed barring spending on interrogation techniques that go beyond the Army Field Manual, which bans physical pressure or pain. Under their proposal, the only exception would have been when the president determined “that an individual has information about a specific and imminent threat.” The amendment failed when Senator Bill Nelson, Democrat of Florida, joined all the Republicans in voting no. A C.I.A. spokesman, Paul Gimigliano, said the program “has helped our country and others disrupt plots and save lives” and has been “conducted lawfully,” with the approval of “multiple elements of our government, not just the C.I.A.” http://www.nytimes.com/2007/06/01/wa...n/01intel.html  Taking Liberties? Brian Wheeler People will only wake up to the destruction of their civil liberties when it is too late to do anything about it. That is the fear driving a new documentary film which aims to do for civil liberties what Fahrenheit 9/11, Michael Moore's anti-George Bush polemic, did for the anti-war movement. Director Chris Atkins wants Taking Liberties to shake the British public out of their apathy over what he sees as the dangerous erosion of traditional rights and freedoms under Tony Blair. "This film uses shock tactics. We needed to be unashamedly populist. "We wanted to give people a slap around the face and then they can go away and unearth some of the more complex cases," says Atkins. But although it shares a producer - and some stylistic tricks - with Fahrenheit 9/11, Atkins is wary of too many comparisons with Moore's film. Tony Blair was a "handy villain", he says, but it is not enough to try and pin the blame on one political leader who is, in any case, standing down soon. "We didn't want to make the British Fahrenheit. We didn't just want to say 'this guy's an arsehole, let's get rid of him'. "This issue is far more important than one leader. Once you give up traditional liberties such as free speech and the right to protest you are not going to easily get them back," says Atkins. Personal freedom Tony Blair has often insisted that he understands the need to balance new police powers with the protection of civil liberties - but he is also confident he has public opinion on his side when it comes to fighting terror. His argument, as he explains in an archive clip in the film, is that it would only take one more atrocity to silence the civil libertarians, and have people asking why he had not gone further. Atkins' argument - told through a mix of animation, news footage and interviews - is that Labour has over-reacted to the terror threat, using it as an excuse to bring in a series of alarming curbs on personal freedom. "If I had died, I would not have wanted the constitution to be shredded on my behalf," says Rachel North, who was injured in the 7 July attacks, at one point. There are interviews with Walter Wolfgang - the veteran peace campaigner ejected from the 2005 Labour conference and briefly held under anti-terror laws for heckling Jack Straw - and Maya Evans, arrested for breaking the ban on unauthorised protests in Westminster for reading out names of soldiers killed in Iraq near the Cenotaph. Sinister tales? The film also tries to highlight what Atkins sees as the more absurd aspects of new anti-terror laws. There is much footage of gleeful protesters trying to outfox baffled-looking police officers, struggling to apply the new laws. But there are more apparently sinister tales too. In one sequence, climate change protesters picketing an airport are held for a day and a half under anti-terror laws before being released in an unknown location, without phones or money, and told not to speak to each other again. Atkins claims the film is "politically neutral" - the only MPs to give their views are Conservatives Boris Johnson and Ken Clarke and former Labour minister Clare Short. Rendition flights But he says his requests for interviews with senior Labour figures, such as Mr Blair and Jack Straw, were rejected - and found himself being held under anti-terror laws as he attempted to buttonhole Home Secretary John Reid at last year's Labour conference. "We actually interviewed Geoff Hoon but then he refused to appear on film," he adds. Mr Hoon's comments, on the issue of rendition flights, will appear instead in an accompanying book, which like the film will be released next Friday, 8 June. Atkins is a recent convert to the civil liberties cause. Until two years ago, he was a producer of low-budget dramas in Scotland, mostly known for his work with director - and former lead singer of punk band The Skids - Richard Jobson. He says he raised the cash for Taking Liberties by borrowing from friends and persuading his girlfriend to mortgage her flat - "something she won't let me forget." As a result, he says, he is conscious of avoiding the sort of dull but worthy film that will be seen "by about seven people". 'Lefty protesters' He keeps interviews with "civil liberties nerds" - as Liberty chief Shami Chakrabati describes herself at one point - to a minimum, focusing instead on the personal stories of those who have fallen foul of new anti-terror laws. "It can happen to anyone. It isn't just middle class lefty protesters," says Atkins. "It isn't just people you read about in the papers. A lot of people haven't gone out of their way to find trouble. Trouble has found them. "That was the message we wanted to get across - if it can happen to them it can happen to you." Atkins' only hope is that, with an initial release on just 20 cinema screens around UK, in London and other big cities, it will create enough of an impact to break through to the mainstream audience at which it is aimed. http://news.bbc.co.uk/go/pr/fr/-/2/h...cs/6705375.stm  Riot Troops Break Up a Gay Rights Rally in Moscow Michael Schwirtz The police and riot troops Sunday prevented a rally for homosexual rights in Moscow, detaining organizers along with European lawmakers, as members of Orthodox Christian and nationalist groups pummeled gay rights demonstrators with insults, eggs and fists. Nikolai Alekseyev, the main organizer of the event, appeared at Moscow City Hall, but the police immediately pushed him and several other demonstrators into a police bus. Meanwhile, skirmishes broke out across from City Hall along Tverskaya Street, the main thoroughfare of Moscow, between gay rights protesters and counterprotesters. The general disorder obscured the number of participants in the demonstration, and the police had no clear figures. A man in camouflage clothing struck Peter Tatchell, a prominent British gay rights campaigner, hard in the face as he tried to address the news media. The police arrested the assailant and took Tatchell to a police van for his protection, said Evgeni Gildeyev, a spokesman with the Moscow police. Later, Marco Cappato, a member of the European Parliament from Italy, traded blows with a Russian man dressed in camouflage as riot police officers looked on. The police detained Cappato, along with Volker Beck, a member of the Bundestag, but later released them. In all, the police detained about 30 people, though it was unclear how many of those detained would face charges, Gildeyev said. "They charged me with disobeying police orders," Alekseyev said, speaking by telephone from a police detention center. He said he would spend at least one night in jail. The protest Sunday was the second attempt by organizers to hold a gay pride demonstration. A similar event, a little more than a year ago, ended in bloodshed when more than 100 ultranationalists and radical Orthodox Christians attacked gay rights demonstrators in central Moscow. Like last year, organizers of the event Sunday violated a government ban, though protesters faced less violence this year, according to organizers and participants. Still, many gay rights demonstrators, some holding rainbow flags, others chanting slogans, faced anti-homosexual vitriol meted out by representatives from the radical Union of Orthodox Flag Bearers and a group calling itself the Black Hundreds, who vowed to prevent the demonstration. A group of people surrounded one demonstrator shouting "Sodom will not stand!" and "Moscow is not Sodom!" Several protesters were pelted with eggs. "We will not allow the corruption of our land," said Aleksei Shtilmont, a member of the Black Hundreds. The Russian Orthodox Church, in a statement last week, lashed out at what it called "homosexual propaganda" and called on "society to unite against forces attempting to compel us to live contrary to notions of good and evil." "By filling the public arena with untruths about the normalcy of deviant sexual manifestations, homosexuality finds new victims, new slaves, stripped of the ability to participate with God in creation," the statement said. Unlike in some West European countries, there is little public acceptance of homosexuality in Russia, where even prominent public officials have made disparaging remarks about homosexuals. Yuri Luzhkov, the Moscow mayor, referred to a gay pride parade as a "satanic event" during an address in January. "We consider impermissible the activities of a destructive sect and the propaganda of so-called same-sex love," he said. President Vladimir Putin, responding to a question about Luzhkov's statements during a news conference Feb. 1, suggested that homosexuality had exacerbated the demographic crisis in Russia. Representatives from gay rights groups, however, seemed undaunted by the strong anti-homosexual rhetoric and violence, and vowed to continue organizing demonstrations. "This is only the beginning, and it is a good beginning," said Ksenia Prilepskaya, who acted as an unofficial translator for Tatchell, the British activist. She said that, unlike last year, more Russians turned out to support the event. These included the Russian pop group Tatu and Aleksei Mitrofanov, a State Duma deputy from the nationalist Liberal Democratic Party. Speaking before the event, Alekseyev said he hoped the European Court of Human Rights, to which he appealed after the demonstration last year, would compel Russian officials to permit a gay pride parade in 2008. Irina Fet, a member of the Russian Lesbian, Gay, Bisexual and Transgendered organization, or LGBT, whose leaders were arrested before the demonstration, brushed off the need for government sanction of gay rights protests. "We will hold this every year regardless," she said. http://www.iht.com/articles/2007/05/27/news/moscow.php  No Polish Probe for Teletubbies Poland's watchdog for children's rights was quoted as saying she would ask psychologists to investigate whether the Teletubbies character Tinky Winky is gay. Yesterday, she backed away from the comments. Ewa Sowinska, Ombudsman for Children's Rights, said the purse-carrying character on the British Broadcasting Corp.'s Teletubbies children's show could promote homosexuality. When journalists from the weekly magazine Wprost asked about Tinky Winky, Sowinska replied, "I noticed that he has a purse, but I didn't realize he's a boy. "Later, I learned that there could be some hidden homosexual undertones," she said. Sowinska said she would ask her office's psychologists to look into the allegations "and judge whether it can be shown on public television and whether the suggested problem really exists." The interview was approved by her office before publication. Yesterday, Sowinska's spokeswoman, Wieslawa Lipinska, told The Associated Press that Sowinska "hasn't asked and won't ask" psychologists to investigate whether Teletubbies promote homosexuality. Sowinska is a member of the League of Polish Families party, which is militantly anti-gay rights and anti-abortion. The party is a junior member in the coalition government led by Prime Minister Jaroslaw Kaczynski. http://www.theglobeandmail.com/servl...nt/Television/  eHarmony Sued in California for Excluding Gays Jill Serjeant The popular online dating service eHarmony was sued on Thursday for refusing to offer its services to gays, lesbians and bisexuals. A lawsuit alleging discrimination based on sexual orientation was filed in Los Angeles Superior Court on behalf of Linda Carlson, who was denied access to eHarmony because she is gay. Lawyers bringing the action said they believed it was the first lawsuit of its kind against eHarmony, which has long rankled the gay community with its failure to offer a "men seeking men" or "women seeking women" option. They were seeking to make it a class action lawsuit on behalf of gays and lesbians excluded from the dating service. eHarmony was founded in 2000 by evangelical Christian Dr. Neil Clark Warren and had strong early ties with the influential religious conservative group Focus on the Family. It has more than 12 million registered users, and heavy television advertising has made it one of the nation's biggest Internet dating sites. The company said the allegations of discrimination against gays were false and reckless. "The research that eHarmony has developed, through years of research, to match couples has been based on traits and personality patterns of successful heterosexual marriages," it said in a statement. "Nothing precludes us from providing same-sex matching in the future. It's just not a service we offer now based upon the research we have conducted," eHarmony added. According to the lawsuit, Carlson, who lives in the San Francisco Bay area, tried to use the site's dating services in February 2007. When she was denied access, she wrote to eHarmony saying that its anti-gay policy was discriminatory under California law but the company refused to change it. "Such outright discrimination is hurtful and disappointing for a business open to the public in this day and age," she said. Carlson's lawyer Todd Schneider said the lawsuit was "about changing the landscape and making a statement out there that gay people, just like heterosexuals, have the right and desire to meet other people with whom they can fall in love." Carlson's lawyers expect a significant number of gays and lesbians to join the class action, which seeks to force eHarmony to end its policy as well as unspecified damages for those denied eHarmony services based on their sexual orientation. http://www.reuters.com/article/domes...22132120070531  LiveJournal Apologizes for Mass Deletion Declan McCullagh LiveJournal apologized Thursday for a mass deletion of sex-themed discussions that purged literary criticism and accounts belonging to role-playing game characters and led to an unprecedented user revolt. In a public announcement, Barak Berkowitz, chairman and chief executive of LiveJournal owner Six Apart, said, "Well, we really screwed this one up" and promised to reinstate a wide swath of communities that were deleted as part of the company's attempt to eradicate pedophilia-related discussions. "Over the next few hours we will review the journals that were taken down and wherever appropriate we will restore these journals or communities," Berkowitz said. A day before, in an interview with CNET News.com, he had defended the deletion as not required by law but part of an effort to set standards based on "what we think is appropriate." (About 500 communities were removed.) LiveJournal's famously tight-knit community of about 13 million users had mixed responses to the apology Thursday: some applauded the company's frankness, while others called the deletion unforgivable. Comments ranged from "I'm just glad to see that you're honestly trying to fix the situation" to "you guys screwed up big time, especially in the eyes of someone like myself, who spent 150 bucks to help me enjoy my fandom experience here" with a paid account. The mass reinstatement means that the deleted science fiction and fantasy "fandom" groups--many of which boast sexually explicit fiction written by fans about characters such as those from the Harry Potter or Buffy the Vampire Slayer universes--began reappearing Thursday. 'pornish_pixies' celebrates its return One Harry Potter-themed group called pornish_pixies celebrated its return by posting an erotic story of a teenage Harry having intimate relations with arch-nemesis Draco Malfoy. One restored group deals with fictional tales of incest. Another, called lol_porn, includes links to bloopers and other unintentionally amusing pornographic Web sites. What outraged the LiveJournal protesters earlier this week is that the censored discussions and accounts went far beyond what they believe was necessary to target pedophilia. One post noted that two journals were deleted on grounds that "that they in some way encouraged illegal behavior" even though the accounts belonged to clearly labeled fictional characters in a role-playing game (one listed as interests "beating people up"). Another deleted community was home to Spanish-language discussions of Vladimir Nabokov's famous novel Lolita. A "fandom_counts" group set up as a kind of petition to draw attention to the protest had 29,423 members as of late Thursday. LiveJournal's terms of service bans "objectionable" content and says any account can be deleted "for any reason." But the company also claims to "provide users with as much freedom of speech as possible." LiveJournal has said it was responding to complaints from groups, including one called Warriors for Innocence. A representative from the group, who gave her name only as "Sues," said in an e-mail Thursday that "we did not knowingly report any 'fandom' communities or role-playing journals." In posts to her personal blog, Sues describes herself as an ardent conservative who views homosexuality as "sick" and a "twisted agenda" and lumps gays and lesbians into the same category as pedophiles and rapists. In her e-mail, Sues added, "While we sympathize with those who had their journals inadvertently deleted as part of LJ's efforts to clean up their online community, LJ's terms of service are clear in this regard; they've simply chosen to enforce them." http://news.com.com/LiveJournal+apol...3-6187960.html  Charles Nelson Reilly, Tony-Winning Comic Actor, Dies at 76 Patrick McGeehan Charles Nelson Reilly, who acted and directed on Broadway but came to be best known for his campy television appearances on talk shows and “Match Game,” died on Friday in Los Angeles. He was 76 and lived in Beverly Hills, Calif. The cause was complications of pneumonia, said his partner, Patrick Hughes, who is his only immediate survivor. Mr. Reilly had been ill for more than a year, he said. Long before moving west to become what he somewhat ruefully described as a “game show fixture,” Mr. Reilly was an actor and an acting teacher in New York City. In 1962, he won a Tony Award for his portrayal of Bud Frump in the original Broadway production of “How to Succeed in Business Without Really Trying.” But he was proudest of “The Belle of Amherst,” a one-woman play starring Julie Harris based on the life of Emily Dickinson, which he directed on Broadway at the Longacre Theater in 1976, said Timothy Helgeson, who collaborated with him on the show. Two decades later, Mr. Reilly directed Ms. Harris and Charles Durning in a revival of “The Gin Game” at the Lyceum Theater. He was nominated for a Tony for best director in 1997, and Ms. Harris was nominated for best actress. His final work was an autobiographical one-man show, “Save It for the Stage: The Life of Reilly,” in which he recounted his difficult childhood. Born in the Bronx, the only child of a Swedish mother and an Irish father, Mr. Reilly told of the pain of being considered the oddest member of a decidedly odd family. He explained the title of his show by saying that, when he was a child, his mother would often cut him off from speaking by admonishing him to “save it for the stage.” His father, he told audiences, never got over having passed up a chance to move to Hollywood and work with a budding animation artist named Walt Disney. In the 1970s and 1980s, Mr. Reilly, with his ascots, oversize spectacles and over-the-top penchant for double-entendres, was a regular on television. He appeared more than 95 times on the “Tonight” show with Johnny Carson and was a panelist on game shows like “Match Game” and “Hollywood Squares.” In a 2001 interview with The Advocate, the national gay magazine, Mr. Reilly reflected on the effect those shows had on his professional prospects. “You can’t do anything else once you do game shows,” he said. “You have no career.” Mr. Reilly’s openly gay persona was many years ahead of its time on television, and it had its risks. He recalled being dismissed early in his career by a network executive, who told him that “they don’t let queers on television.” Paul Linke, who directed the one-man show, said Mr. Reilly later had the last laugh when he would page through TV Guide and count how many times he was on the air that week. http://www.nytimes.com/2007/05/28/theater/28reilly.html  Linux Foundation Fires Back at Microsoft If you earned $34 million a day from Windows and Office, you too would try to spook the market with patent threats Jim Zemlin Last week, Microsoft (MSFT) initiated what can only be described as a rather bizarre public-relations campaign in which they alleged that Linux and Open Office may violate hundreds of the software maker's patents. While some of the mainstream press reported Microsoft's statements as news, many journalists and bloggers keenly identified the most intriguing aspect of this aggressive maneuver: a glimpse of a threatened giant struggling to keep a grasp on its empire. What most people don't realize is that the story really isn't about patents at all—it's about a rational actor trying to protect its privileged position. In the time it will likely take you to read this article, Microsoft will have made $500,000 in net profit. It's instructive to note that the majority of that profit comes from its Windows operating system and Office suite of business software. Not coincidentally, those are the two product lines most threatened by Linux operating systems and Open Office. Patent Wars Shortchange Customers Given the high stakes involved, it's not surprising that Microsoft would take steps to protect its turf. In fact, it makes perfect sense. Let's face it: If you were making $1 billion a month, what would you do? Perhaps engage in rhetoric and hyperbole to generate some old-fashioned FUD (fear, uncertainty, and doubt)? Just looking at the numbers, it's easy to see that even if the scare campaign merely delays a customer's migration from Windows to Linux by a single day, Microsoft is $34 million dollars better off. But as we said before, Microsoft is, above all, a rational actor. The software maker is hesitant to instigate a patent war, as it has too much experience with the downside of such litigation. Just ask Microsoft about its MP3 patent dispute, in which a jury recently ordered the software maker to pay $1.5 billion to Alcatel-Lucent (ALU). The Linux Foundation's membership comprises hundreds of companies, organizations, and individuals heavily invested in the continued success of a vibrant Linux ecosystem. Microsoft, our membership, and software users in general all know that a patent war guarantees only one sure outcome: The customer loses. Customers want choice and innovation. That's why open-source is winning. That's why Microsoft should embrace open-source to bolster competition in the marketplace. Competition will make us all better. Even Microsoft. Reform the Patent System The Linux Foundation does believe the current software patent system is problematic. The superpowers have their stockpiles. The trolls have their stashes. Rather than spurring innovation, which is of course the raison d'être of the patent system, today's patent games will divert dollars away from research and development in the U.S. Instead, those dollars will fund innovative activities in countries that have better things to do with their time and money than litigate. That said, we are also rational actors working within an existing system. Touch one member of the Linux community, and you will have to deal with all of us. Microsoft is not the only—perhaps not even the largest—owner of patents in this area. Individual members of the Linux ecosystem have significant patent portfolios. Industry groups, such as the Open Innovation Network and our own legal programs at the Linux Foundation, aggregate our membership's patents into an arsenal with which to deter predatory patent attacks. With our members' backing, the Linux Foundation also has created a legal fund to defend developers and users of open-source software against malicious attack. We don't expect to but, if needed, we will use this fund to defend Linux. In 2005, Microsoft General Counsel Brad Smith called on Congress to reform the patent system for software, stating reforms were needed to curb "abusive litigation." We agree. In fact, we call on Microsoft to work with the Linux ecosystem to restore confidence in the patent system by making sure they are issued only for truly unique, innovative, and novel functions that advance the state of the art. We ask Microsoft to stop engaging in FUD campaigns that only serve to undermine confidence in the U.S. intellectual-property system. Instead, please work with us to make the patent system tighter, more reasonable, and efficient for everyone in the software business. http://www.businessweek.com/technolo...pStories_ssi_5  Millions of Addresses and Thousands of Sites, All Leading to One Bob Tedeschi THINK you have a good handle on the Internet economy? Try this one. What Internet business has raised $120 million in financing in the last year, owns 725,000 Web sites, and has as its chief executive the former head of Primedia and International Data Group? If you guessed NameMedia, a privately held owner and developer of Web sites based in Waltham, Mass., you take the prize. Otherwise, consider reading on. According to Kelly P. Conlin, the chief executive of NameMedia, the company’s business is best seen as an online property developer. “What we’ve wanted to do, quietly, is amass the largest real estate position on the Internet, which we feel we have,” Mr. Conlin said. Some of those properties, he said, are the equivalent of “oceanfront” sites, or high-value addresses like Photography.com or DailyHoroscope.com that NameMedia will populate with relevant editorial content. Those who type in any of NameMedia’s other 6,000 or so photography-related Internet addresses, like photographyproducts.com, will land on Photography.com. The business is a far cry from the days of cybersquatting, where speculators bought up names of businesses to which they had no legitimate claim, but it does represent a vindication of sorts for many who bought hundreds or thousands of random Web address names on the hope that one day they would be worth something. Analysts suggest that NameMedia and its competitors could represent the next wave of Internet initial public offerings, while also providing a peek at a significant change in what people see when they stumble onto obscure Web properties. Behind this suddenly active business category — which includes companies like iREIT in Houston, Marchex in Seattle, and Demand Media in Santa Monica, Calif. — is the recognition that not all Internet users turn to a search engine when they are confused about where to find something online. Rather, 5 percent to 10 percent of people will simply type in a name that sounds as if it might suit their needs. The so-called direct search or direct navigation approach is seldom fruitful for users, nor has it been particularly profitable for owners of the sites that they visit. An obscure Web address may have four or so visitors a month, and perhaps half will click on an ad. “But if you have hundreds of thousands of those, it adds up,” Mr. Conlin said. “It’s an inside-out way of creating volume.” Mr. Conlin said that the properties in his portfolio, which includes about 1.4 million Internet addresses that independent owners have placed on NameMedia’s network of sites, attracts about 60 million monthly visitors. NameMedia will choose which ads to place on those sites, and will collect some of the revenue. For other sites not likely to be sought by hobbyists, like CellularPlans.com or CareerGuide.com, NameMedia fills the home page with links that users would otherwise see if they typed the same search Web address into a Yahoo or Google search box. The search engines pay NameMedia a commission whenever someone clicks on the links. NameMedia, which began in 1999 as YesDirect, was reintroduced in May 2006 with an undisclosed amount of equity financing from Highland Capital Partners and Summit Partners, two Boston venture capital groups, and more than $100 million in debt financing from Goldman Sachs. The company used part of that money to buy the portfolios of dozens of domain-name consolidators. To decide which of those sites to develop and which to fill with search engine ads, NameMedia hired Hugh O’Neill, who previously oversaw $30 billion worth of financial derivatives for Sun Life Financial. Mr. O’Neill uses, among other things, the expected number of clicks and the value of the ads in a category to calculate the future value of a domain name. If a prospective buyer is interested in a site that appears on NameMedia’s network, the transaction is conducted on one of the company’s marketplace sites, like BuyDomains.com or Afternic.com, and NameMedia collects a commission. So far the company’s strategy is paying off, Mr. Conlin said, with company revenue doubling last year, to $60 million. Youssef Squali, an analyst with the investment firm Jefferies & Company, said NameMedia faces stiff competition, “but I see these guys as the front-runner.” Among other things, Mr. Squali said the profit margin at NameMedia was 40 percent — a number that other industry executives said fairly represents the category over all. “They’re paying nothing to acquire a customer,” he said. “I think the next wave of I.P.O.’s will be around this area.” The direct navigation market attracted more than $800 million in ads last year, which publishers largely shared with Google and Yahoo. That figure could reach $1.1 billion in 2007, said Jordan Rohan, an analyst with RBC Capital Markets. Site owners understand they can earn more ad dollars if their sites display more than text ads. The question, however, is how to fill the more valuable sites with content without hiring teams of writers, video producers or others. Executives have found interesting workarounds. Marchex, for instance, will reintroduce in June its roughly 100,000 sites, using proprietary technology that automatically pulls relevant content from sites outside the Marchex network, and shares with those sites any ad revenues that result. Marchex also announced that the Latin American Channels division of Fox Broadcasting would provide videos for more than 100 Spanish-language sites in the Marchex network. IREIT, likewise, recently struck a deal with RealNetworks to distribute that company’s online games on its game-related Web sites. According to Craig Snyder, the chief executive of iREIT, online publishers are happy to find a way to distribute their content to more people, and thereby increase their revenues. “It’s become harder and harder for them to gain audience share,” he said. NameMedia recently finished building technology where visitors to niche sites — say, one on 1957 Mustangs — will be presented with links to other sites with similar images. The links will be between sites within the NameMedia network, but Mr. Conlin said that an unnamed Internet photo-sharing service with more than five million monthly users would soon join. “It’ll be a thinking person’s social network,” Mr. Conlin said. “The community becomes the content.” http://www.iht.com/articles/2007/05/...ess/ecom28.php  Photo Tagging as a Privacy Problem? Posted by Zonk An anonymous reader writes "The Harvard Law Review, a journal for legal scholarship, recently published a short piece on the privacy implications of online photo-tagging (pdf). The anonymously penned piece dourly concludes that 'privacy law, in its current form, is of no help to those unwillingly tagged.' Focusing on the privacy threat from newly emergent automatic facial recognition search engines', like Polar Rose but not Flickr or Facebook, the article states that 'for several reasons, existing privacy law is simply ill-suited for this new invasion.' The article suggests that Congress create a photo-tagging opt-out system, similar to what they did with telemarketing calls and the Do-Not-Call Registry." How would you enforce such a registry, though? http://yro.slashdot.org/article.pl?sid=07/06/02/026202  Google Photos Stir a Debate Over Privacy Miguel Helft For Mary Kalin-Casey, it was never about her cat. Ms. Kalin-Casey, who manages an apartment building here with her husband, John Casey, was a bit shaken when she tried a new feature in Google’s map service called Street View. She typed in her address and the screen showed a street-level view of her building. As she zoomed in, she could see Monty, her cat, sitting on a perch in the living room window of her second-floor apartment. “The issue that I have ultimately is about where you draw the line between taking public photos and zooming in on people’s lives,” Ms. Kalin-Casey said in an interview Thursday on the front steps of the building. “The next step might be seeing books on my shelf. If the government was doing this, people would be outraged.” Her husband quickly added, “It’s like peeping.” Ms. Kalin-Casey first shared her concerns about the service in an e-mail message to the blog Boing Boing on Wednesday. Since then, the Web has been buzzing about the privacy implications of Street View — with varying degrees of seriousness. Several sites have been asking users to submit interesting images captured by the Google service, which offers panoramic views of miles of streets around San Francisco, New York, Las Vegas, Miami and Denver. On a Wired magazine blog, for instance, readers can vote on the “Best Urban Images” that others find in Street View. On Thursday afternoon, a picture of two young women sunbathing in their bikinis on the Stanford campus in Palo Alto, Calif., ranked near the top. Another showed a man scaling the front gate of an apartment building in San Francisco. The caption read, “Is he breaking in or has he just locked himself out?” Google said in a statement that it takes privacy seriously and considered the privacy implications of its service before it was introduced on Tuesday. “Street View only features imagery taken on public property,” the company said. “This imagery is no different from what any person can readily capture or see walking down the street.” Google said that it had consulted with public service organizations and considered their feedback in developing the service, which allows users to request that a photo be removed for privacy reasons. A Google spokeswoman said the company had received few such requests. For instance, Google worked with the Safety Net Project at the National Network to End Domestic Violence, which represents shelters for victims of domestic violence nationwide, to remove pictures of those shelters. “They reached out in advance to us so we could reach out to our network,” said Cindy Southworth, founder and director of the organization. Not everyone believes the service raises serious privacy concerns. “You don’t have a right to ‘privacy’ over what can be seen while driving the speed limit past your house,” wrote a Boing Boing reader, identified as Rich Gibson, in response to Ms. Kalin-Casey’s complaint. Others dismissed her as a crazy cat lady. Edward A. Jurkevics, a principal at Chesapeake Analytics, a consulting firm specializing in mapping and imagery, said that courts have consistently ruled that people in public spaces can be photographed. “In terms of privacy, I doubt if there is much of a problem,” Mr. Jurkevics said. Still, the issues raised by the service, thorny or merely funny, were perfect blog fodder. The hunt was on for quirky or potentially embarrassing images that could be found by wandering the virtual streets of the service. There was the picture of a clearly identifiable man standing in front of an establishment offering lap dances and other entertainment in San Francisco. The site LaudonTech.com showed an image of a man entering a pornographic bookstore in Oakland, but his face was not visible. Others pointed to pictures of cars whose license plates were clearly readable. One pointed to images captured inside the Brooklyn Battery Tunnel, a controversial location for photography in this high-security era. On Lombard Street in San Francisco, various tourists who had come to photograph the famously curvy street were photographed themselves. Google said that the images had been captured by vehicles equipped with special cameras. The company took some of the photographs itself and purchased others from Immersive Media, a data provider. “I think that this product illustrates a tension between our First Amendment right to document public spaces around us, and the privacy interests people have as they go about their day,” said Kevin Bankston, a staff lawyer at the Electronic Frontier Foundation, a digital rights group. Mr. Bankston said Google could have avoided privacy concerns by blurring people’s faces. Back at her apartment, Ms. Kalin-Casey acknowledged that plenty of information about her — that she manages an apartment complex, that she was an editor at the film site Reel.com — is already easily accessible through Google and other search engines. “People’s jobs are pretty public,” she said. “But that doesn’t mean they want a shot of their sofa on Google.” She has asked Google to remove the image of her building, which was still online as of Thursday evening. When a reporter first arrived to interview her, Monty the cat was visible in the window. http://www.nytimes.com/2007/06/01/te...01private.html  In Fierce Competition, Google Finds Novel Ways to Feed Hiring Machine Miguel Helft On a spring Saturday, about 90 students from Stanford and as many from the University of California, Berkeley, converged on Google’s corporate campus for a day of spirited team competition over mind-bending puzzles, Lego building problems and video games. It was called the Google Games, a convivial way for the mostly computer science and engineering students to renew the Stanford-Berkeley rivalry. But behind the fun was a serious corporate recruiting event that underscores a rivalry no less intense: the tug of war for talent between Google and its competitors. As much of the high-tech industry is enjoying a renewed boom, the competition for top recruits in engineering and other fields is as intense as ever. Companies like Google, Microsoft and Yahoo frequently find themselves going after the same candidates or recruiting in one another’s backyards. At the same time, they are running up against a myriad of start-up companies across Silicon Valley that have been pumped up with venture capital in recent years. To lure talent, these companies have expanded their recruiting arsenal far beyond the traditional job fair to include a growing number of events like technology lectures, cocktail parties, pizza parties, treasure hunts and programming contests, dubbed “code jams” or “hack days.” Much like the Google Games, these are no-pressure recruiting occasions meant to create excitement around their companies and impress potential recruits as young as college freshmen. “It comes down to just getting them introduced to our culture, showing them that, hey, being part of Google could be a lot of fun,” said Ken Krieger, a Google engineer who had volunteered to supervise the Lego-building contest. Google, more than any other company, looms large in this latest chapter of Silicon Valley’s talent wars. The company has been vacuuming talent wherever it can find it to keep fueling its torrid growth. Its work force has roughly doubled every year for the last several years, to more than 12,200 at the end of March. Google is now adding about 500 workers each month. Its Web site lists nearly 800 open positions in the San Francisco Bay Area alone. If Google is hungry for top talent, the class of 2007 seems to think that a Google job offer is a prized commodity. Stories about Google’s notoriously tough and sometimes off-putting recruiting process continue to surface. Even so, the company was considered the most desirable employer for all undergraduates this year, and for the first time, it edged out the blue-chip consulting firm McKinsey & Company as the most desirable employer among M.B.A.’s, a position McKinsey had held for the last 12 years, according to surveys conducted by Universum, a research firm. “Being in an environment where you are going to learn a lot is the most important thing to me,” said Alice Yu-shan Chang, one of hundreds of recruits who are graduating this year and heading for Google. Ms. Chang, who is finishing master’s degrees in computer science and management science at Stanford, was sought by both Microsoft and Google, as well as eBay and Oracle. She said Microsoft had done what it could to find the right group for her, first at its headquarters in Redmond, Wash., and then, upon learning that she did not want to leave the Bay Area, at its Mountain View campus, not far from Google’s. She received phone calls from company vice presidents and met face-to-face with one of them. “With Google, you don’t have that much face time with high-up people,” she said. But there was some wining and dining on the part of Google, which Ms. Chang would not discuss in detail because she had signed a nondisclosure agreement. Eventually, Google won, in part because it had agreed to permit Ms. Chang to rotate positions every six months in the first year and half, and because, for her, it was a better cultural fit. “There are a lot of young people there who are very creative,” Ms. Chang, 25, said. Many of her peers at Microsoft would have been in their 30s and 40s “and more family oriented,” she said. In the last two years, Google has expanded its university recruiting programs to nearly 200 campuses from about 70. But the ubiquity of its events has ruffled some feathers. Max Levchin, the chief executive of Slide, a technology start-up in San Francisco, said he used to have good luck recruiting from his alma mater, the University of Illinois at Urbana-Champaign, by going there in midyear and persuading computer-science students to defer graduation and join him in Silicon Valley. “Now all I hear about is Google holding a puzzle hunt this, or Google campus pizza that,” Mr. Levchin said in an e-mail interview. Chief executives at other start-ups had similar frustrations. Stanford does not keep an official tally of where its students go, and even informal numbers are not in for the class of 2007. But an unscientific, voluntary check of students run by the university’s career center showed that Stanford had funneled more of its graduates to Google than to any other employer in the last three years. While playing down the rivalry with Microsoft, which is hiring at an even faster rate than Google, albeit into a company nearly six times as large, Google has not shied away from bringing the competition for talent to Microsoft’s door. Google has more openings in the Seattle area than anywhere else in the country other than California and New York. “I think it’s unlikely that you’ll see us back up a truck to their parking lot,” Google’s director for staffing programs, Judy Gilbert, said. “We have done a lot of things to engage with the local talent in an appropriate way.” As an example, Ms. Gilbert, a former recruiter for McKinsey, pointed to a lecture this year at Google by Kaifu Lee, the president of Google Greater China, which was intended to appeal to the “large community of Chinese ex-pats” in the Seattle area. Mr. Lee used to head Microsoft’s research organization in China. After Google hired him in 2005, Microsoft sued Google and Mr. Lee, accusing him of violating a noncompete agreement and misusing inside information. The lawsuit was later settled. Google’s efforts notwithstanding, Microsoft and Yahoo say they are able to hire the candidates they need. “Our competition is really the market for top talent, not a specific company,” said Scott Pitarsky, Microsoft’s general manager for talent acquisition. Similarly, Yahoo, which held a hack day at its campus that was attended by about 500 programmers, as well as smaller ones elsewhere, said its recruiting strategies were working. The company also opened a research center at Berkeley in part to attract student interns. “Dozens of people have come from the labs into Yahoo,” said Bradley Horowitz, vice president for product strategy at Yahoo. All three companies say their toughest recruiting challenges come from start-ups, who snap up people like Nitay Joffe. Mr. Joffe, who had summer internships at Google for the last two years, expected to go to work there. But before Mr. Joffe, a recent computer engineering graduate of the University of California, San Diego, accepted a job, a friend suggested he check out a San Francisco start-up, Powerset, which is trying to build a rival search engine. “Powerset had everything that Google had in terms of what I was looking for — smart people, interesting projects, great amenities,” Mr. Joffe said. Powerset also had one thing Google could not offer: the potential to strike it rich with the Internet equivalent of a lottery ticket. “When you get a stock option at 5 cents and it goes to $50 ...,” Mr. Joffe said, before his voice trailed off. With Google’s shares hovering around $480, it no longer offers the same potential. “Google isn’t going to $4,000,” said Mr. Joffe, who began working at Powerset recently. For every recruit who gets away, Google hopes many more enter its pipeline of potential employees at events like the Google Games. “We never say, ‘Come work for us,’ ” said Ronner Lee, who is in charge of Google’s university programs at Berkeley. “If they like what they see here and they want to approach us with questions, that’s great.” If the goal was to impress this crowd, it did not hurt that the games were held inside one of Google’s cafeterias, where the food is free, healthful and plentiful. Or that students were picked up at their campuses by Google’s free shuttles, which are outfitted with wireless Internet access. Or that many of the puzzles were created by the No. 2 Sudoku player in the world, who, by the way, happens to work at Google. David Nguyen, a doctoral student at Berkeley who went to Google for the games, said the company clearly understands its target audience. “This is exactly the kind of person they want,” Mr. Nguyen said, “someone who is going to work and solve problems on a Saturday and enjoy it.” http://www.nytimes.com/2007/05/28/te...28recruit.html  Google Deal for DoubleClick is Reportedly Under Scrutiny Steve Lohr The Federal Trade Commission has opened a preliminary antitrust investigation into Google's planned $3.1 billion purchase of the online advertising company DoubleClick, an industry executive briefed on the agency's plans said. The inquiry began at the end of last week, after it was decided that the Federal Trade Commission instead of the Justice Department would conduct the review, said the executive, who asked not to be identified because he had not been authorized to speak on the matter. An FTC spokesman said Monday that the agency did not comment on pending inquiries. The deal, involving powerful forces in their respective niches of the online advertising business, prompted privacy advocates and competitors to raise concerns after it was announced last month. Those concerns and the deal's size made a preliminary investigation all but certain, antitrust experts said. The FTC will soon decide whether to escalate its investigation into the Google deal, the experts said. Such a second request for information would suggest that the proposed acquisition raises more serious antitrust issues. Google said it was confident that the deal would withstand scrutiny. Privacy groups said it was significant that the FTC, the agency that monitors online privacy issues, would be conducting the review, rather than the Justice Department, which shares antitrust enforcement with the agency. "We think it's very important that the FTC is taking a look at the Google-DoubleClick deal," said Marc Rotenberg, executive director of the Electronic Privacy Information Center, a privacy rights group. Privacy issues are not typically the concern of antitrust officials. In reviewing a proposed merger, legal experts said, regulators weigh the likely impact on competition and struggle with tricky technical matters like defining the relevant market to measure. "To the extent that a reduction in competition could make it more difficult to protect privacy, it could be a consideration," said Andrew Gavil, a law professor at Howard University. "But it would have to be linked to competition. Strictly speaking, privacy is not an antitrust issue." In the days after the planned merger was announced, Rotenberg's center and two other advocacy groups, the Center for Digital Democracy and the U.S. Public Interest Research Group, asked the FTC to investigate the privacy implications. In the complaint, the groups noted that Google collects the search histories of its users, while DoubleClick tracks what Web sites people visit. The merger, according to their complaint, would "give one company access to more information about the Internet activities of consumers than any other company in the world." Google has built a lucrative business in selling small text ads that appear alongside its search results and on other Web sites. DoubleClick is the leader among companies that specialize in placing graphical and video ads online. Jeff Chester, executive director of the Center for Digital Democracy, said that decisions made now about the structure of the online advertising industry could have lasting effects on data collection and personal privacy on the Internet, especially if control rests with a "few powerful gatekeepers" led by Google. Google, the Internet search giant, is facing questions about its privacy practices not only from advocacy groups in the United States, but also from an advisory panel for the European Union. The company has said it welcomes the debate. It defends its privacy safeguards and says its business is based on consumer trust. As for the DoubleClick acquisition, Google repeated its optimism that antitrust regulators would approve the deal. "We are confident that upon further review the FTC will conclude that this acquisition poses no risk to competition and should be approved," said Don Harrison, a senior corporate counsel for Google. Harrison pointed to the flurry of deals in recent weeks, after Google announced its bid for DoubleClick on April 13. Later in the month, Yahoo announced it would pay $680 million for the 80 percent of Right Media, an online ad exchange, that it did not already own. In May, WPP Group, the giant advertising agency conglomerate, said it would pay $649 million for 24/7 Real Media, whose ad serving business competes with DoubleClick. And then Microsoft agreed to pay $6 billion for aQuantive, an Internet ad company. One of aQuantive's units, Atlas, competes with DoubleClick. Harrison said that "the online advertising industry is a dynamic and evolving space, as evidenced by a number of recently announced acquisitions." And he added that "rich competition in this industry will bring more relevant ads to consumers and more choices for advertisers and Web site publishers." Among the competitors that had called for an antitrust review were Microsoft, which had lost out in the bidding for DoubleClick, and AT&T, which distributes services like digital television over the Internet. http://www.iht.com/articles/2007/05/...ck.1-63487.php  Newspapers Want Google News' Quarter Greg Sandoval For years now, newspapers have quietly watched Google index their headlines and offer users a synopsis of their stories without paying them a dime. Google is supposed to make it easier for newspaper readers to find content online. But some in the industry are questioning whether it makes business sense to allow Google to use their material for free. "If all of the newspapers in America did not allow Google to steal their content, how profitable would Google be?" Sam Zell, the new owner of the Tribune Company, asked reporters during a speech at Stanford University last month. The Tribune Company operates the Los Angeles Times and Chicago Tribune. Zell didn't wait for the reporters to reply, according to The Washington Post. "Not very," he said. At a time when anyone with a blog can compete against vast media empires for readership, newspapers may be taking a harder look at their relationship with search engines and sites that aggregate headlines. The question some analysts are asking of media companies is: what's taken so long? "Newspapers are trying to find their way to understanding and addressing the value of linking," said Aly Colon, an instructor at The Poynter Institute, a school for journalists. "The search engines are supposed to be sending traffic to newspapers. But on the other hand (journalism) is hard work...There is going to be some sort of attempt by newspapers to figure out how they can be fully compensated for their work." Google's position about paying newspapers to index headlines has never wavered. "We don't pay to index news content," said a Google spokesman in an e-mail. The spokesman was responding to last weekend's report in Scotland's Sunday Herald that Google was in talks with British newspapers to obtain the rights to use their stories. Google flatly denied the story. "We have not changed our approach to Google News," the company said in a statement about the Herald's story. "We believe Google News is legal. We index the content of thousands of news sources online. When users go to Google News, they see only headlines, snippets and image thumbnails from the relevant news articles. If people want to read the story, they must click through links in our results to the original Web site." But not everyone agrees Google News is legal. A Belgium court ruled against Google last year after a newspaper association there sued the search engine. The newspaper group asserted that by offering snippets and headlines from their publications, Google violated copyright law. Google immediately stopped indexing stories belonging to the association's members. This month, however, links to the Belgium newspapers reappeared. Google and the newspapers said they settled their differences on some issues and were trying to resolve others. Last month, Paris-based news agency Agence France-Presse reached a licensing agreement to settle its copyright lawsuit against Google that allows Google to post AFP content, including news stories and photographs, on Google News, as well as on other Google services. Last August, Google announced an agreement with the Associated Press that allows it to use AP news and photos, but not in Google News. The content will be part of an undisclosed service under development. While some in newspaper circles point to the Belgium court ruling and the content deals with AP and AFP as a sign Google may be willing to pay for content, Google fans and bloggers interpreted the news quite differently. To them, it was obvious that the Belgium group had agreed to settle--even after winning its court case--because they discovered that they needed Google's traffic more than the fees that could be generated from news snippets. Observers note that with newspapers receiving about 25 percent of their traffic from search engines, losing Google's traffic had to sting. In business stories, newspapers are often lumped in with industries supposedly being bulldozed into extinction by the Internet. Readership across the board is falling fast and advertisers continue to migrate to the Web. The big newspaper companies, which typically enjoyed monopoly-like domination in their communities' advertising sector, are now scrambling to find new business models. Newsrooms continue to shrink. More bad news came last week when the San Francisco Chronicle announced it was laying off 100 out of 400 editorial staff workers. Yet, even in a climate like this, newspapers should look for ways to boost revenue other than taking on Google, said Barry Parr, an analyst with JupiterResearch. "They should be looking for the broadest distribution means possible," Parr said. "If you look at the penetration rate of newspaper Web sites, it's not all that high." Now on News.com What would happen if newspapers went the other way and demanded that Google compensate them for using their stories? Parr predicted newspapers would take a thrashing. In such a scenario, Parr said, Google would refuse to pay and stop indexing their headlines. It may not even be worth it for Google to fight it out in court. "Google isn't exactly raking in the bucks on Google News," Parr said. "There's no advertising on it." Meanwhile, said Parr, newspapers would lose readers. Competitors would likely rush in to fill the void. "(Newspapers) wouldn't be missed," Parr said. "Some people who used to go to The New York Times will find something else to do. They have to realize that the choice isn't between the Times and The Washington Post anymore. The choice is between the Times or watching YouTube. Newspapers are competing with a wide array of media." http://news.com.com/Newspapers+want+...3-6185896.html  Nervous bloggers AP to Copyright Infringers: Pay Up, for News Online Donna Bogatin Has the Web’s copyright infringement tide turned? A (very) “old media” company is taking the digital copyright protection lead, big time. When I met with Jim Brock, CEO of stealth-mode start-up Attributor, in New York City earlier this month, he shared with me his vision for mapping, tracking and assisting in appropriately monetizing the proprietary content of publishers across the Web. SEE: Web content DNA Map: Copyright control, monetization online Brock also was itching to share with me his “big news” about Attributor’s first big client, and it indeed is big, as Brock was able to share with me today. Attributor announces that it has been retained by the Associated Press to provide Web-wide monitoring and analysis of the online use of AP content with the aim of identifying unauthorized use. Attributor technology will be used to fingerprint AP copy and to identify and document its display wherever it appears across the Internet. Brock told me today “Attributor aims to bring transparency and accountability to the online content economy.” In gaining the confidence of AP, not only has Attributor landed its first paid client, it is collaborating with “one of the largest producers and distributors of online content.” What is in it for AP? The leading news orgnization is intensifying its efforts to protect its copyrights on the Web and hopes to uncover new sources of revenue. In subscribing to Attributor’s service, the AP will track how its stories are distributed across thousands of Web sites. Plans include eventual expansion for monitoring of the use of photos and videos on the Internet, as well. Brock told me, “In addition to helping publishers of all kinds protect the value of content assets for authorized licensees, we will also help them capture additional editorial and advertising value.” The AP is putting it more bluntly. Srinandan Kasi, the news cooperative’s general counsel: What we are trying to say is that if someone wants to use our news, they have to pay for it. Why is Kasi attracted by the Attributor solution? Attributor so far has indexed more than 13 billion Web pages, providing the AP with a potentially powerful tool for better understanding how its content is being consumed online and, ultimately, detect copyright violations. Rather than trying to scan all the material that AP produces each day, Attributor initially will focus on a few hundred stories likely to attract a lot of readers. Web sites that are updated frequently will be tracked more intensively. The AP can log in to Attributor’s service to track usage and flag potential copyright violations. AP will compensate Attributor depending upon usage levels. “It’s the start of a movement,” Brock enthused. A real “Claim Your Content” movement! http://blogs.zdnet.com/micro-markets/?p=1472  Dow Jones Says It Will Consider Options for Sale Andrew Ross Sorkin and Richard Pérez-Peña The family that controls Dow Jones & Company, publisher of The Wall Street Journal and one of the great names in American journalism, announced yesterday that it would consider selling the company. The announcement came after the family, the Bancrofts, said that it was willing to meet with Rupert Murdoch, just weeks after the family rejected an initial $5 billion takeover offer from Mr. Murdoch’s News Corporation. The decision, which represents a remarkable turnaround for both the company and for Mr. Murdoch’s bid, could end more than a century of family control over the company. For much of that time, The Wall Street Journal has been the gold standard in financial journalism. “After a detailed review of the business of Dow Jones and the evolving competitive environment in which it operates, the family has reached consensus that the mission of Dow Jones may be better accomplished in combination or collaboration with another organization, which may include News Corporation,” a statement from the family said. According to people close to both News Corporation and to the Bancroft family, there are no immediate plans for the meeting, but one family member said it would be “sooner rather than later.” Yesterday’s announcements do not necessarily mean that Mr. Murdoch will capture Dow Jones, which he has long coveted. The company could solicit competing offers or consider another financial arrangement. According to people close to the family who declined to be identified, the family wants any bidder to meet two conditions. The first is more money, which means that any bidder, including Mr. Murdoch, would have to beat his first offer of $60 a share. Second, and perhaps more important, the family wants an independent overseer to guarantee what it called “the editorial independence and integrity of The Wall Street Journal.” While the Bancroft family originally came out against Mr. Murdoch’s offer, people close to the family now suggest that its straw poll may have been taken too quickly and did not fully represent the view of the entire family. Moreover, some family members who seemed to be Mr. Murdoch’s staunchest opposition, decided, in the end, to consider a sale. One of those family members was Christopher Bancroft, who just last week told The Wall Street Journal in an interview: “I’m open to any situation that benefits The Wall Street Journal and Dow Jones and its shareholders. At the moment, I don’t see anything that would do that.” People close to the family now say that Mr. Bancroft’s comments may have been a negotiating tactic. “There’s been a whole series of stages of this,” said another family member, who declined to be identified. “It wasn’t any one event or one time that people came around. But this consensus has been evolving over the last couple of weeks as we watched what’s in the news, as we talked to investment advisers.” Over the last several weeks, different strains of the Bancroft family have been swayed to at least meet with Mr. Murdoch by a variety of factors. His third letter to the family, offering an independent board to oversee the editorial integrity of The Journal, weighed heavily on some family members, these people said. More decisive was a presentation given by the chairman of Dow Jones, Richard F. Zannino, that laid out the company’s future with and without a sale. For several family members, Mr. Zannino was far more persuasive in describing the former, suggesting that the company was unlikely to achieve results that would match the value of Mr. Murdoch’s offer. And a series of outside factors also played a role: the merger of the Reuters news agency and the Thomson Corporation changed some minds, as did a speech two weeks ago by the chief marketing officer for Macy’s department stores, in which she explained why her company was moving ad dollars to other media like TV, magazines and the Internet and she questioned the relevance of newspapers. “Obviously, the Thomson deal is yet another of a myriad of factors that would make you think that you might need to be bigger to compete,” said the family member, adding that the more the family heard from its advisers at Merrill Lynch and elsewhere, the more some of the older Bancrofts came to believe that holding on to the company was not a great business strategy. Richard Siklos contributed reporting. http://www.nytimes.com/2007/06/01/bu.../01dow.html?hp  Sales Barely Up, Book Trade Yearns for Next Blockbuster Motoko Rich In the absence of a new Harry Potter book or a blockbuster by Dan Brown, the publishing industry struggled to sell more copies last year than it did the year before, according to a report to be released today by the Book Industry Study Group, a publishing trade association. Publishers sold 3.1 billion books in 2006, up just 0.5 percent from the 3.09 billion sold the year before, according to Book Industry Trends 2007, an annual report that looks at sales in the United States. As a result of higher retail book prices, net revenue climbed 3.2 percent, to $35.7 billion from $34.6 billion. The data is being released as publishers, booksellers, librarians, authors and agents are assembled in New York for the second day of the industry’s annual BookExpo America convention, a frenzy of parties, celebrity author appearances, book signings and panel discussions to herald the fall lineup of new books. “There was a time when publishers thought that people wouldn’t pay above $25 for a book,” said Albert N. Greco, a senior researcher at the nonprofit Institute for Publishing Research who analyzed the data in the study. These days, cover prices can exceed $25. With heavy discounts at chain bookstores and other outlets, consumers often pay less, but the publisher still nets half of the cover price. “Even raising the price by $1 a year, or even 50 cents, you still get more money,” said Mr. Greco, who is also a professor of marketing at Fordham University. The strongest growth segment in publishing last year continued to be religious books, where 263.4 million were sold, up 3.1 percent from the previous year. The niche of religious books, which includes titles like “The Purpose Driven Life” by Rick Warren and “Your Best Life Now” by Joel Osteen, sold 197.3 million copies, up 6.7 percent from 2005. Net revenue for that segment increased 9.2 percent, to $1.65 billion. Sales of Bibles, testaments, hymnals and prayer books, however, slid 6.2 percent, to 66.2 million, and revenue was down 1.3 percent, to $772.9 million. Adult trade paperbacks increased unit sales by 3.5 percent, to 418.2 million, with net revenue rising 6.1 percent, to $3.69 billion. “We think there has been a migration towards adult trade paperback because of price,” Mr. Greco said. He said that people who shop at stores like Target, Wal-Mart and Costco are particularly attracted to trade paperbacks, where discounts can bring the cover price down to $8.99 or less. “The stock market is doing great, but gas prices are up, so paperback will continue to be a nice format,” he said. Sales of adult hardcovers dipped 0.1 percent, to 406 million copies last year, although revenue rose 2.4 percent, to $5.49 billion. Mr. Greco noted that best sellers generally sell fewer copies in hardcover than in years past: In 1994, for example, the No. 1 fiction seller, “The Chamber” by John Grisham, sold 3.2 million copies in hardcover. Last year, Mitch Albom had the No. 1 best-selling fiction title with “For One Day More,” but it sold only 2.7 million copies in hardcover, according to data from Publishers Weekly, a trade magazine. Similarly, in 1994, the No. 1 nonfiction title was “In the Kitchen With Rosie,” according to Mr. Greco. It sold 5.5 million copies, compared with just 2.2 million of John Grisham’s “Innocent Man,” last year’s top nonfiction best seller. This was the second year the figures included results from small and midsize publishers with sales of less than $50 million each. Mr. Greco noted that mass market paperbacks, which are the more compact editions generally favored by commercial authors like Dean Koontz and Nora Roberts, may show relatively stronger growth over the next five years because smaller publishers are increasingly selling books in this format through nontraditional channels like direct-to-consumer online sites and at seminars. Harry Potter is expected to drive sales of juvenile hardcovers this year. The Book Industry Study Group expects a 9 percent increase in revenue for that segment, and a 6.5 percent increase in sales. Scholastic, the North American publisher of the Harry Potter series, is planning an initial print run of 12 million copies for “Harry Potter and the Deathly Hallows,” the seventh and final book in the series; it comes out July 21. That compares with 10.8 million copies for the sixth book, “Harry Potter and the Half-Blood Prince.” But after Harry’s big year, sales in the juvenile segment are expected to remain flat for several years, although revenue will rise modestly, because of increases in cover prices. The strongest growth segment this year is expected to be elementary and high school textbooks, where the Study Group projects 9.6 percent growth in sales as several states adopt new series of textbooks. Mr. Greco said that strong growth would continue for the next three years. http://www.nytimes.com/2007/06/01/books/01books.html  Getting in the Game at Microsoft Robbie Bach's job is to make software giant's entertainment division profitable Dan Fost and Ryan Kim For all the challenges Microsoft Corp. faces as it moves into the future, the Redmond, Wash., software giant remains a formidable money machine. Its last quarter saw record profit, largely thanks to new versions of its Windows operating system and Office software. In its push to the digital future, however, where Microsoft envisions a world of "connected computing," where devices like phones, music players and game consoles increasingly define how people interact with computers, the company often finds itself playing catch-up. That's where Robbie Bach comes in. Bach, 45, is president of Microsoft's Entertainment and Devices Division, which includes the Xbox game console, the Zune music player, software that runs on mobile devices and new television projects. While the division has yet to turn a profit, Bach said in an interview that profitability is just around the corner, and Microsoft is relishing its competition with companies like Apple, Sony, Nintendo and Research In Motion. The following interview has been edited for space and clarity. Question: Your division is obviously one of the keys to the future for Microsoft, and one of the places where a lot of exciting things are emerging, but you're still trying to get to profitability. How does that work? What is the overall strategy and hope for the division? Bach: From a strategy perspective, we've been focused for a while on what we call connected entertainment. It's the idea that your media, whether it's music, video, photos, games, whatever -- you should have access to that wherever you are and on whatever device you want -- a PC, an Xbox, a Zune, a phone, whatever works and in whatever room it works. In order to do that, Microsoft has taken assets from across the company and consolidated them in this division. Part of my job now is forming that into a group. We're working on the specific areas of video, music, gaming and mobile, and also trying to work to make all those things come together in a coherent, logical way. It's a strategy where Microsoft can differentiate itself, because it's a strategy that relies on software and services. Those are both things where we have a competitive advantage. Regarding profitability, when you make an investment in a business like this, you're doing two things. When you make the investment, you're building assets. The trick as a manager is, when the assets get built, you have to turn that into operating income. We think next fiscal year, which starts in July, we'll do that for entertainment and devices. Question: Is that something that can turn the same kind of profit as Windows and Office, the big cash cows for Microsoft? Bach: The dynamics of the business are actually quite different. It's largely a consumer business and that has a different margin structure. We're also in hardware businesses. By most measures, Office and Windows are great businesses from a (profit and loss) structure. If Microsoft waited and said we can only be in businesses that replicate Office and Windows, we probably wouldn't be in very many businesses. Question: You've been the top dog in your traditional business, but in entertainment and devices you're a challenger in many ways, compared to an Apple or a RIM. How does Microsoft like that position? Bach: We have some places where we're leaders and some places where we're challengers. I like having that mix. For three or four years we were trailing Sony. That was an interesting challenge. It gave us good competition, good things to look at. Now, in the Xbox business, we're in more of a leadership position. The competition has its own excitement. In the music business, competing with Apple aggressively is fun. I enjoy that. They're a great company and a worthy competitor. In the mobile phone space, one of the ironies is, we actually outsell RIM today. It's one of those interesting dynamics where, from a sales dynamic, we're the leader. Your comment reflects the perception, which I think is true, that RIM somehow is ahead of us. There's times when it's fun being the person out front blazing the new trail, and times when it's fun to say we've got to hunker down and get after this. Question: One of the hotly awaited new products is the Apple iPhone, coming out next month. Does that change any strategy for you? Is there a Microsoft phone coming out? You already have a lot of mobile products. Is there a Zune phone? Bach: The iPhone hasn't changed any of our fundamental approaches to that marketplace. It'll be a very interesting product. Apple is very good at design; they come up with interesting approaches to products. Like anything else, it will have its trade-offs. It will be pretty high priced, and just on the Cingular (AT&T) network. But, it's an Apple product. It'll attract its level of attention from Apple enthusiasts, and we'll see where it goes from there. And it's a new concept, highly integrated. In the phone space, we're very comfortable with the model we've chosen. We think phones are deeply personal. Some people want a flip phone, some people want a candy bar (shaped phone), some people want a QWERTY keyboard, some people want a touch screen, some people want music phones -- people have different needs. We work with handset manufacturers and operators to produce that web of offerings, while still producing the same consistent software so people can get done what they need to get done regardless of which phone they choose. Question: Can you talk a little bit about the Zune overall? Will we see next-generation Zunes coming out, particularly flash-based players? Bach: We're still about nine months into having Zune in the marketplace. We're very pleased with the progress. We've sold a little over a million Zunes. In the category we're in, the hard-disk-based category, we've got about 10 percent market share. It's a good start. It's not an overwhelming start. I'm not going to pretend it's some gigantic move. As we look to the future, you're certainly going to see us continue to invest in that category. We don't enter things like that lightly. There will be new things down the path (in the fall). We just came out with a special edition pink Zune and a watermelon-colored Zune, which are the personal favorites with my kids. Question: How is the Zune marketplace doing overall? Sandisk just put out a new Wi-Fi player to enable people to download wirelessly. Are you looking at the Zune having that? Bach: The Zune marketplace is doing very well. We have a pretty typical attach rate of songs to Zunes. Certainly, like on an iPod, if you looked at the number of songs people have on a device, the majority are CD-ripped songs. You're going to see us expand in that space, a little bit more from the social aspects of connecting people together, a little more than just a store. As to the Wi-Fi, we think the idea of these devices being connected where you want them connected is very important. That's why we shipped the original Zune with Wi-Fi built in. The cool thing about that is, the innovation can all be in software. Wi-Fi is an important area. We'll see how that Sandisk project does. Question: Are people sharing music by beaming songs from Zune to Zune? Do you have any way to gauge that? Bach: People are sharing. When your installed base is a million, the benefits of sharing, frankly, aren't as wide as we hope to see in the future. One of the challenges for us is continuing to build on the install base. Sharing is a tip of the iceberg of what you can do in the social nature of music, and what you can do when you have a device that you can connect when you're at a Starbucks, when you're at work, when you're at home. That really, over time, will change things, for Zune and for consumers. Question: Community is one of the buzzwords that you guys have been using. Can you talk about how you are approaching that vision of community and connecting people? Bach: The easiest way to see that in our business is to think about Xbox Live and the work we've done with now over 6 million members on Xbox Live. Essentially what happens, there's a certain audience there to play multiplayer games. There's another audience who are there to have fun with their friends. Gaming is the context for that fun. What's one of the most successful games on Xbox Live? Uno. People aren't there because they're competitive Uno players. They're there because they can have a great experience with a camera, socialize with their friends and have fun, and Uno is the context for that taking place. The whole idea of giving people a place to have a social connection with their friends is very powerful. Question: Are you going to make any foray into social networking, like MySpace? Bach: Microsoft certainly has aspects of social networking in what we do today. We have the largest messenger community in the world. We just announced an ability to communicate from Xbox Live. You're going to see the community grow in that place. Question: It seems like, with all these balls in the air, integration and execution are going to be key. What have you done well? What do you have to do in that way? Bach: You can't have connected entertainment if don't have things people want to connect. We have to make sure Zune gets to scale. We have to make sure Xbox 360 continues to grow, and that Windows Mobile maintains its lead over RIM. Question: You want to see people have a complete universe of Microsoft products -- a phone, an Xbox, a Zune. But people don't want to think that way. They think, maybe I want an iPod, a BlackBerry, a Wii. Shouldn't everything work together? Bach: In an ideal world, there would be a set of standards that would make the basics of connectivity work really well. Question: Like the way that the Internet works. Bach: That's right. It may be that Wi-Fi and Internet connectivity will enable that to happen. Certainly there are things we do to support other things. You can take an iPod and plug it into your Xbox 360 and play your music. There's a (copy-protection) issue on music you bought on the iTunes service, but that's not our issue, that's something Apple put in place, saying "We don't want to give you the ability to play these songs." OK, that's their choice. We try to make those scenarios come alive for consumers as best as we can. Question: What do you think of the challenge of the Wii, Nintendo's latest game console? It seems a lot of people are drawn toward it. Has that changed any of your views toward casual gaming, or gaming overall? Bach: It really hasn't changed any of our views. Nintendo has done a very good job taking casual gaming, a younger audience, and putting that into a really interesting product. We'll compete with them. There are big sections where we don't compete with them and they don't compete with us. With Sony, it's much more overlapping. I think of Sony as much more of the direct competition. Question: Do you want to talk about Sony? They seem to be taking a slower approach. Bach: Historically, taking a slower approach at the early part of a cycle hasn't helped, because it's effectively a cycle that builds on installed base. If developers are shifting resources around, the questions are how much are they going to allocate to the PS3? We've never had stronger support for the 360. Sony has some significant challenges right now. They have a price differential that's going to be tough for them to bridge because the costs are going to be higher. They've got not enough traction in my opinion in the marketplace. And they've got Nintendo competing with them at the casual low end, and us competing very aggressively in the core gaming market, Nintendo competing with them in Japan and us here and in Europe. It makes for a difficult diagram for them to navigate their way through. They're a great company. They do great work. So I expect them to compete aggressively, but their challenge is pretty large right now. To listen to the interview with Microsoft's Robbie Bach, go to sfgate.com/podcasts. http://sfgate.com/cgi-bin/article.cg.../MICROSOFT.TMP  Windows Vista no More Secure Than XP: Report Ken Fisher The strength of Windows Vista's security model is easily the biggest question facing the nascent operating system. While sales will be strong simply on account of the way OEMs have adopted Vista on their midrange and high-end offerings, the place of Vista in the enterprise is not yet clear. Microsoft must demonstrate that its approach to security with Vista is indeed effective; otherwise, IT managers will see little benefit to moving to the new OS anytime soon. Windows Vista only offers "marginal security advantages over XP" according to tests completed by CRN. "Vista remains riddled with holes, despite its multilayer security architecture and embedded security tools." The report's findings are mixed and at times a little unfair, but it does demonstrate the problems that Microsoft has to face—technical and otherwise. The report faults Vista for "providing no improvement in virus protection vs. XP," but of course Windows Vista does not ship with antivirus software—something the reviewer fails to mention. Faulting an AV-less Vista for not stopping viruses is a bit like faulting a door without a lock for opening when the handle is twisted. Any business that is deploying Vista (or XP) without an antivirus solution is, of course, out of its mind. What Vista does have built in is Windows Defender and User Account Control, which should both help stop forms of malware other than viruses. And CRN found that Vista does have an "edge" over XP when detecting spyware and adware. It wasn't perfect though: some malware slipped though. Here, though, we run into the issue of deciding what counts as "stopping" malware. For instance, CRN says that Vista "missed" Trojan-Spy.Win32.Goldun.ms, when in fact UAC warns a user when it is accessed (I can confirm that). CRN faults Windows Defender for not identifying and blocking the Trojan outright (it did block others), while Microsoft will tell you that UAC did its job by throwing up a warning and asking for user intervention. In testing some remote data exploits, the reviewers were unable to determine if all of the exploits they tested actually target Vista, making their findings rather questionable. IE7 did stop one RDS exploit while missing four others that may have been only targeted at XP. Notably, XP did not stop any of the RDS exploits. Vista is better here, but the jury is out on how well it did or did not do since the reviewers were unable to determine the full threat of the exploits they were using. Vista and XP both failed miserably at finding scripting exploits in the HTTP stream, and this remains a big problem for both operating systems. Vista failed to flag the exploits as they came down the pipe, though the firewall did detect when the exploits attempted to communicate over the 'net. This is what we've found in our testing as well (the results of which we hope to publish next month). CRN doesn't tell the whole story with such exploits, however. IE7 in protected mode forces such scripts to run at a very restricted user privilege level, unlike XP which will allow those same scripts to run at the same privilege level as a user. Vista may let some of those scripts through, but the damage they do is also mitigated to a certain extent. This is why Microsoft believes such threats will have to evolve to survive with fewer rights and less access to the system: if they get through, they will find a very limited sandbox to play in. CRN's coverage complete ignores this point and fails to test for its effectiveness. It was also disappointing to see CRN completely ignore the issue of buffer overflows, which has been addressed well in Vista by most accounts. This was a major weak spot with XP, and so far, Vista looks strong in this area, strong enough that Vista may never get its own "SQL Slammer." Why CRN didn't address this is a mystery, as it is no minor matter. Indeed, while the CRN report is informative, it lacks much critical information to support its judgment that Vista is only a minor improvement. For instance, it's not enough to know if an exploit "got through" IE. What happened afterward? Did it modify system files, corrupt the registry, or deliver some other payload? CRN doesn't report on the effects it observed. We cannot know if the scripting exploits really bypassed Vista because CRN doesn't tell us what the scripts did. There's a big difference between 1) a script exploit running and then installing a rootkit in XP and 2) a script exploit running in Vista but failing at installing that same rootkit. CRN makes no distinction. In all, the CRN report finds that Vista was as good as XP in seven categories and better in four others (notably, Spyware/Adware, Obfuscated Code Exploits, RDS Exploits, and Trojans). Importantly, it was never outperformed by XP, and just as importantly, these tests were carried out using default settings. The scripting exploits, for instance, are largely defanged by tweaking IE7's zone settings, and there are other moves that a competent IT shop would undertake to make Vista more secure before releasing it to Joe User. And again, CRN didn't measure the effect of these exploits, which ignores a big piece of the overall security overhaul in Vista. Still, Vista's security is most certainly not a "slam dunk," and that should worry Microsoft. The mantra that Vista is an evolutionary step in security should be met with better results than this. As one IT contact told me recently, some shops view Windows security primarily as an issue of aggressive filtering at the corporate firewall, and Vista doesn't look poised to change that. All the reviews in the world probably won't change that, either. Time, coupled with a relatively clean record for Vista, is probably the only thing that will change skeptical minds. http://arstechnica.com/news.ars/post...xp-report.html  Touch Screen in a Table Is the Latest Wrinkle in Computers Michel Marriott Having just tried its hand at developing a digital music player, Microsoft is working on something new: digital furniture. The company plans to unveil a computing device today called Microsoft Surface, featuring a 30-inch screen embedded in an acrylic tabletop. The device’s electronic guts are hidden in the low-slung table’s thick pedestal. At first glance, Surface is reminiscent of an old-fashioned arcade game table around which patrons played Pac-Man. But there is no joystick here, and no mouse or keyboard either. The device is controlled by touching the tabletop display. Microsoft says this touch screen will allow people to “interact with digital content the same way they have interacted with everyday items such as photos, paintbrushes and music their entire life: with hands, with gestures and by putting real-world objects on the surface.” For example, when a digital camera with Wi-Fi capabilities is placed on the display, the table recognizes the camera and, at a touch of the screen, downloads its photos and video clips. The digital pictures can be sorted and sized by “handling” them as if they were physical prints. The device uses cameras under the display to detect touches, and unlike traditional touch screens it can handle multiple touches at the same time, said Jeff Gattis, the director of product management for Surface. Similarly, Surface can read bar codes and identification tags embedded in objects like hotel chain membership cards. Microsoft hopes this technology will someday be common in homes, but its first uses will be commercial. By the end of this year, Surface will appear in hotels, restaurants, retail stores and public entertainment sites, where it will serve as an information kiosk and handle things like basic customer service. Steven A. Ballmer, Microsoft’s chief executive, was scheduled to unveil the product today at The Wall Street Journal’s “D: All Things Digital” conference in Carlsbad, Calif. “With Surface, we are creating more intuitive ways for people to interact with technology,” Mr. Ballmer said in a statement. “We see this as a multibillion-dollar category, and we envision a time when surface computing technologies will be pervasive, from tabletops and counters to the hallway mirror.” Microsoft also named several partners that will be among the first companies to use Surface, including Harrah’s Entertainment, Starwood Hotels and Resorts Worldwide and T-Mobile USA. The device’s cost was not disclosed. http://www.nytimes.com/2007/05/30/te...=1&oref=slogin  iPod Killer Graveyard: Failures Equal NIB Bargains Richard Menta Last holiday season MP3 Newswire said in its semi-annual digital portable roundup "We have run the iPod Killers for Christmas/Summer series since 2004. In that time we reported on 149 portable players and NOT one iPod killer from the bunch". As we were finishing up our Summer 2007 edition of the series it occurred to us - what happens to all the unsold stock after these players fail? Do they get crushed in a big...crushing thing, melted and recycled? That's when it dawned on us that all of these players were most likely sold for pennies on the dollar to overstock vendors who then pawn them off cheap to the public, all New in Box (NIB) items, albeit a couple of years old. Now add to this all the portables given as gifts and never opened and that open bazaar we know as eBay can hold some hidden gems. This means there are some old players that if cheap enough could offer excellent value, even when compared against today's units and prices. So we spent a couple of weeks checking out eBay to get some idea of what is out there. The trick is to find players that are well under their original price, but are not yet obsolete. For example, Creative just announced the 1GB Zen Stone for $39, so it makes no sense to buy a 512 MB Sony Walkman Bean, which was in our Christmas 2005 guide, for $59. That's the price we saw Overstock.com peddling it. The other trick is to identify reasonably good players. Some of these units died a quick death for good reasons. Despite heavy advertising, including a million dollar Super Bowl ad, the Olympus MR500i from our Christmas 2004 guide garnered poor reviews and disappeared quickly. Value is a subjective measure and for some an old player is just that, yesterday's news. Improvements have been dramatic over the last couple of years too, so a cutting-edge portable in 2004 may just barely be average by today's standards. The digital savvy know what features are most important to them and they can tell right off if an older player at a steep discount makes a compelling option. A good way to gauge value for any user is to measure them against a contemporary player that's popular and well priced. In this case, we will use the iPod shuffle, which is a basic 1GB player with no display for $79.00. If a older player can offer more and do it for a price equal or less than the shuffle's it certainly becomes an option. The iPod shuffle is particularly good for this, because there are many users who find significant value in just the iPod name alone. It is also very tiny, a feature that is important to some users, but inconsequential to others. For those who have any interest in this New Old Stock (NOS) market, below are some examples of old stock alternatives to the $80 shuffle that we think might be of interest. Check out all your old favorites to see what they offer. We only saw a limited supply of some makes like Cowon and we could find nothing on others, at least during the brief time we monitored this. One player we were particularly looking for, but could not find, was the SoniqCast Aireo2, the first Wi-Fi DAP from late 2004. A couple of more notes, a few of the units we found on eBay were reconditioned units. The overstock vendors were upfront with this in their posts and, for the most part, these units have been fixed and retested so they should be fine. Still, factor that into to your value assessment when you make a decision, especially since some companies like Rio don't exist anymore so there is no warranty. We noticed some overstock vendors are asking at or near the original list price for these old units. Just ignore them, they'll catch on the hard way eventually. Finally, bear in mind that Li-ion batteries decay with time, even when unused, so non-reconditioned players using these batteries may or may not be able to draw a full charge out of the box. Virgin Player VM-500 5GB (2004) Released for the Christmas 2004 season, Virgin's CEO Richard Branson has high hopes for this little player. Targeted against the iPod mini, the Virgin Player was a little smaller and lighter and used the same 5GB Hitachi Microdrive. The following March the entire Virgin DAP line was discontinued due to very poor sales, despite the fact that the VM-500 garnered good reviews from the likes of CNet and PC Mag. On eBay several NIB units started at $39 - and closed with one or zero bids. Toshiba Gigabeat F40 (2005) This unit was part of Toshiba's first generation Gigabeat line, which came in 10GB, 20GB, 40GB and 60GB capacities. Toshiba Gigabeat F40 offered 40GB of space, an in-line remote, a dock, photo capability and a brushed aluminum finish. The player drew high praise from the digerati who in 2005 drooled over the F40's 2.2-inch QVGA color display, though they weren't particularly happy with the unit's transfer software. The overstock/backstock people are asking around $125 for the player on eBay, but the bids were flocking to user-sold NIB players, which sold for between $80 and $90, a compelling price for a 40GB hard drive unit. Rio Carbon 5GB (2004) After SonicBlue was acquired by Denon & Marantz it looked like the maker of the Rio finally had a parent with deep enough pockets to help what was once the number one player in the US at least reach double digit sales against the iPod. Instead, D&M decided to eventually shutter the whole division and get out of the digital portable market all together. Biggest casualty was the Rio Carbon C, also known as the Rio Cubic, which promised to bring one of the best portables at that time to the Christmas 2005 season. The Carbon C was not to be, but the excellent (again, for the period) Rio Carbon is available. New-in-box Rio Carbon's pull quite a few bids on the eBay market, but the bids generally close for around $60. We are assuming D&M no longer honors the warranty (though we have not confirmed this), but for 3/4ths the cost of an iPod Shuffle it's worth a look. AlienWare CE-IV (2005) Measuring 3.1 x 2 x 0.7 inches and weighing just 1.3 ounces, the AlienWare CE_IV was that computer makers attempt to follow in the footsteps of the Dell DJ. The unit offered an FM tuner, 3D sound and an SD/MMC slot for expansion. What was most interesting about the player is that it offered a matching speaker system as an option that also served to recharge the player. Reviews on the CE-IV ranged from excellent to so-so, so do your research. Mostly it is here because one overstock shop on eBay is selling factory sealed 1GB CE-IVs in a package deal with the sound dock, and is getting between $50 and $80 for the set. Dell DJ Series (2005) An NIB 512MB Dell DJ Ditty went unsold at $14.99, probably because the eBay seller tried to hit the buyer for $12.50 to ship a player that weighs less than the paper that wraps the package. If you can pay actual shipping costs this player makes a nice stocking stuffer for under eighteen dollars total. The hard drive-based Dell DJs aren't badly priced either. There seem to be quite a few NIB DJ-20s (20GB) around with a starting bid of $49.99. Keep the final bid under the price of the iPod shuffle and you are doing OK. Creative Zen Series Refurbished (2005) Did you know that Creative has its own store on eBay to sell their reconditioned electronics? And did you know they come with a 30 day warranty from the manufacturer? The Zen Micro was Creative's answer to the iPod Mini, offering 6GB of space on its Microdrive, an FM tuner, replaceable battery, and voice record. A refurb model in orange has a "buy it now" price of $69.99. How about a 1GB Zen nano for $19.99 or the 20GB Zen Touch for $99.99? They also sell reconditioned players of more recent vintage as well as non-refurbished units for list price. Archos AV700 Mobile DVR (2005) For a little perspective we thought we would include a very high-end player. Archos is actually one of the more successful iPod competitors, it just serves a smaller niche of high-end users. The AV700 has a monster 7-inch 16:9 display and comes with a dock to time record your TV programs (who needs to BUY episodes of Lost?). So when we saw an NIB unit with 40GB going unnoticed on eBay for $180 it caught our attention. This is a huge player though, weighing in at over a pound, so it's not for everyone. We found some overstock vendors were asking prices of over $400 for this model, which is silly as you can buy Archos' new Wi-Fi 604 for that money. http://www.mp3newswire.net/stories/7...graveyard.html  Where’s the Other Half of Your Music File? Wilson Rothman CHANCES are that even if you have taken the plunge and started building a digital music collection, you have never had to tangle with the word “bitrate.” That may be about to change. The Apple iTunes store, the largest seller of music downloads, began selling tracks from EMI Music yesterday without any restrictions on copying, for a slightly higher price than usual, $1.29 instead of 99 cents. To sweeten the deal, those tracks have better sound, with a bitrate of 256 kilobits per second (kbps), up from the standard 128 kbps. Apple has gone so far as to say that this results “in audio quality indistinguishable from the original recording.” So what exactly is a bitrate? Simply put, it is a measure of the amount of data used to represent each second of music. A higher number means that more sonic information can be used to recreate the sound. To careful listeners, or those with good audio equipment, more data can make a big difference. Last fall, Dr. Naresh Patel, a physician in Fort Wayne, Ind., moved into a home he designed with his wife, Valerie. It has a home theater, complete with projector, surround-sound speakers and a high-end amplification system. The sonic centerpiece is two Bowers & Wilkins loudspeakers that cost Dr. Patel $12,000 “with a discount.” It was all working beautifully until Dr. Patel connected his iPod to the system. Sitting down in the theater’s sweet spot to enjoy his music, he was instead appalled. “I couldn’t believe what I heard,” he said. “You don’t need a trained ear to hear the complete lack of so many things: imaging, the width and the depth of the sound stage. It almost sounded monaural, like listening to music in mono. The clarity, silkiness, the musicality of the music, if you will, was not there.” The problem was compression — the process of removing audio data to fit the music into a smaller file. Compressed audio making audiophiles crinkle their noses is not surprising, nor is it new. It has its roots in the debate of the 1980s, pitting the digital CD against the beloved analog vinyl record. The degradation of CD quality into something even more limited is simply proof to many fervent music listeners that Armageddon is indeed at hand. But several factors are making the debate over sound quality and bitrates more relevant now. Digital storage is cheaper than ever, download speeds are increasingly fast and digital music files have taken the place of CDs in many home theaters and cars. Many people are specifically asking for higher-quality downloads, and Apple and other online retailers are eager to deliver them — for a higher price, of course. (The price of complete albums from iTunes in the higher-quality format will remain the same.) Barney Wragg, who oversees EMI’s global digital music efforts, said there had been a shift in the music marketplace. “What was an entirely PC, MP3-player experience has changed; now people are wiring music via iPods into their stereos in their home and their car,” he said. “That’s what is driving the demand for increased fidelity. When I connect an iPod directly into the hi-fi in my car, I really notice the difference.” Apart from bitrate, the sound quality of digital music is also affected by its format, which is determined by the software used to compress it, known as a codec. MP3 is one of the older techniques for compressing audio and is not widely used by online stores. Apple has chosen a newer format called Advanced Audio Coding (AAC), which plays on iPods and some other devices. Most other online stores use the similarly modern Windows Media Audio, or WMA, which does not play on iPods. All three of these formats are “lossy,” meaning the encoding software surgically trims out audio information that is not easy to hear, because it is covered up by other sound or is situated at the highest and lowest ranges of human hearing. The Norah Jones track “Come Away With Me” is 33.4 megabytes when stored in an uncompressed format; the lossy compression methods bring that down to 6.1 megabytes at 256 kbps, or 3.1 megabytes at 128 kbps, regardless of the codec used. (When turning your CDs into song files on your PC, you can choose the bitrate you want in the settings of iTunes or Windows Media Player.) Codecs do vary in quality. Mr. Wragg of EMI said that as a rule of thumb, an MP3 at 320 kbps is roughly the same as an AAC file at 256 kbps. “The difference between WMA and AAC is more difficult to say,” he added. “Each has a slightly different way of getting compression. But in double-blind tests they perform pretty similarly — bitrate for bitrate they sound similar, but some prefer one over the other.” Until now, online retailers have dealt in 128 Kbps tracks — most retailers, that is. Two years ago, a group of audiophiles created MusicGiants, a digital download store that specializes in “lossless” files that are compressed in a way that does not discard any audio information, resulting in tracks that average 25 megabytes in size. MusicGiants now has more than 500,000 songs from most major labels. Scott Bahneman, chief executive of MusicGiants, said that comparing lossless tracks and compressed tracks was like comparing photos taken with a high-end digital camera and those taken with a camera phone. “Every bit counts when you’re trying to get sound quality, resolution or anything else,” he said. The site’s core audience is the type of person who spends large sums of money on home theater equipment, and wants music stored as digital files rather than on CD. Mr. Bahneman said his company planned to offer better-than-CD-quality music in files originally created for the DVD-Audio and Super Audio CD disc formats, which did not catch on with consumers. Each song will be 250 megabytes, about the same size as one episode of a sitcom on iTunes, but without the video. These “Super HD” files will have a bitrate of up to 11,000 kbps (that is, 11 megabits per second), and will be sold by the album rather than the track, at $20 each. Mr. Bahneman said that with the latest broadband services and huge hard drives, downloading and storing high-resolution audio files should not be a big hurdle. MusicGiants’ giant files are unlikely to appeal to the masses. Most people agree that on run-of-the-mill headphones, car speakers and compact sound systems, it is not easy to tell a low bitrate from a high one, because what is lost in compression is also lost in the reproduction of sound through those kind of speakers. To test the effect of different bitrates, I borrowed a sound system that was not an audiophile’s wildest dream, but was certainly higher quality than the gear owned by most music buyers: a Harman Kardon AVR 147 receiver ($449) and two JBL L880 speakers ($1,400 a pair), connected to an iPod via the Harman Kardon Bridge adapter ($70). This unscientific study involved three people (including myself) who listen to music daily in a variety of formats, from FM radio to CD. I loaded an iPod with 11 versions of “Come Away With Me,” spanning various qualities of MP3 and AAC from 64 kbps to 320 kbps, as well as one in Apple’s lossless format. Sitting in the sweet spot, we each listened to the different versions, played in random sequence, trying to determine if each subsequent version was higher or lower in quality. It was a straightforward test, and the result was surprising. The difference between 64 and 128 kbps was stark. All three of us picked up on it. As bitrates climbed above 128 kbps, however, our guesses became increasingly haphazard; none of us could determine the difference between 320 kbps and lossless. One unexpected result was that we all thought low-bitrate AAC files sounded better than low-bitrate MP3s. Still, even if poorer-quality tracks do not sound so terrible to all listeners, the difference between 128 kbps and 256 kbps is real. Many people will spend extra money for better-quality merchandise, perhaps in anticipation of a future sound-system upgrade. You may not buy all of your downloaded tracks a second time at higher quality, but you may decide that from now on $1.29 is a fair price to pay for an improved track. Dr. Patel said he had mixed feelings. He said he would always prefer CD quality to compressed audio, even at 320 kbps. Will the higher-quality downloads from iTunes matter? “I’ll take the best of what I can get,” he said, “but I’m not terribly excited because it’s not that much of an improvement.” http://www.nytimes.com/2007/05/31/te...=1&oref=slogin  Apple Takes a Bite out of DRM Michael Brown Apple's iTunes store—in partnership with EMI—is now hawking DRM-free music at twice the bit rate of its standard fare (256Kb/s vs. 128Kb/s) and charging a $0.30-per-track premium for it. We’re all for DRM-free music, but 256Kb/s still seems like a pretty low bit rate—especially when you’re using a lossy codec. So we decided to test a random sample of our colleagues to see if they could detect any audible difference between a song ripped from a CD and encoded in Apple’s lossy AAC format at 128K/s, and the same song ripped and encoded in lossy AAC at 256Kb/s. Our 10 test subjects range in age from 23 to 56. Seven of the 10 are male. Eight are editors by trade; two art directors. Four participants have musical backgrounds (defined as having played an instrument and/or sung in a band). We asked each participant to provide us with a CD containing a track they considered themselves to be intimately familiar with. We used iTunes to rip the tracks and copied them to a fifth-generation 30GB iPod. We were hoping participants would choose a diverse collection of music, and they did: Classical, jazz, electronica, alternative, straight-ahead rock, and pop were all represented; in fact country was the only style not in the mix. (See the chart at the end of the story for details.) We hypothesized that no one would be able to discern the difference using the inexpensive earbuds (MSRP: $29) that Apple provides with its product, so we also acquired a set of high-end Shure SE420 earphones (MSRP: $400). We were confident that the better phones would make the task much easier, since they would reveal more flaws in the songs encoded at lower bit rates. Methodology We asked each participant to listen with the Apple buds first and to choose between Track A, Track B, or to express no preference. We then tested using the SE420’s and asked the participant to choose between Track C, Track D, or to express no preference. The tests were administered double-blind, meaning that neither the test subject nor the person conducting the test knew which tracks were encoded at which bit rates. The biggest surprise of the test actually disproved our hypothesis: Eight of the 10 participants expressed a preference for the higher-bit rate songs while listening with the Apple buds, compared to only six who picked the higher-quality track while listening to the Shure’s. Several of the test subjects went so far as to tell they felt more confident expressing a preference while listening to the Apple buds. We theorize that the Apple buds were less capable of reproducing high frequencies and that this weakness amplified the listeners' perception of aliasing in the compressed audio signal. But that’s just a theory. Leave It To The Old Fogeys Age also factored differently than we expected. Our hearing tends to deteriorate as we get older, but all three of our subjects who are over 40 years old (and the oldest listener in the next-oldest bracket) correctly identified the higher bit-rate tracks using both the Apple and the Shure earphones. Three of the four subjects aged between 31 and 40 correctly identified the higher bit-rate tracks with the Apple earbuds, but only two were successful with the Shures. Two of three under-30 subjects picked the higher-quality tracks with the Apples, but only one of them made the right choice with the Shures. All four musicians picked the higher-quality track while listening to the Apples, and three of the four were correct with the Shures. Despite being less able to detect the bit rate of the songs while listening to the Shure SE420 earphones, eight of 10 subjects expressed a preference for them over the Apple buds. Several people commented on the Shure’s ability to block extraneous noise. While listening to the SE420s, one person remarked “Wow, I’d forgotten that wood-block sound was even in this song.” Another said “The difference between the Shure earphones and the Apple earbuds was more significant than the difference between the song encoded at 128Kb/s and the one recorded at 256Kb/s.” One of the two people who expressed a preference for Apple’s product told us “It seemed like I got better kick from the bass.” That’s A Wrap! To our subjects’ ears, there wasn’t a tremendous distinction between the tracks encoded at 128Kb/s and those encoded at 256Kb/s. None of them were absolutely sure about their choices with either set of earphones, even after an average of five back-to-back A/B listening tests. That tells us the value in the Apple’s and EMI’s more expensive tracks lies solely in the fact that they’re free of DRM restrictions. And as much as we dislike DRM, we just don't think DRM-free tracks alone are worth paying an extra 30 cents a track for.. It would be crazy to pay that premium if you're going to buy the entire album. We'd be more excited if Apple increased the bit rate even further, or--even better--if they used a lossless format. In the end, Apple's move doesn't change our opinion that the best way to acquire digital music remains buying the CD: You can rip and encode it at any bit rate you want, you can transfer it to any device you want, you know you won't have any DRM issues to worry about, and you won't have to pay anything extra for it. As for buying high-end earphones, eight of our 10 test subjects enjoyed listening to the Shure SE420’s more than they did Apple’s stock buds--an interesting finding since fewer listeners correctly identified the higher bit rate tracks with the Shures than did the Apples. We suspect that the performance of the Shures masked the flaws in the tracks encoded at lower bit rates. Your audio system is only as strong as its weakest link, and if you're listening to cheap earphones, you're missing out on what your MP3 player is capable of delivering. The SE420's fit tight inside your ear canal, so they isolate your ears from extraneous noise. Many of our listeners found that they could turn the player's volume down significantly because the earphones weren't competing with environmental racket. That not only makes your listening experience more enjoyable, but it can also prevent hearing loss. Despite what Apple charges for a set of its replacement buds, the earphones that come with 90 percent of the digital media players on the market are throw-away items--they're only in the box so you'll have something to listen to when you bring the player home. Do yourself a huge favor and dump 'em. Spending a few bucks more for something that sounds better, feels better, and will last longer just makes sense; after all, you only get one set of ears in life. Listening Results ARTIST ALBUM TRACK PICKED HIGH BIT RATE W/APPLES? PICKED HIGH BIT RATE W/SHURES? Nine Inch Nails Year Zero The Great Destroyer Yes No Tea Leaf Green Taught to be Proud If it Wasn't for the Money No No Guns & Roses Use Your Illusion II Civil War Yes Yes Husker Du New Day Rising Celebrated Summer Yes No Massive Attack 100th Window Future Proof Yes No Stevie Wonder Original Musiquarium I Vol. II Sir Duke No Yes Mingus Big Band Gunslinging Birds Jump Monk Yes Yes Sunday's Best Where Are You Now? Truest You Yes Yes Andres Segovia Legendary Andres Segovia in an All-Bach Program Chaconne (from Violin Partita No. 2) Yes Yes Steely Dan Aja Josie Yes Yes Listener Comments ARTIST WHY THE LISTENER CHOSE THIS TRACK Nine Inch Nails "It has the typical chord progression of a pop song, and then it goes into this crazy, techno solo. I thought the variety would help me identify the differences in the bit rate." Tea Leaf Green "This is a CD that I listen to a lot; I'm very familiar with it." Guns & Roses "This song is meant to be played loud. Axl Rose's voice and the guitars should help me tell the difference." Husker Du "I've been listening to a lot of Husker Du lately. Sometimes you rediscover a band and wonder why you haven't listened to them for so long." Massive Attack "I know this song so well. I figured I'd be able to tell if I was hearing everything that should be there." Stevie Wonder "I thought I'd be able to hear the difference in the sound of the horn section at the beginning of the song. I think the track with the higher bit rate will sound brighter." Mingus Big Band "I'll be listening for dynamic range in the horns. I think I'll perceive differences in the sound of the piano solo and the upright bass." Sunday's Best "The drummer in this band is cymbal crazy. I think it will be hard to capture that sound accurately at a low bit rate." Andres Segovia "I've listened to this recording 40 billion times. I know every nuance in it." Steely Dan "This may be the world's most fanatical band when it comes to recording. One of the things I'll be listening for are the chimes in the opening." http://www.maximumpc.com/article/itunes_256_vs_128_bit  The Trouble With Apple TV Steve Jobs' latest is a dud - and that speaks volumes. Brent Schlender Let's pause for a moment amid the worshipful buzz before the launch of Apple's iPhone in June to consider the heretical notion that Steve Jobs might be promising more than he can deliver. It wouldn't be the first time. There was the Apple III computer, introduced in 1980, which was prone to overheating, followed three years later by an acrobatic flop called the Lisa. (Apple would eventually bury thousands of them in a landfill to get a tax credit.) Jobs' Next computer was another technological marvel, but it couldn't find a market until Apple (Charts, Fortune 500) bought the company and re-purposed its operating system for the Mac. And the gorgeous Power Mac Cube, a Lucite box that looked like a fancy tissue-box holder, was "put on ice" in 2001, a year after its launch. That's not to say that Jobs' batting average hasn't improved since he returned to Apple in 1997. He's been the Hank Aaron of digital home runs. The iPod alone, which he quietly unleashed in 2001, atones for a lot of whiffs. Still, the way Apple is growing, even a nano-manager like Jobs doesn't have the bandwidth to fuss over every detail of every product, as is his wont. Moreover, his notoriously secretive company has been preannouncing products months in advance - the iPhone is just the latest - and even then has missed promised ship dates. Take Apple TV, the $300 set-top box that Jobs unveiled last October and that finally started shipping in at the end of February, several weeks late. You don't see many ads for it on TV, even though Apple is blitzing the airwaves with iPod and iMac spots, and after living with one for the past few weeks, I think I see why. It's just not very good. It's about as uninspired as another prominent dud, the Zune, the MP3 player Microsoft (Charts, Fortune 500) launched last year. In fact, the Apple TV is so Zune-like, you'd think Jobs was so busy with the iPhone that he outsourced the Apple TV project to the folks up in Redmond. To wit: • Apple TV's most highly touted feature is its weakest one: It requires an HDTV, but the video you download is so low-res that it looks as fuzzy as plain old broadcast TV. It's sort of like how the Zune digital music player's touted Wi-Fi connection only lets you temporarily "lend" music to another Zune. • Apple TV's coolest feature is one that wasn't even intended: the screensaver, which plays an ethereal slide show of your digital photos. I guess that tops Zune's sexiest feature, which I would argue is that you can buy it in brown. Love the brown. • There's no way to order a movie directly from the iTunes store via your TV, even though Apple TV has its own connection to the Internet. Instead, you have to download it to your computer first. Likewise, the Zune won't allow you to purchase music directly via its Wi-Fi capability. • Apple TV lets you show photos only from a single computer, even though photos are the one source of HD content everyone has, and are easy and legal to share over a network. That is especially odd, because Apple TV does allow you to share digital music from multiple PCs. The Zune, in a similarly consumer-hostile way, won't let you play purchased digital music recorded in Microsoft's previous music format. There are shortcomings that even Microsoft would not have overlooked: Apple TV doesn't have a DVD drive or a volume control on its minimalist remote or ... but enough. You get the feeling that Apple didn't create this thing because it was insanely great but in order to freeze competitors out of downloadable video. Apple TV could have been a versatile transitional product that not only made it easier for people to use their computer-based content in the living room but also helped unclutter their home entertainment systems. Apple got the shape of the box right, and the screensaver is pretty nice, but that's about it. So it really makes you wonder whether the iPhone, when it finally arrives next month, will be clunky and misguided despite its gorgeousness and slick user interface. Apple could turn off customers if the pricey device can't really do what it promises because of little gotchas like insufficient bandwidth or short battery life or an unusable virtual keyboard. That's the problem with hyping a product before it comes out. It's bound to disappoint no matter how good it is, and if it isn't quite as good as advertised, well, I suppose we'll be surprised by some other cool thing. Maybe the cellphone equivalent of Nintendo's Wii. Nobody saw that one coming. http://money.cnn.com/magazines/fortu...ion=2007053007  At BET, Fighting the Rerun Geraldine Fabrikant Last week, executives from Black Entertainment Television walked through the Shrine Auditorium in Los Angeles, laying out the plans for the annual BET Music Awards on June 26. The broadcast has become the highest-rated award show on cable, topping the MTV Music Awards, ESPN’s ESPY Awards and the Nickelodeon Kids’ Choice Awards. This year’s host is Mo’nique, a popular comedian who is the host of “Flavor of Love Girls: Charm School,” a reality show that draws a large African-American audience. But “Flavor of Love Girls: Charm School” isn’t on BET. Instead, it has become a big hit for VH1, a cable channel that, like BET, is owned by Viacom. Mo’nique’s presence on the BET podium illustrates one of the channel’s persistent struggles. Despite being the first and certainly the largest African-American cable channel, BET has developed few of its own marketable stars and virtually no breakout programs. It relies instead on reruns, movies and music videos for the bulk of its lineup. BET’s chief executive, Debra L. Lee, has tried to reverse that trend, this year increasing the channel’s production budget 50 percent and plunging into original programming with 16 new shows planned for the new season. “What we have found over the years is that acquired and licensed programming has not done as well as we would have liked,” Ms. Lee said. “It was very clear that we had to invest more in original programming.” Ms. Lee joined BET in 1986 as general counsel and vice president, working closely with its founder, Robert L. Johnson. She was named president and chief executive when he left the network in 2005. Although she did not have direct programming experience, the programming department had reported to her since 1995. A calm, businesslike executive, she quickly brought in a team to “take BET to the next level,” she said in a recent interview at Viacom’s Manhattan headquarters, where she commutes from BET’s Washington offices. Ms. Lee’s attempts to remake BET come at time when all cable channels are contending with an increasingly tough landscape as the battle for market share among the mature networks intensifies. BET’s ratings were strong in 2006 but tumbled in the first quarter of this year. And while the channel has had some success with original series like “American Gangster” and “Lil’ Kim: Countdown to Lockdown,” they have been overshadowed by some recent hits on other Viacom cable channels. These include Comedy Central’s “Chappelle’s Show” and VH1’s “Flavor of Love” and two spinoffs: “I Love New York” and “Flavor of Love Girls: Charm School.” The original “Flavor of Love,” in which 20 women vied for the affections of the rapper Flavor Flav of the group Public Enemy, was an enormous hit for cable. The second season finale attracted 7.5 million viewers — VH1’s best rating ever — and drew a 34 share among African-American viewers (meaning 34 percent of all African-Americans watching television during at that time were watching VH1). BET, which is available to about 84 million homes, is still considered extremely profitable by analysts, although Viacom does not break out figures for its cable networks. Louis Carr, executive vice president for BET’s broadcast media sales, said revenue grew last year but at a slower rate. But BET has run into the same wall as many other cable channels. BET has succeeded, analysts said, on the basis of fees from cable operators and cable’s growing piece of the advertising market. But the growth in fees has slowed as the industry matures, said Michael Nathanson, a media analyst at Sanford Bernstein. “The days of double-digit affiliate revenue fee growth from cable systems are over,” Mr. Nathanson said. In response, cable channels have spent more on original programming to attract new viewers and possibly attract new revenue from licensing, DVD sales and other media, like the Web or cellphones. “Networks need to own their programming so they can reap the revenues from those outlets,” said Richard Greenfield, a media analyst at Pali Research. According to a 2005 Nielsen study, African-Americans watch more television on average than the overall population. That appetite for television raises the question of why BET’s ratings are not higher. “BET does not have the ratings it should have with 12 percent of the audience being black,” said Leo Hindery, a partner in Intermedia Partners, which owns a majority stake in the Gospel Channel, a cable network. “It has never developed a soul of its own. I would do more sports than they are doing and I would stay with the youth audience.” Ms. Lee disagrees. “To say we don’t have a soul of our own: I don’t know what that means,” she said, pointing out that the channel did carry black college football games and the ratings were not good. “When you look at our shows that really work, we get a sizable percentage of the population. We are the No. 1 show in black households. We did a fund-raiser after Katrina and raised $113 million, so there was a strong connect to our programming.” To develop BET’s new stable of shows, Ms. Lee turned to Reginald Hudlin, who made his name as the writer and director of movies like “House Party,” “Boomerang” and “The Great White Hype.” He joined BET a year ago with the goal of making it a “creative haven” for talent in the mode of Home Box Office. For the new season, he is developing “Somebodies,” a postcollege comedy based on a 2006 film, and “Baldwin Hills,” a “Laguna Beach”-style documentary about rich teenagers in Los Angeles. Mr. Hudlin has big plans. “I want every black person with a TV watching, and a lot of people with TVs who like black people,” he said. “We want the black audience to start the day with BET and put the remote down at night without switching channels.” Mr. Hudlin is also betting that programming will help assuage critics of the channel, both African-American and white. Over the years, the network has been criticized for depending on music videos and other shows that present a narrow and sometimes violent view of African-American life. Herman S. Gray, a professor of sociology at the University of California, Santa Cruz, said the challenge for BET is to create cost-effective programs that address the complexity of African-American life. “If the network becomes identified with eye candy, then the process of creating complex and subtle programming for the community will be stalled,” Professor Gray said. But it is facing increasing competition from traditional cable networks like USA and Lifetime and from smaller rival channels like TV One, whose major backers include Radio One, a radio company that aims at African-Americans, and Comcast. TV One, which is in 40 million homes, aims at a somewhat older audience than BET. Although Comcast executives decline to be specific, the cost of starting a network is “north of $300 million,” said Jeffrey Shell, president of Comcast’s programming group. “We saw the power of the radio networks to promote the cable network in all its markets,” he said. He is diplomatic about the competition. “If you look at the African-American audience, there is room for several networks,” he said. Mr. Carr from BET is not so generous. “They are a nice sandwich shop,” he said. “They serve a nice sandwich and a nice cup of soup. But if you look at just the facts, we are double in every major variable: distribution, ratings, revenues. We have a great family style menu.” As BET faces new competition and the realities of being a cable channel, it must continue to deal with the cultural undercurrents of being the face of black cable television. The network has long been a lightning rod for critics and it has been attacked over the years for glossing over some of hip-hop culture’s rawer edges. After Don Imus made a racial and sexist insult of the Rutgers women’s basketball team in April, many critics pointed out that such language is common in rap. Ms. Lee said that the network would not have broadcast the particular phrase Mr. Imus used. “We don’t allow that kind of language in our music videos. What we air on BET is the clean version,” she said, conceding that BET does permit other unflattering terms for women in the videos it shows. “The good thing about the Imus controversy is that it raised the issue,” she said. “It makes us more conscious.” http://www.nytimes.com/2007/05/28/bu...8bet.html?8dpc  Irish Classic Is Still a Hit (in Calfskin, Not Paperback) Eamon Quinn For a manuscript written 1,200 years ago and revered as a wonder of the Western world practically ever since, little is known about the Book of Kells and its splendidly illustrated Gospels in Latin. But the book may be about to surrender a few of its many secrets. Experts at Trinity College in Dublin, where the Book of Kells has resided for the past 346 years, are allowing a two-year laser analysis of the treasure, which is one of Ireland’s great tourist draws. The 21st-century laser technology being used, Raman spectroscopy, encourages hopes among those with a romantic view for an ecclesiastical intrigue like “The Da Vinci Code” or “The Name of the Rose.” But the precise subjects are more mundane. The laser will study the chemicals and composition of the book, its pigments, inks and pages of fine vellum. Experts estimate that 185 calves would have been needed to create the vellum on which the art and scriptures were reproduced. Pending the laser analysis, experts assume that expensive materials for some of the blue pigments came from the gemstone lapis lazuli, mined in northeast Afghanistan. Yellow pigments are believed to have been made from arsenic sulfide and, bizarrely, reddish Kermes pigments from the dried pregnant bodies of a genus of Mediterranean insect, suggesting extraordinary trade routes for the ninth century. Some techniques will help to analyze the pigments made from vegetable matter; others will be used to examine the inks. “A lot of what we have done before has been based on anecdotal reports of the materials that were used,” said Robin Adams, the librarian of Trinity College, who hopes the exacting dot-by-dot analysis by laser will unlock secrets and help his staff preserve the book. “Essentially the laser bounces back, and you get a spectrum. That spectrum tells you whether this pigment is lead, copper or whatever. We haven’t got the reports yet, but we very much expect it to tell us new information about what the monks used.” Mr. Adams hopes that Trinity’s manuscript research will answer some of his own questions about the book: “I would like to find out whether this work can tell us its relationship with other manuscripts. Is the material used in Kells the same as might be used in England or France? It could tell us a bit about the movement of materials around the monastic houses. We would love to find out how these monastic houses worked as communities, and whether the techniques were the same. Or whether they developed techniques because of the raw materials they had at hand. That would tell us new information about the times.” For a religious work, the book has a rather exciting history, but its hazier aspects are unlikely to be discovered by a laser. It was created around the year 800 to honor the achievements two centuries before of Columb, also known as Colm Cille. He was an Irish nobleman who in Ireland and Scotland founded one of the world’s earliest Christian monastic traditions dedicated to learning and devotion. Irish legend relates that Colm Cille, after losing a bitter legal ruling over his right to make copies of books, went into exile on Iona, the Scottish isle where the Book of Kells is thought to have been written. But Dutch or Norse Viking raiders landed in 806, and Irish monks evidently removed the book for safekeeping. Eventually it made its way to the Kells in County Meath, a monastery outside Dublin. There it survived new waves of raids, including one by bandits who made off with the book in 1007, according to contemporary chronicles. It was recovered two months later, under dirt, stripped of its gold covering. The book stayed in Kells until Cromwell’s wars in the 17th century. A senior Protestant clergyman, Henry Jones, who had served as a quartermaster general for the invading army, is said to have “donated” the book to Trinity College sometime after 1661. With the original binding lost, the book was split over the years into four volumes. Two are now on display in “Turning Darkness Into Light,” an exhibit at Trinity College, while the others are being analyzed. The enduring mystery about whether the book was written on Iona, Kells or at another Colm Cille monastic site will likely endure. Maybe only a testing of the DNA of the vellum would reveal the age and source of the calfskins used at that time and reveal the place of the book’s manufacture. Mr. Adams would like to know if such an analysis could unlock that secret. “I have always wondered whether a technique could tell us where the cattle were and where they came from,” Mr. Adams said. “Did the skins move around — was there a trade in the skins or were they produced locally? That would add to our knowledge. But that is what we are doing in applying these new techniques.” There is no doubt about the book’s appeal in the present day: it attracts more than 550,000 visitors annually, vying with the Guinness Brewery tour up the road in central Dublin as Ireland’s most popular site. Its popularity leads to crowds during the summer, and there are plans to expand its display area in the college library building, which dates from 1732. It has yet to be decided whether the book will need to be removed during any building work. Other academics vouch for the book’s world importance. “It is one of the most precious books on the planet,” said Terry Dolan, professor of English at University College Dublin. But Professor Dolan said the book had another secret that technology would not reveal. “Little is documented about how the book came to be removed from Kells in the first place and how it ended up in Trinity,” he said. “There is yet another fascinating mystery story there.” http://www.nytimes.com/2007/05/28/wo...e/28kells.html  Windows ‘Longhorn’ Resurrected and Available for Download - Longhorn Lives! Marius Oiaga It lives! Windows Longhorn has been resurrected and is available for download. Microsoft unveiled Longhorn back in early 2002, as the operating system designed to succeed Windows XP. However, the 2002 Windows Longhorn and the January 31, 2007 Windows Vista are not one and the same operating system. I am sure that there are still some of you that recall August 27, 2004, a day when Microsoft announced a scale back and a reset of Longhorn in order to make the then planned 2006 deadline. If Microsoft had not changed course back in 2004, Windows Vista as we know it would have never booted on our desktops. Sure enough, it seems that a group of developers failed to see eye to eye with the Redmond Company on the divergent trajectory from Longhorn. As a result, they took it upon themselves to resurrect Windows Longhorn according to Microsoft's original vision of the operating system. "Longhorn Reloaded is a Project dedicated to the revival of the Operating System known as Code Name "Longhorn". To put the projects aims simply, we aim to finish off what Microsoft started before the operating system was canceled. It is a modification of Windows 6.0.4074, which was originally released during the 2004 Windows Hardware Engineers Conference," reads a message on the Longhorn Reloaded official website. While Windows Vista no longer has the Windows File System (WinFS) feature and its core has been built starting from the Windows Server 2003 kernel, the Joejoe group have gone back to the pre-release Build 4074 of Longhorn and took it from there. "Longhorn Reloaded M1 Technical Refresh - The second public release of Longhorn Reloaded. The serial required is: TCP8W-T8PQJ-WWRRH-QH76C-99FBW. This technical refresh release can now be installed on a partitioned hard drive. You shouldn't have any problems while installing unlike the original Longhorn Reloaded M1 Release," reveals a message that accompanied the download. In fact, the two screenshots that you are able to see at the bottom come not from Windows Vista but from Windows Longhorn Reloaded M1. Microsoft has so far failed to react to the project officially, but the Redmond Company did state that the end users license agreement for the beta build of Longhorn does not allow users to modify and redistribute the code. Meanwhile, the Joejoe group - under the leadership of Jemaho (JeanMarie Houvenaghel) - informed that the development process will move to the M2 milestone. http://news.softpedia.com/news/Windo...ad-55624.shtml  Telepresence TV Paul Burnham Finney High-end videoconferencing — the magical ability to be two places at once — has had a bumpy past, plagued by jerky gestures, out-of-sync lips and sound and cumbersome equipment. Few executives liked what they saw, including unflattering pictures of themselves, and most thought the business tool was not worth the price. But now, thanks to new technology, videoconferencing is delivering on its promise as an alternative to traditional business travel. The high-definition TV images are sharp. Broadband fiber-optic cable has replaced tired telephone lines. And the equipment is often installed in studios that are handsome and appropriately corporate. And as air travel becomes more difficult, virtual meetings provide an alternative. You can sit across a table from a large screen showing someone who looks quite real and life-size, but may be in London or Frankfurt. Only a handshake and exchange of business cards are missing. Equipment suppliers, led by Cisco, Hewlett-Packard, Polycom and Tandberg, have created a new word — “telepresence” — to market the technology. “It’s a big leap forward,” said Claire Schooley, a teleconferencing expert at Forrester Research, a technology and market research consultancy in Cambridge, Mass. “Can you imagine a sales meeting where you go to one of the new sophisticated video rooms and hear the spiel in one hour, compared to attending a meeting in a remote location? It’s perfect if you want to see the body language.” Ken Crangle, general manager of Hewlett-Packard’s telepresence unit, known as HP Halo, said, “I just had a four-way meeting today with a C.E.O in London, people in his company’s New York office and in our Alpharetta office outside Atlanta, and several of us here at headquarters in Oregon.” But telepresence technology comes at a high price: up to $300,000 to $400,000 a studio. “Customers are paying for a Cadillac service,” said Andrew W. Davis, an analyst at Wainhouse Research, a consultancy in Duxbury, Mass., that tracks voice, video and Web trends. “Walk in a Halo room, and everything is ready to run. There’s a slick user interface. But it eats up a massive amount of bandwidth and costs something like $18,000 a month to keep around.” The infant telepresence industry may never produce big numbers in dollars or units shipped, Mr. Davis said. So far, Hewlett-Packard has sold a little more than a hundred units (28 for its own use) since Halo’s introduction in 2005. Cisco just began shipping the first of some 110 units it expects to sell within a year. “I’d guess it will never be more than 1 percent of total videoconferencing sales,” Mr. Davis added. The mainstream market is dominated by simpler systems that use less advanced equipment and cost from about $10,000 to $50,000, depending on location, room size and other features. Last year 163,000 of the units were sold, Mr. Davis said, adding that the market has been growing around 20 percent a year for the last decade. Part of the reason for the increased interest in telepresence videoconferencing is that air travel is more time-consuming than ever, just when companies are putting a premium on rapid decision-making. “The endless problems at airports these days — whether it’s bad weather, maintenance delays, crowded cabins or security lines — make alternatives to travel more attractive,” said Gary Foley, the manager of global conferencing and travel services at Xerox who oversees some 19,000 employees who take business trips. But the trade-off between video and travel can be tricky. “The reason for actual face time is often subjective — quite difficult to quantify,” said Henry H. Harteveldt, the vice president and principal analyst at Forrester. “There’s the need to build a relationship, a desire to deliver good news — or bad news — in person. The virtual meeting may change the mix with fewer people traveling for sales purposes and more for client work and conventions.” Teleconferencing veterans with long memories can recall that the AT&T Picturephone, an early video concept introduced at the 1964 New York World’s Fair, was a commercial flop. But that was then. The new systems, in contrast, are sleek and glamorous. For example, Cisco’s virtual meeting room includes an IP (Internet Protocol) phone, three broadcast-quality cameras, three ultrasensitive mikes, three 60-inch plasma screens, a crescent-shaped table that seats six and soft back-lighting. “The table is maple to complement faces,” said a Cisco spokeswoman, Jacqueline Pigliucci. The studios are painted in identical colors, to give the impression that the people on the screen are in the same room. Cisco’s 3000 model sells for $299,000. “Double that to $600,000 when you add a similar system at a remote location,” said Mr. Foley. But prices for these high-end systems are dropping. “In September of 2005 we were pricing our new Halos at $550,000,” Mr. Crangle said. Now they are $329,000 and $399,000 for the two models. “Going the video route may seem expensive,” Ms. Schooley of Forrester said. “But if you’re talking about high-level executives moving about in a global company — flying first or business class or in a company jet just to see someone in person — travel adds up and the cost of sophisticated video setups can be a wash.” Mr. Foley said, “We get our money back in less than 12 months.” Companies like ABN Amro, AMD, Heinz, General Electric, PepsiCo and Wachovia are using the new virtual meetings for product briefings, training courses, strategy sessions and inspirational chats. Videoconferencing is taking a bite here and there out of the business-travel pie — but the overall pie keeps getting bigger because of globalization. “Videoconferencing isn’t growing at the expense of travel,” said Caleb Tiller of the National Business Travel Association. “Some 68 percent of our travel managers predicted there would be more trips at their companies this year than in 2006.” Drawing on the latest annual study of 1,400 American business travelers, Peter C. Yesawich, president and chief executive of Yesawich, Pepperdine, Brown & Russell, , an Orlando-based travel trend tracker, says that about 33 percent agree that they are “actively seeking ways to use new technology — and not just videoconferencing — to reduce business travel. But when you do the arithmetic, only 3 percent of all business travelers are taking fewer trips because of the advances in technology.” http://www.iht.com/articles/2007/05/...ness/video.php  Moral Rights or the Outraged Heir: Real-Life Drama at House of Molière Alan Riding Since Bernard-Marie Koltès died in 1989 at 41, his reputation as a playwright has continued to grow. In February, for the first time, one of his plays, “Le Retour au Désert,” entered the repertory of the Comédie-Française, the historic Paris theater popularly known as the House of Molière. Yet soon after Muriel Mayette’s production of the play opened there, Mr. Koltès’s brother, François, who owns the copyright to his works, ordered that it be taken off the stage on June 7 after just 30 performances. The reason? The Algerian character, Aziz, is not being played by an Algerian, as stipulated by the playwright. The French theater world was stunned. Need a German actor play Faust, a Dane play Hamlet? In any event Michel Favory, the French actor cast as Aziz, was considered more than up to the role. So was this political correctness gone crazy? Or was Mr. Koltès justifiably protecting his brother’s legacy? Some of these questions may now be decided in court. The Comédie-Française has sued François Koltès for defamation — he described the theater as cynical — and for damages to recover revenue lost by the cancellation of four performances this season and by the withdrawal of the play from next season’s program. A court hearing is scheduled for Tuesday. But whatever the outcome, the tiff has served to highlight the power and privileges enjoyed by the heirs of creative artists. They may have no artistic talent of their own, but they bask in reflected glory, receive royalties and determine how works are interpreted or exploited. In the European Union, as in most copyright protection in the United States, inherited “moral rights” last for 70 years after the death of the artist, so the greats of the more distant past are open to all sorts of license. A Shakespeare play can be updated to the American South, a Mozart opera can be set in Trump Tower, Marcel Duchamp can add a mustache to the image of Mona Lisa — and no one can object. But when it comes to writers and artists who have died since 1937, legal heirs, not always direct descendants, have the last word. In the visual arts disputes often arise when an image is used commercially without permission. Thus the Picasso estate spends a lot of time trying to chase down the illegal use of Picasso drawings or paintings on everything from coffee mugs and T-shirts to posters and prints, while simultaneously selling his name for use on the Citroën Xsara Picasso car. René Magritte poses a different problem. Although his Surrealist images are also reproduced without authorization, more often they inspire advertising images, like figures floating in the sky borrowed from the bowler-hatted men in “Golconda.” But when an idea, not an image, is lifted, it is not protected by copyright. Salvador Dalí’s extraordinary imagination is no less plagiarized, but he got ahead of the game by commercializing his own images to the point that André Breton turned Dalí’s name into an anagram, Avida Dollars. And if fake Dalís abound, it is also because he is said to have signed hundreds of blank sheets of paper before he died in 1989. More recently the question of ownership of an image has been taken up by some architects, who have claimed copyright over published photographs of buildings they have designed. If recognized, this right will also benefit their heirs. On the other hand, in the performing arts, the creator’s intention is more relevant. In dance, choreographers or their trusted assistants usually oversee interpretation of their work. Yet, after their deaths, even when some estates, like the George Balanchine Foundation, insist on approving new productions, original visions are inevitably blurred by individual dancers. But it is in the literary world where some of the most serious rights battles have erupted. Stephen James Joyce, who controls the moral rights to the works of James Joyce, his grandfather, has become famous for blocking the use of Joyce’s words in publications and even at public readings. (That power will end in 2011, 70 years after Joyce’s death.) Similarly, in theater, the Koltès case is not unique. With Bertolt Brecht and Samuel Beckett, who both wrote stage directions for their plays, new productions must be approved by their estates. And not infrequently, when the interpretation or casting is considered inappropriate, changes are demanded or permission is refused. But is it proper for the creative freedom of stage directors to be restricted by heirs or estates? Ms. Mayette, the director of “Le Retour au Désert,” who is also the general administrator of the Comédie-Française, has argued that “it should be forbidden to forbid.” And she had good reason to feel vindicated last week when two actresses in her production won Molières, the French equivalent of Tony Awards. Ms. Mayette’s casting “sin” was of course minor compared with what happens today to centuries-old operas, which may be variously set in modern times, infused with post-Freudian angst or turned into erotic romps. Long-dead composers can count only on vociferous audiences to guard their legacies. But great stage works survive anyway. Shakespeare’s plays were ripped off during his lifetime, many were radically rewritten in the 17th and 18th centuries, and today they remain vulnerable to the whims of theater fashion. Yet, thanks to their poetry, psychology, humor and drama, ol’ Bill is doing just fine. True, Bernard-Marie Koltès is no Shakespeare. But since many critics regard him as France’s most original playwright in decades, his brother does him no service by depriving theatergoers of the chance to discover him. After all, audiences and directors — not heirs or copyright laws — will eventually decide if his oeuvre is to live on. http://www.iht.com/articles/2007/05/...a/entracte.php  Latest U.S. Free Trade Agreement Contains New Twist Gwen Hinze The US Trade Representative’s Office has just released the text of the U.S.- South Korea Free Trade Agreement and it makes for fascinating reading. As those following the debate around the U.S.’s bilateral free trade agreements will know, since 2002 the last nine free trade agreements have required America’s trading partners to adopt very specific intellectual property laws and to provide a higher level of legal protection than international standards embodied in multilateral treaties. Like those before it, the Korea-US Free Trade Agreement requires Korea to create an anti-circumvention law mirroring the controversial 1998 Digital Millennium Copyright Act, extend the copyright term to 70 years beyond the life of the author (beyond the international standard of life of author plus 50 years), create a pre-established statutory damages regime for potential copyright violations that is likely to chill research and innovation, and to adopt the complex U.S. online service provider “safe harbor” regime. But the Korea FTA also includes several new and decidedly disturbing features. There are three side letters to the Intellectual Property chapter. The second focuses on “book piracy”. The third side letter includes the following statement: “The Parties agree on the objective of shutting down Internet sites that permit the unauthorized reproduction, distribution, or transmission of copyright works, of regularly assessing and actively seeking to reduce the impact of new technological means for committing online copyright piracy, and of providing generally for more effective enforcement of intellectual property rights on the Internet.” This language is extraordinarily broad: it appears to apply not just to websites that are directly infringing copyright, but to any site that can be argued to be “permitting” certain activities – perhaps with BitTorrent in mind. The previous FTAs have been particularly troubling for Internet communications since they have required trading partners to treat all temporary reproductions of images and sound files in computer memory as copyright-infringing, but have not exported the fair use limitation of U.S. copyright law: a limitation that provides important balance within the U.S. system, as well as room for the American technology industry to innovate. As the Ninth Circuit recently affirmed in the Perfect10 v. Google decision, under U.S. law temporary copies necessary to enable end-user use of Internet technologies (such as search engines) are highly transformative, and thus non-infringing fair use. Given that, the FTAs appeared to require trading partners to adopt copyright laws that are inconsistent with, and more stringent than, current U.S. law. (Curiously, the Korean FTA contains a new feature that might go some of the way to addressing this problem. Footnote 11 to Article 18.4(1) might allow room for both countries to “adopt or maintain limitations or exceptions.. for fair use” subject to the so-called Three Step Test. For the sake of Korean ISPs, search engines and Internet innovators, let’s hope this important clarification is implemented in a meaningful way in Korea’s national law). The side letter’s second objective of regularly assessing and actively seeking to reduce the impact of technological means of committing copyright infringement is also dangerously broad. Does it, for instance, require the countries to force ISPs to pro-actively monitor and filter network transmissions for potential copyright infringement - something U.S. ISPs have steadfastly resisted as a matter of principle since the early days of the Internet? That would also be inconsistent with current U.S. copyright law. As the Ninth Circuit recently confirmed in its Perfect10 v. CCBill decision, U.S. ISPs do not have an affirmative duty to police their users for evidence of “repeat infringement” in order to get the benefit of the U.S. safe harbor regime. However, even more disturbing than the open-ended “objectives” are the very specific unilateral obligations given by Korea to the U.S. government in the following paragraphs of the side letter. Korea agrees to “work with the private sector”, the U.S. government and other foreign authorities to “prevent, investigate, and prosecute Internet piracy”; to issue a policy directive within 6 months “establishing clear jurisdiction for effective enforcement against online piracy pursuant to a division or joint investigation team that will investigate and take criminal action for online piracy”, at the request of a rightsholder. Korea agrees on the objective of shutting down websites that permit unauthorized downloading including in particular, “webhard” and peer to peer services. And Korea has also been asked to adopt and provide criminal sanctions to enforce the U.S. secondary copyright liability standard of inducement. Korea agrees to “prosecute individuals and companies that profit from developing and maintaining services that effectively induce infringement.” Aside from the appropriateness of asking trading partners to adopt such specific enforcement obligations in a free trade agreement, the side letter also raises two other concerns. First, how does it fit with the online service provider (OSP) safe harbor regime contained in Article 18.10 (30) of the FTA? Second, does it endanger the end-to-end architecture of the Internet? U.S. copyright law provides statutory safe harbors for four common OSP activities: transitory digital communications, caching, web hosting and provision of information location tools, such as hypertext link-based search engines. There are sound policy reasons for doing so. Safe harbors set out the areas where OSPs can operate without fear of a crippling lawsuits arising out of their own, or their end users’ behavior, providing important legal certainty, and allowing OSPs to manage otherwise unpredictable business risk, thus spurring investment in the development of technology. This, in turn, facilitates access to knowledge and increased online freedom of expression for the world’s citizens. The four safe harbors, contained in section 512 of the U.S. copyright statute, have also been incorporated in the Korea FTA and in the last nine bilateral FTAs. U.S. copyright law also imposes limitations on the type of injunctions that courts can grant against OSPs that quality for the safe harbors. For OSPs who host content, cache or provide location tools and have control over information residing on their networks, courts can order the ISP to terminate a particular subscriber, block access to a particular online site on the OSP’s system or network, and issue any other injunctive relief the court considers necessary to prevent or restrain infringement, so long as it’s the least burdensome option for the OSP. For OSPs that provide connectivity and act as mere conduits, U.S. courts can order the OSP to terminate a particular subscriber, or require an ISP to block access to a particular online location outside of the U.S. No US court has ever required the four major U.S. Internet backbone providers to block access to a foreign country’s website for alleged copyright infringement. This last remedy has the potential to erode the end-to-end nature of the Internet. The one case filed by U.S. copyright owners (and subsequently not pursued) that sought that outcome– RIAA v. Listen4Ever.com – was hotly debated at the time precisely because this would amount to private rightsholders using one country’s national copyright law and judicial apparatus to cut off access to another part of the Internet. Since U.S. law already provides for injunctions to block specified online locations outside of the U.S., does the Korea FTA pose any greater threat to the Internet’s core architecture? It's not clear. It depends what the threshold is for “shutting down websites”. In U.S. law, a court could only require an ISP that is a mere conduit to block access to a foreign website if a copyright owner has successfully proven a case of infringement. By comparison, U.S. law allows for only temporary takedown of a website on an allegation of copyright infringement. The Korea FTA side letter is silent as to whether a website would need to be “shut down” only after determination of a lawsuit or on the much lower standard of mere allegation of copyright infringement. The latter would be the worst of all possible worlds– sacrificing the free flow of information on the Internet on the unproven allegation that a website “permits” unauthorized downloading of copyrighted works. The Korea FTA’s language raises more questions than answers. For the Internet community, the most troubling part of all this is that there will be no opportunity for a public debate on the policy implications of creating this world. That’s because the Korean FTA was negotiated using the USTR’s “fast track” authority under the Trade Promotion Act, which only allows the US Congress to vote to accept or reject the free trade agreement in its entirety. The USTR’s “fast track” authority will expire at the end of June this year, unless renewed by Congress. Whether the Korea FTA side language will become a standard part of the USTR’s template free trade agreement in the future depends on that renewal – something that seems more likely after a recent Bipartisan Deal on environment, labor and patent enforcement standards. Let’s hope Washington DC policy-makers pay attention to the impact of the free trade agreements’ IP provisions on Internet innovation when they make that decision. http://www.eff.org/deeplinks/archives/005287.php#005287  ‘Sicko,’ Castro and the ‘120 Years Club’ Anthony DePalma CUBA works hard to jam American TV signals and keep out decadent Hollywood films. But it’s a good bet that Fidel Castro’s government will turn a blind eye to bootleg copies of “Sicko,” Michael Moore’s newest movie, if they show up on the streets of Havana. “Sicko,” the talk of the Cannes Film Festival last week, savages the American health care system — and along the way extols Cuba’s system as the neatest thing since the white linen guayabera. Mr. Moore transports a handful of sick Americans to Cuba for treatment in the course of the film, which is scheduled to open in the United States next month, and he is apparently dumbfounded that they could get there what they couldn’t get here. “There’s a reason Cubans live on average longer than we do,” he told Time magazine. “I’m not trumpeting Castro or his regime. I just want to say to fellow Americans, ‘C’mon, we’re the United States. If they can do this, we can do it.’ ” But hold on. Do they do it? Live longer than, or even as long as, we do? How could a poor developing country — where annual health care spending averages just $230 a person compared with $6,096 in the United States — come anywhere near matching the richest country in the world? Statistics from the World Health Organization, the C.I.A. and other sources all show that the people of Cuba and the United States have about the same life expectancy — 77 years, give or take a few months — while infant mortality in Cuba is significantly lower than in the United States. Of course, many people regard any figures about Cuba as at least partly fiction. But even if the longevity statistics are correct, they are open to interpretation. Carmelo Mesa-Lago, a professor emeritus of economics at the University of Pittsburgh, said statistics also show that Cuba has a high rate of abortion, which can lower infant mortality rates and improve life expectancy figures. The constant flow of refugees also may affect longevity figures, since those births are recorded but the deaths are not. Despite such skepticism, many medical experts say they do believe that average Cubans can live as long as Americans, and the reason may lie in a combination of what Cuba does well and the United States does poorly, if at all. Dr. Robert N. Butler, president of the International Longevity Center in New York and a Pulitzer Prize-winning author on aging, has traveled to Cuba to see firsthand how doctors are trained. He said a principal reason that some health standards in Cuba approach the high American level is that the Cuban system emphasizes early intervention. Clinic visits are free, and the focus is on preventing disease rather than treating it. Dr. Butler said some of Cuba’s shortcomings may actually improve its health profile. “Because they don’t have up-to-date cars, they tend to have to exercise more by walking,” he said. “And they may not have a surfeit of food, which keeps them from problems like obesity, but they’re not starving, either.” Cuban markets are not always well stocked, but city streets are dotted with hot dog and ice cream vendors. Bellies are full, but such food can cause problems in the future, as they have in the United States. Dr. Butler has just completed a study that shows it is possible that because of the epidemic of obesity in children, “this may be the first generation of Americans to live less long than their parents.” There could be one great leveler for Cubans and Americans. While all Cubans have at least minimal free access to doctors, more than 45 million Americans lack basic health insurance. Many are reluctant to seek early treatment they cannot afford, Dr. Butler said. Instead, they wait to be admitted to an emergency room. “I know Americans tend to be skeptical,” he said, “but health and education are two achievements of the Cuban revolution, and they deserve some credit despite the government’s poor record on human rights.” Universal health care has long given the Cuban regime bragging rights, though there is growing concern about the future. In the decades that Cuba drew financial and military support from the Soviet Union, Mr. Castro poured resources into medical education, creating the largest medical school in Latin America and turning out thousands of doctors to practice around the world. But that changed after the collapse of the Soviets, according to Cuban defectors like Dr. Leonel Cordova. By the time Dr. Cordova started practicing in 1992, equipment and drugs were already becoming scarce. He said he was assigned to a four-block neighborhood in Havana Province where he was supposed to care for about 600 people. “But even if I diagnosed something simple like bronchitis,” he said, “I couldn’t write a prescription for antibiotics, because there were none.” He defected in 2000 while on a medical mission in Zimbabwe and made his way to the United States. He is now an urgent-care physician at Baptist Hospital in Miami. Having practiced medicine in both Cuba and the United States, Dr. Cordova has an unusual perspective for comparison. “Actually there are three systems,” Dr. Cordova said, because Cuba has two: one is for party officials and foreigners like those Mr. Moore brought to Havana. “It is as good as this one here, with all the resources, the best doctors, the best medicines, and nobody pays a cent,” he said. But for the 11 million ordinary Cubans, hospitals are often ill equipped and patients “have to bring their own food, soap, sheets — they have to bring everything.” And up to 20,000 Cuban doctors may be working in Venezuela, creating a shortage in Cuba. Still Cuban officials assert that free health care, a variety of sports programs, a healthy, if limited, diet and cultural activities have kept enough Cubans healthy enough well into old age to warrant starting the 120 Years Club, which enrolls people who are 80 and older and strives to help them reach an even riper old age. Until he had to have emergency surgery last year, Fidel Castro — who turned 80 this year — was considered a model of vibrant long life in Cuba. But it was only last week that he acknowledged in an open letter that his initial surgery by Cuban doctors had been botched. He did not confirm, however, that a specialist had been flown in from Spain last December to help set things right. http://www.iht.com/articles/2007/05/...ess/health.php  MySpace Age Verification... for Parents? Nate Anderson The North Carolina Senate has passed a new law designed to protect minors from the "perils" of social networking sites like MySpace. Concern about sexual predators on such sites has been mounting, with much of the pressure coming from state Attorneys General, including North Carolina's Roy Cooper. Now, state legislatures are starting to take action to "protect the children." North Carolina's proposed law stands out because it at least recognizes the difficulties with requiring social networking sites to do age verification. While age verification works pretty well for adults, it is much harder to do with children. The North Carolina legislation takes this lesson to heart by requiring that parents or guardians first sign up and verify their ages; only then can their children register for accounts. Braden Cox recently testified about the legislation before the North Carolina legislature on behalf of the Netchoice Coalition and said that "there is no way to make sure that someone a user designates as their parent is in fact their parent." He argued that the best way to prevent problems is through education, not regulation—an approach that naturally appeals to the corporate backers of Netchoice. Bills like this could be a sign of things to come. Congress has already considered legislation which would have made social networking sites off-limits at schools and libraries, and state Attorneys General have threatened Bud.tv and other sites with lawsuits if they do not implement stronger age verification systems. Social networking sites have clearly gotten the memo about parental worries, and most are moving proactively to head off criticism and safeguard their users. MySpace, for instance, has announced a program called "Zephyr" that will allow parents to access their children's accounts and keep an eye on their electronic doings. Critics have already dismissed the move as not being good enough. Legislation like that being considered by North Carolina is often dismissed as merely pandering to the "Think of the children!" demographic, but protecting children is part of the government's public safety obligation. Few of the proposals we've seen so far seem like good ways to do this, but North Carolina's approach at least has the virtue of novelty—unlike most video game legislation, which relies on similar rhetoric but has been almost universally struck down by the courts, sometimes at great cost to the states. http://arstechnica.com/news.ars/post...r-parents.html  Man Accused of Parole Violation by Posting Profile on Internet AP A convicted sex offender has been accused of violating parole by creating a profile on the social networking site MySpace.com. Christopher Montefusco, 30, was taken into custody Thursday by state Department of Correction officials. Montefusco had registered two different profiles of himself on the site, Connecticut Attorney General Richard Blumenthal said. Last week, MySpace officials provided law enforcement in all 50 states with the names of more than 5,000 people it had identified as sex offenders who had created profiles. Montefusco had been convicted of first-degree sexual assault on Aug. 30, 1996. He served 2 1/2 years in prison. Montefusco has two years of special parole remaining on his sentence, Blumenthal said. Special parole usually involves close supervision and sometimes mandatory participation in support programs. Blumenthal said that one of the conditions of Montefusco's parole was that he not use a computer or the Internet or access social networking sites such as MySpace without first obtaining permission from his parole officer. "The results here demonstrate the urgent and clear need for this kind of information from MySpace and other social networking sites," Blumenthal said. "Clearly, offenders like this are just the most visible tip of the predator iceberg." Montefusco was being held at the New Haven Correctional Facility pending an appearance at Superior Court in New Haven. If Montefusco is convicted of the parole violation, he could be ordered back to prison for two years. Blumenthal said that Montefusco established his first MySpace profile on Aug. 25, 2005. He established a second profile on Oct. 13, 2005. Social networking sites such as MySpace allow users to create online profiles with photos, music and personal information, and let them send messages to one another and, in many cases, browse other profiles. http://hosted.ap.org/dynamic/stories...06-01-07-13-21  Teen Tests Internet's Lewd Track Record  California High Schooler Allison Stokke, 18, Becomes a Victim Of Unwanted Attention After Photo Is Posted on a Sports Blog Eli Saslow Early this month, 18-year-old Allison Stokke walked into her high school track coach's office and asked if he knew any reliable media consultants. Stokke had tired of constant phone calls, of relentless Internet attention, of interview requests from Boston to Brazil. In her high school track and field career, Stokke had won a 2004 California state pole vaulting title, broken five national records and earned a scholarship to the University of California, yet only track devotees had noticed. Then, in early May, she received e-mails from friends who warned that a year-old picture of Stokke idly adjusting her hair at a track meet in New York had been plastered across the Internet. She had more than 1,000 new messages on her MySpace page. A three-minute video of Stokke standing against a wall and analyzing her performance at another meet had been posted on YouTube and viewed 150,000 times. "I just want to find some way to get this all under control," Stokke told her coach. Three weeks later, Stokke has decided that control is essentially beyond her grasp. Instead, she said, she has learned a distressing lesson in the unruly momentum of the Internet. A fan on a Cal football message board posted a picture of the attractive, athletic pole vaulter. A popular sports blogger in New York found the picture and posted it on his site. Dozens of other bloggers picked up the same image and spread it. Within days, hundreds of thousands of Internet users had searched for Stokke's picture and leered. The wave of attention has steamrolled Stokke and her family in Newport Beach, Calif. She is recognized -- and stared at -- in coffee shops. She locks her doors and tries not to leave the house alone. Her father, Allan Stokke, comes home from his job as a lawyer and searches the Internet. He reads message boards and tries to pick out potential stalkers. "We're keeping a watchful eye," Allan Stokke said. "We have to be smart and deal with it the best we can. It's not something that you can just make go away." On May 8, blogger Matt Ufford received Stokke's picture in an e-mail from one of his readers, and he reacted to Stokke's image on instinct. She was hot. She was 18. Readers of Ufford's WithLeather.com -- a sports blog heavy on comedy, opinion and sometimes sex -- would love her. The picture was taken by a track and field journalist and posted as part of a report on a California prep track Web site. The photo was hardly sexually explicit, which made Ufford's decision to post it even easier. At 5 feet 7, Stokke has smooth, olive-colored skin and toned muscles. In the photo, her vaulting pole rests on her right shoulder. Her right hand appears to be adjusting the elastic band on her ponytail. Her spandex uniform -- black shorts and a white tank top that are standard for a track athlete -- reveals a bare midriff. By targeting his comedic writing to 18- to 35-year-old males, Ufford has built a sports blog that attracts almost 1 million visitors each month. Ufford writes tongue-and-cheek items about the things his readers love: athletes and beautiful women. Stokke qualified as both. She was, therefore, a "no-brainer to write about," Ufford said. He posted her picture and typed a four-paragraph blurb to accompany it. Meet pole vaulter Allison Stokke. . . . Hubba hubba and other grunting sounds. "I understand there are certain people who are put off immediately by the tone of my blog," Ufford said. "Every week, there's somebody who takes offense to something, but that's part of being a comedy writer. If nobody is complaining, it probably wasn't funny. You are hoping for some kind of feedback." By that measure, Ufford's post about Stokke created a landmark for success. He received a handful of angry e-mails, including one from the photographer who threatened to file suit if his picture of Stokke remained on the blog. But Ufford also attracted a record number of visitors in May, thanks largely to Stokke's picture. More than 20 message boards and 30 blogs copied or linked to Ufford's item. From her computer at home, Stokke tracked the spread of her image with dismay and disbelief. She had dealt with this once before, when a track fan posted a lewd comment and a picture of her on a message board two years earlier. Stokke had contacted the poster through e-mail and, a few days later, the image had disappeared. But what could she do now, when a search for her name in Yahoo! revealed almost 310,000 hits? "It's not like I could e-mail everybody on the Internet," Stokke said. For the first week, Stokke tried to ignore the Internet attention. She kept it from her parents. She focused on graduating with a grade-point average above 4.0, on overcoming a knee injury and winning her second state title. But at track meets, twice as many photographers showed up to take her picture. The main office at Newport Harbor High School received dozens of requests for Stokke photo shoots, including one from a risqué magazine in Brazil. Stokke read on message boards that dozens of anonymous strangers had turned her picture into the background image on their computers. She felt violated. It was like becoming the victim of a crime, Stokke said. Her body had been stolen and turned into a public commodity, critiqued in fan forums devoted to everything from hip-hop to Hollywood. After dinner one evening in mid-May, Stokke asked her parents to gather around the computer. She gave them the Internet tour that she believed now defined her: to the unofficial Allison Stokke fan page ( http://www.allisonstokke.com), complete with a rolling slideshow of 12 pictures; to the fan group on MySpace, with about 1,000 members; to the message boards and chat forums where hundreds of anonymous users looked at Stokke's picture and posted sexual fantasies. "All of it is like locker room talk," said Cindy Stokke, Allison's mom. "This kind of stuff has been going on for years. But now, locker room talk is just out there in the public. And all of us can read it, even her mother." An impostor created a fake profile of Stokke on Facebook, a social networking site intended mainly for college students. Stokke's classmates at Newport Harbor High School started receiving Facebook messages that seemed to be from Stokke -- except she typed in Southern jargon and listed her interests as only "BOYS!!!!" Last week, Stokke wrote a complaint letter to Facebook, and it immediately took down the fake profile. She hasn't contacted any other Web sites, she said. Allan Stokke, a defense attorney, studied California's statutes so he would know if he saw or read anything about his daughter that went beyond distasteful to illegal. "Even if none of it is illegal, it just all feels really demeaning," Allison Stokke said. "I worked so hard for pole vaulting and all this other stuff, and it's almost like that doesn't matter. Nobody sees that. Nobody really sees me." Last Friday night, Stokke stood underneath the stadium lights at Cerritos College here, 20 miles southeast of downtown Los Angeles. A few thousands fans had come to watch a postseason meet, and dozens of photographers and cameramen roamed the field. Before her first jump, Stokke tried to control her breathing as she chatted with her coach. A good jump here would qualify her for the state championship in Sacramento. A former gymnast, Stokke had tried pole vaulting as a lark as a freshman in high school. Two months later, she set a school record. She won the 2004 state championship three months after that. Stokke had augmented her natural, pole-vaulting disposition -- speed, upper-body strength and courage -- by lifting weights three times each week. College programs including Harvard, Stanford and UCLA also recruited her. During her meet at Cerritos College, Stokke cleared 11 feet, then 12 feet, then 13 feet and qualified for the state meet. By the time she stared ahead at a bar set 13 feet 6 inches, all other nine pole vaulters had maxed out. Stokke warmed up by herself, the only athlete left. She loved pole vaulting because it was a sport built on intricacies. Each motion required calculation and precision. A well-executed vault blended a dancer's timing, a sprinter's speed and a gymnast's grace. "There's so much that happens in a vault below the surface," Stokke said. As the sun set Friday night, Stokke positioned her pole as if she were jousting and sprinted about 100 feet toward the bar. She ran on her tip-toes, like she'd learned from ballet. As she approached her mark, Stokke bent her pole into the ground and coiled her legs to her chest. She lifted upward, twisting her torso 180 degrees as she passed over the bar. It was a beautiful clearance, and the crowd stood to applaud. Back on the ground, her vault accomplished, Stokke smiled and took in the scene around her. In the stands and on the field, she was surrounded by cameras. And for a second Stokke wondered: What, exactly, had they captured? And where, exactly, would it go? http://www.washingtonpost.com/wp-dyn...pid=sec-sports  For Pornographers, Internet’s Virtues Turn to Vices Matt Richtel The Internet was supposed to be a tremendous boon for the pornography industry, creating a global market of images and videos accessible from the privacy of a home computer. For a time it worked, with wider distribution and social acceptance driving a steady increase in sales. But now the established pornography business is in decline — and the Internet is being held responsible. The online availability of free or low-cost photos and videos has begun to take a fierce toll on sales of X-rated DVDs. Inexpensive digital technology has paved the way for aspiring amateur pornographers, who are flooding the market, while everyone in the industry is giving away more material to lure paying customers. And unlike consumers looking for music and other media, viewers of pornography do not seem to mind giving up brand-name producers and performers for anonymous ones, or a well-lighted movie set for a ratty couch at an amateur videographer’s house. After years of essentially steady increases, sales and rentals of pornographic videos were $3.62 billion in 2006, down from $4.28 billion in 2005, according to estimates by AVN, an industry trade publication. If the situation does not change, the overall $13 billion sex-related entertainment market may shrink this year, said Paul Fishbein, president of AVN Media Network, the magazine’s publisher. The industry’s online revenue is substantial but is not growing quickly enough to make up for the drop in video income. Older companies in the industry are responding with better production values and more sophisticated Web offerings. But to their chagrin, making and distributing pornography have become a lot easier. “People are making movies in their houses and dragging and dropping them” onto free Web sites, said Harvey Kaplan, a former maker of pornographic movies and now chief executive of GoGoBill.com, which processes payments for pornographic Web sites. “It’s killing the marketplace.” It is an unusual twist on the Internet-transforms-industry story. The Internet quickly presented a challenge to some businesses, like recorded music and newspapers. But initially, the digital age led to a kind of mainstreaming of pornography by providing easy and anonymous access online. The spread of high-speed Internet access promised even further growth. Instead, faster connections have simply allowed people to download free movies more quickly, and allowed amateur moviemakers to upload their creations easily. Perhaps counterintuitively, the market continues to be flooded with new video releases, both online and on disc. Mr. Fishbein said that this year he expected to see more than 1,000 X-rated DVDs a month produced for retail sale, a figure driven in part by the new spate of low-budget filmmakers. “The barrier to get into the industry is so low: you need a video camera and a couple of people who will have sex,” Mr. Fishbein said. Some companies say they have had success with selling subscriptions to their Web sites, and in offering movies for download or watching online. But Internet revenue, while growing modestly, is not compensating for the drop in video sales and rentals. In 2006, revenue from online subscriptions and sales was $2.8 billion, up from $2.5 billion in 2005, according to estimates from AVN — an increase but nothing near the e-commerce growth enjoyed by many industries. The more traditional pornographic film companies are not giving up, of course. They say they have an answer to the new competition: quality. They are seeking to differentiate themselves from makers of inexpensive films by selling with fancier packaging in stores or through slicker Web sites, and by using better cameras and more experienced directors and performers. They are banking that viewers will be discerning when it comes to sex. “We use good-quality lighting and very good sound,” said David Joseph, president of Red Light District, a production company in Los Angeles that has made films like “Obscene Behavior.” Mr. Joseph said his company did not waste its time, or that of the viewers, on unnecessary plot lines. “There’s not a whole lot of story — it’s basically right to the sex, but we’re consistent with the quality,” he said, noting that the company is also careful to pick interesting backdrops. “We use different locations, rooms and couches.” Red Light’s sales have dropped more than 30 percent in the last two years. To counter the trend, Mr. Joseph says the company plans to start giving film buyers an extra promotional DVD with more scenes from its movies, which typically cost $20. He also plans to improve the packaging of his DVDs. A similar tactic is planned by Sean Logan, chief of Nectar Entertainment, which has made movies like “Exxxtasy Island.” Business is down 25 percent in the last year, Mr. Logan said, and, because his movies cost $50,000 to $80,000 to make, he cannot afford to compete with some DVD competitors who are dropping their prices as low as a few dollars a film to maintain their volume of sales. But Mr. Logan said he could improve his packaging for retail shelves. He has begun adding a sleeve around his box covers that includes a foil logo and metallic sheen to bring out the images, as was done on “Brazilian Island Trilogy.” He said he was sticking to his plan to shoot his movies in exotic locations like Brazil or simulating them with elaborate sets. For the movie “Mystified,” Nectar built an elaborate set that included a waterfall in a warehouse in Canoga Park, Calif. It is not your everyday backdrop for hard-core sex, Mr. Logan noted: “It looks like ‘Lord of the Rings.’ ” Nectar, like Red Light, recently introduced a redesigned Web site to compete better online. Nectar charges $29.95 a month for access, which allows members to look at thousands of still photos and stream 35 movies from its library. But this is a far cry from the price and the volume of free X-rated content available on some sites. One site operated by Adult Entertainment Broadcast Network has 200,000 videos, many of them submitted by amateur videographers, said Scott Coffman, the company’s president. “We get input from all over the world — Japan, Germany, Brazil,” Mr. Coffman said, noting that even he was surprised by the number of contributors. “It’s the same thing as YouTube, where you’re wondering, How many people out there have cameras and are filming this stuff?” Mr. Coffman said he was not in the business of giving away content. About half the videos submitted to the site, he said, are from pornographic movie companies looking to get viewers interested and persuade them to pay for a longer download or DVD. Some companies pay to have their clips displayed on the site, and some give it a cut of the revenue if a visitor turns into a customer. In fact, many of the free video clips circulating online are distributed by companies using them as marketing tools. Mr. Kaplan of GoGoBill.com said he thought that was a failed strategy. “They think that if they give people enough of a free sample, they’ll come back and pay, but that’s not true,” he said. The reality, he said, is that people are surfing for free material, getting what they want and then leaving. But some in the industry disagree. Manny Ulele, the founder of a Las Vegas-based video production company and Web site, said the use of these teaser videos was turning the online pornography business into something of a science. (That is not his real name, but one he uses for business purposes.) Mr. Ulele said his company could pay $500 to $600 a day to get its short clips listed prominently on popular video clearinghouses. He said that fee could be justified by the rates at which people follow through: 1 in 1,000 viewers of the free content click onto his site, he said, and 1 in 600 of those might buy something — a subscription, DVD or other product. Over all, he said, his Web site has around 10,000 customers paying $30 a month to download or stream video clips. “The perception of the consumer is that there is free porn,” Mr. Ulele said. “But most of it nowadays is controlled.” He added that he and other operators understood what length of video clip, and what kind of clip, would hook viewers. “We’ve been fine-tuning it for years,” he said. “We’re able to determine exactly what works and what doesn’t.” http://www.nytimes.com/2007/06/02/te...02porn.html?hp  Super Hi-Vision Makes Your HDTV Obsolete Already Adam Frucci You think your HDTV is impressive? Your HDTV sucks. Sorry, I don't mean to be a jerk, but it's no longer cutting edge. 1920x1080? Please. Japanese broadcaster NHK has come up with what they call Super Hi-Vision, and it puts HD to shame with an insane resolution of 7680x4320. Yeah, that's the equivalent of 16 HDTVs crammed into one. Like I said, your HDTV sucks. That's not all: The viewing distance can be four times as close as HDTV (.75 times the screen height versus 3 times the screen height for HDTV). Fortunately (or unfortunately, depending), you won't need to toss your HDTV for a SHV set anytime soon. That humungous resolution requires an insane 24Gbps stream for broadcast, which is nowhere near what we're currently capable of. Furthermore, they just developed the first sensor for cameras so they can actually, you know, shoot video at that resolution, but there's still a lot of work to be done. Seeing that NHK are the dudes who developed HDTV in 1969, it might be a while before these things start ending up in living rooms. http://gizmodo.com/gadgets/inadequac...ady-264077.php  Semantic Search: An Antidote for Poor Relevancy Dr. Riza C. Berkan Editor's Note: This is a guest post by the CEO of Hakia, Dr Riza C. Berkan. I want to stress that this post is NOT an advertorial - in fact I made it a condition of publication that the post should focus on the theory of semantic search and it should mention Hakia's competition, both of which Dr Berkan has done. I should also mention that while Hakia ads sometimes appear on this site, they are managed separately by FM Publishing. In any case the reason for this post by Dr Berkan is purely to explore the topic of semantic search and try to get a conversation going. Semantic search is seen as one of the next-generation search methods that may challenge Google, so the idea with this post is to understand it better - and perhaps debate its future in the comments. How satisfied search engine users are today is an on-going debate. However, there is wide consensus, from a scientific viewpoint on the competency of the current search engines: They are half-way to the target and there is huge room for improvement. Semantic search is now under the magnifying glass and the question is "can semantic search be an antidote for poor relevancy?" Let's start with "what is semantic search?" Academically speaking, semantic search ought to be a system which understands both the user's query and the Web text using cognitive algorithms similar to that of the human brain, then brings results that are dead on target (right context) at first glance (not requiring to open the Web page for further investigation.) There are several ideas on how to build such a system. But before looking into these variations, let's clarify one thing. A semantic system cannot be called "semantic" if it does not encapsulate the knowledge of languages. From this very basic fundamental requirement, we have to exclude all those fancy algorithms that rely on collecting statistics of links, symbols, words, clicking behaviors, and so forth. Statistics is a tool, not a model of a solution. To go the distance, we need a deterministic model of a language processing solution. We need algorithms that match the meaning of concepts (rather than mere words) and emulate "understanding." For example, the query "what is Palladium useful for?" may bring search results related to the London Palladium Theatre by statistical methods (a popular subject) as opposed to the actual meaning of the query which is not very popular. A semantic algorithm can easily identify that "useful for" implies the element Palladium. The two basic views of a semantic search are identified by the location of the semantic resources to be implanted. The first view is to embed the semantic resources in the Web pages themselves. It is called the "Semantic Web". Why not compose Web pages in a structure that is semantics friendly? The second approach is to locate the semantic resources in search engines which deploy algorithms that use them. This is called "Semantic Search Engine" and works on any text. The "Semantic Web" approach has been around for a long time now. Unfortunately, it is based on an unrealistic assumption that every Web author will abide by the complex rules of semantics - not to mention the education it requires - and place content in the correct buckets of mysteriously unified standards. Another form of this approach may be to design Web factories that crank out refined Web pages once fed by ordinary Web pages. Of course if there is more than one factory, you have the standards issue again. In this day and age of fast content production, the Semantic Web seems to be more idealism than realism. The option of "Semantic Search Engine" has yet to be tested. My company hakia, along with others like Powerset, Cognition Search, and Lexxe are taking steps in this new direction. There are challenges with this approach as well. First and foremost, the knowledge of languages must be built in a structure that would allow a scalable and speedy search process. Building such resources is an expensive, tedious, and time consuming endeavor. Then, all the Web pages must be analyzed using this system to prepare for a retrieval platform; another time-consuming process. But when all of this is done properly, the users will start to experience something totally new. Let me emphasize the word "properly" here, which is an entirely new discussion point. One of the first impacts of semantic search engine will be on the handling of long-tail queries. Without relying on statistics, long-tail queries can be analyzed by semantic algorithms on the fly, and bring search results with the accurate context. With such a capability, we are talking about finding answers to longer than usual, complex, and unpopular queries. Let's make no mistake about it. The long-tail is the bottom part of the iceberg under the water. Philosophically, the number of long-tail queries is infinite where as the tip-of-the-iceberg queries can fit on one large hard drive. Popularity algorithms fail at the long-tail queries (by definition) because there is never enough statistical sampling. Many people are not realizing the fact that long-tail queries are partly personal queries (uniquely unpopular and complex reflecting individual personalities.) Thus, the idea of "personalized search" actually requires semantic capabilities without the need for tracking the user's behavior unless it is been tracked for psychological profiling. In a similar argument, queries against dynamic content are also long-tail queries. Because dynamic content, like news, decays its value very fast during which there is no time to collect statistics. By the time the link referrals are made, or click statistics are collected, the content is no longer in demand. Therefore, a semantic approach is very effective in handling dynamic content and can unleash its full power the second the content is born. Semantic search is definitely an antidote for poor relevancy; but only time will tell how well this can be done. I will close this with a few commonly asked questions. Q. How can a semantic search engine recognize a popular Web page compared to an unpopular one for a given query term(s)? A. A semantic search engine recognizes the correct context for a given query term(s). Once the context is correct, popularity becomes irrelevant, and credibility must be questioned. Credibility of a Web page is a relatively easy task to detect. As a result, if you have the correct context from a credible source, the job is done. You can test this logic for any query today. The popularity method is a replacement of these capabilities as a crude approximation. Q. If the user types "madonna", how would a semantic search engine understands the intent of the user? (i.e., is it the artist, or the religious figure?) A. Semantic Search engine is not a psychic. Thus, attempting to guess the intent is futile for an under-represented query. But the solution is easy, just to give back the user search results of all possible senses of the word. Even better, categorize them neatly. This is within the design envelope of semantic search engines. Q. How can a semantic search engine be manipulated by spam pages? A. If done properly, a semantic search engine cannot be manipulated by text. Because it specializes on detecting the right context, the spammers will have to put the right context for the right query; which is no longer spam per definition. The abuses related to image and video are possible. But these kinds of abuses are common today and can be detected in different ways. Q. Will semantic search take over today's search engines? A. In the long run, they most likely will. Again, this depends on how well they are done. Once the long-tail searches start to show the difference, then it will probably have a domino effect. If people are satisfied in the complex query domain, they are more likely to switch for simple queries as well. Let's remember that there is no cost to switch. Q. There were previous failed attempts of natural language search engines. Why would this work now? A. Natural Language is a wide term that includes all sorts of things. Previous attempts have failed mostly because they were not done properly, and methods used were not based on proper semantic principles. Some of them were merely statistical methods very similar to the conventional search engines. Others were behavior tracking AI applications. And some relied on human labor to keep up with question answering. There are so many ways of doing it improperly, and only one way of doing it right. Q. How would the advertising systems be affected by semantic search? A. The impact will be very big, perhaps more than the search itself. A semantic advertising system, which can detect the right context most of the time in a consistent manner, means a huge jump in ROI. Q. What is the single most drastic problem in front of semantic search today? A. Misconceptions and hype. Business continuity must rely on honest declarations of what is to be expected in accordance with the pace of development. Semantic search is a difficult technological endeavor; it takes time and patience. Investments with short-term agendas will hurt this newly emerging technology sector. http://www.readwriteweb.com/archives..._relevancy.php  Better than Google? Creator Thinks So Rob Gabriel Google is keeping a close eye on a small, suburban Melbourne start-up that claims to be developing a search engine that improves on the world leader. MyLiveSearch, which plans to go live as a public beta in a few weeks, is the brainchild of self-taught software developer Rob Gabriel. Mr Gabriel, 35, says his search engine gives better, more relevant results than the search king because it is a truly "live" search. Google's search engine works by building a vast index of web pages, via automated "spiders" that crawl through billions of web pages a year. However this represents only a fraction of the enormous, sprawling internet, and the index can never be entirely up to date. Yahoo! search and (despite its name) Microsoft's Live search work the same way. MyLiveSearch is fundamentally different. It works through a small browser plug-in. The search terms are put through Google, or other indexed search databases, but those results are treated as "starting points" alongside the user's bookmarks and other popular web hubs. From there, the live search takes over, crawling through hundreds of web pages connected to those starting points in search of more information relevant to the search. Mr Gabriel says the results come back in seconds, and are almost always richer, more detailed and more useful than a standard, index-based search. His product can also search the so-called "invisible web" of dynamically-generated web pages that search engines have trouble indexing. "This has the potential to change the way people search the internet," he said. "Google can't search every page every day (to build its index). The web is so dynamic and changes so often - MyLiveSearch turns your own computer into a 'super-spider' to search it in real time. "This technology could be snapped onto any of the major search engines and improve them." A Google business development representative has met with the MyLiveSearch team at least twice - once when the technology was at a very early stage, and again last week after Next made inquiries about Google's interest in the project. Google did not want to comment on MyLiveSearch, except in general terms. "We're really keen to support Australian developers and IT entrepreneurs," spokesman Rob Shilkin said. "Google Maps was a small Aussie start-up. And Google itself started as two guys in a garage." The company has a history of acquiring technology that might help a competitor. In April last year Google bought the rights to an advanced text-search algorithm invented by University of NSW student Ori Allon. Mr Allon, 26, was given a job at Google's headquarters at Mountain View, California. Mr Gabriel said the meeting last week inspired him to go to Silicon Valley next month to spruik his technology. "It started as a dream and the dream is slowly developing into a reality far greater than all my expectations," he said. Mr Gabriel has worked on MyLiveSearch for two years, along with his younger brother, Mark, and systems engineer Mende Jurukovski - though the original idea came to him 10 years ago. Live search is one solution. Despite Google's immense computing resources, the ranging "googlebot" cannot track updates to the web in real time. The more popular websites are "recrawled" more frequently. Outside the net mainstream, however, visits from the Googlebot are more rare. Even sites that are actively trying to promote themselves can take weeks or even months to turn up on Google's index. Some estimate that even Google has only indexed less than a fifth of the internet. One solution to this problem is "live indexing", where pages are submitted to the search engine and instantly indexed. Another solution is ad-hoc distributed web crawling. The open source Nutch project hopes that tens, hundreds or even thousands of Nutch-powered, specialised web search engines could combine into an index more comprehensive than any single proprietary site. http://www.brisbanetimes.com.au/news...205209239.html  The Concerts Found Onstage While Everyone Else Takes a Break Daniel J. Wakin For seven years, Christopher DeLaurenti went to orchestral concerts wired, wearing a leather vest with microphones nestled in the shoulders and cables running down the back. Come intermission, when the audience wandered out, Mr. DeLaurenti perked up. He made his way toward the stage. With his MiniDisc recorder running, he secretly captured the random sounds that followed: woodwind noodles, honks of oboe reeds, the murmur of voices, the scraping of chairs. For Mr. DeLaurenti, 39, a Seattle-based “sound artist” and composer, the noises were art. Now, out of more than 50 hours of recording, he has compiled a CD of greatest hits. It is called “Favorite Intermissions: Music Before and Between Beethoven, Stravinsky, Holst,” the latest entry in humankind’s search for art in unexpected nooks. “Every composer, every sound artist, every musician, poses a fundamental question to everyone else,” Mr. DeLaurenti said in an interview. “It’s a request to listen. I have faith that in any sound or collection of sounds, music lies therein. “It does sound crazy,” he continued. “Craziness is the root of many great musical ideas and the source for new ways of listening and considering the world around us.” The recordings at first may have all the allure of watching moss grow. But when the tracks on Mr. DeLaurenti’s CD are heard together, with his theories and the history of the musical avant-garde in the background, they make a crazy kind of sense as performances. The first number, “Holst, Hitherto,” comes from an intermission before a performance of Holst’s “Planets.” It opens with an audience murmur and a clarinet flourish, then a few quiet whumps from a bass drum and a repeated glockenspiel note. A woman laughs. A man says, “Excuse me.” Snare-drum rolls swell, a tambourine shimmers, the timpani thud, a xylophonist plays. (The intermission music seems heavy on percussionists, maybe because they tend to practice so obsessively.) Then beefy bassoon notes swirl, and a trombone plays exercises in different keys. Soon snatches of melodies from “The Planets” are recognizable. The volume of instruments and crowd noises grows at a steady pace, until a burst of applause greeting the concertmaster quiets everything down. The oboe sounds its tuning A, finally uniting all the instruments. Silence erupts. Mr. DeLaurenti’s first piece ends. In his liner notes for the CD, he says, “One duty of the composer is to expose the unexpected, overlooked and hidden skeins of music woven in the world around us.” Music has many definitions, he writes. “I hope recording and presenting these intermissions in some small way abets and accelerates the ongoing redefinition of music in our culture towards moving, meaningful, coherent listening.” Intermissions, he added in the interview, are a rare time when classical musicians can be heard improvising together. The recording falls firmly in the conceptual tradition championed by John Cage, who turned randomness into a compositional tool. Witness his “Imaginary Landscape No. 4” for 12 radios, or “4’33,” ” in which a pianist sits silently at the keyboard for 4 minutes 33 seconds and ambient sounds become the performance. Mr. DeLaurenti also identifies himself as a phonographer, one who creates pieces out of field recordings. One of his major works is “Live in New York at the Republican National Convention Protest September 2-August 28, 2004.” A 1999 work consists of a coupon titled “By Reading This You Are Performing This Score So Give Me 50 Cents.” Following the instructions means the piece has been performed. Many of the composer’s works, including “Favorite Intermissions,” are available on delaurenti.net, his Web site. Mr. DeLaurenti’s search for intermission music became something of an obsession. “I couldn’t go to concerts with other people anymore,” he said. “My girlfriend got very upset, because I would disappear at intermission.” The recording itself became a performance, he said, because every movement of his body would alter the way the sound was captured. “I became entranced in doing it,” he said. He recently decided to quit; his efforts were beginning to seem redundant. “It seemed irresponsible to keep recording more,” he said. Virtually all concert halls ban photography or recording, and contracts with musicians’ unions strictly govern what can be preserved, so Mr. DeLaurenti had to go under cover. He said he was never caught but occasionally drew suspicious looks from ushers. He honed a technique of often shifting his posture and moving around. “Most people are not observant and rarely look at one thing for longer than 10 seconds,” he said. He also showed unfailing courtesy when questioned. “People don’t want trouble,” he explained. He has not identified the orchestras in the recordings, he added, to avoid problems but also to maintain a more universal character in the works. At least one orchestra executive seemed untroubled by his methods. “I don’t see that being harmful,” said Mark Volpe, the president of the Boston Symphony Orchestra. “I don’t think the musicians have any expectations that the intermission, which is mostly crowd noise, is proprietary.” And anyway, Mr. Volpe said, there’s not much to be gained by legal action. “What are the damages?” The president of the American Federation of Musicians, Thomas F. Lee, did not return messages seeking comment on the recording. Leonard Leibowitz, a lawyer who represents orchestral and musicians’ unions, said Mr. DeLaurenti’s activity was probably harmless. “It’s not the music that’s being sold,” he added. “It’s the sound of intermission.” At the New York Philharmonic, a spokesman, Eric Latzky, said: “Every effort is made to curtail illegal recording of the concerts of the New York Philharmonic. Whether or not what this person is making is art is not for us to say.” Mr. DeLaurenti grew up in Seattle, the son of a jazz pianist. His grandfather rented out instruments to school bands and, when he died in the mid-1980s, left Mr. DeLaurenti some of his stock. Mr. DeLaurenti taught himself how to play many of the instruments. He attended Evergreen State College in Olympia, Wash., and now makes a living through freelance writing, grants, commissions, CD sales, computer consulting and even computer repair. The intermissions CD was released in a run of about 1,000 copies this year by GD Stereo, a tiny label run by an architect, Jeffrey Dugan, in Upper Manhattan. Its cover includes a blurred photograph of Mr. DeLaurenti, sneaked when he was standing close to the stage at Avery Fisher Hall during a New York Philharmonic intermission (which, he said, is not on the recording). Its design is also a knockoff of the classic Deutsche Grammophon label, which Mr. DeLaurenti called a “seal of approval and a seal of quality.” He called the name of the label, GD Stereo, a “delicious irony.” Deutsche Grammophon did not respond to an inquiry left with a spokeswoman for its American distributor, Universal Classics. “I feel I will have succeeded,” Mr. DeLaurenti said, “if someone merely looks at the package and says, ‘Oh, I should listen next time at intermission and see if I hear something musical.’ ” http://www.nytimes.com/2007/05/30/ar...ic/30inte.html  Encryption Vendor Claims AACS Infringes its Patents, SUES SONY Nate Anderson Canadian encryption vendor Certicom yesterday filed a wide-ranging lawsuit against Sony, claiming that many of the products offered by the electronics giant infringe on two Certicom patents. This might sound like business as usual until you realize what's being targeted: AACS and (by extension) the PlayStation 3. Certicom has done extensive work in elliptic curve cryptography (ECC), and the patents in question build on this work. The patents have already been licensed by groups like the US National Security Agency, which paid $25 million back in 2003 for the right to use 26 Certicom patents, including the two in the Sony case. Now, Certicom wants Sony to pay up, claiming that encryption present in several key Sony technologies violates Certicom patents on "Strengthened public key protocol" and "Digital signatures on a Smartcard." The biggest charge is that the encryption in AACS itself is infringing. The practical implications of this claim are huge; AACS is included in Sony's Blu-ray players, PlayStation 3, and Blu-ray and PS3 discs. Certicom says Sony needs to take out a license for all of these uses. In addition, the company claims that the Digital Transmission Content Protection (DTCP) scheme is also infringing, and it seeks damages for every Sony i.LINK (IEEE 1394) implementation that uses DTCP and every Sony product that uses DTCP-IP. This includes all VAIO computers with i.LINK ports along with a whole host of Sony TVs and a few DVD players; one home theater receiver is even on the list. This certainly could be bad news for Sony. If there's one thing that the company doesn't want to see, it's a cost increase for PS3 manufacturing. But the bigger story is that Certicom has the potential to go after every product that uses AACS, including HD DVD and Blu-ray discs and drives from many of the deepest-pocketed companies in the business. http://arstechnica.com/news.ars/post...sues-sony.html  New Processing Key Found!! (MKB v3 is Now Open) I guess its official now. The new Processing Key was posted by BtCB on freedom to tinker about a week ago (release day +1). its: Code: 45 5F E1 04 22 CA 29 C4 93 3F 95 05 2B 79 2A B2 Save it. Store it. This opens up all newly released (and many to be released) HD DVD and Blu-ray discs. Wanna understand: go here. Regards, arnezami PS. I strongly advise everybody who knows how it was retrieved not to talk about it publicly. -- Btw: To get a VUK you first need to get the Volume ID of the disc (there are several ways). If you have that you can use aacskeys with this Volume ID as input. http://forum.doom9.org/showthread.ph...40#post1008940  New AACS "Fix" Hacked in a Day Jeremy Reimer The ongoing war between content producers and hackers over the AACS copy protection used in HD DVD and Blu-ray discs produced yet another skirmish last week, and as has been the case as of late, the hackers came out on top. The hacker "BtCB" posted the new decryption key for AACS on the Freedom to Tinker web site, just one day after the AACS Licensing Authority (AACS LA) issued the key. In true tongue-in-cheek hacker fashion, the site posted the 128-bit key as a method of decrypting a small haiku that they placed on the same page, noting that it just might accidentally (wink, wink) be the same key that will decrypt new high-definition discs as well. The AACS protection method is quite convoluted, and it's worth taking a brief look back at how the cracks have slowly chipped away at its effectiveness: Simplified high-def decryption diagram, courtesy of arnezami. All the items on the disc itself—the Master Key Block or MKB, the Volume ID, the encrypted title key, and the encrypted content—can be read directly off the disc. The MKB contains multiple encrypted copies of the media key, and when decrypted by unique Device Keys (each standalone player and software player has its own) provides the master Processing Key (Km—the yellow line above). An earlier hack removed the need to find the Private Host Key, so a simple AES-G encryption with the Processing Key and Volume ID is all that is needed to generate the Volume Unique Key (Kvu). The Week in Review is edited and published by Jack Spratts. The Kvu is then combined with the encrypted title key stored on the disc to create the Title Key (Kt) that can then be used to unprotect all the content on the disc. Some of the first AACS hacks simply read the Kvu directly from memory when running a software-based player such as WinDVD, but mandatory software updates keep closing this loophole. The AACS LA is not happy about these Processing Keys being released. When previous keys were leaked, the organization vowed that it would remove the keys from the Internet with cease-and-desist orders. Predictably, this only encouraged people to post them more. The whole series of affairs evokes memories of when DVD decryption was all the rage, and the DeCSS code wound up being printed on t-shirts to express the futility of trying to sue anyone who used or even knew about it. The decryption code for AACS cannot fit easily on a t-shirt, but the 128-bit Processing Keys can, and it's clear that no matter how many times the AACS LA revokes old keys, the new ones are going to be found and released. In the end, the extra money spent developing the intricate and complex AACS system gave hackers a diverting game to play while they went about their work, a game that looks likely to continue. AACS does stop casual copying, but it hasn't prevented unencrypted HD content from being distributed over the Internet. This doesn't mean the AACS LA is giving up, however. Blu-ray discs with a further layer of copy protection called BD+ are rumored to be nearing delivery, which will give hackers more work to do. http://arstechnica.com/news.ars/post...-in-a-day.html  Amazing Mystery of the New AACS Key Leak Cory Doctorow Today I had a remarkable conversation with an anonymous tipster who had a fascinating story to tell about the latest AACS key leak: The world became a little more magical yesterday with the publication of a new "processing key" that can be used to unlock the AACS copy protection on the latest round of HD-DVD movies. This event is remarkable not only for its timing--barely a week after the release of the discs that the key was intended to secure--but also for the clever way in which the key first appeared on the net. Though this second part of the story hasn't received much attention, it deserves to go down in the annals of hacker lore. The previous processing key, 09 F9 …, began circulating in February being discovered by a hacker named arnezami. With this 128-bit number, anyone could strip the encryption from every HD-DVD title on the market. The key was reposted on thousands of sites, and quickly made it to the front page of Digg. When Digg tried to censor the key in response to DMCA threats from the AACS authorities, users staged a revolt, reposting it in hundreds of creative ways. The movie studios switched to technological countermeasures, and, starting last week, all new HD-DVD titles were modified so that the key couldn't decrypt them. Hackers began furiously searching for a new key. In the mean time, Ed Felten of Freedom-to-Tinker satirized the idea that someone could have legal rights to a number. He wrote a blog post, "You Can Own an Integer Too," that gives each reader his or her very own randomly generated 128-bit integer. Hundreds proudly posted their shiny new integers in the comments, some humorously threatening legal action against anyone who would copy them: BC Says: 5D 4A F0 D9 58 04 3B 06 C8 B2 59 85 A1 5D 6A 88 For the record!! This ones mine. You can look but don't touch. Anonymous Says: B8 5C 6D 1E 07 F9 AB 5E 0F 0D 48 A5 3B 1F 6B C7 use it and ill sue! be prepared! Blending in with the rest was this innocuous looking message from a user named BtCB: BtCB Says: Here's mine: 45 5F E1 04 22 CA 29 C4 93 3F 95 05 2B 79 2A B2 What are the odds that this is the new processing key? (Hint for arnezami: uv=00000047) Of course, the odds are basically zero if the number was chosen at random. You have a better chance of winning the Powerball jackpot four days in a row. So, for more than a week, everyone who read the comment assumed that it was just another joke. But one thing about it was different: the cryptic hint to arnezami, a "uv" number, a pointer to a specific key within the AACS keyspace. You can probably guess the rest of the story. Eventually someone tipped off arnezami about the strange comment, and he tried using the 45 5F … number to decrypt the new discs. It worked! It really is the new processing key. As a result, all HD-DVDs are open to the public again, at least until new titles can be updated once more. The next move belongs to the AACS authorities. They're smart enough to know that they can't take the food coloring out of the pool. So will they send out another round of cease-and-desist letters, possibly sparking another revolt, or will they graciously admit defeat for now? http://www.boingboing.net/2007/05/31...tery_of_t.html  I Didn’t Download it, My Router Got Hacked! enigmax People accused of uploading the game ‘Dream Pinball’ who claim they are the victim of a hacker, are starting to get letters back from lawyers explaining what they should do next. Among other things, the lawyers are demanding that the accused demonstrate computer security skills in providing evidence detailing exactly how their equipment was exploited. Earlier this year, 500 people received letters accusing them of illegally distributing a computer game. The letters demand a settlement payment, or a court appearance was threatened. Many people wondered how they were caught at all, while others claimed they had no knowledge of such a game and stopped to consider that their router security may have been compromised. If security features are not enabled on a router, anyone can easily fall victim to an authorized connection. In this case, it’s feared that someone may have accessed an unsecured router, downloaded and redistributed even just a tiny piece of this file via BitTorrent or eMule, with the router’s owner getting the blame. Lawyers representing the game’s publisher state as fact that a full copy of a game must have been uploaded to their monitors for the infringement to be flagged - clearly the lawyers have no idea how a protocol like BitTorrent operates. It would be virtually impossible to download a large file in it’s entirety from just one source and the time it would take would prove totally impractical. There is a very real probability that a tiny transfer of a few hundred kilobytes can trigger legal action against an alleged infringer, a transfer easily achieved by someone accessing a victim’s router for just a few seconds. People who are using this defense are now starting to receive letters, part of which reads; If it is your contention that at the relevant time you did all that you could to secure your network and PC but that, nevertheless, an intrusion occurred and that the infringing act complained of was perpetrated by a person or a person unknown who gained access to the network without your permission, please provide (in accordance with the Practice Directions for Pre-Action Protocol) all copies of the essential documents on which you rely. In other words, forget ‘Innocent Until Proven Guilty‘ and start getting used to ‘Guilty! Now Prove Yourself Innocent!‘ In terms of evidence, the lawyer Davenport Lyons representing the publisher Zuxxez, demands to see; 1. A copy of the instructions accompanying the router 2. Evidence to prove the use of anti-virus software and firewall 3. Evidence detailing exactly how the computer was compromised. 4. Evidence to prove the victim took adequate measures to prevent the intrusion. Despite the fact that producing evidence should be up to the lawyers when dealing with cases, quite how the production of a router manual will affect this case is unclear. Presumably you send off the manual for their tech people to look at, then they use the fact that your router is ‘easily secured’ or the fact that you didn’t read the book, against you. The manner in which PC based anti-virus and firewall software protects an illegally accessed router is also unclear. More worrying is the implication in point 3 that the accused must give a technical report as to how the breach took place, something no-one but an expert could provide - clearly trying to put a fair defense out of reach for the less well-off. The reality of the situation is that an assertion by the accused that the claimed activity was not carried out by him, is sufficient. As for point 4, I do not believe there is a legal requirement for an internet user to train themselves in security before operating a router and connecting to an ISP, nor has there been a decision in an English court to state that an internet subscriber is responsible for the actions of others whilst using his connection. Davenport Lyons have informed users that people in Germany are responsible for what happens on their connections but German law isn’t valid in the UK. This is another important point which these lawyers seem to have purposely overlooked and one which makes them appear to be attempting to misdirect people by quoting an irrelevant case from from a completely different country. Furthermore, even though they demand ‘evidence’, don’t think for one minute that corresponding with these lawyers is something that can bear fruit. One unfortunate gentleman whose wife has been wrongly accused of distributing the game has been talking to Davenport Lyons via letter, trying to sort the matter out, until he received a letter from them with this paragraph; ….we consider that to enter into further correspondence with you on technical or evidential points is unnecessary and unhelpful and will serve only to increase costs. We are therefore instructed not to continue this circular correspondence. So by this measure, trying to clear your name is deemed “unecessary and unhelpful’ by the lawyers, something which is considered by many as one of the cornerstones of British justice and a fundamental right of it’s citizens. Of course, if you’re a lawyer working on tight profit margins, any correspondence will cut into that profit. ‘Unhelpful’ indeed. The letter finishes up; ‘If we do not receive a response from you within the next fourteen days we will take our client’s instructions regarding the issuing of proceedings against you’ “Instructions which could be to ‘drop it’…” says a regular Usenet poster on the issue. http://torrentfreak.com/i-didnt-down...er-got-hacked/  For the hacker who has everything The Slurpr WiFi Aggregator Promises "Free" Broadband -- and Jail Time Thomas Ricker  Oh my, the 5-0 won't like this one bit. Meet The Slurpr, a WiFi access point which aggregates up to six "available" (read: unprotected) 54Mbps WiFi channels into one bigazz, "free" connection. It's the latest invention by Dutch hacker, Mark Hoekstra and his new sidekick (or is it the other way around?) Boris. Of course, use of the Slurpr in its current incarnation will likely violate wardriving laws in at least few countries. So the inclusion of Mark's next feature -- 64/128-bit WEP-cracking -- could well land you in a Turkish prison. Still interested, Billy? Then head on over to Mark's site where you can pre-order the €999 / $1,347 box today. http://www.engadget.com/2007/05/29/t...band-and-jail/ Until next week, - js.  Current Week In Review  Recent WiRs - May 26th, May 19th, May 12th, May 5th, April 28th Jack Spratts' Week In Review is published every Friday. Submit letters, articles and press releases in plain text English to jackspratts (at) lycos (dot) com. Submission deadlines are Thursdays @ 1400 UTC. Please include contact info. Questions or comments? Call 213-814-0165, country code U.S.. "The First Amendment rests on the assumption that the widest possible dissemination of information from diverse and antagonistic sources is essential to the welfare of the public." - Hugo Black |
|
|

|
|
|
#3 |
|
Thanks for being with arse
Join Date: Jan 2002
Location: The other side of the world
Posts: 10,343
|
bumper issue !
 |
|
|

|
 |
| Thread Tools | Search this Thread |
| Display Modes | |
|
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| Peer-To-Peer News - The Week In Review - May 19th, '07 | JackSpratts | Peer to Peer | 1 | 16-05-07 09:58 AM |
| Peer-To-Peer News - The Week In Review - December 9th, '06 | JackSpratts | Peer to Peer | 5 | 09-12-06 03:01 PM |
| Peer-To-Peer News - The Week In Review - September 16th, '06 | JackSpratts | Peer to Peer | 2 | 14-09-06 09:25 PM |
| Peer-To-Peer News - The Week In Review - July 22nd, '06 | JackSpratts | Peer to Peer | 1 | 20-07-06 03:03 PM |
| Peer-To-Peer News - The Week In Review - June 24th, ’06 | JackSpratts | Peer to Peer | 1 | 22-06-06 12:02 PM |